CTF-PWN: 全保护下格式化字符串利用 [第一届“吾杯”网络安全技能大赛 如果能重来] 赛后学习(没思路了)
通过网盘分享的文件:如果能重来.zip
链接: https://pan.baidu.com/s/1XKIJx32nWVcSpKiWFQGpYA?pwd=1111 提取码: 1111
--来自百度网盘超级会员v2的分享
漏洞分析
格式化字符串漏洞,在printf(format);
__int64 sub_13D7()
{char format[56]; // [rsp+10h] [rbp-40h] BYREFunsigned __int64 v2; // [rsp+48h] [rbp-8h]v2 = __readfsqword(0x28u);printf("Please input your name: ");if ( (int)sub_1247(format, 55LL) > 0 ){if ( dword_404C ){printf(format);--dword_404C;puts("There will be a gift for you here . . .");}else{puts("0.o? ");}return 0LL;}else{puts("Error reading name.");return 0xFFFFFFFFLL;}
}
确定参数偏移
❯ gdb pwn
GNU gdb (Ubuntu 12.1-0ubuntu1~22.04.2) 12.1
Copyright (C) 2022 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<https://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:<http://www.gnu.org/software/gdb/documentation/>.For help, type "help".
Type "apropos word" to search for commands related to "word"...
startpwndbg: loaded 165 pwndbg commands and 46 shell commands. Type pwndbg [--shell | --all] [filter] for a list.
pwndbg: created $rebase, $base, $bn_sym, $bn_var, $bn_eval, $ida GDB functions (can be used with print/break)
Reading symbols from pwn...
(No debugging symbols found in pwn)
------- tip of the day (disable with set show-tips off) -------
If you want Pwndbg to clear screen on each command (but still save previous output in history) use set context-clear-screen on
pwndbg> start
Temporary breakpoint 1 at 0x5555555550e0Temporary breakpoint 1, 0x00005555555550e0 in ?? ()
LEGEND: STACK | HEAP | CODE | DATA | WX | RODATA
───────────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]───────────────────────────────────────RAX 0x1cRBX 0RCX 0x7fffffffc478 —▸ 0x7fffffffc82b ◂— 'SYSTEMD_EXEC_PID=1816'RDX 0x7ffff7fe0d60 ◂— endbr64 RDI 0x7ffff7ffe190 —▸ 0x555555554000 ◂— 0x10102464c457fRSI 0x7ffff7ffe730 ◂— 0R8 0R9 2R10 0xfR11 0R12 0x5555555550e0 ◂— endbr64 R13 0x7fffffffc460 ◂— 1R14 0R15 0RBP 0RSP 0x7fffffffc460 ◂— 1RIP 0x5555555550e0 ◂— endbr64
────────────────────────────────────────────────[ DISASM / x86-64 / set emulate on ]────────────────────────────────────────────────► 0x5555555550e0 endbr64 0x5555555550e4 xor ebp, ebp EBP => 00x5555555550e6 mov r9, rdx R9 => 0x7ffff7fe0d60 ◂— endbr64 0x5555555550e9 pop rsi RSI => 10x5555555550ea mov rdx, rsp RDX => 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'0x5555555550ed and rsp, 0xfffffffffffffff0 RSP => 0x7fffffffc460 (0x7fffffffc468 & -0x10)0x5555555550f1 push rax0x5555555550f2 push rsp0x5555555550f3 lea r8, [rip + 0x426] R8 => 0x555555555520 ◂— endbr64 0x5555555550fa lea rcx, [rip + 0x3af] RCX => 0x5555555554b0 ◂— endbr64 0x555555555101 lea rdi, [rip + 0x385] RDI => 0x55555555548d ◂— endbr64
─────────────────────────────────────────────────────────────[ STACK ]──────────────────────────────────────────────────────────────
00:0000│ r13 rsp 0x7fffffffc460 ◂— 1
01:0008│ 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
02:0010│ 0x7fffffffc470 ◂— 0
03:0018│ rcx 0x7fffffffc478 —▸ 0x7fffffffc82b ◂— 'SYSTEMD_EXEC_PID=1816'
04:0020│ 0x7fffffffc480 —▸ 0x7fffffffc841 ◂— 'SSH_AUTH_SOCK=/run/user/1000/keyring/ssh'
05:0028│ 0x7fffffffc488 —▸ 0x7fffffffc86a ◂— 'SESSION_MANAGER=local/ubuntu:@/tmp/.ICE-unix/1816,unix/ubuntu:/tmp/.ICE-unix/1816'
06:0030│ 0x7fffffffc490 —▸ 0x7fffffffc8bc ◂— 'PAPERSIZE=a4'
07:0038│ 0x7fffffffc498 —▸ 0x7fffffffc8c9 ◂— 'GNOME_TERMINAL_SCREEN=/org/gnome/Terminal/screen/aab6f309_847c_4363_b37f_36574de33f67'
───────────────────────────────────────────────────────────[ BACKTRACE ]────────────────────────────────────────────────────────────► 0 0x5555555550e01 0x12 0x7fffffffc80b3 0x0
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> b *$rebase(0x1444)
Breakpoint 2 at 0x555555555401
pwndbg> run
Starting program: /home/a5rz/Desktop/pwn/file/pwn
Please input your name: aaaaaaaa%p%p%p%p%p%p%p%p%p%p%p%pBreakpoint 2, 0x0000555555555444 in ?? ()
LEGEND: STACK | HEAP | CODE | DATA | WX | RODATA
───────────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]───────────────────────────────────────RAX 0RBX 0x5555555554b0 ◂— endbr64 RCX 0RDX 1RDI 0x7fffffffc2e0 ◂— 'aaaaaaaa%p%p%p%p%p%p%p%p%p%p%p%pSomething strange here'RSI 0x7fffffffc2af ◂— 0x1000000200a /* '\n ' */R8 0x18R9 0x18R10 0x555555556008 ◂— 'Please input your name: 'R11 0x246R12 0x5555555550e0 ◂— endbr64 R13 0x7fffffffc460 ◂— 1R14 0R15 0RBP 0x7fffffffc320 —▸ 0x7fffffffc360 —▸ 0x7fffffffc370 ◂— 0RSP 0x7fffffffc2d0 ◂— 0RIP 0x555555555444 ◂— call 0x5555555550b0
