北邮《计算机网络》英文选择题课堂小测
课堂小测验及答疑汇总
2020年 5 月 12 日
Q1. Which is the network address after aggregation of following 3 networks: 200.2.50.0/23,
200.2.52.0/22 and 200.2.56.0/22?
A. 200.2.48.0/20
B. 200.2.50.0/20
C. 200.2.48.0/21
D. 200.2.50.0/21
Answer: A
Q2 An IP Datagram with a 20-byte header and total length of 1500 bytes is to be forwarded
into a network with a MTU of 800 bytes, thus fragmentation is necessary. What is the
offset value in the 2nd fragment?
A. 800
B. 780
C. 100
D. 97
Answer: D.
课堂练习
A company (with network 114.23.5.0/24) has 3 departments A, B and C, with 64,
10 and 30 hosts(routers) respectively. How to allocate addresses to them in the
order of A, B and then C? Write out the network address of each department. Is
there a more efficient way for address allocation?
2020年 5 月 7 日
Q1. Network 191.168.0.0 is divided into 8 subnets with same size,which is the correct
subnet mask of each subnet?
A. 255.255.0.0
B. 255.255.224.0
C. 255.255.240.0
D. 255.255.255.0
Answer: B
Q2. For a network with 100 hosts (including routers), which subnet mask shall be adopted as
a best choice? (按照最少够用原则)
A. /23
B. /24
C. /25
D. /26
Answer: C
2020 年 4 月 28 日
Q1. When the load in the network reaches the network capacity, the packet delay _____
and the network throughput reaches ______.
A. increases sharply; its minimum
B. increases sharply; its maximum
C. decreases sharply; its minimum
D. decreases sharply; its maximum
Answer: B
2020 年 4 月 24 日
Q1. Which statement is NOT true for Link State Routing?
A. Compared with Distance Vector Routing, bandwidth consumed is more
due to flooding.
B. It is based on local knowledge since routers only know part of network topology.
C. It makes use of Dijkstra algorithm to build routing table.
D. Compared with Distance Vector Routing, it converges faster and does not
have the problem of count-to-infinity.
Answer: B
Q2. Which congestion control method is reactive and adopts explicit congestion signaling
with the help of destination host?
A. Choke packet
B. Back pressure
C. Traffic aware routing
D. ECN
Answer: D
2020 年 4 月 21 日
Q1. About virtual circuit and datagram, which statement is NOT true?
A. Both use packet switching technology
B. Virtual circuit networks provide connection-oriented service, while datagram
networks provide connectionless service.
C. In datagram networks, packets from same source to same destination may
traverse over different paths, while in virtual circuit networks, belonging to
same VC, they will flow over the same path.
D. Datagram routers always use full address, while virtual circuit routers only deal
with VCI.
Answer: D
2020 年 4 月 17 日
Q1. About VLAN, which statement is NOT TRUE?
A. VLAN decouples the logical topology from the physical topology.
B. For computers connected to a HUB,some can be VLAN-aware while others
are not VLAN-aware.
C. VLAN-aware bridges can limit the scope of broadcasting frames while normal bridges cannot.
D. Legacy Ethernet frame does not support VLAN.
Answer: B
Q2. 一台有 1 个 WAN 口、4 个 LAN 口的路由器,可以连接几个网络?
A. 1
B. 2
C. 4
D. 5
Answer: B
Q3. About virtual circuit, which statement is NOT TRUE?
A. A physical connection is set up before the source sends out data packets.
B. A route from source to destination is chosen at connection setup, so all data
packets will arrive in same sequence as they are sent out.
C. Over an outgoing port of a router, 2 virtual connections cannot use the
same VCI.
D. As VCI is local-significant, it may change along the path from source to
destination.
Answer: A
2020年 4 月 14 日
Q1. In an IEEE802.11 network, at some instant, 3 stations sense the channel and find it is idle,
then multiple frames are to be transmitted, including a RTS, a re-transmitted data frame
and an ACK, which ONE will probably be sent?
A. RTS
B. re-transmitted data frame
C. ACK
D. None of them
Answer: C
Q2. In which case(s), a LAN switch will flood an incoming frame?
A. the destination address is unknown
B. the destination address is known, the outgoing port is same with incoming port
C. the destination address is known, the outgoing port is different from incoming
port
D. the destination address is 0xFF-FF-FF-FF-FF-FF
Answer: A,D
Q2. About Ethernet, consider Ture(T) or False(F) for the statements below:
- In Gigabit Ethernet, if computers connect to a Hub, they work in half-duplex,
which means that data could be transmitted in only one direction at a time,
either from computer to hub, or from hub to computer. - CSMA/CD can be used sometimes in a fully switched Ethernet.
- Manchester encoding is not used in Ethernet with data rate higher than 10Mbps.
Answer: TFT
2020 年 4 月 7 日
Q1.For a CSMA/CD network with bus topology, assume the frame time is T0, and the
propagation delay of the cable is τ, which are the vulnerable period and
contention slot time respectively?
A. T0, 2T0
B. T0, 2τ
C. τ, 2T0
D. τ, 2τ
Answer: D
Q2. About IEEE802 Reference Model, determine True(T) or False(F) for the statements
below:
- Different LAN may have different LLC sub-layer protocols.
- Different LAN may have different MAC sub-layer protocols.
- A LAN protocol may include multiple physical layer protocols.
Answer: FTT
2020 年 4 月 3 日
Q1. What type of service is provided by Ethernet?
A. connection-oriented service
B. connectionless service
C. connectionless service with explicit ACK
D. None of the above
Answer: B
Q2. Which statement is NOT TRUE for stations using pure ALOHA?
A. A station transmits at will without coordination with other stations
B. A station can only find collision when timer expires
C. After timer expires, the station retransmits the frame at once.
D. The vulnerable period is twice the frame time, i.e. 2T0
Answer: C
2020 年 3 月 31 日
Q1. (多选)For protocol 6, in which cases NAK will be sent while frame-expected=6 and no_nak is true?
A. received a damaged frame with seq=6
B. received a frame with seq=4
C. received a duplicated ACK
D. received a frame with seq=7
Answer: A、B、D
Q2. Consider a 50-kbps satellite channel with a 500-msec round-trip propagation delay, 1000-
bit frames are sent with Go-back-N ARQ and short ACK frames as acknowledgement. If
a line utilization of 50% is required, how many bits at least shall be used for sequence
number?
