识别密文加密类型
离线密码破解:
离线不会触发密码锁定机制
不会产生大量登录失败日志引起管理员注意
HASH识别工具(识别哈希类型):
hash-identifier
Hashid
yara规则匹配文件得到特定加密算法
一、hash-identifier
Kali Linux提供工具hash-identifier来识别加密类型。
运行该命令,然后输入哈希密文,就可以得到密文所使用的哈希算法类型。有了这个算法类型,再选择对应的工具或者彩虹表,获取密码明文就容易多了。
核心代码如下:逻辑匹配
Hash_ID.py:
#!/usr/bin/env python
# encoding: utf-8
# Hash Identifier v1.1
# By Zion3R
# www.Blackploit.com
# Root@Blackploit.comlogo=''' ########################################################################## __ __ __ ______ _____ ## /\ \/\ \ /\ \ /\__ _\ /\ _ `\ ## \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ ## \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ ## \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ ## \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ ## \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.1 ## By Zion3R ## www.Blackploit.com ## Root@Blackploit.com ##########################################################################'''algorithms={"102020":"ADLER-32", "102040":"CRC-32", "102060":"CRC-32B", "101020":"CRC-16", "101040":"CRC-16-CCITT", "104020":"DES(Unix)", "101060":"FCS-16", "103040":"GHash-32-3", "103020":"GHash-32-5", "115060":"GOST R 34.11-94", "109100":"Haval-160", "109200":"Haval-160(HMAC)", "110040":"Haval-192", "110080":"Haval-192(HMAC)", "114040":"Haval-224", "114080":"Haval-224(HMAC)", "115040":"Haval-256", "115140":"Haval-256(HMAC)", "107080":"Lineage II C4", "106025":"Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))", "102080":"XOR-32", "105060":"MD5(Half)", "105040":"MD5(Middle)", "105020":"MySQL", "107040":"MD5(phpBB3)", "107060":"MD5(Unix)", "107020":"MD5(Wordpress)", "108020":"MD5(APR)", "106160":"Haval-128", "106165":"Haval-128(HMAC)", "106060":"MD2", "106120":"MD2(HMAC)", "106040":"MD4", "106100":"MD4(HMAC)", "106020":"MD5", "106080":"MD5(HMAC)", "106140":"MD5(HMAC(Wordpress))", "106029":"NTLM", "106027":"RAdmin v2.x", "106180":"RipeMD-128", "106185":"RipeMD-128(HMAC)", "106200":"SNEFRU-128", "106205":"SNEFRU-128(HMAC)", "106220":"Tiger-128", "106225":"Tiger-128(HMAC)", "106240":"md5($pass.$salt)", "106260":"md5($salt.'-'.md5($pass))", "106280":"md5($salt.$pass)", "106300":"md5($salt.$pass.$salt)", "106320":"md5($salt.$pass.$username)", "106340":"md5($salt.md5($pass))", "106360":"md5($salt.md5($pass).$salt)", "106380":"md5($salt.md5($pass.$salt))", "106400":"md5($salt.md5($salt.$pass))", "106420":"md5($salt.md5(md5($pass).$salt))", "106440":"md5($username.0.$pass)", "106460":"md5($username.LF.$pass)", "106480":"md5($username.md5($pass).$salt)", "106500":"md5(md5($pass))", "106520":"md5(md5($pass).$salt)", "106540":"md5(md5($pass).md5($salt))", "106560":"md5(md5($salt).$pass)", "106580":"md5(md5($salt).md5($pass))", "106600":"md5(md5($username.$pass).$salt)", "106620":"md5(md5(md5($pass)))", "106640":"md5(md5(md5(md5($pass))))", "106660":"md5(md5(md5(md5(md5($pass)))))", "106680":"md5(sha1($pass))", "106700":"md5(sha1(md5($pass)))", "106720":"md5(sha1(md5(sha1($pass))))", "106740":"md5(strtoupper(md5($pass)))", "109040":"MySQL5 - SHA-1(SHA-1($pass))", "109060":"MySQL 160bit - SHA-1(SHA-1($pass))", "109180":"RipeMD-160(HMAC)", "109120":"RipeMD-160", "109020":"SHA-1", "109140":"SHA-1(HMAC)", "109220":"SHA-1(MaNGOS)", "109240":"SHA-1(MaNGOS2)", "109080":"Tiger-160", "109160":"Tiger-160(HMAC)", "109260":"sha1($pass.$salt)", "109280":"sha1($salt.$pass)", "109300":"sha1($salt.md5($pass))", "109320":"sha1($salt.md5($pass).$salt)", "109340":"sha1($salt.sha1($pass))", "109360":"sha1($salt.sha1($salt.sha1($pass)))", "109380":"sha1($username.$pass)", "109400":"sha1($username.$pass.$salt)", "1094202":"sha1(md5($pass))", "109440":"sha1(md5($pass).$salt)", "109460":"sha1(md5(sha1($pass)))", "109480":"sha1(sha1($pass))", "109500":"sha1(sha1($pass).$salt)", "109520":"sha1(sha1($pass).substr($pass,0,3))", "109540":"sha1(sha1($salt.$pass))", "109560":"sha1(sha1(sha1($pass)))", "109580":"sha1(strtolower($username).$pass)", "110020":"Tiger-192", "110060":"Tiger-192(HMAC)", "112020":"md5($pass.$salt) - Joomla", "113020":"SHA-1(Django)", "114020":"SHA-224", "114060":"SHA-224(HMAC)", "115080":"RipeMD-256", "115160":"RipeMD-256(HMAC)", "115100":"SNEFRU-256", "115180":"SNEFRU-256(HMAC)", "115200":"SHA-256(md5($pass))", "115220":"SHA-256(sha1($pass))", "115020":"SHA-256", "115120":"SHA-256(HMAC)", "116020":"md5($pass.$salt) - Joomla", "116040":"SAM - (LM_hash:NT_hash)", "117020":"SHA-256(Django)", "118020":"RipeMD-320", "118040":"RipeMD-320(HMAC)", "119020":"SHA-384", "119040":"SHA-384(HMAC)", "120020":"SHA-256", "121020":"SHA-384(Django)", "122020":"SHA-512", "122060":"SHA-512(HMAC)", "122040":"Whirlpool", "122080":"Whirlpool(HMAC)"}# hash.islower() minusculas
# hash.isdigit() numerico
# hash.isalpha() letras
# hash.isalnum() alfanumericodef CRC16():hs='4607'if len(hash)==len(hs) and hash.isalpha()==False and hash.isalnum()==True:jerar.append("101020")
def CRC16CCITT():hs='3d08'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("101040")
def FCS16():hs='0e5b'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("101060")def CRC32():hs='b33fd057'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("102040")
def ADLER32():hs='0607cb42'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("102020")
def CRC32B():hs='b764a0d9'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("102060")
def XOR32():hs='0000003f'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("102080")def GHash323():hs='80000000'if len(hash)==len(hs) and hash.isdigit()==True and hash.isalpha()==False and hash.isalnum()==True:jerar.append("103040")
def GHash325():hs='85318985'if len(hash)==len(hs) and hash.isdigit()==True and hash.isalpha()==False and hash.isalnum()==True:jerar.append("103020")def DESUnix():hs='ZiY8YtDKXJwYQ'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False:jerar.append("104020")def MD5Half():hs='ae11fd697ec92c7c'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("105060")
def MD5Middle():hs='7ec92c7c98de3fac'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("105040")
def MySQL():hs='63cea4673fd25f46'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("105020")def DomainCachedCredentials():hs='f42005ec1afe77967cbc83dce1b4d714'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106025")
def Haval128():hs='d6e3ec49aa0f138a619f27609022df10'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106160")
def Haval128HMAC():hs='3ce8b0ffd75bc240fc7d967729cd6637'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106165")
def MD2():hs='08bbef4754d98806c373f2cd7d9a43c4'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106060")
def MD2HMAC():hs='4b61b72ead2b0eb0fa3b8a56556a6dca'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106120")
def MD4():hs='a2acde400e61410e79dacbdfc3413151'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106040")
def MD4HMAC():hs='6be20b66f2211fe937294c1c95d1cd4f'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106100")
def MD5():hs='ae11fd697ec92c7c98de3fac23aba525'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106020")
def MD5HMAC():hs='d57e43d2c7e397bf788f66541d6fdef9'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106080")
def MD5HMACWordpress():hs='3f47886719268dfa83468630948228f6'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106140")
def NTLM():hs='cc348bace876ea440a28ddaeb9fd3550'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106029")
def RAdminv2x():hs='baea31c728cbf0cd548476aa687add4b'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106027")
def RipeMD128():hs='4985351cd74aff0abc5a75a0c8a54115'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106180")
def RipeMD128HMAC():hs='ae1995b931cf4cbcf1ac6fbf1a83d1d3'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106185")
def SNEFRU128():hs='4fb58702b617ac4f7ca87ec77b93da8a'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106200")
def SNEFRU128HMAC():hs='59b2b9dcc7a9a7d089cecf1b83520350'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106205")
def Tiger128():hs='c086184486ec6388ff81ec9f23528727'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106220")
def Tiger128HMAC():hs='c87032009e7c4b2ea27eb6f99723454b'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106225")
def md5passsalt():hs='5634cc3b922578434d6e9342ff5913f7'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106240")
def md5saltmd5pass():hs='245c5763b95ba42d4b02d44bbcd916f1'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106260")
def md5saltpass():hs='22cc5ce1a1ef747cd3fa06106c148dfa'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106280")
def md5saltpasssalt():hs='469e9cdcaff745460595a7a386c4db0c'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106300")
def md5saltpassusername():hs='9ae20f88189f6e3a62711608ddb6f5fd'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106320")
def md5saltmd5pass():hs='aca2a052962b2564027ee62933d2382f'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106340")
def md5saltmd5passsalt():hs='de0237dc03a8efdf6552fbe7788b2fdd'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106360")
def md5saltmd5passsalt():hs='5b8b12ca69d3e7b2a3e2308e7bef3e6f'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106380")
def md5saltmd5saltpass():hs='d8f3b3f004d387086aae24326b575b23'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106400")
def md5saltmd5md5passsalt():hs='81f181454e23319779b03d74d062b1a2'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106420")
def md5username0pass():hs='e44a60f8f2106492ae16581c91edb3ba'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106440")
def md5usernameLFpass():hs='654741780db415732eaee12b1b909119'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106460")
def md5usernamemd5passsalt():hs='954ac5505fd1843bbb97d1b2cda0b98f'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106480")
def md5md5pass():hs='a96103d267d024583d5565436e52dfb3'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106500")
def md5md5passsalt():hs='5848c73c2482d3c2c7b6af134ed8dd89'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106520")
def md5md5passmd5salt():hs='8dc71ef37197b2edba02d48c30217b32'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106540")
def md5md5saltpass():hs='9032fabd905e273b9ceb1e124631bd67'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106560")
def md5md5saltmd5pass():hs='8966f37dbb4aca377a71a9d3d09cd1ac'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106580")
def md5md5usernamepasssalt():hs='4319a3befce729b34c3105dbc29d0c40'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106600")
def md5md5md5pass():hs='ea086739755920e732d0f4d8c1b6ad8d'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106620")
def md5md5md5md5pass():hs='02528c1f2ed8ac7d83fe76f3cf1c133f'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106640")
def md5md5md5md5md5pass():hs='4548d2c062933dff53928fd4ae427fc0'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106660")
def md5sha1pass():hs='cb4ebaaedfd536d965c452d9569a6b1e'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106680")
def md5sha1md5pass():hs='099b8a59795e07c334a696a10c0ebce0'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106700")
def md5sha1md5sha1pass():hs='06e4af76833da7cc138d90602ef80070'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106720")
def md5strtouppermd5pass():hs='519de146f1a658ab5e5e2aa9b7d2eec8'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("106740")def LineageIIC4():hs='0x49a57f66bd3d5ba6abda5579c264a0e4'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True and hash[0:2].find('0x')==0:jerar.append("107080")
def MD5phpBB3():hs='$H$9kyOtE8CDqMJ44yfn9PFz2E.L2oVzL1'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==False and hash[0:3].find('$H$')==0:jerar.append("107040")
def MD5Unix():hs='$1$cTuJH0Ju$1J8rI.mJReeMvpKUZbSlY/'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==False and hash[0:3].find('$1$')==0:jerar.append("107060")
def MD5Wordpress():hs='$P$BiTOhOj3ukMgCci2juN0HRbCdDRqeh.'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==False and hash[0:3].find('$P$')==0:jerar.append("107020")def MD5APR():hs='$apr1$qAUKoKlG$3LuCncByN76eLxZAh/Ldr1'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash[0:4].find('$apr')==0:jerar.append("108020")def Haval160():hs='a106e921284dd69dad06192a4411ec32fce83dbb'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109100")