────────────────────────────────────────────────[ DISASM / x86-64 / set emulate on ]────────────────────────────────────────────────► 0x555555555444 call printf@plt <printf@plt>format: 0x7fffffffc2e0 ◂— 'aaaaaaaa%p%p%p%p%p%p%p%p%p%p%p%pSomething strange here'vararg: 0x7fffffffc2af ◂— 0x1000000200a /* '\n ' */0x555555555449 mov eax, dword ptr [rip + 0x2bfd] EAX, [0x55555555804c]0x55555555544f sub eax, 10x555555555452 mov dword ptr [rip + 0x2bf4], eax0x555555555458 lea rdi, [rip + 0xbd9] RDI => 0x555555556038 ◂— 'There will be a gift for you here . . .'0x55555555545f call puts@plt <puts@plt>0x555555555464 jmp 0x555555555472 <0x555555555472>↓0x555555555472 mov eax, 0 EAX => 00x555555555477 mov rdx, qword ptr [rbp - 8]0x55555555547b xor rdx, qword ptr fs:[0x28]0x555555555484 je 0x55555555548b <0x55555555548b>
─────────────────────────────────────────────────────────────[ STACK ]──────────────────────────────────────────────────────────────
00:0000│ rsp 0x7fffffffc2d0 ◂— 0
01:0008│-048 0x7fffffffc2d8 ◂— 0xf7fc37d0f7fc25c0
02:0010│ rdi 0x7fffffffc2e0 ◂— 'aaaaaaaa%p%p%p%p%p%p%p%p%p%p%p%pSomething strange here'
03:0018│-038 0x7fffffffc2e8 ◂— '%p%p%p%p%p%p%p%p%p%p%p%pSomething strange here'
... ↓ 2 skipped
06:0030│-020 0x7fffffffc300 ◂— 'Something strange here'
07:0038│-018 0x7fffffffc308 ◂— 'g strange here'
───────────────────────────────────────────────────────────[ BACKTRACE ]────────────────────────────────────────────────────────────► 0 0x5555555554441 0x5555555553bc2 0x5555555554a93 0x7ffff7df9083 __libc_start_main+2434 0x55555555510e
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> stack 90
00:0000│ rsp 0x7fffffffc2d0 ◂— 0
01:0008│-048 0x7fffffffc2d8 ◂— 0xf7fc37d0f7fc25c0
02:0010│ rdi 0x7fffffffc2e0 ◂— 'aaaaaaaa%p%p%p%p%p%p%p%p%p%p%p%pSomething strange here'
03:0018│-038 0x7fffffffc2e8 ◂— '%p%p%p%p%p%p%p%p%p%p%p%pSomething strange here'
... ↓ 2 skipped
06:0030│-020 0x7fffffffc300 ◂— 'Something strange here'
07:0038│-018 0x7fffffffc308 ◂— 'g strange here'
08:0040│-010 0x7fffffffc310 ◂— 0x657265682065 /* 'e here' */
09:0048│-008 0x7fffffffc318 ◂— 0x4d8fe1de9078d800
0a:0050│ rbp 0x7fffffffc320 —▸ 0x7fffffffc360 —▸ 0x7fffffffc370 ◂— 0
0b:0058│+008 0x7fffffffc328 —▸ 0x5555555553bc ◂— mov eax, 0
0c:0060│+010 0x7fffffffc330 ◂— 'welcome to WuCup !'
0d:0068│+018 0x7fffffffc338 ◂— 'to WuCup !'
0e:0070│+020 0x7fffffffc340 ◂— 0x555555002120 /* ' !' */
0f:0078│+028 0x7fffffffc348 —▸ 0x7fffffffc460 ◂— 1
10:0080│+030 0x7fffffffc350 ◂— 0
11:0088│+038 0x7fffffffc358 ◂— 0x4d8fe1de9078d800
12:0090│+040 0x7fffffffc360 —▸ 0x7fffffffc370 ◂— 0
13:0098│+048 0x7fffffffc368 —▸ 0x5555555554a9 ◂— mov eax, 0
14:00a0│+050 0x7fffffffc370 ◂— 0
15:00a8│+058 0x7fffffffc378 —▸ 0x7ffff7df9083 (__libc_start_main+243) ◂— mov edi, eax
16:00b0│+060 0x7fffffffc380 —▸ 0x7ffff7ffc620 (_rtld_global_ro) ◂— 0x50fa700000000
17:00b8│+068 0x7fffffffc388 —▸ 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
18:00c0│+070 0x7fffffffc390 ◂— 0x100000000
19:00c8│+078 0x7fffffffc398 —▸ 0x55555555548d ◂— endbr64
1a:00d0│+080 0x7fffffffc3a0 —▸ 0x5555555554b0 ◂— endbr64
1b:00d8│+088 0x7fffffffc3a8 ◂— 0xb19ed39ac14d0a56
1c:00e0│+090 0x7fffffffc3b0 —▸ 0x5555555550e0 ◂— endbr64
1d:00e8│+098 0x7fffffffc3b8 —▸ 0x7fffffffc460 ◂— 1
1e:00f0│+0a0 0x7fffffffc3c0 ◂— 0
1f:00f8│+0a8 0x7fffffffc3c8 ◂— 0
20:0100│+0b0 0x7fffffffc3d0 ◂— 0x4e612c65464d0a56 ('V\nMFe,aN')
21:0108│+0b8 0x7fffffffc3d8 ◂— 0x4e613c25e1230a56
22:0110│+0c0 0x7fffffffc3e0 ◂— 0
... ↓ 2 skipped
25:0128│+0d8 0x7fffffffc3f8 ◂— 1
26:0130│+0e0 0x7fffffffc400 —▸ 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
27:0138│+0e8 0x7fffffffc408 —▸ 0x7fffffffc478 —▸ 0x7fffffffc82b ◂— 'SYSTEMD_EXEC_PID=1816'
28:0140│+0f0 0x7fffffffc410 —▸ 0x7ffff7ffe190 —▸ 0x555555554000 ◂— 0x10102464c457f
29:0148│+0f8 0x7fffffffc418 ◂— 0
2a:0150│+100 0x7fffffffc420 ◂— 0
2b:0158│+108 0x7fffffffc428 —▸ 0x5555555550e0 ◂— endbr64
2c:0160│+110 0x7fffffffc430 —▸ 0x7fffffffc460 ◂— 1
2d:0168│+118 0x7fffffffc438 ◂— 0
2e:0170│+120 0x7fffffffc440 ◂— 0
2f:0178│+128 0x7fffffffc448 —▸ 0x55555555510e ◂— hlt
30:0180│+130 0x7fffffffc450 —▸ 0x7fffffffc458 ◂— 0x1c
31:0188│+138 0x7fffffffc458 ◂— 0x1c
32:0190│ r13 0x7fffffffc460 ◂— 1
33:0198│+148 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
34:01a0│+150 0x7fffffffc470 ◂— 0
35:01a8│+158 0x7fffffffc478 —▸ 0x7fffffffc82b ◂— 'SYSTEMD_EXEC_PID=1816'
36:01b0│+160 0x7fffffffc480 —▸ 0x7fffffffc841 ◂— 'SSH_AUTH_SOCK=/run/user/1000/keyring/ssh'
37:01b8│+168 0x7fffffffc488 —▸ 0x7fffffffc86a ◂— 'SESSION_MANAGER=local/ubuntu:@/tmp/.ICE-unix/1816,unix/ubuntu:/tmp/.ICE-unix/1816'
38:01c0│+170 0x7fffffffc490 —▸ 0x7fffffffc8bc ◂— 'PAPERSIZE=a4'
