用OpenSSL搭建PKI证书体系
1 创建PKI结构目录
mkdir 07_PKI
cd 07_PKI
mkdir 01_RootCA 02_SubCA 03_Client
2 创建根CA
cd 01_RootCA
mkdir key csr cert newcerts
touch index.txt index.txt.attr
echo 01 > serial
2.1 创建根CA密钥对
2.1.1 生成 长度为2048 bit 的RSA私钥。
cd key
openssl genrsa -out pri_key.pem 2048
2.1.2 查看生成的RSA私钥。
openssl rsa -in pri_key.pem -text
2.1.3 从私钥文件中提取RSA公钥
openssl rsa -in pri_key.pem -pubout -out pub_key.pem#
2.2 创建根CA的证书签名请求(CSR)
2.2.1 创建CSR
创建根 CA 配置文件 rootca.conf:
cd ..
touch rootca.conf
根 CA 配置文件 rootca.conf 内容如下:
[ ca ]
default_ca = CA_default[ CA_default ]
dir = E:/07_PKI/01_RootCA
certs = $dir/cert
crl_dir = $dir/crl
database = $dir/index.txt
new_certs_dir = $dir/newcerts
certificate = $dir/cert/rootca_cert.crt
serial = $dir/serial
crlnumber = $dir/crlnumber
crl = $dir/crl.pem
private_key = $dir/key/pri_key.pem
RANDFILE = $dir/key/.rand
unique_subject = nox509_extensions = usr_cert
copy_extensions = copyname_opt = ca_default
cert_opt = ca_defaultdefault_days = 5475
default_crl_days= 60
default_md = sha256
preserve = no
policy = policy_ca[ policy_ca ]
countryName = supplied
stateOrProvinceName = supplied
localityName = supplied
organizationName = supplied
organizationalUnitName = optional
commonName = supplied
emailAddress = optional[ req ]
default_bits = 2048
default_keyfile = pri_key.pem
distinguished_name = req_distinguished_name
attributes = req_attributes
x509_extensions = v3_ca
string_mask = utf8only
utf8 = yes
prompt = no[ req_distinguished_name ]
countryName = CN
stateOrProvinceName = GuangDong
localityName = ShenZhen
organizationName = TangTring
commonName = RootCA[ usr_cert ]
basicConstraints = CA:TRUE[ v3_ca ]
basicConstraints = CA:TRUE[ req_attributes ]创建根 CA 证书签名请求文件,指定签名算法为 sha256,默认为 sha1 算法。
cd csr
openssl req -new -key ../key/pri_key.pem -out rootca_csr.pem -config ../rootca.conf
2.2.2 查看CSR
openssl req -in rootca_csr.pem
输出内容如下:
-----BEGIN CERTIFICATE REQUEST-----
MIICnjCCAYYCAQAwWTELMAkGA1UEBhMCQ04xEjAQBgNVBAgMCUd1YW5nRG9uZzER
MA8GA1UEBwwIU2hlblpoZW4xEjAQBgNVBAoMCVRhbmdUcmluZzEPMA0GA1UEAwwG
Um9vdENBMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsGjDN8ge3f9i
CrAfsrLln/RMXz7EAqMMIjGmChMlQdXEArCT/FdxfoomOWfTHRTREnFthZ9w+TOq
kvgOyQuiFGTJRZ2c3T2FidfFJ5yA06UOELBXWXqhjvYYP+EWGtdn0kOg/tA7QKTG
ZyggQzJQmsAfZkk5vpV1Ok+ZtwoxWZPL0/xBRxZAuF2gxByN4Mt81rsgWLowPX5X
tINDCifEx1BlHZGxlWUWVIVj1SAf+g2S42s5d1xNrZNpKTMe46bduLuYGk4SqeZP
uXyTkVLq00VmgM7Ma9UHucrBmYQ/ybDJlOjgON1rVQqXR0dWTwx65iOVzAf+0hYj
Lc96+ZarEwIDAQABoAAwDQYJKoZIhvcNAQELBQADggEBAAecVqSze262UIRgBYWG
RQAri+DM84tfVzj7ayIZnpBCHpi2dsatFRxAmwgKwhv/syE7xyTRQ8kUzBBIts6s
hqDblMRl/RDO05iXlk1US3rIoWhJvUrK++aWLHQTYfMMCCdEblRg4IMi1E1CFWSW
nmsnqHsb/JSdWKrGlpZFHamLHafR0IcTWwLierQ30DEvDuLLYbWO2VKq2u2r69V8
MDhOc8em1PEEdLGZR+QkJ+wKj1xt5ICn2KuQfrQXk5QdnkR2Wti/hZMm4rOQd8A1
APOWJAroYwdgNam/csyNF7binpEczCSamseWgrajTPhIdB+IUfjk3ha+djP10ivo
JYo=
-----END CERTIFICATE REQUEST-----
以文本形式输出请求文件头使用 -noout -text 参数.
openssl req -in rootca_csr.pem -text -noout
输出如下:
Certificate Request:Data:Version: 1 (0x0)Subject: C=CN, ST=GuangDong, L=ShenZhen, O=TangTring, CN=RootCASubject Public Key Info:Public Key Algorithm: rsaEncryptionPublic-Key: (2048 bit)Modulus:00:b0:68:c3:37:c8:1e:dd:ff:62:0a:b0:1f:b2:b2:e5:9f:f4:4c:5f:3e:c4:02:a3:0c:22:31:a6:0a:13:25:41:d5:c4:02:b0:93:fc:57:71:7e:8a:26:39:67:d3:1d:14:d1:12:71:6d:85:9f:70:f9:33:aa:92:f8:0e:c9:0b:a2:14:64:c9:45:9d:9c:dd:3d:85:89:d7:c5:27:9c:80:d3:a5:0e:10:b0:57:59:7a:a1:8e:f6:18:3f:e1:16:1a:d7:67:d2:43:a0:fe:d0:3b:40:a4:c6:67:28:20:43:32:50:9a:c0:1f:66:49:39:be:95:75:3a:4f:99:b7:0a:31:59:93:cb:d3:fc:41:47:16:40:b8:5d:a0:c4:1c:8d:e0:cb:7c:d6:bb:20:58:ba:30:3d:7e:57:b4:83:43:0a:27:c4:c7:50:65:1d:91:b1:95:65:16:54:85:63:d5:20:1f:fa:0d:92:e3:6b:39:77:5c:4d:ad:93:69:29:33:1e:e3:a6:dd:b8:bb:98:1a:4e:12:a9:e6:4f:b9:7c:93:91:52:ea:d3:45:66:80:ce:cc:6b:d5:07:b9:ca:c1:99:84:3f:c9:b0:c9:94:e8:e0:38:dd:6b:55:0a:97:47:47:56:4f:0c:7a:e6:23:95:cc:07:fe:d2:16:23:2d:cf:7a:f9:96:ab:13Exponent: 65537 (0x10001)Attributes:(none)Requested Extensions:Signature Algorithm: sha256WithRSAEncryptionSignature Value:07:9c:56:a4:b3:7b:6e:b6:50:84:60:05:85:86:45:00:2b:8b:e0:cc:f3:8b:5f:57:38:fb:6b:22:19:9e:90:42:1e:98:b6:76:c6:ad:15:1c:40:9b:08:0a:c2:1b:ff:b3:21:3b:c7:24:d1:43:c9:14:cc:10:48:b6:ce:ac:86:a0:db:94:c4:65:fd:10:ce:d3:98:97:96:4d:54:4b:7a:c8:a1:68:49:bd:4a:ca:fb:e6:96:2c:74:13:61:f3:0c:08:27:44:6e:54:60:e0:83:22:d4:4d:42:15:64:96:9e:6b:27:a8:7b:1b:fc:94:9d:58:aa:c6:96:96:45:1d:a9:8b:1d:a7:d1:d0:87:13:5b:02:e2:7a:b4:37:d0:31:2f:0e:e2:cb:61:b5:8e:d9:52:aa:da:ed:ab:eb:d5:7c:30:38:4e:73:c7:a6:d4:f1:04:74:b1:99:47:e4:24:27:ec:0a:8f:5c:6d:e4:80:a7:d8:ab:90:7e:b4:17:93:94:1d:9e:44:76:5a:d8:bf:85:93:26:e2:b3:90:77:c0:35:00:f3:96:24:0a:e8:63:07:60:35:a9:bf:72:cc:8d:17:b6:e2:9e:91:1c:cc:24:9a:9a:c7:96:82:b6:a3:4c:f8:48:74:1f:88:51:f8:e4:de:16:be:76:33:f5:d2:2b:e8:25:8a
2.2.3 验证CSR的签名
openssl req -verify -in rootca_csr.pem -noout
输出:
Certificate request self-signature verify OK
2.3 创建根CA自签名证书
2.3.1 生成根CA证书
生成自签名的根CA证书:
cd ../cert
openssl ca -selfsign -in ../csr/rootca_csr.pem -out rootca_cert.crt -config ../rootca.conf
输出内容如下:
Using configuration from ../rootca.conf
Check that the request matches the signature
Signature ok
Certificate Details:Serial Number: 1 (0x1)ValidityNot Before: Sep 24 07:32:28 2024 GMTNot After : Sep 21 07:32:28 2039 GMTSubject:countryName = CNstateOrProvinceName = GuangDonglocalityName = ShenZhenorganizationName = TangTringcommonName = RootCAX509v3 extensions:X509v3 Basic Constraints:CA:TRUE
Certificate is to be certified until Sep 21 07:32:28 2039 GMT (5475 days)
Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Database updated
2.3.2 查看证书文件:
以文本形式查看证书文件:
openssl x509 -in rootca_cert.crt -text -noout
