Linux firewalld 常用命令
本文参考RedHat官网文章How to configure a firewall on Linux with firewalld。
Firewalld 是守护进程名,对应命令为firewall-cmd。帮助详见以下命令:
$ firewall-cmd --helpUsage: firewall-cmd [OPTIONS...]General Options-h, --help Prints a short help text and exits-V, --version Print the version string of firewalld-q, --quiet Do not print status messagesStatus Options--state Return and print firewalld state--reload Reload firewall and keep state information--complete-reload Reload firewall and lose state information--runtime-to-permanentCreate permanent from runtime configuration--reset-to-defaultsReset configuration to firewalld's default configuration--check-config Check permanent configuration for errorsLog Denied Options--get-log-denied Print the log denied value--set-log-denied=<value>Set log denied valuePermanent Options--permanent Set an option permanentlyUsable for options marked with [P]Zone Options--get-default-zone Print default zone for connections and interfaces--set-default-zone=<zone>Set default zone--get-active-zones Print currently active zones--get-zones Print predefined zones [P]--get-services Print predefined services [P]--get-icmptypes Print predefined icmptypes [P]--get-zone-of-interface=<interface>Print name of the zone the interface is bound to [P]--get-zone-of-source=<source>[/<mask>]|<MAC>|ipset:<ipset>Print name of the zone the source is bound to [P]--list-all-zones List everything added for or enabled in all zones [P]--new-zone=<zone> Add a new zone [P only]--new-zone-from-file=<filename> [--name=<zone>]Add a new zone from file with optional name [P only]--delete-zone=<zone> Delete an existing zone [P only]--load-zone-defaults=<zone>Load zone default settings [P only]--zone=<zone> Use this zone to set or query options, else default zoneUsable for options marked with [Z]--info-zone=<zone> Print information about a zone--path-zone=<zone> Print file path of a zone [P only]Policy Options--get-policies Print predefined policies--get-active-policiesPrint currently active policies--list-all-policies List everything added for or enabled in all policies--new-policy=<policy>Add a new empty policy--new-policy-from-file=<filename> [--name=<policy>]Add a new policy from file with optional name override [P only]--delete-policy=<policy>Delete an existing policy--load-policy-defaults=<policy>Load policy default settings--policy=<policy> Use this policy to set or query optionsUsable for options marked with [O]--info-policy=<policy>Print information about a policy--path-policy=<policy>Print file path of a policyIPSet Options--get-ipset-types Print the supported ipset types--new-ipset=<ipset> --type=<ipset type> [--option=<key>[=<value>]]..Add a new ipset [P only]--new-ipset-from-file=<filename> [--name=<ipset>]Add a new ipset from file with optional name [P only]--delete-ipset=<ipset>Delete an existing ipset [P only]--load-ipset-defaults=<ipset>Load ipset default settings [P only]--info-ipset=<ipset> Print information about an ipset--path-ipset=<ipset> Print file path of an ipset [P only]--get-ipsets Print predefined ipsets--ipset=<ipset> --set-description=<description>Set new description to ipset [P only]--ipset=<ipset> --get-descriptionPrint description for ipset [P only]--ipset=<ipset> --set-short=<description>Set new short description to ipset [P only]--ipset=<ipset> --get-shortPrint short description for ipset [P only]--ipset=<ipset> --add-entry=<entry>Add a new entry to an ipset [P]--ipset=<ipset> --remove-entry=<entry>Remove an entry from an ipset [P]--ipset=<ipset> --query-entry=<entry>Return whether ipset has an entry [P]--ipset=<ipset> --get-entriesList entries of an ipset [P]--ipset=<ipset> --add-entries-from-file=<entry>Add a new entries to an ipset [P]--ipset=<ipset> --remove-entries-from-file=<entry>Remove entries from an ipset [P]IcmpType Options--new-icmptype=<icmptype>Add a new icmptype [P only]--new-icmptype-from-file=<filename> [--name=<icmptype>]Add a new icmptype from file with optional name [P only]--delete-icmptype=<icmptype>Delete an existing icmptype [P only]--load-icmptype-defaults=<icmptype>Load icmptype default settings [P only]--info-icmptype=<icmptype>Print information about an icmptype--path-icmptype=<icmptype>Print file path of an icmptype [P only]--icmptype=<icmptype> --set-description=<description>Set new description to icmptype [P only]--icmptype=<icmptype> --get-descriptionPrint description for icmptype [P only]--icmptype=<icmptype> --set-short=<description>Set new short description to icmptype [P only]--icmptype=<icmptype> --get-shortPrint short description for icmptype [P only]--icmptype=<icmptype> --add-destination=<ipv>Enable destination for ipv in icmptype [P only]--icmptype=<icmptype> --remove-destination=<ipv>Disable destination for ipv in icmptype [P only]--icmptype=<icmptype> --query-destination=<ipv>Return whether destination ipv is enabled in icmptype [P only]--icmptype=<icmptype> --get-destinationsList destinations in icmptype [P only]Service Options--new-service=<service>Add a new service [P only]--new-service-from-file=<filename> [--name=<service>]Add a new service from file with optional name [P only]--delete-service=<service>Delete an existing service [P only]--load-service-defaults=<service>Load icmptype default settings [P only]--info-service=<service>Print information about a service--path-service=<service>Print file path of a service [P only]--service=<service> --set-description=<description>Set new description to service [P only]--service=<service> --get-descriptionPrint description for service [P only]--service=<service> --set-short=<description>Set new short description to service [P only]--service=<service> --get-shortPrint short description for service [P only]--service=<service> --add-port=<portid>[-<portid>]/<protocol>Add a new port to service [P only]--service=<service> --remove-port=<portid>[-<portid>]/<protocol>Remove a port from service [P only]--service=<service> --query-port=<portid>[-<portid>]/<protocol>Return whether the port has been added for service [P only]--service=<service> --get-portsList ports of service [P only]--service=<service> --add-protocol=<protocol>Add a new protocol to service [P only]--service=<service> --remove-protocol=<protocol>Remove a protocol from service [P only]--service=<service> --query-protocol=<protocol>Return whether the protocol has been added for service [P only]--service=<service> --get-protocolsList protocols