SSD202D-UBOOT-FDT-获取DTB
因为一些需求,我们决定给uboot添加一个功能,在boot阶段识别获取出dtb,然后获取dts参数
DTS引脚是这样设置的
/*
* infinity2m-ssc011a-s01a-padmux-display.dtsi- Sigmastar
*
* Copyright (c) [2019~2020] SigmaStar Technology.
*
*
* This software is licensed under the terms of the GNU General Public
* License version 2, as published by the Free Software Foundation, and
* may be copied, distributed, and modified under those terms.
*
* This program is distributed in the hope that it will be useful,
* but WITHOUT ANY WARRANTY; without even the implied warranty of
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
* GNU General Public License version 2 for more details.
*
*/#include <../../../../drivers/sstar/include/infinity2m/padmux.h>
#include <../../../../drivers/sstar/include/mdrv_puse.h>/ {soc {padmux {compatible = "sstar-padmux";schematic =//<PAD_GPIO0 >,<PAD_GPIO1 PINMUX_FOR_GPIO_MODE MDRV_PUSE_I2C1_DEV_RESET >,<PAD_GPIO2 PINMUX_FOR_I2C1_MODE_1 MDRV_PUSE_I2C1_SCL >,<PAD_GPIO3 PINMUX_FOR_I2C1_MODE_1 MDRV_PUSE_I2C1_SDA >,<PAD_GPIO4 PINMUX_FOR_PWM0_MODE_3 MDRV_PUSE_PWM0 >,<PAD_GPIO5 PINMUX_FOR_PWM1_MODE_4 MDRV_PUSE_PWM1 >,<PAD_GPIO6 PINMUX_FOR_GPIO_MODE MDRV_PUSE_EJ_TDO >,<PAD_GPIO7 PINMUX_FOR_GPIO_MODE MDRV_PUSE_EJ_TDI >,<PAD_GPIO8 PINMUX_FOR_UART2_MODE_2 MDRV_PUSE_UART2_RX>,<PAD_GPIO9 PINMUX_FOR_UART2_MODE_2 MDRV_PUSE_UART2_TX>,<PAD_GPIO11 PINMUX_FOR_GPIO_MODE MDRV_PUSE_I2CSW_SCL>,<PAD_GPIO13 PINMUX_FOR_GPIO_MODE MDRV_PUSE_I2C1_DEV_IRQ >,<PAD_FUART_CTS PINMUX_FOR_GPIO_MODE MDRV_PUSE_CPUFREQ_VID0>,<PAD_FUART_RTS PINMUX_FOR_GPIO_MODE MDRV_PUSE_CPUFREQ_VID1>,<PAD_FUART_RX PINMUX_FOR_FUART_MODE_2 MDRV_PUSE_FUART_RX >,<PAD_FUART_TX PINMUX_FOR_FUART_MODE_2 MDRV_PUSE_FUART_TX >,<PAD_UART1_RX PINMUX_FOR_UART1_MODE_1 MDRV_PUSE_UART1_RX >,<PAD_UART1_TX PINMUX_FOR_UART1_MODE_1 MDRV_PUSE_UART1_TX >,<PAD_GPIO0 PINMUX_FOR_GPIO_MODE MDRV_PUSE_SDIO0_PWR >,<PAD_PM_LED0 PINMUX_FOR_PM_LED_MODE_1 MDRV_PUSE_EMAC0_LED>,<PAD_PM_LED1 PINMUX_FOR_PM_LED_MODE_1 MDRV_PUSE_EMAC0_LED>,<PAD_SAR_GPIO0 PINMUX_FOR_SAR_MODE MDRV_PUSE_SAR_GPIO0 >, <PAD_HSYNC_OUT PINMUX_FOR_IDAC_MODE MDRV_PUSE_IDAC_HSYNC>,<PAD_VSYNC_OUT PINMUX_FOR_IDAC_MODE MDRV_PUSE_IDAC_VSYNC>;status = "ok"; // ok or disable//status = "disable";};};};
/ {soc {padmux {compatible = "sstar-padmux";schematic =<1 0x00 0x00060102 >,<2 0x10 0x00060100 >,<3 0x10 0x00060101 >,<4 0x34 0x00080000 >,<5 0x3a 0x00080100 >,<6 0x00 0x00050002 >,<7 0x00 0x00050003 >,<8 0x2d 0x00070020>,<9 0x2d 0x00070021>,<11 0x00 0x00061000>,<13 0x00 0x00060103 >,<17 0x00 0x00030000>,<18 0x00 0x00030001>,<15 0x1e 0x00070030 >,<16 0x1e 0x00070031 >,<49 0x28 0x00070010 >,<50 0x28 0x00070011 >,<0 0x00 0x00020000 >,<69 0x77 0x00010000>,<70 0x77 0x00010000>,<71 0x7c 0x000D0000 >,<79 0x7e 0x000E0000 >,<80 0x7e 0x000E0000 >,<81 0x7e 0x000E0100 >,<82 0x7e 0x000E0100 >,<85 0x65 0x000B0100>,<86 0x65 0x000B0101>;status = "ok";};};};上手就开始调,调用node = fdt_path_offset(bootm_fdt, "/soc/padmux");
