ubuntu22.04 使用crash
文章目录
- 前言
- 一、apt 安装dbgsym vnlinux
- 二、使用.ddeb包安装dbgsym vnlinux
- 三、dbgsym发行版
- 四、crash调试
- 参考资料
前言
最近在适配 ubuntu系统,记录一下其crash的安装。
一、apt 安装dbgsym vnlinux
# echo "deb http://ddebs.ubuntu.com $(lsb_release -cs) main restricted universe multiversedeb http://ddebs.ubuntu.com $(lsb_release -cs)-updates main restricted universe multiversedeb http://ddebs.ubuntu.com $(lsb_release -cs)-proposed main restricted universe multiverse" | sudo tee -a /etc/apt/sources.list.d/ddebs.list
$ sudo apt install ubuntu-dbgsym-keyring
$ sudo apt-get update
# apt -y install linux-image-$(uname -r)-dbgsym
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
The following additional packages will be installed:linux-image-unsigned-5.15.0-122-generic-dbgsym
The following NEW packages will be installed:linux-image-5.15.0-122-generic-dbgsym linux-image-unsigned-5.15.0-122-generic-dbgsym
0 upgraded, 2 newly installed, 0 to remove and 42 not upgraded.
Need to get 1,061 MB of archives.
After this operation, 6,917 MB of additional disk space will be used.
Get:1 http://ddebs.ubuntu.com jammy-updates/main amd64 linux-image-unsigned-5.15.0-122-generic-dbgsym amd64 5.15.0-122.132 [1,061 MB]
二、使用.ddeb包安装dbgsym vnlinux
也可以直接在 http://ddebs.ubuntu.com/pool/main/l/linux/下载对应的.ddeb包:

dpkg -i linux-image-unsigned-5.15.0-122-generic-dbgsym_5.15.0-122.132_amd64.ddeb
三、dbgsym发行版
在http://ddebs.ubuntu.com/pool/main/l/linux/查看支持的dbgsym vmlinux:
| 发行版 | 内核版本 |
|---|---|
| 14.04 | 3.13.0 |
| 16.04 | 4.4.0 |
| 18.04 | 4.15.0 |
| 20.04 | 5.4.0 |
| 22.04 | 5.15.0 |
| 24.04 | 6.8.0 |
其他内核版本,请参考:http://ddebs.ubuntu.com/pool/main/l/
四、crash调试
# cat /etc/os-release
PRETTY_NAME="Ubuntu 22.04.1 LTS"
NAME="Ubuntu"
VERSION_ID="22.04"
VERSION="22.04.1 LTS (Jammy Jellyfish)"
VERSION_CODENAME=jammy
ID=ubuntu
ID_LIKE=debian
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
UBUNTU_CODENAME=jammy# uname -r
6.5.0-18-generic
我这里用ubuntu22.04 的6.5.0-18-generic内核调试为例:
/** 64-bit SYSCALL instruction entry. Up to 6 arguments in registers.** This is the only entry point used for 64-bit system calls. The* hardware interface is reasonably well designed and the register to* argument mapping Linux uses fits well with the registers that are* available when SYSCALL is used.** SYSCALL instructions can be found inlined in libc implementations as* well as some other programs and libraries. There are also a handful* of SYSCALL instructions in the vDSO used, for example, as a* clock_gettimeofday fallback.** 64-bit SYSCALL saves rip to rcx, clears rflags.RF, then saves rflags to r11,* then loads new ss, cs, and rip from previously programmed MSRs.* rflags gets masked by a value from another MSR (so CLD and CLAC* are not needed). SYSCALL does not save anything on the stack* and does not change rsp.** Registers on entry:* rax system call number* rcx return address* r11 saved rflags (note: r11 is callee-clobbered register in C ABI)* rdi arg0* rsi arg1* rdx arg2* r10 arg3 (needs to be moved to rcx to conform to C ABI)* r8 arg4* r9 arg5* (note: r12-r15, rbp, rbx are callee-preserved in C ABI)** Only called from user space.** When user can change pt_regs->foo always force IRET. That is because* it deals with uncanonical addresses better. SYSRET has trouble* with them due to bugs in both AMD and Intel CPUs.*/SYM_CODE_START(entry_SYSCALL_64)UNWIND_HINT_ENTRYENDBRswapgs/* tss.sp2 is scratch space. */movq %rsp, PER_CPU_VAR(cpu_tss_rw + TSS_sp2)SWITCH_TO_KERNEL_CR3 scratch_reg=%rspmovq PER_CPU_VAR(pcpu_hot + X86_top_of_stack), %rspSYM_INNER_LABEL(entry_SYSCALL_64_safe_stack, SYM_L_GLOBAL)ANNOTATE_NOENDBR/* Construct struct pt_regs on stack */pushq $__USER_DS /* pt_regs->ss */pushq PER_CPU_VAR(cpu_tss_rw + TSS_sp2) /* pt_regs->sp */pushq %r11 /* pt_regs->flags */pushq $__USER_CS /* pt_regs->cs */pushq %rcx /* pt_regs->ip */
SYM_INNER_LABEL(entry_SYSCALL_64_after_hwframe, SYM_L_GLOBAL)......
SYM_INNER_LABEL(entry_SYSCALL_64_after_hwframe, SYM_L_GLOBAL)pushq %rax /* pt_regs->orig_ax */PUSH_AND_CLEAR_REGS rax=$-ENOSYS/* IRQs are off. */movq %rsp, %rdi/* Sign extend the lower 32bit as syscall numbers are treated as int */movslq %eax, %rsi/* clobbers %rax, make sure it is after saving the syscall nr */IBRS_ENTERUNTRAIN_RETcall do_syscall_64 /* returns with IRQs disabled */......
看其vmlinux:
cat /boot/System.map-6.5.0-18-generic | grep entry_SYSCALL_64_after_hwframe
ffffffff82200078 T entry_SYSCALL_64_after_hwframe
ffffffff82200078: 50 push %rax
ffffffff82200079: 57 push %rdi
ffffffff8220007a: 56 push %rsi
ffffffff8220007b: 52 push %rdx
ffffffff8220007c: 51 push %rcx
ffffffff8220007d: 6a da push $0xffffffffffffffda
ffffffff8220007f: 41 50 push %r8
ffffffff82200081: 41 51 push %r9
ffffffff82200083: 41 52 push %r10
ffffffff82200085: 41 53 push %r11
ffffffff82200087: 53 push %rbx
ffffffff82200088: 55 push %rbp
ffffffff82200089: 41 54 push %r12
ffffffff8220008b: 41 55 push %r13
ffffffff8220008d: 41 56 push %r14
ffffffff8220008f: 41 57 push %r15
ffffffff82200091: 31 f6 xor %esi,%esi
ffffffff82200093: 31 d2 xor %edx,%edx
......
ffffffff822000d1: 90 nop
ffffffff822000d2: 90 nop
ffffffff822000d3: 90 nop
ffffffff822000d4: 90 nop
ffffffff822000d5: 90 nop
ffffffff822000d6: 90 nop
ffffffff822000d7: 90 nop
ffffffff822000d8: 90 nop
ffffffff822000d9: 90 nop
ffffffff822000da: 90 nop
ffffffff822000db: 90 nop
ffffffff822000dc: 90 nop
ffffffff822000dd: 90 nop
ffffffff822000de: 90 nop
ffffffff822000df: 90 nop
ffffffff822000e0: 90 nop
ffffffff822000e1: e8 9a 4a f1 ff call 0xffffffff82114b80
ffffffff822000e6: 90 nop
ffffffff822000e7: 90 nop
ffffffff822000e8: 90 nop
ffffffff822000e9: 90 nop
ffffffff822000ea: 90 nop
到了ffffffff822000d1处,全是 nop指令:
# cat /boot/System.map-6.5.0-18-generic | grep '\<do_syscall_64\>'
ffffffff82114b80 T do_syscall_64
而我看crash:
crash> dis entry_SYSCALL_64_after_hwframe
0xffffffff97400078 <entry_SYSCALL_64_after_hwframe>: push %rax
0xffffffff97400079 <entry_SYSCALL_64_after_hwframe+1>: push %rdi
0xffffffff9740007a <entry_SYSCALL_64_after_hwframe+2>: push %rsi