A. 3
B. 4
C. 5
D. 6
Answer: B
. 2020 年 3 月 27 日
Q1. For a Go-back-N ARQ with 3-bit sequence number, if the seq number in
current receiving windows is 0,while the entity receives an un-damaged frame with r.seq=1, what will the entity do for a proper operation?
(Assume the entity always has a packet to send)
A. accept the frame and send a frame with s.ack=1
B. discard the frame
C. discard the frame and send a frame with s.ack=0
D. discard the frame and send a frame with s.ack=7
Answer:D
. 2020 年 3 月 24 日
Q1. Assume 3-bit sequence number is used in Protocol 4. When a node receives a frame with r.seq=7 and r.ack=7, what will s.seq and s.ack be in the frame s it will send as a response?
A. 7 and 7
B. 7 and 0
C. 0 and 7
D. 0 and 0
Answer:C
Q2. Assume 3-bit sequence number is used in a Go-back-N protocol. Now the
sender has sent out 8 frames with sequence number 0,1,… and 7. When
timing out, the sender only received ACK1 and ACK3, how many frames will the sender retransmit?
A. 2
B. 4
C. 6
D. 8
Answer:B
2020 年 3 月 20 日
Q1. A data link layer sending entity has 3 jobs before delivering bit stream to its physical layer,
- bit stuffing
- adding header flag and trailer flag
- adding checksum bits
What is the correct sequence of the 3 jobs?
A. 123
B. 312
C. 132
D. 321
Answer:B
Q2. 计算题
若 G(x)=x5+x2+x+1,接收方收到的数据是:1001 1011 1110 0101 1000,请判断该帧是否传输出错。
Answer:传输出错。
Q3.附加作业题
The following character encoding is used in a data link protocol: A: 01000111; B: 11100011; FLAG: 01111110; ESC: 11100000
Show the bit sequence transmitted (in binary) for the four-character frame: A B ESC FLAG when each of the following framing methods are used:
(a) Character count.
(b) Flag bytes with byte stuffing.
© Starting and ending flag bytes, with bit stuffing.
(d) Calculate the efficiency (as a percentage of real data per bit sent) of your answers to (a), (b)and © .
Answer:
1)字符计数法:
00000101 01000111 11100011 11100000 01111110
增加了一个长度字节(长度值包括其本身),效率为 4/5=80%
2)字节填充法:
01111110 01000111 11100011 11100000 11100000
11100000 0111 1110 011111110
增加了首尾标志和 2 个转义字符,效率为 4/8=50%
3)比特填充法:
01111110 01000111 110100011 111000000 011111010 01111110
增加了首尾标志和 3 位填充,效率为 32/51=62.75%
2020 年 3 月 17 日
Q1. What type of service is provided to network layer by 10BaseT?
A. connectionless service
B. connectionless service with acknowledgement
C. frame-based connection-oriented service
D. byte-based connection-oriented service
Answer:A
Q2. 计算题
从信道上收到比特序列: 1101 0111 1110 0111 1110 1101 1011 1110 0010 1100 0101 1111 0101 1001 1111 1001,该比特序列中包含一个完整的帧,用十六进制写出该帧的内 容(不包含帧的首尾标志)。
Answer:D B E 5 8 B F 6
2020 年 3 月 13 日
Q1.Which is the maximum data rate over a 4-kHz channel whose signal-to-noise ratio is 30 dB, and QAM-16 modulation is used?
A. 8Kbps
B. 32Kbps
C. 40Kbps
D. 64Kbps
Answer:B
Q2. About routing (hunting for a path) in a circuit switching network, which is true?
A.There is no need for routing in circuit switching network.
B. Routing is required only at connection set up phase.
C. Routing is necessary during the whole procedure of communication.
D. Routing is necessary at circuit termination phase.
Answer:B
2020 年 3 月 10 日
Q1. Which multiplexing scheme is adopted in Internet?
A. Code Division Multiple Access
B. Frequency Division Multiplexing
C. Time Division Multiplexing
D. Wavelength Division Multiplexing
Answer:C
2020 年 3 月 6 日
Q1. Which of the following is not defined in network architecture?
A. Function of each layer
B. Protocols in each layer
C. Services provided by each layer
D. Implementation of certain service in each layer
Answer:D
Q2. Talking about bandwidith in Hz, which is true?
A. Twisted pair < Radio and TV < Coax < Fiber
B. Radio and TV < Twisted pair < Coax < Fiber
C. Radio and TV < Coax < Twisted pair < Fiber
D. Coax < Radio and TV < Twisted pair < Fiber
Answer:A
. 2020 年 3 月 3 日
Q1. For the following 2 statements, decide true or false.
- Layer N protocol must be used to implement the service provided by layer N.
- There is no need to consider the format of PDU when designing service
primitives.
A. True, True
B. True, False
C. False, True
D. False, False
Answer:A
Q2. In communications between 2 adjacent routers, which layer provides the function of data block exchange?
A. Physical layer
B. Data Link layer
C. Network layer
D. Transport layer
Answer:B
. 2020 年 2 月 28 日
Q1.(不定项) Which statement(s) is/are correct for a wifi network?
A. It is a broadcast network
B. It is a point-to-point network
C. It is an access network
D. It is an edge of 4G mobile communication network
Answer:AC
Q2. Which statement is NOT true?
A. A computer network can be organized as a set of layers.
B. A single function can be performed by the cooperation of adjacent 2 layers, thus the implementation is visible to both layers.
C. Each layer offers a certain service(s) to its upper layer.
D. The upper layer access the service provided through the interface.
Answer: B
. 2020 年 2 月 25 日
Q1. Which of the following is/are NOT a type of computer network?
A. Internet
B. a Wifi network in a Cafetiria
C. World Wide Web
D. 10 computers connecting to a router with cable
Answer:C
相关文章:

北邮《计算机网络》英文选择题课堂小测
课堂小测验及答疑汇总 2020年 5 月 12 日 Q1. Which is the network address after aggregation of following 3 networks: 200.2.50.0/23, 200.2.52.0/22 and 200.2.56.0/22? A. 200.2.48.0/20 B. 200.2.50.0/20 C. 200.2.48.0/21 D. 200.2.50.0/21 Answer: A Q…...