of service [P only]--service=<service> --add-source-port=<portid>[-<portid>]/<protocol>Add a new source port to service [P only]--service=<service> --remove-source-port=<portid>[-<portid>]/<protocol>Remove a source port from service [P only]--service=<service> --query-source-port=<portid>[-<portid>]/<protocol>Return whether the source port has been added for service [P only]--service=<service> --get-source-portsList source ports of service [P only]--service=<service> --add-helper=<helper>Add a new helper to service [P only]--service=<service> --remove-helper=<helper>Remove a helper from service [P only]--service=<service> --query-helper=<helper>Return whether the helper has been added for service [P only]--service=<service> --get-service-helpersList helpers of service [P only]--service=<service> --set-destination=<ipv>:<address>[/<mask>]Set destination for ipv to address in service [P only]--service=<service> --remove-destination=<ipv>Disable destination for ipv i service [P only]--service=<service> --query-destination=<ipv>:<address>[/<mask>]Return whether destination ipv is set for service [P only]--service=<service> --get-destinationsList destinations in service [P only]--service=<service> --add-include=<service>Add a new include to service [P only]--service=<service> --remove-include=<service>Remove a include from service [P only]--service=<service> --query-include=<service>Return whether the include has been added for service [P only]--service=<service> --get-includesList includes of service [P only]Options to Adapt and Query Zones and Policies--list-all List everything added for or enabled [P] [Z] [O]--timeout=<timeval> Enable an option for timeval time, where timeval isa number followed by one of letters 's' or 'm' or 'h'Usable for options marked with [T]--set-description=<description>Set new description [P only] [Z] [O]--get-description Print description [P only] [Z] [O]--get-target Get the target [P only] [Z] [O]--set-target=<target>Set the target [P only] [Z] [O]--set-short=<description>Set new short description [Z] [O]--get-short Print short description [P only] [Z] [O]--list-services List services added [P] [Z]--add-service=<service>Add a service [P] [Z] [O] [T]--remove-service=<service>Remove a service [P] [Z] [O]--query-service=<service>Return whether service has been added [P] [Z] [O]--list-ports List ports added [P] [Z] [O]--add-port=<portid>[-<portid>]/<protocol>Add the port [P] [Z] [O] [T]--remove-port=<portid>[-<portid>]/<protocol>Remove the port [P] [Z] [O]--query-port=<portid>[-<portid>]/<protocol>Return whether the port has been added [P] [Z] [O]--list-protocols List protocols added [P] [Z] [O]--add-protocol=<protocol>Add the protocol [P] [Z] [O] [T]--remove-protocol=<protocol>Remove the protocol [P] [Z] [O]--query-protocol=<protocol>Return whether the protocol has been added [P] [Z] [O]--list-source-ports List source ports added [P] [Z] [O]--add-source-port=<portid>[-<portid>]/<protocol>Add the source port [P] [Z] [O] [T]--remove-source-port=<portid>[-<portid>]/<protocol>Remove the source port [P] [Z] [O]--query-source-port=<portid>[-<portid>]/<protocol>Return whether the source port has been added [P] [Z] [O]--list-icmp-blocks List Internet ICMP type blocks added [P] [Z] [O]--add-icmp-block=<icmptype>Add an ICMP block [P] [Z] [O] [T]--remove-icmp-block=<icmptype>Remove the ICMP block [P] [Z] [O]--query-icmp-block=<icmptype>Return whether an ICMP block has been added [P] [Z] [O]--list-forward-ports List IPv4 forward ports added [P] [Z] [O]--add-forward-port=port=<portid>[-<portid>]:proto=<protocol>[:toport=<portid>[-<portid>]][:toaddr=<address>[/<mask>]]Add the IPv4 forward port [P] [Z] [O] [T]--remove-forward-port=port=<portid>[-<portid>]:proto=<protocol>[:toport=<portid>[-<portid>]][:toaddr=<address>[/<mask>]]Remove the IPv4 forward port [P] [Z] [O]--query-forward-port=port=<portid>[-<portid>]:proto=<protocol>[:toport=<portid>[-<portid>]][:toaddr=<address>[/<mask>]]Return whether the IPv4 forward port has been added [P] [Z] [O]--add-masquerade Enable IPv4 masquerade [P] [Z] [O] [T]--remove-masquerade Disable IPv4 masquerade [P] [Z] [O]--query-masquerade Return whether IPv4 masquerading has been enabled [P] [Z] [O]--list-rich-rules List rich language rules added [P] [Z] [O]--add-rich-rule=<rule>Add rich language rule 'rule' [P] [Z] [O] [T]--remove-rich-rule=<rule>Remove rich language rule 'rule' [P] [Z] [O]--query-rich-rule=<rule>Return whether a rich language rule 'rule' has beenadded [P] [Z] [O]Options to Adapt and Query Zones--add-icmp-block-inversionEnable inversion of icmp blocks for a zone [P] [Z]--remove-icmp-block-inversionDisable inversion of icmp blocks for a zone [P] [Z]--query-icmp-block-inversionReturn whether inversion of icmp blocks has been enabledfor a zone [P] [Z]--add-forward Enable forwarding of packets between interfaces andsources in a zone [P] [Z] [T]--remove-forward Disable forwarding of packets between interfaces andsources in a zone [P] [Z]--query-forward Return whether forwarding of packets between interfacesand sources has been enabled for a zone [P] [Z]Options to Adapt and Query Policies--get-priority Get the priority [P only] [O]--set-priority=<priority>Set the priority [P only] [O]--list-ingress-zonesList ingress zones that are bound to a policy [P] [O]--add-ingress-zone=<zone>Add the ingress zone to a policy [P] [O]--remove-ingress-zone=<zone>Remove the ingress zone from a policy [P] [O]--query-ingress-zone=<zone>Query whether the ingress zone has been adedd to apolicy [P] [O]--list-egress-zonesList egress zones that are bound to a policy [P] [O]--add-egress-zone=<zone>Add the egress zone to a policy [P] [O]--remove-egress-zone=<zone>Remove the egress zone from a policy [P] [O]--query-egress-zone=<zone>Query whether the egress zone has been adedd to apolicy [P] [O]Options to Handle Bindings of Interfaces--list-interfaces List interfaces that are bound to a zone [P] [Z]--add-interface=<interface>Bind the <interface> to a zone [P] [Z]--change-interface=<interface>Change zone the <interface> is bound to [P] [Z]--query-interface=<interface>Query whether <interface> is bound to a zone [P] [Z]--remove-interface=<interface>Remove binding of <interface> from a zone [P] [Z]Options to Handle Bindings of Sources--list-sources List sources that are bound to a zone [P] [Z]--add-source=<source>[/<mask>]|<MAC>|ipset:<ipset>Bind the source to a zone [P] [Z]--change-source=<source>[/<mask>]|<MAC>|ipset:<ipset>Change zone the source is bound to [Z]--query-source=<source>[/<mask>]|<MAC>|ipset:<ipset>Query whether the source is bound to a zone [P] [Z]--remove-source=<source>[/<mask>]|<MAC>|ipset:<ipset>Remove binding of the source from a zone [P] [Z]Helper Options--new-helper=<helper> --module=<module> [--family=<family>]Add a new helper [P only]--new-helper-from-file=<filename> [--name=<helper>]Add a new helper from file with optional name [P only]--delete-helper=<helper>Delete an existing helper [P only]--load-helper-defaults=<helper>Load helper default settings [P only]--info-helper=<helper> Print information about an helper--path-helper=<helper> Print file path of an helper [P only]--get-helpers Print predefined helpers--helper=<helper> --set-description=<description>Set new description to helper [P only]--helper=<helper> --get-descriptionPrint description for helper [P only]--helper=<helper> --set-short=<description>Set new short description to helper [P only]--helper=<helper> --get-shortPrint short description for helper [P only]--helper=<helper> --add-port=<portid>[-<portid>]/<protocol>Add a new port to helper [P only]--helper=<helper> --remove-port=<portid>[-<portid>]/<protocol>Remove a port from helper [P only]--helper=<helper> --query-port=<portid>[-<portid>]/<protocol>Return whether the port has been added for helper [P only]--helper=<helper> --get-portsList ports of helper [P only]--helper=<helper> --set-module=<module>Set module to helper [P only]--helper=<helper> --get-moduleGet module from helper [P only]--helper=<helper> --set-family={ipv4|ipv6|}Set family for helper [P only]--helper=<helper> --get-familyGet module from helper [P only]Direct Options--direct First option for all direct options--get-all-chainsGet all chains [P]--get-chains {ipv4|ipv6|eb} <table>Get all chains added to the table [P]--add-chain {ipv4|ipv6|eb} <table> <chain>Add a new chain to the table [P]--remove-chain {ipv4|ipv6|eb} <table> <chain>Remove the chain from the table [P]--query-chain {ipv4|ipv6|eb} <table> <chain>Return whether the chain has been added to the table [P]--get-all-rulesGet all rules [P]--get-rules {ipv4|ipv6|eb} <table> <chain>Get all rules added to chain in table [P]--add-rule {ipv4|ipv6|eb} <table> <chain> <priority> <arg>...Add rule to chain in table [P]--remove-rule {ipv4|ipv6|eb} <table> <chain> <priority> <arg>...Remove rule with priority from chain in table [P]--remove-rules {ipv4|ipv6|eb} <table> <chain>Remove rules from chain in table [P]--query-rule {ipv4|ipv6|eb} <table> <chain> <priority> <arg>...Return whether a rule with priority has been added tochain in table [P]--passthrough {ipv4|ipv6|eb} <arg>...Pass a command through (untracked by firewalld)--get-all-passthroughsGet all tracked passthrough rules [P]--get-passthroughs {ipv4|ipv6|eb} <arg>...Get tracked passthrough rules [P]--add-passthrough {ipv4|ipv6|eb} <arg>...Add a new tracked passthrough rule [P]--remove-passthrough {ipv4|ipv6|eb} <arg>...Remove a tracked passthrough rule [P]--query-passthrough {ipv4|ipv6|eb} <arg>...Return whether the tracked passthrough rule has beenadded [P]Lockdown Options--lockdown-on Enable lockdown.--lockdown-off Disable lockdown.--query-lockdown Query whether lockdown is enabledLockdown Whitelist Options--list-lockdown-whitelist-commandsList all command lines that are on the whitelist [P]--add-lockdown-whitelist-command=<command>Add the command to the whitelist [P]--remove-lockdown-whitelist-command=<command>Remove the command from the whitelist [P]--query-lockdown-whitelist-command=<command>Query whether the command is on the whitelist [P]--list-lockdown-whitelist-contextsList all contexts that are on the whitelist [P]--add-lockdown-whitelist-context=<context>Add the context context to the whitelist [P]--remove-lockdown-whitelist-context=<context>Remove the context from the whitelist [P]--query-lockdown-whitelist-context=<context>Query whether the context is on the whitelist [P]--list-lockdown-whitelist-uidsList all user ids that are on the whitelist [P]--add-lockdown-whitelist-uid=<uid>Add the user id uid to the whitelist [P]--remove-lockdown-whitelist-uid=<uid>Remove the user id uid from the whitelist [P]--query-lockdown-whitelist-uid=<uid>Query whether the user id uid is on the whitelist [P]--list-lockdown-whitelist-usersList all user names that are on the whitelist [P]--add-lockdown-whitelist-user=<user>Add the user name user to the whitelist [P]--remove-lockdown-whitelist-user=<user>Remove the user name user from the whitelist [P]--query-lockdown-whitelist-user=<user>Query whether the user name user is on the whitelist [P]Panic Options--panic-on Enable panic mode--panic-off Disable panic mode--query-panic Query whether panic mode is enabledFirewalld 使用区域(Zone)的概念来划分与系统交互的流量。网络接口被分配给一个或多个区域,每个区域包含允许的端口和服务列表。默认区域也可用于管理与任何区域都不匹配的流量。
如果配置了服务,则守护进程的启用,启停、重启和查看命令如下:
sudo systemctl enable firewalld
sudo systemctl start firewalld
sudo systemctl stop firewalld
sudo systemctl restart firewalld
sudo systemctl status firewalld
如果没配置服务,也可以用以下的命令查看状态:
sudo firewall-cmd --state
查看区域和默认区域:
$ sudo firewall-cmd --get-zones
block dmz drop external home internal nm-shared public trusted work$ sudo firewall-cmd --get-default-zone
public
在以下做出改变之前,先保存下当前状态:
$ sudo firewall-cmd --list-all
public (active)target: defaulticmp-block-inversion: nointerfaces: eth0sources:services: cockpit dhcpv6-client sshports:protocols:forward: yesmasquerade: noforward-ports:source-ports:icmp-blocks:rich rules:允许端口,例如postgresql的5432端口:
# 临时添加
sudo firewall-cmd --add-port=5432/tcp
# 永久添加
sudo firewall-cmd --add-port=5432/tcp --permanent
# 使改变生效
sudo firewall-cmd --reload
确认生效:
$ sudo firewall-cmd --list-ports
5432/tcp
删除刚添加的端口:
sudo firewall-cmd --remove-port=5432/tcp --permanent
# 此时执行sudo firewall-cmd --list-ports,输出为5432/tcp
sudo firewall-cmd --reload
# 此时执行sudo firewall-cmd --list-ports,输出为空
如果系统定义了服务,则可以添加服务,其实和加端口意思一样:
$ grep postgres /etc/services
postgres 5432/tcp postgresql # POSTGRES
postgres 5432/udp postgresql # POSTGRES$ sudo firewall-cmd --list-services
cockpit dhcpv6-client ssh$ sudo firewall-cmd --add-service postgresql
success$ sudo firewall-cmd --list-services
cockpit dhcpv6-client postgresql ssh
以上端口和服务都是限制目标的,也可以限制源:
$ sudo firewall-cmd --zone=internal --add-source=172.16.1.0/24 --permanent
最后,推荐两个命令速查表:
- Advanced Linux commands cheat sheet
- Advanced Linux Commands Cheat Sheet
相关文章:

Linux firewalld 常用命令
本文参考RedHat官网文章How to configure a firewall on Linux with firewalld。 Firewalld 是守护进程名,对应命令为firewall-cmd。帮助详见以下命令: $ firewall-cmd --helpUsage: firewall-cmd [OPTIONS...]General Options-h, --help Pr…...

LeetCode 热题 100 49. 字母异位词分组
LeetCode 热题 100 | 49. 字母异位词分组 大家好,今天我们来解决一道经典的算法题——字母异位词分组。这道题在LeetCode上被标记为中等难度,要求我们将字母异位词组合在一起。下面我将详细讲解解题思路,并附上Python代码实现。 问题描述 给…...

从 DeepSeek 到飞算 JavaAI:AI 开发工具如何重塑技术生态?
在科技飞速发展的当下,AI 开发工具正以前所未有的态势重塑技术生态。从备受瞩目的 DeepSeek 到崭露头角的飞算 JavaAI,它们在不同维度上推动着软件开发领域的变革,深刻影响着开发者的工作方式与行业发展走向。 DeepSeek:AI 开发领…...

OceanBase 初探学习历程之二——操作系统参数最佳实践
本文章分享OB操作系统参数最佳实践值,相关参数部分来自PK项目得知,仅供参考,实际参数设置仍需结合现有设备条件及业务系统特点是否有必要如此设置,但我任务大部分场景均可用(仅本人个人观点)。 1、磁盘配置…...
)
全面指南:使用JMeter进行性能压测与性能优化(中间件压测、数据库压测、分布式集群压测、调优)
目录 一、性能测试的指标 1、并发量 2、响应时间 3、错误率 4、吞吐量 5、资源使用率 二、压测全流程 三、其他注意点 1、并发和吞吐量的关系 2、并发和线程的关系 四、调优及分布式集群压测(待仔细学习) 1.线程数量超过单机承载能力时的解决…...

《机器学习实战》专栏 No12:项目实战—端到端的机器学习项目Kaggle糖尿病预测
《机器学习实战》专栏 第12集:项目实战——端到端的机器学习项目Kaggle糖尿病预测 本集为专栏最后一集,本专栏的特点是短平快,聚焦重点,不长篇大论纠缠于理论,而是在介绍基础理论框架基础上,快速切入实战项…...

【vue项目中如何实现一段文字跑马灯效果】
在Vue项目中实现一段文字跑马灯效果,可以通过多种方式实现,以下是几种常见的方法: 方法一:使用CSS动画和Vue数据绑定 这种方法通过CSS动画实现文字的滚动效果,并结合Vue的数据绑定动态更新文本内容。 步骤ÿ…...

DeepSeek 细节之 MLA (Multi-head Latent Attention)
DeepSeek 系统模型的基本架构仍然基于Transformer框架,为了实现高效推理和经济高效的训练,DeepSeek 还采用了MLA(多头潜在注意力)。 MHA(多头注意力)通过多个注意力头并行工作捕捉序列特征,但面临高计算成本…...

