内存检测工具Sanitizers
Sanitizers介绍
Sanitizers 是谷歌开源的内存检测工具,包括AddressSanitizer、MemorySanitizer、ThreadSanitizer、LeakSanitizer。
Sanitizers是LLVM的一部分。
gcc4.8:支持Address和Thread Sanitizer。
gcc4.9:支持Leak Sanitizer和UBSanitizer。
注意:gcc不支持MemorySanitizer。
可以支持的内存检测问题:
(1)heap use after free 堆内存释放后继续使用
(2)stack use after return 栈内存函数返回后继续使用
(3)stack use after scope 栈内存在作用域范围外继续使用
(4)heap buffer overflow 堆内存溢出
(5)stack buffer overflow 栈内存溢出
(6)global buffer overflow 全局内存溢出
(7)memory leaks 内存泄露
(8)double free 堆内存重复释放
(9)initialization order bugs 初始化命令错误
编译参数:
(1)(2)(3)(4)(5)(6):-fsanitize=address
(7):-fsanitize=address 或者 -fsanitize=leak
(8):-fsanitize=address
(9):-fsanitize=memory
编译参数通过 -fsanitize 决定开启 sanitizer:
-fsanitize=address
开启AddressSanitizer(ASan),包括LeakSanitizer(LSan),检测:地址越界 和 内存泄漏。
-fsanitize=leak
开启LeakSanitizer(LSan),检测:内存泄漏。
-fsanitize=address 和 -fsanitize=leak 都能检测 内存泄漏。
-fsanitize=thread
开启ThreadSanitizer(TSan),检测:数据竞争和死锁。
-fsanitize=undefined
开启UndefinedBehaviorSanitizer(UBSsan),检测:未定义行为。
-fsanitize=memory
开启MemorySanitizer(MSan),检测:未初始化内存问题。(gcc不支持MemorySanitizer)
-fno-omit-frame-pointer
检测到内存错误时打印函数调用栈,这个参数一直都带上。
检测案例
编译器:gcc/g++
(1)heap use after free 堆内存释放后继续使用
#include <stdio.h>
int main (int argc, char* argv[]) {int* p = new int[100];delete [] p;int num = p[0];return 0;
}
编译命令:
g++ -o out main.cpp -g -fsanitize=address -fno-omit-frame-pointer
执行命令:
./out
=================================================================
==10606==ERROR: AddressSanitizer: heap-use-after-free on address 0x61400000fe40 at pc 0x00000040075d bp 0x7ffe7a4adfe0 sp 0x7ffe7a4adfd8
READ of size 4 at 0x61400000fe40 thread T0#0 0x40075c in main /home/code/main.cpp:5#1 0x7efec0def504 in __libc_start_main (/lib64/libc.so.6+0x22504)#2 0x400628 (/home/code/out+0x400628)0x61400000fe40 is located 0 bytes inside of 400-byte region [0x61400000fe40,0x61400000ffd0)
freed by thread T0 here:#0 0x7efec1ac1f2a in operator delete[](void*) ../../../../libsanitizer/asan/asan_new_delete.cc:96#1 0x400725 in main /home/code/main.cpp:4#2 0x7efec0def504 in __libc_start_main (/lib64/libc.so.6+0x22504)previously allocated by thread T0 here:#0 0x7efec1ac19ea in operator new[](unsigned long) ../../../../libsanitizer/asan/asan_new_delete.cc:62#1 0x40070e in main /home/code/main.cpp:3#2 0x7efec0def504 in __libc_start_main (/lib64/libc.so.6+0x22504)SUMMARY: AddressSanitizer: heap-use-after-free /home/code/main.cpp:5 main
Shadow bytes around the buggy address:0x0c287fff9f70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa0x0c287fff9f80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa0x0c287fff9f90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa0x0c287fff9fa0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa0x0c287fff9fb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c287fff9fc0: fa fa fa fa fa fa fa fa[fd]fd fd fd fd fd fd fd0x0c287fff9fd0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd0x0c287fff9fe0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd0x0c287fff9ff0: fd fd fd fd fd fd fd fd fd fd fa fa fa fa fa fa0x0c287fffa000: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa0x0c287fffa010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):Addressable: 00Partially addressable: 01 02 03 04 05 06 07Heap left redzone: faHeap right redzone: fbFreed heap region: fdStack left redzone: f1Stack mid redzone: f2Stack right redzone: f3Stack partial redzone: f4Stack after return: f5Stack use after scope: f8Global redzone: f9Global init order: f6Poisoned by user: f7Container overflow: fcArray cookie: acIntra object redzone: bbASan internal: fe
==10606==ABORTING
(2)stack use after return 栈内存函数返回后继续使用
#include <stdio.h>
int* p = NULL;
void fun() {int a[10];p = a; // 或者 p = &a[0];
}
int main(int argc, char* argv[]) {fun();int num = p[0];return 0;
}
编译命令:
g++ -o out main.cpp -g -fsanitize=address -fno-omit-frame-pointer
执行命令:
ASAN_OPTIONS=detect_stack_use_after_return=1 ./out
注意: 默认没有开启,需要在运行时开启。
=================================================================
==18619==ERROR: AddressSanitizer: stack-use-after-return on address 0x7f4f81500020 at pc 0x0000004008ea bp 0x7fffb49f6700 sp 0x7fffb49f66f8
WRITE of size 4 at 0x7f4f81500020 thread T0#0 0x4008e9 in main /home/code/main.cpp:9#1 0x7f4f84a7a504 in __libc_start_main (/lib64/libc.so.6+0x22504)#2 0x400708 (/home/code/out+0x400708)Address 0x7f4f81500020 is located in stack of thread T0 at offset 32 in frame#0 0x4007e5 in fun() /home/code/main.cpp:3This frame has 1 object(s):[32, 72) 'a' <== Memory access at offset 32 is inside this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-use-after-return /home/code/main.cpp:9 main
Shadow bytes around the buggy address:0x0fea70297fb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0fea70297fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0fea70297fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0fea70297fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0fea70297ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0fea70298000: f5 f5 f5 f5[f5]f5 f5 f5 f5 f5 f5 f5 f5 f5 f5 f50x0fea70298010: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0fea70298020: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0fea70298030: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0fea70298040: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0fea70298050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):Addressable: 00Partially addressable: 01 02 03 04 05 06 07Heap left redzone: faHeap right redzone: fbFreed heap region: fdStack left redzone: f1Stack mid redzone: f2Stack right redzone: f3Stack partial redzone: f4Stack after return: f5Stack use after scope: f8Global redzone: f9Global init order: f6Poisoned by user: f7Container overflow: fcArray cookie: acIntra object redzone: bbASan internal: fe
==18619==ABORTING
(3)stack use after scope 栈内存在作用域范围外继续使用
暂时还没有找到能够检测出来的样例。
(4)heap buffer overflow 堆内存溢出
#include <stdio.h>
int main (int argc, char* argv[]) {int* p = new int[100];int num = p[100];delete [] p;return 0;
}
编译命令:
g++ -o out main.cpp -g -fsanitize=address -fno-omit-frame-pointer
执行命令:
./out
=================================================================
==9226==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61400000ffd0 at pc 0x000000400750 bp 0x7ffef70c5d80 sp 0x7ffef70c5d78
READ of size 4 at 0x61400000ffd0 thread T0#0 0x40074f in main /home/code/main.cpp:4#1 0x7f12e7482504 in __libc_start_main (/lib64/libc.so.6+0x22504)#2 0x400628 (/home/code/out+0x400628)0x61400000ffd0 is located 0 bytes to the right of 400-byte region [0x61400000fe40,0x61400000ffd0)
allocated by thread T0 here:#0 0x7f12e81549ea in operator new[](unsigned long) ../../../../libsanitizer/asan/asan_new_delete.cc:62#1 0x40070e in main /home/code/main.cpp:3#2 0x7f12e7482504 in __libc_start_main (/lib64/libc.so.6+0x22504)SUMMARY: AddressSanitizer: heap-buffer-overflow /home/code/main.cpp:4 main