0xffffffff9740007b <entry_SYSCALL_64_after_hwframe+3>: push %rdx
0xffffffff9740007c <entry_SYSCALL_64_after_hwframe+4>: push %rcx
0xffffffff9740007d <entry_SYSCALL_64_after_hwframe+5>: push $0xffffffffffffffda
0xffffffff9740007f <entry_SYSCALL_64_after_hwframe+7>: push %r8
0xffffffff97400081 <entry_SYSCALL_64_after_hwframe+9>: push %r9
0xffffffff97400083 <entry_SYSCALL_64_after_hwframe+11>: push %r10
0xffffffff97400085 <entry_SYSCALL_64_after_hwframe+13>: push %r11
0xffffffff97400087 <entry_SYSCALL_64_after_hwframe+15>: push %rbx
0xffffffff97400088 <entry_SYSCALL_64_after_hwframe+16>: push %rbp
0xffffffff97400089 <entry_SYSCALL_64_after_hwframe+17>: push %r12
0xffffffff9740008b <entry_SYSCALL_64_after_hwframe+19>: push %r13
0xffffffff9740008d <entry_SYSCALL_64_after_hwframe+21>: push %r14
0xffffffff9740008f <entry_SYSCALL_64_after_hwframe+23>: push %r15
0xffffffff97400091 <entry_SYSCALL_64_after_hwframe+25>: xor %esi,%esi
0xffffffff97400093 <entry_SYSCALL_64_after_hwframe+27>: xor %edx,%edx
0xffffffff97400095 <entry_SYSCALL_64_after_hwframe+29>: xor %ecx,%ecx
0xffffffff97400097 <entry_SYSCALL_64_after_hwframe+31>: xor %r8d,%r8d
0xffffffff9740009a <entry_SYSCALL_64_after_hwframe+34>: xor %r9d,%r9d
0xffffffff9740009d <entry_SYSCALL_64_after_hwframe+37>: xor %r10d,%r10d
0xffffffff974000a0 <entry_SYSCALL_64_after_hwframe+40>: xor %r11d,%r11d
0xffffffff974000a3 <entry_SYSCALL_64_after_hwframe+43>: xor %ebx,%ebx
0xffffffff974000a5 <entry_SYSCALL_64_after_hwframe+45>: xor %ebp,%ebp
0xffffffff974000a7 <entry_SYSCALL_64_after_hwframe+47>: xor %r12d,%r12d
0xffffffff974000aa <entry_SYSCALL_64_after_hwframe+50>: xor %r13d,%r13d
0xffffffff974000ad <entry_SYSCALL_64_after_hwframe+53>: xor %r14d,%r14d
0xffffffff974000b0 <entry_SYSCALL_64_after_hwframe+56>: xor %r15d,%r15d
0xffffffff974000b3 <entry_SYSCALL_64_after_hwframe+59>: mov %rsp,%rdi
0xffffffff974000b6 <entry_SYSCALL_64_after_hwframe+62>: movslq %eax,%rsi
0xffffffff974000b9 <entry_SYSCALL_64_after_hwframe+65>: xchg %ax,%ax
0xffffffff974000bb <entry_SYSCALL_64_after_hwframe+67>: mov $0x48,%ecx
0xffffffff974000c0 <entry_SYSCALL_64_after_hwframe+72>: mov %gs:0x1fbd0,%rdx
0xffffffff974000c9 <entry_SYSCALL_64_after_hwframe+81>: mov %edx,%eax
0xffffffff974000cb <entry_SYSCALL_64_after_hwframe+83>: shr $0x20,%rdx
0xffffffff974000cf <entry_SYSCALL_64_after_hwframe+87>: wrmsr
0xffffffff974000d1 <entry_SYSCALL_64_after_hwframe+89>: jmp 0xffffffff974000e1 <entry_SYSCALL_64_after_hwframe+105>
0xffffffff974000d3 <entry_SYSCALL_64_after_hwframe+91>: int3
0xffffffff974000d4 <entry_SYSCALL_64_after_hwframe+92>: int3
0xffffffff974000d5 <entry_SYSCALL_64_after_hwframe+93>: int3
0xffffffff974000d6 <entry_SYSCALL_64_after_hwframe+94>: int3
0xffffffff974000d7 <entry_SYSCALL_64_after_hwframe+95>: int3
0xffffffff974000d8 <entry_SYSCALL_64_after_hwframe+96>: int3
0xffffffff974000d9 <entry_SYSCALL_64_after_hwframe+97>: int3
0xffffffff974000da <entry_SYSCALL_64_after_hwframe+98>: int3
0xffffffff974000db <entry_SYSCALL_64_after_hwframe+99>: int3
0xffffffff974000dc <entry_SYSCALL_64_after_hwframe+100>: int3
0xffffffff974000dd <entry_SYSCALL_64_after_hwframe+101>: int3
0xffffffff974000de <entry_SYSCALL_64_after_hwframe+102>: int3
0xffffffff974000df <entry_SYSCALL_64_after_hwframe+103>: int3
0xffffffff974000e0 <entry_SYSCALL_64_after_hwframe+104>: int3
0xffffffff974000e1 <entry_SYSCALL_64_after_hwframe+105>: call 0xffffffff97314b80 <do_syscall_64>
在0xffffffff974000d1处nop指令变成了jmp:
0xffffffff974000d1 <entry_SYSCALL_64_after_hwframe+89>: jmp 0xffffffff974000e1 <entry_SYSCALL_64_after_hwframe+105>
......
0xffffffff974000e1 <entry_SYSCALL_64_after_hwframe+105>: call 0xffffffff97314b80 <do_syscall_64>
与UNTRAIN_RET指令有关。
(2)
/** Save all registers in pt_regs. Return GSBASE related information* in EBX depending on the availability of the FSGSBASE instructions:** FSGSBASE R/EBX* N 0 -> SWAPGS on exit* 1 -> no SWAPGS on exit** Y GSBASE value at entry, must be restored in paranoid_exit** R14 - old CR3* R15 - old SPEC_CTRL*/
SYM_CODE_START(paranoid_entry)ANNOTATE_NOENDBRUNWIND_HINT_FUNCPUSH_AND_CLEAR_REGS save_ret=1ENCODE_FRAME_POINTER 8/** Always stash CR3 in %r14. This value will be restored,* verbatim, at exit. Needed if paranoid_entry interrupted* another entry that already switched to the user CR3 value* but has not yet returned to userspace.** This is also why CS (stashed in the "iret frame" by the* hardware at entry) can not be used: this may be a return* to kernel code, but with a user CR3 value.** Switching CR3 does not depend on kernel GSBASE so it can* be done before switching to the kernel GSBASE. This is* required for FSGSBASE because the kernel GSBASE has to* be retrieved from a kernel internal table.*/SAVE_AND_SWITCH_TO_KERNEL_CR3 scratch_reg=%rax save_reg=%r14/** Handling GSBASE depends on the availability of FSGSBASE.