然后发现事情并不简单,老是死在FDT_CHECK_HEADER(fdt);这个函数
#define FDT_CHECK_HEADER(fdt) \{ \int __err; \if ((__err = fdt_check_header(fdt)) != 0) \return __err; \}///
int fdt_check_header(const void *fdt)
{if (fdt_magic(fdt) == FDT_MAGIC) {/* Complete tree */if (fdt_version(fdt) < FDT_FIRST_SUPPORTED_VERSION)return -FDT_ERR_BADVERSION;if (fdt_last_comp_version(fdt) > FDT_LAST_SUPPORTED_VERSION)return -FDT_ERR_BADVERSION;} else if (fdt_magic(fdt) == FDT_SW_MAGIC) {/* Unfinished sequential-write blob */if (fdt_size_dt_struct(fdt) == 0)return -FDT_ERR_BADSTATE;} else {return -FDT_ERR_BADMAGIC;}return 0;
}
//
#define fdt_get_header(fdt, field) \(fdt32_to_cpu(((const struct fdt_header *)(fdt))->field))
#define fdt_magic(fdt) (fdt_get_header(fdt, magic))
#define fdt_totalsize(fdt) (fdt_get_header(fdt, totalsize))
#define fdt_off_dt_struct(fdt) (fdt_get_header(fdt, off_dt_struct))
#define fdt_off_dt_strings(fdt) (fdt_get_header(fdt, off_dt_strings))
#define fdt_off_mem_rsvmap(fdt) (fdt_get_header(fdt, off_mem_rsvmap))
#define fdt_version(fdt) (fdt_get_header(fdt, version))
#define fdt_last_comp_version(fdt) (fdt_get_header(fdt, last_comp_version))
#define fdt_boot_cpuid_phys(fdt) (fdt_get_header(fdt, boot_cpuid_phys))
#define fdt_size_dt_strings(fdt) (fdt_get_header(fdt, size_dt_strings))
#define fdt_size_dt_struct(fdt) (fdt_get_header(fdt, size_dt_struct))这里就是检查dtb的头部和头部架构体的资料
#define OF_DT_HEADER 0xd00dfeed
U-Boot> fdt header magic: 0xd00dfeed
///读取到的头部///magic: 0xd00dfeed
totalsize: 0x91aa (37290)
off_dt_struct: 0x38
off_dt_strings: 0x8cb0
off_mem_rsvmap: 0x28
version: 17
last_comp_version: 16
boot_cpuid_phys: 0x0
size_dt_strings: 0x4fa
size_dt_struct: 0x8c78
number mem_rsv: 0x0//头部结构体/struct fdt_header {uint32_t magic; /* magic word FDT_MAGIC */uint32_t totalsize; /* total size of DT block */uint32_t off_dt_struct; /* offset to structure */uint32_t off_dt_strings; /* offset to strings */uint32_t off_mem_rsvmap; /* offset to memory reserve map */uint32_t version; /* format version */uint32_t last_comp_version; /* last compatible version *//* version 2 fields below */uint32_t boot_cpuid_phys; /* Which physical CPU id we'rebooting on *//* version 3 fields below */uint32_t size_dt_strings; /* size of the strings block *//* version 17 fields below */uint32_t size_dt_struct; /* size of the structure block */
};所以头部不正确,就一直报错,然后就开始查询原因,原来是没有读到dtb,而且要使用boot的FDT功能
打开fdt
--- a/boot/common/Kconfig
+++ b/boot/common/Kconfig
@@ -365,4 +365,23 @@ config XZconfig MZbool "MZ"config SILENT_CONSOLE
- bool "SILENT_CONSOLE"
\ No newline at end of file
+ bool "SILENT_CONSOLE"
+
+config OF_LIBFDT
+ bool "ftd"
+ default y
+ help
+ Boot an application image from the ftd.
