基于OAuth2-proxy和Keycloak为comfyui实现SSO
背景
comfyui无认证被漏扫后易被rce挖矿
攻击过程
https://www.oschina.net/news/340226
https://github.com/comfyanonymous/ComfyUI/discussions/5165
阿里云漏洞库关于comfyui的漏洞
https://avd.aliyun.com/search?q=comfyui×tamp__1384=n4%2BxBD0GitGQ0QD8ID%2FiW4BIY0Ki%3DdYre1rN74D
RCE示例
https://github.com/hay86/ComfyUI_AceNodes/blob/5ba01db8a3b7afb8e4aecfaa48823ddeb132bbbb/nodes.py#L1193
逻辑图示意

理论上,配合istio的reuquestauthorization可以加密k8s中所有的需要认证的界面
Keycloak
支持邮箱认证,等各种SSO,RBAC权限控制等。
keycloak镜像需要先build一下,再放到k8s中作为启动镜像直接使用
FROM registry.xx.local/keycloak/keycloak:26.2.4 AS builder
# Enable health and metrics support
ENV KC_HEALTH_ENABLED=true
ENV KC_METRICS_ENABLED=true# Configure a database vendor
ENV KC_DB=postgresWORKDIR /opt/keycloak
RUN /opt/keycloak/bin/kc.sh buildFROM registry.xx.local/keycloak/keycloak:26.2.4
COPY --from=builder /opt/keycloak/ /opt/keycloak/
ENTRYPOINT ["/opt/keycloak/bin/kc.sh"]
keycloak postgresql部署文件
apiVersion: v1
kind: Service
metadata:name: keycloaklabels:app: keycloak
spec:ports:- protocol: TCPport: 8080targetPort: httpname: httpselector:app: keycloaktype: ClusterIP
---
apiVersion: v1
kind: Service
metadata:labels:app: keycloak# Used toname: keycloak-discovery
spec:selector:app: keycloak# Allow not-yet-ready Pods to be visible to ensure the forming of a cluster if Pods come up concurrentlypublishNotReadyAddresses: trueclusterIP: Nonetype: ClusterIP
---
apiVersion: apps/v1
# Use a stateful setup to ensure that for a rolling update Pods are restarted with a rolling strategy one-by-one.
# This prevents losing in-memory information stored redundantly in two Pods.
kind: StatefulSet
metadata:name: keycloaklabels:app: keycloak
spec:serviceName: keycloak-discovery# Run with one replica to save resources, or with two replicas to allow for rolling updates for configuration changesreplicas: 1selector:matchLabels:app: keycloaktemplate:metadata:labels:app: keycloakspec:affinity:nodeAffinity:requiredDuringSchedulingIgnoredDuringExecution:nodeSelectorTerms:- matchExpressions:- key: kubernetes.io/archoperator: Invalues:- arm64containers:- name: keycloakimage: registry.xxx.local/keycloak/keycloak:26.2.4-optionsargs: ["start", "--optimized"] # 注意启动参数env:- name: KC_BOOTSTRAP_ADMIN_USERNAMEvalue: "admin"- name: KC_BOOTSTRAP_ADMIN_PASSWORDvalue: "brainkeyClock@2025"# In a production environment, add a TLS certificate to Keycloak to either end-to-end encrypt the traffic between# the client or Keycloak, or to encrypt the traffic between your proxy and Keycloak.# Respect the proxy headers forwarded by the reverse proxy# In a production environment, verify which proxy type you are using, and restrict access to Keycloak# from other sources than your proxy if you continue to use proxy headers.- name: KC_PROXY_HEADERSvalue: "xforwarded"- name: KC_HTTP_ENABLEDvalue: "true"# In this explorative setup, no strict hostname is set.# For production environments, set a hostname for a secure setup.- name: KC_HOSTNAME_STRICTvalue: "false"- name: KC_HEALTH_ENABLEDvalue: "true"- name: 'KC_CACHE'value: 'ispn'# Use the Kubernetes configuration for distributed caches which is based on DNS- name: 'KC_CACHE_STACK'value: 'kubernetes'# Passing the Pod's IP primary address to the JGroups clustering as this is required in IPv6 only setups- name: POD_IPvalueFrom:fieldRef:fieldPath: status.podIP# Instruct JGroups which DNS hostname to use to discover other Keycloak nodes# Needs to be unique for each Keycloak cluster- name: JAVA_OPTS_APPENDvalue: '-Djgroups.dns.query="keycloak-discovery" -Djgroups.bind.address=$(POD_IP)'- name: 'KC_DB_URL_DATABASE'value: 'keycloak'- name: 'KC_DB_URL_HOST'value: 'postgres'- name: 'KC_DB'value: 'postgres'# In a production environment, use a secret to store username and password to the database- name: 'KC_DB_PASSWORD'value: 'CEPEiRjHVT'- name: 'KC_DB_USERNAME'value: 'keycloak'ports:- name: httpcontainerPort: 8080startupProbe:httpGet:path: /health/startedport: 9000readinessProbe:httpGet:path: /health/readyport: 9000livenessProbe:httpGet:path: /health/liveport: 9000resources:limits:cpu: 2000mmemory: 2000Mirequests:cpu: 500mmemory: 1700Mi
---
apiVersion: v1
kind: PersistentVolumeClaim
metadata:name: postgres-data-pvcnamespace: infrastructure
spec:storageClassName: csi-cephfs-scaccessModes:- ReadWriteOnceresources:requests:storage: 2Gi
---
# This is deployment of PostgreSQL with an ephemeral storage for testing: Once the Pod stops, the data is lost.
# For a production setup, replace it with a database setup that persists your data.
apiVersion: apps/v1
kind: Deployment
metadata:name: postgreslabels:app: postgres
spec:replicas: 1selector:matchLabels:app: postgrestemplate:metadata:labels:app: postgresspec:affinity:nodeAffinity:requiredDuringSchedulingIgnoredDuringExecution:nodeSelectorTerms:- matchExpressions:- key: kubernetes.io/archoperator: Invalues:- arm64- key: kubernetes.io/hostnameoperator: Invalues:- 10.17.3.8containers:- name: postgresimage: registry.xxx.local/keycloak/postgres:17env:- name: POSTGRES_USERvalue: "keycloak"- name: POSTGRES_PASSWORDvalue: "CEPEiRjHVT"- name: POSTGRES_DBvalue: "keycloak"- name: POSTGRES_LOG_STATEMENTvalue: "all"- name: PGDATAvalue: "/var/lib/postgresql/data"ports:- name: postgrescontainerPort: 5432volumeMounts:# Using volume mount for PostgreSQL's data folder as it is otherwise not writable- name: postgres-datamountPath: /var/lib/postgresql/datavolumes:- name: postgres-datapersistentVolumeClaim:claimName: postgres-data-pvc
---
apiVersion: v1
kind: Service
metadata:labels:app: postgresname: postgres
spec:selector:app: postgresports:- protocol: TCPport: 5432targetPort: 5432type: ClusterIP
keycloak web界面配置
- 创建realms
- 创建client
- 创建user
创建realms