** Without FSGSBASE the kernel enforces that negative GSBASE* values indicate kernel GSBASE. With FSGSBASE no assumptions* can be made about the GSBASE value when entering from user* space.*/ALTERNATIVE "jmp .Lparanoid_entry_checkgs", "", X86_FEATURE_FSGSBASE/** Read the current GSBASE and store it in %rbx unconditionally,* retrieve and set the current CPUs kernel GSBASE. The stored value* has to be restored in paranoid_exit unconditionally.** The unconditional write to GS base below ensures that no subsequent* loads based on a mispredicted GS base can happen, therefore no LFENCE* is needed here.*/SAVE_AND_SET_GSBASE scratch_reg=%rax save_reg=%rbxjmp .Lparanoid_gsbase_done.Lparanoid_entry_checkgs:/* EBX = 1 -> kernel GSBASE active, no restore required */movl $1, %ebx/** The kernel-enforced convention is a negative GSBASE indicates* a kernel value. No SWAPGS needed on entry and exit.*/movl $MSR_GS_BASE, %ecxrdmsrtestl %edx, %edxjs .Lparanoid_kernel_gsbase/* EBX = 0 -> SWAPGS required on exit */xorl %ebx, %ebxswapgs
.Lparanoid_kernel_gsbase:FENCE_SWAPGS_KERNEL_ENTRY
.Lparanoid_gsbase_done:/** Once we have CR3 and %GS setup save and set SPEC_CTRL. Just like* CR3 above, keep the old value in a callee saved register.*/IBRS_ENTER save_reg=%r15UNTRAIN_RET_FROM_CALLRET
SYM_CODE_END(paranoid_entry)
查看vmlinux:
# cat /boot/System.map-6.5.0-18-generic | grep '\<paranoid_entry\>'
ffffffff822013b0 T paranoid_entry
ffffffff822013b0: 56 push %rsi
ffffffff822013b1: 48 8b 74 24 08 mov 0x8(%rsp),%rsi
ffffffff822013b6: 48 89 7c 24 08 mov %rdi,0x8(%rsp)
ffffffff822013bb: 52 push %rdx
ffffffff822013bc: 51 push %rcx
ffffffff822013bd: 50 push %rax
ffffffff822013be: 41 50 push %r8
ffffffff822013c0: 41 51 push %r9
ffffffff822013c2: 41 52 push %r10
ffffffff822013c4: 41 53 push %r11
ffffffff822013c6: 53 push %rbx
ffffffff822013c7: 55 push %rbp
ffffffff822013c8: 41 54 push %r12
ffffffff822013ca: 41 55 push %r13
ffffffff822013cc: 41 56 push %r14
ffffffff822013ce: 41 57 push %r15
ffffffff822013d0: 56 push %rsi
ffffffff822013d1: 31 f6 xor %esi,%esi
ffffffff822013d3: 31 d2 xor %edx,%edx
......
ffffffff82201484: 90 nop
ffffffff82201485: 90 nop
ffffffff82201486: 90 nop
ffffffff82201487: 90 nop
ffffffff82201488: 90 nop
ffffffff82201489: 90 nop
ffffffff8220148a: 90 nop
ffffffff8220148b: 90 nop
ffffffff8220148c: 90 nop
ffffffff8220148d: 90 nop
ffffffff8220148e: 90 nop
ffffffff8220148f: 90 nop
ffffffff82201490: 90 nop
ffffffff82201491: 90 nop
ffffffff82201492: 90 nop
到了ffffffff82201484处都是nop指令。
crash查看:
crash> dis paranoid_entry
0xffffffff974013b0 <paranoid_entry>: push %rsi
0xffffffff974013b1 <paranoid_entry+1>: mov 0x8(%rsp),%rsi
0xffffffff974013b6 <paranoid_entry+6>: mov %rdi,0x8(%rsp)
0xffffffff974013bb <paranoid_entry+11>: push %rdx
0xffffffff974013bc <paranoid_entry+12>: push %rcx
0xffffffff974013bd <paranoid_entry+13>: push %rax
0xffffffff974013be <paranoid_entry+14>: push %r8
0xffffffff974013c0 <paranoid_entry+16>: push %r9
0xffffffff974013c2 <paranoid_entry+18>: push %r10
0xffffffff974013c4 <paranoid_entry+20>: push %r11
0xffffffff974013c6 <paranoid_entry+22>: push %rbx
0xffffffff974013c7 <paranoid_entry+23>: push %rbp
0xffffffff974013c8 <paranoid_entry+24>: push %r12
0xffffffff974013ca <paranoid_entry+26>: push %r13
0xffffffff974013cc <paranoid_entry+28>: push %r14
0xffffffff974013ce <paranoid_entry+30>: push %r15
0xffffffff974013d0 <paranoid_entry+32>: push %rsi
0xffffffff974013d1 <paranoid_entry+33>: xor %esi,%esi
0xffffffff974013d3 <paranoid_entry+35>: xor %edx,%edx
......
0xffffffff97401484 <paranoid_entry+212>: jmp 0xffffffff97401493 <paranoid_entry+227>
0xffffffff97401486 <paranoid_entry+214>: int3
0xffffffff97401487 <paranoid_entry+215>: int3
0xffffffff97401488 <paranoid_entry+216>: int3
0xffffffff97401489 <paranoid_entry+217>: int3
0xffffffff9740148a <paranoid_entry+218>: int3
0xffffffff9740148b <paranoid_entry+219>: int3
0xffffffff9740148c <paranoid_entry+220>: int3
0xffffffff9740148d <paranoid_entry+221>: int3
0xffffffff9740148e <paranoid_entry+222>: int3
0xffffffff9740148f <paranoid_entry+223>: int3
0xffffffff97401490 <paranoid_entry+224>: int3
0xffffffff97401491 <paranoid_entry+225>: int3
0xffffffff97401492 <paranoid_entry+226>: int3
0xffffffff97401493 <paranoid_entry+227>: ret
0xffffffff97401494 <paranoid_entry+228>: int3
0xffffffff97401495 <paranoid_entry+229>: int3
0xffffffff97401496 <paranoid_entry+230>: int3
0xffffffff97401497 <paranoid_entry+231>: int3
到了0xffffffff97401484:
0xffffffff97401484 <paranoid_entry+212>: jmp 0xffffffff97401493 <paranoid_entry+227>
0xffffffff97401493 <paranoid_entry+227>: ret
也是nop指令变成了jmp指令。
这与UNTRAIN_RET_FROM_CALL指令有关。
参考资料
https://ebpf.top/post/ubuntu_kdump_crash/
相关文章:

ubuntu22.04 使用crash
文章目录 前言一、apt 安装dbgsym vnlinux二、使用.ddeb包安装dbgsym vnlinux三、dbgsym发行版四、crash调试参考资料 前言 最近在适配 ubuntu系统,记录一下其crash的安装。 一、apt 安装dbgsym vnlinux # echo "deb http://ddebs.ubuntu.com $(lsb_release…...

Linux高性能服务器编程 | 读书笔记 |9.定时器
9. 定时器 网络程序需要处理定时事件,如定期检测一个客户连接的活动状态。服务器程序通常管理着众多定时事件,有效地组织这些定时事件,使其在预期的时间被触发且不影响服务器的主要逻辑,对于服务器的性能有至关重要的影响。为此&…...

OSG开发笔记(三十九):OSG中模型的透明度实现、球体透明度Demo
若该文为原创文章,未经允许不得转载 本文章博客地址:https://blog.csdn.net/qq21497936/article/details/144424531 各位读者,知识无穷而人力有穷,要么改需求,要么找专业人士,要么自己研究 长沙红胖子Qt…...

phpSpider如何处理网页内容的动态加载问题
phpSpider处理网页内容的动态加载问题,主要采取以下几种策略: 一、分析并直接请求API 现代网站中,很多动态加载的内容是通过后端的API接口以JSON或XML等格式返回的。phpSpider可以通过分析网页的请求,找到这些API接口的URL&…...

【Go】-倒排索引的简单实现
目录 什么是倒排索引 定义 基本结构和原理 分词在倒排索引中的重要性 简单倒排索引的实现 接口定义 简单数据库的实现 倒排索引 正排索引 测试 总结 什么是倒排索引 定义 倒排索引(Inverted Index)是一种索引数据结构,它是文档检…...

Python:基于PyCharm的简单程序创建及运行-HelloWorld
1. 新建项目 2. 设置文件位置,并创建项目 文件位置由“目录项目名称”组成,如:D:\PycharmProjects\HelloWorld,“HelloWorld”则是项目名称。 3. 创建Python文件 4. 定义文件名称,如HelloWorld。双击【Python 文件】完…...

设置HP条UI
概述 设置常见的生命值条, 实现过程 设置UI/image作为形状 设置UI/Image作为背景 设置UI/image(healthfill)作为填充图片,层数低于背景 设置heathfill的imagetype为filled fillmethod为horizontal [SerializeField] private Im…...

开源分布式系统追踪-03-CNCF jaeger-02-快速开始
分布式跟踪系列 CAT cat monitor 分布式监控 CAT-是什么? cat monitor-02-分布式监控 CAT埋点 cat monitor-03-深度剖析开源分布式监控CAT cat monitor-04-cat 服务端部署实战 cat monitor-05-cat 客户端集成实战 cat monitor-06-cat 消息存储 skywalking …...