输出内容如下:
Certificate:Data:Version: 3 (0x2)Serial Number:54:31:e1:11:20:6c:0e:7b:a2:3b:fc:17:64:a4:30:a3:d7:75:b2:00Signature Algorithm: sha256WithRSAEncryptionIssuer: C=CN, ST=GuangDong, L=ShenZhen, O=TangTring, CN=RootCAValidityNot Before: Sep 24 02:52:22 2024 GMTNot After : Sep 22 02:52:22 2034 GMTSubject: C=CN, ST=GuangDong, L=ShenZhen, O=TangTring, CN=RootCASubject Public Key Info:Public Key Algorithm: rsaEncryptionPublic-Key: (2048 bit)Modulus:00:b0:68:c3:37:c8:1e:dd:ff:62:0a:b0:1f:b2:b2:e5:9f:f4:4c:5f:3e:c4:02:a3:0c:22:31:a6:0a:13:25:41:d5:c4:02:b0:93:fc:57:71:7e:8a:26:39:67:d3:1d:14:d1:12:71:6d:85:9f:70:f9:33:aa:92:f8:0e:c9:0b:a2:14:64:c9:45:9d:9c:dd:3d:85:89:d7:c5:27:9c:80:d3:a5:0e:10:b0:57:59:7a:a1:8e:f6:18:3f:e1:16:1a:d7:67:d2:43:a0:fe:d0:3b:40:a4:c6:67:28:20:43:32:50:9a:c0:1f:66:49:39:be:95:75:3a:4f:99:b7:0a:31:59:93:cb:d3:fc:41:47:16:40:b8:5d:a0:c4:1c:8d:e0:cb:7c:d6:bb:20:58:ba:30:3d:7e:57:b4:83:43:0a:27:c4:c7:50:65:1d:91:b1:95:65:16:54:85:63:d5:20:1f:fa:0d:92:e3:6b:39:77:5c:4d:ad:93:69:29:33:1e:e3:a6:dd:b8:bb:98:1a:4e:12:a9:e6:4f:b9:7c:93:91:52:ea:d3:45:66:80:ce:cc:6b:d5:07:b9:ca:c1:99:84:3f:c9:b0:c9:94:e8:e0:38:dd:6b:55:0a:97:47:47:56:4f:0c:7a:e6:23:95:cc:07:fe:d2:16:23:2d:cf:7a:f9:96:ab:13Exponent: 65537 (0x10001)X509v3 extensions:X509v3 Subject Key Identifier:D9:C2:22:B4:CA:46:BA:AC:32:D6:AC:97:BF:81:17:09:A9:D5:04:F6X509v3 Authority Key Identifier:D9:C2:22:B4:CA:46:BA:AC:32:D6:AC:97:BF:81:17:09:A9:D5:04:F6X509v3 Basic Constraints: criticalCA:TRUESignature Algorithm: sha256WithRSAEncryptionSignature Value:76:02:c3:e9:da:e5:c9:37:75:57:fd:97:62:80:9f:3b:67:a0:f3:32:7d:1e:3a:f4:bd:c2:e4:10:3f:b6:64:7c:2e:9a:47:e4:5a:56:c6:c4:fc:b9:68:2a:ef:83:d9:10:b3:e2:23:93:2c:47:49:4c:df:d4:3f:ea:c2:76:bb:2a:c4:a0:c6:c0:f9:2c:5a:43:1f:dd:84:16:89:6d:a6:b4:7c:16:58:fa:90:a9:36:0c:b1:e4:d8:57:30:a4:47:d9:ec:a4:df:df:57:ea:69:9a:fa:27:7c:db:77:5f:ad:25:84:78:8b:a5:2c:cc:22:93:01:f8:9d:65:ce:dc:4a:b3:a2:e7:df:b8:c4:74:ee:99:d3:27:db:1e:6a:13:e2:b1:d2:6d:86:05:be:f7:46:e6:4d:14:67:85:27:a2:af:6b:39:95:ed:b3:a3:43:3d:17:4c:5c:53:2d:42:97:47:6a:9b:bb:d2:3a:4e:7d:92:74:a3:51:a8:dd:d4:c7:c1:9a:e1:31:68:3c:71:ea:42:1b:77:09:d0:1d:29:ca:16:a7:87:28:47:f4:c9:c9:43:c1:1d:d6:9d:4a:27:40:c8:86:e2:39:c0:3d:a7:ad:d6:0a:ae:d2:f9:bf:21:aa:b8:68:23:db:83:fd:d9:72:f8:39:d4:be:1d:3f:f6:2c:39:e8
3 创建二级CA证书
cd ../../02_SubCA
mkdir key csr cert newcerts
touch index.txt index.txt.attr
echo 01 > serial
3.1 创建二级CA秘钥对
cd key
openssl genrsa -out pri_key.pem 2048
3.2 创建二级CA证书签名请求
创建二级CA配置文件
cd ../
vim subca.conf
subca.conf 文件内容如下:
[ ca ]
default_ca = CA_default[ CA_default ]
dir = E:/07_PKI/02_SubCA
certs = $dir/cert
crl_dir = $dir/crl
database = $dir/index.txt
new_certs_dir = $dir/newcerts
certificate = $dir/cert/subca_cert.crt
serial = $dir/serial
crlnumber = $dir/crlnumber
crl = $dir/crl.pem
private_key = $dir/key/pri_key.pem
RANDFILE = $dir/key/.rand
unique_subject = nox509_extensions = usr_cert
copy_extensions = copyname_opt = ca_default
cert_opt = ca_defaultdefault_days = 3650
default_crl_days = 30
default_md = sha256
preserve = no
policy = policy_ca[ policy_ca ]
countryName = supplied
stateOrProvinceName = supplied
localityName = supplied
organizationName = supplied
organizationalUnitName = optional
commonName = supplied
emailAddress = optional[ req ]
default_bits = 2048
default_keyfile = pri_key.pem
distinguished_name = req_distinguished_name
attributes = req_attributes
x509_extensions = v3_ca
string_mask = utf8only
utf8 = yes
prompt = no[ req_distinguished_name ]
countryName = CN
stateOrProvinceName = GuangDong
localityName = ShenZhen
organizationName = TangTring
commonName = SubCA[ usr_cert ]
basicConstraints = CA:FALSE[ v3_ca ]
basicConstraints = CA:TRUE[ req_attributes ]
cd csr
openssl req -new -key ../key/pri_key.pem -out subca_csr.pem -config ../subca.conf
3.3 创建二级CA证书
cd ../cert
openssl ca -in ../csr/subca_csr.pem -out subca_cert.crt -config ../../01_RootCA/rootca.conf -days 3650
输出内容如下:
Using configuration from ../../01_RootCA/rootca.conf
Check that the request matches the signature
Signature ok
Certificate Details:Serial Number: 3 (0x3)ValidityNot Before: Sep 24 07:55:39 2024 GMTNot After : Sep 22 07:55:39 2034 GMTSubject:countryName = CNstateOrProvinceName = GuangDonglocalityName = ShenZhenorganizationName = TangTringcommonName = SubCAX509v3 extensions:X509v3 Basic Constraints:CA:TRUE
Certificate is to be certified until Sep 22 07:55:39 2034 GMT (3650 days)
Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Database updated
生成的二级CA证书如下:
$ openssl x509 -in subca_cert.crt -text -noout
Certificate:Data:Version: 3 (0x2)Serial Number: 3 (0x3)Signature Algorithm: sha256WithRSAEncryptionIssuer: C=CN, ST=GuangDong, L=ShenZhen, O=TangTring, CN=RootCAValidityNot Before: Sep 24 07:55:39 2024 GMTNot After : Sep 22 07:55:39 2034 GMTSubject: C=CN, ST=GuangDong, L=ShenZhen, O=TangTring, CN=SubCASubject Public Key Info:Public Key Algorithm: rsaEncryptionPublic-Key: (2048 bit)Modulus:00:be:8b:38:47:90:f9:dd:6d:79:3d:0d:1f:8e:ee:e1:2b:8d:7b:ce:a9:3b:0a:03:4b:c0:d2:dc:3d:a9:69:d2:49:5e:22:65:bc:96:cf:05:1d:a9:ed:a7:fb:a5:03:71:30:0f:4d:7c:cb:4d:b5:bd:d0:22:5c:42:83:ff:27:1f:31:c2:e3:e9:d4:b8:d1:c9:9a:3d:d1:91:31:f0:56:c3:85:b9:e9:06:5b:f6:fb:82:bc:33:f6:c4:e7:58:36:f3:eb:6c:ea:2d:24:b7:ca:ff:21:e2:b1:00:7f:5f:d6:39:c1:16:5a:d1:c6:58:a7:db:1f:cd:43:df:f3:c0:b9:ca:88:3d:f9:6d:a4:08:d2:f9:58:d5:50:ea:60:e1:92:89:21:df:30:42:f6:b5:ec:fe:2d:c0:03:cb:77:da:46:02:5c:ea:cf:fc:80:21:1e:10:83:d0:b8:19:bc:68:77:45:ce:53:98:c9:c8:89:af:3e:19:73:f1:cd:9c:92:05:34:0b:f3:4d:77:2d:cc:c5:db:f0:0e:cf:c8:d9:e3:1b:da:31:d6:9c:c9:3e:2c:f3:a3:90:0e:c0:a2:f5:0c:35:9e:95:ed:8e:26:c8:97:2c:ec:5d:5c:93:8b:70:18:3b:a5:30:c8:4c:77:3f:fe:47:10:f9:bc:1a:81:1f:13:07:58:a5Exponent: 