在comfyui realms下创建client






设置邮箱,开启校验,用户校验界面选项GPT解释如下
| 名称 | 是否勾选 | 含义与说明 |
|---|---|---|
| Standard flow ✅ | 已勾选 | 启用 授权码模式(Authorization Code Flow)。这是 OAuth2 / OIDC 中最安全的认证方式,适用于 Web 应用。用户先跳转到 Keycloak 登录,登录成功后用授权码换取 token。 👉 推荐用于 OAuth2 Proxy / Web 前端认证场景。 |
| Implicit flow ⛔️ | 未勾选 | 启用 隐式授权模式,直接在浏览器中返回 access_token(不通过授权码)。 ✅ 适用于老式前端 SPA,但因安全性差(token 暴露在 URL),已被 OpenID Connect 官方弃用。 👉 不推荐启用,现代系统应使用 PKCE 替代。 |
| Direct access grants ⛔️ | 未勾选 | 启用 资源所有者密码模式(Password Grant),客户端可直接用用户名+密码换 token(不跳转登录页)。 👉 适合 CLI 工具或可信环境,不适合浏览器 Web 应用。 |
| Service accounts roles ⛔️ | 未勾选 | 启用 客户端凭证模式(Client Credentials Grant),用于服务对服务的通信,客户端代表自己(非用户)访问资源。 👉 适合后端服务间通信,不涉及用户登录。 |
| Standard Token Exchange ⛔️ | 未勾选 | 启用 token 交换(Token Exchange),允许一个 token 换成另一个 token(比如 impersonation)。 👉 一般用于微服务或代理层,需要更高控制的场景。 |
| OAuth 2.0 Device Authorization Grant ⛔️ | 未勾选 | 支持“设备授权码模式”,常用于智能电视、物联网设备登录场景(输入验证码方式登录)。 |
| OIDC CIBA Grant ⛔️ | 未勾选 | “Client Initiated Backchannel Authentication”,用于异步认证场景,比如银行确认付款请求。非常少用,适用于强身份确认。 |
创建的users需要启用邮箱验证才能登录,否则报错500
验证用户列表页面的邮箱列