def Haval160HMAC():hs='29206f83edc1d6c3f680ff11276ec20642881243'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109200")
def MySQL5():hs='9bb2fb57063821c762cc009f7584ddae9da431ff'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109040")
def MySQL160bit():hs='*2470c0c06dee42fd1618bb99005adca2ec9d1e19'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==False and hash[0:1].find('*')==0:jerar.append("109060")
def RipeMD160():hs='dc65552812c66997ea7320ddfb51f5625d74721b'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109120")
def RipeMD160HMAC():hs='ca28af47653b4f21e96c1235984cb50229331359'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109180")
def SHA1():hs='4a1d4dbc1e193ec3ab2e9213876ceb8f4db72333'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109020")
def SHA1HMAC():hs='6f5daac3fee96ba1382a09b1ba326ca73dccf9e7'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109140")
def SHA1MaNGOS():hs='a2c0cdb6d1ebd1b9f85c6e25e0f8732e88f02f96'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109220")
def SHA1MaNGOS2():hs='644a29679136e09d0bd99dfd9e8c5be84108b5fd'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109240")
def Tiger160():hs='c086184486ec6388ff81ec9f235287270429b225'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109080")
def Tiger160HMAC():hs='6603161719da5e56e1866e4f61f79496334e6a10'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109160")
def sha1passsalt():hs='f006a1863663c21c541c8d600355abfeeaadb5e4'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109260")
def sha1saltpass():hs='299c3d65a0dcab1fc38421783d64d0ecf4113448'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109280")
def sha1saltmd5pass():hs='860465ede0625deebb4fbbedcb0db9dc65faec30'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109300")
def sha1saltmd5passsalt():hs='6716d047c98c25a9c2cc54ee6134c73e6315a0ff'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109320")
def sha1saltsha1pass():hs='58714327f9407097c64032a2fd5bff3a260cb85f'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109340")
def sha1saltsha1saltsha1pass():hs='cc600a2903130c945aa178396910135cc7f93c63'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109360")
def sha1usernamepass():hs='3de3d8093bf04b8eb5f595bc2da3f37358522c9f'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109380")
def sha1usernamepasssalt():hs='00025111b3c4d0ac1635558ce2393f77e94770c5'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109400")
def sha1md5pass():hs='fa960056c0dea57de94776d3759fb555a15cae87'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("1094202")
def sha1md5passsalt():hs='1dad2b71432d83312e61d25aeb627593295bcc9a'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109440")
def sha1md5sha1pass():hs='8bceaeed74c17571c15cdb9494e992db3c263695'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109460")
def sha1sha1pass():hs='3109b810188fcde0900f9907d2ebcaa10277d10e'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109480")
def sha1sha1passsalt():hs='780d43fa11693b61875321b6b54905ee488d7760'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109500")
def sha1sha1passsubstrpass03():hs='5ed6bc680b59c580db4a38df307bd4621759324e'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109520")
def sha1sha1saltpass():hs='70506bac605485b4143ca114cbd4a3580d76a413'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109540")
def sha1sha1sha1pass():hs='3328ee2a3b4bf41805bd6aab8e894a992fa91549'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109560")
def sha1strtolowerusernamepass():hs='79f575543061e158c2da3799f999eb7c95261f07'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("109580")def Haval192():hs='cd3a90a3bebd3fa6b6797eba5dab8441f16a7dfa96c6e641'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("110040")
def Haval192HMAC():hs='39b4d8ecf70534e2fd86bb04a877d01dbf9387e640366029'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("110080")
def Tiger192():hs='c086184486ec6388ff81ec9f235287270429b2253b248a70'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("110020")
def Tiger192HMAC():hs='8e914bb64353d4d29ab680e693272d0bd38023afa3943a41'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("110060")def MD5passsaltjoomla1():hs='35d1c0d69a2df62be2df13b087343dc9:BeKMviAfcXeTPTlX'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==False and hash[32:33].find(':')==0:jerar.append("112020")def SHA1Django():hs='sha1$Zion3R$299c3d65a0dcab1fc38421783d64d0ecf4113448'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==False and hash[0:5].find('sha1$')==0:jerar.append("113020")def Haval224():hs='f65d3c0ef6c56f4c74ea884815414c24dbf0195635b550f47eac651a'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("114040")
def Haval224HMAC():hs='f10de2518a9f7aed5cf09b455112114d18487f0c894e349c3c76a681'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("114080")
def SHA224():hs='e301f414993d5ec2bd1d780688d37fe41512f8b57f6923d054ef8e59'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("114020")
def SHA224HMAC():hs='c15ff86a859892b5e95cdfd50af17d05268824a6c9caaa54e4bf1514'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("114060")def SHA256():hs='2c740d20dab7f14ec30510a11f8fd78b82bc3a711abe8a993acdb323e78e6d5e'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("115020")
def SHA256HMAC():hs='d3dd251b7668b8b6c12e639c681e88f2c9b81105ef41caccb25fcde7673a1132'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("115120")
def Haval256():hs='7169ecae19a5cd729f6e9574228b8b3c91699175324e6222dec569d4281d4a4a'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("115040")
def Haval256HMAC():hs='6aa856a2cfd349fb4ee781749d2d92a1ba2d38866e337a4a1db907654d4d4d7a'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("115140")
def GOSTR341194():hs='ab709d384cce5fda0793becd3da0cb6a926c86a8f3460efb471adddee1c63793'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("115060")
def RipeMD256():hs='5fcbe06df20ce8ee16e92542e591bdea706fbdc2442aecbf42c223f4461a12af'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("115080")
def RipeMD256HMAC():hs='43227322be1b8d743e004c628e0042184f1288f27c13155412f08beeee0e54bf'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("115160")
def SNEFRU256():hs='3a654de48e8d6b669258b2d33fe6fb179356083eed6ff67e27c5ebfa4d9732bb'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("115100")
def SNEFRU256HMAC():hs='4e9418436e301a488f675c9508a2d518d8f8f99e966136f2dd7e308b194d74f9'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("115180")
def SHA256md5pass():hs='b419557099cfa18a86d1d693e2b3b3e979e7a5aba361d9c4ec585a1a70c7bde4'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("115200")
def SHA256sha1pass():hs='afbed6e0c79338dbfe0000efe6b8e74e3b7121fe73c383ae22f5b505cb39c886'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("115220")def MD5passsaltjoomla2():hs='fb33e01e4f8787dc8beb93dac4107209:fxJUXVjYRafVauT77Cze8XwFrWaeAYB2'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==False and hash[32:33].find(':')==0:jerar.append("116020")
def SAM():hs='4318B176C3D8E3DEAAD3B435B51404EE:B7C899154197E8A2A33121D76A240AB5'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==False and hash.islower()==False and hash[32:33].find(':')==0:jerar.append("116040")def SHA256Django():hs='sha256$Zion3R$9e1a08aa28a22dfff722fad7517bae68a55444bb5e2f909d340767cec9acf2c3'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==False and hash[0:6].find('sha256')==0:jerar.append("117020")def RipeMD320():hs='b4f7c8993a389eac4f421b9b3b2bfb3a241d05949324a8dab1286069a18de69aaf5ecc3c2009d8ef'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("118020")
def RipeMD320HMAC():hs='244516688f8ad7dd625836c0d0bfc3a888854f7c0161f01de81351f61e98807dcd55b39ffe5d7a78'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("118040")def SHA384():hs='3b21c44f8d830fa55ee9328a7713c6aad548fe6d7a4a438723a0da67c48c485220081a2fbc3e8c17fd9bd65f8d4b4e6b'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("119020")
def SHA384HMAC():hs='bef0dd791e814d28b4115eb6924a10beb53da47d463171fe8e63f68207521a4171219bb91d0580bca37b0f96fddeeb8b'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("119040")def SHA256s():hs='$6$g4TpUQzk$OmsZBJFwvy6MwZckPvVYfDnwsgktm2CckOlNJGy9HNwHSuHFvywGIuwkJ6Bjn3kKbB6zoyEjIYNMpHWBNxJ6g.'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==False and hash[0:3].find('$6$')==0:jerar.append("120020")def SHA384Django():hs='sha384$Zion3R$88cfd5bc332a4af9f09aa33a1593f24eddc01de00b84395765193c3887f4deac46dc723ac14ddeb4d3a9b958816b7bba'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==False and hash[0:6].find('sha384')==0:print " [+] SHA-384(Django)"jerar.append("121020")def SHA512():hs='ea8e6f0935b34e2e6573b89c0856c81b831ef2cadfdee9f44eb9aa0955155ba5e8dd97f85c73f030666846773c91404fb0e12fb38936c56f8cf38a33ac89a24e'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("122020")
def SHA512HMAC():hs='dd0ada8693250b31d9f44f3ec2d4a106003a6ce67eaa92e384b356d1b4ef6d66a818d47c1f3a2c6e8a9a9b9bdbd28d485e06161ccd0f528c8bbb5541c3fef36f'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("122060")
def Whirlpool():hs='76df96157e632410998ad7f823d82930f79a96578acc8ac5ce1bfc34346cf64b4610aefa8a549da3f0c1da36dad314927cebf8ca6f3fcd0649d363c5a370dddb'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("122040")
def WhirlpoolHMAC():hs='77996016cf6111e97d6ad31484bab1bf7de7b7ee64aebbc243e650a75a2f9256cef104e504d3cf29405888fca5a231fcac85d36cd614b1d52fce850b53ddf7f9'if len(hash)==len(hs) and hash.isdigit()==False and hash.isalpha()==False and hash.isalnum()==True:jerar.append("122080")print logo
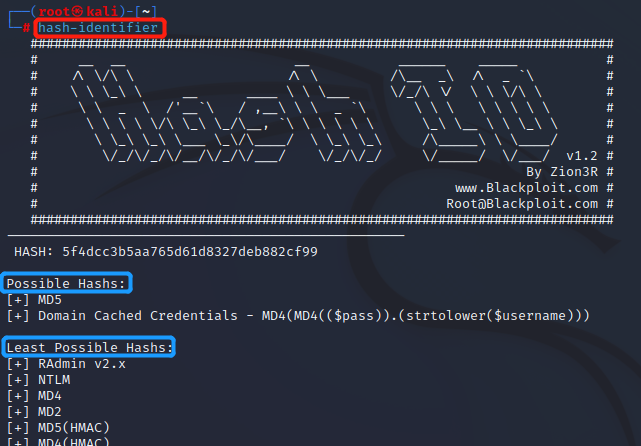
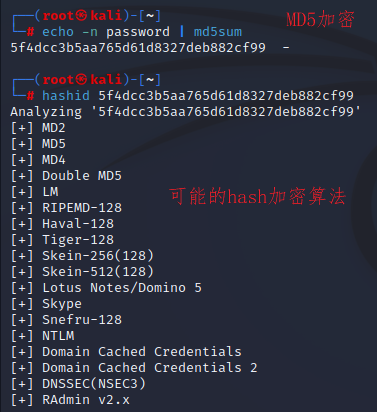
while True:jerar=[]print """-------------------------------------------------------------------------"""hash = raw_input(" HASH: ")ADLER32(); CRC16(); CRC16CCITT(); CRC32(); CRC32B(); DESUnix(); DomainCachedCredentials(); FCS16(); GHash323(); GHash325(); GOSTR341194(); Haval128(); Haval128HMAC(); Haval160(); Haval160HMAC(); Haval192(); Haval192HMAC(); Haval224(); Haval224HMAC(); Haval256(); Haval256HMAC(); LineageIIC4(); MD2(); MD2HMAC(); MD4(); MD4HMAC(); MD5(); MD5APR(); MD5HMAC(); MD5HMACWordpress(); MD5phpBB3(); MD5Unix(); MD5Wordpress(); MD5Half(); MD5Middle(); MD5passsaltjoomla1(); MD5passsaltjoomla2(); MySQL(); MySQL5(); MySQL160bit(); NTLM(); RAdminv2x(); RipeMD128(); RipeMD128HMAC(); RipeMD160(); RipeMD160HMAC(); RipeMD256(); RipeMD256HMAC(); RipeMD320(); RipeMD320HMAC(); SAM(); SHA1(); SHA1Django(); SHA1HMAC(); SHA1MaNGOS(); SHA1MaNGOS2(); SHA224(); SHA224HMAC(); SHA256(); SHA256s(); SHA256Django(); SHA256HMAC(); SHA256md5pass(); SHA256sha1pass(); SHA384(); SHA384Django(); SHA384HMAC(); SHA512(); SHA512HMAC(); SNEFRU128(); SNEFRU128HMAC(); SNEFRU256(); SNEFRU256HMAC(); Tiger128(); Tiger128HMAC(); Tiger160(); Tiger160HMAC(); Tiger192(); Tiger192HMAC(); Whirlpool(); WhirlpoolHMAC(); XOR32(); md5passsalt(); md5saltmd5pass(); md5saltpass(); md5saltpasssalt(); md5saltpassusername(); md5saltmd5pass(); md5saltmd5passsalt(); md5saltmd5passsalt(); md5saltmd5saltpass(); md5saltmd5md5passsalt(); md5username0pass(); md5usernameLFpass(); md5usernamemd5passsalt(); md5md5pass(); md5md5passsalt(); md5md5passmd5salt(); md5md5saltpass(); md5md5saltmd5pass(); md5md5usernamepasssalt(); md5md5md5pass(); md5md5md5md5pass(); md5md5md5md5md5pass(); md5sha1pass(); md5sha1md5pass(); md5sha1md5sha1pass(); md5strtouppermd5pass(); sha1passsalt(); sha1saltpass(); sha1saltmd5pass(); sha1saltmd5passsalt(); sha1saltsha1pass(); sha1saltsha1saltsha1pass(); sha1usernamepass(); sha1usernamepasssalt(); sha1md5pass(); sha1md5passsalt(); sha1md5sha1pass(); sha1sha1pass(); sha1sha1passsalt(); sha1sha1passsubstrpass03(); sha1sha1saltpass(); sha1sha1sha1pass(); sha1strtolowerusernamepass()if len(jerar)==0:print ""print " Not Found."elif len(jerar)>2:jerar.sort()print ""print "Possible Hashs:"print "[+] ",algorithms[jerar[0]]print "[+] ",algorithms[jerar[1]]print ""print "Least Possible Hashs:"for a in range(int(len(jerar))-2):print "[+] ",algorithms[jerar[a+2]]else:jerar.sort()print ""print "Possible Hashs:"for a in range(len(jerar)):print "[+] ",algorithms[jerar[a]]hash-identifier 它会列出最有可能的两种加密算法:Possible Hashs:和可能性不大的Least Possible Hashs:
5f4dcc3b5aa765d61d8327deb882cf99
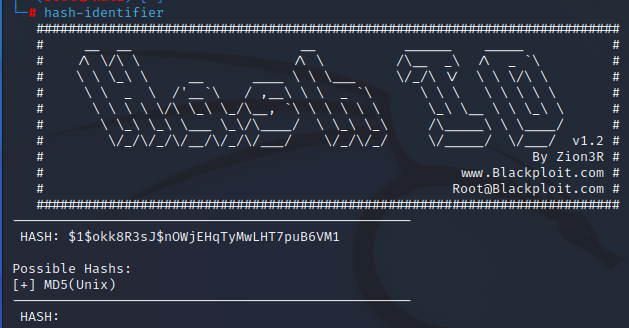
$1$okk8R3sJ$nOWjEHqTyMwLHT7puB6VM1
二、hashid
2.1、介绍
识别用于加密数据的不同类型的哈希,尤其是密码。
这个工具是用来代替hash-identifier的,因为hash-identifier已经过时啦!
