suricata安装测试
系统版本为Ubuntu 22.04.4。
# cat /etc/issue
Ubuntu 22.04.4 LTS \n \l
#
# uname -a
Linux logging 6.8.0-49-generic #49~22.04.1-Ubuntu SMP PREEMPT_DYNAMIC Wed Nov 6 17:42:15 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
添加suricata的apt库。
# add-apt-repository ppa:oisf/suricata-stable
Repository: 'deb https://ppa.launchpadcontent.net/oisf/suricata-stable/ubuntu/ jammy main'
Description:
Suricata IDS/IPS/NSM stable packages
https://suricata.io/
https://oisf.net/Suricata IDS/IPS/NSM - Suricata is a high performance Intrusion Detection and Prevention System and Network Security Monitoring engine.Open Source and owned by a community run non-profit foundation, the Open Information Security Foundation (OISF). Suricata is developed by the OISF, its supporting vendors and the community....and many more great features -
https://suricata.io/features/all-features/
More info: https://launchpad.net/~oisf/+archive/ubuntu/suricata-stable
Adding repository.
Press [ENTER] to continue or Ctrl-c to cancel.
Adding deb entry to /etc/apt/sources.list.d/oisf-ubuntu-suricata-stable-jammy.list
Adding disabled deb-src entry to /etc/apt/sources.list.d/oisf-ubuntu-suricata-stable-jammy.list
Adding key to /etc/apt/trusted.gpg.d/oisf-ubuntu-suricata-stable.gpg with fingerprint 121504ADE276E141AD704A75AC10378CF205C960
执行update,尅看到对应的suricata源地址https://ppa.launchpadcontent.net/oisf/suricata-stable/ubuntu。
# apt-get update
Hit:1 http://mirrors.tuna.tsinghua.edu.cn/ubuntu jammy InRelease
Hit:2 http://mirrors.tuna.tsinghua.edu.cn/ubuntu jammy-updates InRelease
Hit:3 http://mirrors.tuna.tsinghua.edu.cn/ubuntu jammy-backports InRelease
Hit:4 http://security.ubuntu.com/ubuntu jammy-security InRelease
Hit:5 https://ppa.launchpadcontent.net/oisf/suricata-stable/ubuntu jammy InRelease
Reading package lists... Done
执行安装命令:
# apt-get install suricata -y
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
The following additional packages will be installed:libevent-core-2.1-7 libevent-pthreads-2.1-7 libhiredis0.14 libhtp2 libhyperscan5 liblzma-dev libnetfilter-queue1
Suggested packages:liblzma-doc
The following NEW packages will be installed:libevent-core-2.1-7 libevent-pthreads-2.1-7 libhiredis0.14 libhtp2 libhyperscan5 liblzma-dev libnetfilter-queue1 suricata
0 upgraded, 8 newly installed, 0 to remove and 115 not upgraded.
Need to get 6,038 kB of archives.
After this operation, 27.9 MB of additional disk space will be used.
当前安装的版本为7.0.8。
# suricata -V
This is Suricata version 7.0.8 RELEASE
配置suricata,配置文件/etc/suricata/suricata.yaml。
# ls -al /etc/suricata/
total 116
drwxr-xr-x 2 root root 4096 3月 9 20:01 .
drwxr-xr-x 143 root root 12288 3月 9 20:01 ..
-rw-r--r-- 1 root root 3327 12月 12 18:14 classification.config
-rw-r--r-- 1 root root 1375 12月 12 18:14 reference.config
-rw-r--r-- 1 root root 86374 12月 12 23:10 suricata.yaml
-rw-r--r-- 1 root root 1643 12月 12 18:14 threshold.config
首先确定系统的网卡名称,如下为ens32,其地址为192.168.1.168/24。
# ip link
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
2: ens32: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000link/ether 00:0c:29:2b:cb:01 brd ff:ff:ff:ff:ff:ffaltname enp2s0$ ip address show ens32
2: ens32: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000link/ether 00:0c:29:2b:cb:01 brd ff:ff:ff:ff:ff:ffaltname enp2s0inet 192.168.1.168/24 brd 192.168.1.255 scope global dynamic noprefixroute ens32valid_lft 466377sec preferred_lft 466377sec
修改配置文件suricata.yaml中的HOME_NET变量。
15 vars:16 # more specific is better for alert accuracy and performance17 address-groups:18 HOME_NET: "[192.168.0.0/16,10.0.0.0/8,172.16.0.0/12]"
修改该为:15 vars:16 # more specific is better for alert accuracy and performance17 address-groups:18 HOME_NET: "[192.168.1.0/24]"
修改配置文件中的网卡名称,af-packet使用ens32接口:
620 # Linux high speed capture support621 af-packet:622 - interface: eth0
修改为:620 # Linux high speed capture support621 af-packet:622 - interface: ens32
libpcap使用的接口ens32。
813 # Cross platform libpcap capture support814 pcap:815 - interface: eth0
修改为:813 # Cross platform libpcap capture support814 pcap:815 - interface: ens32
suricata的规则集目录配置如下,无需做修改。如果增加本地的规则文件,可在rule-files执行添加。
2170 ##
2171 ## Configure Suricata to load Suricata-Update managed rules.
2172 ##
2173
2174 default-rule-path: /var/lib/suricata/rules
2175
2176 rule-files:
2177 - suricata.rules
查看规则目录,目前还不存在。
# ls /var/lib/suricata
ls: cannot access '/var/lib/suricata': No such file or directory
分布的规则默认位于目录/usr/share/suricata/rules下:
# ls /usr/share/suricata/rules
app-layer-events.rules dns-events.rules http-events.rules mqtt-events.rules rfb-events.rules stream-events.rules
decoder-events.rules files.rules ipsec-events.rules nfs-events.rules smb-events.rules tls-events.rules
dhcp-events.rules ftp-events.rules kerberos-events.rules ntp-events.rules smtp-events.rules
dnp3-events.rules http2-events.rules modbus-events.rules quic-events.rules ssh-events.rules