+
+config FIT
+ bool "FIT"
+ default y
+ help
+ Boot an application image from the ftd.
+
+config OF_CONTROL_1
+ bool "OF_CONTROL"
+ default y
+ help
+ Boot an application image from the OF_CONTROL.
+--- a/boot/lib/Makefile
+++ b/boot/lib/Makefile
@@ -23,8 +23,8 @@ obj-y += crc7.oobj-y += crc8.oobj-y += crc16.oobj-$(CONFIG_FIT) += fdtdec_common.o
-obj-$(CONFIG_OF_CONTROL) += fdtdec_common.o
-obj-$(CONFIG_OF_CONTROL) += fdtdec.o
+obj-$(CONFIG_OF_CONTROL_1) += fdtdec_common.o
+obj-$(CONFIG_OF_CONTROL_1) += fdtdec.oobj-$(CONFIG_TEST_FDTDEC) += fdtdec_test.oobj-$(CONFIG_GZIP) += gunzip.oobj-$(CONFIG_GZIP_COMPRESSED) += gzip.o打开之后编译FDT模块了,然后开机进入boot阶段使用help可以看到fdt功能
SSD202D # help
? - alias for 'help'fatinfo - print information about filesystem
fatload - load binary file from a dos filesystem
fatls - list files in a directory (default /)
fatread - FAT fatread with FSTART
fatsize - determine a file's size
fdt - flattened device tree utility commands
get_adc - usage:get_adc channel_num , channel_num:0~3
/
SSD202D # fdt header
magic: 0xd00dfeed
totalsize: 0x91aa (37290)
off_dt_struct: 0x38
off_dt_strings: 0x8cb0
off_mem_rsvmap: 0x28
version: 17
last_comp_version: 16
boot_cpuid_phys: 0x0
size_dt_strings: 0x4fa
size_dt_struct: 0x8c78
number mem_rsv: 0x0
这个时候就是boot的fdt功能完好了
tftp 0x32000000 infinity2m.dtb
fdt addr 32000000
tftp 0x32000000 Image
fdt addr 324a7d20
tftp 0x32000000 uImage
fdt addr 324a7d60//
SSD202D # tftp 0x32000000 infinity2m-spinand-ssc011a-s01a-display.dtb
Using sstar_emac device
TFTP from server 192.168.1.143; our IP address is 192.168.1.160
Filename 'infinity2m.dtb'.
Load address: 0x32000000
Loading: ###449.2 KiB/s
done
Bytes transferred = 37290 (91aa hex)
SSD202D # md 32000000
32000000: edfe0dd0 aa910000 38000000 b08c0000 ...........8....
32000010: 28000000 11000000 10000000 00000000 ...(............
32000020: fa040000 788c0000 00000000 00000000 .......x........
32000030: 00000000 00000000 01000000 00000000 ................
32000040: 03000000 04000000 00000000 01000000 ................
32000050: 03000000 04000000 0f000000 01000000 ................
32000060: 03000000 1a000000 1b000000 49464e49 ............INFI
32000070: 5954494e 53204d32 31304353 532d4131 NITY2M SSC011A-S
32000080: 2d413130 00000053 03000000 11000000 01A-S...........
32000090: 21000000 61747373 6e692c72 696e6966 ...!sstar,infini
320000a0: 6d327974 00000000 01000000 736f6863 ty2m........chos
320000b0: 00006e65 03000000 88000000 2c000000 en.............,
320000c0: 2e696275 3d64746d 30322c39 72203834 ubi.mtd=9,2048 r
320000d0: 3d746f6f 3a696275 54535953 72204d45 oot=ubi:SYSTEM r
320000e0: 6f722077 7366746f 65707974 6962753d w rootfstype=ubi
320000f0: 69207366 3d74696e 6e696c2f 63727875 fs init=/linuxrcSSD202D # tftp 0x32000000 Image
Using sstar_emac device
TFTP from server 192.168.1.143; our IP address is 192.168.1.160
Filename 'Image'.