39:01c8│+178 0x7fffffffc498 —▸ 0x7fffffffc8c9 ◂— 'GNOME_TERMINAL_SCREEN=/org/gnome/Terminal/screen/aab6f309_847c_4363_b37f_36574de33f67'
3a:01d0│+180 0x7fffffffc4a0 —▸ 0x7fffffffc91f ◂— 'LANGUAGE=zh_CN:en_GB:en'
3b:01d8│+188 0x7fffffffc4a8 —▸ 0x7fffffffc937 ◂— 'LANG=zh_CN.UTF-8'
3c:01e0│+190 0x7fffffffc4b0 —▸ 0x7fffffffc948 ◂— 'WAYLAND_DISPLAY=wayland-0'
3d:01e8│+198 0x7fffffffc4b8 —▸ 0x7fffffffc962 ◂— 'LC_IDENTIFICATION=zh_CN.UTF-8'
3e:01f0│+1a0 0x7fffffffc4c0 —▸ 0x7fffffffc980 ◂— 'XDG_SESSION_CLASS=user'
3f:01f8│+1a8 0x7fffffffc4c8 —▸ 0x7fffffffc997 ◂— 'XDG_CURRENT_DESKTOP=ubuntu:GNOME'
40:0200│+1b0 0x7fffffffc4d0 —▸ 0x7fffffffc9b8 ◂— 'PWD=/home/a5rz/Desktop/pwn/file'
41:0208│+1b8 0x7fffffffc4d8 —▸ 0x7fffffffc9d8 ◂— 'QT_IM_MODULE=ibus'
42:0210│+1c0 0x7fffffffc4e0 —▸ 0x7fffffffc9ea ◂— 'USER=a5rz'
43:0218│+1c8 0x7fffffffc4e8 —▸ 0x7fffffffc9f4 ◂— 'DESKTOP_SESSION=ubuntu'
44:0220│+1d0 0x7fffffffc4f0 —▸ 0x7fffffffca0b ◂— 'XDG_MENU_PREFIX=gnome-'
45:0228│+1d8 0x7fffffffc4f8 —▸ 0x7fffffffca22 ◂— 'OLDPWD=/home/a5rz/Desktop/pwn/file'
46:0230│+1e0 0x7fffffffc500 —▸ 0x7fffffffca45 ◂— 'LC_MEASUREMENT=zh_CN.UTF-8'
47:0238│+1e8 0x7fffffffc508 —▸ 0x7fffffffca60 ◂— 'DBUS_SESSION_BUS_ADDRESS=unix:path=/run/user/1000/bus,guid=648017a497f89697dfa1bf47674d827a'
48:0240│+1f0 0x7fffffffc510 —▸ 0x7fffffffcabc ◂— 'LC_NUMERIC=zh_CN.UTF-8'
49:0248│+1f8 0x7fffffffc518 —▸ 0x7fffffffcad3 ◂— 'SSH_AGENT_LAUNCHER=gnome-keyring'
4a:0250│+200 0x7fffffffc520 —▸ 0x7fffffffcaf4 ◂— '_=/home/a5rz/Desktop/pwn/file/pwn'
4b:0258│+208 0x7fffffffc528 —▸ 0x7fffffffcb16 ◂— 'GTK_MODULES=gail:atk-bridge'
4c:0260│+210 0x7fffffffc530 —▸ 0x7fffffffcb32 ◂— 'VTE_VERSION=6800'
4d:0268│+218 0x7fffffffc538 —▸ 0x7fffffffcb43 ◂— 'XDG_SESSION_DESKTOP=ubuntu'
4e:0270│+220 0x7fffffffc540 —▸ 0x7fffffffcb5e ◂— 'QT_ACCESSIBILITY=1'
4f:0278│+228 0x7fffffffc548 —▸ 0x7fffffffcb71 ◂— 'GNOME_DESKTOP_SESSION_ID=this-is-deprecated'
50:0280│+230 0x7fffffffc550 —▸ 0x7fffffffcb9d ◂— 'GNOME_SETUP_DISPLAY=:1'
51:0288│+238 0x7fffffffc558 —▸ 0x7fffffffcbb4 ◂— 'LC_TIME=zh_CN.UTF-8'
52:0290│+240 0x7fffffffc560 —▸ 0x7fffffffcbc8 ◂— 'LOGNAME=a5rz'
53:0298│+248 0x7fffffffc568 —▸ 0x7fffffffcbd5 ◂— 'GNOME_TERMINAL_SERVICE=:1.112'
54:02a0│+250 0x7fffffffc570 —▸ 0x7fffffffcbf3 ◂— 'LC_PAPER=zh_CN.UTF-8'
55:02a8│+258 0x7fffffffc578 —▸ 0x7fffffffcc08 ◂— 'HOME=/home/a5rz'
56:02b0│+260 0x7fffffffc580 —▸ 0x7fffffffcc18 ◂— 'GNOME_SHELL_SESSION_MODE=ubuntu'
57:02b8│+268 0x7fffffffc588 —▸ 0x7fffffffcc38 ◂— 'XDG_DATA_DIRS=/usr/local/share/:/usr/share/:/var/lib/snapd/desktop'
58:02c0│+270 0x7fffffffc590 —▸ 0x7fffffffcc7b ◂— 'XMODIFIERS=@im=ibus'
59:02c8│+278 0x7fffffffc598 —▸ 0x7fffffffcc8f ◂— 'XDG_RUNTIME_DIR=/run/user/1000'
pwndbg> ni
aaaaaaaa0x7fffffffc2af0x1(nil)0x180x18(nil)0xf7fc37d0f7fc25c00x61616161616161610x70257025702570250x70257025702570250x70257025702570250x6e696874656d6f53Something
aaaaaaaa
0x7fffffffc2af
0x1
(nil)
0x18
0x18
(nil)
0xf7fc37d0f7fc25c0
0x6161616161616161
0x70257025702570250x70257025702570250x70257025702570250x6e696874656d6f53Something
得知偏移量为8,验证
pwndbg> run
Starting program: /home/a5rz/Desktop/pwn/file/pwn
Please input your name: aaaaaaaa%8$pBreakpoint 2, 0x0000555555555444 in ?? ()
LEGEND: STACK | HEAP | CODE | DATA | WX | RODATA
───────────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]───────────────────────────────────────RAX 0RBX 0x5555555554b0 ◂— endbr64 RCX 0RDX 1RDI 0x7fffffffc2e0 ◂— 0x6161616161616161 ('aaaaaaaa')RSI 0x7fffffffc2af ◂— 0x10000000c0a /* '\n\x0c' */R8 0x18R9 0x18R10 0x555555556008 ◂— 'Please input your name: 'R11 0x246R12 0x5555555550e0 ◂— endbr64 R13 0x7fffffffc460 ◂— 1R14 0R15 0RBP 0x7fffffffc320 —▸ 0x7fffffffc360 —▸ 0x7fffffffc370 ◂— 0RSP 0x7fffffffc2d0 ◂— 0RIP 0x555555555444 ◂— call 0x5555555550b0
────────────────────────────────────────────────[ DISASM / x86-64 / set emulate on ]────────────────────────────────────────────────► 0x555555555444 call printf@plt <printf@plt>format: 0x7fffffffc2e0 ◂— 0x6161616161616161 ('aaaaaaaa')vararg: 0x7fffffffc2af ◂— 0x10000000c0a /* '\n\x0c' */0x555555555449 mov eax, dword ptr [rip + 0x2bfd] EAX, [0x55555555804c]0x55555555544f sub eax, 10x555555555452 mov dword ptr [rip + 0x2bf4], eax0x555555555458 lea rdi, [rip + 0xbd9] RDI => 0x555555556038 ◂— 'There will be a gift for you here . . .'0x55555555545f call puts@plt <puts@plt>0x555555555464 jmp 0x555555555472 <0x555555555472>↓0x555555555472 mov eax, 0 EAX => 00x555555555477 mov rdx, qword ptr [rbp - 8]0x55555555547b xor rdx, qword ptr fs:[0x28]0x555555555484 je 0x55555555548b <0x55555555548b>
─────────────────────────────────────────────────────────────[ STACK ]──────────────────────────────────────────────────────────────