执行规则更新命令suricata-update。数据目录为/var/lib/suricata,Suricata自身提供的规则目录/usr/share/suricata/rules。默认使用Emerging Threats提供的开源版规则集,如下为emerging.rules.tar.gz。
# suricata-update
9/3/2025 -- 21:01:15 - <Info> -- Using data-directory /var/lib/suricata.
9/3/2025 -- 21:01:15 - <Info> -- Using Suricata configuration /etc/suricata/suricata.yaml
9/3/2025 -- 21:01:15 - <Info> -- Using /usr/share/suricata/rules for Suricata provided rules.
9/3/2025 -- 21:01:15 - <Info> -- Found Suricata version 7.0.8 at /usr/bin/suricata.
9/3/2025 -- 21:01:15 - <Info> -- Loading /etc/suricata/suricata.yaml
9/3/2025 -- 21:01:15 - <Info> -- Disabling rules for protocol pgsql
9/3/2025 -- 21:01:15 - <Info> -- Disabling rules for protocol modbus
9/3/2025 -- 21:01:15 - <Info> -- Disabling rules for protocol dnp3
9/3/2025 -- 21:01:15 - <Info> -- Disabling rules for protocol enip
9/3/2025 -- 21:01:15 - <Info> -- No sources configured, will use Emerging Threats Open
9/3/2025 -- 21:01:15 - <Info> -- Fetching https://rules.emergingthreats.net/open/suricata-7.0.8/emerging.rules.tar.gz.100% - 4803034/4803034
9/3/2025 -- 21:04:48 - <Info> -- Done.
9/3/2025 -- 21:04:48 - <Info> -- Loading distribution rule file /usr/share/suricata/rules/app-layer-events.rules
最终,更新了57405条规则,其中使能了42240条。
9/3/2025 -- 21:04:48 - <Info> -- Ignoring file 029f98278a177b2c54e8d37841dc5528/rules/emerging-deleted.rules
9/3/2025 -- 21:04:50 - <Info> -- Loaded 57405 rules.
9/3/2025 -- 21:04:51 - <Info> -- Disabled 13 rules.
9/3/2025 -- 21:04:51 - <Info> -- Enabled 0 rules.
9/3/2025 -- 21:04:51 - <Info> -- Modified 0 rules.
9/3/2025 -- 21:04:51 - <Info> -- Dropped 0 rules.
9/3/2025 -- 21:04:51 - <Info> -- Enabled 136 rules for flowbit dependencies.
9/3/2025 -- 21:04:51 - <Info> -- Creating directory /var/lib/suricata/rules.
9/3/2025 -- 21:04:51 - <Info> -- Backing up current rules.
9/3/2025 -- 21:04:51 - <Info> -- Writing rules to /var/lib/suricata/rules/suricata.rules: total: 57405; enabled: 42240; added: 57405; removed 0; modified: 0
9/3/2025 -- 21:04:52 - <Info> -- Writing /var/lib/suricata/rules/classification.config
9/3/2025 -- 21:04:52 - <Info> -- Testing with suricata -T.
9/3/2025 -- 21:05:16 - <Info> -- Done.
如下更新了文件classification.config和suricata.rules。
# ls -l /var/lib/suricata/rules/
total 35224
-rw-r--r-- 1 root root 3228 3月 9 21:04 classification.config
-rw-r--r-- 1 root root 36064668 3月 9 21:04 suricata.rules
打开文件suricata.rules,共57405行,每行一条规则。
57403 alert tcp [95.99.30.188,96.126.105.219,96.20.102.87,96.2.25.180,96.232.181.85,96.244.38.131,96.245.83.39,96.255.94.70,96.65.68.193,96.92.142.206] any -> $HOME_NET any (msg:"ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 942"; reference:url,doc.emergingthreats.net/bin/view/Main/TorRules; threshold: type limit, track by_src, seconds 60, count 1; classtype:misc-attack; flowbits:set,ET.TorIP; sid:2522941; rev:5821; metadata:affected_product Any, attack_target Any, deployment Perimeter, tag TOR, signature_severity Informational, created_at 2008_12_01, updated_at 2025_03_07;)
57404 alert tcp [97.107.139.108,97.116.1.84,97.126.191.34,97.85.41.53,97.87.178.49,97.88.88.7,98.109.42.110,98.114.62.110,98.115.87.163,98.121.68.25] any -> $HOME_NET any (msg:"ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 943"; reference:url,d oc.emergingthreats.net/bin/view/Main/TorRules; threshold: type limit, track by_src, seconds 60, count 1; classtype:misc-attack ; flowbits:set,ET.TorIP; sid:2522942; rev:5821; metadata:affected_product Any, attack_target Any, deployment Perimeter, tag TOR, signature_severity Informational, created_at 2008_12_01, updated_at 2025_03_07;)
57405 alert tcp [98.128.173.1,98.128.175.45,98.128.175.69,98.168.31.145,98.1.90.15,98.206.28.99,98.22.27.104,98.232.88.235,98.29.199.207,98.60.249.63] any -> $HOME_NET any (msg:"ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 944"; reference:url,doc.emergingthreats.net/bin/view/Main/TorRules; threshold: type limit, track by_src, seconds 60, count 1; classtype:misc-attack; flowbits:set,ET.TorIP; sid:2522943; rev:5821; metadata:affected_product Any, attack_target Any, deployment Perimeter, tag TOR, signature_severity Informational, created_at 2008_12_01, updated_at 2025_03_07;)
如下命令查看支持的规则集源,可以使用update-sources命令更新源。默认使用的为Proofpoint提供的et/open规则集。
# suricata-update list-sources
9/3/2025 -- 21:23:04 - <Info> -- Found Suricata version 7.0.8 at /usr/bin/suricata.
9/3/2025 -- 21:23:04 - <Warning> -- Source index does not exist, will use bundled one.
9/3/2025 -- 21:23:04 - <Warning> -- Please run suricata-update update-sources.
Name: abuse.ch/feodotrackerVendor: Abuse.chSummary: Abuse.ch Feodo Tracker Botnet C2 IP rulesetLicense: CC0-1.0
Name: et/openVendor: ProofpointSummary: Emerging Threats Open RulesetLicense: MIT