手机实时提取SIM卡打电话的信令声音--社会价值(一、方案解决了什么问题)
手机实时提取SIM卡打电话的信令声音 --社会价值(一、方案解决了什么问题) 一、前言 这段时间,我们在技术范围之外陷入了一个自证或者说下定义的怪圈,即要怎么样去介绍或者描述:我们是一个什么样的产品。它在当前这个世界上,处于…...

FFmpeg功能使用
步骤:1,安装FFmpeg Download FFmpeg 在这里点击->Windows builds from gyan.dev;如下图 会跳到另外的下载界面: 在里面下拉选择点击ffmpeg-7.1-essentials_build.zip: 即可下载到FFmpeg; 使用&#…...

Windows安装WSL子系统及docker,以及WSL和docker配置、使用及问题解决
在Windows操作系统中,Ubuntu子系统(也称为Windows Subsystem for Linux, WSL)为开发者提供了一个在Windows环境下运行Linux环境的平台。然而,有时用户在按照Ubuntu子系统或者使用WSL时,可能会遇到各种问题,下面总结一下解决方式。 想要在Windows上安装Docker(实际上是基…...

飞牛 fnos docker镜像部署OpenSpeedtest宽带网速测试教程
penSpeedTest是一个跨平台的网络测速应用,支持不同操作系统的浏览器,无需安装额外软件或插件。您可以在iPhone、iPad、Android设备、Windows和Linux系统的电脑、手机和平板上直接测试设备与NAS之间的宽带速度。 通过这个可以排查出设备与NAS之间的传输速…...

【kubernetes】资源管理方式
目录 1. 说明2. 命令式对象管理3. 命令式对象配置4. 声明式对象配置5. 三种方式的对比 1. 说明 1.在Kubernetes(k8s)中,资源管理是一个核心功能,它允许用户通过操作资源来管理Kubernetes集群。2.Kubernetes将所有的内容都抽象为资…...

chromedriver可运行的docker环境
以常见的linux x86服务器为例 chrome driver 官网:https://googlechromelabs.github.io/chrome-for-testing/ 下载chrome linux64位:https://storage.googleapis.com/chrome-for-testing-public/131.0.6778.85/xxx 下载chrome driver linux64位&#x…...

【YashanDB知识库】如何将mysql含有group by的SQL转换成崖山支持的SQL
本文内容来自YashanDB官网,原文内容请见 https://www.yashandb.com/newsinfo/7610112.html?templateId1718516 问题现象 以下SQL在MYSQL下均能执行成功,在崖山下执行报错。 SELECT Sname,Ssex, min(Sage) FROM Student group by Ssex;SELECT Sname,c…...

希迪智驾持续亏损8.2亿:毛利率下滑,冲刺“自动驾驶矿卡第一股”
《港湾商业观察》黄懿 近日,希迪智驾(湖南)股份有限公司(下称“希迪智驾”)向港交所主板递交上市申请,联席保荐人为中金公司、中信建投国际、中国平安资本(香港)。 资料显示&#…...
部署GitLab服务器
文章目录 环境准备GitLab部署GitLab服务器GitLab中主要的概念客户端上传代码到gitlab服务器CI-CD概述软件程序上线流程安装Jenkins服务器 配置jenkins软件版本管理配置jenkins访问gitlab远程仓库下载到子目录部署代码到web服务器自动化部署流程 配置共享服务器配置jenkins把git…...

利用cnocr库完成中文扫描pdf文件的文字识别
很多pdf文件文字识别软件都会收费,免费的网页版可能会带来信息泄露,还有一些类似于腾讯AI和百度AI的接口都有调用次数限制,因此,利用识别正确率极高且免费的cnocr库来自己动手做个pdf文件文字识别程序就是一个很不错的选择。以下程…...

pythonselenium自动化初始配置
基础配置 更新pip: 在Terminal中使用命令‘python -m pip install --upgrade pip’就可以安装pip最新版本。 python -m pip install --upgrade pip -i https://pypi.tuna.tsinghua.edu.cn/simple 常用的镜像源: 清华: https://pypi.tuna.tsinghua.edu.cn/simpl…...

【C++】数的性质问题分析与优化
博客主页: [小ᶻ☡꙳ᵃⁱᵍᶜ꙳] 本文专栏: C 文章目录 💯前言💯题目解析与分析题目描述题目分析 💯我的解法与详细解读初始代码实现解法分析 💯老师解法与其改进思路老师代码实现改进与优势 💯对比分析…...
)
浏览器访问 AWS ECS 上部署的 Docker 容器(监听 80 端口)
✅ 一、ECS 服务配置 Dockerfile 确保监听 80 端口 EXPOSE 80 CMD ["nginx", "-g", "daemon off;"]或 EXPOSE 80 CMD ["python3", "-m", "http.server", "80"]任务定义(Task Definition&…...

高频面试之3Zookeeper
高频面试之3Zookeeper 文章目录 高频面试之3Zookeeper3.1 常用命令3.2 选举机制3.3 Zookeeper符合法则中哪两个?3.4 Zookeeper脑裂3.5 Zookeeper用来干嘛了 3.1 常用命令 ls、get、create、delete、deleteall3.2 选举机制 半数机制(过半机制࿰…...