Load address: 0x32000000
Loading: ###########################################################################################################################################################################################################################################################################################################################################################1.6 MiB/s
done
Bytes transferred = 5091328 (4db000 hex)
SSD202D # md 324a7d20 40
324a7d20: edfe0dd0 aa910000 38000000 b08c0000 ...........8....
324a7d30: 28000000 11000000 10000000 00000000 ...(............
324a7d40: fa040000 788c0000 00000000 00000000 .......x........
324a7d50: 00000000 00000000 01000000 00000000 ................
324a7d60: 03000000 04000000 00000000 01000000 ................
324a7d70: 03000000 04000000 0f000000 01000000 ................
324a7d80: 03000000 1a000000 1b000000 49464e49 ............INFI
324a7d90: 5954494e 53204d32 31304353 532d4131 NITY2M SSC011A-S
324a7da0: 2d413130 00000053 03000000 11000000 01A-S...........
324a7db0: 21000000 61747373 6e692c72 696e6966 ...!sstar,infini
324a7dc0: 6d327974 00000000 01000000 736f6863 ty2m........chos
324a7dd0: 00006e65 03000000 88000000 2c000000 en.............,
324a7de0: 2e696275 3d64746d 30322c39 72203834 ubi.mtd=9,2048 r
324a7df0: 3d746f6f 3a696275 54535953 72204d45 oot=ubi:SYSTEM r
324a7e00: 6f722077 7366746f 65707974 6962753d w rootfstype=ubi
324a7e10: 69207366 3d74696e 6e696c2f 63727875 fs init=/linuxrc
SSD202D # //
SSD202D # tftp 0x32000000 uImage
Using sstar_emac device
TFTP from server 192.168.1.143; our IP address is 192.168.1.160
Filename 'uImage'.
Load address: 0x32000000
Loading: ###########################################################################################################################################################################################################################################################################################################################################################1.6 MiB/s
done
Bytes transferred = 5091392 (4db040 hex)
SSD202D # md 324a7d60 40
324a7d60: edfe0dd0 aa910000 38000000 b08c0000 ...........8....
324a7d70: 28000000 11000000 10000000 00000000 ...(............
324a7d80: fa040000 788c0000 00000000 00000000 .......x........
324a7d90: 00000000 00000000 01000000 00000000 ................
324a7da0: 03000000 04000000 00000000 01000000 ................
324a7db0: 03000000 04000000 0f000000 01000000 ................
324a7dc0: 03000000 1a000000 1b000000 49464e49 ............INFI
324a7dd0: 5954494e 53204d32 31304353 532d4131 NITY2M SSC011A-S
324a7de0: 2d413130 00000053 03000000 11000000 01A-S...........
324a7df0: 21000000 61747373 6e692c72 696e6966 ...!sstar,infini
324a7e00: 6d327974 00000000 01000000 736f6863 ty2m........chos
324a7e10: 00006e65 03000000 88000000 2c000000 en.............,
324a7e20: 2e696275 3d64746d 30322c39 72203834 ubi.mtd=9,2048 r
324a7e30: 3d746f6f 3a696275 54535953 72204d45 oot=ubi:SYSTEM r
324a7e40: 6f722077 7366746f 65707974 6962753d w rootfstype=ubi
324a7e50: 69207366 3d74696e 6e696c2f 63727875 fs init=/linuxrc
SSD202D # md 32000000 40
32000000: 56190527 492d0fec bb35be64 00b04d00 '..V..-Id.5..M..
32000010: 00800020 00800020 37d8df88 00020205 ... ......7....
32000020: 3458564d 32492323 3467234d 64313835 MVX4##I2M#g4581d
32000030: 36653437 4c5f4c4b 39303458 425b2323 74e6KL_LX409##[B
32000040: e28f9001 e12fff19 fa5af00c 8900f3ef ....../...Z.....
32000050: 091af089 0f1ff019 091ff029 09d3f049 ........)...I...
32000060: 0920f049 f449d109 f20f7980 f3990e13 I. ...I..y......
32000070: f38e8f00 f3de8e30 f3898f00 ee108100 ....0...........
32000080: f0019f10 ea5ffa1e bf080a05 ba36f001 ......_.......6.
32000090: e893a30d eba30110 44a00404 f8cef000 ...........D....
320000a0: f868f000 f8a6f000 f812f000 d014f8df ..h.............