Python爬虫具体是如何解析商品信息的?
在使用Python爬虫解析亚马逊商品信息时,通常会结合requests库和BeautifulSoup库来实现。requests用于发送HTTP请求并获取网页内容,而BeautifulSoup则用于解析HTML页面并提取所需数据。以下是具体的解析过程,以按关键字搜索亚马逊商品为例。 …...

lerobot调试记录
这里写自定义目录标题 libtiff.so undefined symbol libtiff.so undefined symbol anaconda3/envs/lerobot3/lib/python3.10/site-packages/../.././libtiff.so.6: undefined symbol: jpeg12_write_raw_data, version LIBJPEG_8.01.安装库 conda install -c conda-forge jpeg …...

【Word转PDF】在线Doc/Docx转换为PDF格式 免费在线转换 功能强大好用
在日常办公和学习中,将Word文档转换为PDF格式的需求非常普遍。无论是制作简历、撰写报告还是分享文件,都需要确保文档格式在不同设备上保持一致。而小白工具的“Word转PDF”功能正是为此需求量身打造的一款高效解决方案。 【Word转PDF】在线Doc/Docx转换…...

Jenkins 配置 Credentials 凭证
Jenkins 配置 Credentials 凭证 一、创建凭证 Dashboard -> Manage Jenkins -> Manage Credentials 在 Domain 列随便点击一个 (global) 二、添加 凭证 点击左侧 Add Credentials 四、填写凭证 Kind:凭证类型 Username with password: 配置 用…...

Datawhale Ollama教程笔记5
Dify 接入 Ollama 部署的本地模型 Dify 支持接入 Ollama 部署的大型语言模型推理和 embedding 能力。 快速接入 下载 Ollama 访问 Ollama 安装与配置,查看 Ollama 本地部署教程。 运行 Ollama 并与 Llama 聊天 ollama run llama3.1Copy to clipboardErrorCopied …...

小爱音箱连接电脑外放之后,浏览器网页视频暂停播放后,音箱整体没声音问题解决
背景 22年买的小爱音箱增强版play,小爱音箱连接电脑外放之后,浏览器网页视频暂停播放后,音箱整体没声音(一边打着游戏,一边听歌,一边放视频,视频一暂停,什么声音都没了,…...

go设置镜像代理
前言 在 Go 开发中,如果直接从官方源(https://proxy.golang.org)下载依赖包速度较慢,可以通过设置 镜像代理 来加速依赖包的下载。以下是增加 Go 镜像代理的详细方法: 一、设置 Go 镜像代理 1. 使用环境变量设置代理…...

Python爬虫系列教程之第十二篇:爬虫异常处理与日志记录
大家好,欢迎继续关注本系列爬虫教程!在实际的爬虫项目中,网络请求可能会因为各种原因失败,如连接超时、目标服务器拒绝访问、解析错误等。此外,大规模爬虫任务运行过程中,各种异常情况层出不穷,…...

将Google文档导入WordPress:简单实用的几种方法
Google文档是内容创作者非常实用的写作工具。它支持在线编辑、多人协作,并能够自动保存内容。但当我们想把Google文档中的内容导入WordPress网站时,可能会遇到一些小麻烦,比如格式错乱、图片丢失等问题。本文将为大家介绍几种简单实用的方法&…...

大白话实战Gateway
网关功能 网关在分布式系统中起了什么作用?参考下图: 前端想要访问业务访问,就需要知道各个访问的地址,而业务集群服务有很多,前端需要记录非常多的服务器地址,这种情况下,我们需要对整个业务集群做一个整体屏蔽,这个时候就引入Gateway网关,它就是所有服务的请求入…...

深入学习解析:183页可编辑PPT华为市场营销MPR+LTC流程规划方案
华为终端正面临销售模式转型的关键时刻,旨在通过构建MPRLTC项目,以规避对运营商定制的过度依赖,并探索新的增长路径。项目核心在于建设一套全新的销售流程与IT系统,支撑双品牌及自有品牌的战略发展。 项目总体方案聚焦于四大关键议…...

【微中子代理踩坑-前端node-sass安装失败】
微中子代理踩坑-前端node-sass安装失败-windows 1.npm版本2.python2.73.安装Visual Studio 1.npm版本 当前使用node版本13.12.0 2.python2.7 安装python2.7.9并配置环境变量 3.安装Visual Studio 安装Visual Studio 我是直接勾选了3个windows的sdk,然后就好了 最后 npm in…...
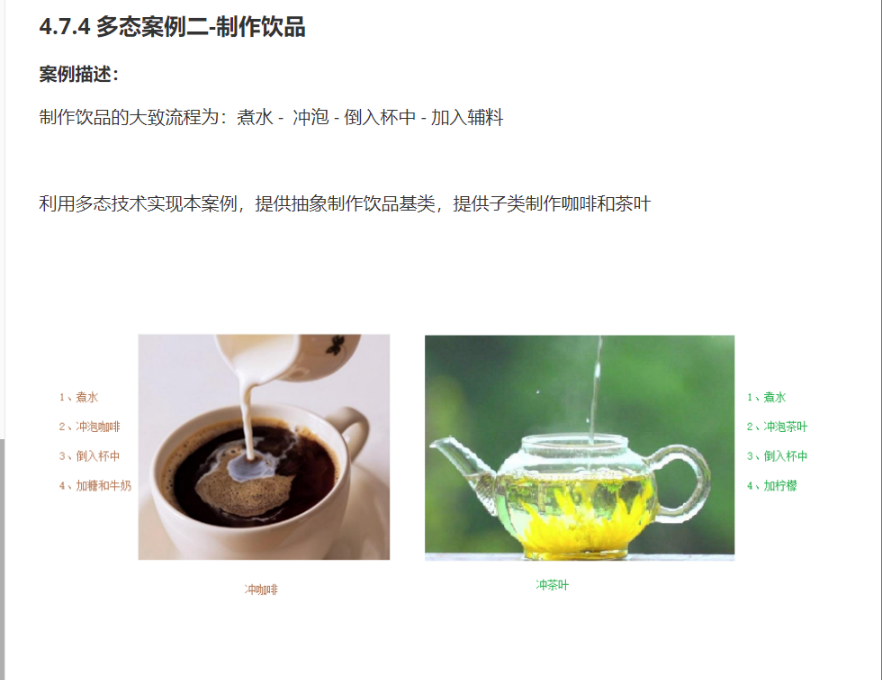
C++_核心编程_多态案例二-制作饮品
#include <iostream> #include <string> using namespace std;/*制作饮品的大致流程为:煮水 - 冲泡 - 倒入杯中 - 加入辅料 利用多态技术实现本案例,提供抽象制作饮品基类,提供子类制作咖啡和茶叶*//*基类*/ class AbstractDr…...