hashID 是一个用 Python3 编写的工具,它支持使用正则表达式识别 220 多种唯一的哈希类型。可在此处找找到支持的哈希的详细列表。
它能够识别单个哈希,解析文件或读取多个文件并标识其中的哈希。 hashID还能够在其输出中包含相应的hashcat模式和/或JohnTheRipper格式。
hashID 在任何平台上都可以与 Python2 ≥ 2.7.x 或 Python3 ≥ 3.3 开箱即用。
核心代码:正则匹配
hashid.py:
#!/usr/bin/env python3
# -*- coding: utf-8 -*-# hashid.py - Software to identify the different types of hashes
# Copyright (C) 2013-2015 by c0re <c0re@psypanda.org>
#
# This program is free software: you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation, either version 3 of the License, or
# (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License
# along with this program. If not, see <http://www.gnu.org/licenses/>.import io
import os
import re
import sys
import argparse
from collections import namedtuple__author__ = "c0re"
__version__ = "3.2.0-dev"
__github__ = "https://github.com/psypanda/hashID"
__license__ = "License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>"
__banner__ = "hashID v{0} by {1} ({2})".format(__version__, __author__, __github__)Prototype = namedtuple('Prototype', ['regex', 'modes'])
HashInfo = namedtuple('HashInfo', ['name', 'hashcat', 'john', 'extended'])prototypes = [Prototype(regex=re.compile(r'^[a-f0-9]{4}$', re.IGNORECASE),modes=[HashInfo(name='CRC-16', hashcat=None, john=None, extended=False),HashInfo(name='CRC-16-CCITT', hashcat=None, john=None, extended=False),HashInfo(name='FCS-16', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{8}$', re.IGNORECASE),modes=[HashInfo(name='Adler-32', hashcat=None, john=None, extended=False),HashInfo(name='CRC-32B', hashcat=None, john=None, extended=False),HashInfo(name='FCS-32', hashcat=None, john=None, extended=False),HashInfo(name='GHash-32-3', hashcat=None, john=None, extended=False),HashInfo(name='GHash-32-5', hashcat=None, john=None, extended=False),HashInfo(name='FNV-132', hashcat=None, john=None, extended=False),HashInfo(name='Fletcher-32', hashcat=None, john=None, extended=False),HashInfo(name='Joaat', hashcat=None, john=None, extended=False),HashInfo(name='ELF-32', hashcat=None, john=None, extended=False),HashInfo(name='XOR-32', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{6}$', re.IGNORECASE),modes=[HashInfo(name='CRC-24', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^(\$crc32\$[a-f0-9]{8}.)?[a-f0-9]{8}$', re.IGNORECASE),modes=[HashInfo(name='CRC-32', hashcat=None, john='crc32', extended=False)]),Prototype(regex=re.compile(r'^\+[a-z0-9\/.]{12}$', re.IGNORECASE),modes=[HashInfo(name='Eggdrop IRC Bot', hashcat=None, john='bfegg', extended=False)]),Prototype(regex=re.compile(r'^[a-z0-9\/.]{13}$', re.IGNORECASE),modes=[HashInfo(name='DES(Unix)', hashcat=1500, john='descrypt', extended=False),HashInfo(name='Traditional DES', hashcat=1500, john='descrypt', extended=False),HashInfo(name='DEScrypt', hashcat=1500, john='descrypt', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{16}$', re.IGNORECASE),modes=[HashInfo(name='MySQL323', hashcat=200, john='mysql', extended=False),HashInfo(name='DES(Oracle)', hashcat=3100, john=None, extended=False),HashInfo(name='Half MD5', hashcat=5100, john=None, extended=False),HashInfo(name='Oracle 7-10g', hashcat=3100, john=None, extended=False),HashInfo(name='FNV-164', hashcat=None, john=None, extended=False),HashInfo(name='CRC-64', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-z0-9\/.]{16}$', re.IGNORECASE),modes=[HashInfo(name='Cisco-PIX(MD5)', hashcat=2400, john='pix-md5', extended=False)]),Prototype(regex=re.compile(r'^\([a-z0-9\/+]{20}\)$', re.IGNORECASE),modes=[HashInfo(name='Lotus Notes/Domino 6', hashcat=8700, john='dominosec', extended=False)]),Prototype(regex=re.compile(r'^_[a-z0-9\/.]{19}$', re.IGNORECASE),modes=[HashInfo(name='BSDi Crypt', hashcat=None, john='bsdicrypt', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{24}$', re.IGNORECASE),modes=[HashInfo(name='CRC-96(ZIP)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-z0-9\/.]{24}$', re.IGNORECASE),modes=[HashInfo(name='Crypt16', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^(\$md2\$)?[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='MD2', hashcat=None, john='md2', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{32}(:.+)?$', re.IGNORECASE),modes=[HashInfo(name='MD5', hashcat=0, john='raw-md5', extended=False),HashInfo(name='MD4', hashcat=900, john='raw-md4', extended=False),HashInfo(name='Double MD5', hashcat=2600, john=None, extended=False),HashInfo(name='LM', hashcat=3000, john='lm', extended=False),HashInfo(name='RIPEMD-128', hashcat=None, john='ripemd-128', extended=False),HashInfo(name='Haval-128', hashcat=None, john='haval-128-4', extended=False),HashInfo(name='Tiger-128', hashcat=None, john=None, extended=False),HashInfo(name='Skein-256(128)', hashcat=None, john=None, extended=False),HashInfo(name='Skein-512(128)', hashcat=None, john=None, extended=False),HashInfo(name='Lotus Notes/Domino 5', hashcat=8600, john='lotus5', extended=False),HashInfo(name='Skype', hashcat=23, john=None, extended=False),HashInfo(name='ZipMonster', hashcat=None, john=None, extended=True),HashInfo(name='PrestaShop', hashcat=11000, john=None, extended=True),HashInfo(name='md5(md5(md5($pass)))', hashcat=3500, john=None, extended=True),HashInfo(name='md5(strtoupper(md5($pass)))', hashcat=4300, john=None, extended=True),HashInfo(name='md5(sha1($pass))', hashcat=4400, john=None, extended=True),HashInfo(name='md5($pass.$salt)', hashcat=10, john=None, extended=True),HashInfo(name='md5($salt.$pass)', hashcat=20, john=None, extended=True),HashInfo(name='md5(unicode($pass).$salt)', hashcat=30, john=None, extended=True),HashInfo(name='md5($salt.unicode($pass))', hashcat=40, john=None, extended=True),HashInfo(name='HMAC-MD5 (key = $pass)', hashcat=50, john='hmac-md5', extended=True),HashInfo(name='HMAC-MD5 (key = $salt)', hashcat=60, john='hmac-md5', extended=True),HashInfo(name='md5(md5($salt).$pass)', hashcat=3610, john=None, extended=True),HashInfo(name='md5($salt.md5($pass))', hashcat=3710, john=None, extended=True),HashInfo(name='md5($pass.md5($salt))', hashcat=3720, john=None, extended=True),HashInfo(name='md5($salt.$pass.$salt)', hashcat=3810, john=None, extended=True),HashInfo(name='md5(md5($pass).md5($salt))', hashcat=3910, john=None, extended=True),HashInfo(name='md5($salt.md5($salt.$pass))', hashcat=4010, john=None, extended=True),HashInfo(name='md5($salt.md5($pass.$salt))', hashcat=4110, john=None, extended=True),HashInfo(name='md5($username.0.$pass)', hashcat=4210, john=None, extended=True)]),Prototype(regex=re.compile(r'^(\$snefru\$)?[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='Snefru-128', hashcat=None, john='snefru-128', extended=False)]),Prototype(regex=re.compile(r'^(\$NT\$)?[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='NTLM', hashcat=1000, john='nt', extended=False)]),Prototype(regex=re.compile(r'^([^\\\/:*?"<>|]{1,20}:)?[a-f0-9]{32}(:[^\\\/:*?"<>|]{1,20})?$', re.IGNORECASE),modes=[HashInfo(name='Domain Cached Credentials', hashcat=1100, john='mscach', extended=False)]),Prototype(regex=re.compile(r'^([^\\\/:*?"<>|]{1,20}:)?(\$DCC2\$10240#[^\\\/:*?"<>|]{1,20}#)?[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='Domain Cached Credentials 2', hashcat=2100, john='mscach2', extended=False)]),Prototype(regex=re.compile(r'^{SHA}[a-z0-9\/+]{27}=$', re.IGNORECASE),modes=[HashInfo(name='SHA-1(Base64)', hashcat=101, john='nsldap', extended=False),HashInfo(name='Netscape LDAP SHA', hashcat=101, john='nsldap', extended=False)]),Prototype(regex=re.compile(r'^\$1\$[a-z0-9\/.]{0,8}\$[a-z0-9\/.]{22}(:.*)?$', re.IGNORECASE),modes=[HashInfo(name='MD5 Crypt', hashcat=500, john='md5crypt', extended=False),HashInfo(name='Cisco-IOS(MD5)', hashcat=500, john='md5crypt', extended=False),HashInfo(name='FreeBSD MD5', hashcat=500, john='md5crypt', extended=False)]),Prototype(regex=re.compile(r'^0x[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='Lineage II C4', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$H\$[a-z0-9\/.]{31}$', re.IGNORECASE),modes=[HashInfo(name='phpBB v3.x', hashcat=400, john='phpass', extended=False),HashInfo(name='Wordpress v2.6.0/2.6.1', hashcat=400, john='phpass', extended=False),HashInfo(name="PHPass' Portable Hash", hashcat=400, john='phpass', extended=False)]),Prototype(regex=re.compile(r'^\$P\$[a-z0-9\/.]{31}$', re.IGNORECASE),modes=[HashInfo(name=u'Wordpress ≥ v2.6.2', hashcat=400, john='phpass', extended=False),HashInfo(name=u'Joomla ≥ v2.5.18', hashcat=400, john='phpass', extended=False),HashInfo(name="PHPass' Portable Hash", hashcat=400, john='phpass', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{32}:[a-z0-9]{2}$', re.IGNORECASE),modes=[HashInfo(name='osCommerce', hashcat=21, john=None, extended=False),HashInfo(name='xt:Commerce', hashcat=21, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$apr1\$[a-z0-9\/.]{0,8}\$[a-z0-9\/.]{22}$', re.IGNORECASE),modes=[HashInfo(name='MD5(APR)', hashcat=1600, john=None, extended=False),HashInfo(name='Apache MD5', hashcat=1600, john=None, extended=False),HashInfo(name='md5apr1', hashcat=1600, john=None, extended=True)]),Prototype(regex=re.compile(r'^{smd5}[a-z0-9$\/.]{31}$', re.IGNORECASE),modes=[HashInfo(name='AIX(smd5)', hashcat=6300, john='aix-smd5', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{32}:[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='WebEdition CMS', hashcat=3721, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{32}:.{5}$', re.IGNORECASE),modes=[HashInfo(name=u'IP.Board ≥ v2+', hashcat=2811, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{32}:.{8}$', re.IGNORECASE),modes=[HashInfo(name=u'MyBB ≥ v1.2+', hashcat=2811, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-z0-9]{34}$', re.IGNORECASE),modes=[HashInfo(name='CryptoCurrency(Adress)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{40}(:.+)?$', re.IGNORECASE),modes=[HashInfo(name='SHA-1', hashcat=100, john='raw-sha1', extended=False),HashInfo(name='Double SHA-1', hashcat=4500, john=None, extended=False),HashInfo(name='RIPEMD-160', hashcat=6000, john='ripemd-160', extended=False),HashInfo(name='Haval-160', hashcat=None, john=None, extended=False),HashInfo(name='Tiger-160', hashcat=None, john=None, extended=False),HashInfo(name='HAS-160', hashcat=None, john=None, extended=False),HashInfo(name='LinkedIn', hashcat=190, john='raw-sha1-linkedin', extended=False),HashInfo(name='Skein-256(160)', hashcat=None, john=None, extended=False),HashInfo(name='Skein-512(160)', hashcat=None, john=None, extended=False),HashInfo(name='MangosWeb Enhanced CMS', hashcat=None, john=None, extended=True),HashInfo(name='sha1(sha1(sha1($pass)))', hashcat=4600, john=None, extended=True),HashInfo(name='sha1(md5($pass))', hashcat=4700, john=None, extended=True),HashInfo(name='sha1($pass.