kafka 集群安全认证机制的设计实现
kafka 集群安全认证机制的实现 Kafka 提供了多种安全认证机制来保护数据传输的安全性,包括加密、身份认证和授权。这些机制确保 了 Kafka 集群的通信安全和数据访问控制。以下是 Kafka 安全认证机制的实现和配置指南。 1. 安全认证机制概述 Kafka 支持以下几种主要的安全机…...

pandas保存成CSV格式时数据换行:SQL的REPLACE函数过滤掉数据的回车符
在使用Pandas保存数据到CSV文件时,如果数据中包含换行符(例如\n),这可能会导致数据在CSV文件中被分割成多行,影响数据的完整性和可读性。为了解决这个问题,你可以在保存CSV之前使用Pandas的replace函数来替…...

紧贴国家大战略需求,聚焦当前行业热点-海云安D10入选第四届香蜜湖金融科技创新奖拟奖项目
近日,第四届香蜜湖金融科技创新奖终审总结会在深圳市福田区湾区国际金融科技城成功举办,活动现场,专家评审委员会最终揭晓25个拟奖项目。海云安“开发者安全助手系统”项目,实力入选第四届香蜜湖金融科技创新奖-优秀项目奖。 1、香…...

构建 Linux 内核指南
该指南列出了用于构建 Linux 内核的各种目标及其说明。 清理目标: clean - 删除大多数生成的文件,但保留配置文件和足以构建外部模块的构建支持。 mrproper - 删除所有生成的文件 配置文件 各个备份文件。 distclean - mrproper 删除编辑器备份和补丁…...
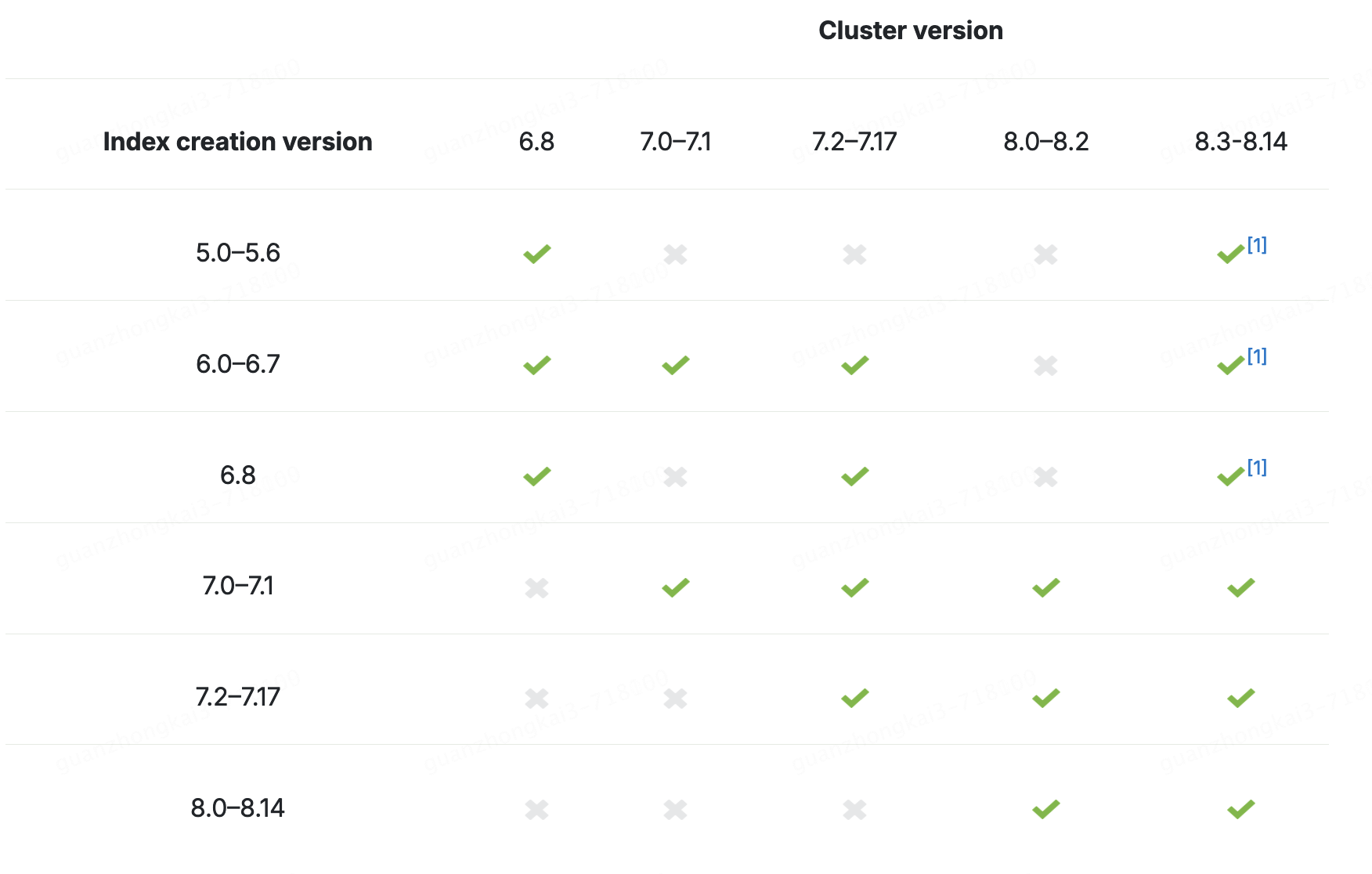
Elasticsearch的快照
ES的快照是什么? snapshot是一个ES集群或者某个指定索引的备份,快照一般用在 不停机的状态下对ES集群进行备份当硬件故障时恢复集群数据用于跨集群的数据迁移对冷数据或冻结数据做快照以降低存储成本,依赖于可搜索的快照。-收费功能 一个快…...

C/C++混合编译说明
C调用C的函数: C的头文件中声明,被C调用的函数,是以C的方式编译 C的头文件: #ifdef __cplusplus extern "C" { #endif void func_c(void); #ifdef __cplusplus } #endif C调用C的函数: C的源文件中声明ÿ…...

三种方式实现人车流统计(yolov5+opencv+deepsort+bytetrack+iou)
一、运行环境 1、项目运行环境如下 2、CPU配置 3、GPU配置 如果没有GPU yolov5目标检测时间会比较久 二、编程语言与使用库版本 项目编程语言使用c++,使用的第三方库,onnxruntime-linux-x64-1.12.1,opencv-4.6.0 opencv 官方地址Releases - OpenCV opencv github地址ht…...