Shadow bytes around the buggy address:0x0c287fff9fa0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa0x0c287fff9fb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa0x0c287fff9fc0: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 000x0c287fff9fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0c287fff9fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c287fff9ff0: 00 00 00 00 00 00 00 00 00 00[fa]fa fa fa fa fa0x0c287fffa000: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa0x0c287fffa010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa0x0c287fffa020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa0x0c287fffa030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa0x0c287fffa040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):Addressable: 00Partially addressable: 01 02 03 04 05 06 07Heap left redzone: faHeap right redzone: fbFreed heap region: fdStack left redzone: f1Stack mid redzone: f2Stack right redzone: f3Stack partial redzone: f4Stack after return: f5Stack use after scope: f8Global redzone: f9Global init order: f6Poisoned by user: f7Container overflow: fcArray cookie: acIntra object redzone: bbASan internal: fe
==9226==ABORTING
(5)stack buffer overflow 栈内存溢出
#include <stdio.h>
int main(int argc, char* argv[]) {int a[2] = {100,200};int num = a[2];return 0;
}
编译命令:
g++ -o out main.cpp -g -fsanitize=address -fno-omit-frame-pointer
执行命令:
./out
=================================================================
==787==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffcade3daa8 at pc 0x0000004007df bp 0x7ffcade3da50 sp 0x7ffcade3da48
READ of size 4 at 0x7ffcade3daa8 thread T0#0 0x4007de in main /home/code/main.cpp:4#1 0x7f8c39562504 in __libc_start_main (/lib64/libc.so.6+0x22504)#2 0x400648 (/home/code/out+0x400648)Address 0x7ffcade3daa8 is located in stack of thread T0 at offset 40 in frame#0 0x400725 in main /home/code/main.cpp:2This frame has 1 object(s):[32, 40) 'a' <== Memory access at offset 40 overflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow /home/code/main.cpp:4 main
Shadow bytes around the buggy address:0x100015bbfb00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x100015bbfb10: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x100015bbfb20: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x100015bbfb30: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x100015bbfb40: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x100015bbfb50: f1 f1 f1 f1 00[f4]f4 f4 f3 f3 f3 f3 00 00 00 000x100015bbfb60: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x100015bbfb70: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x100015bbfb80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x100015bbfb90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x100015bbfba0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):Addressable: 00Partially addressable: 01 02 03 04 05 06 07Heap left redzone: faHeap right redzone: fbFreed heap region: fdStack left redzone: f1Stack mid redzone: f2Stack right redzone: f3Stack partial redzone: f4Stack after return: f5Stack use after scope: f8Global redzone: f9Global init order: f6Poisoned by user: f7Container overflow: fcArray cookie: acIntra object redzone: bbASan internal: fe
==787==ABORTING
(6)global buffer overflow 全局内存溢出
#include <stdio.h>
int a[100];
int main(int argc, char* argv[]) {int num = a[100];return 0;
}
编译命令:
g++ -o out main.cpp -g -fsanitize=address -fno-omit-frame-pointer
执行命令:
./out
=================================================================
==9628==ERROR: AddressSanitizer: global-buffer-overflow on address 0x000000601270 at pc 0x000000400755 bp 0x7ffd15bcd0d0 sp 0x7ffd15bcd0c8
READ of size 4 at 0x000000601270 thread T0#0 0x400754 in main /home/code/main.cpp:4#1 0x7fc3d46e9504 in __libc_start_main (/lib64/libc.so.6+0x22504)#2 0x400648 (/home/code/out+0x400648)0x000000601270 is located 0 bytes to the right of global variable 'array' defined in 'main.cpp:2:5' (0x6010e0) of size 400
SUMMARY: AddressSanitizer: global-buffer-overflow /home/code/main.cpp:4 main
Shadow bytes around the buggy address:0x0000800b81f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0000800b8200: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0000800b8210: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0000800b8220: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0000800b8230: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0000800b8240: 00 00 00 00 00 00 00 00 00 00 00 00 00 00[f9]f90x0000800b8250: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 000x0000800b8260: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0000800b8270: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0000800b8280: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 000x0000800b8290: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):Addressable: 00Partially addressable: 01 02 03 04 05 06 07Heap left redzone: faHeap right redzone: fbFreed heap region: fdStack left redzone: f1Stack mid redzone: f2Stack right redzone: f3Stack partial redzone: f4Stack after return: f5Stack use after scope: f8Global redzone: f9Global init order: f6Poisoned by user: f7Container overflow: fcArray cookie: acIntra object redzone: bbASan internal: fe
==9628==ABORTING
(7)memory leaks 内存泄露
#include <stdlib.h>
int main(int argc, char *argv[]) {int* p = (int*)malloc(10 * sizeof(int));return 0;
}
编译命令:
g++ -o out main.cpp -g -fsanitize=address -fno-omit-frame-pointer
或者
g++ -o out main.cpp -g -fsanitize=leak -fno-omit-frame-pointer
执行命令:
./out
=================================================================
==12458==ERROR: LeakSanitizer: detected memory leaksDirect leak of 40 byte(s) in 1 object(s) allocated from:#0 0x7f36642dc5e6 in __interceptor_malloc ../../../../libsanitizer/lsan/lsan_interceptors.cc:51#1 0x400611 in main /home/code/main.cpp:3#2 0x7f3663692504 in __libc_start_main (/lib64/libc.so.6+0x22504)SUMMARY: LeakSanitizer: 40 byte(s) leaked in 1 allocation(s).
(8)double free 堆内存重复释放
#include <stdio.h>
int main(int argc, char* argv[]) {int* p = new int[10];delete [] p;delete [] p;return 0;
}
编译命令:
g++ -o out main.cpp -g -fsanitize=address -fno-omit-frame-pointer
执行命令:
./out
=================================================================
==31497==ERROR: AddressSanitizer: attempting double-free on 0x60400000dfd0 in thread T0:#0 0x7fa32a746f2a in operator delete[](void*) ../../../../libsanitizer/asan/asan_new_delete.cc:96#1 0x4006d8 in main /home/code/main.cpp:5#2 0x7fa329a74504 in __libc_start_main (/lib64/libc.so.6+0x22504)#3 0x4005c8 (/home/code/out+0x4005c8)0x60400000dfd0 is located 0 bytes inside of 40-byte region [0x60400000dfd0,0x60400000dff8)
freed by thread T0 here:#0 0x7fa32a746f2a in operator delete[](void*) ../../../../libsanitizer/asan/asan_new_delete.cc:96#1 0x4006c5 in main /home/code/main.cpp:4#2 0x7fa329a74504 in __libc_start_main (/lib64/libc.so.6+0x22504)previously allocated by thread T0 here:#0 0x7fa32a7469ea in operator new[](unsigned long) ../../../../libsanitizer/asan/asan_new_delete.cc:62#1 0x4006ae in main /home/code/main.cpp:3#2 0x7fa329a74504 in __libc_start_main (/lib64/libc.so.6+0x22504)SUMMARY: AddressSanitizer: double-free ../../../../libsanitizer/asan/asan_new_delete.cc:96 operator delete[](void*)
==31497==ABORTING
(9)initialization order bugs 初始化命令错误
暂时还没有找到能够检测出来的样例。
相关文章:

内存检测工具Sanitizers
Sanitizers介绍 Sanitizers 是谷歌开源的内存检测工具,包括AddressSanitizer、MemorySanitizer、ThreadSanitizer、LeakSanitizer。 Sanitizers是LLVM的一部分。 gcc4.8:支持Address和Thread Sanitizer。 gcc4.9:支持Leak Sanitizer和UBSani…...

Triton : OpenAI 开发的用于Gpu开发语言
Triton : OpenAI 开发的用于Gpu开发语言https://openai.com/blog/triton/1、介绍 https://openai.com/blog/triton/ 2、git地址 https://github.com/openai/triton 3、论文 http://www.eecs.harvard.edu/~htk/publication/2019-mapl-tillet-kung-cox.pdf SIMD : Single Inst…...
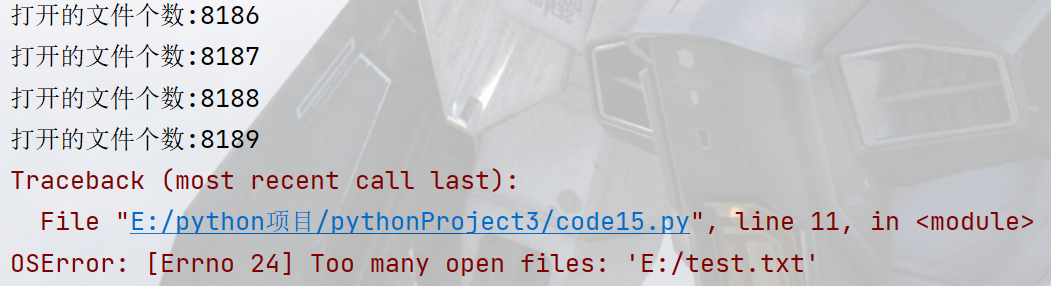
Python文件操作-代码案例
文章目录文件打开文件open写文件上下文管理器第三方库简单应用案例使用python生成二维码使用python操作excel程序员鼓励师学生管理系统文件 变量就在内存中,文件在硬盘中. 内存空间更小,访问速度快,成本贵,数据容易丢失,硬盘空间大,访问慢,偏移,持久化存储. \\在才是 \的含义…...