Name: et/proVendor: ProofpointSummary: Emerging Threats Pro RulesetLicense: CommercialReplaces: et/openParameters: secret-codeSubscription: https://www.proofpoint.com/us/threat-insight/et-pro-ruleset
使能其它的规则源,在enable-source之后跟上源的名称。
# suricata-update enable-source abuse.ch/feodotracker
9/3/2025 -- 21:29:12 - <Info> -- Using data-directory /var/lib/suricata.
9/3/2025 -- 21:29:12 - <Info> -- Using Suricata configuration /etc/suricata/suricata.yaml
9/3/2025 -- 21:29:12 - <Info> -- Using /usr/share/suricata/rules for Suricata provided rules.
9/3/2025 -- 21:29:12 - <Info> -- Found Suricata version 7.0.8 at /usr/bin/suricata.
9/3/2025 -- 21:29:12 - <Warning> -- Source index does not exist, will use bundled one.
9/3/2025 -- 21:29:12 - <Warning> -- Please run suricata-update update-sources.
9/3/2025 -- 21:29:12 - <Info> -- Creating directory /var/lib/suricata/update/sources
9/3/2025 -- 21:29:12 - <Info> -- Enabling default source et/open
9/3/2025 -- 21:29:12 - <Info> -- Source abuse.ch/feodotracker enabled
再次执行更新,与之前相比,增加了5条规则。
# suricata-update
9/3/2025 -- 21:30:21 - <Info> -- Using data-directory /var/lib/suricata.
...
9/3/2025 -- 21:30:21 - <Info> -- Fetching https://feodotracker.abuse.ch/downloads/feodotracker.tar.gz.100% - 572/572
9/3/2025 -- 21:30:22 - <Info> -- Done.
9/3/2025 -- 21:30:22 - <Info> -- Checking https://rules.emergingthreats.net/open/suricata-7.0.8/emerging.rules.tar.gz.md5.9/3/2025 -- 21:30:27 - <Info> -- Backing up current rules.
9/3/2025 -- 21:30:30 - <Info> -- Writing rules to /var/lib/suricata/rules/suricata.rules: total: 57410; enabled: 42245; added: 5; removed 0; modified: 0
9/3/2025 -- 21:30:30 - <Info> -- Writing /var/lib/suricata/rules/classification.config
9/3/2025 -- 21:30:31 - <Info> -- Testing with suricata -T.
9/3/2025 -- 21:30:54 - <Info> -- Done.
如下5条规则,追加到了suricata.rules文件末尾:
57406 alert tcp $HOME_NET any -> [79.137.13.24] 443 (msg:"Feodo Tracker: potential Emotet CnC Traffic detected"; threshold: type limit, track by_src, seconds 60, count 1; classtype:trojan-activity; reference:url, feodotracker.abuse.ch/browse/host/79.137.13.2 4/; sid:900511539; rev:1;)
57407 alert tcp $HOME_NET any -> [91.230.49.1] 443 (msg:"Feodo Tracker: potential QakBot CnC Traffic detected"; threshold: type limit, track by_src, seconds 60, count 1; classtype:trojan-activity; reference:url, feodotracker.abuse.ch/browse/host/91.230.49.1/ ; sid:900513682; rev:1;)
57408 alert tcp $HOME_NET any -> [193.238.227.136] 443 (msg:"Feodo Tracker: potential QakBot CnC Traffic detected"; threshold: type limit, track by_src, seconds 60, count 1; classtype:trojan-activity; reference:url, feodotracker.abuse.ch/browse/host/193.238. 227.136/; sid:900513683; rev:1;)
57409 alert tcp $HOME_NET any -> [172.232.58.237] 443 (msg:"Feodo Tracker: potential QakBot CnC Traffic detected"; threshold: type limit, track by_src, seconds 60, count 1; classtype:trojan-activity; reference:url, feodotracker.abuse.ch/browse/host/172.232.5 8.237/; sid:900513684; rev:1;)
57410 alert tcp $HOME_NET any -> [172.232.58.169] 443 (msg:"Feodo Tracker: potential QakBot CnC Traffic detected"; threshold: type limit, track by_src, seconds 60, count 1; classtype:trojan-activity; reference:url, feodotracker.abuse.ch/browse/host/172.232.5 8.169/; sid:900513685; rev:1;)
根据提示,我们测试下suricata的配置和规则集。日志文件fast.log和eve.json记录入侵日志,后者为json格式。42245条规则成功加载了。
# suricata -T -c /etc/suricata/suricata.yaml -v
Notice: suricata: This is Suricata version 7.0.8 RELEASE running in SYSTEM mode
Info: cpu: CPUs/cores online: 4
Info: suricata: Running suricata under test mode
Info: suricata: Setting engine mode to IDS mode by default
Info: exception-policy: master exception-policy set to: auto
Info: logopenfile: fast output device (regular) initialized: fast.log
Info: logopenfile: eve-log output device (regular) initialized: eve.json
Info: logopenfile: stats output device (regular) initialized: stats.log
Info: detect: 1 rule files processed. 42245 rules successfully loaded, 0 rules failed, 0
Info: threshold-config: Threshold config parsed: 0 rule(s) found
Info: detect: 42248 signatures processed. 1262 are IP-only rules, 4329 are inspecting packet payload, 36441 inspect application layer, 108 are decoder event only
Notice: suricata: Configuration provided was successfully loaded. Exiting.
使用systemctl启动suricata。
# systemctl start suricata.service
#
# systemctl status suricata.service
● suricata.service - LSB: Next Generation IDS/IPSLoaded: loaded (/etc/init.d/suricata; generated)Active: active (running) since Sun 2025-03-09 21:45:08 CST; 9s agoDocs: man:systemd-sysv-generator(8)Process: 212803 ExecStart=/etc/init.d/suricata start (code=exited, status=0/SUCCESS)Tasks: 1 (limit: 9377)Memory: 347.6MCPU: 9.917sCGroup: /system.slice/suricata.service└─212812 /usr/bin/suricata -c /etc/suricata/suricata.yaml --pidfile /var/run/suricata.pid --af-packet -D -vvv3月 09 21:45:08 logging systemd[1]: Starting LSB: Next Generation IDS/IPS...