$salt)', hashcat=110, john=None, extended=True),HashInfo(name='sha1($salt.$pass)', hashcat=120, john=None, extended=True),HashInfo(name='sha1(unicode($pass).$salt)', hashcat=130, john=None, extended=True),HashInfo(name='sha1($salt.unicode($pass))', hashcat=140, john=None, extended=True),HashInfo(name='HMAC-SHA1 (key = $pass)', hashcat=150, john='hmac-sha1', extended=True),HashInfo(name='HMAC-SHA1 (key = $salt)', hashcat=160, john='hmac-sha1', extended=True),HashInfo(name='sha1($salt.$pass.$salt)', hashcat=4710, john=None, extended=True)]),Prototype(regex=re.compile(r'^\*[a-f0-9]{40}$', re.IGNORECASE),modes=[HashInfo(name='MySQL5.x', hashcat=300, john='mysql-sha1', extended=False),HashInfo(name='MySQL4.1', hashcat=300, john='mysql-sha1', extended=False)]),Prototype(regex=re.compile(r'^[a-z0-9]{43}$', re.IGNORECASE),modes=[HashInfo(name='Cisco-IOS(SHA-256)', hashcat=5700, john=None, extended=False)]),Prototype(regex=re.compile(r'^{SSHA}[a-z0-9\/+]{38}==$', re.IGNORECASE),modes=[HashInfo(name='SSHA-1(Base64)', hashcat=111, john='nsldaps', extended=False),HashInfo(name='Netscape LDAP SSHA', hashcat=111, john='nsldaps', extended=False),HashInfo(name='nsldaps', hashcat=111, john='nsldaps', extended=True)]),Prototype(regex=re.compile(r'^[a-z0-9=]{47}$', re.IGNORECASE),modes=[HashInfo(name='Fortigate(FortiOS)', hashcat=7000, john='fortigate', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{48}$', re.IGNORECASE),modes=[HashInfo(name='Haval-192', hashcat=None, john=None, extended=False),HashInfo(name='Tiger-192', hashcat=None, john='tiger', extended=False),HashInfo(name='SHA-1(Oracle)', hashcat=None, john=None, extended=False),HashInfo(name='OSX v10.4', hashcat=122, john='xsha', extended=False),HashInfo(name='OSX v10.5', hashcat=122, john='xsha', extended=False),HashInfo(name='OSX v10.6', hashcat=122, john='xsha', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{51}$', re.IGNORECASE),modes=[HashInfo(name='Palshop CMS', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-z0-9]{51}$', re.IGNORECASE),modes=[HashInfo(name='CryptoCurrency(PrivateKey)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^{ssha1}[0-9]{2}\$[a-z0-9$\/.]{44}$', re.IGNORECASE),modes=[HashInfo(name='AIX(ssha1)', hashcat=6700, john='aix-ssha1', extended=False)]),Prototype(regex=re.compile(r'^0x0100[a-f0-9]{48}$', re.IGNORECASE),modes=[HashInfo(name='MSSQL(2005)', hashcat=132, john='mssql05', extended=False),HashInfo(name='MSSQL(2008)', hashcat=132, john='mssql05', extended=False)]),Prototype(regex=re.compile(r'^(\$md5,rounds=[0-9]+\$|\$md5\$rounds=[0-9]+\$|\$md5\$)[a-z0-9\/.]{0,16}(\$|\$\$)[a-z0-9\/.]{22}$', re.IGNORECASE),modes=[HashInfo(name='Sun MD5 Crypt', hashcat=3300, john='sunmd5', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{56}$', re.IGNORECASE),modes=[HashInfo(name='SHA-224', hashcat=None, john='raw-sha224', extended=False),HashInfo(name='Haval-224', hashcat=None, john=None, extended=False),HashInfo(name='SHA3-224', hashcat=None, john=None, extended=False),HashInfo(name='Skein-256(224)', hashcat=None, john=None, extended=False),HashInfo(name='Skein-512(224)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^(\$2[axy]|\$2)\$[0-9]{2}\$[a-z0-9\/.]{53}$', re.IGNORECASE),modes=[HashInfo(name='Blowfish(OpenBSD)', hashcat=3200, john='bcrypt', extended=False),HashInfo(name='Woltlab Burning Board 4.x', hashcat=None, john=None, extended=False),HashInfo(name='bcrypt', hashcat=3200, john='bcrypt', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{40}:[a-f0-9]{16}$', re.IGNORECASE),modes=[HashInfo(name='Android PIN', hashcat=5800, john=None, extended=False)]),Prototype(regex=re.compile(r'^(S:)?[a-f0-9]{40}(:)?[a-f0-9]{20}$', re.IGNORECASE),modes=[HashInfo(name='Oracle 11g/12c', hashcat=112, john='oracle11', extended=False)]),Prototype(regex=re.compile(r'^\$bcrypt-sha256\$(2[axy]|2)\,[0-9]+\$[a-z0-9\/.]{22}\$[a-z0-9\/.]{31}$', re.IGNORECASE),modes=[HashInfo(name='bcrypt(SHA-256)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{32}:.{3}$', re.IGNORECASE),modes=[HashInfo(name='vBulletin < v3.8.5', hashcat=2611, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{32}:.{30}$', re.IGNORECASE),modes=[HashInfo(name=u'vBulletin ≥ v3.8.5', hashcat=2711, john=None, extended=False)]),Prototype(regex=re.compile(r'^(\$snefru\$)?[a-f0-9]{64}$', re.IGNORECASE),modes=[HashInfo(name='Snefru-256', hashcat=None, john='snefru-256', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{64}(:.+)?$', re.IGNORECASE),modes=[HashInfo(name='SHA-256', hashcat=1400, john='raw-sha256', extended=False),HashInfo(name='RIPEMD-256', hashcat=None, john=None, extended=False),HashInfo(name='Haval-256', hashcat=None, john='haval-256-3', extended=False),HashInfo(name='GOST R 34.11-94', hashcat=6900, john='gost', extended=False),HashInfo(name='GOST CryptoPro S-Box', hashcat=None, john=None, extended=False),HashInfo(name='SHA3-256', hashcat=5000, john='raw-keccak-256', extended=False),HashInfo(name='Skein-256', hashcat=None, john='skein-256', extended=False),HashInfo(name='Skein-512(256)', hashcat=None, john=None, extended=False),HashInfo(name='Ventrilo', hashcat=None, john=None, extended=True),HashInfo(name='sha256($pass.$salt)', hashcat=1410, john=None, extended=True),HashInfo(name='sha256($salt.$pass)', hashcat=1420, john=None, extended=True),HashInfo(name='sha256(unicode($pass).$salt)', hashcat=1430, john=None, extended=True),HashInfo(name='sha256($salt.unicode($pass))', hashcat=1440, john=None, extended=True),HashInfo(name='HMAC-SHA256 (key = $pass)', hashcat=1450, john='hmac-sha256', extended=True),HashInfo(name='HMAC-SHA256 (key = $salt)', hashcat=1460, john='hmac-sha256', extended=True)]),Prototype(regex=re.compile(r'^[a-f0-9]{32}:[a-z0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='Joomla < v2.5.18', hashcat=11, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f-0-9]{32}:[a-f-0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='SAM(LM_Hash:NT_Hash)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^(\$chap\$0\*)?[a-f0-9]{32}[\*:][a-f0-9]{32}(:[0-9]{2})?$', re.IGNORECASE),modes=[HashInfo(name='MD5(Chap)', hashcat=4800, john='chap', extended=False),HashInfo(name='iSCSI CHAP Authentication', hashcat=4800, john='chap', extended=False)]),Prototype(regex=re.compile(r'^\$episerver\$\*0\*[a-z0-9\/=+]+\*[a-z0-9\/=+]{27,28}$', re.IGNORECASE),modes=[HashInfo(name='EPiServer 6.x < v4', hashcat=141, john='episerver', extended=False)]),Prototype(regex=re.compile(r'^{ssha256}[0-9]{2}\$[a-z0-9$\/.]{60}$', re.IGNORECASE),modes=[HashInfo(name='AIX(ssha256)', hashcat=6400, john='aix-ssha256', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{80}$', re.IGNORECASE),modes=[HashInfo(name='RIPEMD-320', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$episerver\$\*1\*[a-z0-9\/=+]+\*[a-z0-9\/=+]{42,43}$', re.IGNORECASE),modes=[HashInfo(name=u'EPiServer 6.x ≥ v4', hashcat=1441, john='episerver', extended=False)]),Prototype(regex=re.compile(r'^0x0100[a-f0-9]{88}$', re.IGNORECASE),modes=[HashInfo(name='MSSQL(2000)', hashcat=131, john='mssql', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{96}$', re.IGNORECASE),modes=[HashInfo(name='SHA-384', hashcat=10800, john='raw-sha384', extended=False),HashInfo(name='SHA3-384', hashcat=None, john=None, extended=False),HashInfo(name='Skein-512(384)', hashcat=None, john=None, extended=False),HashInfo(name='Skein-1024(384)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^{SSHA512}[a-z0-9\/+]{96}$', re.IGNORECASE),modes=[HashInfo(name='SSHA-512(Base64)', hashcat=1711, john='ssha512', extended=False),HashInfo(name='LDAP(SSHA-512)', hashcat=1711, john='ssha512', extended=False)]),Prototype(regex=re.compile(r'^{ssha512}[0-9]{2}\$[a-z0-9\/.]{16,48}\$[a-z0-9\/.]{86}$', re.IGNORECASE),modes=[HashInfo(name='AIX(ssha512)', hashcat=6500, john='aix-ssha512', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{128}(:.+)?$', re.IGNORECASE),modes=[HashInfo(name='SHA-512', hashcat=1700, john='raw-sha512', extended=False),HashInfo(name='Whirlpool', hashcat=6100, john='whirlpool', extended=False),HashInfo(name='Salsa10', hashcat=None, john=None, extended=False),HashInfo(name='Salsa20', hashcat=None, john=None, extended=False),HashInfo(name='SHA3-512', hashcat=None, john='raw-keccak', extended=False),HashInfo(name='Skein-512', hashcat=None, john='skein-512', extended=False),HashInfo(name='Skein-1024(512)', hashcat=None, john=None, extended=False),HashInfo(name='sha512($pass.$salt)', hashcat=1710, john=None, extended=True),HashInfo(name='sha512($salt.$pass)', hashcat=1720, john=None, extended=True),HashInfo(name='sha512(unicode($pass).$salt)', hashcat=1730, john=None, extended=True),HashInfo(name='sha512($salt.unicode($pass))', hashcat=1740, john=None, extended=True),HashInfo(name='HMAC-SHA512 (key = $pass)', hashcat=1750, john='hmac-sha512', extended=True),HashInfo(name='HMAC-SHA512 (key = $salt)', hashcat=1760, john='hmac-sha512', extended=True)]),Prototype(regex=re.compile(r'^[a-f0-9]{136}$', re.IGNORECASE),modes=[HashInfo(name='OSX v10.7', hashcat=1722, john='xsha512', extended=False)]),Prototype(regex=re.compile(r'^0x0200[a-f0-9]{136}$', re.IGNORECASE),modes=[HashInfo(name='MSSQL(2012)', hashcat=1731, john='msql12', extended=False),HashInfo(name='MSSQL(2014)', hashcat=1731, john='msql12', extended=False)]),Prototype(regex=re.compile(r'^\$ml\$[0-9]+\$[a-f0-9]{64}\$[a-f0-9]{128}$', re.IGNORECASE),modes=[HashInfo(name='OSX v10.8', hashcat=7100, john='pbkdf2-hmac-sha512', extended=False),HashInfo(name='OSX v10.9', hashcat=7100, john='pbkdf2-hmac-sha512', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{256}$', re.IGNORECASE),modes=[HashInfo(name='Skein-1024', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^grub\.pbkdf2\.sha512\.[0-9]+\.([a-f0-9]{128,2048}\.|[0-9]+\.)?[a-f0-9]{128}$', re.IGNORECASE),modes=[HashInfo(name='GRUB 2', hashcat=7200, john=None, extended=False)]),Prototype(regex=re.compile(r'^sha1\$[a-z0-9]+\$[a-f0-9]{40}$', re.IGNORECASE),modes=[HashInfo(name='Django(SHA-1)', hashcat=124, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{49}$', re.IGNORECASE),modes=[HashInfo(name='Citrix Netscaler', hashcat=8100, john='citrix_ns10', extended=False)]),Prototype(regex=re.compile(r'^\$S\$[a-z0-9\/.]{52}$', re.IGNORECASE),modes=[HashInfo(name='Drupal > v7.x', hashcat=7900, john='drupal7', extended=False)]),Prototype(regex=re.compile(r'^\$5\$(rounds=[0-9]+\$)?[a-z0-9\/.]{0,16}\$[a-z0-9\/.]