320000b0: 0e0bf20f f8da46a0 44d4c010 f00146e7 .....F.....D.F..
320000c0: 0000b987 c04792e1 c0008088 c0000000 ......G.........
320000d0: 4400f508 4480f5a4 f04f4620 f5000300 ...D...D FO.....
320000e0: f8404680 f8403b04 f8403b04 f8403b04 .F@..;@..;@..;@.
320000f0: ea903b04 d1f40f06 7008f8da e890a01a .;.........p....尝试直接下载dtb和Image和Uimage,对应的地址可以读取到dtb
//ssd202d\kernel\arch\arm\boot\Makefileifeq ($(CONFIG_SS_BUILTIN_DTB), y)#update builtin DTB@test "${SS_DTB_NAME}" = "" || \if [ -e ${SS_DTB_NAME} ]; then \echo " IMAGE $(obj)/Image"; \echo " BNDTB ${SS_DTB_NAME}"; \python scripts/ms_builtin_dtb_update.py $(obj)/Image ${SS_DTB_NAME}; \echo; \fi;#update Image-fpga DTB@if [ -e "arch/arm/boot/dts/$(CHIP_NAME)-fpga.dtb" ]; then \echo " IMAGE $(obj)/Image-fpga"; \cp -f $(obj)/Image $(obj)/Image-fpga; \echo " BNDTB $(CHIP_NAME)-fpga.dtb"; \python scripts/ms_builtin_dtb_update.py $(obj)/Image-fpga "arch/arm/boot/dts/$(CHIP_NAME)-fpga.dtb"; \echo; \fi;
endif///
kernel\scripts\ms_builtin_dtb_update.py#!/usr/bin/pythonimport re, fnmatch, os, sys, mmap, structif __name__ == '__main__':name='#MS_DTB#'dtb_file=open(sys.argv[2])dtb_file.seek(0,os.SEEK_END)size=dtb_file.tell()dtb_file.seek(0,os.SEEK_SET)dtb=dtb_file.read()dtb_file.close()if sys.getsizeof(dtb) > (64*1024):print ('DTB size 0x%08X too big to fit in 64K limit!!' % dtb.size())sys.exit() fmap=mmap.mmap(os.open(sys.argv[1],os.O_RDWR),0)offset=fmap.find(name) if offset >=0:print ('offset:0x%08X' % offset)print (' size:0x%08X' % size )fmap.seek(offset + 8, os.SEEK_SET)fmap.write(struct.pack('<I', size))fmap.seek(offset + 16, os.SEEK_SET)fmap.write(dtb)fmap.close()可以看到edfe0dd0 的头部,image里面有dtb的内容,uimage是在image前面加了一个头部
(这个头部可以百度去看uimage内容不细说)
然后这边使用了uimage.xz包,就是还要有一个代码的解压才可以获取dtb,太难了
解压函数在boot里面
int bootm_decomp_image(int comp, ulong load, ulong image_start, int type,void *load_buf, void *image_buf, ulong image_len,uint unc_len, ulong *load_end)
{const char *type_name = genimg_get_type_name(type);
// __attribute__((unused)) uint unc_len = CONFIG_SYS_BOOTM_LEN;printf("longmin bootm_decomp_image 444443 comp=%d; load=0x%lx;image_start=0x%lx;type=%d;image_len=0x%lx;unc_len=0x%lx;load_end=0x%lx;\n",comp,load,image_start,type,image_len,unc_len,load_end);*load_end = load;switch (comp) {case IH_COMP_XIP:case IH_COMP_NONE:if (load == image_start) {printf(" XIP %s ... ", type_name);}else if(IH_COMP_XIP==comp){printf(" Force XIP %s ... ", type_name);image_start=load;}else {printf(" Loading %s ... ", type_name);memmove_wd(load_buf, image_buf, image_len, CHUNKSZ);}*load_end = load + image_len;break;
#ifdef CONFIG_GZIPcase IH_COMP_GZIP:printf(" Uncompressing %s ... \n", type_name);if (gunzip(load_buf, unc_len, image_buf, &image_len) != 0) {puts(" GUNZIP: uncompress, out-of-mem or overwrite error - must RESET board to recover\n");return BOOTM_ERR_RESET;}*load_end = load + image_len;break;
#endif /* CONFIG_GZIP */