为用户设置密码

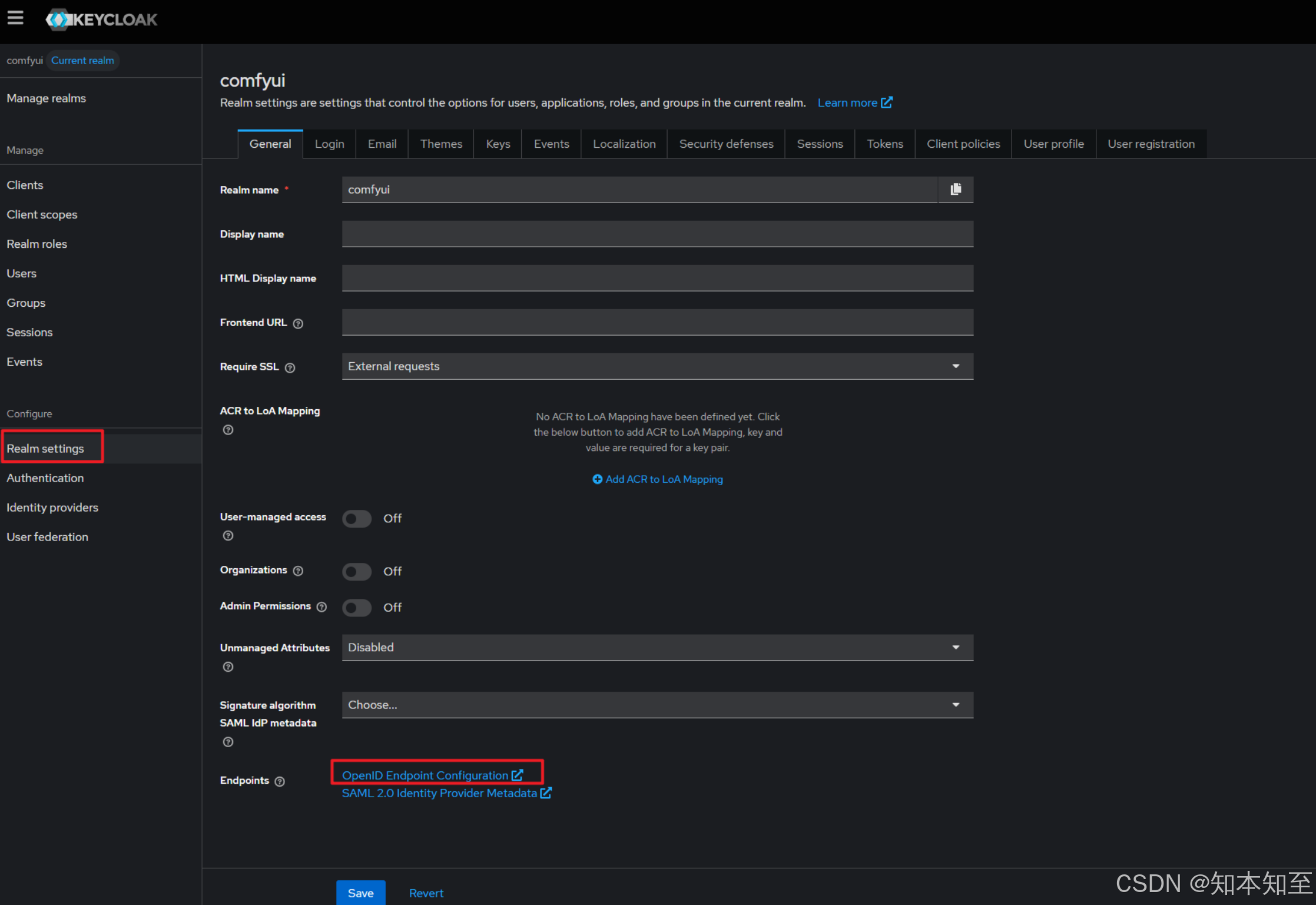
keycloak openid endpoint
postgresql
keycloak中的web界面配置realms client user存储在后端的postgresql中。
注意挂载目录和PGDATA变量,default PGDATA=/var/lib/postgresql/data
不能直接挂载/var/lib/postgresql到目录下,否则删除postgresql pod后,数据目录中的内容也会清空
OAuth2-proxy
使用helm部署
helm repo add oauth2-proxy https://oauth2-proxy.github.io/manifests
helm repo list
NAME URL
oauth2-proxy https://oauth2-proxy.github.io/manifests
# 下载
helm pull oauth2-proxy/oauth2-proxy
# 将gz包上传到master节点部署机
主要配置如下
- clientId
- clientSecret
- cookieSecret
- upstreams 内部comfyui的地址
- oidc_issuer_url oidc openid 身份提供者 签发地址
- redirect_url 重定向回客户端和keycloak中的Valid redirect URIs 相同
cookeSecret获取openssl rand -base64 32 | head -c 32 | base64
values.yaml如下
global: {}
# To help compatibility with other charts which use global.imagePullSecrets.
# global:
# imagePullSecrets:
# - name: pullSecret1
# - name: pullSecret2## Override the deployment namespace
##
namespaceOverride: "infrastructure"# Force the target Kubernetes version (it uses Helm `.Capabilities` if not set).
# This is especially useful for `helm template` as capabilities are always empty
# due to the fact that it doesn't query an actual cluster
kubeVersion:# Oauth client configuration specifics
config:# Add config annotationsannotations: {}# OAuth client IDclientID: "comfyui"# OAuth client secretclientSecret: "JQXnuxI9gyGiTp8p"# Create a new secret with the following command# openssl rand -base64 32 | head -c 32 | base64# Use an existing secret for OAuth2 credentials (see secret.yaml for required fields)# Example:# existingSecret: secretcookieSecret: "dPSHySO6TexpR5uyDQC2H"# The name of the cookie that oauth2-proxy will create# If left empty, it will default to the release namecookieName: ""google: {}# adminEmail: xxxx# useApplicationDefaultCredentials: true# targetPrincipal: xxxx# serviceAccountJson: xxxx# Alternatively, use an existing secret (see google-secret.yaml for required fields)# Example:# existingSecret: google-secret# groups: []# Example:# - group1@example.com# - group2@example.com# Default configuration, to be overriddenconfigFile: |-email_domains = [ "*" ]upstreams = [ "http://comfyui:80/" ] # 内部comfyui的地址provider = "oidc"oidc_issuer_url = "https://keycloak.xx.xxx.xx.cn/realms/comfyui"redirect_url = "https://comfyui.xx.xx.xx.cn/oauth2/callback"pass_authorization_header = truepass_access_token = true# Custom configuration file: oauth2_proxy.cfg# configFile: |-# pass_basic_auth = false# pass_access_token = true# Use an existing config map (see configmap.yaml for required fields)# Example:# existingConfig: configalphaConfig:enabled: false# Add config annotationsannotations: {}# Arbitrary configuration data to append to the server sectionserverConfigData: {}# Arbitrary configuration data to append to the metrics sectionmetricsConfigData: {}# Arbitrary configuration data to appendconfigData: {}# Arbitrary configuration to append# This is treated as a Go template and rendered with the root contextconfigFile: ""# Use an existing config map (see secret-alpha.yaml for required fields)existingConfig: ~# Use an existing secretexistingSecret: ~image:repository: "registry.xx.local/infra/quay.io/oauth2-proxy"# appVersion is used by defaulttag: ""pullPolicy: "IfNotPresent"command: []# Optionally specify an array of imagePullSecrets.
# Secrets must be manually created in the namespace.
# ref: https://kubernetes.io/docs/concepts/containers/images/#specifying-imagepullsecrets-on-a-pod
imagePullSecrets: []# - name: myRegistryKeySecretName# Set a custom containerPort if required.
# This will default to 4180 if this value is not set and the httpScheme set to http
# This will default to 4443 if this value is not set and the httpScheme set to https
# containerPort: 4180extraArgs:- --show-debug-on-error=true- --show-debug-on-error=true- --set-authorization-header=true- --reverse-proxy=true- --auth-logging=true- --cookie-httponly=true- --pass-access-token=true- --standard-logging=trueextraEnv: []envFrom: []
# Load environment variables from a ConfigMap(s) and/or Secret(s)
# that already exists (created and managed by you).
# ref: https://kubernetes.io/docs/tasks/configure-pod-container/configure-pod-configmap/#configure-all-key-value-pairs-in-a-configmap-as-container-environment-variables
#
# PS: Changes in these ConfigMaps or Secrets will not be automatically
# detected and you must manually restart the relevant Pods after changes.
#
# - configMapRef:
# name: special-config
# - secretRef:
# name: special-config-secret# -- Custom labels to add into metadata
customLabels: {}# To authorize individual email addresses
# That is part of extraArgs but since this needs special treatment we need to do a separate section
authenticatedEmailsFile:enabled: false# Defines how the email addresses file will be projected, via a configmap or secretpersistence: configmap# template is the name of the configmap what contains the email user list but has been configured without this chart.# It's a simpler way to maintain only one configmap (user list) instead changing it for each oauth2-proxy service.# Be aware the value name in the extern config map in data needs to be named to "restricted_user_access" or to the# provided value in restrictedUserAccessKey field.template: ""# The configmap/secret key under which the list of email access is stored# Defaults to "restricted_user_access" if not filled-in, but can be overridden to allow flexibilityrestrictedUserAccessKey: ""# One email per line# example:# restricted_access: |-# name1@domain# name2@domain# If you override the config with restricted_access it will configure a user list within this chart what takes care of the# config map resource.restricted_access: ""annotations: {}# helm.sh/resource-policy: keepservice:type: ClusterIP# when service.type is ClusterIP ...# clusterIP: 192.0.2.20# when service.type is LoadBalancer ...# loadBalancerIP: 198.51.100.40# loadBalancerSourceRanges: 203.0.113.0/24# when service.type is NodePort ...# nodePort: 80portNumber: 80# Protocol set on the serviceappProtocol: httpannotations: {}# foo.io/bar: "true"# configure externalTrafficPolicyexternalTrafficPolicy: ""# configure internalTrafficPolicyinternalTrafficPolicy: ""# configure service target porttargetPort: ""## Create or use ServiceAccount
serviceAccount:## Specifies whether a ServiceAccount should be createdenabled: true## The name of the ServiceAccount to use.## If not set and create is true, a name is generated using the fullname templatename:automountServiceAccountToken: trueannotations: {}ingress:enabled: false# className: nginxpath: /# Only used if API capabilities (networking.k8s.io/v1) allow itpathType: ImplementationSpecific# Used to create an Ingress record.# hosts:# - chart-example.local# Extra paths to prepend to every host configuration. This is useful when working with annotation based services.# Warning! The configuration is dependant on your current k8s API version capabilities (networking.k8s.io/v1)# extraPaths:# - path: /*# pathType: ImplementationSpecific# backend:# service:# name: ssl-redirect# port:# name: use-annotationlabels: {}# annotations:# kubernetes.io/ingress.class: nginx# kubernetes.io/tls-acme: "true"# tls:# Secrets must be manually created in the namespace.# - secretName: chart-example-tls# hosts:# - chart-example.localresources: {}# limits:# cpu: 100m# memory: 300Mi# requests:# cpu: 100m# memory: 300MiextraVolumes: []# - name: ca-bundle-cert# secret:# secretName: <secret-name>extraVolumeMounts: []# - mountPath: /etc/ssl/certs/# name: ca-bundle-cert# Additional containers to be added to the pod.
extraContainers: []# - name: my-sidecar# image: nginx:latest# Additional Init containers to be added to the pod.
extraInitContainers: []# - name: wait-for-idp# image: my-idp-wait:latest# command:# - sh# - -c# - wait-for-idp.shpriorityClassName: ""# hostAliases is a list of aliases to be added to /etc/hosts for network name resolution
hostAliases: []
# - ip: "10.xxx.xxx.xxx"
# hostnames:
# - "auth.example.com"
# - ip: 127.0.0.1
# hostnames:
# - chart-example.local
# - example.local# [TopologySpreadConstraints](https://kubernetes.io/docs/concepts/workloads/pods/pod-topology-spread-constraints/) configuration.
# Ref: https://kubernetes.io/docs/reference/kubernetes-api/workload-resources/pod-v1/#scheduling
# topologySpreadConstraints: []# Affinity for pod assignment
# Ref: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/#affinity-and-anti-affinity
affinity:nodeAffinity:requiredDuringSchedulingIgnoredDuringExecution:nodeSelectorTerms:- matchExpressions:- key: kubernetes.io/archoperator: Invalues:- arm64# Tolerations for pod assignment
# Ref: https://kubernetes.io/docs/concepts/configuration/taint-and-toleration/
tolerations: []# Node labels for pod assignment
# Ref: https://kubernetes.io/docs/user-guide/node-selection/
nodeSelector: {}# Whether to use secrets instead of environment values for setting up OAUTH2_PROXY variables
proxyVarsAsSecrets: true# Configure Kubernetes liveness and readiness probes.
# Ref: https://kubernetes.io/docs/tasks/configure-pod-container/configure-liveness-readiness-probes/
# Disable both when deploying with Istio 1.0 mTLS. https://istio.io/help/faq/security/#k8s-health-checks
livenessProbe:enabled: trueinitialDelaySeconds: 0timeoutSeconds: 1readinessProbe:enabled: trueinitialDelaySeconds: 0timeoutSeconds: 5periodSeconds: 10successThreshold: 1# Configure Kubernetes security context for container
# Ref: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/
securityContext:enabled: trueallowPrivilegeEscalation: falsecapabilities:drop:- ALLreadOnlyRootFilesystem: truerunAsNonRoot: truerunAsUser: 2000runAsGroup: 2000seccompProfile:type: RuntimeDefaultdeploymentAnnotations: {}
podAnnotations: {}
podLabels: {}
replicaCount: 1
revisionHistoryLimit: 10
strategy: {}
enableServiceLinks: true## PodDisruptionBudget settings
## ref: https://kubernetes.io/docs/concepts/workloads/pods/disruptions/
podDisruptionBudget:enabled: trueminAvailable: 1## Horizontal Pod Autoscaling
## ref: https://kubernetes.io/docs/tasks/run-application/horizontal-pod-autoscale/
autoscaling:enabled: falseminReplicas: 1maxReplicas: 10targetCPUUtilizationPercentage: 80
# targetMemoryUtilizationPercentage: 80annotations: {}# Configure Kubernetes security context for pod
# Ref: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/
podSecurityContext: {}# whether to use http or https
httpScheme: httpinitContainers:# if the redis sub-chart is enabled, wait for it to be ready# before starting the proxy# creates a role binding to get, list, watch, the redis master pod# if service account is enabledwaitForRedis:enabled: trueimage:repository: "alpine"tag: "latest"pullPolicy: "IfNotPresent"# uses the kubernetes version of the cluster# the chart is deployed on, if not setkubectlVersion: ""securityContext:enabled: trueallowPrivilegeEscalation: falsecapabilities:drop:- ALLreadOnlyRootFilesystem: truerunAsNonRoot: truerunAsUser: 65534runAsGroup: 65534seccompProfile:type: RuntimeDefaulttimeout: 180resources: {}# limits:# cpu: 100m# memory: 300Mi# requests:# cpu: 100m# memory: 300Mi# Additionally authenticate against a htpasswd file. Entries must be created with "htpasswd -B" for bcrypt encryption.
# Alternatively supply an existing secret which contains the required information.
htpasswdFile:enabled: falseexistingSecret: ""entries: []# One row for each user# example:# entries:# - testuser:$2y$05$gY6dgXqjuzFhwdhsiFe7seM9q9Tile4Y3E.CBpAZJffkeiLaC21Gy# Configure the session storage type, between cookie and redis