00:0000│ rsp 0x7fffffffc2d0 ◂— 0
01:0008│-048 0x7fffffffc2d8 ◂— 0xf7fc37d0f7fc25c0
02:0010│ rdi 0x7fffffffc2e0 ◂— 0x6161616161616161 ('aaaaaaaa')
03:0018│-038 0x7fffffffc2e8 ◂— 0x7fff70243825
04:0020│-030 0x7fffffffc2f0 ◂— 0
05:0028│-028 0x7fffffffc2f8 —▸ 0x7fffffffc300 ◂— 'Something strange here'
06:0030│-020 0x7fffffffc300 ◂— 'Something strange here'
07:0038│-018 0x7fffffffc308 ◂— 'g strange here'
───────────────────────────────────────────────────────────[ BACKTRACE ]────────────────────────────────────────────────────────────► 0 0x5555555554441 0x5555555553bc2 0x5555555554a93 0x7ffff7df9083 __libc_start_main+2434 0x55555555510e
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> c
Continuing.
aaaaaaaa0x6161616161616161�There will be a gift for you here . . .
[Inferior 1 (process 3806) exited normally]
ebp总是指向上一个ebp,我们可以使用这个特性用第一个ebp改写第二个ebp,再用第二个ebp作为跳板更改栈上任意地址?
pwndbg> stack 60
00:0000│ rsp 0x7fffffffc2d0 ◂— 0
01:0008│-048 0x7fffffffc2d8 ◂— 0xf7fc37d0f7fc25c0
02:0010│ rdi 0x7fffffffc2e0 ◂— 0x30 /* '0' */
03:0018│-038 0x7fffffffc2e8 —▸ 0x7ffff7e67525 ◂— cmp eax, -1
04:0020│-030 0x7fffffffc2f0 ◂— 0
05:0028│-028 0x7fffffffc2f8 —▸ 0x7fffffffc300 ◂— 'Something strange here'
06:0030│-020 0x7fffffffc300 ◂— 'Something strange here'
07:0038│-018 0x7fffffffc308 ◂— 'g strange here'
08:0040│-010 0x7fffffffc310 ◂— 0x657265682065 /* 'e here' */
09:0048│-008 0x7fffffffc318 ◂— 0x1fdd857982303200
0a:0050│ rbp 0x7fffffffc320 —▸ 0x7fffffffc360 —▸ 0x7fffffffc370 ◂— 0
0b:0058│+008 0x7fffffffc328 —▸ 0x5555555553bc ◂— mov eax, 0
0c:0060│+010 0x7fffffffc330 ◂— 'welcome to WuCup !'
0d:0068│+018 0x7fffffffc338 ◂— 'to WuCup !'
0e:0070│+020 0x7fffffffc340 ◂— 0x555555002120 /* ' !' */
0f:0078│+028 0x7fffffffc348 —▸ 0x7fffffffc460 ◂— 1
10:0080│+030 0x7fffffffc350 ◂— 0
11:0088│+038 0x7fffffffc358 ◂— 0x1fdd857982303200
12:0090│+040 0x7fffffffc360 —▸ 0x7fffffffc370 ◂— 0
13:0098│+048 0x7fffffffc368 —▸ 0x5555555554a9 ◂— mov eax, 0
14:00a0│+050 0x7fffffffc370 ◂— 0
15:00a8│+058 0x7fffffffc378 —▸ 0x7ffff7df9083 (__libc_start_main+243) ◂— mov edi, eax
16:00b0│+060 0x7fffffffc380 —▸ 0x7ffff7ffc620 (_rtld_global_ro) ◂— 0x50fa700000000
17:00b8│+068 0x7fffffffc388 —▸ 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
18:00c0│+070 0x7fffffffc390 ◂— 0x100000000
19:00c8│+078 0x7fffffffc398 —▸ 0x55555555548d ◂— endbr64
1a:00d0│+080 0x7fffffffc3a0 —▸ 0x5555555554b0 ◂— endbr64
1b:00d8│+088 0x7fffffffc3a8 ◂— 0x3d68c2224b0eb8ed
1c:00e0│+090 0x7fffffffc3b0 —▸ 0x5555555550e0 ◂— endbr64
1d:00e8│+098 0x7fffffffc3b8 —▸ 0x7fffffffc460 ◂— 1
1e:00f0│+0a0 0x7fffffffc3c0 ◂— 0
1f:00f8│+0a8 0x7fffffffc3c8 ◂— 0
20:0100│+0b0 0x7fffffffc3d0 ◂— 0xc2973dddcc0eb8ed
21:0108│+0b8 0x7fffffffc3d8 ◂— 0xc2972d9d6b60b8ed
22:0110│+0c0 0x7fffffffc3e0 ◂— 0
... ↓ 2 skipped
25:0128│+0d8 0x7fffffffc3f8 ◂— 1
26:0130│+0e0 0x7fffffffc400 —▸ 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
27:0138│+0e8 0x7fffffffc408 —▸ 0x7fffffffc478 —▸ 0x7fffffffc82b ◂— 'SYSTEMD_EXEC_PID=1816'
28:0140│+0f0 0x7fffffffc410 —▸ 0x7ffff7ffe190 —▸ 0x555555554000 ◂— 0x10102464c457f
29:0148│+0f8 0x7fffffffc418 ◂— 0
2a:0150│+100 0x7fffffffc420 ◂— 0
2b:0158│+108 0x7fffffffc428 —▸ 0x5555555550e0 ◂— endbr64
2c:0160│+110 0x7fffffffc430 —▸ 0x7fffffffc460 ◂— 1
2d:0168│+118 0x7fffffffc438 ◂— 0
2e:0170│+120 0x7fffffffc440 ◂— 0
2f:0178│+128 0x7fffffffc448 —▸ 0x55555555510e ◂— hlt
30:0180│+130 0x7fffffffc450 —▸ 0x7fffffffc458 ◂— 0x1c
31:0188│+138 0x7fffffffc458 ◂— 0x1c
32:0190│ r13 0x7fffffffc460 ◂— 1
33:0198│+148 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
34:01a0│+150 0x7fffffffc470 ◂— 0
35:01a8│+158 0x7fffffffc478 —▸ 0x7fffffffc82b ◂— 'SYSTEMD_EXEC_PID=1816'
36:01b0│+160 0x7fffffffc480 —▸ 0x7fffffffc841 ◂— 'SSH_AUTH_SOCK=/run/user/1000/keyring/ssh'
37:01b8│+168 0x7fffffffc488 —▸ 0x7fffffffc86a ◂— 'SESSION_MANAGER=local/ubuntu:@/tmp/.ICE-unix/1816,unix/ubuntu:/tmp/.ICE-unix/1816'
38:01c0│+170 0x7fffffffc490 —▸ 0x7fffffffc8bc ◂— 'PAPERSIZE=a4'
39:01c8│+178 0x7fffffffc498 —▸ 0x7fffffffc8c9 ◂— 'GNOME_TERMINAL_SCREEN=/org/gnome/Terminal/screen/aab6f309_847c_4363_b37f_36574de33f67'
3a:01d0│+180 0x7fffffffc4a0 —▸ 0x7fffffffc91f ◂— 'LANGUAGE=zh_CN:en_GB:en'
3b:01d8│+188 0x7fffffffc4a8 —▸ 0x7fffffffc937 ◂— 'LANG=zh_CN.UTF-8'
确实没思路了,有没有师傅能发个wp或指点一下?谢谢了,先看看另一道web&pwn了
相关文章:
)
CTF-PWN: 全保护下格式化字符串利用 [第一届“吾杯”网络安全技能大赛 如果能重来] 赛后学习(没思路了)
通过网盘分享的文件:如果能重来.zip 链接: https://pan.baidu.com/s/1XKIJx32nWVcSpKiWFQGpYA?pwd1111 提取码: 1111 --来自百度网盘超级会员v2的分享漏洞分析 格式化字符串漏洞,在printf(format); __int64 sub_13D7() {char format[56]; // [rsp10h] [rbp-40h]…...