QMC5883L的驱动
简介 本篇文章的代码已经上传到了github上面,开源代码 作为一个电子罗盘模块,我们可以通过I2C从中获取偏航角yaw,相对于六轴陀螺仪的yaw,qmc5883l几乎不会零飘并且成本较低。 参考资料 QMC5883L磁场传感器驱动 QMC5883L磁力计…...
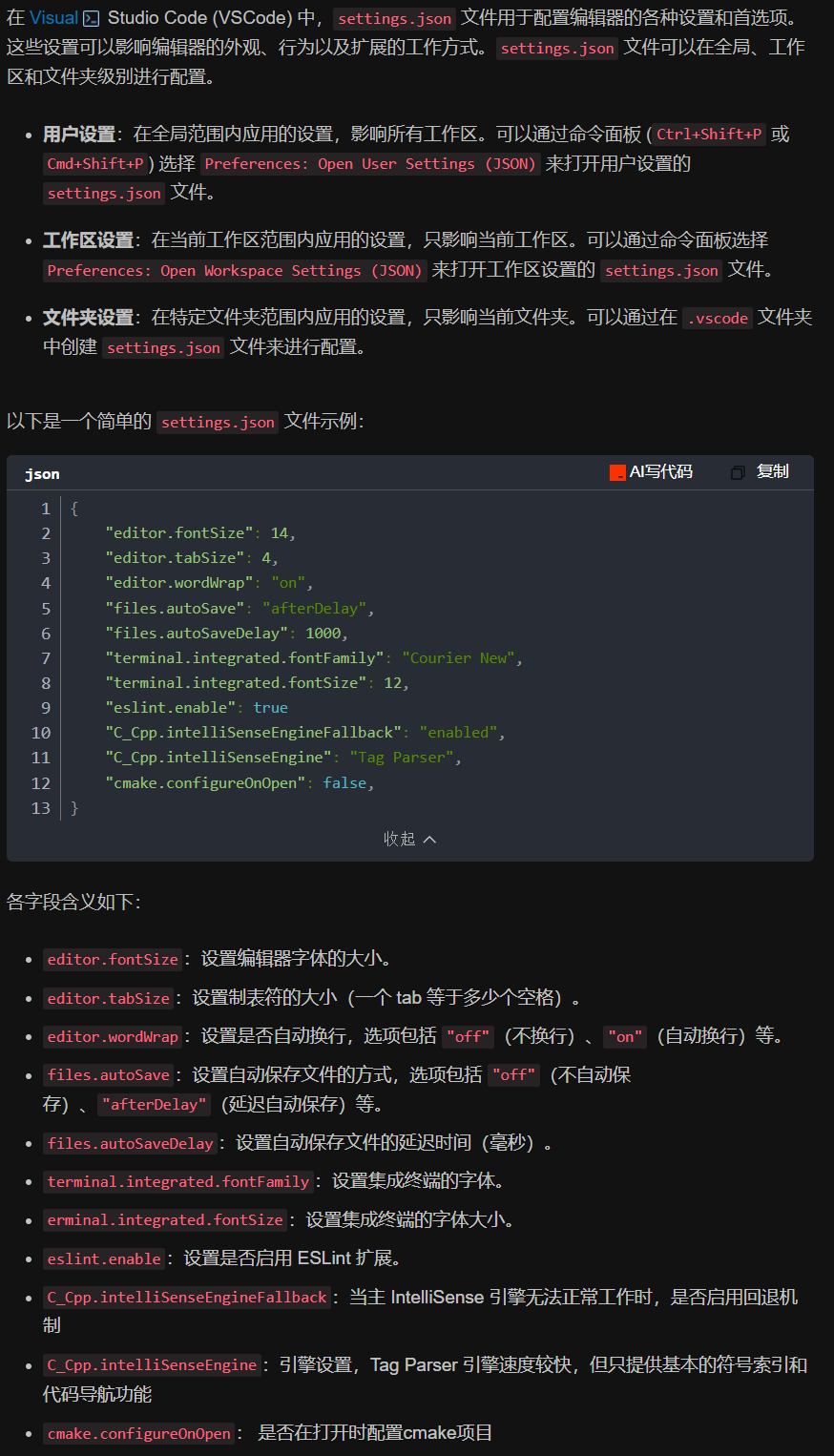
vscode(仍待补充)
写于2025 6.9 主包将加入vscode这个更权威的圈子 vscode的基本使用 侧边栏 vscode还能连接ssh? debug时使用的launch文件 1.task.json {"tasks": [{"type": "cppbuild","label": "C/C: gcc.exe 生成活动文件"…...

