不一样的SYSTEM APP(SYSTEM flag和system_prop区别)
1.问题引入
在Android开发中,
1)Framework中PackageManager扫包后,会把app归类为SYSTEM, SYSTEM_EXT, PRIVILEGED 类别.
2)同样的, SeAndroid也会把APP归类程platform_app, system_app, untrusted_app(甚至还有其他,mediaprovider,gmscore_app).
flag SYSTEM和system_app我们都称之为系统app.
但是他们不是同一个概念的"系统app".
2.PackageSettings flag SYSTEM
dumpsys package com.android.systemui为例, 输出如下:
Packages:Package [com.android.systemui] (d6f33bf):appId=10187sharedUser=SharedUserSetting{4058ad4 android.uid.systemui/10187}pkg=Package{aa0e47d com.android.systemui}codePath=/system_ext/priv-app/SystemUIresourcePath=/system_ext/priv-app/SystemUIlegacyNativeLibraryDir=/system_ext/priv-app/SystemUI/libextractNativeLibs=trueprimaryCpuAbi=arm64-v8asecondaryCpuAbi=nullcpuAbiOverride=nullversionCode=1410014 minSdk=33 targetSdk=34minExtensionVersions=[]versionName=14.00.14usesNonSdkApi=falsesplits=[base]apkSigningVersion=3flags=[ SYSTEM HAS_CODE PERSISTENT ]privateFlags=[ PRIVATE_FLAG_ACTIVITIES_RESIZE_MODE_RESIZEABLE_VIA_SDK_VERSION ALLOW_AUDIO_PLAYBACK_CAPTURE DEFAULT_TO_DEVICE_PROTECTED_STORAGE DIRECT_BOOT_AWARE PARTIALLY_DIRECT_BOOT_AWARE PRIVILEGED SYSTEM_EXT PRIVATE_FLAG_ALLOW_NATIVE_HEAP_POINTER_TAGGING ]forceQueryable=false
根据输出可以看到两个重要的flag,分别为flags和privateFlags.其中flags其中标签为SYSTEM和PERSISTENT, 而privateFlags其中两个输出为PRIVILEGED/SYSTEM_EXT.
对应的输出代码如下:
@NeverCompile // Avoid size overhead of debugging code.void dumpPackageLPr(PrintWriter pw, String prefix, String checkinTag,ArraySet<String> permissionNames, PackageSetting ps,LegacyPermissionState permissionsState, SimpleDateFormat sdf, Date date,List<UserInfo> users, boolean dumpAll, boolean dumpAllComponents) {AndroidPackage pkg = ps.getPkg();// 省略好多if (pkg != null) {pw.print(prefix); pw.print(" versionName="); pw.println(pkg.getVersionName());pw.print(prefix); pw.print(" usesNonSdkApi="); pw.println(pkg.isUsesNonSdkApi());pw.print(prefix); pw.print(" splits="); dumpSplitNames(pw, pkg); pw.println();final int apkSigningVersion = pkg.getSigningDetails().getSignatureSchemeVersion();pw.print(prefix); pw.print(" apkSigningVersion="); pw.println(apkSigningVersion);pw.print(prefix); pw.print(" flags=");printFlags(pw, PackageInfoUtils.appInfoFlags(pkg, ps), FLAG_DUMP_SPEC); pw.println();int privateFlags = PackageInfoUtils.appInfoPrivateFlags(pkg, ps);if (privateFlags != 0) {pw.print(prefix); pw.print(" privateFlags="); printFlags(pw,privateFlags, PRIVATE_FLAG_DUMP_SPEC); pw.println();}if (pkg.hasPreserveLegacyExternalStorage()) {pw.print(prefix); pw.print(" hasPreserveLegacyExternalStorage=true");pw.println();}pw.print(prefix); pw.print(" forceQueryable=");pw.print(ps.getPkg().isForceQueryable());if (ps.isForceQueryableOverride()) {pw.print(" (override=true)");}
static void printFlags(PrintWriter pw, int val, Object[] spec) {pw.print("[ ");for (int i=0; i<spec.length; i+=2) {int mask = (Integer)spec[i];if ((val & mask) != 0) {pw.print(spec[i+1]);pw.print(" ");}}pw.print("]");
}
从上可知是PackageManagerService扫包解析后缓存在PackageSettings中的相关状态值记录,用于区分各类APP.
- FLAG_DUMP_SPEC

- PRIVATE_FLAG_DUMP_SPEC

从上可知,输出来源于和这些flag与运算后转换成对应的字串输出.
再看ApplicationInfo中的定义:
[1] FLAG_SYSTEM

注意表述,只要是预装在System镜像里边的即表示该APP为SYSTEM APP.
再对照着下边几个FLAG来看,

发现如果APP预制在OEM/ VENDOR/PRODUCT/SYSTEM_EXT分区,都会分别别打上对应的PRIVATE_FLAG_DUMP_SPEC标签.
以我自用的Android14真机举例:
/product/app/Ether