sessionStorage:# Can be one of the supported session storage cookie|redistype: cookieredis:# Name of the Kubernetes secret containing the redis & redis sentinel password values (see also `sessionStorage.redis.passwordKey`)existingSecret: ""# Redis password value. Applicable for all Redis configurations. Taken from redis subchart secret if not set. `sessionStorage.redis.existingSecret` takes precedencepassword: ""# Key of the Kubernetes secret data containing the redis password value. If you use the redis sub chart, make sure# this password matches the one used in redis.global.redis.password (see below).passwordKey: "redis-password"# Can be one of standalone|cluster|sentinelclientType: "standalone"standalone:# URL of redis standalone server for redis session storage (e.g. `redis://HOST[:PORT]`). Automatically generated if not setconnectionUrl: ""cluster:# List of Redis cluster connection URLs. Array or single string allowed.connectionUrls: []# - "redis://127.0.0.1:8000"# - "redis://127.0.0.1:8001"sentinel:# Name of the Kubernetes secret containing the redis sentinel password value (see also `sessionStorage.redis.sentinel.passwordKey`). Default: `sessionStorage.redis.existingSecret`existingSecret: ""# Redis sentinel password. Used only for sentinel connection; any redis node passwords need to use `sessionStorage.redis.password`password: ""# Key of the Kubernetes secret data containing the redis sentinel password valuepasswordKey: "redis-sentinel-password"# Redis sentinel master namemasterName: ""# List of Redis cluster connection URLs. Array or single string allowed.connectionUrls: []# - "redis://127.0.0.1:8000"# - "redis://127.0.0.1:8001"# Enables and configure the automatic deployment of the redis subchart
redis:# provision an instance of the redis sub-chartenabled: false# Redis specific helm chart settings, please see:# https://github.com/bitnami/charts/tree/master/bitnami/redis#parameters# global:# redis:# password: yourpassword# If you install Redis using this sub chart, make sure that the password of the sub chart matches the password# you set in sessionStorage.redis.password (see above).# redisPort: 6379# architecture: standalone# Enables apiVersion deprecation checks
checkDeprecation: true# Allows graceful shutdown
# terminationGracePeriodSeconds: 65
# lifecycle:
# preStop:
# exec:
# command: [ "sh", "-c", "sleep 60" ]metrics:# Enable Prometheus metrics endpointenabled: true# Serve Prometheus metrics on this portport: 44180# when service.type is NodePort ...# nodePort: 44180# Protocol set on the service for the metrics portservice:appProtocol: httpserviceMonitor:# Enable Prometheus Operator ServiceMonitorenabled: false# Define the namespace where to deploy the ServiceMonitor resourcenamespace: ""# Prometheus Instance definitionprometheusInstance: default# Prometheus scrape intervalinterval: 60s# Prometheus scrape timeoutscrapeTimeout: 30s# Add custom labels to the ServiceMonitor resourcelabels: {}## scheme: HTTP scheme to use for scraping. Can be used with `tlsConfig` for example if using istio mTLS.scheme: ""## tlsConfig: TLS configuration to use when scraping the endpoint. For example if using istio mTLS.## Of type: https://github.com/coreos/prometheus-operator/blob/master/Documentation/api.md#tlsconfigtlsConfig: {}## bearerTokenFile: Path to bearer token file.bearerTokenFile: ""## Used to pass annotations that are used by the Prometheus installed in your cluster to select Service Monitors to work with## ref: https://github.com/coreos/prometheus-operator/blob/master/Documentation/api.md#prometheusspecannotations: {}## Metric relabel configs to apply to samples before ingestion.## [Metric Relabeling](https://prometheus.io/docs/prometheus/latest/configuration/configuration/#metric_relabel_configs)metricRelabelings: []# - action: keep# regex: 'kube_(daemonset|deployment|pod|namespace|node|statefulset).+'# sourceLabels: [__name__]## Relabel configs to apply to samples before ingestion.## [Relabeling](https://prometheus.io/docs/prometheus/latest/configuration/configuration/#relabel_config)relabelings: []# - sourceLabels: [__meta_kubernetes_pod_node_name]# separator: ;# regex: ^(.*)$# targetLabel: nodename# replacement: $1# action: replace# Extra K8s manifests to deploy
extraObjects: []# - apiVersion: secrets-store.csi.x-k8s.io/v1# kind: SecretProviderClass# metadata:# name: oauth2-proxy-secrets-store# spec:# provider: aws# parameters:# objects: |# - objectName: "oauth2-proxy"# objectType: "secretsmanager"# jmesPath:# - path: "client_id"# objectAlias: "client-id"# - path: "client_secret"# objectAlias: "client-secret"# - path: "cookie_secret"# objectAlias: "cookie-secret"# secretObjects:# - data:# - key: client-id# objectName: client-id# - key: client-secret# objectName: client-secret# - key: cookie-secret# objectName: cookie-secret# secretName: oauth2-proxy-secrets-store# type: Opaque
oauth2-proxy参数
Usage of oauth2-proxy:--acr-values string acr values string: optional--allow-query-semicolons allow the use of semicolons in query args--allowed-group strings restrict logins to members of this group (may be given multiple times)--allowed-role strings (keycloak-oidc) restrict logins to members of these roles (may be given multiple times)--alpha-config string path to alpha config file (use at your own risk - the structure in this config file may change between minor releases)
unknown flag: --debug--api-route strings return HTTP 401 instead of redirecting to authentication server if token is not valid. Format: path_regex--approval-prompt string OAuth approval_prompt (default "force")--auth-logging Log authentication attempts (default true)--auth-logging-format string Template for authentication log lines (default "{{.Client}} - {{.RequestID}} - {{.Username}} [{{.Timestamp}}] [{{.Status}}] {{.Message}}")--auth-request-response-mode string Authorization request response mode--authenticated-emails-file string authenticate against emails via file (one per line)--azure-graph-group-field id configures the group field to be used when building the groups list(id or `displayName`. Default is `id`) from Microsoft Graph(available only for v2.0 oidc url). Based on this value, the `allowed-group` config values should be adjusted accordingly. If using `id` as group field, `allowed-group` should contains groups IDs, if using `displayName` as group field, `allowed-group` should contains groups name--azure-tenant string go to a tenant-specific or common (tenant-independent) endpoint. (default "common")--backend-logout-url string url to perform a backend logout, {id_token} can be used as placeholder for the id_token--banner string custom banner string. Use "-" to disable default banner.--basic-auth-password string the password to set when passing the HTTP Basic Auth header--bearer-token-login-fallback if skip-jwt-bearer-tokens is set, fall back to normal login redirect with an invalid JWT. If false, 403 instead (default true)--bitbucket-repository string restrict logins to user with access to this repository--bitbucket-team string restrict logins to members of this team--client-id string the OAuth Client ID: ie: "123456.apps.googleusercontent.com"--client-secret string the OAuth Client Secret--client-secret-file string the file with OAuth Client Secret--code-challenge-method string use PKCE code challenges with the specified method. Either 'plain' or 'S256'--config string path to config file--convert-config-to-alpha if true, the proxy will load configuration as normal and convert existing configuration to the alpha config structure, and print it to stdout--cookie-csrf-expire duration expire timeframe for CSRF cookie (default 15m0s)--cookie-csrf-per-request When this property is set to true, then the CSRF cookie name is built based on the state and varies per request. If property is set to false, then CSRF cookie has the same name for all requests.--cookie-domain .yourcompany.com Optional cookie domains to force cookies to (ie: .yourcompany.com). The longest domain matching the request's host will be used (or the shortest cookie domain if there is no match).--cookie-expire duration expire timeframe for cookie (default 168h0m0s)--cookie-httponly set HttpOnly cookie flag (default true)--cookie-name string the name of the cookie that the oauth_proxy creates (default "_oauth2_proxy")--cookie-path string an optional cookie path to force cookies to (ie: /poc/)* (default "/")--cookie-refresh duration refresh the cookie after this duration; 0 to disable--cookie-samesite string set SameSite cookie attribute (ie: "lax", "strict", "none", or ""). --cookie-secret string the seed string for secure cookies (optionally base64 encoded)--cookie-secure set secure (HTTPS) cookie flag (default true)--custom-sign-in-logo string path or URL to an custom image for the sign_in page logo. Use "-" to disable default logo.--custom-templates-dir string path to custom html templates--display-htpasswd-form display username / password login form if an htpasswd file is provided (default true)--email-domain strings authenticate emails with the specified domain (may be given multiple times). Use * to authenticate any email--encode-state will encode oauth state with base64--entra-id-allowed-tenant strings list of tenants allowed for MS Entra ID multi-tenant application--entra-id-federated-token-auth enable oAuth client authentication with federated token projected by Azure Workload Identity plugin, instead of client secret.--errors-to-info-log Log errors to the standard logging channel instead of stderr--exclude-logging-path strings Exclude logging requests to paths (eg: '/path1,/path2,/path3')--extra-jwt-issuers strings if skip-jwt-bearer-tokens is set, a list of extra JWT issuer=audience pairs (where the issuer URL has a .well-known/openid-configuration or a .well-known/jwks.json)--flush-interval duration period between response flushing when streaming responses (default 1s)--footer string custom footer string. Use "-" to disable default footer.--force-code-challenge-method string Deprecated - use --code-challenge-method--force-https force HTTPS redirect for HTTP requests--force-json-errors will force JSON errors instead of HTTP error pages or redirects--gcp-healthchecks Enable GCP/GKE healthcheck endpoints--github-org string restrict logins to members of this organisation--github-repo string restrict logins to collaborators of this repository--github-team string restrict logins to members of this team--github-token string the token to use when verifying repository collaborators (must have push access to the repository)--github-user strings allow users with these usernames to login even if they do not belong to the specified org and team or collaborators (may be given multiple times)--gitlab-group strings restrict logins to members of this group (may be given multiple times)--gitlab-project group/project=accesslevel restrict logins to members of this project (may be given multiple times) (eg group/project=accesslevel). Access level should be a value matching Gitlab access levels (see https://docs.gitlab.com/ee/api/members.html#valid-access-levels), defaulted to 20 if absent--google-admin-email string the google admin to impersonate for api calls--google-group strings restrict logins to members of this google group (may be given multiple times).