65537 (0x10001)X509v3 extensions:X509v3 Basic Constraints:CA:TRUEX509v3 Subject Key Identifier:B6:CC:8A:AD:75:53:3A:5A:95:3D:53:20:7B:87:2E:E4:8A:90:63:F9X509v3 Authority Key Identifier:D9:C2:22:B4:CA:46:BA:AC:32:D6:AC:97:BF:81:17:09:A9:D5:04:F6Signature Algorithm: sha256WithRSAEncryptionSignature Value:8f:37:94:68:95:fe:91:d4:f3:ea:eb:70:10:24:02:c4:af:87:a6:09:60:d3:e7:5b:c4:b5:62:4b:58:d4:7a:d0:b4:15:ca:2e:d1:1b:32:a1:8c:7f:8b:68:43:1a:61:e4:7a:01:b1:56:30:b3:a5:1e:5e:d9:35:8f:cf:9a:34:80:8a:ab:7c:68:f3:54:fb:71:45:87:09:5f:71:0d:d2:c8:a9:36:fc:6a:5d:00:7a:d3:2a:7a:00:f5:d4:37:25:66:ed:0d:b2:df:3f:fd:7c:11:71:17:f0:a6:41:2c:d6:70:3d:76:af:ef:4d:03:ee:ba:05:8a:1b:ea:0c:5a:dc:ca:5e:07:b4:fc:b0:71:80:f2:bd:20:e7:5f:ca:42:51:f7:90:2a:cc:f5:de:be:cf:42:22:58:51:28:fa:43:af:e3:68:7b:11:20:35:a1:9e:0f:da:bc:e2:2a:4e:c4:9b:f7:ed:e1:65:96:68:4a:24:59:c2:fd:04:3d:e5:e3:4d:38:4a:0d:38:7a:0a:e3:fd:48:ad:88:93:f0:bb:a0:21:c3:fe:9e:ce:b5:e6:11:8b:2a:4b:3a:12:b0:9c:92:4c:bb:a6:1c:ba:f7:de:6f:9e:ff:6b:fa:d0:fa:8b:37:7b:76:be:cd:e5:e4:c6:7f:6e:43:49:ff:70:64:86:c0:35:e0
4 使用二级CA证书签发实体端证书
4.1 创建实体端证书配置文件
cd ../../03_Client/
mkdir key csr cert
touch client.conf
client.conf文件内容如下:
[ req ]
prompt = no
distinguished_name = server_distinguished_name
req_extensions = req_ext
x509_extensions = v3_req
attributes = req_attributes[ server_distinguished_name ]
countryName = CN
stateOrProvinceName = GuangDong
localityName = ShenZhen
organizationName = TangTring
commonName = SPNM04_CN[ v3_req ]
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment[ req_attributes ][ req_ext ]
subjectAltName = [ alternate_names ]
DNS.1 = SPNM04_CN.cn
DNS.2 = bbs.SPNM04_CN.cn
4.2 创建实体端证书秘钥
cd key
openssl genrsa -out pri_key.pem 2048
4.3 创建实体端证书签名请求
cd ../csr
openssl req -new -key ../key/pri_key.pem -out client_csr.pem -config ../client.conf
4.4 生成实体端证书
cd ../cert
openssl ca -in ../csr/client_csr.pem -out client_cert.crt -config ../../02_SubCA/subca.conf -days 1825
输出内容如下:
Using configuration from ../../02_SubCA/subca.conf
Check that the request matches the signature
Signature ok
Certificate Details:Serial Number: 1 (0x1)ValidityNot Before: Sep 24 08:22:57 2024 GMTNot After : Sep 23 08:22:57 2029 GMTSubject:countryName = CNstateOrProvinceName = GuangDonglocalityName = ShenZhenorganizationName = TangTringcommonName = SPNM04_CNX509v3 extensions:X509v3 Basic Constraints:CA:FALSEX509v3 Subject Alternative Name:DNS:SPNM04_CN.cn, DNS:bbs.SPNM04_CN.cn
Certificate is to be certified until Sep 23 08:22:57 2029 GMT (1825 days)
Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Database updated
生成的实体端证书如下:
$ openssl x509 -in client_cert.crt -text -noout
Certificate:Data:Version: 3 (0x2)Serial Number: 1 (0x1)Signature Algorithm: sha256WithRSAEncryptionIssuer: C=CN, ST=GuangDong, L=ShenZhen, O=TangTring, CN=SubCAValidityNot Before: Sep 24 08:22:57 2024 GMTNot After : Sep 23 08:22:57 2029 GMTSubject: C=CN, ST=GuangDong, L=ShenZhen, O=TangTring, CN=SPNM04_CNSubject Public Key Info:Public Key Algorithm: rsaEncryptionPublic-Key: (2048 bit)Modulus:00:e4:5c:fd:94:01:11:47:8e:25:6a:76:42:1d:65:bc:68:dd:52:ba:1b:0e:43:98:c9:f2:27:a9:bb:13:a1:e9:76:43:e3:ac:c7:7e:ab:2e:cf:fc:e6:72:0a:1f:b4:0d:6c:dc:f1:c7:09:b2:09:72:d2:8f:53:6f:65:bf:1a:4d:dc:80:ca:5c:c0:66:be:4c:8a:77:e5:47:95:b6:96:eb:75:83:13:09:95:d6:e8:3c:ac:bf:e3:96:54:b7:c6:16:ea:5c:84:15:9a:c7:9a:22:c5:33:60:97:30:63:1d:37:c0:8a:6d:b4:50:1f:86:99:86:1c:88:0e:bf:9e:db:c6:03:e2:85:90:32:53:2a:7c:72:7c:40:1f:d7:ba:46:88:56:d8:5d:7c:c1:0c:4f:95:4a:ec:53:5f:63:cf:fc:aa:43:b9:f0:23:e2:f9:4c:29:30:95:4f:3b:57:af:51:ff:27:05:f9:4f:15:63:2f:34:92:c6:b3:ad:fd:21:3b:9d:36:b0:c1:6b:12:9c:60:d9:15:85:8f:d2:f1:ee:3c:1e:d3:c9:f0:86:ee:57:36:0c:07:2a:c6:d6:85:aa:96:a2:a4:7b:5c:8f:c1:22:3c:d5:4e:23:47:fa:99:87:fc:5c:90:3d:5f:3d:f4:57:e6:40:c2:a9:7d:6b:47:09:87:10:efExponent: 65537 (0x10001)X509v3 extensions:X509v3 Basic Constraints:CA:FALSEX509v3 Subject Alternative Name:DNS:SPNM04_CN.cn, DNS:bbs.SPNM04_CN.cnX509v3 Subject Key Identifier:C1:B6:B5:FC:8A:8D:8A:21:E9:60:DE:5B:8C:C1:AB:CA:59:44:57:D4X509v3 Authority Key Identifier:B6:CC:8A:AD:75:53:3A:5A:95:3D:53:20:7B:87:2E:E4:8A:90:63:F9Signature Algorithm: sha256WithRSAEncryptionSignature Value:24:2c:17:dc:80:0b:a4:61:20:18:f6:70:0b:72:26:a5:44:41:af:8c:76:be:d3:a9:25:e1:26:95:a2:5c:2c:5d:bd:7b:26:00:91:29:69:5b:20:4c:09:4a:4d:7a:b6:41:8e:d3:b7:df:7e:05:26:af:7f:4a:d4:97:88:10:d9:61:1b:03:1a:b4:48:db:0c:c8:fc:ec:58:49:dc:50:c5:8a:1c:22:7e:4a:40:a2:b3:43:b8:f9:f6:32:98:6e:31:46:2e:bd:2a:7e:ca:ba:07:2d:c3:9b:5f:14:33:2e:99:64:c0:dc:74:d3:a3:10:4c:7d:9f:26:59:5e:d5:a4:c7:1a:c2:08:9a:fd:eb:4d:7e:9a:23:78:94:7c:f0:1b:a5:2d:81:35:71:84:b1:66:dd:4e:b7:78:f6:79:ed:b6:37:e2:e8:9d:89:25:3e:94:76:78:00:20:d7:3f:9d:e1:71:ea:e1:5a:2d:da:c5:20:70:65:e5:9d:48:06:91:3a:5f:d3:92:0a:68:f2:84:de:a3:3f:11:10:f3:61:be:a8:eb:85:88:a1:95:f8:a5:c7:bf:d9:85:a7:8e:5e:38:3f:3c:dc:e3:41:0d:9d:94:c8:d5:3f:c3:33:59:21:da:47:03:10:49:78:12:5f:ca:55:9b:e2:54:b9:bd:75:92:0d:d7:79
5 其他常用openssl命令
5.1 聚合证书
聚合的时候要注意顺序
cd ../../
cat 03_Client/cert/client_cert.crt 02_SubCA/cert/subca_cert.crt 01_RootCA/cert/rootca_cert.crt | tee 03_Client/all_cert.crt
5.2 pem和der格式转换
转换 RSA 秘钥格式:
openssl rsa -inform pem -in pri_key.pem -outform der -out pri_key.der
crt证书转换为pem证书:
openssl x509 -in client_cert.crt -outform pem -out client_cert.pem
crt、pem证书转换为der证书格式:
openssl x509 -inform pem -in client_cert.crt -outform der -out client_cert.der
openssl x509 -inform pem -in client_cert.pem -outform der -out client_cert.der
pem证书转换为der证书:
openssl x509 -inform der -in client_cert.der -outform pem -out client_cert.pem
相关文章:

用OpenSSL搭建PKI证书体系
1 创建PKI结构目录 mkdir 07_PKI cd 07_PKI mkdir 01_RootCA 02_SubCA 03_Client2 创建根CA cd 01_RootCA mkdir key csr cert newcerts touch index.txt index.txt.attr echo 01 > serial2.1 创建根CA密钥对 2.1.1 生成 长度为2048 bit 的RSA私钥。 cd key openssl gen…...
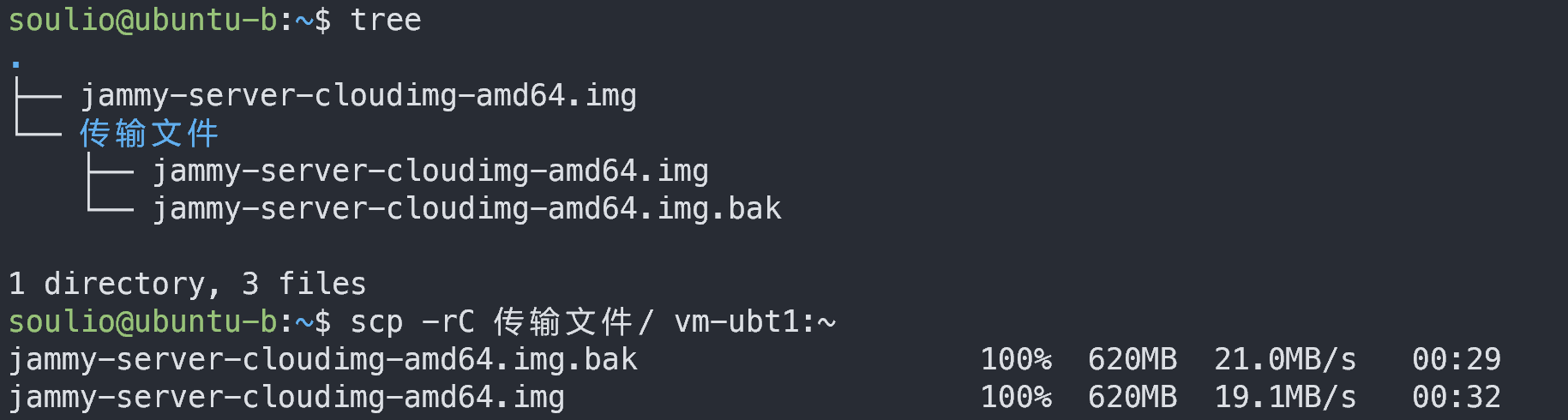
scp 命令:在两台主机间远程传输文件
一、命令简介 scp 命令使用 SSH 加密的方式在本地主机和远程主机之间复制文件。 二、命令参数 格式 scp [选项] 发送方主机和目录 接收方主机和目录注意:左边是发送方,右边是接收方。固定格式。 示例 #示例1 scp ~/test.txt soulio172.1…...