/product/priv-app/OppoGallery2

/system_ext/app/OTA/OTA.apk

/vendor/overlay/WifiResTarget_mainline.apk

/data/app/OppoCompass2

从以上可知,在product/system_ext/system/vendor/oem分区的都带FLAG_SYSTEM. 而可卸载的/data分区的不带(即便是OPPO预装的).
oem的例子:
/oem/priv-app/SearchSelector

因此需要注意ApplicationInfo中的注释,一个是is installed in the device’s system image, 一个是is pre-installed on the xxx partition of the system image.
因此, 暂且可以简单理解为非data分区的都可以是SYSTEM app.
如果是自安装APP(安装在/data分区), 即使是平台签名,也不是FLAG_SYSTEM.

3.seAndroid system_app
Android 默认是回来其enforcing模式的. 规则中会把各类app分门别类,从而达到其对各分区资源的操作访问做权限管理.
http://aospxref.com/android-13.0.0_r3/xref/system/sepolicy/private/mac_permissions.xml
<?xml version="1.0" encoding="utf-8"?>
<policy><!--* A signature is a hex encoded X.509 certificate or a tag defined inkeys.conf and is required for each signer tag. The signature caneither appear as a set of attached cert child tags or as an attribute.* A signer tag must contain a seinfo tag XOR multiple package stanzas.* Each signer/package tag is allowed to contain one seinfo tag. This tagrepresents additional info that each app can use in setting a SELinux securitycontext on the eventual process as well as the apps data directory.* seinfo assignments are made according to the following rules:- Stanzas with package name refinements will be checked first.- Stanzas w/o package name refinements will be checked second.- The "default" seinfo label is automatically applied.* valid stanzas can take one of the following forms:// single cert protecting seinfo<signer signature="@PLATFORM" ><seinfo value="platform" /></signer>// multiple certs protecting seinfo (all contained certs must match)<signer><cert signature="@PLATFORM1"/><cert signature="@PLATFORM2"/><seinfo value="platform" /></signer>// single cert protecting explicitly named app<signer signature="@PLATFORM" ><package name="com.android.foo"><seinfo value="bar" /></package></signer>// multiple certs protecting explicitly named app (all certs must match)<signer><cert signature="@PLATFORM1"/><cert signature="@PLATFORM2"/><package name="com.android.foo"><seinfo value="bar" /></package></signer>
--><!-- Platform dev key in AOSP --><signer signature="@PLATFORM" ><seinfo value="platform" /></signer><!-- Sdk Sandbox key --><signer signature="@SDK_SANDBOX" ><seinfo value="sdk_sandbox" /></signer><!-- Bluetooth key in AOSP --><signer signature="@BLUETOOTH" ><seinfo value="bluetooth" /></signer><!-- Media key in AOSP --><signer signature="@MEDIA" ><seinfo value="media" /></signer><signer signature="@NETWORK_STACK" ><seinfo value="network_stack" /></signer>
</policy>
以上定义了signer和seinfo之间的对应关系.
http://aospxref.com/android-13.0.0_r3/xref/system/sepolicy/private/seapp_contexts
关键部分:
user=_app seinfo=platform name=com.android.traceur domain=traceur_app type=app_data_file levelFrom=all
user=system seinfo=platform domain=system_app type=system_app_data_file
user=_app seinfo=platform domain=platform_app type=app_data_file levelFrom=user
user=_app isPrivApp=true domain=priv_app type=privapp_data_file levelFrom=user
user=_app isPrivApp=true name=com.google.android.providers.media.module domain=mediaprovider_app type=privapp_data_file levelFrom=all
全部内容如下:
# The entries in this file define how security contexts for apps are determined.
# Each entry lists input selectors, used to match the app, and outputs which are
# used to determine the security contexts for matching apps.
#
# Input selectors:
# isSystemServer (boolean)
# isEphemeralApp (boolean)
# user (string)
# seinfo (string)
# name (string)
# isPrivApp (boolean)
# minTargetSdkVersion (unsigned integer)
# fromRunAs (boolean)
#
# All specified input selectors in an entry must match (i.e. logical AND).
# An unspecified string or boolean selector with no default will match any
# value.
# A user, or name string selector that ends in * will perform a prefix
# match.
# String matching is case-insensitive.
# See external/selinux/libselinux/src/android/android_platform.c,
# seapp_context_lookup().
#
# isSystemServer=true only matches the system server.
# An unspecified isSystemServer defaults to false.
# isEphemeralApp=true will match apps marked by PackageManager as Ephemeral
# user=_app will match any regular app process.
# user=_isolated will match any isolated service process.
# user=_sdksandbox will match sdk sandbox process for an app.
# Other values of user are matched against the name associated with the process
# UID.