活动目录(Active Directory)管理,AD自动化
每个IT管理员几乎每天都在Active Directory管理中面临许多挑战,尤其是在管理Active Directory用户帐户方面。手动配置用户属性非常耗时、令人厌烦且容易出错,尤其是在大型、复杂的 Windows 网络中。Active Directory管理员和IT经理大多必须执行重复和世俗…...
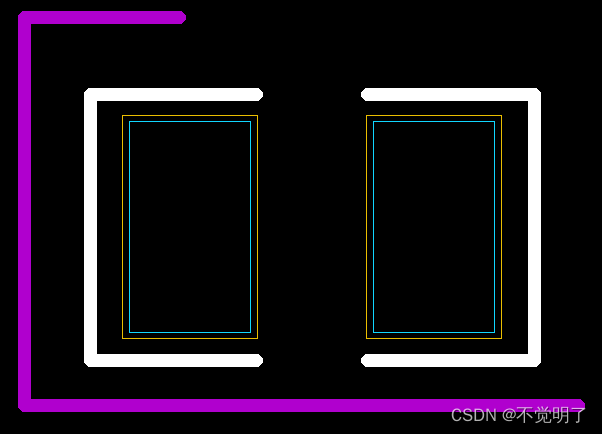
Allegro如何使用Vertext命令修改丝印线段的形状操作指导
Allegro如何使用Vertext命令修改丝印线段的形状操作指导 在用Allegro画丝印线段的时候,如果画了一段不是自己需要形状的线段,无需删除重画,可以用Vertext命令直接编辑 如下图 修改前 修改后 具体操作如下 选择Edit...

Leetcode力扣秋招刷题路-0030
从0开始的秋招刷题路,记录下所刷每道题的题解,帮助自己回顾总结 30. 串联所有单词的子串 给定一个字符串 s 和一个字符串数组 words。 words 中所有字符串 长度相同。 s 中的 串联子串 是指一个包含 words 中所有字符串以任意顺序排列连接起来的子串。…...
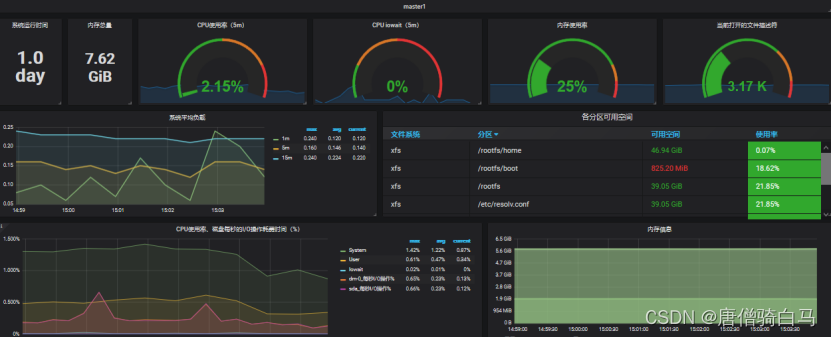
基于Prometheus和k8s搭建监控系统
文章目录1、实验环境2、Prometheus介绍?3、Prometheus特点3.1 样本4、Prometheus组件介绍5、Prometheus和zabbix对比分析6、Prometheus的几种部署模式6.1 基本高可用模式6.2 基本高可用远程存储6.3 基本HA 远程存储 联邦集群方案7、Prometheus的四种数据类型7.1 C…...
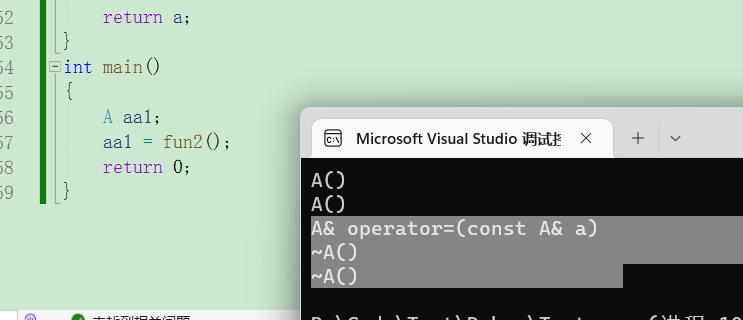
类和对象(下)
类和对象(下)再谈构造函数构造函数体赋值初始化列表explicit关键字static成员静态成员的特性友元友元函数友元类成员函数做友元内部类匿名对象编译器的一些优化再谈构造函数 构造函数体赋值 在创建对象的时候编译器会调用构造函数给对象中的成员变量一…...