Vue Router的命名路由和路由组件传参)
(四十四)Vue Router的命名路由和路由组件传参
文章目录 命名路由组件传参query参数方式参数传递参数接收 params参数方式参数传递参数接收 props配置方式布尔值形式对象模式函数模式 上一篇:(四十三)Vue Router之嵌套路由 命名路由 命名路由是为路由配置项提供一个名称,以便…...
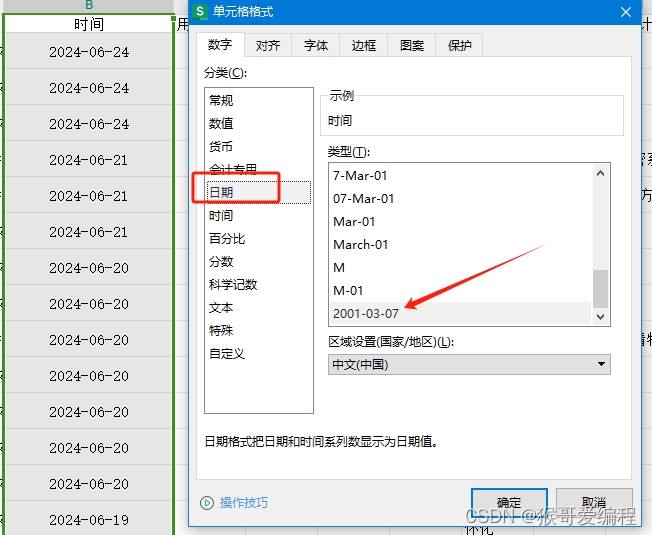
EXCEL表格怎么批量删除日期后的时间?
竞价师最近有点忙了,因为百度新出来一个“线索有效性诊断”功能 一、下载电话、表单、咨询表格 二、选中整列 三、选中ctrlf 进行替换,日期输入空格,时间输入*,替换为空即可! 四、整列单元格格式“日期”拉倒底部&…...
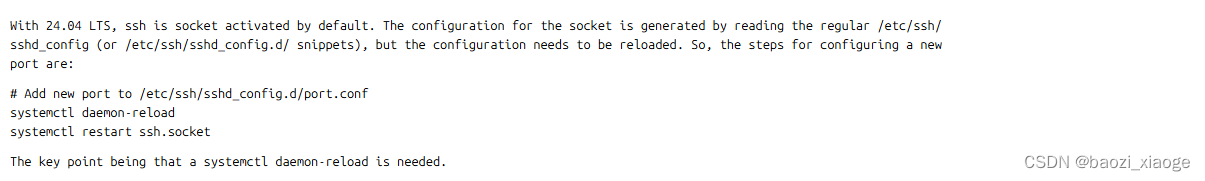
乌班图Ubuntu 24.04 SSH Server 修改默认端口重启无效
试用最新的乌班图版本,常规修改ssh端口,修改完毕后重启sshd提示没有找到service,然后尝试去掉d重启ssh后查看状态,端口仍然是默认的22,各种尝试都试了不行,重启服务器后倒是端口修改成功了,心想…...
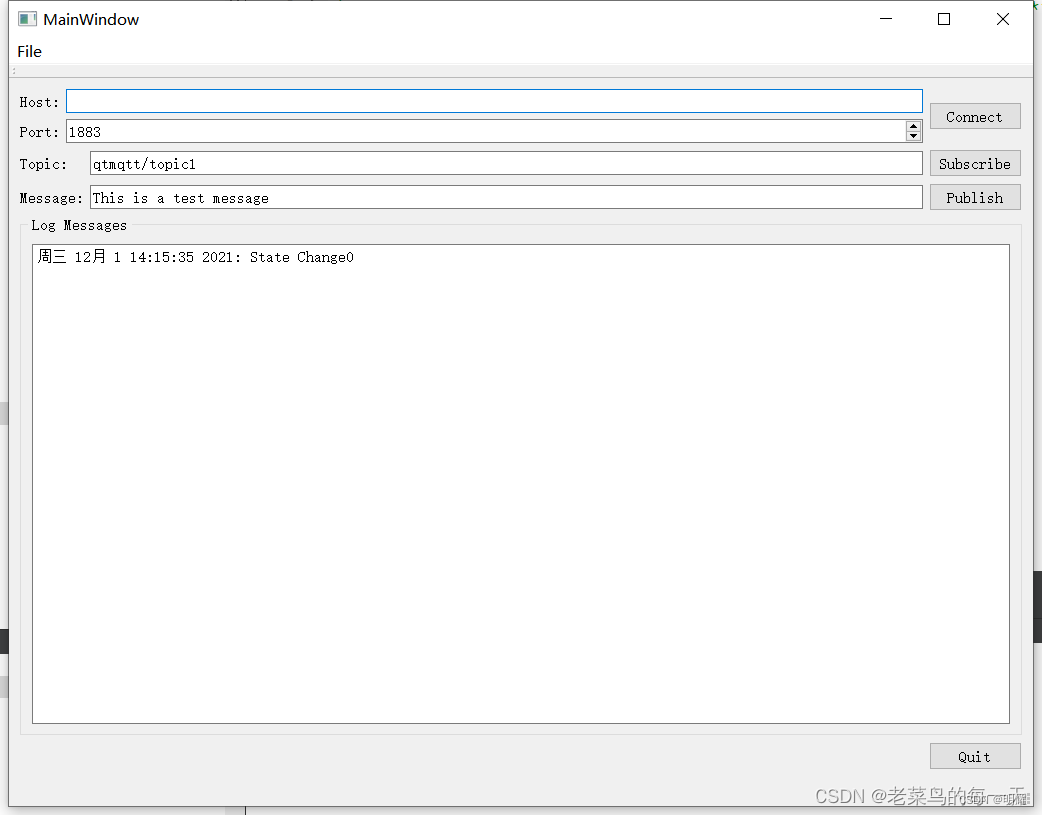
QT MQTT (二)编译与集成
一、QT MQTT 提供 MQTT 客户端服务的 Qt 专用库基于标准化发布 / 订阅协议,用于在设备和组件之间可靠地共享数据。MQTT 是为保证状态正确性、满足高安全标准和交换最小数据而设计的协议,因此被广泛应用于各种分布式系统和物联网解决方案中。 Qt开发MQT…...