家用迷你洗衣机哪款质量高?五大热销高分单品强势来袭
迷你内衣洗衣机一般是为婴儿宝宝,或者一些有特殊需要的用户而设计使用的,宝宝衣物换洗频繁,而且对卫生方面的除菌要求高,而为避免交叉感染,所以一般不适合和大人的衣物放在一起洗,因此对于有宝宝的家庭来说…...

rpm 命令:RedHat底层包管理器
一、命令简介 rpm 是 Red Hat Package Manager 的缩写,是 Red Hat、CentOS、Fedora 等基于 Red Hat 的 Linux 发行版中用于管理和安装软件包的工具。它能够安装、卸载、升级、查询和验证软件包。 相关命令: rpm 是基础,提供了底层的软…...

Xilinx 使用DDS实现本振混频上下变频
文章目录 一、什么是混频?二、为什么要进行混频?三、Matlab实现混频操作四、FPGA实现混频上下变频操作4.1 例化IP4.2 仿真验证 一、什么是混频? 混频(Mixing)是信号处理中的一个核心概念,混频的本质是将两个…...
ClickHouse-Kafka Engine 正确的使用方式
Kafka 是大数据领域非常流行的一款分布式消息中间件,是实时计算中必不可少的一环,同时一款 OLAP 系统能否对接 Kafka 也算是考量是否具备流批一体的衡量指标之一。ClickHouse 的 Kafka 表引擎能够直接与 Kafka 系统对接,进而订阅 Kafka 中的 …...
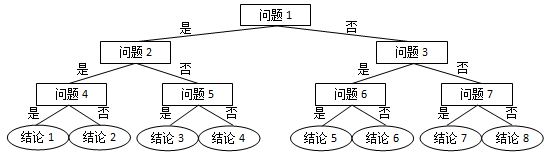
PTA L1-071 前世档案
L1-071 前世档案(20分) 网络世界中时常会遇到这类滑稽的算命小程序,实现原理很简单,随便设计几个问题,根据玩家对每个问题的回答选择一条判断树中的路径(如下图所示),结论就是路径终…...