# seinfo= matches aginst the seinfo tag for the app, determined from
# mac_permissions.xml files.
# The ':' character is reserved and may not be used in seinfo.
# name= matches against the package name of the app.
# isPrivApp=true will only match for applications preinstalled in
# /system/priv-app.
# minTargetSdkVersion will match applications with a targetSdkVersion
# greater than or equal to the specified value. If unspecified,
# it has a default value of 0.
# fromRunAs=true means the process being labeled is started by run-as. Default
# is false.
#
# Precedence: entries are compared using the following rules, in the order shown
# (see external/selinux/libselinux/src/android/android_platform.c,
# seapp_context_cmp()).
# (1) isSystemServer=true before isSystemServer=false.
# (2) Specified isEphemeralApp= before unspecified isEphemeralApp=
# boolean.
# (3) Specified user= string before unspecified user= string;
# more specific user= string before less specific user= string.
# (4) Specified seinfo= string before unspecified seinfo= string.
# (5) Specified name= string before unspecified name= string;
# more specific name= string before less specific name= string.
# (6) Specified isPrivApp= before unspecified isPrivApp= boolean.
# (7) Higher value of minTargetSdkVersion= before lower value of
# minTargetSdkVersion= integer. Note that minTargetSdkVersion=
# defaults to 0 if unspecified.
# (8) fromRunAs=true before fromRunAs=false.
# (A fixed selector is more specific than a prefix, i.e. ending in *, and a
# longer prefix is more specific than a shorter prefix.)
# Apps are checked against entries in precedence order until the first match,
# regardless of their order in this file.
#
# Duplicate entries, i.e. with identical input selectors, are not allowed.
#
# Outputs:
# domain (string)
# type (string)
# levelFrom (string; one of none, all, app, or user)
# level (string)
#
# domain= determines the label to be used for the app process; entries
# without domain= are ignored for this purpose.
# type= specifies the label to be used for the app data directory; entries
# without type= are ignored for this purpose. The label specified must
# have the app_data_file_type attribute.
# levelFrom and level are used to determine the level (sensitivity + categories)
# for MLS/MCS.
# levelFrom=none omits the level.
# levelFrom=app determines the level from the process UID.
# levelFrom=user determines the level from the user ID.
# levelFrom=all determines the level from both UID and user ID.
#
# levelFrom=user is only supported for _app or _isolated UIDs.
# levelFrom=app or levelFrom=all is only supported for _app UIDs.
# level may be used to specify a fixed level for any UID.
#
# For backwards compatibility levelFromUid=true is equivalent to levelFrom=app
# and levelFromUid=false is equivalent to levelFrom=none.
#
#
# Neverallow Assertions
# Additional compile time assertion checks for the rules in this file can be
# added as well. The assertion
# rules are lines beginning with the keyword neverallow. Full support for PCRE
# regular expressions exists on all input and output selectors. Neverallow
# rules are never output to the built seapp_contexts file. Like all keywords,
# neverallows are case-insensitive. A neverallow is asserted when all key value
# inputs are matched on a key value rule line.
## only the system server can be assigned the system_server domains
neverallow isSystemServer=false domain=system_server
neverallow isSystemServer=false domain=system_server_startup
neverallow isSystemServer="" domain=system_server
neverallow isSystemServer="" domain=system_server_startup# system domains should never be assigned outside of system uid
neverallow user=((?!system).)* domain=system_app
neverallow user=((?!system).)* type=system_app_data_file# any non priv-app with a non-known uid with a specified name should have a specified
# seinfo
neverallow user=_app isPrivApp=false name=.* seinfo=""
neverallow user=_app isPrivApp=false name=.* seinfo=default# neverallow shared relro to any other domain
# and neverallow any other uid into shared_relro
neverallow user=shared_relro domain=((?!shared_relro).)*
neverallow user=((?!shared_relro).)* domain=shared_relro# neverallow non-isolated uids into isolated_app domain
# and vice versa
neverallow user=_isolated domain=((?!isolated_app).)*
neverallow user=((?!_isolated).)* domain=isolated_app# uid shell should always be in shell domain, however non-shell