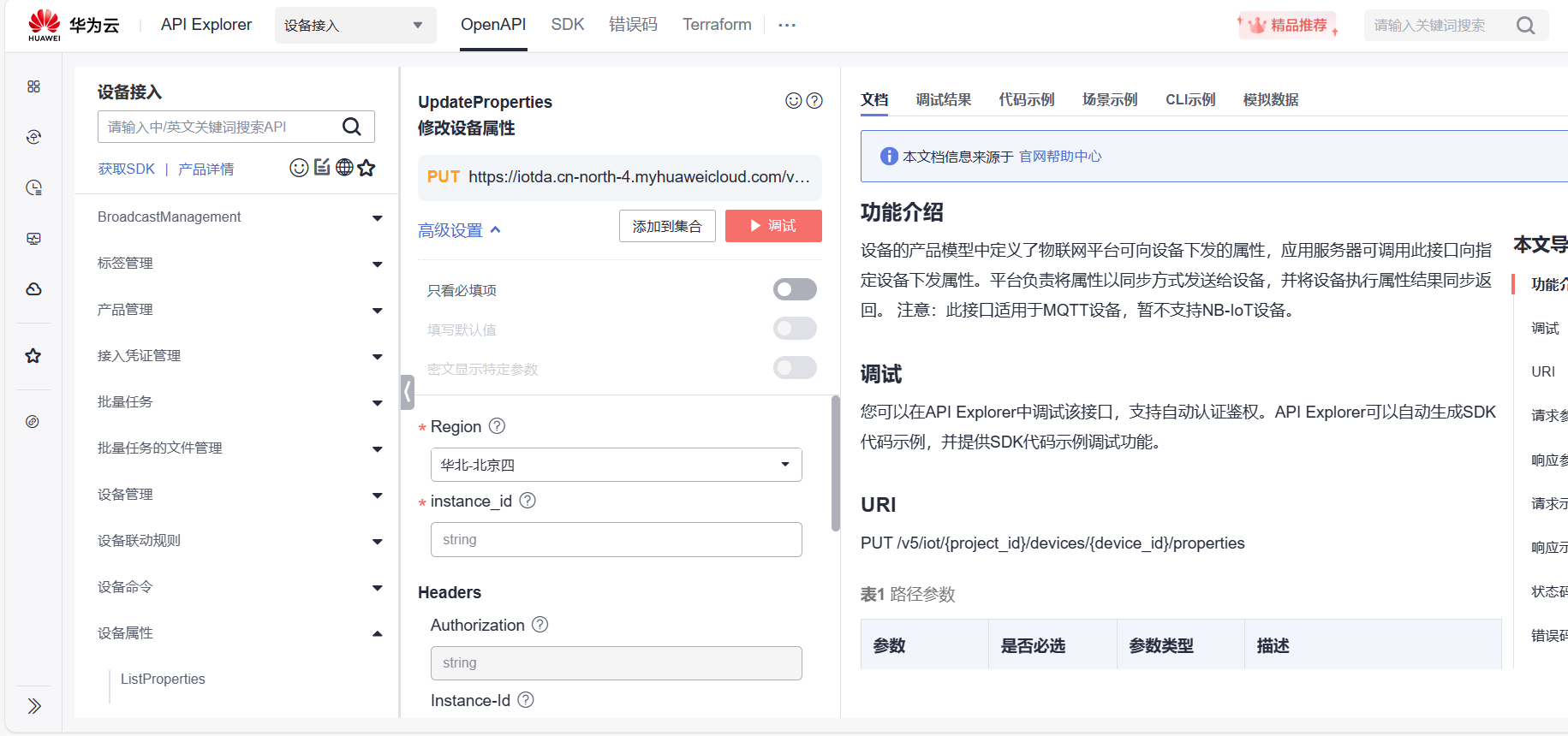
(上位机APP开发)调用华为云属性修改API接口修改设备属性
一、功能说明 通过调用华为云IOT提供的属性修改API接口,给设备下发属性修改消息。 API接口地址:https://support.huaweicloud.com/api-iothub/iot_06_v5_0034.html 此接口支持在线调试:https://console.huaweicloud.com/apiexplorer/#/openapi/IoTDA/doc?api=UpdatePrope…...

爆火的儿童绘本如何用AI制作?一文解锁从制作到变现的全流程!
大家好我是安琪! AI绘图发展势头如此猛烈,无论是Stable Diffusion,Midjourney,还是国内百度的文心一格,字节的豆包等,AI绘图技术越来越成熟,风格也越来越多样化。那么问题来了,对于普…...

Go interface{}类型转换
💝💝💝欢迎莅临我的博客,很高兴能够在这里和您见面!希望您在这里可以感受到一份轻松愉快的氛围,不仅可以获得有趣的内容和知识,也可以畅所欲言、分享您的想法和见解。 推荐:「stormsha的主页」…...

利用opencv自带的Haar级联分类器模型
OpenCV自带的Haar级联分类器模型: haarcascade_eye.xml: 这个模型用于检测眼睛。 haarcascade_eye_tree_eyeglasses.xml: 这个模型用于检测眼镜。 haarcascade_frontalcatface.xml: 这个模型用于检测猫脸。 haarcascade_frontalcatface_extended.xml: 这个模型用…...