#ifdef CONFIG_BZIP2case IH_COMP_BZIP2:printf(" Uncompressing %s ... \n", type_name);/** If we've got less than 4 MB of malloc() space,* use slower decompression algorithm which requires* at most 2300 KB of memory.*/int i = BZ2_bzBuffToBuffDecompress(load_buf, &unc_len,image_buf, image_len,CONFIG_SYS_MALLOC_LEN < (4096 * 1024), 0);if (i != BZ_OK) {printf(" BUNZIP2: uncompress or overwrite error %d - must RESET board to recover\n",i);return BOOTM_ERR_RESET;}*load_end = load + unc_len;break;
#endif /* CONFIG_BZIP2 */
#if defined CONFIG_LZMA || defined CONFIG_XZcase IH_COMP_LZMA: {#ifdef CONFIG_XZstruct xz_buf b;struct xz_dec *s;enum xz_ret ret;printf(" Uncompressing %s ... \n", type_name);xz_crc32_init();/** Support up to 64 MiB dictionary. The actually needed memory* is allocated once the headers have been parsed.*/s = xz_dec_init(XZ_SINGLE, 16*1024);if(s==NULL){printf(" xz_dec_init ERROR!!");}b.in = image_buf/*hardcore here*/;b.in_pos = 0;b.in_size = image_len;b.out = load_buf;b.out_pos = 0;b.out_size = unc_len;ret = xz_dec_run(s, &b);// if(ret != XZ_OK || ret != XZ_STREAM_END)
// printf("\nXZ: uncompress erro %d\n", ret);printf(" XZ: uncompressed size=0x%x, ret=%d\n",b.out_pos, ret);xz_dec_end(s);break;#elseSizeT lzma_len = unc_len;int ret;printf(" Uncompressing %s ... \n", type_name);ret = lzmaBuffToBuffDecompress(load_buf, &lzma_len,image_buf, image_len);unc_len = lzma_len;if (ret != SZ_OK) {printf(" LZMA: uncompress or overwrite error %d - must RESET board to recover\n",ret);bootstage_error(BOOTSTAGE_ID_DECOMP_IMAGE);return BOOTM_ERR_RESET;}*load_end = load + unc_len;break;#endif}
#endif /* CONFIG_LZMA */
#ifdef CONFIG_LZOcase IH_COMP_LZO: {size_t size = unc_len;int ret;printf(" Uncompressing %s ... \n", type_name);ret = lzop_decompress(image_buf, image_len, load_buf, &size);if (ret != LZO_E_OK) {printf(" LZO: uncompress or overwrite error %d - must RESET board to recover\n",ret);return BOOTM_ERR_RESET;}*load_end = load + size;break;}
#endif /* CONFIG_LZO */
#ifdef CONFIG_MZcase IH_COMP_MZ:{extern size_t tinfl_decompress_mem_to_mem(void *pOut_buf, size_t out_buf_len, const void *pSrc_buf, size_t src_buf_len, int flags);int ret=-1;printf(" Uncompressing %s ... \n", type_name);
// printf(" 0x%08X, 0x%08X, 0x%08X, 0x%08X\n",load_buf, unc_len, image_buf, image_len);if ((ret=tinfl_decompress_mem_to_mem(load_buf, unc_len, image_buf, image_len, 0)) <0) {puts(" MZ: uncompress failed - must RESET board to recover\n");return BOOTM_ERR_RESET;}else{printf(" MZ: uncompressed size=0x%x\n",ret);}*load_end = load + image_len;break;}
#endif /* CONFIG_MZ */default:printf(" Unimplemented compression type %d\n", comp);return BOOTM_ERR_UNIMPLEMENTED;}puts("OK\n");return 0;
}
然后由于涉及bootm又是一大知识点
要了解bootm后,发现
要读取uiamge.xz要先运行环境变量
nand read.e 0x22000000 RECOVERY 0x300000
先把recovery分区读取到0x22000000上
SSD202D # md 22000000
30000000: 00000000 ffffffff 00000000 ffffffff ................
30000010: 08000001 f7fffffe 08000001 f7fffffe ................
30000020: 10000002 effffffd 10000002 effffffd ................
30000030: 18000003 e7fffffc 18000003 e7fffffc ................
30000040: 20000004 dffffffb 20000004 dffffffb ... ....... ....
30000050: 28000005 d7fffffa 28000005 d7fffffa ...(.......(....