C++学习日记---第16天
笔记复习 1.C对象模型 在C中,类内的成员变量和成员函数分开存储 我们知道,C中的成员变量和成员函数均可分为两种,一种是普通的,一种是静态的,对于静态成员变量和静态成员函数,我们知道他们不属于类的对象…...

SOA、分布式、微服务之间的关系和区别?
在当今的软件开发领域,SOA(面向服务架构)、分布式系统和微服务是三个重要的概念。它们各自有着独特的特性和应用场景,同时也存在着密切的关系。以下是关于这三者之间关系和区别的详细分析: 关系 分布式架构的范畴&…...

java基础概念46-数据结构1
一、引入 List集合的三种实现类使用了不同的数据结构! 二、数据结构的定义 三、常见的数据结构 3-1、栈 特点:先进后出,后进先出。 java内存容器: 3-2、队列 特点:先进先出、后进后出。 栈VS队列-小结 3-3、数组 3-…...

Node.js-Mongodb数据库
MongoDB MongoDB是什么? MongoDB是一个基于分布式文件存储的数据库 数据库是什么? 数据库(DataBase)是按照数据结构来组织、存储和管理数据的应用程序(软件) 数据库作用? 对数据进行增、删…...

STM32 ADC --- 知识点总结
STM32 ADC — 知识点总结 文章目录 STM32 ADC --- 知识点总结cubeMX中配置注解单次转换模式、连续转换模式、扫描模式单通道采样的情况单次转换模式:连续转换模式: 多通道采样的情况禁止扫描模式(单次转换模式或连续转换模式)单次…...

技术创新与人才培养并重 软通动力子公司鸿湖万联亮相OpenHarmony人才生态大会
11月27日,由开放原子开源基金会指导,OpenHarmony项目群工作委员会主办的OpenHarmony人才生态大会2024在武汉隆重举办。软通动力子公司鸿湖万联作为OpenHarmony项目群A类捐赠人应邀出席。大会期间,鸿湖万联不仅深度参与了OpenHarmony人才生态年…...

兔子繁衍问题
7-2 兔子繁衍问题 分数 15 全屏浏览 切换布局 作者 徐镜春 单位 浙江大学 一对兔子,从出生后第3个月起每个月都生一对兔子。小兔子长到第3个月后每个月又生一对兔子。假如兔子都不死,请问第1个月出生的一对兔子,至少需要繁衍到第几个月时兔…...

汉代风云人物 1晁错
晁错曾是汉景帝的老师。汉景帝登基后,晁错提出削藩建议,这一举措遭到诸多藩国诸侯的强烈反对,由此引发了紧张局势。 袁盎此前曾担任吴国的宰相,晁错觉得袁盎与吴国等藩国关系密切,很可能知晓藩王们谋反的相关情况却没…...

学习threejs,使用specularMap设置高光贴图
👨⚕️ 主页: gis分享者 👨⚕️ 感谢各位大佬 点赞👍 收藏⭐ 留言📝 加关注✅! 👨⚕️ 收录于专栏:threejs gis工程师 文章目录 一、🍀前言1.1 ☘️THREE.MeshPhongMaterial高…...
【UE5 C++】判断两点连线是否穿过球体
目录 前言 方法一 原理 代码 测试 结果 方法二 原理 一、检查连线与球体的相交情况 二、检查距离与球体半径的关系 三、检查连线与球体的相交 代码 前言 通过数学原理判断空间中任意两点的连线是否穿过球体,再通过射线检测检验算法的正确性。 方法一 …...

【Blender】如何创建空心管道
步骤 1:创建一个圆柱体 添加圆柱体: 在 Object Mode 下按 Shift A > Mesh > Cylinder。 步骤 2:制作空心效果 进入编辑模式: 选中圆柱体,按 Tab 进入 Edit Mode。 删除顶部和底部面: 按 3 进入面选…...

ChromeBook11 HP G7EE 刷入Ubuntu的记录
设置开发模式-> 拆电池(解锁)-> 刷入bios ->使用u盘刷入系统。 下面是详细过程,除了拆机有点紧,没有难度(我不负责~ 其实我试了好几次其他系统的,先进了pe,pe没问题(音频x),有一个win10的u盘(几个…...