# uid's can be in shell domain
neverallow user=shell domain=((?!shell).)*# only the package named com.android.shell can run in the shell domain
neverallow domain=shell name=((?!com\.android\.shell).)*
neverallow user=shell name=((?!com\.android\.shell).)*# Ephemeral Apps must run in the ephemeral_app domain
neverallow isEphemeralApp=true domain=((?!ephemeral_app).)*isSystemServer=true domain=system_server_startup# sdksandbox must run in the sdksandbox domain
neverallow name=com.android.sdksandbox domain=((?!sdk_sandbox).)*user=_app seinfo=platform name=com.android.traceur domain=traceur_app type=app_data_file levelFrom=all
user=_app isPrivApp=true name=com.android.remoteprovisioner domain=remote_prov_app type=app_data_file levelFrom=all
user=system seinfo=platform domain=system_app type=system_app_data_file
user=bluetooth seinfo=bluetooth domain=bluetooth type=bluetooth_data_file
user=network_stack seinfo=network_stack domain=network_stack type=radio_data_file
user=nfc seinfo=platform domain=nfc type=nfc_data_file
user=secure_element seinfo=platform domain=secure_element levelFrom=all
user=radio seinfo=platform domain=radio type=radio_data_file
user=shared_relro domain=shared_relro levelFrom=all
user=shell seinfo=platform domain=shell name=com.android.shell type=shell_data_file
user=webview_zygote seinfo=webview_zygote domain=webview_zygote
user=_isolated domain=isolated_app levelFrom=user
user=_sdksandbox domain=sdk_sandbox type=sdk_sandbox_data_file levelFrom=all
user=_app seinfo=app_zygote domain=app_zygote levelFrom=user
user=_app seinfo=media domain=mediaprovider type=app_data_file levelFrom=user
user=_app seinfo=platform domain=platform_app type=app_data_file levelFrom=user
user=_app isEphemeralApp=true domain=ephemeral_app type=app_data_file levelFrom=all
user=_app isPrivApp=true domain=priv_app type=privapp_data_file levelFrom=user
user=_app isPrivApp=true name=com.google.android.permissioncontroller domain=permissioncontroller_app type=privapp_data_file levelFrom=all
user=_app seinfo=media isPrivApp=true name=com.android.providers.media.module domain=mediaprovider_app type=privapp_data_file levelFrom=all
user=_app isPrivApp=true name=com.google.android.providers.media.module domain=mediaprovider_app type=privapp_data_file levelFrom=all
user=_app seinfo=platform isPrivApp=true name=com.android.permissioncontroller domain=permissioncontroller_app type=privapp_data_file levelFrom=all
user=_app isPrivApp=true name=com.android.vzwomatrigger domain=vzwomatrigger_app type=privapp_data_file levelFrom=all
user=_app isPrivApp=true name=com.google.android.gms domain=gmscore_app type=privapp_data_file levelFrom=user
user=_app isPrivApp=true name=com.google.android.gms.* domain=gmscore_app type=privapp_data_file levelFrom=user
user=_app isPrivApp=true name=com.google.android.gms:* domain=gmscore_app type=privapp_data_file levelFrom=user
user=_app isPrivApp=true name=com.google.android.gsf domain=gmscore_app type=privapp_data_file levelFrom=user
user=_app minTargetSdkVersion=32 domain=untrusted_app type=app_data_file levelFrom=all
user=_app minTargetSdkVersion=30 domain=untrusted_app_30 type=app_data_file levelFrom=all
user=_app minTargetSdkVersion=29 domain=untrusted_app_29 type=app_data_file levelFrom=all
user=_app minTargetSdkVersion=28 domain=untrusted_app_27 type=app_data_file levelFrom=all
user=_app minTargetSdkVersion=26 domain=untrusted_app_27 type=app_data_file levelFrom=user
user=_app domain=untrusted_app_25 type=app_data_file levelFrom=user
user=_app minTargetSdkVersion=28 fromRunAs=true domain=runas_app levelFrom=all
user=_app fromRunAs=true domain=runas_app levelFrom=user从以上定义可知,当签名是platform, 且user是system时,默认匹配到的就是system_app;同样可以在指定包名的情况下为特定APP指定特殊的domain.
例如:com.android.traceur,对应的domain已经是:traceur_app.
[小结]
1.platform签名 + system user 才是system_app;
2.platform签名 + 非system user ,是platform_app;
3.自己安装的三方APP是untrusted_app.
注意这里的system user是指示UID 1000, 如果是个APP, 那么他的AndroidManifest.xml必须声明android:sharedUserId=“android.uid.system”.
注意文件seapp_contexts中对user的定义说明.
user=_app will match any regular app process.
user=_isolated will match any isolated service process.
user=_sdksandbox will match sdk sandbox process for an app.
Other values of user are matched against the name associated with the process UID.
4.结论
- framework中的system app, 指的是预装在system image里边的APP.
- seAndroid中的system_app,是指拥有平台签名且user为system的APP.
参考资料
SEAndroid安全机制框架分析
<android Selinux 之 platform_app,system_app,priv_app,untrusted_app>
相关文章:

不一样的SYSTEM APP(SYSTEM flag和system_prop区别)
1.问题引入 在Android开发中, 1)Framework中PackageManager扫包后,会把app归类为SYSTEM, SYSTEM_EXT, PRIVILEGED 类别. 2)同样的, SeAndroid也会把APP归类程platform_app, system_app, untrusted_app(甚至还有其他,mediaprovider,gmscore_app). flag SYSTEM和system_app我们…...
C++ 和 JAVA 位运算符
C 和 JAVA 位运算符...

项目进度和成本管理
1.如何正确标识出软件项目活动? 正确标识软件项目活动是项目管理中的一个重要步骤,它有助于确保项目的顺利进行和成功完成。以下是一些标识软件项目活动的步骤和建议: 项目范围定义:首先明确项目的目标和范围,这将帮助…...

Dorkish:一款针对OSINT和网络侦查任务的Chrome扩展
关于Dorkish Dorkish是一款功能强大的Chrome扩展工具,该工具可以为广大研究人员在执行OSINT和网络侦查任务期间提供强大帮助。 一般来说,广大研究人员在执行网络侦查或进行OSINT信息收集任务过程中,通常会使用到Google Dorking和Shodan&…...

树莓派4B_OpenCv学习笔记10:调整视频帧大小
今日继续学习树莓派4B 4G:(Raspberry Pi,简称RPi或RasPi) 本人所用树莓派4B 装载的系统与版本如下: 版本可用命令 (lsb_release -a) 查询: Opencv 版本是4.5.1: 今日学习一下如何降低视频帧像素 文章提供测试代码讲解…...
:数据过滤)
MySQL 保姆级教程(五):数据过滤
第 7 章 数据过滤 7.1 组合 WHERE 子句 MySQL 允许给出多个 WHERE 子句,这些子句可用用两种方式使用:AND 或 OR 操作符 7.1.1 AND 操作符 输入: SELECT server_cost.cost_name,server_cost.cost_value,server_cost.default_value FROM server_cost W…...

《全职猎人》
《全职猎人》 [1-2]是日本漫画家富坚义博的作品。 1999年版改编电视动画由日本动画公司负责动画制作,于1999年10月16日-2001年3月30日在富士电视台播出,该动画的故事至贪婪之岛篇章结束,全92话。 该作在富坚义博老师天马行空的想…...

Linux各目录的作用
Linux各目录的作用 目录作用~登录用户对应的目录.当前工作目录$PATH环境变量/根目录/boot启动Linux使用的文件,例如Linux内核,包括连接文件和镜像文件,(删了就启动不了了)/bin(/usr/bin,/usr/local/bin)Binary&#x…...

Windows Docker Desktop 安装 postgres
Docker Desktop安装 postgres 12.6 数据库 step docker pull postgres:12.6提前创建F:/D-dockerData/postgres-12.6/data 文件夹用于bind mountdocker run docker run --name postgres-12.6 \-e POSTGRES_PASSWORD123456 \-p 5432:5432 \-v F:/D-dockerData/postgres-12.6/d…...

C# OpenCvSharp Mat操作-创建Mat-构造函数
🌟 Mat类:图像与多维矩阵的魔法 ✨ Mat类是OpenCvSharp中用于表示图像和多维矩阵的核心类。它提供了多种构造函数来创建和初始化矩阵对象。下面我们逐一解释这些构造函数,并通过示例来说明它们的用法。📸 🚀 默认构造函数 Mat() 创建一个空的Mat对象。 Mat mat = …...
【制作100个unity游戏之29】使用unity复刻经典游戏《愤怒的小鸟》(完结,附带项目源码)
最终效果 文章目录 最终效果前言素材下载简单搭建环境控制小鸟生成弹簧 限制小鸟的控制范围弹簧线的显示隐藏飞行新增木头木头销毁不同血量的木头状态配置更多物品爆炸效果创建敌人的小猪创建多个小鸟循环游戏结束相机跟随加分特效不同定义技能的鸟加速鸟回旋鸟爆炸鸟效果 轨迹…...