达梦数据库单机部署
一、安装前准备 1. 安装环境 操作系统:redhat7.9 达梦数据库版本:V8 内存:2G CPU:x86_64 2. 新建用户组和用户 groupadd dinstall useradd -g dinstall -m -d /home/dmdba -S /bin/bash dmdba passwd dmdba3. 配置参数 vi /etc/security/limits.conf #在末尾添加以下内…...
状态和路由)
从零到一学习Flutter——(二)状态和路由
背景 前文提到了Widget的状态,在Flutter中一切都是Widget,那么由Widget组成的页面,会有很多复杂的父子关系,要想交互友好,则需要这些Widget进行通讯,也就是所谓的状态管理。 同时在了解了布局之后,我们会写出很多的页面,那么在这些页面切换,也是一个很重要的能力。 …...
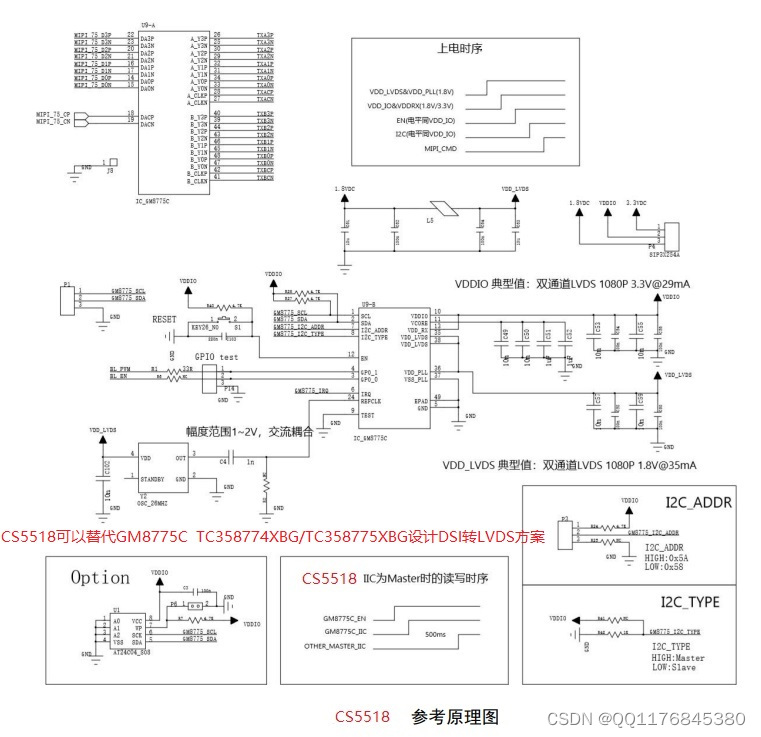
TC358774XBG/TC358775XBG替代方案|CS5518替代TC358774XBG/TC358775XBG设计DSI转LVSD设计资料
TC358774XBG/TC358775XBG替代方案|CS5518替代TC358774XBG/TC358775XBG设计DSI转LVSD设计资料 TC358774XBG/TC358775XBG 芯片的主要功能是作为 DSI - LVDS 通信协议桥接,主芯片的视频数据可通过 DSI 链路流 出,以驱动兼容 LVDS 的显示板。换句话说&#x…...
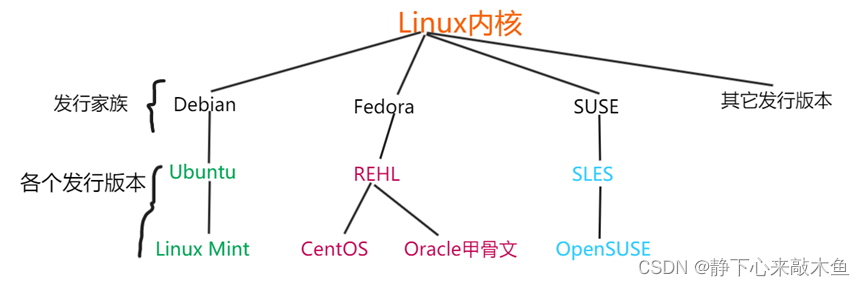
Linux---Kernal与Shell讲解