--google-service-account-json string the path to the service account json credentials--google-target-principal string the target principal to impersonate when using ADC--google-use-application-default-credentials string use application default credentials instead of service account json (i.e. GKE Workload Identity)--htpasswd-file string additionally authenticate against a htpasswd file. Entries must be created with "htpasswd -B" for bcrypt encryption--htpasswd-user-group strings the groups to be set on sessions for htpasswd users (may be given multiple times)--http-address string [http://]<addr>:<port> or unix://<path> or fd:<int> (case insensitive) to listen on for HTTP clients (default "127.0.0.1:4180")--https-address string <addr>:<port> to listen on for HTTPS clients (default ":443")--insecure-oidc-allow-unverified-email Don't fail if an email address in an id_token is not verified--insecure-oidc-skip-issuer-verification Do not verify if issuer matches OIDC discovery URL--insecure-oidc-skip-nonce skip verifying the OIDC ID Token's nonce claim (default true)--jwt-key string private key in PEM format used to sign JWT, so that you can say something like -jwt-key="${OAUTH2_PROXY_JWT_KEY}": required by login.gov--jwt-key-file string path to the private key file in PEM format used to sign the JWT so that you can say something like -jwt-key-file=/etc/ssl/private/jwt_signing_key.pem: required by login.gov--keycloak-group strings restrict logins to members of these groups (may be given multiple times)--logging-compress Should rotated log files be compressed using gzip--logging-filename string File to log requests to, empty for stdout--logging-local-time If the time in log files and backup filenames are local or UTC time (default true)--logging-max-age int Maximum number of days to retain old log files (default 7)--logging-max-backups int Maximum number of old log files to retain; 0 to disable--logging-max-size int Maximum size in megabytes of the log file before rotation (default 100)--login-url string Authentication endpoint--metrics-address string the address /metrics will be served on (e.g. ":9100")--metrics-secure-address string the address /metrics will be served on for HTTPS clients (e.g. ":9100")--metrics-tls-cert-file string path to certificate file for secure metrics server--metrics-tls-key-file string path to private key file for secure metrics server--oidc-audience-claim strings which OIDC claims are used as audience to verify against client id (default [aud])--oidc-email-claim string which OIDC claim contains the user's email (default "email")--oidc-extra-audience strings additional audiences allowed to pass audience verification--oidc-groups-claim string which OIDC claim contains the user groups (default "groups")--oidc-issuer-url string OpenID Connect issuer URL (ie: https://accounts.google.com)--oidc-jwks-url string OpenID Connect JWKS URL (ie: https://www.googleapis.com/oauth2/v3/certs)--oidc-public-key-file strings path to public key file in PEM format to use for verifying JWT tokens (may be given multiple times)--pass-access-token pass OAuth access_token to upstream via X-Forwarded-Access-Token header--pass-authorization-header pass the Authorization Header to upstream--pass-basic-auth pass HTTP Basic Auth, X-Forwarded-User and X-Forwarded-Email information to upstream (default true)--pass-host-header pass the request Host Header to upstream (default true)--pass-user-headers pass X-Forwarded-User and X-Forwarded-Email information to upstream (default true)--ping-path string the ping endpoint that can be used for basic health checks (default "/ping")--ping-user-agent string special User-Agent that will be used for basic health checks--prefer-email-to-user Prefer to use the Email address as the Username when passing information to upstream. Will only use Username if Email is unavailable, eg. htaccess authentication. Used in conjunction with -pass-basic-auth and -pass-user-headers--profile-url string Profile access endpoint--prompt string OIDC prompt--provider string OAuth provider (default "google")--provider-ca-file strings One or more paths to CA certificates that should be used when connecting to the provider. If not specified, the default Go trust sources are used instead.--provider-display-name string Provider display name--proxy-prefix string the url root path that this proxy should be nested under (e.g. /<oauth2>/sign_in) (default "/oauth2")--proxy-websockets enables WebSocket proxying (default true)--pubjwk-url string JWK pubkey access endpoint: required by login.gov--ready-path string the ready endpoint that can be used for deep health checks (default "/ready")--real-client-ip-header string Header used to determine the real IP of the client (one of: X-Forwarded-For, X-Real-IP, X-ProxyUser-IP, X-Envoy-External-Address, or CF-Connecting-IP) (default "X-Real-IP")--redeem-url string Token redemption endpoint--redirect-url string the OAuth Redirect URL. ie: "https://internalapp.yourcompany.com/oauth2/callback"--redis-ca-path string Redis custom CA path--redis-cluster-connection-urls strings List of Redis cluster connection URLs (eg redis://[USER[:PASSWORD]@]HOST[:PORT]). Used in conjunction with --redis-use-cluster--redis-connection-idle-timeout int Redis connection idle timeout seconds, if Redis timeout option is non-zero, the --redis-connection-idle-timeout must be less then Redis timeout option--redis-connection-url string URL of redis server for redis session storage (eg: redis://[USER[:PASSWORD]@]HOST[:PORT])--redis-insecure-skip-tls-verify Use insecure TLS connection to redis--redis-password --redis-connection-url Redis password. Applicable for all Redis configurations. Will override any password set in --redis-connection-url--redis-sentinel-connection-urls strings List of Redis sentinel connection URLs (eg redis://[USER[:PASSWORD]@]HOST[:PORT]). Used in conjunction with --redis-use-sentinel--redis-sentinel-master-name string Redis sentinel master name. Used in conjunction with --redis-use-sentinel--redis-sentinel-password --redis-password Redis sentinel password. Used only for sentinel connection; any redis node passwords need to use --redis-password--redis-use-cluster Connect to redis cluster. Must set --redis-cluster-connection-urls to use this feature--redis-use-sentinel Connect to redis via sentinels. Must set --redis-sentinel-master-name and --redis-sentinel-connection-urls to use this feature--redis-username --redis-connection-url Redis username. Applicable for Redis configurations where ACL has been configured. Will override any username set in --redis-connection-url--relative-redirect-url allow relative OAuth Redirect URL.--request-id-header string Request header to use as the request ID (default "X-Request-Id")--request-logging Log HTTP requests (default true)--request-logging-format string Template for HTTP request log lines (default "{{.Client}} - {{.RequestID}} - {{.Username}} [{{.Timestamp}}] {{.Host}} {{.RequestMethod}} {{.Upstream}} {{.RequestURI}} {{.Protocol}} {{.UserAgent}} {{.StatusCode}} {{.ResponseSize}} {{.RequestDuration}}")--resource string The resource that is protected (Azure AD only)--reverse-proxy are we running behind a reverse proxy, controls whether headers like X-Real-Ip are accepted--scope string OAuth scope specification--session-cookie-minimal strip OAuth tokens from cookie session stores if they aren't needed (cookie session store only)--session-store-type string the session storage provider to use (default "cookie")--set-authorization-header set Authorization response headers (useful in Nginx auth_request mode)--set-basic-auth set HTTP Basic Auth information in response (useful in Nginx auth_request mode)--set-xauthrequest set X-Auth-Request-User and X-Auth-Request-Email response headers (useful in Nginx auth_request mode)--show-debug-on-error show detailed error information on error pages (WARNING: this may contain sensitive information - do not use in production)--signature-key string GAP-Signature request signature key (algorithm:secretkey)--silence-ping-logging Disable logging of requests to ping & ready endpoints--skip-auth-preflight will skip authentication for OPTIONS requests--skip-auth-regex strings (DEPRECATED for --skip-auth-route) bypass authentication for requests path's that match (may be given multiple times)--skip-auth-route strings bypass authentication for requests that match the method & path. Format: method=path_regex OR method!=path_regex. For all methods: path_regex OR !=path_regex--skip-auth-strip-headers strips X-Forwarded-* style authentication headers & Authorization header if they would be set by oauth2-proxy (default true)--skip-claims-from-profile-url Skip loading missing claims from profile URL--skip-jwt-bearer-tokens will skip requests that have verified JWT bearer tokens (default false)--skip-oidc-discovery Skip OIDC discovery and use manually supplied Endpoints--skip-provider-button will skip sign-in-page to directly reach the next step: oauth/start--ssl-insecure-skip-verify skip validation of certificates presented when using HTTPS providers--ssl-upstream-insecure-skip-verify skip validation of certificates presented when using HTTPS upstreams--standard-logging Log standard runtime information (default true)--standard-logging-format string Template for standard log lines (default "[{{.Timestamp}}] [{{.File}}] {{.Message}}")--tls-cert-file string path to certificate file--tls-cipher-suite strings restricts TLS cipher suites to those listed (e.g. TLS_RSA_WITH_RC4_128_SHA) (may be given multiple times)--tls-key-file string path to private key file--tls-min-version string minimal TLS version for HTTPS clients (either "TLS1.2" or "TLS1.3")--trusted-ip strings list of IPs or CIDR ranges to allow to bypass authentication. WARNING: trusting by IP has inherent security flaws, read the configuration documentation for more information.--upstream strings the http url(s) of the upstream endpoint, file:// paths for static files or static://<status_code> for static response. Routing is based on the path--upstream-timeout duration maximum amount of time the server will wait for a response from the upstream (default 30s)--use-system-trust-store Determines if 'provider-ca-file' files and the system trust store are used. If set to true, your custom CA files and the system trust store are used otherwise only your custom CA files.--user-id-claim oidc-email-claim (DEPRECATED for oidc-email-claim) which claim contains the user ID (default "email")--validate-url string Access token validation endpoint--version print version string--whitelist-domain strings allowed domains for redirection after authentication. Prefix domain with a . or a *. to allow subdomains (eg .example.com, *.example.com)
Istio vs路由调整
kubectl get vs comfyui-virtualservice-exposed -o yaml
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:annotations:kubectl.kubernetes.io/last-applied-configuration: |{"apiVersion":"networking.istio.io/v1beta1","kind":"VirtualService","metadata":{"annotations":{},"name":"comfyui-virtualservice-exposed","namespace":"infrastructure"},"spec":{"gateways":["istio-system/ingressgateway"],"hosts":["comfyui.x.x.x.cn"],"http":[{"match":null,"route":[{"destination":{"host":"comfyui","port":{"number":80}},"weight":100}]}]}}creationTimestamp: "2025-02-28T09:56:39Z"generation: 4name: comfyui-virtualservice-exposednamespace: infrastructureresourceVersion: "547356253"uid: bc6b739d-918e-4206-8657-e44361a4bc9b
spec:gateways:- istio-system/ingressgatewayhosts:- comfyui.x.x.x.cnhttp:- route:- destination:host: oauth2-proxyport:number: 80weight: 100
测试
访问comfyui账密
访问comfyui界面会跳转到OAuth2-proxy认证界面后跳转到keycloak界面输入账密后才能访问comfyui