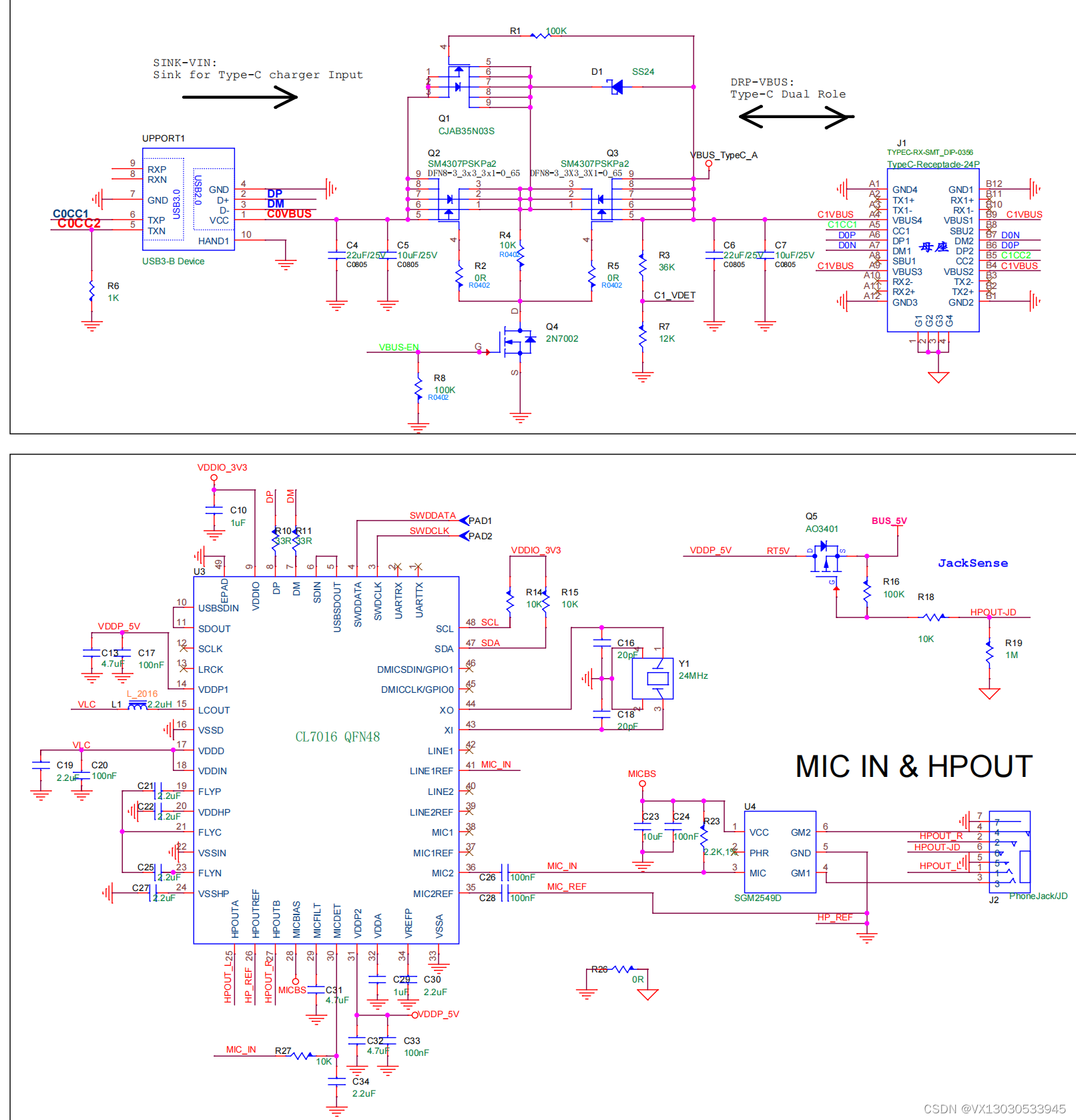
国产USB音频转换芯片CL7016C 支持国美标线控USB Type-C音频编解码器
CL7016C是一款高保真 USB Type-C 兼容音频编解码芯片。可以录制和回放有 24 比特音乐和声音。内置回放通路信号 动态压缩, 最大42db录音通路增益, PDM 数字麦克风,和立体声无需电容耳机驱动放大器。 5V单电源供电。兼容 USB 2.0 全速工业标…...
【linux网络(六)】IP协议详解
💓博主CSDN主页:杭电码农-NEO💓 ⏩专栏分类:Linux从入门到精通⏪ 🚚代码仓库:NEO的学习日记🚚 🌹关注我🫵带你学更多操作系统知识 🔝🔝 Linux网络 1. 前言2. IP协议报…...
)
CesiumJS【Basic】- #012添加点线面(entity方式)
文章目录 添加点线面(entity方式)1 目标2 实现2.1 GeometryManager.ts2.2 main.ts添加点线面(entity方式) 1 目标 使用实体方式添加点线面 2 实现 2.1 GeometryManager.ts // src/GeometryManager.tsimport * as Cesium from cesium;export class GeometryManager {pr…...

【Redis】内存回收和内存淘汰机制
1 概念 Redis 所有的数据都是存储在内存中的, 如果不进行任何的内存回收, 那么很容易出现内存爆满的情况。因此,在某些情况下需要对占用的内存空间进行释放。 Redis 中内存的释放主要分为两类 Redis 中内存的释放主要分为两类: 内存回收: 将过期的 key 清除&#…...

HTML 语义化
目录 HTML 语义化HTML5 新特性HTML 语义化的好处语义化标签的使用场景最佳实践 HTML 语义化 HTML5 新特性 标准答案: 语义化标签: <header>:页头<nav>:导航<main>:主要内容<article>&#x…...
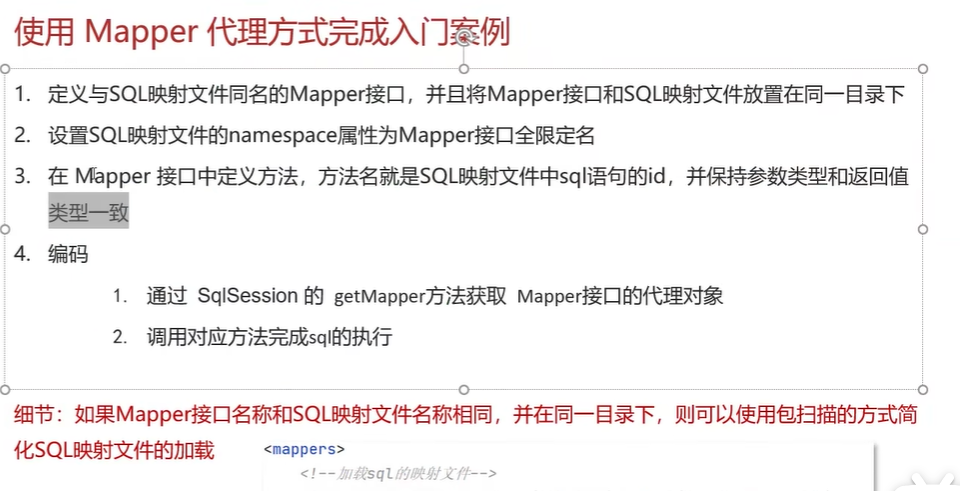
黑马Mybatis
Mybatis 表现层:页面展示 业务层:逻辑处理 持久层:持久数据化保存 在这里插入图片描述 Mybatis快速入门 
MySQL 隔离级别:脏读、幻读及不可重复读的原理与示例
一、MySQL 隔离级别 MySQL 提供了四种隔离级别,用于控制事务之间的并发访问以及数据的可见性,不同隔离级别对脏读、幻读、不可重复读这几种并发数据问题有着不同的处理方式,具体如下: 隔离级别脏读不可重复读幻读性能特点及锁机制读未提交(READ UNCOMMITTED)允许出现允许…...