目录 Shell简介 什么是Shell Shell分类 内核Kernal Shell简介 什么是Shell 我们首先需要知道一台完整的计算机是由硬件组成的,而人不可以直接与硬件交互,为了完成交互,进行了以下的操作 将硬件设备交由内核管理,给硬件套个内…...
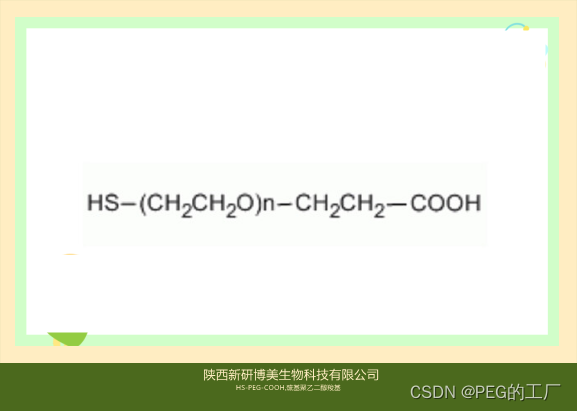
Thiol-PEG-Acid,HS-PEG-COOH,巯基-聚乙二醇-羧基试剂供应
一:产品描述 1、名称 英文:HS-PEG-COOH,Thiol-PEG-Acid 中文:巯基-聚乙二醇-羧基 2、CAS编号:N/A 3、所属分类:Carboxylic acid PEG Thiol PEG 4、分子量:可定制,Thiol-聚乙二…...
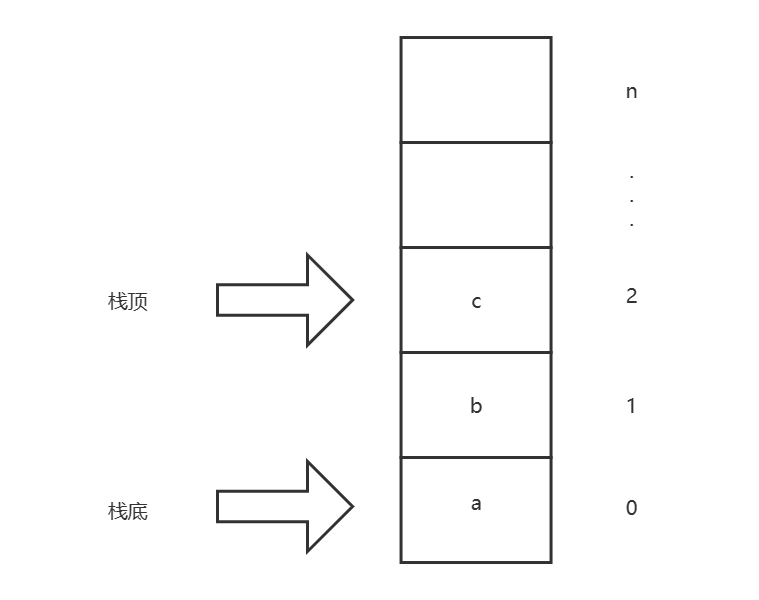
数据结构与算法基础-学习-09-线性表之栈的理解、初始化顺序栈、判断顺序栈空、获取顺序栈长度的实现
一、个人理解栈是线性表的一种衍生,和之前的顺序表和链表在插入和删除元素上有较大差异,其他基本相同,栈是数据只能插入表的尾部(栈顶),删除数据时只能删除表的尾部(栈顶)数据&#…...
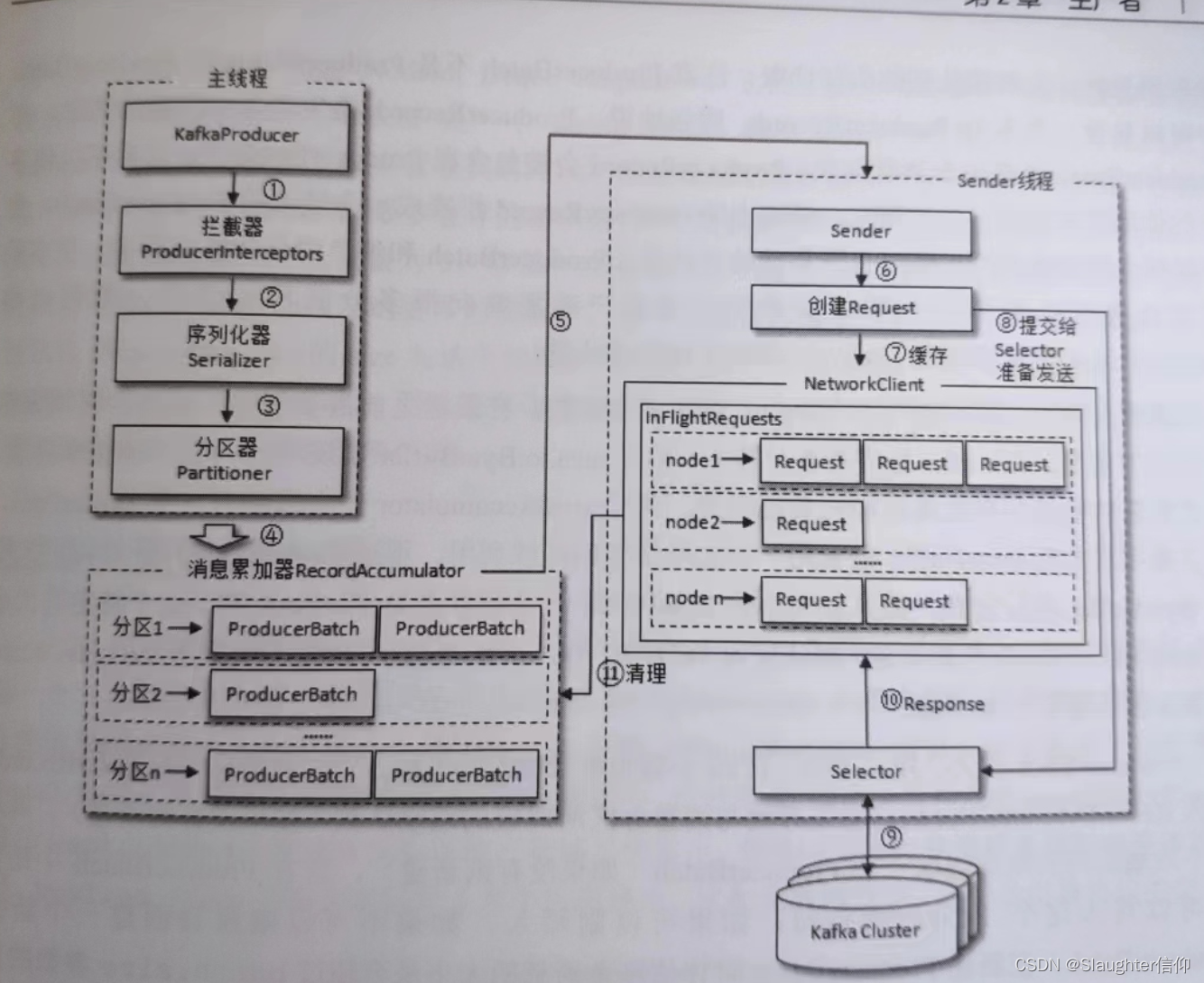
深入Kafka核心设计与实践原理读书笔记第二章
1 生产者 生产逻辑 配置生产者客户端参数及创建相应的生产者实例。构建待发送的消息。发送消息关闭实列 参数说明 bootstrap.servers :用来指定生产者客户端链接Kafka集群搜需要的broker地址清单,具体格式 host1:port1,host2:port2,可以设置一个或多…...