16asm - 汇编介绍 和 debug使用
文章目录 前言硬件运行机制微机系统硬件组成计算机系统组成8086cpu组织架构dosbox安装配置debug debug使用R命令D命令E命令U命令T命令A命令标志寄存器 总结 前言 各位师傅大家好,我是qmx_07,今天给大家讲解 十六位汇编 和 debug调试器的使用 硬件运行…...
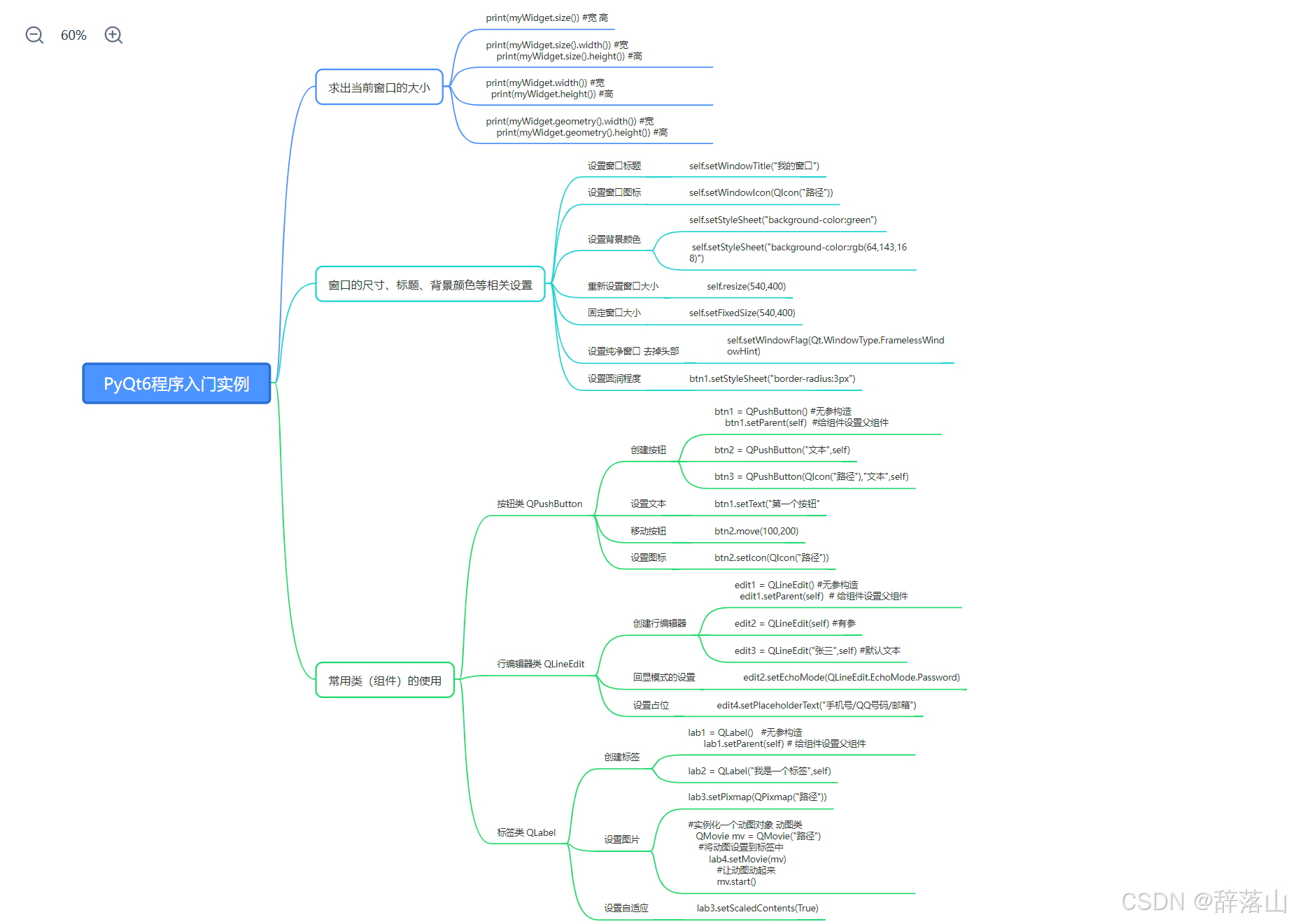
初识QT第一天
思维导图 利用Qt尝试做出原神登陆界面 import sys from PyQt6.QtGui import QIcon, QPixmap, QMovie from PyQt6.QtWidgets import QApplication, QWidget, QLabel, QPushButton, QLineEdit# 封装原神窗口类 class Genshin(QWidget):# 构造函数def __init__(self):# 初始化父类…...

ChatGPT科研应用、论文写作、课题申报、数据分析与AI绘图
随着人工智能技术的飞速发展,ChatGPT等先进语言模型正深刻改变着科研工作的面貌。从科研灵感的激发、论文的高效撰写,到课题的成功申报,乃至复杂数据的深度分析与可视化呈现,AI技术均展现出前所未有的潜力。其实众多科研前沿工作者…...

原子类、AtomicLong、AtomicReference、AtomicIntegerFieldUpdater、LongAdder
原子类 JDK提供的原子类,即Atomic*类有很多,大体可做如下分类: 形式类别举例Atomic*基本类型原子类AtomicInteger、AtomicLong、AtomicBooleanAtomic*Array数组类型原子类AtomicIntegerArray、AtomicLongArray、AtomicReferenceArrayAtomic…...

c语言——数组名该如何理解呢?
一般情况下,数组名表示首元素地址,以下2种除外: ①、sizeof(数组名) 表示整个数组 ※只有数组名的情况 sizeof(数组名i) 就不能表示整个数组 ②、&数组名 表示整个数组,取的是整个数…...

Linux学习笔记13 系统进程管理
前文 Linux学习笔记10 系统启动初始化,服务和进程管理(上)-CSDN博客 Linux学习笔记11 系统启动初始化,服务和进程管理(下)-CSDN博客 Linux学习笔记12 systemd的其他命令-CSDN博客 之前学习了怎么使用sy…...