)
【位运算】消失的两个数字(hard)
消失的两个数字(hard) 题⽬描述:解法(位运算):Java 算法代码:更简便代码 题⽬链接:⾯试题 17.19. 消失的两个数字 题⽬描述: 给定⼀个数组,包含从 1 到 N 所有…...
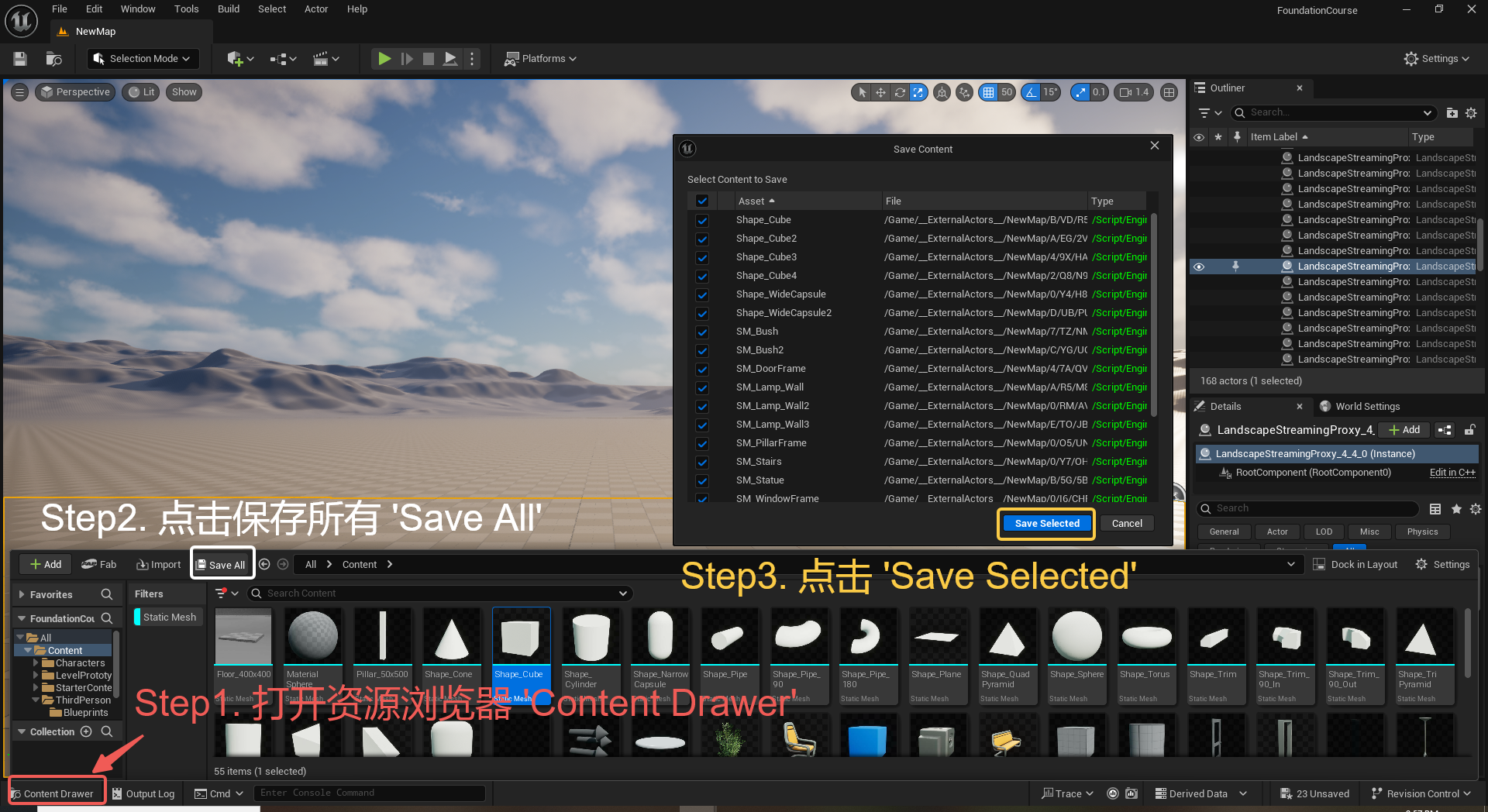
UE5 学习系列(三)创建和移动物体
这篇博客是该系列的第三篇,是在之前两篇博客的基础上展开,主要介绍如何在操作界面中创建和拖动物体,这篇博客跟随的视频链接如下: B 站视频:s03-创建和移动物体 如果你不打算开之前的博客并且对UE5 比较熟的话按照以…...
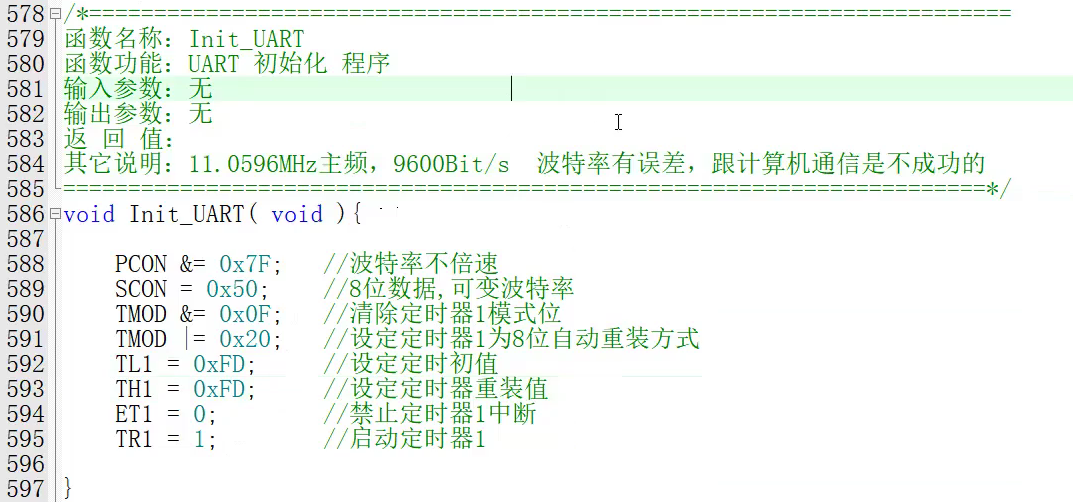
【单片机期末】单片机系统设计
主要内容:系统状态机,系统时基,系统需求分析,系统构建,系统状态流图 一、题目要求 二、绘制系统状态流图 题目:根据上述描述绘制系统状态流图,注明状态转移条件及方向。 三、利用定时器产生时…...