连锁超市冷库节能解决方案:如何实现超市降本增效
在连锁超市冷库运营中,高能耗、设备损耗快、人工管理低效等问题长期困扰企业。御控冷库节能解决方案通过智能控制化霜、按需化霜、实时监控、故障诊断、自动预警、远程控制开关六大核心技术,实现年省电费15%-60%,且不改动原有装备、安装快捷、…...

工程地质软件市场:发展现状、趋势与策略建议
一、引言 在工程建设领域,准确把握地质条件是确保项目顺利推进和安全运营的关键。工程地质软件作为处理、分析、模拟和展示工程地质数据的重要工具,正发挥着日益重要的作用。它凭借强大的数据处理能力、三维建模功能、空间分析工具和可视化展示手段&…...
指令的指南)
在Ubuntu中设置开机自动运行(sudo)指令的指南
在Ubuntu系统中,有时需要在系统启动时自动执行某些命令,特别是需要 sudo权限的指令。为了实现这一功能,可以使用多种方法,包括编写Systemd服务、配置 rc.local文件或使用 cron任务计划。本文将详细介绍这些方法,并提供…...
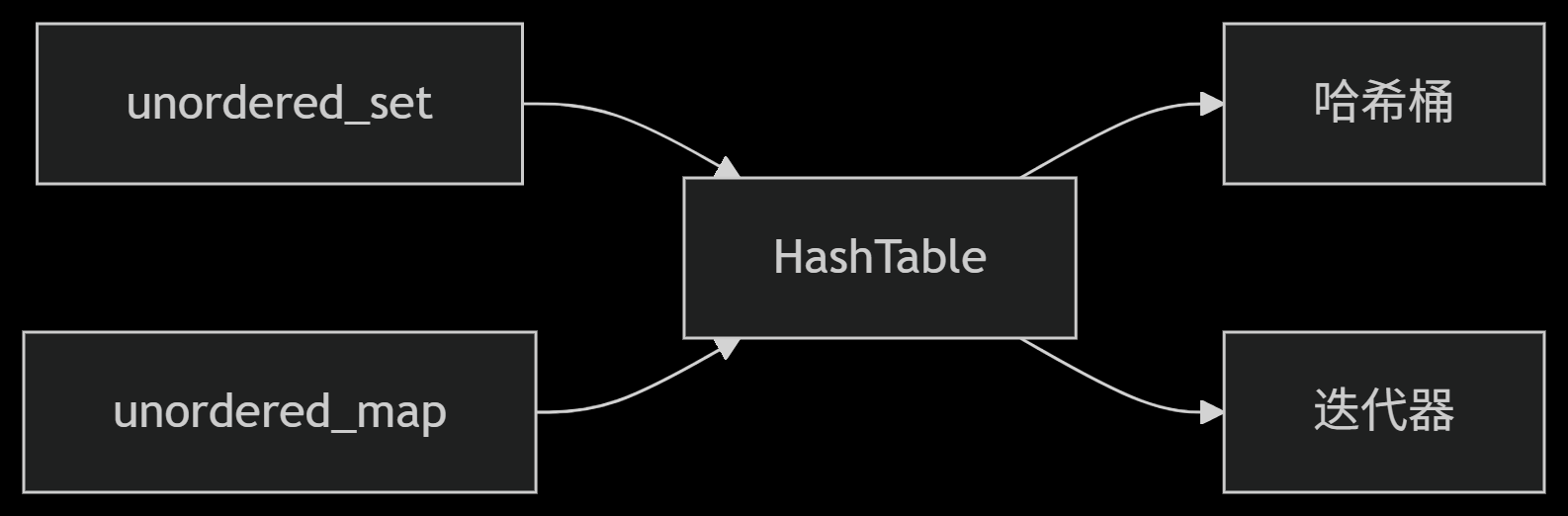
从零实现STL哈希容器:unordered_map/unordered_set封装详解
本篇文章是对C学习的STL哈希容器自主实现部分的学习分享 希望也能为你带来些帮助~ 那咱们废话不多说,直接开始吧! 一、源码结构分析 1. SGISTL30实现剖析 // hash_set核心结构 template <class Value, class HashFcn, ...> class hash_set {ty…...