3月 09 21:45:08 logging suricata[212803]: Likely stale PID 208293 with /var/run/suricata.pid exists, but process is not running!
3月 09 21:45:08 logging suricata[212803]: Removing stale PID file /var/run/suricata.pid
3月 09 21:45:08 logging suricata[212803]: Starting suricata in IDS (af-packet) mode... done.
3月 09 21:45:08 logging systemd[1]: Started LSB: Next Generation IDS/IPS.
查看suricata进程:
# ps aux | grep suricata
root 212812 53.3 5.9 1129060 477708 ? Ssl 21:45 0:23 /usr/bin/suricata -c /etc/suricata/suricata.yaml --pidfile /var/run/suricata.pid --af-packet -D -vvv
查看线程信息:
# ps -eLf | grep suricata
root 212812 1 212812 11 10 21:45 ? 00:00:23 /usr/bin/suricata -c /etc/suricata/suricata.yaml --pidfile /var/run/suricata.pid --af-packet -D -vvv
root 212812 1 213226 0 10 21:45 ? 00:00:00 /usr/bin/suricata -c /etc/suricata/suricata.yaml --pidfile /var/run/suricata.pid --af-packet -D -vvv
root 212812 1 213227 0 10 21:45 ? 00:00:00 /usr/bin/suricata -c /etc/suricata/suricata.yaml --pidfile /var/run/suricata.pid --af-packet -D -vvv
root 212812 1 213228 0 10 21:45 ? 00:00:00 /usr/bin/suricata -c /etc/suricata/suricata.yaml --pidfile /var/run/suricata.pid --af-packet -D -vvv
root 212812 1 213229 0 10 21:45 ? 00:00:00 /usr/bin/suricata -c /etc/suricata/suricata.yaml --pidfile /var/run/suricata.pid --af-packet -D -vvv
root 212812 1 213230 0 10 21:45 ? 00:00:00 /usr/bin/suricata -c /etc/suricata/suricata.yaml --pidfile /var/run/suricata.pid --af-packet -D -vvv
root 212812 1 213231 0 10 21:45 ? 00:00:00 /usr/bin/suricata -c /etc/suricata/suricata.yaml --pidfile /var/run/suricata.pid --af-packet -D -vvv
root 212812 1 213232 0 10 21:45 ? 00:00:00 /usr/bin/suricata -c /etc/suricata/suricata.yaml --pidfile /var/run/suricata.pid --af-packet -D -vvv
root 212812 1 213233 0 10 21:45 ? 00:00:00 /usr/bin/suricata -c /etc/suricata/suricata.yaml --pidfile /var/run/suricata.pid --af-packet -D -vvv
root 212812 1 213234 0 10 21:45 ? 00:00:00 /usr/bin/suricata -c /etc/suricata/suricata.yaml --pidfile /var/run/suricata.pid --af-packet -D -vvv
suricata日志文件目录:
# ls -al /var/log/suricata/
total 68
drwxr-xr-x 5 root root 4096 3月 9 20:01 .
drwxrwxr-x 16 root syslog 4096 3月 9 20:01 ..
drwxr-xr-x 2 root root 4096 12月 12 23:10 certs
drwxr-xr-x 2 root root 4096 12月 12 23:10 core
-rw-r--r-- 1 root root 0 3月 9 20:01 eve.json
-rw-r--r-- 1 root root 0 3月 9 20:01 fast.log
drwxr-xr-x 2 root root 4096 12月 12 23:10 files
-rw-r--r-- 1 root root 0 3月 9 20:01 stats.log
-rw-r--r-- 1 root root 44574 3月 9 21:41 suricata.log
-rw-r--r-- 1 root root 1319 3月 9 21:41 suricata-start.log
查看启动日志。
# tail -f /var/log/suricata/suricata.log
[212812 - Suricata-Main] 2025-03-09 21:45:31 Perf: ioctl: ens32: disabling sg offloading
[212812 - Suricata-Main] 2025-03-09 21:45:31 Info: runmodes: ens32: creating 4 threads
[212812 - Suricata-Main] 2025-03-09 21:45:31 Config: flow-manager: using 1 flow manager threads
[212812 - Suricata-Main] 2025-03-09 21:45:31 Config: flow-manager: using 1 flow recycler threads
[212812 - Suricata-Main] 2025-03-09 21:45:31 Info: unix-manager: unix socket '/var/run/suricata/suricata-command.socket'
[213226 - W#01-ens32] 2025-03-09 21:45:31 Perf: af-packet: ens32: rx ring: block_size=32768 block_nr=26 frame_size=1600 frame_nr=520
[213227 - W#02-ens32] 2025-03-09 21:45:31 Perf: af-packet: ens32: rx ring: block_size=32768 block_nr=26 frame_size=1600 frame_nr=520
[213228 - W#03-ens32] 2025-03-09 21:45:31 Perf: af-packet: ens32: rx ring: block_size=32768 block_nr=26 frame_size=1600 frame_nr=520
[213229 - W#04-ens32] 2025-03-09 21:45:32 Perf: af-packet: ens32: rx ring: block_size=32768 block_nr=26 frame_size=1600 frame_nr=520
[212812 - Suricata-Main] 2025-03-09 21:45:32 Notice: threads: Threads created -> W: 4 FM: 1 FR: 1 Engine started.
我们下载一个病毒文件,进行测试。
# wget http://192.168.1.9/Testing/eicar.com
查看日志eve.json:
{"timestamp":"2025-03-09T21:54:11.511716+0800","flow_id":1034246583273967,"in_iface":"ens32","event_type":"http","src_ip":"192.168.1.168","src_port":39850,"dest_ip":"192.168.1.9","dest_port":80,"proto":"TCP","pkt_src":"wire/pcap","tx_id":0,"http":{"hostname":"192.168.1.9","url":"/Testing/eicar.com","http_user_agent":"Wget/1.21.2","http_content_type":"application/x-msdos-program","http_method":"GET","protocol":"HTTP/1.1","status":200,"length":68}}
{"timestamp":"2025-03-09T21:54:11.513080+0800","flow_id":1034246583273967,"in_iface":"ens32","event_type":"fileinfo","src_ip":"192.168.1.9","src_port":80,"dest_ip":"192.168.1.168","dest_port":39850,"proto":"TCP","pkt_src":"wire/pcap","http":{"hostname":"192.168.1.9","url":"/Testing/eicar.com","http_user_agent":"Wget/1.21.2","http_content_type":"application/x-msdos-program","http_method":"GET","protocol":"HTTP/1.1","status":200,"length":68},"app_proto":"http","fileinfo":{"filename":"/Testing/eicar.com","gaps":false,"state":"CLOSED","stored":false,"size":68,"tx_id":0}}
相关文章:

suricata安装测试
系统版本为Ubuntu 22.04.4。 # cat /etc/issue Ubuntu 22.04.4 LTS \n \l # # uname -a Linux logging 6.8.0-49-generic #49~22.04.1-Ubuntu SMP PREEMPT_DYNAMIC Wed Nov 6 17:42:15 UTC 2 x86_64 x86_64 x86_64 GNU/Linux添加suricata的apt库。 # add-apt-repository pp…...

Java反射简单理解
Java反射是指在运行时(runtime)能够动态地获取类的内部信息,并能直接操作类的属性和方法的一种机制。通过反射,开发者可以在运行时检查类、接口、字段和方法,并且可以调用这些方法和访问这些字段,而无需在编…...

WPS Word中英文混杂空格和行间距不一致调整方案
文章目录 问题1:在两端对齐的情况下,如何删除参考文献(英文)的空格问题2:中英文混杂行间距不一致问题问题3:设置中文为固定字体,设置西文为固定字体参考 问题1:在两端对齐的情况下&a…...

探秘沃尔什-哈达玛变换(WHT)原理
沃尔什-哈达玛变换(WHT)起源 起源与命名(20世纪早期) 数学基础:该变换的理论基础由法国数学家雅克哈达玛(Jacques Hadamard)在1893年提出,其核心是哈达玛矩阵的构造。扩展与命名&…...