解决mac下 Android Studio gradle 下载很慢,如何手动配置
抓住人生中的一分一秒,胜过虚度中的一月一年! 小做个动图开篇引题 前言 平时我们clone git 上项目,项目对应gradle版本本地没有,ide编译会自动下载,但是超级慢可能还下载失败,下面讲解下此问题如 如下图所示ÿ…...

第三篇 第17章 工程计量与支付
第三篇 工程计价 第17章 工程计量与支付 17.1 工程计量 17.1.1 工程计量的原则 承包人完成合同工程且应予计量的工程数量确定计量周期可以月为单位,也可以按其他时间节点、工程形象进度分段计量因承包人原因造成的超出合同工程范围施工或返工的工程量、发包人不予计量 17.1…...

[半导体检测-1]:半导体检测概述
前言: 半导体检测是半导体产业链中不可或缺的一环,它贯穿于产品生产制造流程的始终,对于提高产线良率、提升产品竞争实力具有关键作用。以下是对半导体检测的详细概述: 一、什么是半导体检测 半导体检测是指运用专业技术手段&a…...

公共字段自动填充
问题分析 总会有些公共字段,例如创建时间和创建人 实现思路 对mapper定义注解,使用切面思想来判断是不是更新和新增操作对于指定的操作来更新公共字段 自定义操作类型 package com.sky.enumeration;/*** 数据库操作类型*/ public enum OperationType {/*…...

超详细 Git 教程:二十篇博客,三万字干货
Git 是最流行的版本管理工具,可以说是任何程序员都应该掌握的工具。 当然,其他人也可以学习它用来进行版本控制 为此,我将之前学习 Git 时的笔记整理了下(预计有二十篇),作为博客发出来,希望能帮…...

“出参”和“入参”的命名由来
有些开发者会用“入参”和“出参”来描述函数、方法或接口的参数和返回值。尽管我们基本都知道“入参”就是方法的参数,“出参”就是返回值。但是对于一些起步就是JAVA的开发者来说,可能并不清楚这两个名词的由来。这篇文章就来分享一下关于“入参”和“…...

webrtc gclient sync报错问题解决
报错信息 strp_current_url current_url[:-4] if current_url.endswith( ^^^^^^^^^^^^^^^^^^^^ AttributeError: ‘NoneType’ object has no attribute ‘endswith’ gclient syncsrc/base (ERROR) ---------------------------------------- [0:00:00] Started. ----------…...

FLUX模型,或许这几点你还未曾都了解,最详细的Flux模型介绍(附模型安装包)
当我们还在沉浸在惊叹和体验快手的Kolors模型之时,SD原开发团队组成的“黑森林”出的FLUX模型就袭来了。我们不得不感叹FLUX模型给我们带来的冲击,模型所绘制的画面质感、精细度的确让我们眼前一亮,之前发布的SD3开源模型给我们带来的些许失落…...

RAG(Retrieval-Augmented Generation)检索增强生成技术基础了解学习与实践
RAG(Retrieval-Augmented Generation)是一种结合了信息检索(Retrieval)和生成模型(Generation)的技术,旨在提高生成模型的性能和准确性。RAG 技术通过在生成过程中引入外部知识库,使…...