Java 二维码
Java 二维码 **技术:**谷歌 ZXing 实现 首先添加依赖 <!-- 二维码依赖 --><dependency><groupId>com.google.zxing</groupId><artifactId>core</artifactId><version>3.5.1</version></dependency><de…...
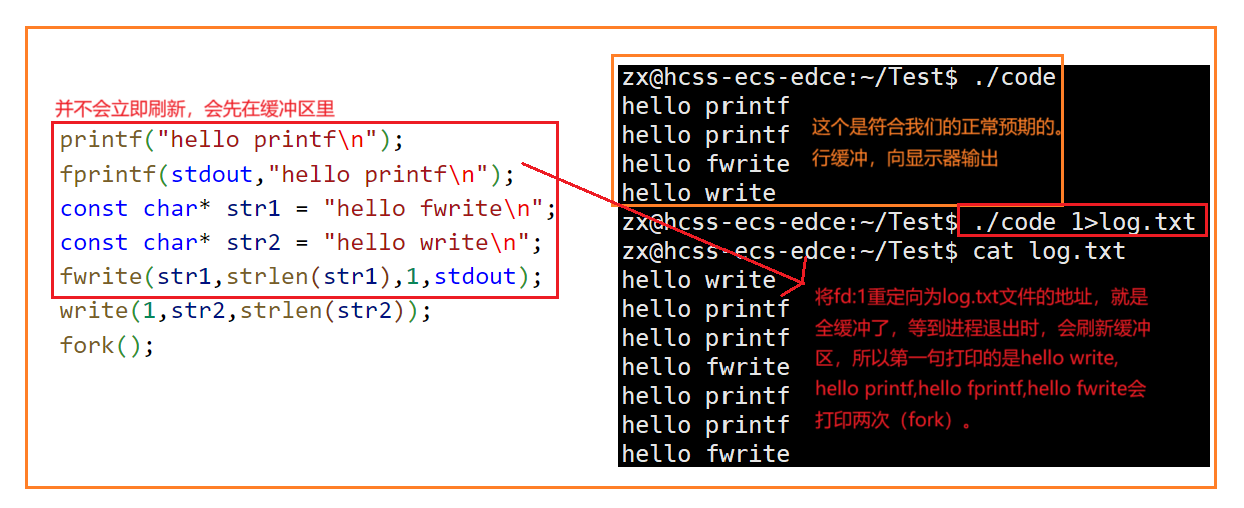
Linux中《基础IO》详细介绍
目录 理解"文件"狭义理解广义理解文件操作的归类认知系统角度文件类别 回顾C文件接口打开文件写文件读文件稍作修改,实现简单cat命令 输出信息到显示器,你有哪些方法stdin & stdout & stderr打开文件的方式 系统⽂件I/O⼀种传递标志位…...
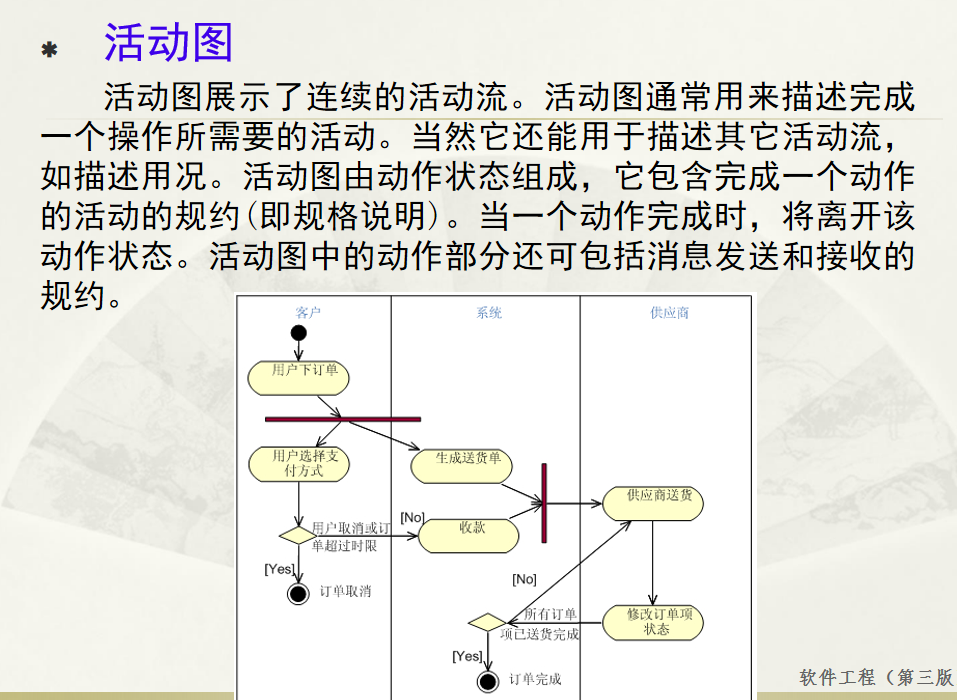
软件工程 期末复习
瀑布模型:计划 螺旋模型:风险低 原型模型: 用户反馈 喷泉模型:代码复用 高内聚 低耦合:模块内部功能紧密 模块之间依赖程度小 高内聚:指的是一个模块内部的功能应该紧密相关。换句话说,一个模块应当只实现单一的功能…...

Spring Boot + MyBatis 集成支付宝支付流程
Spring Boot MyBatis 集成支付宝支付流程 核心流程 商户系统生成订单调用支付宝创建预支付订单用户跳转支付宝完成支付支付宝异步通知支付结果商户处理支付结果更新订单状态支付宝同步跳转回商户页面 代码实现示例(电脑网站支付) 1. 添加依赖 <!…...