优雅拼接字符串:StringJoiner 的完整指南
在Java开发中,字符串拼接是高频操作。无论是日志格式化、构建CSV数据,还是生成动态SQL,开发者常需处理分隔符、前缀和后缀的组合。传统的StringBuilder虽然灵活,但代码冗余且易出错。Java 8推出的StringJoiner类,以简洁…...

AFL++安装
学习fuzzing也几天了,今天记录AFL的安装及使用 一、实验环境 虚拟机:ubuntu20.04 当然也可以uname -a去看自己的版本号 二、AFL安装 1.先更新一下工具 sudo apt update2.安装AFL必要的一些依赖,例如编译工具(如 build-essen…...

开发者社区测试报告(功能测试+性能测试)
功能测试 测试相关用例 开发者社区功能背景 在当今数字化时代,编程已经成为一项核心技能,越来越多的人开始学习编程,以适应快速变化的科技 环境。基于这一需求,我设计开发了一个类似博客的论坛系统,专注于方便程序员…...

如何优化 VS Code 远程开发环境?高效配置与性能提升策略
相关系列文章 《新手教学系列——善用 VSCode 工作区,让开发更高效》 《新手教学系列——用 VSCode 实现高效远程开发》 《Webpack 优化全攻略:彻底解决 Vue 项目 npm run dev 的内存泄露问题》 引言 随着开发环境不断进化,VS Code 作为一款轻量级的代码编辑器,已经成为…...

【二】JavaScript能力提升---this对象
目录 this的理解 this的原理 事件绑定中的this 行内绑定 动态绑定 window定时器中的this 相信小伙伴们看完这篇文章,对于this的对象可以有一个很大的提升! this的理解 对于this指针,可以先记住以下两点: this永远指向一个…...

YC 孵化项目 Pinch:实时语音翻译视频会议平台;Mistral OCR:能处理多语言多模态复杂文档丨日报
开发者朋友们大家好: 这里是 「RTE 开发者日报」 ,每天和大家一起看新闻、聊八卦。 我们的社区编辑团队会整理分享 RTE(Real-Time Engagement) 领域内「有话题的 技术 」、「有亮点的 产品 」、「有思考的 文章 」、「有态度的 …...

OSPF报文分析
OSPF报文分析 组播地址 224.0.0.0~224.0.0.255为预留的组播地址(永久组地址),地址224.0.0.0保留不做分配,其它地址供路由协议使用; 224.0.1.0~238.255.255.255为用户可用的组播地址(…...

蓝桥杯刷题周计划(第二周)
目录 前言题目一题目代码题解分析 题目二题目代码题解分析 题目三题目代码题解分析 题目四题目代码题解分析 题目五题目代码题解分析 题目六题目代码题解分析 题目七题目代码题解分析 题目八题目题解分析 题目九题目代码题解分析 题目十题目代码题解分析 题目十一题目代码题解分…...

PH热榜 | 2025-03-09
1. ResumeUp 2.0 标语:聊聊,几分钟内就能帮助你打造完美的ATS简历。 介绍:告别为写完美简历而烦恼的日子吧!只需与人工智能聊天,回答几个简单的问题,就能在几分钟内生成强有力的简历,不仅能通…...

《gradio :AI demos》
《gradio :AI demos》 Folders and files Name Last commit message Last commit date parent directory .. agent_chatbot Declare exports in __all__ for type checking (#10238) 3 months ago all_demos Fix deployed Spaces (#10271) 2 months ago …...

Interop_UdsProtocolStack之数据解析器使用方法
一、背景与需求 在汽车电子领域,UDS(Unified Diagnostic Services)协议栈的响应报文解析是实现ECU诊断功能的核心环节。本文提出一种基于配置驱动的通用解析器开发方案,满足以下行业需求: 多协议兼容性:支…...