基于SpringBoot实现高性能缓存组件
1. 简介 为了体现我们的实力,首先我们要有造轮子的能力。这意味着我们不仅要熟练掌握现有的技术栈和框架,还要具备深厚的技术功底。通过自主设计和实现关键组件,如高性能缓存系统,我们能够深入理解技术背后的原理,掌握…...
 详细理解并附实现代码。)
【深度学习基础模型】递归神经网络 (Recurrent Neural Networks, RNN) 详细理解并附实现代码。
【深度学习基础模型】递归神经网络 (Recurrent Neural Networks, RNN) 【深度学习基础模型】递归神经网络 (Recurrent Neural Networks, RNN) 文章目录 【深度学习基础模型】递归神经网络 (Recurrent Neural Networks, RNN)1.算法原理介绍:递归神经网络 (Recurrent…...
 hashlib、shutil和tarfile、configparser)
python全栈学习记录(十九) hashlib、shutil和tarfile、configparser
hashlib、shutil和tarfile、configparser 文章目录 hashlib、shutil和tarfile、configparser一、hashlib二、shutil和tarfile1.shutil2.tarfile 三、configparser 一、hashlib hash是一种算法,该算法接受传入的内容,经过运算得到一串hash值。如果把hash…...
:变分推断、生成模型、SAC)
RL进阶(一):变分推断、生成模型、SAC
参考资料: 视频课程《CS285: Deep Reinforcement Learning, Decision Making, and Control》第18讲、第19讲,Sergey Levine,UCerkeley课件PDF下载:https://rail.eecs.berkeley.edu/deeprlcourse/主要内容:变分推断、生成模型、以及Soft Actor-Critic。变分推断在model-bas…...
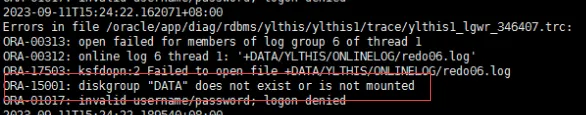
19c补丁后oracle属主变化,导致不能识别磁盘组
补丁后服务器重启,数据库再次无法启动 ORA01017: invalid username/password; logon denied Oracle 19c 在打上 19.23 或以上补丁版本后,存在与用户组权限相关的问题。具体表现为,Oracle 实例的运行用户(oracle)和集…...
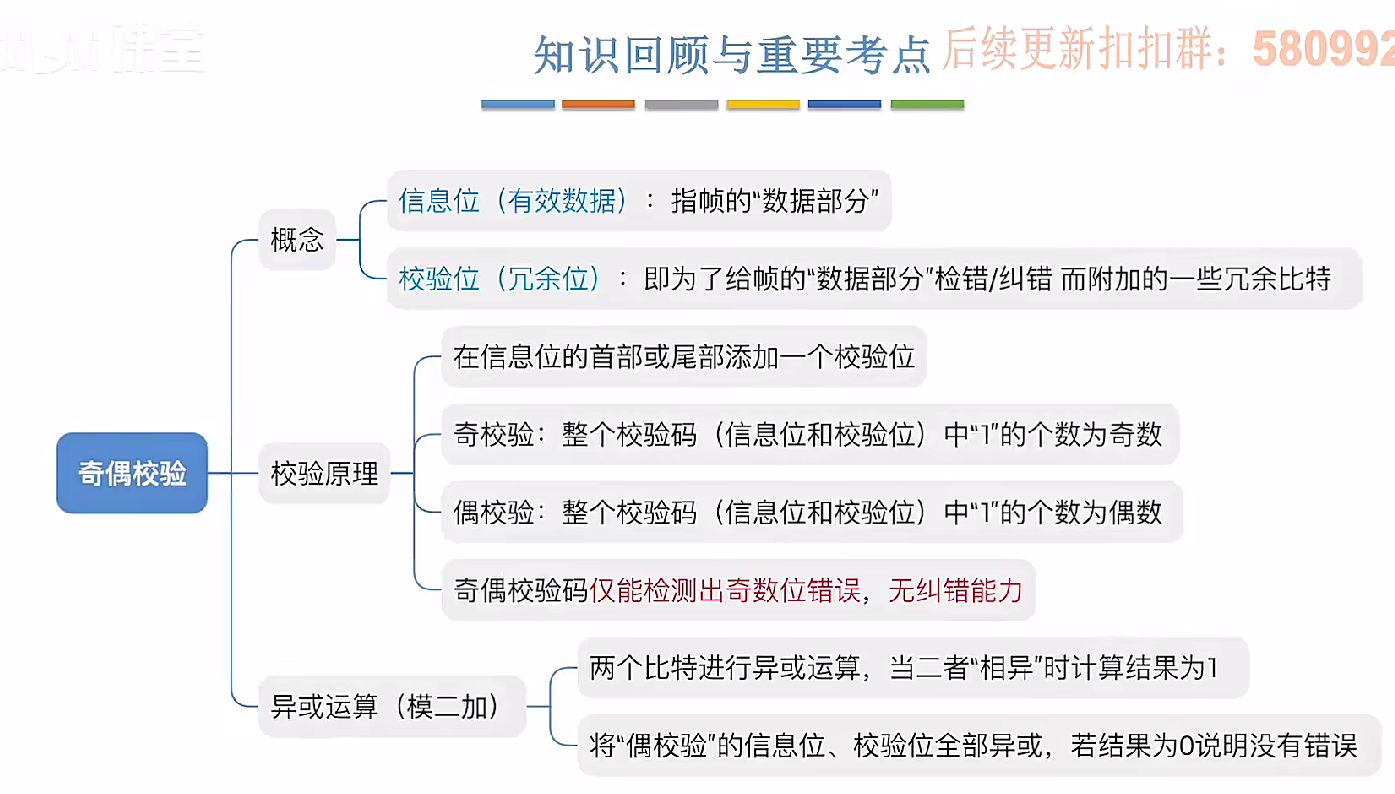
3.3.1_1 检错编码(奇偶校验码)
从这节课开始,我们会探讨数据链路层的差错控制功能,差错控制功能的主要目标是要发现并且解决一个帧内部的位错误,我们需要使用特殊的编码技术去发现帧内部的位错误,当我们发现位错误之后,通常来说有两种解决方案。第一…...
` 方法)
深入浅出:JavaScript 中的 `window.crypto.getRandomValues()` 方法
深入浅出:JavaScript 中的 window.crypto.getRandomValues() 方法 在现代 Web 开发中,随机数的生成看似简单,却隐藏着许多玄机。无论是生成密码、加密密钥,还是创建安全令牌,随机数的质量直接关系到系统的安全性。Jav…...