{43}$', re.IGNORECASE),modes=[HashInfo(name='SHA-256 Crypt', hashcat=7400, john='sha256crypt', extended=False)]),Prototype(regex=re.compile(r'^0x[a-f0-9]{4}[a-f0-9]{16}[a-f0-9]{64}$', re.IGNORECASE),modes=[HashInfo(name='Sybase ASE', hashcat=8000, john='sybasease', extended=False)]),Prototype(regex=re.compile(r'^\$6\$(rounds=[0-9]+\$)?[a-z0-9\/.]{0,16}\$[a-z0-9\/.]{86}$', re.IGNORECASE),modes=[HashInfo(name='SHA-512 Crypt', hashcat=1800, john='sha512crypt', extended=False)]),Prototype(regex=re.compile(r'^\$sha\$[a-z0-9]{1,16}\$([a-f0-9]{32}|[a-f0-9]{40}|[a-f0-9]{64}|[a-f0-9]{128}|[a-f0-9]{140})$', re.IGNORECASE),modes=[HashInfo(name='Minecraft(AuthMe Reloaded)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^sha256\$[a-z0-9]+\$[a-f0-9]{64}$', re.IGNORECASE),modes=[HashInfo(name='Django(SHA-256)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^sha384\$[a-z0-9]+\$[a-f0-9]{96}$', re.IGNORECASE),modes=[HashInfo(name='Django(SHA-384)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^crypt1:[a-z0-9+=]{12}:[a-z0-9+=]{12}$', re.IGNORECASE),modes=[HashInfo(name='Clavister Secure Gateway', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{112}$', re.IGNORECASE),modes=[HashInfo(name='Cisco VPN Client(PCF-File)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{1329}$', re.IGNORECASE),modes=[HashInfo(name='Microsoft MSTSC(RDP-File)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^[^\\\/:*?"<>|]{1,20}[:]{2,3}([^\\\/:*?"<>|]{1,20})?:[a-f0-9]{48}:[a-f0-9]{48}:[a-f0-9]{16}$', re.IGNORECASE),modes=[HashInfo(name='NetNTLMv1-VANILLA / NetNTLMv1+ESS', hashcat=5500, john='netntlm', extended=False)]),Prototype(regex=re.compile(r'^([^\\\/:*?"<>|]{1,20}\\)?[^\\\/:*?"<>|]{1,20}[:]{2,3}([^\\\/:*?"<>|]{1,20}:)?[^\\\/:*?"<>|]{1,20}:[a-f0-9]{32}:[a-f0-9]+$', re.IGNORECASE),modes=[HashInfo(name='NetNTLMv2', hashcat=5600, john='netntlmv2', extended=False)]),Prototype(regex=re.compile(r'^\$(krb5pa|mskrb5)\$([0-9]{2})?\$.+\$[a-f0-9]{1,}$', re.IGNORECASE),modes=[HashInfo(name='Kerberos 5 AS-REQ Pre-Auth', hashcat=7500, john='krb5pa-md5', extended=False)]),Prototype(regex=re.compile(r'^\$scram\$[0-9]+\$[a-z0-9\/.]{16}\$sha-1=[a-z0-9\/.]{27},sha-256=[a-z0-9\/.]{43},sha-512=[a-z0-9\/.]{86}$', re.IGNORECASE),modes=[HashInfo(name='SCRAM Hash', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{40}:[a-f0-9]{0,32}$', re.IGNORECASE),modes=[HashInfo(name='Redmine Project Management Web App', hashcat=7600, john=None, extended=False)]),Prototype(regex=re.compile(r'^(.+)?\$[a-f0-9]{16}$', re.IGNORECASE),modes=[HashInfo(name='SAP CODVN B (BCODE)', hashcat=7700, john='sapb', extended=False)]),Prototype(regex=re.compile(r'^(.+)?\$[a-f0-9]{40}$', re.IGNORECASE),modes=[HashInfo(name='SAP CODVN F/G (PASSCODE)', hashcat=7800, john='sapg', extended=False)]),Prototype(regex=re.compile(r'^(.+\$)?[a-z0-9\/.+]{30}(:.+)?$', re.IGNORECASE),modes=[HashInfo(name='Juniper Netscreen/SSG(ScreenOS)', hashcat=22, john='md5ns', extended=False)]),Prototype(regex=re.compile(r'^0x[a-f0-9]{60}\s0x[a-f0-9]{40}$', re.IGNORECASE),modes=[HashInfo(name='EPi', hashcat=123, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{40}:[^*]{1,25}$', re.IGNORECASE),modes=[HashInfo(name=u'SMF ≥ v1.1', hashcat=121, john=None, extended=False)]),Prototype(regex=re.compile(r'^(\$wbb3\$\*1\*)?[a-f0-9]{40}[:*][a-f0-9]{40}$', re.IGNORECASE),modes=[HashInfo(name='Woltlab Burning Board 3.x', hashcat=8400, john='wbb3', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{130}(:[a-f0-9]{40})?$', re.IGNORECASE),modes=[HashInfo(name='IPMI2 RAKP HMAC-SHA1', hashcat=7300, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{32}:[0-9]+:[a-z0-9_.+-]+@[a-z0-9-]+\.[a-z0-9-.]+$', re.IGNORECASE),modes=[HashInfo(name='Lastpass', hashcat=6800, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-z0-9\/.]{16}([:$].{1,})?$', re.IGNORECASE),modes=[HashInfo(name='Cisco-ASA(MD5)', hashcat=2410, john='asa-md5', extended=False)]),Prototype(regex=re.compile(r'^\$vnc\$\*[a-f0-9]{32}\*[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='VNC', hashcat=None, john='vnc', extended=False)]),Prototype(regex=re.compile(r'^[a-z0-9]{32}(:([a-z0-9-]+\.)?[a-z0-9-.]+\.[a-z]{2,7}:.+:[0-9]+)?$', re.IGNORECASE),modes=[HashInfo(name='DNSSEC(NSEC3)', hashcat=8300, john=None, extended=False)]),Prototype(regex=re.compile(r'^(user-.+:)?\$racf\$\*.+\*[a-f0-9]{16}$', re.IGNORECASE),modes=[HashInfo(name='RACF', hashcat=8500, john='racf', extended=False)]),Prototype(regex=re.compile(r'^\$3\$\$[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='NTHash(FreeBSD Variant)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$sha1\$[0-9]+\$[a-z0-9\/.]{0,64}\$[a-z0-9\/.]{28}$', re.IGNORECASE),modes=[HashInfo(name='SHA-1 Crypt', hashcat=None, john='sha1crypt', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{70}$', re.IGNORECASE),modes=[HashInfo(name='hMailServer', hashcat=1421, john='hmailserver', extended=False)]),Prototype(regex=re.compile(r'^[:\$][AB][:\$]([a-f0-9]{1,8}[:\$])?[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='MediaWiki', hashcat=3711, john='mediawiki', extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{140}$', re.IGNORECASE),modes=[HashInfo(name='Minecraft(xAuth)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$pbkdf2(-sha1)?\$[0-9]+\$[a-z0-9\/.]+\$[a-z0-9\/.]{27}$', re.IGNORECASE),modes=[HashInfo(name='PBKDF2-SHA1(Generic)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$pbkdf2-sha256\$[0-9]+\$[a-z0-9\/.]+\$[a-z0-9\/.]{43}$', re.IGNORECASE),modes=[HashInfo(name='PBKDF2-SHA256(Generic)', hashcat=None, john='pbkdf2-hmac-sha256', extended=False)]),Prototype(regex=re.compile(r'^\$pbkdf2-sha512\$[0-9]+\$[a-z0-9\/.]+\$[a-z0-9\/.]{86}$', re.IGNORECASE),modes=[HashInfo(name='PBKDF2-SHA512(Generic)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$p5k2\$[0-9]+\$[a-z0-9\/+=-]+\$[a-z0-9\/+-]{27}=$', re.IGNORECASE),modes=[HashInfo(name='PBKDF2(Cryptacular)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$p5k2\$[0-9]+\$[a-z0-9\/.]+\$[a-z0-9\/.]{32}$', re.IGNORECASE),modes=[HashInfo(name='PBKDF2(Dwayne Litzenberger)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^{FSHP[0123]\|[0-9]+\|[0-9]+}[a-z0-9\/+=]+$', re.IGNORECASE),modes=[HashInfo(name='Fairly Secure Hashed Password', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$PHPS\$.+\$[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='PHPS', hashcat=2612, john='phps', extended=False)]),Prototype(regex=re.compile(r'^[0-9]{4}:[a-f0-9]{16}:[a-f0-9]{2080}$', re.IGNORECASE),modes=[HashInfo(name='1Password(Agile Keychain)', hashcat=6600, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{64}:[a-f0-9]{32}:[0-9]{5}:[a-f0-9]{608}$', re.IGNORECASE),modes=[HashInfo(name='1Password(Cloud Keychain)', hashcat=8200, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{256}:[a-f0-9]{256}:[a-f0-9]{16}:[a-f0-9]{16}:[a-f0-9]{320}:[a-f0-9]{16}:[a-f0-9]{40}:[a-f0-9]{40}:[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='IKE-PSK MD5', hashcat=5300, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{256}:[a-f0-9]{256}:[a-f0-9]{16}:[a-f0-9]{16}:[a-f0-9]{320}:[a-f0-9]{16}:[a-f0-9]{40}:[a-f0-9]{40}:[a-f0-9]{40}$', re.IGNORECASE),modes=[HashInfo(name='IKE-PSK SHA1', hashcat=5400, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-z0-9\/+]{27}=$', re.IGNORECASE),modes=[HashInfo(name='PeopleSoft', hashcat=133, john=None, extended=False)]),Prototype(regex=re.compile(r'^crypt\$[a-f0-9]{5}\$[a-z0-9\/.]{13}$', re.IGNORECASE),modes=[HashInfo(name='Django(DES Crypt Wrapper)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^(\$django\$\*1\*)?pbkdf2_sha256\$[0-9]+\$[a-z0-9]+\$[a-z0-9\/+=]{44}$', re.IGNORECASE),modes=[HashInfo(name='Django(PBKDF2-HMAC-SHA256)', hashcat=10000, john='django', extended=False)]),Prototype(regex=re.compile(r'^pbkdf2_sha1\$[0-9]+\$[a-z0-9]+\$[a-z0-9\/+=]{28}$', re.IGNORECASE),modes=[HashInfo(name='Django(PBKDF2-HMAC-SHA1)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^bcrypt(\$2[axy]|\$2)\$[0-9]{2}\$[a-z0-9\/.]{53}$', re.IGNORECASE),modes=[HashInfo(name='Django(bcrypt)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^md5\$[a-f0-9]+\$[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='Django(MD5)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^\{PKCS5S2\}[a-z0-9\/+]{64}$', re.IGNORECASE),modes=[HashInfo(name='PBKDF2(Atlassian)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^md5[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='PostgreSQL MD5', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^\([a-z0-9\/+]{49}\)$', re.IGNORECASE),modes=[HashInfo(name='Lotus Notes/Domino 8', hashcat=9100, john=None, extended=False)]),Prototype(regex=re.compile(r'^SCRYPT:[0-9]{1,}:[0-9]{1}:[0-9]{1}:[a-z0-9:\/+=]{1,}$', re.IGNORECASE),modes=[HashInfo(name='scrypt', hashcat=8900, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$8\$[a-z0-9\/.]{14}\$[a-z0-9\/.]{43}$', re.IGNORECASE),modes=[HashInfo(name='Cisco Type 8', hashcat=9200, john='cisco8', extended=False)]),Prototype(regex=re.compile(r'^\$9\$[a-z0-9\/.]{14}\$[a-z0-9\/.]{43}$', re.IGNORECASE),modes=[HashInfo(name='Cisco Type 9', hashcat=9300, john='cisco9', extended=False)]),Prototype(regex=re.compile(r'^\$office\$\*2007\*[0-9]{2}\*[0-9]{3}\*[0-9]{2}\*[a-z0-9]{32}\*[a-z0-9]{32}\*[a-z0-9]{40}$', re.IGNORECASE),modes=[HashInfo(name='Microsoft Office 2007', hashcat=9400, john='office', extended=False)]),Prototype(regex=re.compile(r'^\$office\$\*2010\*[0-9]{6}\*[0-9]{3}\*[0-9]{2}\*[a-z0-9]{32}\*[a-z0-9]{32}\*[a-z0-9]{64}$', re.IGNORECASE),modes=[HashInfo(name='Microsoft Office 2010', hashcat=9500, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$office\$\*2013\*[0-9]{6}\*[0-9]{3}\*[0-9]{2}\*[a-z0-9]{32}\*[a-z0-9]{32}\*[a-z0-9]{64}$', re.IGNORECASE),modes=[HashInfo(name='Microsoft Office 2013', hashcat=9600, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$fde\$[0-9]{2}\$[a-f0-9]{32}\$[0-9]{2}\$[a-f0-9]{32}\$[a-f0-9]{3072}$', re.IGNORECASE),modes=[HashInfo(name=u'Android FDE ≤ 4.3', hashcat=8800, john='fde', extended=False)]),Prototype(regex=re.compile(r'^\$oldoffice\$[01]\*[a-f0-9]{32}\*[a-f0-9]{32}\*[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name=u'Microsoft Office ≤ 2003 (MD5+RC4)', hashcat=9700, john='oldoffice', extended=False),HashInfo(name=u'Microsoft Office ≤ 2003 (MD5+RC4) collider-mode #1', hashcat=9710, john='oldoffice', extended=False),HashInfo(name=u'Microsoft Office ≤ 2003 (MD5+RC4) collider-mode #2', hashcat=9720, john='oldoffice', extended=False)]),Prototype(regex=re.compile(r'^\$oldoffice\$[34]\*[a-f0-9]{32}\*[a-f0-9]{32}\*[a-f0-9]{40}$', re.IGNORECASE),modes=[HashInfo(name=u'Microsoft Office ≤ 2003 (SHA1+RC4)', hashcat=9800, john=None, extended=False),HashInfo(name=u'Microsoft Office ≤ 2003 (SHA1+RC4) collider-mode #1', hashcat=9810, john=None, extended=False),HashInfo(name=u'Microsoft Office ≤ 2003 (SHA1+RC4) collider-mode #2', hashcat=9820, john=None, extended=False)]),Prototype(regex=re.compile(r'^(\$radmin2\$)?