登录成功后可以在keycloak界面看到用户的session
可以在keycloak界面调整用户的session超时时间等。
reference
https://github.com/keycloak
优化容器
https://www.keycloak.org/server/containers
operator
https://www.keycloak.org/operator/installation#_installing_by_using_kubectl_without_operator_lifecycle_manager
配置文件
https://www.keycloak.org/server/configuration
OAuth2-proxy helm地址
https://artifacthub.io/packages/helm/oauth2-proxy/oauth2-proxy
相关文章:

基于OAuth2-proxy和Keycloak为comfyui实现SSO
背景 comfyui无认证被漏扫后易被rce挖矿 攻击过程 https://www.oschina.net/news/340226 https://github.com/comfyanonymous/ComfyUI/discussions/5165 阿里云漏洞库关于comfyui的漏洞 https://avd.aliyun.com/search?qcomfyui×tamp__1384n4%2BxBD0GitGQ0QD8ID%2F…...
SmartSoftHelp 之 SQL Server 数据库安全备份与安全还原详解---深度优化版:SmartSoftHelp DeepCore XSuite
SmartSoftHelp 菜单之 DBMS 数据库备份与还原 (DBBackRest) 使用实例 SQL Server 数据库备份与还原详解 SQL Server 数据库的备份与还原是管理数据库的核心任务之一,涉及本地与远程操作、大小监控及目录管理等多个方面。以下是详细说明: 一、数据库…...