稀疏矩阵是什么 如何求
稀疏矩阵是一种特殊类型的矩阵,其中大多数元素都是零。由于稀疏矩阵中非零元素的数量远少于零元素,因此可以使用特定的数据结构和算法来高效地存储和处理它们,从而节省存储空间和计算时间。 RowPtr 数组中的每个元素表示对应行的第一个非零元…...
 -- SOCKET : Unix domain)
57.Linux/Unix 系统编程手册(下) -- SOCKET : Unix domain
https://blog.51cto.com/u_15567199/5204540 【linux网络编程】容错处理文件 wrap.h、wrap.c_wx623c6c9. // 容错处理 wrap.h #ifndef _WRAP_H_ #define _WRAP_H_#include <stdio.h> #include <stdlib.h> #include <unistd.h> #include <error.h> #i…...
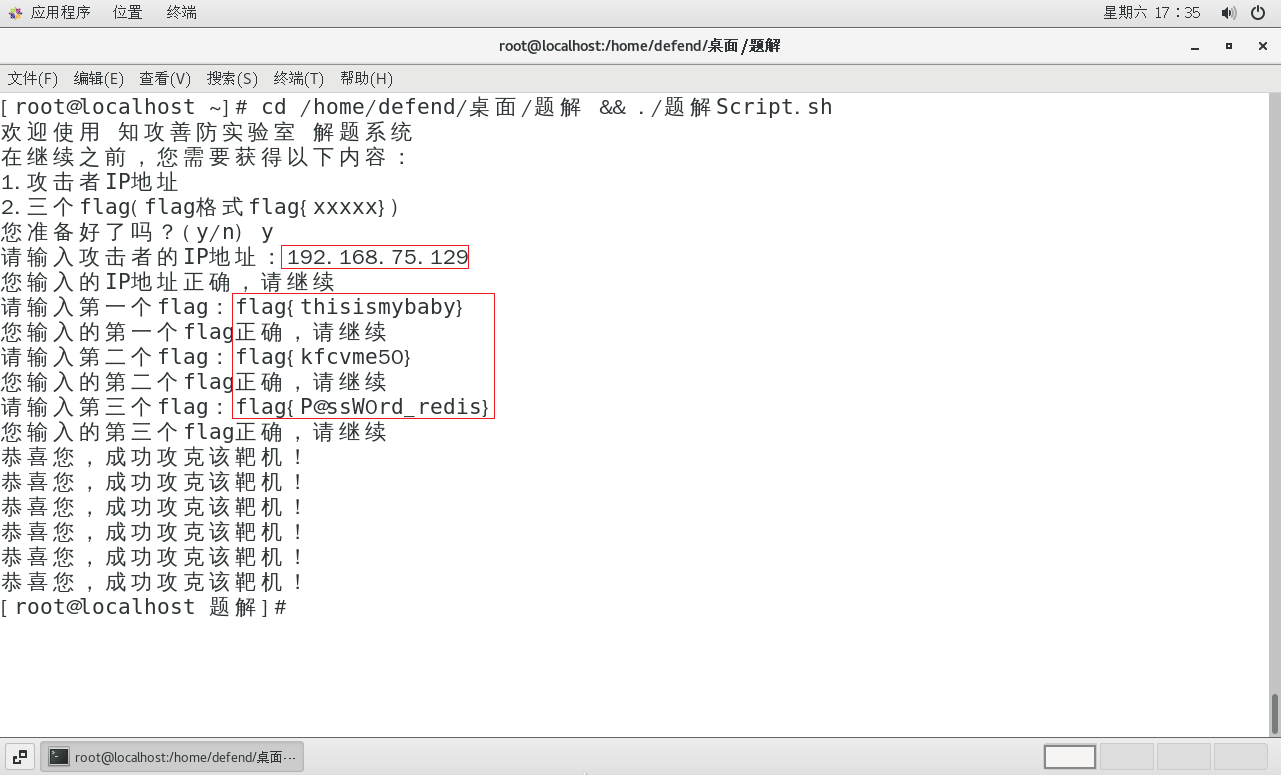
Hvv--知攻善防应急响应靶机--Linux1
HW–应急响应靶机–Linux1 所有靶机均来自 知攻善防实验室 靶机整理: 夸克网盘:https://pan.quark.cn/s/4b6dffd0c51a#/list/share百度云盘:https://pan.baidu.com/s/1NnrS5asrS1Pw6LUbexewuA?pwdtxmy 官方WP:https://mp.weixin.…...

Solus Linux: 有自己的软件包管理器
Solus Linux 是一个独立的 Linux 发行版,它以简单易用和现代化的用户体验而著称。Solus Linux 使用的包管理器是 eopkg,它具有以下优势和特点: 用户友好的界面:eopkg 提供了一个简洁直观的命令行界面,使得用户可以轻松…...