[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='RAdmin v2.x', hashcat=9900, john='radmin', extended=False)]),Prototype(regex=re.compile(r'^{x-issha,\s[0-9]{4}}[a-z0-9\/+=]+$', re.IGNORECASE),modes=[HashInfo(name='SAP CODVN H (PWDSALTEDHASH) iSSHA-1', hashcat=10300, john='saph', extended=False)]),Prototype(regex=re.compile(r'^\$cram_md5\$[a-z0-9\/+=-]+\$[a-z0-9\/+=-]{52}$', re.IGNORECASE),modes=[HashInfo(name='CRAM-MD5', hashcat=10200, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{16}:2:4:[a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='SipHash', hashcat=10100, john=None, extended=False)]),Prototype(regex=re.compile(r'^[a-f0-9]{4,}$', re.IGNORECASE),modes=[HashInfo(name='Cisco Type 7', hashcat=None, john=None, extended=True)]),Prototype(regex=re.compile(r'^[a-z0-9\/.]{13,}$', re.IGNORECASE),modes=[HashInfo(name='BigCrypt', hashcat=None, john='bigcrypt', extended=True)]),Prototype(regex=re.compile(r'^(\$cisco4\$)?[a-z0-9\/.]{43}$', re.IGNORECASE),modes=[HashInfo(name='Cisco Type 4', hashcat=None, john='cisco4', extended=False)]),Prototype(regex=re.compile(r'^bcrypt_sha256\$\$(2[axy]|2)\$[0-9]+\$[a-z0-9\/.]{53}$', re.IGNORECASE),modes=[HashInfo(name='Django(bcrypt-SHA256)', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$postgres\$.[^\*]+[*:][a-f0-9]{1,32}[*:][a-f0-9]{32}$', re.IGNORECASE),modes=[HashInfo(name='PostgreSQL Challenge-Response Authentication (MD5)', hashcat=11100, john='postgres', extended=False)]),Prototype(regex=re.compile(r'^\$siemens-s7\$[0-9]{1}\$[a-f0-9]{40}\$[a-f0-9]{40}$', re.IGNORECASE),modes=[HashInfo(name='Siemens-S7', hashcat=None, john='siemens-s7', extended=False)]),Prototype(regex=re.compile(r'^(\$pst\$)?[a-f0-9]{8}$', re.IGNORECASE),modes=[HashInfo(name='Microsoft Outlook PST', hashcat=None, john=None, extended=False)]),Prototype(regex=re.compile(r'^sha256[:$][0-9]+[:$][a-z0-9\/+]+[:$][a-z0-9\/+]{32,128}$', re.IGNORECASE),modes=[HashInfo(name='PBKDF2-HMAC-SHA256(PHP)', hashcat=10900, john=None, extended=False)]),Prototype(regex=re.compile(r'^(\$dahua\$)?[a-z0-9]{8}$', re.IGNORECASE),modes=[HashInfo(name='Dahua', hashcat=None, john='dahua', extended=False)]),Prototype(regex=re.compile(r'^\$mysqlna\$[a-f0-9]{40}[:*][a-f0-9]{40}$', re.IGNORECASE),modes=[HashInfo(name='MySQL Challenge-Response Authentication (SHA1)', hashcat=11200, john=None, extended=False)]),Prototype(regex=re.compile(r'^\$pdf\$[24]\*[34]\*128\*[0-9-]{1,5}\*1\*(16|32)\*[a-f0-9]{32,64}\*32\*[a-f0-9]{64}\*(8|16|32)\*[a-f0-9]{16,64}$', re.IGNORECASE),modes=[HashInfo(name='PDF 1.4 - 1.6 (Acrobat 5 - 8)', hashcat=10500, john='pdf', extended=False)])
]class HashID(object):"""HashID with configurable prototypes"""def __init__(self, prototypes=prototypes):super(HashID, self).__init__()# Set self.prototypes to a copy of prototypes to allow# modification after instantiationself.prototypes = list(prototypes)def identifyHash(self, phash):"""Returns identified HashInfo"""phash = phash.strip()for prototype in self.prototypes:if prototype.regex.match(phash):for mode in prototype.modes:yield modedef writeResult(identified_modes, outfile, hashcatMode=False, johnFormat=False, extended=False):"""Write human readable output from identifyHash"""count = 0hashTypes = ""for mode in identified_modes:if not mode.extended or extended:count += 1hashTypes += u"[+] {0} ".format(mode.name)if hashcatMode and mode.hashcat is not None:hashTypes += "[Hashcat Mode: {0}]".format(mode.hashcat)if johnFormat and mode.john is not None:hashTypes += "[JtR Format: {0}]".format(mode.john)hashTypes += "\n"outfile.write(hashTypes)if count == 0:outfile.write(u"[+] Unknown hash\n")return (count > 0)def main():usage = "{0} [-h] [-e] [-m] [-j] [-o FILE] [--version] INPUT".format(os.path.basename(__file__))parser = argparse.ArgumentParser(description="Identify the different types of hashes used to encrypt data",usage=usage,epilog=__license__,add_help=False,formatter_class=lambda prog: argparse.HelpFormatter(prog, max_help_position=27))parser.add_argument("strings",metavar="INPUT", type=str, nargs="*",help="input to analyze (default: STDIN)")group = parser.add_argument_group('options')group.add_argument("-e", "--extended",action="store_true",help="list all possible hash algorithms including salted passwords")group.add_argument("-m", "--mode",action="store_true",help="show corresponding Hashcat mode in output")group.add_argument("-j", "--john",action="store_true",help="show corresponding JohnTheRipper format in output")group.add_argument("-o", "--outfile",metavar="FILE", type=str,help="write output to file")group.add_argument("-h", "--help",action="help",help="show this help message and exit")group.add_argument("--version",action="version",version=__banner__)args = parser.parse_args()hashID = HashID()if not args.outfile:outfile = sys.stdoutelse:try:outfile = io.open(args.outfile, "w", encoding="utf-8")except EnvironmentError:parser.error("Could not open {0}".format(args.output))if not args.strings or args.strings[0] == "-":while True:line = sys.stdin.readline()if not line:breakoutfile.write(u"Analyzing '{0}'\n".format(line.strip()))writeResult(hashID.identifyHash(line), outfile, args.mode, args.john, args.extended)sys.stdout.flush()else:for string in args.strings:if os.path.isfile(string):try:with io.open(string, "r", encoding="utf-8") as infile:outfile.write("--File '{0}'--\n".format(string))for line in infile:if line.strip():outfile.write(u"Analyzing '{0}'\n".format(line.strip()))writeResult(hashID.identifyHash(line), outfile, args.mode, args.john, args.extended)except (EnvironmentError, UnicodeDecodeError):outfile.write("--File '{0}' - could not open--".format(string))else:outfile.write("--End of file '{0}'--".format(string))else:outfile.write(u"Analyzing '{0}'\n".format(string.strip()))writeResult(hashID.identifyHash(string), outfile, args.mode, args.john, args.extended)if __name__ == "__main__":try:main()except KeyboardInterrupt:pass2.2、安装
您可以使用以下命令安装、升级、卸载 hashID:
$ pip install hashid
$ pip install --upgrade hashid
$ pip uninstall hashid或者,您可以通过克隆存储库进行安装:
$ sudo apt-get install python3 git
$ git clonehttps://github.com/psypanda/hashid.git
$ cd hashid
$ sudo install -g 0 -o 0 -m 0644 doc/man/hashid.7 /usr/share/man/man7/
$ sudo gzip /usr/share/man/man7/hashid.72.3、用法
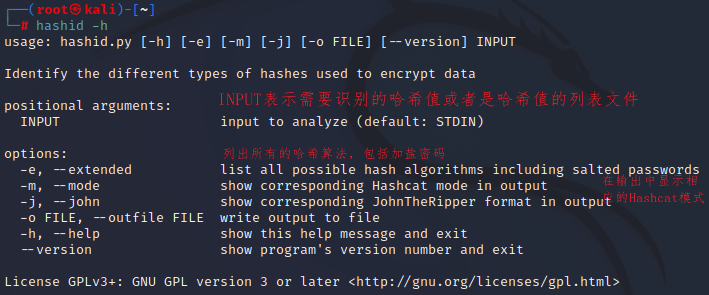
-e 把包括加盐的HASH算法显示出来
-m 显示对应的hashcat解密模式编号(hashcat是款很棒的密码爆破工具,开源),该参数是为配合hashcat工具使用的;
-j 显示对应的johnTheRipper 格式名称;
-o file 输出结果到文件
INPUT 要识别的哈希值或者哈希值的列表文件
$./hashid.py'$P$8ohUJ.1sdFw09/bMaAQPTGDNi2BIUt1'
Analyzing'$P$8ohUJ.1sdFw09/bMaAQPTGDNi2BIUt1'
[+]Wordpress ≥ v2.6.2
[+]Joomla ≥ v2.5.18
[+]PHPass' Portable Hash$./hashid.py-mj'$racf$*AAAAAAAA*3c44ee7f409c9a9b'
Analyzing'$racf$*AAAAAAAA*3c44ee7f409c9a9b'
[+]RACF[Hashcat Mode:8500][JtR Format:racf]$./hashid.py hashes.txt
--File'hashes.txt'--
Analyzing'*85ADE5DDF71E348162894C71D73324C043838751'
[+]MySQL5.x
[+]MySQL4.1
Analyzing'$2a$08$VPzNKPAY60FsAbnq.c.h5.XTCZtC1z.j3hnlDFGImN9FcpfR1QnLq'
[+]Blowfish(OpenBSD)
[+]Woltlab Burning Board4.x
[+]bcrypt
--End of file'hashes.txt'--三、yara规则匹配查找文件使用的特定加密算法
文件:libcurl.so.5.3.0
yara文件:https://github.com/leiwuhen92/yara_rule/blob/main/compile_rule/crypto_hints.yc
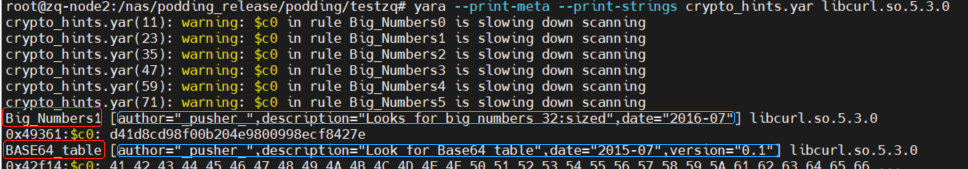
代码逻辑如下:
import pathlib
import yaraNAME = "crypto_hints"
DESCRIPTION = "find indicators of specific crypto algorithms"
CHINESE_NAME ="加密算法检测"
CHINESE_DESCRIPTION = "查找特定加密算法"# 结果存储位置
classFileAnalysis():def__init__(self):self.file_path="libcurl.so.5.3.0"self.processed_analysis={}
file_object=FileAnalysis()# 特征文件路径
compile_path=pathlib.Path("crypto_hints.yc")
# 加载特征文件
rule=yara.load(str(compile_path))# 匹配
result=rule.match(file_object.file_path)
print("result:%s"%result) # result:[Big_Numbers1, BASE64_table]# 解析结果
file_object.processed_analysis[NAME]={}
summary=set()
foriteminresult:print(item)print(item.rule)print(item.meta)summary.add(item.rule)file_object.processed_analysis[NAME][item.rule]={"meta":item.meta}
file_object.processed_analysis[NAME]["summary"]=list(summary)mongo_data={"file_path":file_object.file_path,"processed_analysis":file_object.processed_analysis
}
print(mongo_data)'''
result:[Big_Numbers1, BASE64_table]
Big_Numbers1
Big_Numbers1
{'author': '_pusher_', 'description': 'Looks for big numbers 32:sized', 'date': '2016-07'}
BASE64_table
BASE64_table
{'author': '_pusher_', 'description': 'Look for Base64 table', 'date': '2015-07', 'version': '0.1'}{"file_path": "libcurl.so.5.3.0","processed_analysis": {"crypto_hints": {"Big_Numbers1": {"meta": {"author": "_pusher_","description": "Looks for big numbers 32:sized","date": "2016-07"}},"BASE64_table": {"meta": {"author": "_pusher_","description": "Look for Base64 table","date": "2015-07","version": "0.1"}},"summary": ["BASE64_table","Big_Numbers1"]}}
}
'''结果可知,libcurl.so.5.3.0文件的加密算法有两种:BASE64_table、Big_Numbers1。
备注:工具匹配操作如下
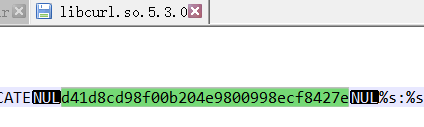
> Big_Numbers1的yara规则如下:[0-9a-fA-F]{32}
rule Big_Numbers1
{meta:author = "_pusher_"description = "Looks for big numbers 32:sized"date = "2016-07"strings:$c0 = /[0-9a-fA-F]{32}/ fullword wide asciicondition:$c0
}notepad打开libcurl.so.5.3.0,编码选择ANSI,正则搜索[0-9a-fA-F]{32},匹配到了
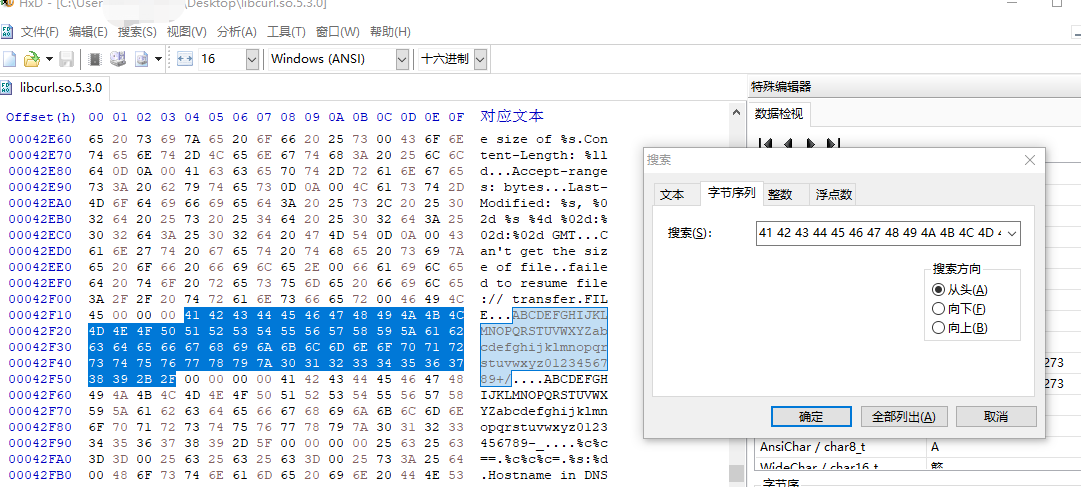
> BASE64_table的yara规则如下:
rule BASE64_table {meta:author = "_pusher_"description = "Look for Base64 table"date = "2015-07"version = "0.1"strings:$c0 = { 41 42 43 44 45 46 47 48 49 4A 4B 4C 4D 4E 4F 50 51 52 53 54 55 56 57 58 59 5A 61 62 63 64 65 66 67 68 69 6A 6B 6C 6D 6E 6F 70 71 72 73 74 75 76 77 78 79 7A 30 31 32 33 34 35 36 37 38 39 2B 2F }condition:$c0
}HxD打开,十六进制,ANSI编码,根据“字节序列”搜索“41 42 43 44 45 46 47 48 49 4A 4B 4C 4D 4E 4F 50 51 52 53 54 55 56 57 58 59 5A 61 62 63 64 65 66 67 68 69 6A 6B 6C 6D 6E 6F 70 71 72 73 74 75 76 77 78 79 7A 30 31 32 33 34 35 36 37 38 39 2B 2F”,匹配到了
四、参考
(1条消息) hashid/hash-identifier显示加密算法_ANIJ的博客-CSDN博客_hash-identifier
https://github.com/psypanda/hashid.git
https://github.com/Miserlou/Hash-Identifier.git
相关文章:

识别密文加密类型
离线密码破解:离线不会触发密码锁定机制不会产生大量登录失败日志引起管理员注意HASH识别工具(识别哈希类型):hash-identifierHashid yara规则匹配文件得到特定加密算法一、hash-identifierKali Linux提供工具hash-identifier来识…...
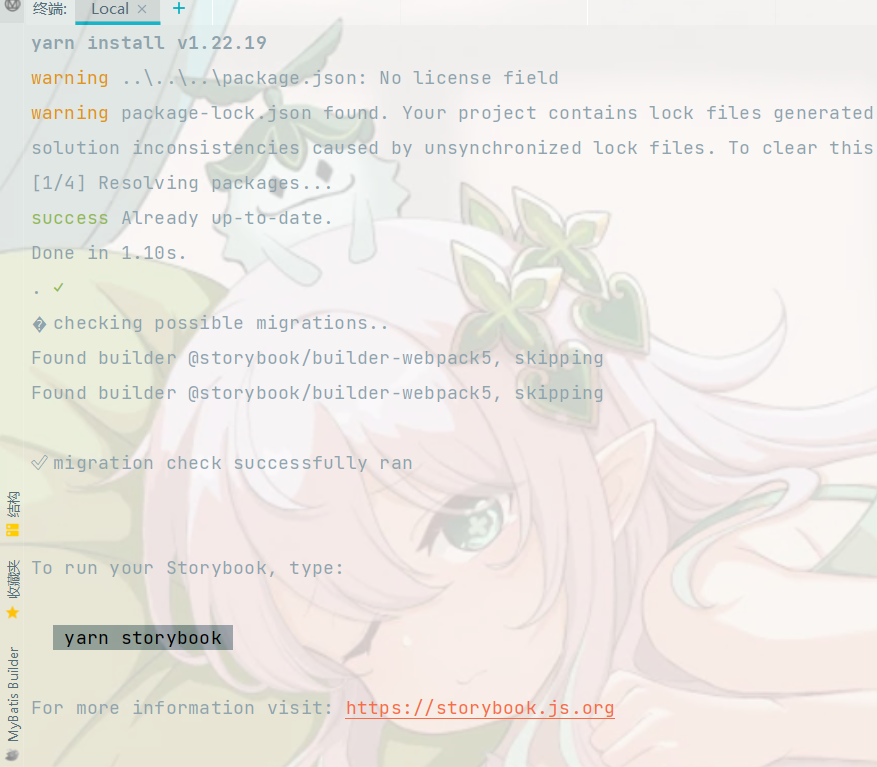
node报错
记录bug:运行 npx -p storybook/cli sb init 时报错gyp info spawn C:\Program Files\Microsoft Visual Studio\2022\Community\MSBuild\Current\Bin\MSBuild.exegyp info spawn args [gyp info spawn args build/binding.sln,gyp info spawn args /nologo,gyp info spawn args…...