Spring 代理与 Redis 分布式锁冲突:一次锁释放异常的分析与解决
Spring 代理与 Redis 分布式锁冲突:一次锁释放异常的分析与解决 Spring 代理与 Redis 分布式锁冲突:一次锁释放异常的分析与解决1. 问题现象与初步分析2 . 原因探究:代理机制对分布式锁生命周期的干扰3. 问题复现伪代码4. 解决方案࿱…...

【数据结构】队列的完整实现
队列的完整实现 队列的完整实现github地址前言1. 队列的概念及其结构1.1 概念1.2 组织结构 2. 队列的实现接口一览结构定义与架构初始化和销毁入队和出队取队头队尾数据获取size和判空 完整代码与功能测试结语 队列的完整实现 github地址 有梦想的电信狗 前言 队列&…...

2025 全球优质 AI 产品深度测评:从通用工具到垂直领域的技术突围 —— 轻量聚合工具篇
在 AI 技术爆发式增长的 2025 年,全球范围内涌现出大量兼具技术创新与场景价值的优质产品。本文从通用对话、多模态生成、开发者工具、企业级方案及垂直领域深耕五个维度,深度解析 18 款国内外标杆产品,附独家对比数据与选型策略,…...

Python爬虫实战:获取天气网最近一周北京的天气数据,为日常出行做参考
1. 引言 随着互联网技术的发展,气象数据的获取与分析已成为智慧城市建设的重要组成部分。天气网作为权威的气象信息发布平台,其数据具有较高的准确性和实时性。然而,人工获取和分析天气数据效率低下,无法满足用户对精细化、个性化气象服务的需求。本文设计并实现了一套完整…...

根据YOLO数据集标签计算检测框内目标面积占比(YOLO7-10都适用)
程序: 路径改成自己的,阈值可以修改也可以默认 #zhouzhichao #25年5月17日 #计算时频图中信号面积占检测框面积的比值import os import numpy as np import pandas as pd from PIL import Image# Define the path to the directory containing the lab…...

Helm简介、安装、配置、使用!
一、简介 Helm 是 Kubernetes 的包管理器。包管理器类似于我们在 Ubuntu 中使用的apt、Centos中使用的yum 或者Python中的 pip 一样,能快速查找、下载和安装软件包。Helm 由客户端组件 helm 和服务端组件 Tiller 组成, 能够将一组K8S资源打包统一管理, 是查找、共享…...

LLM笔记(九)KV缓存(2)
文章目录 1. 背景与动机2. 不使用 KV Cache 的情形2.1 矩阵形式展开2.2 计算复杂度 3. 使用 KV Cache 的优化3.1 核心思想3.2 矩阵形式展开3.3 计算复杂度对比 4. 总结5. GPT-2 中 KV 缓存的实现分析5.1 缓存的数据结构与类型5.2 在注意力机制 (GPT2Attention) 中使用缓存5.3 缓…...

开发 前端搭建npm v11.4.0 is known not to run on Node.js v14.18.1.
错误nodejs 和npm 版本不一致 ERROR: npm v11.4.0 is known not to run on Node.js v14.18.1. This version of npm supports the following node versions: ^20.17.0 || >22.9.0. You can find the latest version at https://nodejs.org/. ERROR: D:\softTool\node-v14…...