Spring Boot 项目集成camunda流程引擎
Spring Boot 项目集成camunda流程引擎 camunda地址 camunda中文地址 使用camunda开源工作流引擎有:通过docker运行、使用springboot集成、部署camunda发行包、基于源代码编译运行等多种方式。 文本重点介绍如何在Spring Boot应用程序中如何集成Camunda Platform开…...
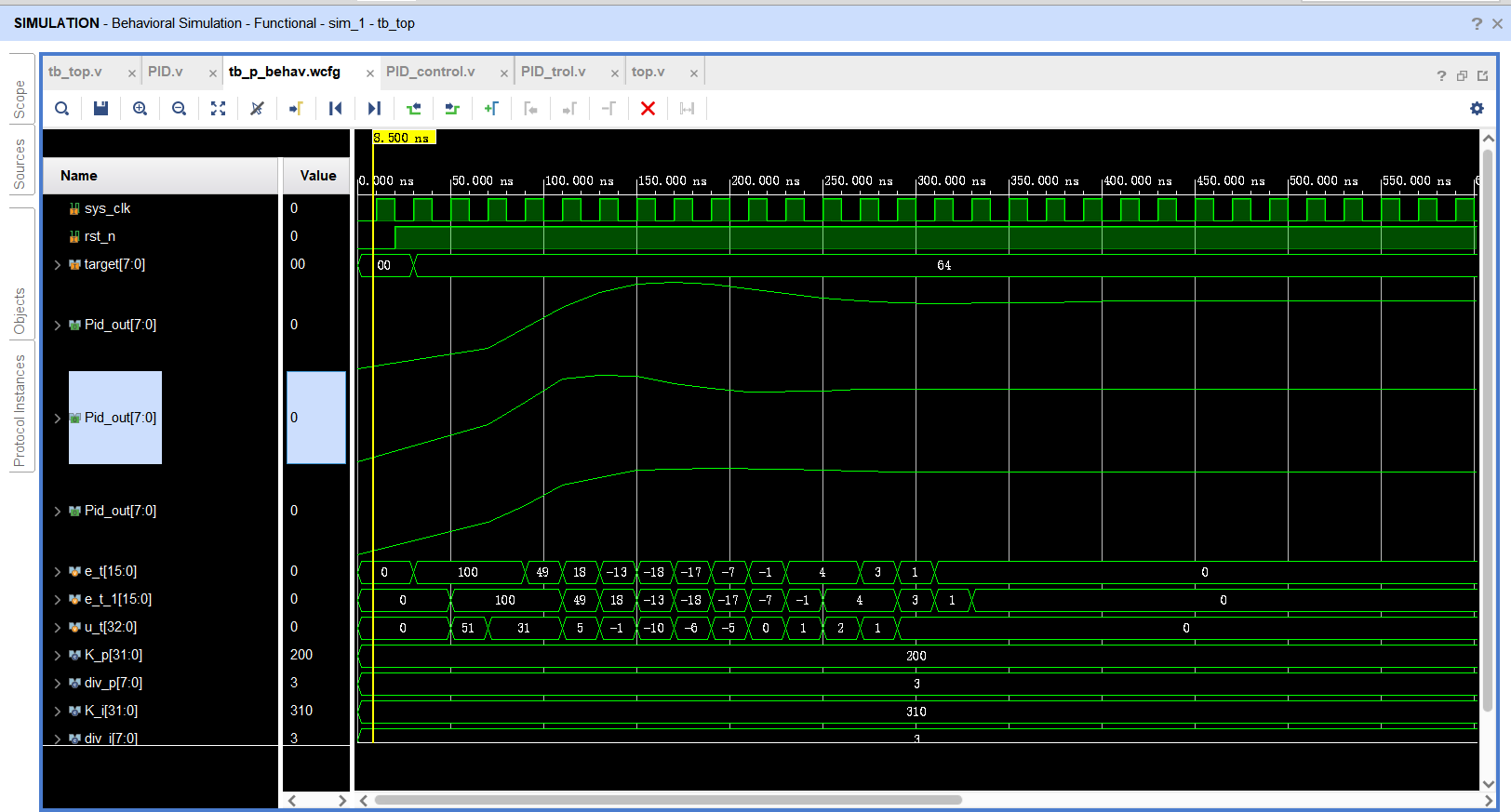
基于FPGA的PID算法学习———实现PID比例控制算法
基于FPGA的PID算法学习 前言一、PID算法分析二、PID仿真分析1. PID代码2.PI代码3.P代码4.顶层5.测试文件6.仿真波形 总结 前言 学习内容:参考网站: PID算法控制 PID即:Proportional(比例)、Integral(积分&…...

PHP和Node.js哪个更爽?
先说结论,rust完胜。 php:laravel,swoole,webman,最开始在苏宁的时候写了几年php,当时觉得php真的是世界上最好的语言,因为当初活在舒适圈里,不愿意跳出来,就好比当初活在…...
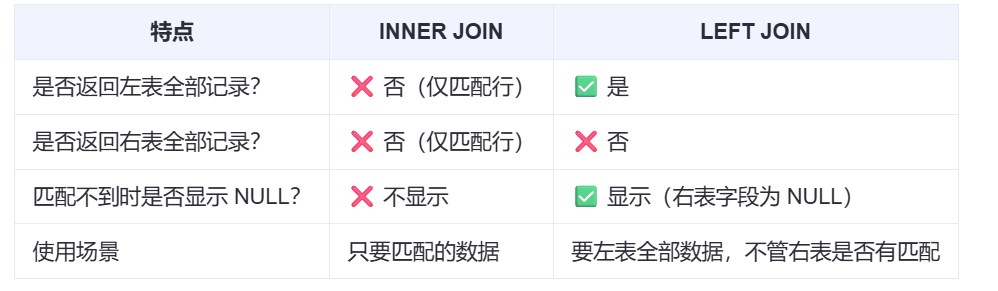
【SQL学习笔记1】增删改查+多表连接全解析(内附SQL免费在线练习工具)
可以使用Sqliteviz这个网站免费编写sql语句,它能够让用户直接在浏览器内练习SQL的语法,不需要安装任何软件。 链接如下: sqliteviz 注意: 在转写SQL语法时,关键字之间有一个特定的顺序,这个顺序会影响到…...