基于服务器使用 apt 安装、配置 Nginx
🧾 一、查看可安装的 Nginx 版本 首先,你可以运行以下命令查看可用版本: apt-cache madison nginx-core输出示例: nginx-core | 1.18.0-6ubuntu14.6 | http://archive.ubuntu.com/ubuntu focal-updates/main amd64 Packages ng…...
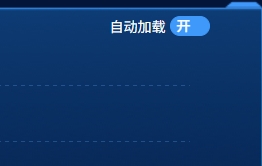
el-switch文字内置
el-switch文字内置 效果 vue <div style"color:#ffffff;font-size:14px;float:left;margin-bottom:5px;margin-right:5px;">自动加载</div> <el-switch v-model"value" active-color"#3E99FB" inactive-color"#DCDFE6"…...
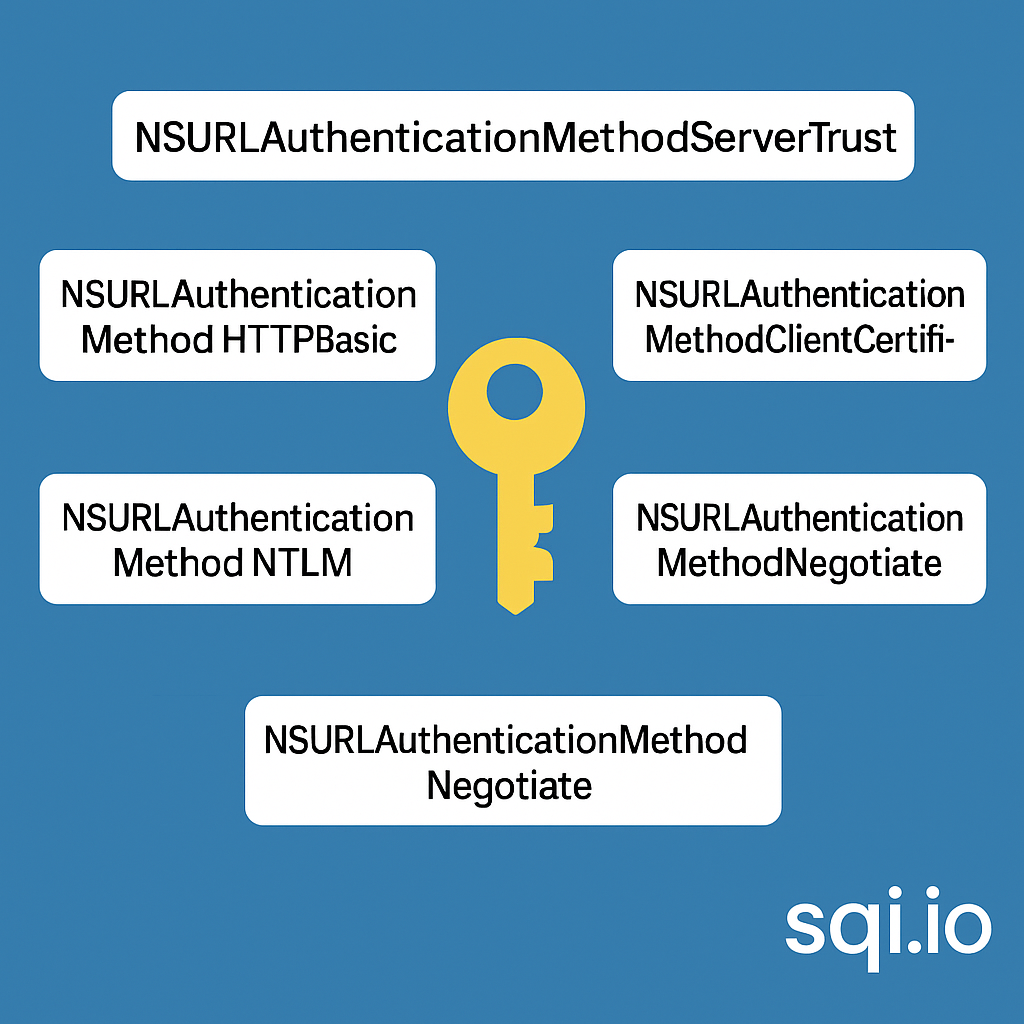
ServerTrust 并非唯一
NSURLAuthenticationMethodServerTrust 只是 authenticationMethod 的冰山一角 要理解 NSURLAuthenticationMethodServerTrust, 首先要明白它只是 authenticationMethod 的选项之一, 并非唯一 1 先厘清概念 点说明authenticationMethodURLAuthenticationChallenge.protectionS…...