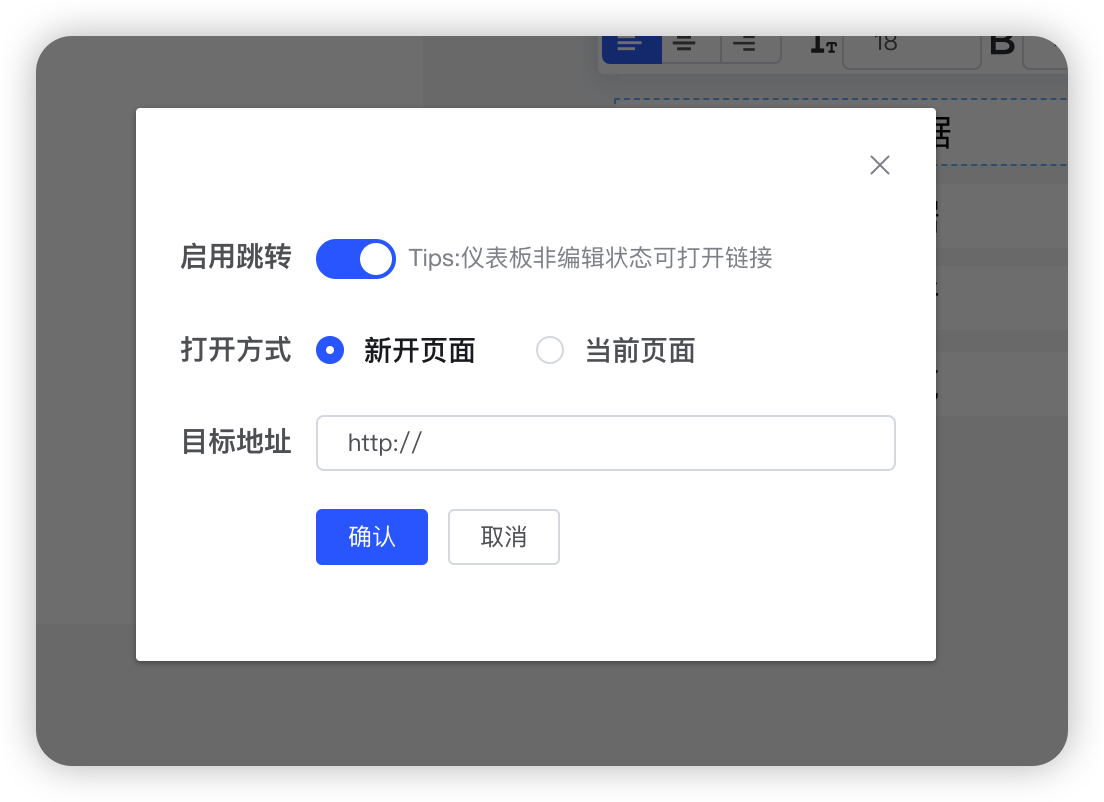
如何使用开源 BI 工具 DataEase 实现系列数据分析呢?
当我们使用可视化分析工具制作仪表板时,可能需要制作的仪表板不是单个单个的可视化大屏,而是一系列的仪表板,我们需要用它来产生一个连续性的故事,那么这个时候我们该怎么办呢?例如说总分形式,我们需要一个…...
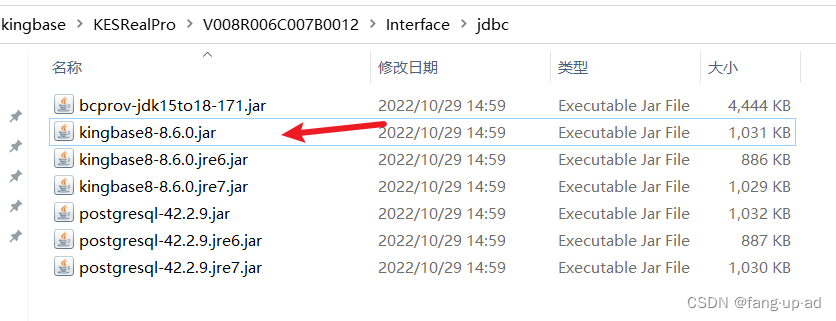
金仓数据库安装
一、麒麟操作系统安装金仓数据库 操作系统 DISTRIB_IDKylin DISTRIB_RELEASEV10 DISTRIB_CODENAMEjuniper 按照安装文档的步骤安装,记得记住设置的数据库的用户名、密码 二、window安装连接数据库的工具软件 三、jdbc连接数据库 (1)连接工…...

深入浅出Webpack2-快速掌握webpack基本配置
深入浅出Webpack2-快速掌握webpack基本配置1.Entry1.1 context1.2 Entry类型2.Output2.1 filename2.2 path3.Module3.1配置Loader4.Resolve4.1 alias4.2 extensions4.3 modules5.Plugin6.DevServer7.其他配置项上一篇文章我们快速上手认识了一下webpack,今天这篇文章…...
如何使评论具有可操作性?取悦客户的指南
永远不要低估承认的力量。 当品牌与客户互动时,认可会带来更好的关系和更好的沟通。与买家和客户建立更多的个人联系意味着品牌需要证明他们支持他们的产品和客户。评论是利用客户分享他们的故事的那些时刻的绝佳机会。 为什么评论在 SaaS 中至关重要 在 B2B 软件的…...
一文带你彻底搞懂Nginx反向代理
一文带你彻底搞懂Nginx反向代理一、什么是反向代理1.1 正向代理1.2 反向代理1.3 总结二、配置反向代理2.1 准备 Tomcat2.2 配置 Nginx一、什么是反向代理 1.1 正向代理 举一个通俗的例子,因为众所周知的原因,我们无法访问谷歌,但是因为某些…...
手写SpringBoot的starter
自定义SpringBoot的starter 引言 starter命名格式: 官方的 starter 的命名格式为 spring-boot-starter-{xxxx} 比如spring-boot-starter-activemq 第三方我们自己的命名格式为 {xxxx}-spring-boot-starter。比如mybatis-spring-boot-starter。 如果我们忽略这种约定…...
pytorch1.2.0+python3.6
一、说明 pytorch1.2.0python3.6CUDA10.0cudnn7.4.1.5 二、步骤 在conda中创建一个新的虚拟环境 查看一下自己的所有环境 激活虚拟环境 conda activate torch1.2.0 关于cuda和cudnn 1、查看自己电脑系统是10.2版本 http://链接:https://pan.baidu.com/s/1v5cN6…...
WindowsPowerShell 停止、启动、暂停和重启服务、卸载服务
PowerShell 停止、启动、暂停和重启服务、卸载服务 PowerShell 停止、启动、暂停和重启服务 官文 powershell卸载服务 官文 目录PowerShell 停止、启动、暂停和重启服务、卸载服务停止、启动、暂停和重启停止服务启动服务暂停服务重启服务卸载移除服务停止、启动、暂停、重启…...
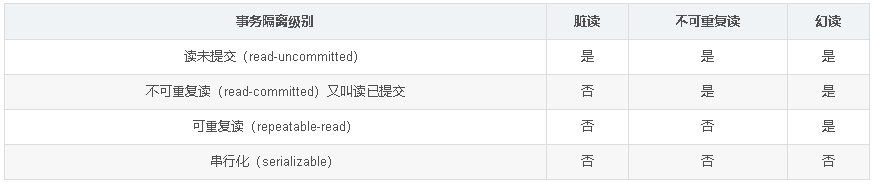
数据库专题
请简洁描述 MySQL 中 InnoDB 支持的四种事务隔离级别名称,以及逐级之间的区别? 默认隔离级别 mysql repeatable-read oracle read-committed 脏读:不可重复读:幻读: CHAR 和 VARCHAR 的区别?…...
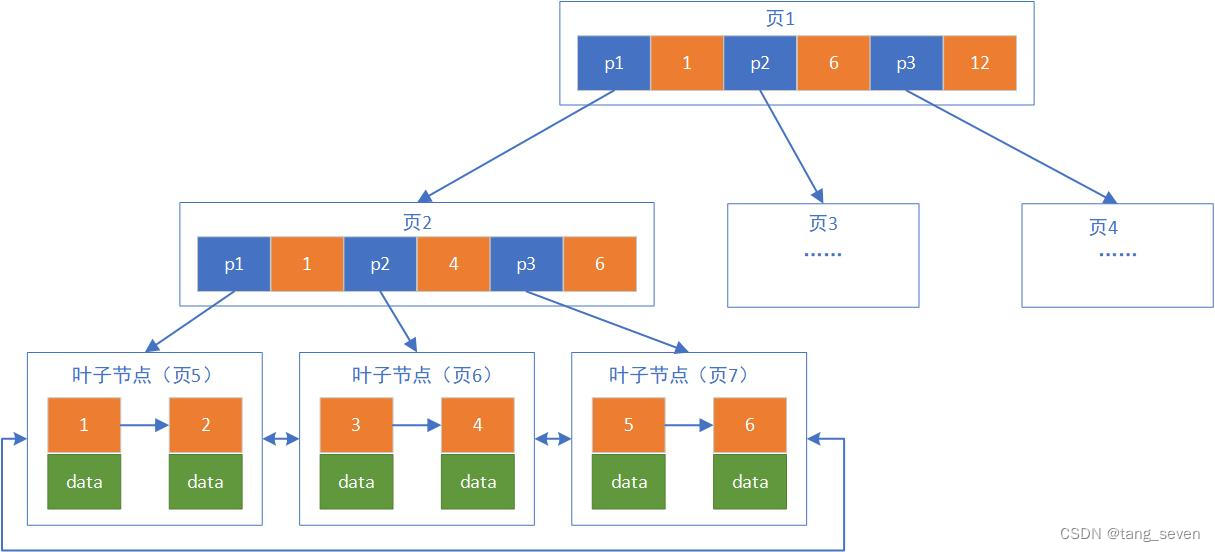
浅谈MySQL索引
目录 1.索引的定义 2.索引的原理 3.Hash索引与B Tree索引 4.索引的分类 5.建立索引的注意事项 1.索引的定义 索引是存储引擎用于快速找到数据记录的一种数据结构,它是某个表中一列或若干列值的集合和相应的指向表中物理标识这些值的数据页的逻辑指针清单。 索…...

安装包UI美化之路-通过nsNiuniuSkin来做Electron程序的打包、发布与升级
nsNiuniuSkin从发布之初,因其简单、简洁、高效,受到了非常多公司的青睐,现在已经越来越多的公司采用我们的这套解决方案来制作安装包了! 从一个安装包UI插件,逐步演化成一套集美观、安全、简洁、自动化为一体的完整的…...
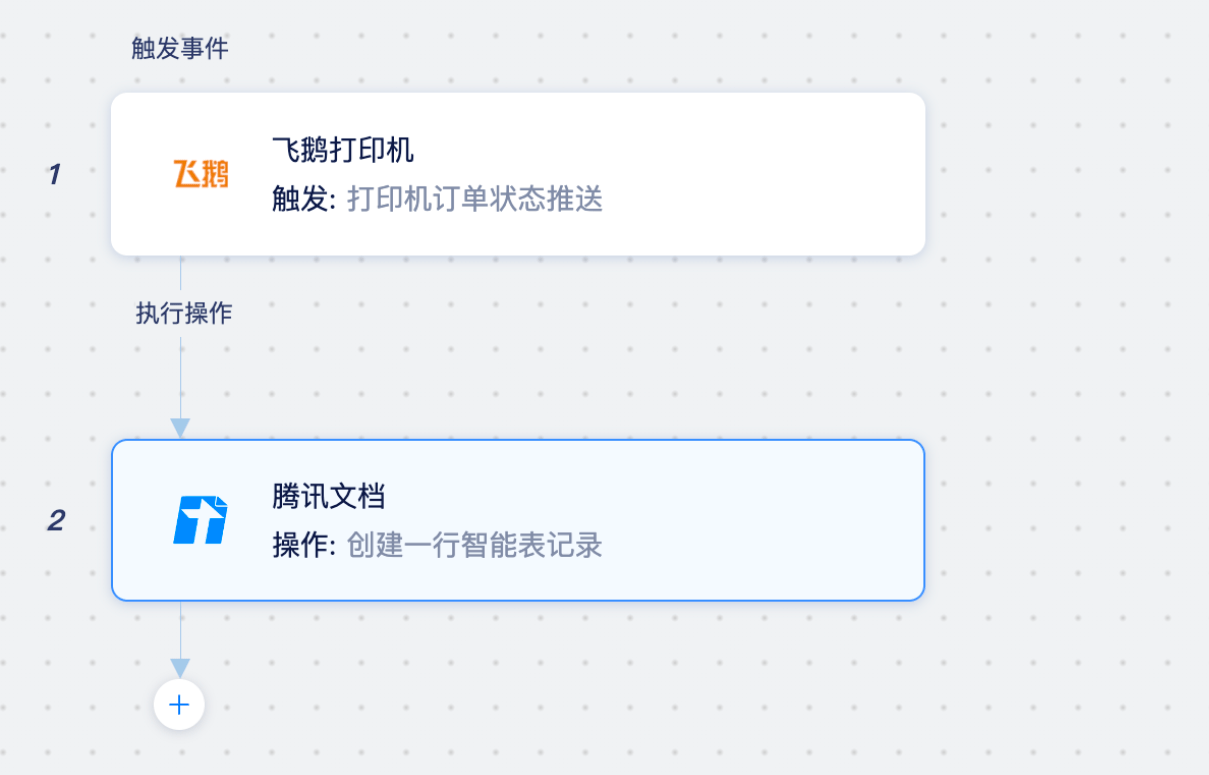
飞鹅打印机怎么样?飞鹅打印机好用吗?飞鹅打印机怎么知道订单是否漏单?
外卖打印机怎么选?飞鹅打印机好用吗?飞鹅智能云打印机产品专注于云打印的解决方案和技术服务提供。2019 年飞鹅已经成为国内先进的云打印服务提供商,主要是服务美团、饿了么客户,产品主要优势:自动接单、自动打印,无需…...