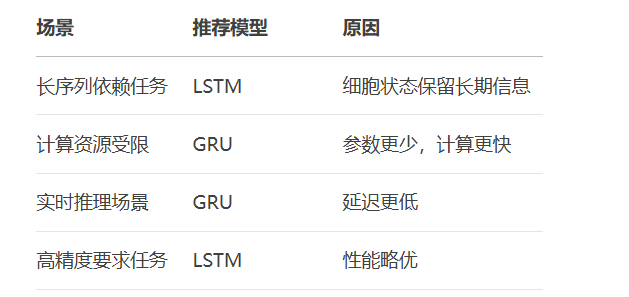
RNN避坑指南:从数学推导到LSTM/GRU工业级部署实战流程
本文较长,建议点赞收藏,以免遗失。更多AI大模型应用开发学习视频及资料,尽在聚客AI学院。 本文全面剖析RNN核心原理,深入讲解梯度消失/爆炸问题,并通过LSTM/GRU结构实现解决方案,提供时间序列预测和文本生成…...
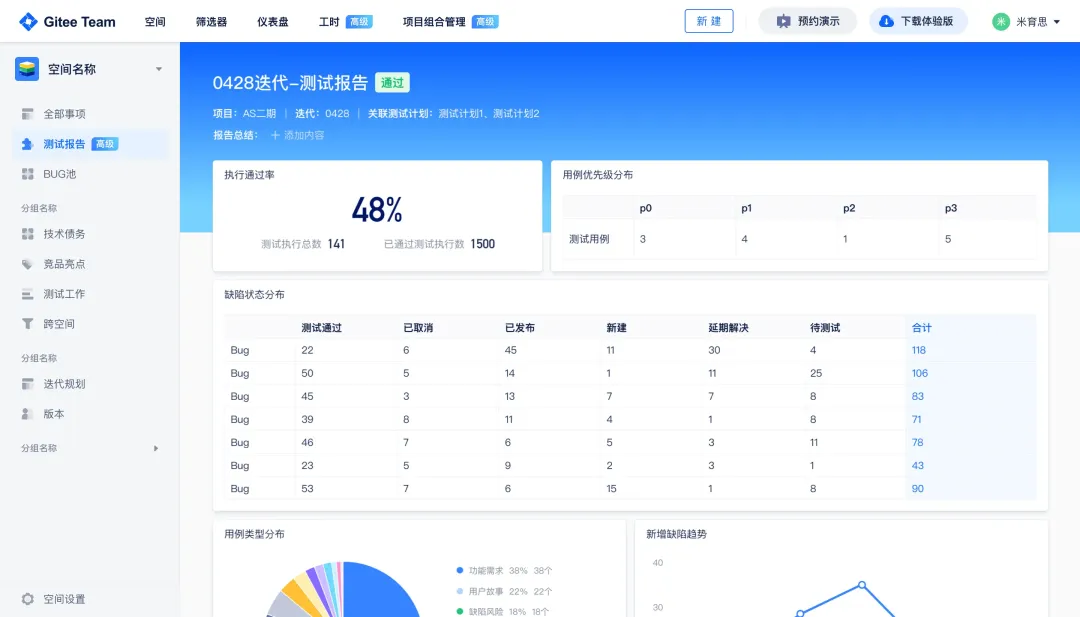
关键领域软件测试的突围之路:如何破解安全与效率的平衡难题
在数字化浪潮席卷全球的今天,软件系统已成为国家关键领域的核心战斗力。不同于普通商业软件,这些承载着国家安全使命的软件系统面临着前所未有的质量挑战——如何在确保绝对安全的前提下,实现高效测试与快速迭代?这一命题正考验着…...
)
C#学习第29天:表达式树(Expression Trees)
目录 什么是表达式树? 核心概念 1.表达式树的构建 2. 表达式树与Lambda表达式 3.解析和访问表达式树 4.动态条件查询 表达式树的优势 1.动态构建查询 2.LINQ 提供程序支持: 3.性能优化 4.元数据处理 5.代码转换和重写 适用场景 代码复杂性…...
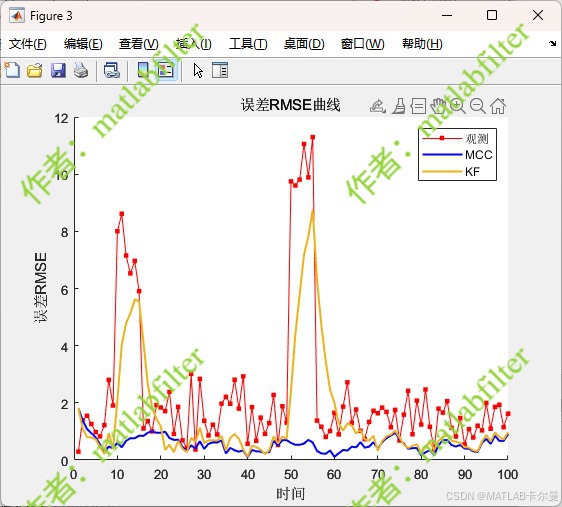
【MATLAB代码】基于最大相关熵准则(MCC)的三维鲁棒卡尔曼滤波算法(MCC-KF),附源代码|订阅专栏后可直接查看
文章所述的代码实现了基于最大相关熵准则(MCC)的三维鲁棒卡尔曼滤波算法(MCC-KF),针对传感器观测数据中存在的脉冲型异常噪声问题,通过非线性加权机制提升滤波器的抗干扰能力。代码通过对比传统KF与MCC-KF在含异常值场景下的表现,验证了后者在状态估计鲁棒性方面的显著优…...