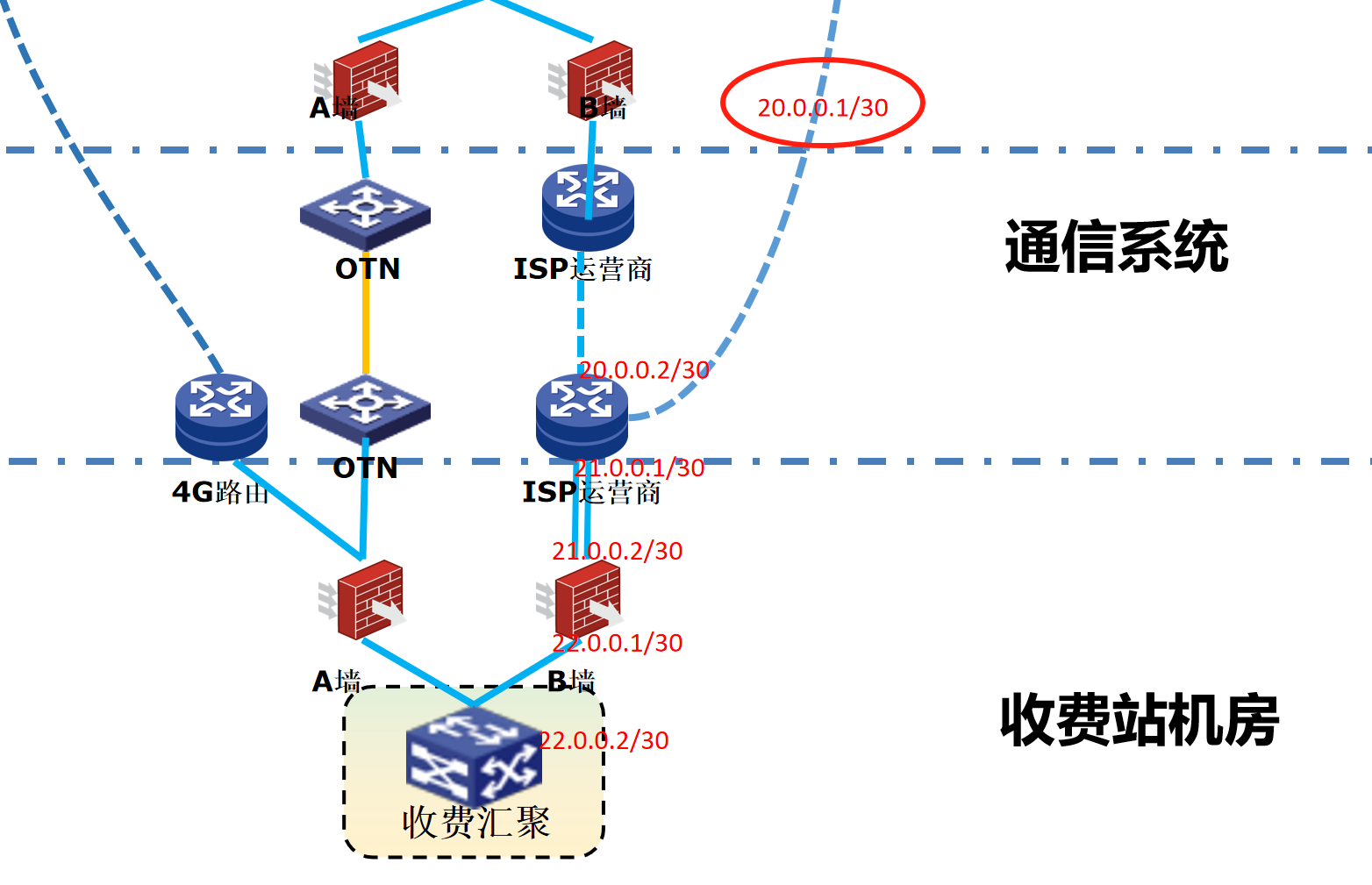
浪潮交换机配置track检测实现高速公路收费网络主备切换NQA
浪潮交换机track配置 项目背景高速网络拓扑网络情况分析通信线路收费网络路由 收费汇聚交换机相应配置收费汇聚track配置 项目背景 在实施省内一条高速公路时遇到的需求,本次涉及的主要是收费汇聚交换机的配置,浪潮网络设备在高速项目很少,通…...
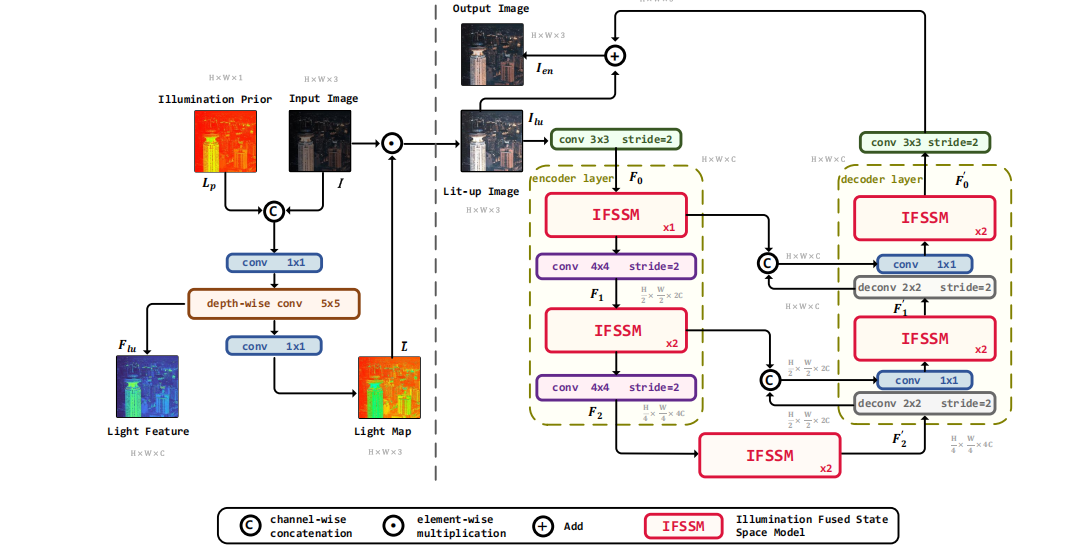
深度学习水论文:mamba+图像增强
🧀当前视觉领域对高效长序列建模需求激增,对Mamba图像增强这方向的研究自然也逐渐火热。原因在于其高效长程建模,以及动态计算优势,在图像质量提升和细节恢复方面有难以替代的作用。 🧀因此短时间内,就有不…...

【Linux】自动化构建-Make/Makefile
前言 上文我们讲到了Linux中的编译器gcc/g 【Linux】编译器gcc/g及其库的详细介绍-CSDN博客 本来我们将一个对于编译来说很重要的工具:make/makfile 1.背景 在一个工程中源文件不计其数,其按类型、功能、模块分别放在若干个目录中,mak…...
Unity VR/MR开发-VR开发与传统3D开发的差异
视频讲解链接:【XR马斯维】VR/MR开发与传统3D开发的差异【UnityVR/MR开发教程--入门】_哔哩哔哩_bilibili...