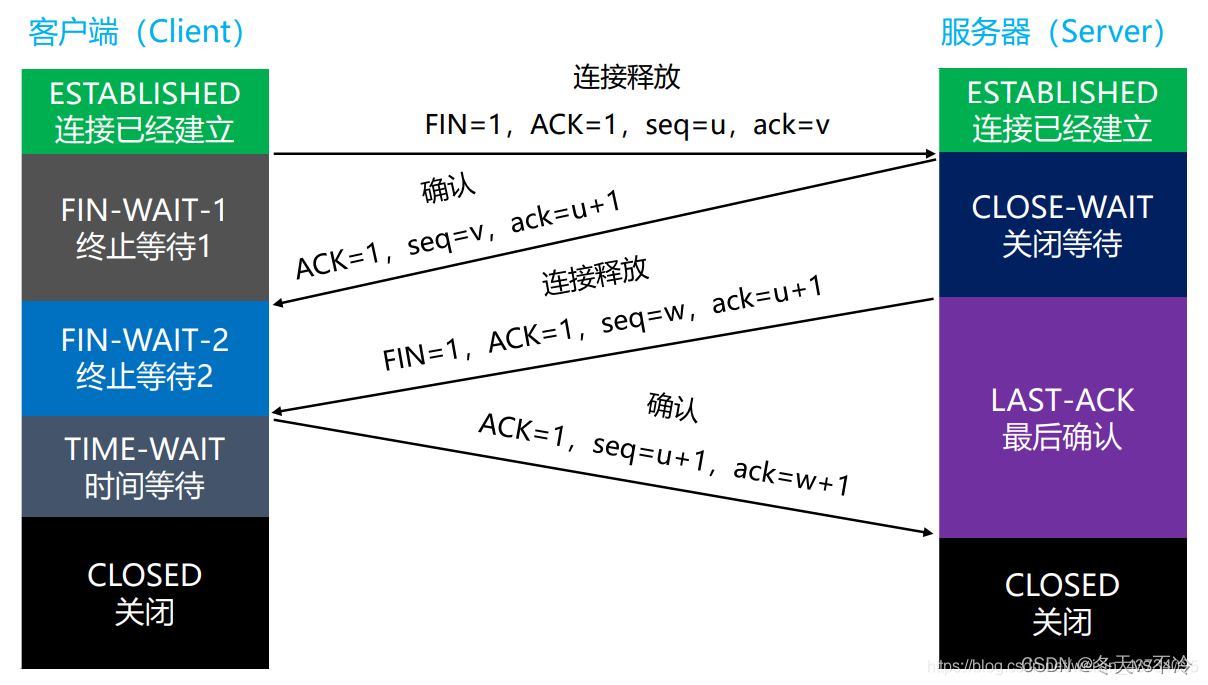
网络协议(八):传输层-TCP(三次握手、四次挥手原理)
网络协议系列文章 网络协议(一):基本概念、计算机之间的连接方式 网络协议(二):MAC地址、IP地址、子网掩码、子网和超网 网络协议(三):路由器原理及数据包传输过程 网络协议(四):网络分类、ISP、上网方式、公网私网、NAT 网络…...

最新OpenMVG编译安装与逐命令运行增量式和全局式SfM教程
openmvg是一个轻便的可以逐步运行的SfM开源库,它同时实现了增量式和全局式两种算法。 说明文档地址:https://openmvg.readthedocs.io/en/latest/ github主页地址:https://github.com/openMVG/openMVG 1 编译安装 openmvg的安装比较简单&…...

数据结构与算法系列之插入排序
💗 💗 博客:小怡同学 💗 💗 个人简介:编程小萌新 💗 💗 如果博客对大家有用的话,请点赞关注再收藏 🌞 什么是插入排序 有一个已经有序的数据序列,要求在这个已经排好的数…...

Text to image论文精读ALR-GAN:文本到图像合成的自适应布局优化
ALR-GAN是北京工业大学学者提出的一种自适应布局优化生成对抗网络,其可以在没有任何辅助信息的情况下自适应地优化合成图像的布局。 文章发表于2023年,IEEE Transactions on Multimedia(TMM)期刊(CCF B,JCR…...
windows版 redis在同一局域网下互联
项目场景: 同一局域网下各个主机互相连接同一个redis 问题描述 无法连接 原因分析: 没有放行对方的地址 解决方案: 修改配置文件 最重要的一步如下 然后把 redis.windows.conf的文件也照上面的修改一下保持一致 然后安装一下redis服务这…...

Near-Optimal Bayesian Online Assortment of Reusable Resources
摘要 受租赁服务在电子商务中的应用的激励,我们考虑为不同类型的到达消费者提供可重复使用资源的在线分类的收入最大化。我们针对贝叶斯环境中的最优在线策略设计了具有竞争力的在线算法,其中类型随时间独立于已知的异构分布绘制。在初始库存最小值cmin…...
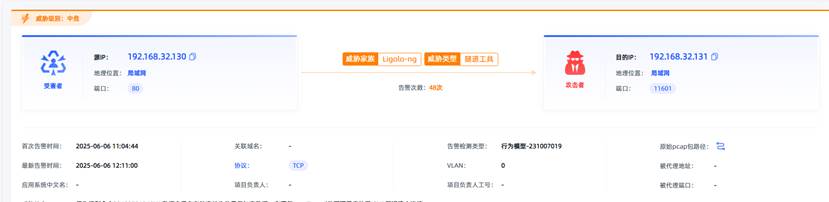
观成科技:隐蔽隧道工具Ligolo-ng加密流量分析
1.工具介绍 Ligolo-ng是一款由go编写的高效隧道工具,该工具基于TUN接口实现其功能,利用反向TCP/TLS连接建立一条隐蔽的通信信道,支持使用Let’s Encrypt自动生成证书。Ligolo-ng的通信隐蔽性体现在其支持多种连接方式,适应复杂网…...

day52 ResNet18 CBAM
在深度学习的旅程中,我们不断探索如何提升模型的性能。今天,我将分享我在 ResNet18 模型中插入 CBAM(Convolutional Block Attention Module)模块,并采用分阶段微调策略的实践过程。通过这个过程,我不仅提升…...
【机器视觉】单目测距——运动结构恢复
ps:图是随便找的,为了凑个封面 前言 在前面对光流法进行进一步改进,希望将2D光流推广至3D场景流时,发现2D转3D过程中存在尺度歧义问题,需要补全摄像头拍摄图像中缺失的深度信息,否则解空间不收敛…...
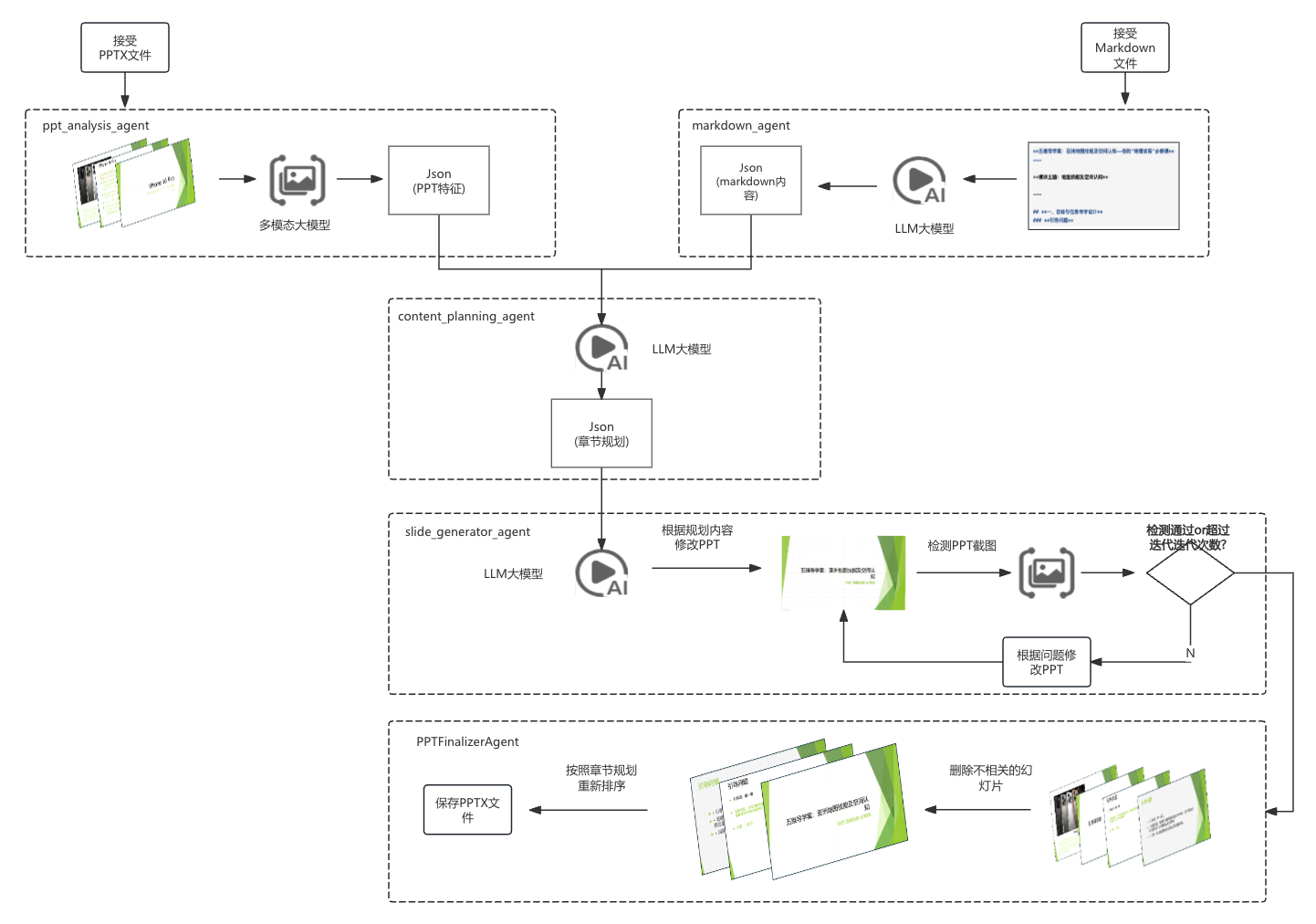
【项目实战】通过多模态+LangGraph实现PPT生成助手
PPT自动生成系统 基于LangGraph的PPT自动生成系统,可以将Markdown文档自动转换为PPT演示文稿。 功能特点 Markdown解析:自动解析Markdown文档结构PPT模板分析:分析PPT模板的布局和风格智能布局决策:匹配内容与合适的PPT布局自动…...
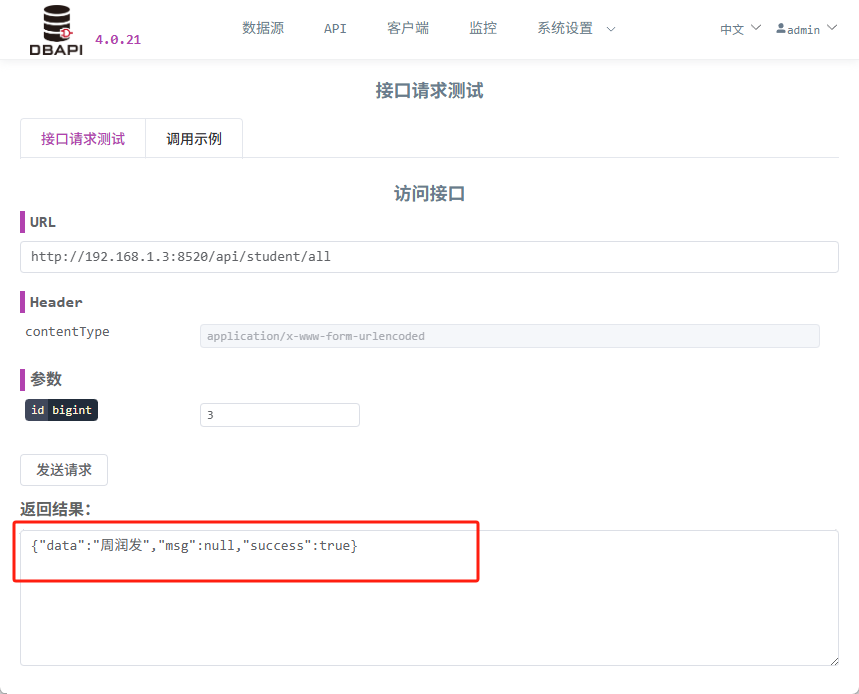
DBAPI如何优雅的获取单条数据
API如何优雅的获取单条数据 案例一 对于查询类API,查询的是单条数据,比如根据主键ID查询用户信息,sql如下: select id, name, age from user where id #{id}API默认返回的数据格式是多条的,如下: {&qu…...

CRMEB 框架中 PHP 上传扩展开发:涵盖本地上传及阿里云 OSS、腾讯云 COS、七牛云
目前已有本地上传、阿里云OSS上传、腾讯云COS上传、七牛云上传扩展 扩展入口文件 文件目录 crmeb\services\upload\Upload.php namespace crmeb\services\upload;use crmeb\basic\BaseManager; use think\facade\Config;/*** Class Upload* package crmeb\services\upload* …...

CMake控制VS2022项目文件分组
我们可以通过 CMake 控制源文件的组织结构,使它们在 VS 解决方案资源管理器中以“组”(Filter)的形式进行分类展示。 🎯 目标 通过 CMake 脚本将 .cpp、.h 等源文件分组显示在 Visual Studio 2022 的解决方案资源管理器中。 ✅ 支持的方法汇总(共4种) 方法描述是否推荐…...

Kafka主题运维全指南:从基础配置到故障处理
#作者:张桐瑞 文章目录 主题日常管理1. 修改主题分区。2. 修改主题级别参数。3. 变更副本数。4. 修改主题限速。5.主题分区迁移。6. 常见主题错误处理常见错误1:主题删除失败。常见错误2:__consumer_offsets占用太多的磁盘。 主题日常管理 …...
tauri项目,如何在rust端读取电脑环境变量
如果想在前端通过调用来获取环境变量的值,可以通过标准的依赖: std::env::var(name).ok() 想在前端通过调用来获取,可以写一个command函数: #[tauri::command] pub fn get_env_var(name: String) -> Result<String, Stri…...
【Linux手册】探秘系统世界:从用户交互到硬件底层的全链路工作之旅
目录 前言 操作系统与驱动程序 是什么,为什么 怎么做 system call 用户操作接口 总结 前言 日常生活中,我们在使用电子设备时,我们所输入执行的每一条指令最终大多都会作用到硬件上,比如下载一款软件最终会下载到硬盘上&am…...