知乎kol投放怎么做?知乎kol资源从哪里找?
每个领域都有一些比较专业且具有话语权的大V博主,他们推荐某个产品或是品牌就能对粉丝产生很深的影响力,影响用户消费决策。 互联网时代,每个热门的内容平台上都活跃着一大批kol博主,做kol投放具有很高的商业价值。 知乎内容社区…...

python设计模式-享元设计模式,抽象工厂设计模式,面向对象设计模式
享元设计模式 享元(flyweight)设计模式属于结构设计模式类别。 它提供了一种减少对象数的方法。 它包含各种有助于改进应用程序结构的功能。享元对象最重要的特性是不可变的。 这意味着一旦构建就不能修改它们。 该模式使用HashMap来存储引用对象 如何实现享元(flyweight)设计…...

10条终身受益的Salesforce职业发展建议!
Salesforce这个千亿美金巨兽,在全球范围内有42,000多名员工。作为一家发展迅速的科技公司,一直在招聘各种角色,包括销售、营销、工程师和管理人员等。 据IDC估计,从2016年到2020年,该生态系统创造了190万个工作岗位。…...
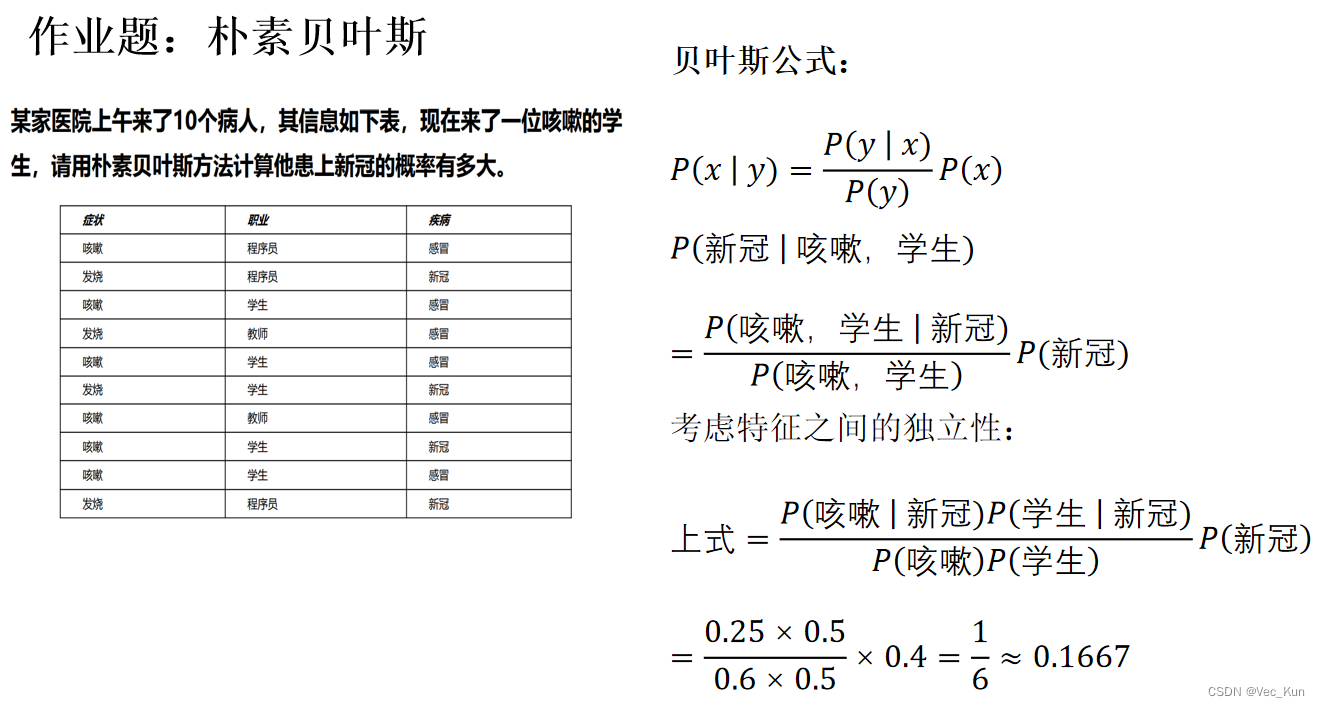
电子科技大学人工智能期末复习笔记(四):概率与贝叶斯网络
目录 前言 概率 概率公式 贝叶斯公式 链式条件概率 例题 1. 求联合概率分布/边缘概率分布/条件概率分布 2. 灵活运用贝叶斯公式 概率总结 贝叶斯网络 判断独立性 两个事件独立的判断 条件独立性的判断 假设条件独立的链式法则 ⚠Active / Inactive Paths 判断独…...
码上掘金实现电子木鱼
前言 前几天在朋友圈看到“敲电子木鱼”的视频,敲一下木鱼就提示“功德 1”,还带有敲击声和念经的声音,感觉挺有意思的。 心血来潮,捣鼓了一晚上,借助码上掘金实现了这个功能。 展示效果 素材 准备素材如下&#…...

Vim 调用外部命令学习笔记
Vim 外部命令集成完全指南 文章目录 Vim 外部命令集成完全指南核心概念理解命令语法解析语法对比 常用外部命令详解文本排序与去重文本筛选与搜索高级 grep 搜索技巧文本替换与编辑字符处理高级文本处理编程语言处理其他实用命令 范围操作示例指定行范围处理复合命令示例 实用技…...

Android Wi-Fi 连接失败日志分析
1. Android wifi 关键日志总结 (1) Wi-Fi 断开 (CTRL-EVENT-DISCONNECTED reason3) 日志相关部分: 06-05 10:48:40.987 943 943 I wpa_supplicant: wlan0: CTRL-EVENT-DISCONNECTED bssid44:9b:c1:57:a8:90 reason3 locally_generated1解析: CTR…...

java调用dll出现unsatisfiedLinkError以及JNA和JNI的区别
UnsatisfiedLinkError 在对接硬件设备中,我们会遇到使用 java 调用 dll文件 的情况,此时大概率出现UnsatisfiedLinkError链接错误,原因可能有如下几种 类名错误包名错误方法名参数错误使用 JNI 协议调用,结果 dll 未实现 JNI 协…...