从0开始完成基于异步服务器的boost搜索引擎
文章目录 前言一、本项目涉及的技术栈和环境二、boost是什么?三、项目的相关背景四、项目的相关原理五、正排索引 vs 倒排索引 - 搜索引擎具体原理六、 编写数据去标签与数据清洗的模块 Parser6.1 下载boost的文档库6.2 去标签6.3 代码编写 七、索引模块7.1. 整体框…...
与食材特性”的动态平衡)
炒菜本质是 “能量(火候)与食材特性”的动态平衡
炒菜看似简单,但想要做到色香味俱全,需遵循一套清晰的逻辑链条。以下从底层逻辑到实操步骤拆解: 一、核心逻辑:控制变量,精准匹配 炒菜本质是 “能量(火候)与食材特性”的动态平衡,…...
)
AI Copilot——维新派的贾维斯,守旧派的墓志铭(程序员视角)
6500万年前的那颗陨石好像要落下来了 这一段时间,伴随着claude sonnet 3.7的发布 以及cursor,windsurf 等一众AI智能编辑器的涌现,社区的programming自媒体坐不住了,有一个观点已经快要溢出屏幕:程序员这个岗位要黄&a…...
)
Java Spring MVC (2)
常见的Request Controller 和 Response Controller 的区别 用餐厅点餐来理解 想象你去一家餐厅吃饭: Request Controller(接单员):负责处理你的点餐请求,记录你的口味、桌号等信息。Response Controller(…...
对开源VLA sota π0的微调——如何基于各种开源数据集、以及你自己的私有数据集微调π0(含我司的微调实践)
前言 25年2.4日,几个月前推出π0的公司Physical Intelligence (π)宣布正式开源π0及π0-FAST,如之前所介绍的,他们对用超过 10,000 小时的机器人数据进行了预训练 该GitHub代码仓库「 π0及π0-FAST的GitHub地址:github.com/Ph…...
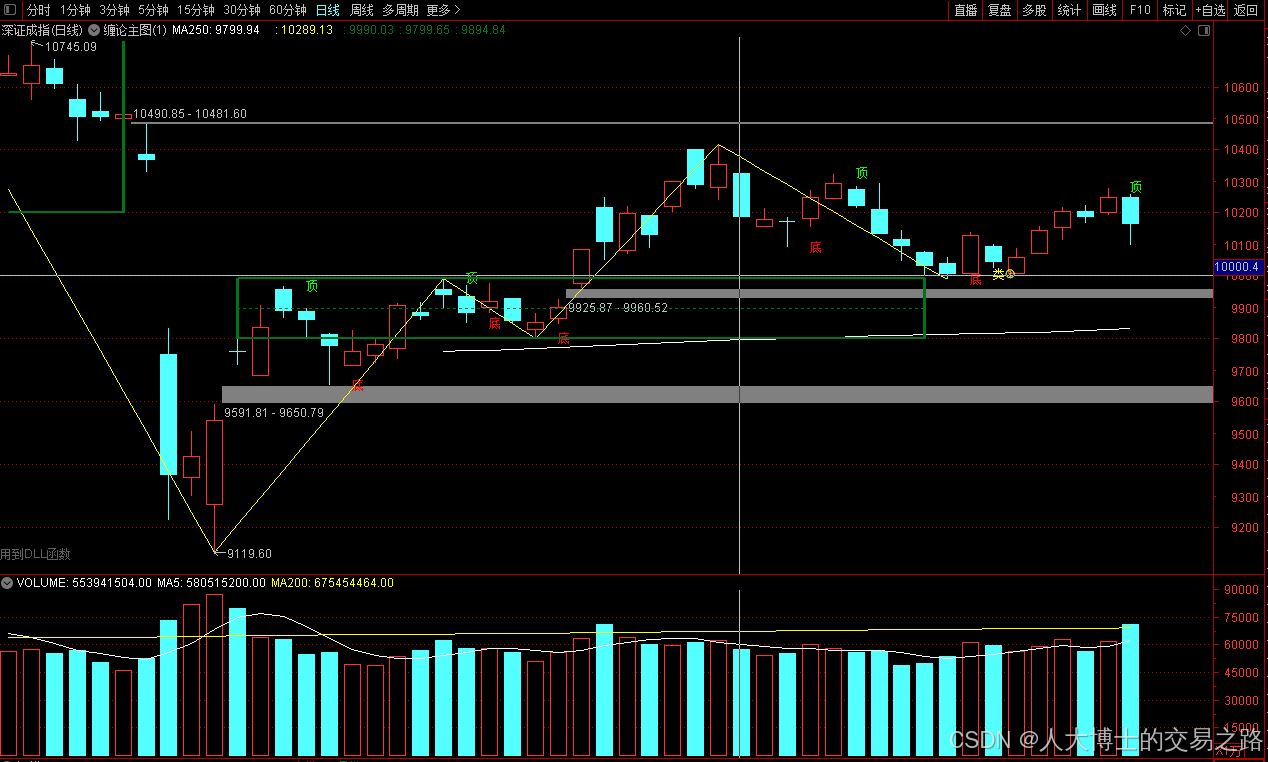
龙虎榜——20250610
上证指数放量收阴线,个股多数下跌,盘中受消息影响大幅波动。 深证指数放量收阴线形成顶分型,指数短线有调整的需求,大概需要一两天。 2025年6月10日龙虎榜行业方向分析 1. 金融科技 代表标的:御银股份、雄帝科技 驱动…...
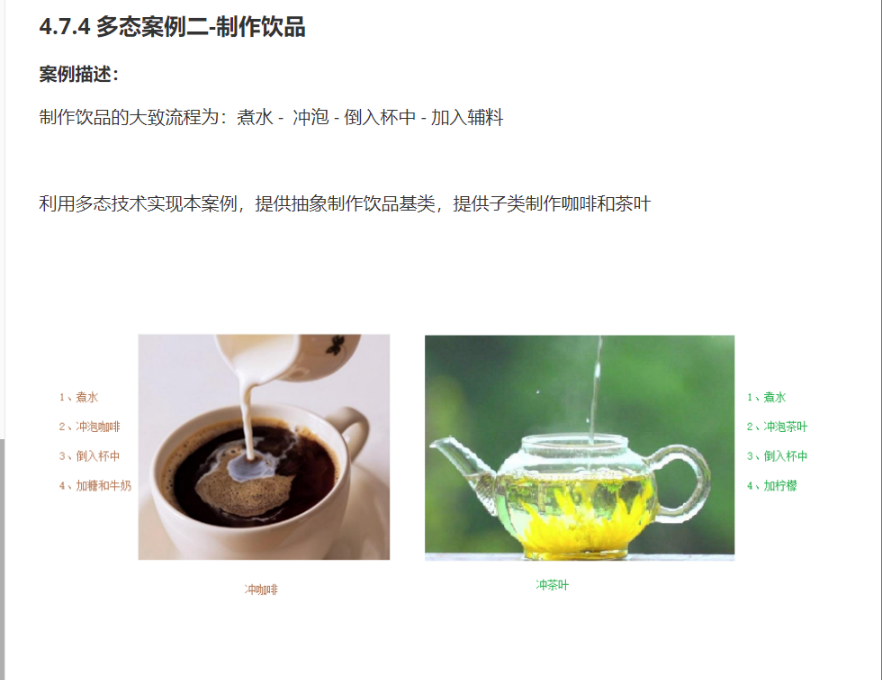
C++_核心编程_多态案例二-制作饮品
#include <iostream> #include <string> using namespace std;/*制作饮品的大致流程为:煮水 - 冲泡 - 倒入杯中 - 加入辅料 利用多态技术实现本案例,提供抽象制作饮品基类,提供子类制作咖啡和茶叶*//*基类*/ class AbstractDr…...