LVS 负载均衡集群应用实战
前提:三台虚拟机,有nginx,要做负载 1. LVS-server 安装lvs管理软件 [root@lvs-server ~]# yum -y install ipvsadm 程序包:ipvsadm(LVS管理工具) 主程序:/usr/sbin/ipvsadm 规则保存工具:/usr/sbin/ipvsadm-save > /path/to/file 配置文件:/etc/sysconfig/ipvsad…...

MySQL——基本查询内置函数
目录 CRUD Create Retrieve where order by limit Update Delete 去重操作 聚合函数 聚合统计 内置函数 日期函数 字符函数 数学函数 其它函数 实战OJ 批量插入数据 找出所有员工当前薪水salary情况 查找最晚入职员工的所有信息 查找入职员工时间升序排…...

Day34打卡 @浙大疏锦行
知识点回归: CPU性能的查看:看架构代际、核心数、线程数GPU性能的查看:看显存、看级别、看架构代际GPU训练的方法:数据和模型移动到GPU device上类的call方法:为什么定义前向传播时可以直接写作self.fc1(x) 作业 计算资…...
Docker安装Jitsi Meet指南-使用内网IP访问)
【Jitsi Meet】(腾讯会议的平替)Docker安装Jitsi Meet指南-使用内网IP访问
Docker安装Jitsi Meet指南-使用内网IP访问 下载官方代码配置环境变量复制示例环境文件并修改配置:编辑 .env 文件: 修改 docker-compose.yml 文件生成自签名证书启动服务最终验证 腾讯会议的平替。我们是每天开早晚会的,都是使用腾讯会议。腾…...

AdGuard解锁高级版(Nightly)_v4.10.36 安卓去除手机APP广告
AdGuard解锁高级版(Nightly)_v4.10.36 安卓去除手机APP广告 AdGuard Nightly是AdGuard团队为及时更新软件而推出的最新测试版本,适合追求最新功能和愿意尝试新版本的用户。但使用时需注意其潜在的不稳定性和风险。…...

C++修炼:红黑树的模拟实现
Hello大家好!很高兴我们又见面啦!给生活添点passion,开始今天的编程之路! 我的博客:<但凡. 我的专栏:《编程之路》、《数据结构与算法之美》、《题海拾贝》、《C修炼之路》 欢迎点赞,关注&am…...

基于Python+YOLO模型的手势识别系统
本项目是一个基于Python、YOLO模型、PyQt5的实时手势识别系统,通过摄像头或导入图片、视频,能够实时识别并分类不同的手势动作。系统采用训练好的深度学习模型进行手势检测和识别,可应用于人机交互、智能控制等多种场景。 1、系统主要功能包…...

自制操作系统day10叠加处理
day10叠加处理 叠加处理(harib07b) 现在是鼠标的叠加处理,以后还有窗口的叠加处理 涉及图层 最上面小图层是鼠标指针,最下面的一张图层用来存放桌面壁纸。移动图层的方法实现鼠标指针的移动以及窗口的移动。 struct SHEET { u…...

docker初学
加载镜像:docker load -i ubuntu.tar 导出镜像:docker save -o ubuntu1.tar ubuntu 运行: docker run -it --name mu ubuntu /bin/bash ocker run -dit --name mmus docker.1ms.run/library/ubuntu /bin/bash 进入容器:docke…...

## Docker 中 Elasticsearch 启动失败:日志文件权限问题排查与解决
好的,这是一份关于你遇到的 Docker Elasticsearch 启动报错问题的笔记,包含问题描述、我的分析判断以及最终的解决方案,适合用于整理成文章。 Docker 中 Elasticsearch 启动失败:日志文件权限问题排查与解决 在使用 Docker部署 E…...

鸿蒙Flutter实战:23-混合开发详解-3-源码模式引入
引言 在前面的文章混合开发详解-2-Har包模式引入中,我们介绍了如何将 Flutter 模块打包成 Har 包,并引入到原生鸿蒙工程中。本文中,我们将介绍如何通过源码依赖的方式,将 Flutter 模块引入到原生鸿蒙工程中。 创建工作 创建一个…...

leetcode:2469. 温度转换(python3解法,数学相关算法题)
难度:简单 给你一个四舍五入到两位小数的非负浮点数 celsius 来表示温度,以 摄氏度(Celsius)为单位。 你需要将摄氏度转换为 开氏度(Kelvin)和 华氏度(Fahrenheit),并以数…...

【软件安装】Windows操作系统中安装mongodb数据库和mongo-shell工具
这篇文章,主要介绍Windows操作系统中如何安装mongodb数据库和mongo-shell工具。 目录 一、安装mongodb数据库 1.1、下载mongodb安装包 1.2、添加配置文件 1.3、编写启动脚本(可选) 1.4、启动服务 二、安装mongo-shell工具 2.1、下载mo…...

跨域问题及其CORS解决方案:gin框架中配置跨域
一、同源策略 浏览器的同源策略(Same-Origin Policy)要求:只有协议、域名和端口都相同的请求才被视为同源,才允许正常访问。 两个URL在以下三个方面完全相同时称为"同源": 协议相同(如都是http或…...

记共享元素动画导致的内存泄露
最近在给项目的预览图片页增加共享元素动画的时候,发现了LeakCanary一直报内存泄露。 LeakCanary日志信息 ┬─── │ GC Root: Thread object │ ├─ java.lang.Thread instance │ Leaking: NO (the main thread always runs) │ Thread name: main │ …...

Flyweight(享元)设计模式 软考 享元 和 代理属于结构型设计模式
1.目的:运用共享技术有效地支持大量细粒度的对象 Flyweight(享元)设计模式 是一种结构型设计模式,它的核心目的是通过共享对象来减少内存消耗,特别是在需要大量相似对象的场景中。Flyweight 模式通过将对象的共享细节与…...

Win/Linux安装flash attention2
1.Win 安装Flash_attn (1)第一步:下载flash_attn-xxx.whl 文件 在 1)地址1:HuggingFace 官网 Flash-attn页面 2)地址2:Github 地址 下载对应cuda、torch、python版本的whl文件; …...

【原创】ubuntu22.04下载编译AOSP 15
安装依赖的库,顺便把vim 也安装一下 sudo apt-get install vim sudo apt-get install git gnupg flex bison build-essential zip curl zlib1g-dev libc6-dev-i386 x11proto-core-dev libx11-dev lib32z1-dev libgl1-mesa-dev libxml2-utils xsltproc unzip font…...

服务器网络配置 netplan一个网口配置两个ip(双ip、辅助ip、别名IP别名)
文章目录 问答 问 # This is the network config written by subiquity network:ethernets:enp125s0f0:dhcp4: noaddresses: [192.168.90.180/24]gateway4: 192.168.90.1nameservers:addresses:- 172.0.0.207- 172.0.0.208enp125s0f1:dhcp4: trueenp125s0f2:dhcp4: trueenp125…...
响应面法(Response Surface Methodology ,RSM)
响应面法是一种结合统计学和数学建模的实验优化技术,通过有限的实验数据,建立输入变量与输出响应之间的数学模型,找到最优操作条件。 1.RSM定义 RSM通过设计实验、拟合数学模型(如多项式方程)和分析响应曲面ÿ…...