Qwen3-Embedding-0.6B深度解析:多语言语义检索的轻量级利器
第一章 引言:语义表示的新时代挑战与Qwen3的破局之路 1.1 文本嵌入的核心价值与技术演进 在人工智能领域,文本嵌入技术如同连接自然语言与机器理解的“神经突触”——它将人类语言转化为计算机可计算的语义向量,支撑着搜索引擎、推荐系统、…...
详解:相对定位 绝对定位 固定定位)
css的定位(position)详解:相对定位 绝对定位 固定定位
在 CSS 中,元素的定位通过 position 属性控制,共有 5 种定位模式:static(静态定位)、relative(相对定位)、absolute(绝对定位)、fixed(固定定位)和…...

今日科技热点速览
🔥 今日科技热点速览 🎮 任天堂Switch 2 正式发售 任天堂新一代游戏主机 Switch 2 今日正式上线发售,主打更强图形性能与沉浸式体验,支持多模态交互,受到全球玩家热捧 。 🤖 人工智能持续突破 DeepSeek-R1&…...
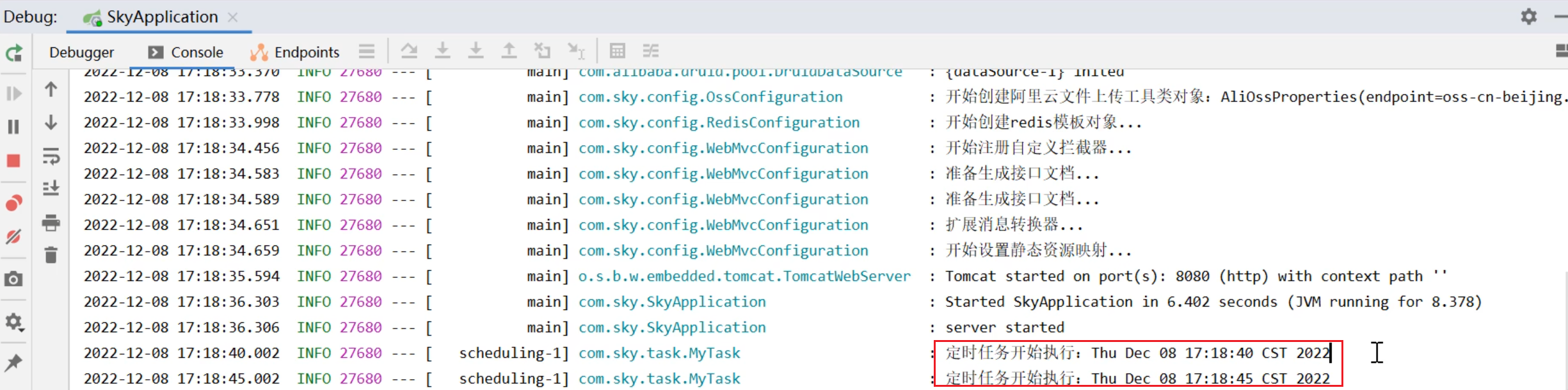
SpringTask-03.入门案例
一.入门案例 启动类: package com.sky;import lombok.extern.slf4j.Slf4j; import org.springframework.boot.SpringApplication; import org.springframework.boot.autoconfigure.SpringBootApplication; import org.springframework.cache.annotation.EnableCach…...

智能分布式爬虫的数据处理流水线优化:基于深度强化学习的数据质量控制
在数字化浪潮席卷全球的今天,数据已成为企业和研究机构的核心资产。智能分布式爬虫作为高效的数据采集工具,在大规模数据获取中发挥着关键作用。然而,传统的数据处理流水线在面对复杂多变的网络环境和海量异构数据时,常出现数据质…...
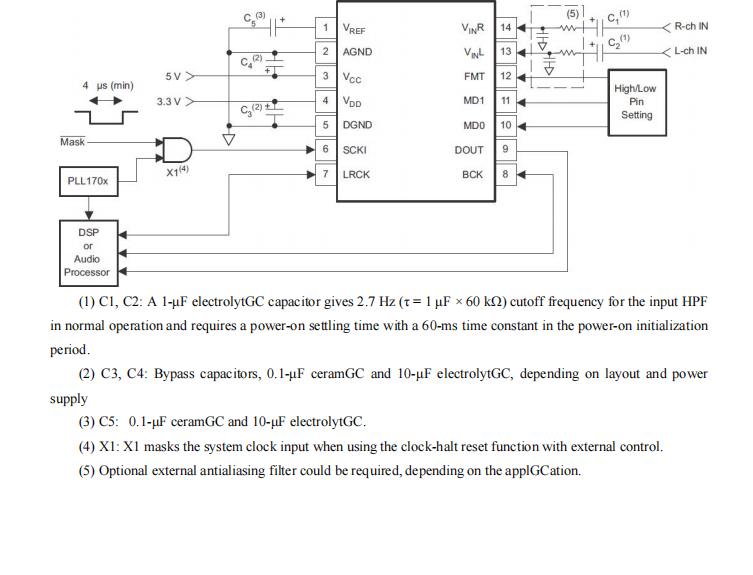
GC1808高性能24位立体声音频ADC芯片解析
1. 芯片概述 GC1808是一款24位立体声音频模数转换器(ADC),支持8kHz~96kHz采样率,集成Δ-Σ调制器、数字抗混叠滤波器和高通滤波器,适用于高保真音频采集场景。 2. 核心特性 高精度:24位分辨率,…...

【Java学习笔记】BigInteger 和 BigDecimal 类
BigInteger 和 BigDecimal 类 二者共有的常见方法 方法功能add加subtract减multiply乘divide除 注意点:传参类型必须是类对象 一、BigInteger 1. 作用:适合保存比较大的整型数 2. 使用说明 创建BigInteger对象 传入字符串 3. 代码示例 import j…...