HTML 列表、表格、表单
1 列表标签 作用:布局内容排列整齐的区域 列表分类:无序列表、有序列表、定义列表。 例如: 1.1 无序列表 标签:ul 嵌套 li,ul是无序列表,li是列表条目。 注意事项: ul 标签里面只能包裹 li…...

电脑插入多块移动硬盘后经常出现卡顿和蓝屏
当电脑在插入多块移动硬盘后频繁出现卡顿和蓝屏问题时,可能涉及硬件资源冲突、驱动兼容性、供电不足或系统设置等多方面原因。以下是逐步排查和解决方案: 1. 检查电源供电问题 问题原因:多块移动硬盘同时运行可能导致USB接口供电不足&#x…...

大语言模型如何处理长文本?常用文本分割技术详解
为什么需要文本分割? 引言:为什么需要文本分割?一、基础文本分割方法1. 按段落分割(Paragraph Splitting)2. 按句子分割(Sentence Splitting)二、高级文本分割策略3. 重叠分割(Sliding Window)4. 递归分割(Recursive Splitting)三、生产级工具推荐5. 使用LangChain的…...

渲染学进阶内容——模型
最近在写模组的时候发现渲染器里面离不开模型的定义,在渲染的第二篇文章中简单的讲解了一下关于模型部分的内容,其实不管是方块还是方块实体,都离不开模型的内容 🧱 一、CubeListBuilder 功能解析 CubeListBuilder 是 Minecraft Java 版模型系统的核心构建器,用于动态创…...
Nuxt.js 中的路由配置详解
Nuxt.js 通过其内置的路由系统简化了应用的路由配置,使得开发者可以轻松地管理页面导航和 URL 结构。路由配置主要涉及页面组件的组织、动态路由的设置以及路由元信息的配置。 自动路由生成 Nuxt.js 会根据 pages 目录下的文件结构自动生成路由配置。每个文件都会对…...

Java 加密常用的各种算法及其选择
在数字化时代,数据安全至关重要,Java 作为广泛应用的编程语言,提供了丰富的加密算法来保障数据的保密性、完整性和真实性。了解这些常用加密算法及其适用场景,有助于开发者在不同的业务需求中做出正确的选择。 一、对称加密算法…...

全面解析各类VPN技术:GRE、IPsec、L2TP、SSL与MPLS VPN对比
目录 引言 VPN技术概述 GRE VPN 3.1 GRE封装结构 3.2 GRE的应用场景 GRE over IPsec 4.1 GRE over IPsec封装结构 4.2 为什么使用GRE over IPsec? IPsec VPN 5.1 IPsec传输模式(Transport Mode) 5.2 IPsec隧道模式(Tunne…...
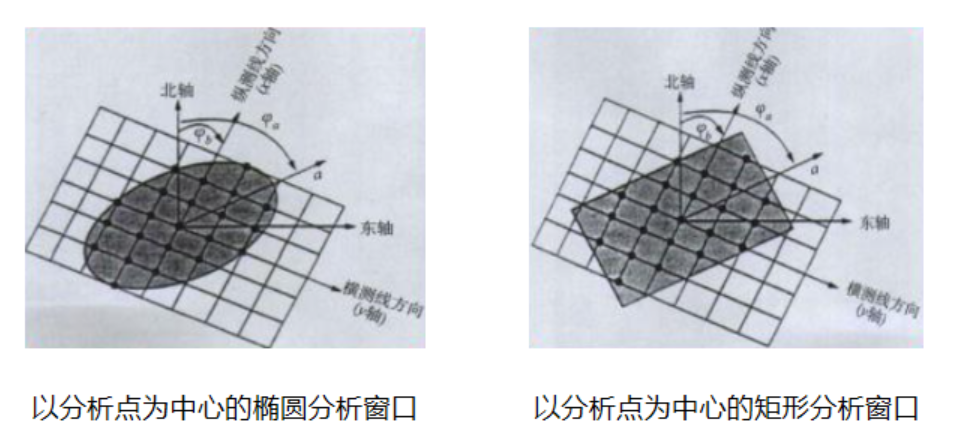
论文笔记——相干体技术在裂缝预测中的应用研究
目录 相关地震知识补充地震数据的认识地震几何属性 相干体算法定义基本原理第一代相干体技术:基于互相关的相干体技术(Correlation)第二代相干体技术:基于相似的相干体技术(Semblance)基于多道相似的相干体…...