Java GUI编程
引言 图形用户界面(GUI)编程是使应用程序与用户进行交互的重要部分。Java提供了多种用于GUI开发的工具和库,最常用的是Swing和AWT。本文将详细介绍Java GUI编程的基础知识,包括Swing和AWT框架、事件处理以及高级GUI组件的使用&…...
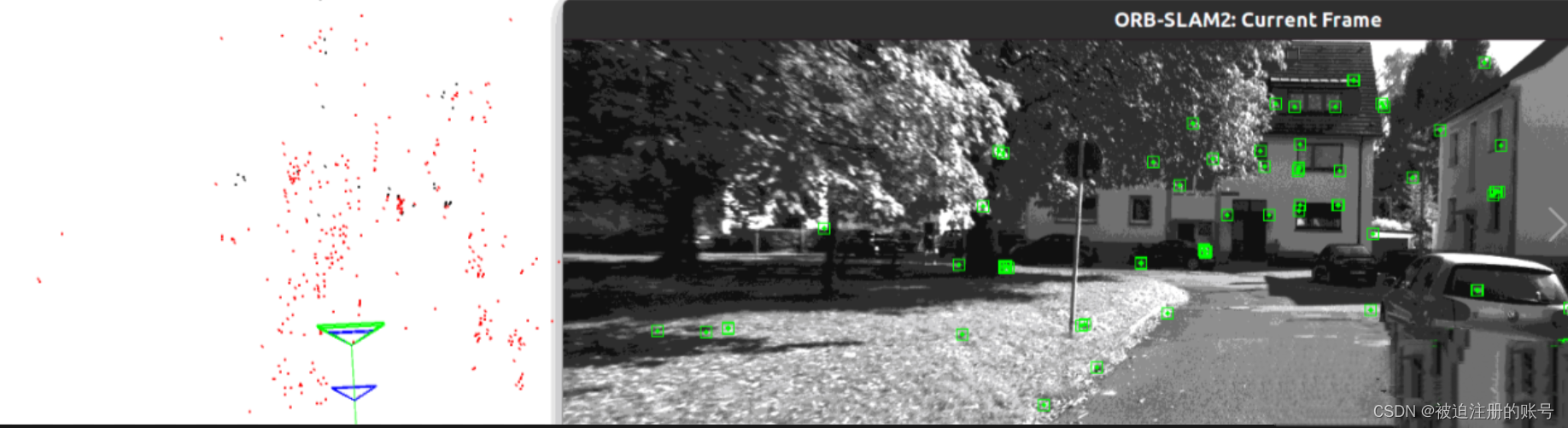
ROS机器人小车建模仿真与SLAM
文章目录 一、URDF二、创建小车模型1.创建功能包2.导入依赖3.创建urdf,launch文件:4.可视化 三、添加雷达1.xacro文件2.集成和修改launch3.添加摄像头和雷达 三.GAZEBO仿真四、orbslam2kitti1.下载2.安装编译ORB_SLAM23.运行Kitee数据集 一、URDF URDFÿ…...
Windows10安装Docker Desktop(实操步骤版)
1,下载Docker Desktop 官网下载地址: https://desktop.docker.com/win/stable/amd64/Docker%20Desktop%20Installer.exe 国内镜像下载地址(本人下载这个): https://smartidedl.blob.core.chinacloudapi.cn/docker/2…...
)
Leetcode 45. 跳跃游戏 II(DP 双指针)
Leetcode 45. 跳跃游戏 II 动态规划 使用dp [ ] 记录每个位置可达的最小步数,每到达一个点时,更新该点所能跳跃区间内的所有点的dp值 时间复杂度较高 class Solution {public int jump(int[] nums) {int n nums.length;int dp[] new int [n];int N …...
(实时更新))
Codeforces Round 952 (Div. 4)(实时更新)
A - Creating Words 题意:略 代码: #include<bits/stdc.h> #define ios ios::sync_with_stdio(0),cin.tie(0),cout.tie(0)//不能使用scanf了 #define int long long #define loop(n) for(int i0;i<n;i) #define rloop(n) for(int in-1;i>…...

AI-调查研究-01-正念冥想有用吗?对健康的影响及科学指南
点一下关注吧!!!非常感谢!!持续更新!!! 🚀 AI篇持续更新中!(长期更新) 目前2025年06月05日更新到: AI炼丹日志-28 - Aud…...
css实现圆环展示百分比,根据值动态展示所占比例
代码如下 <view class""><view class"circle-chart"><view v-if"!!num" class"pie-item" :style"{background: conic-gradient(var(--one-color) 0%,#E9E6F1 ${num}%),}"></view><view v-else …...
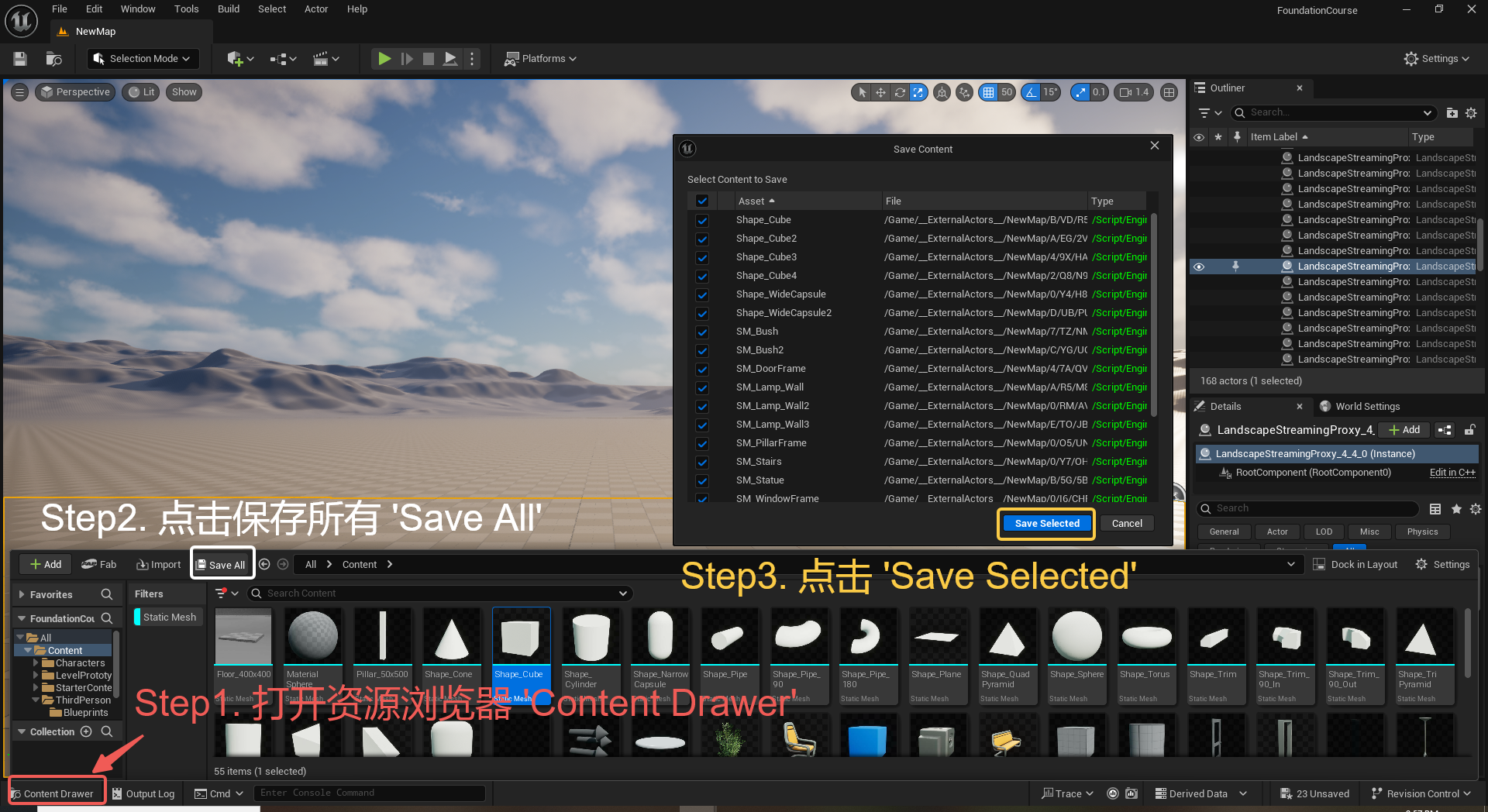
UE5 学习系列(三)创建和移动物体
这篇博客是该系列的第三篇,是在之前两篇博客的基础上展开,主要介绍如何在操作界面中创建和拖动物体,这篇博客跟随的视频链接如下: B 站视频:s03-创建和移动物体 如果你不打算开之前的博客并且对UE5 比较熟的话按照以…...