iPhone密码忘记了办?iPhoneUnlocker,iPhone解锁工具Aiseesoft iPhone Unlocker 高级注册版分享
平时用 iPhone 的时候,难免会碰到解锁的麻烦事。比如密码忘了、人脸识别 / 指纹识别突然不灵,或者买了二手 iPhone 却被原来的 iCloud 账号锁住,这时候就需要靠谱的解锁工具来帮忙了。Aiseesoft iPhone Unlocker 就是专门解决这些问题的软件&…...
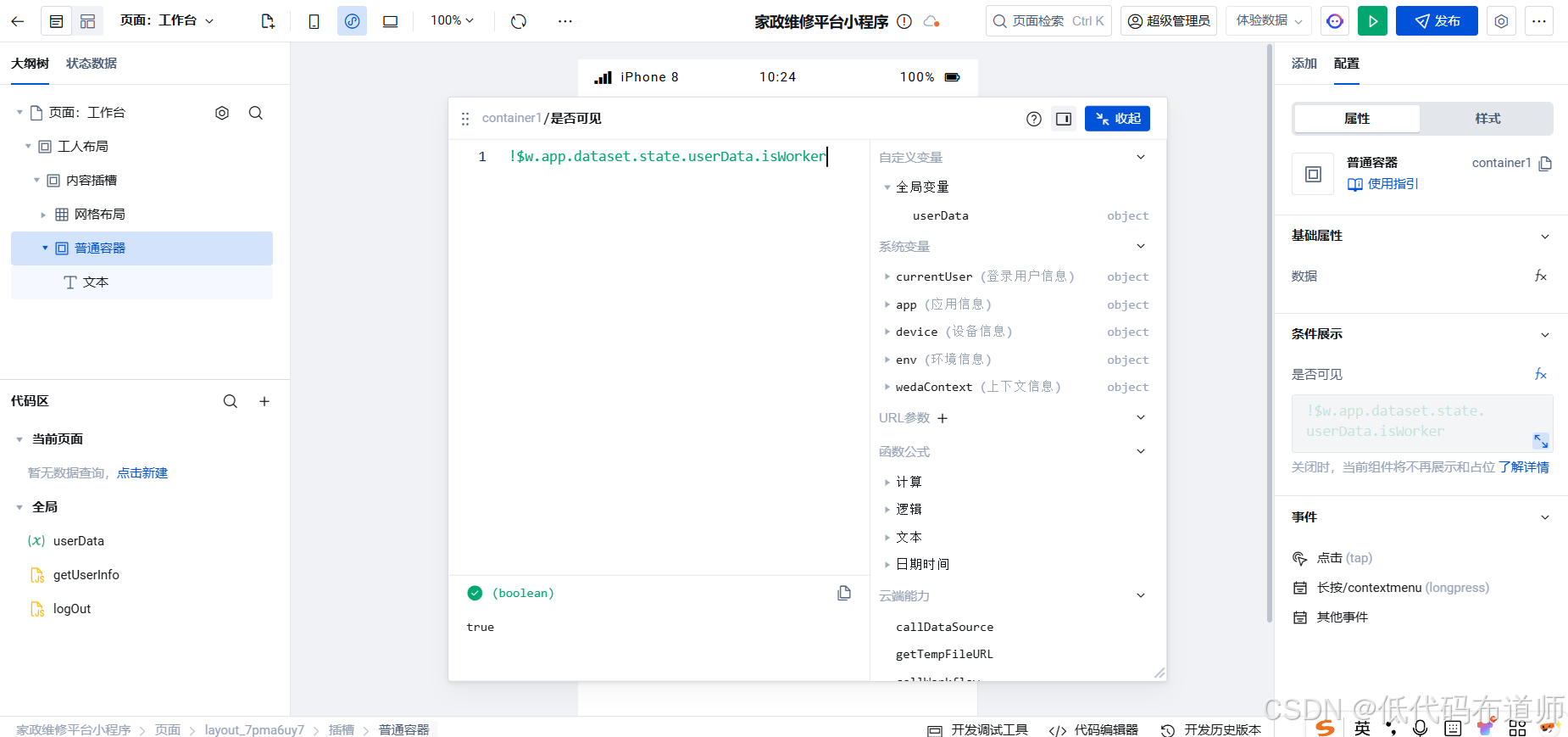
家政维修平台实战20:权限设计
目录 1 获取工人信息2 搭建工人入口3 权限判断总结 目前我们已经搭建好了基础的用户体系,主要是分成几个表,用户表我们是记录用户的基础信息,包括手机、昵称、头像。而工人和员工各有各的表。那么就有一个问题,不同的角色…...

镜像里切换为普通用户
如果你登录远程虚拟机默认就是 root 用户,但你不希望用 root 权限运行 ns-3(这是对的,ns3 工具会拒绝 root),你可以按以下方法创建一个 非 root 用户账号 并切换到它运行 ns-3。 一次性解决方案:创建非 roo…...
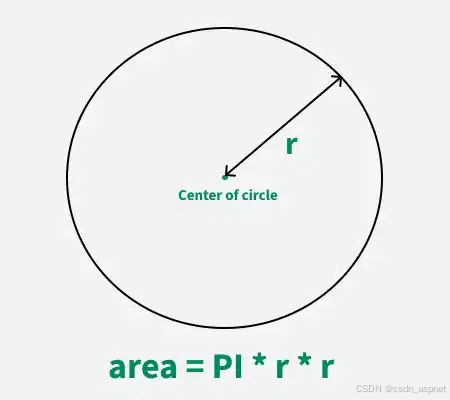
C++ 求圆面积的程序(Program to find area of a circle)
给定半径r,求圆的面积。圆的面积应精确到小数点后5位。 例子: 输入:r 5 输出:78.53982 解释:由于面积 PI * r * r 3.14159265358979323846 * 5 * 5 78.53982,因为我们只保留小数点后 5 位数字。 输…...

在web-view 加载的本地及远程HTML中调用uniapp的API及网页和vue页面是如何通讯的?
uni-app 中 Web-view 与 Vue 页面的通讯机制详解 一、Web-view 简介 Web-view 是 uni-app 提供的一个重要组件,用于在原生应用中加载 HTML 页面: 支持加载本地 HTML 文件支持加载远程 HTML 页面实现 Web 与原生的双向通讯可用于嵌入第三方网页或 H5 应…...
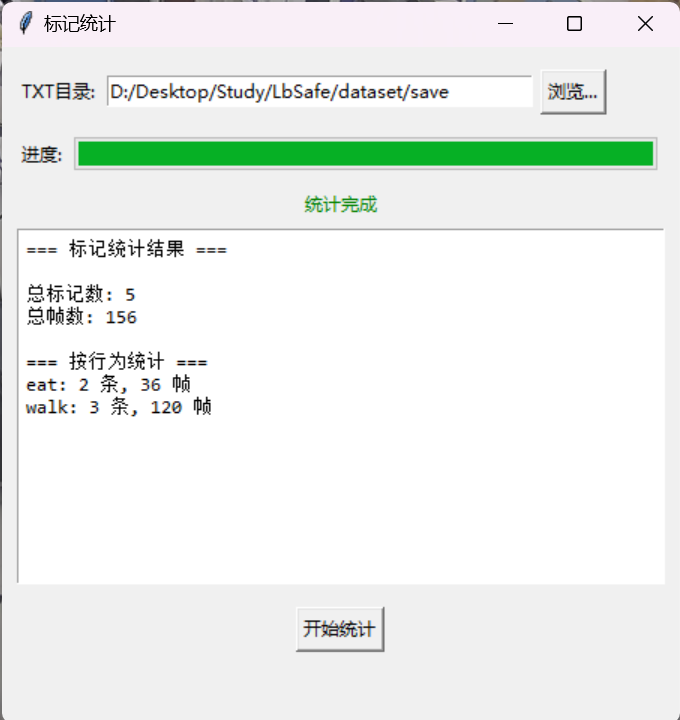
视频行为标注工具BehaviLabel(源码+使用介绍+Windows.Exe版本)
前言: 最近在做行为检测相关的模型,用的是时空图卷积网络(STGCN),但原有kinetic-400数据集数据质量较低,需要进行细粒度的标注,同时粗略搜了下已有开源工具基本都集中于图像分割这块,…...
短视频矩阵系统文案创作功能开发实践,定制化开发
在短视频行业迅猛发展的当下,企业和个人创作者为了扩大影响力、提升传播效果,纷纷采用短视频矩阵运营策略,同时管理多个平台、多个账号的内容发布。然而,频繁的文案创作需求让运营者疲于应对,如何高效产出高质量文案成…...