linux 错误码总结
1,错误码的概念与作用 在Linux系统中,错误码是系统调用或库函数在执行失败时返回的特定数值,用于指示具体的错误类型。这些错误码通过全局变量errno来存储和传递,errno由操作系统维护,保存最近一次发生的错误信息。值得注意的是,errno的值在每次系统调用或函数调用失败时…...
Cinnamon修改面板小工具图标
Cinnamon开始菜单-CSDN博客 设置模块都是做好的,比GNOME简单得多! 在 applet.js 里增加 const Settings imports.ui.settings;this.settings new Settings.AppletSettings(this, HTYMenusonichy, instance_id); this.settings.bind(menu-icon, menu…...
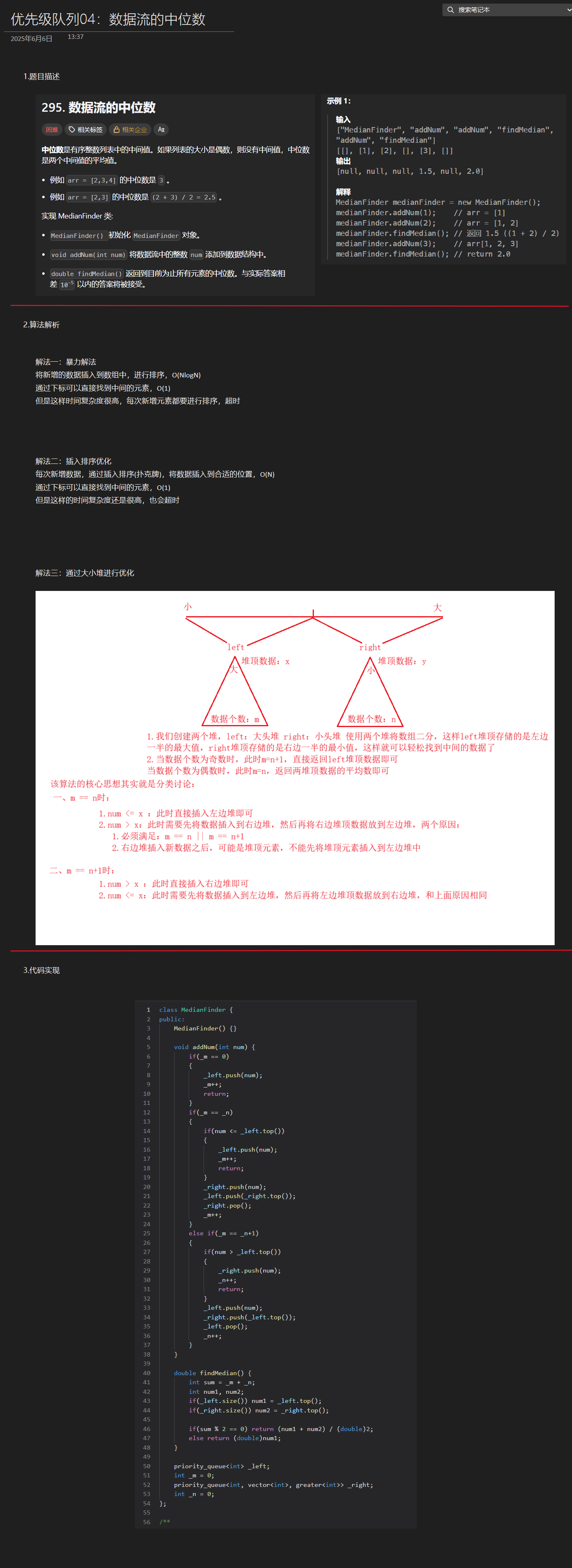
优选算法第十二讲:队列 + 宽搜 优先级队列
优选算法第十二讲:队列 宽搜 && 优先级队列 1.N叉树的层序遍历2.二叉树的锯齿型层序遍历3.二叉树最大宽度4.在每个树行中找最大值5.优先级队列 -- 最后一块石头的重量6.数据流中的第K大元素7.前K个高频单词8.数据流的中位数 1.N叉树的层序遍历 2.二叉树的锯…...
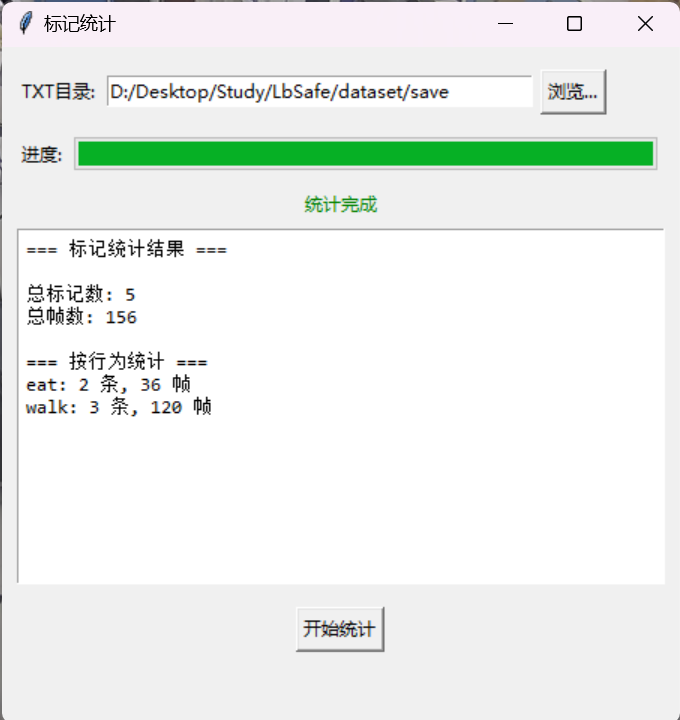
视频行为标注工具BehaviLabel(源码+使用介绍+Windows.Exe版本)
前言: 最近在做行为检测相关的模型,用的是时空图卷积网络(STGCN),但原有kinetic-400数据集数据质量较低,需要进行细粒度的标注,同时粗略搜了下已有开源工具基本都集中于图像分割这块,…...
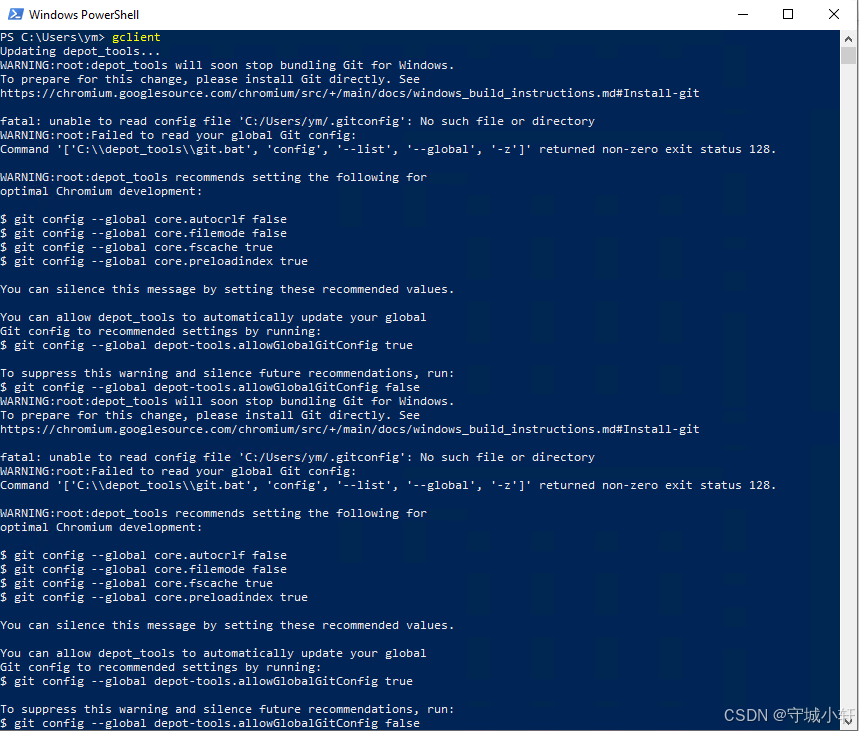
Chromium 136 编译指南 Windows篇:depot_tools 配置与源码获取(二)
引言 工欲善其事,必先利其器。在完成了 Visual Studio 2022 和 Windows SDK 的安装后,我们即将接触到 Chromium 开发生态中最核心的工具——depot_tools。这个由 Google 精心打造的工具集,就像是连接开发者与 Chromium 庞大代码库的智能桥梁…...

根目录0xa0属性对应的Ntfs!_SCB中的FileObject是什么时候被建立的----NTFS源代码分析--重要
根目录0xa0属性对应的Ntfs!_SCB中的FileObject是什么时候被建立的 第一部分: 0: kd> g Breakpoint 9 hit Ntfs!ReadIndexBuffer: f7173886 55 push ebp 0: kd> kc # 00 Ntfs!ReadIndexBuffer 01 Ntfs!FindFirstIndexEntry 02 Ntfs!NtfsUpda…...

十九、【用户管理与权限 - 篇一】后端基础:用户列表与角色模型的初步构建
【用户管理与权限 - 篇一】后端基础:用户列表与角色模型的初步构建 前言准备工作第一部分:回顾 Django 内置的 `User` 模型第二部分:设计并创建 `Role` 和 `UserProfile` 模型第三部分:创建 Serializers第四部分:创建 ViewSets第五部分:注册 API 路由第六部分:后端初步测…...