Objective-C常用命名规范总结
【OC】常用命名规范总结 文章目录 【OC】常用命名规范总结1.类名(Class Name)2.协议名(Protocol Name)3.方法名(Method Name)4.属性名(Property Name)5.局部变量/实例变量(Local / Instance Variables&…...

python如何将word的doc另存为docx
将 DOCX 文件另存为 DOCX 格式(Python 实现) 在 Python 中,你可以使用 python-docx 库来操作 Word 文档。不过需要注意的是,.doc 是旧的 Word 格式,而 .docx 是新的基于 XML 的格式。python-docx 只能处理 .docx 格式…...
【配置 YOLOX 用于按目录分类的图片数据集】
现在的图标点选越来越多,如何一步解决,采用 YOLOX 目标检测模式则可以轻松解决 要在 YOLOX 中使用按目录分类的图片数据集(每个目录代表一个类别,目录下是该类别的所有图片),你需要进行以下配置步骤&#x…...
c#开发AI模型对话
AI模型 前面已经介绍了一般AI模型本地部署,直接调用现成的模型数据。这里主要讲述讲接口集成到我们自己的程序中使用方式。 微软提供了ML.NET来开发和使用AI模型,但是目前国内可能使用不多,至少实践例子很少看见。开发训练模型就不介绍了&am…...
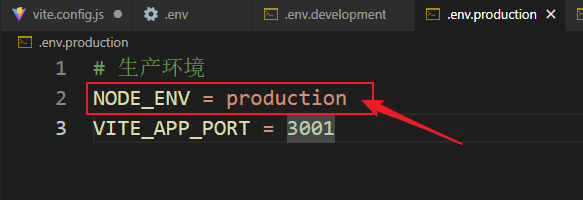
vue3+vite项目中使用.env文件环境变量方法
vue3vite项目中使用.env文件环境变量方法 .env文件作用命名规则常用的配置项示例使用方法注意事项在vite.config.js文件中读取环境变量方法 .env文件作用 .env 文件用于定义环境变量,这些变量可以在项目中通过 import.meta.env 进行访问。Vite 会自动加载这些环境变…...
的原因分类及对应排查方案)
JVM暂停(Stop-The-World,STW)的原因分类及对应排查方案
JVM暂停(Stop-The-World,STW)的完整原因分类及对应排查方案,结合JVM运行机制和常见故障场景整理而成: 一、GC相关暂停 1. 安全点(Safepoint)阻塞 现象:JVM暂停但无GC日志,日志显示No GCs detected。原因:JVM等待所有线程进入安全点(如…...

Java 二维码
Java 二维码 **技术:**谷歌 ZXing 实现 首先添加依赖 <!-- 二维码依赖 --><dependency><groupId>com.google.zxing</groupId><artifactId>core</artifactId><version>3.5.1</version></dependency><de…...