30000060: 30000006 cffffff9 30000006 cffffff9 ...0.......0....
30000070: 38000007 c7fffff8 38000007 c7fffff8 ...8.......8....
30000080: 40000008 bffffff7 40000008 bffffff7 ...@.......@....
30000090: 48000009 b7fffff6 48000009 b7fffff6 ...H.......H....
300000a0: 5000000a affffff5 5000000a affffff5 ...P.......P....
300000b0: 5800000b a7fffff4 5800000b a7fffff4 ...X.......X....
300000c0: 6000000c 9ffffff3 6000000c 9ffffff3 ...`.......`....
300000d0: 6800000d 97fffff2 6800000d 97fffff2 ...h.......h....
300000e0: 7000000e 8ffffff1 7000000e 8ffffff1 ...p.......p....
300000f0: 7800000f 87fffff0 7800000f 87fffff0 ...x.......x....SSD202D # nand read.e 0x22000000 RECOVERY 0x300000NAND read: device 0 offset 0x840000, size 0x300000
Time:612945 us, speed:5132 KB/s3145728 bytes read: OKSSD202D # md 22000000
22000000: 56190527 936a491c 6a2aae64 ac472500 '..V.Ij.d.*j.%G.
22000010: 00800020 00800020 20d7ceca 03020205 ... ...... ....
22000020: 3458564d 32492323 3467234d 64313835 MVX4##I2M#g4581d
22000030: 36653437 4c5f4c4b 39303458 425b2323 74e6KL_LX409##[B
22000040: 587a37fd 0400005a 46b4d6e6 01210002 .7zXZ......F..!.
22000050: 00000016 a3e52f74 ef3b93e1 00005dff ....t/....;..]..
22000060: 68caeea4 07fa8f83 dd905c6c a3918ccb ...h....l\......
22000070: 909d8eac cc1177a8 7acf7427 c8668976 .....w..'t.zv.f.
22000080: 8c2bded9 40446de8 7c69be73 f24ffaf3 ..+..mD@s.i|..O.
22000090: 89c13f55 d07fdb26 ee616487 9fab9e46 U?..&....da.F...
220000a0: 91f6a7f4 11a1f851 fc341f01 ab57fae7 ....Q.....4...W.
220000b0: 822a3c67 9a14e408 f401cb55 21d54575 g<*.....U...uE.!
220000c0: 8c6107da 3ec7f930 fd9e6a48 8f462c70 ..a.0..>Hj..p,F.
220000d0: d67825cc 96fb0899 729f9296 9bd16e40 .%x........r@n..
220000e0: c7e1fbf6 f82442d9 7a7550b2 8204e085 .....B$..Puz....
220000f0: 69055244 d12f0ab4 e6e5dafe b51f73b2 DR.i../......s..然后再运行bootm_decomp_image就可以子在0x20008000上看到解压的image
SSD202D # md 20008000 40
20008000: e28f9001 e12fff19 fa5af00c 8900f3ef ....../...Z.....
20008010: 091af089 0f1ff019 091ff029 09d3f049 ........)...I...
20008020: 0920f049 f449d109 f20f7980 f3990e13 I. ...I..y......
20008030: f38e8f00 f3de8e30 f3898f00 ee108100 ....0...........
20008040: f0019f10 ea5ffa1e bf080a05 ba36f001 ......_.......6.
20008050: e893a30d eba30110 44a00404 f8cef000 ...........D....
20008060: f868f000 f8a6f000 f812f000 d014f8df ..h.............
20008070: 0e0bf20f f8da46a0 44d4c010 f00146e7 .....F.....D.F..
20008080: 0000b987 c04792e1 c0008088 c0000000 ......G.........
20008090: 4400f508 4480f5a4 f04f4620 f5000300 ...D...D FO.....
200080a0: f8404680 f8403b04 f8403b04 f8403b04 .F@..;@..;@..;@.
200080b0: ea903b04 d1f40f06 7008f8da e890a01a .;.........p....
200080c0: eba00068 44050003 ea4f4406 ea4f5515 h......D.DO..UO.
200080d0: ea475616 f8445305 42b53025 3501bf3c .VG..SD.%0.B<..5
200080e0: f504e7f7 4e0f5040 0307ea48 4696eb04 ....@P.NH......F
200080f0: 3b04f840 1380f503 d9f942b0 5012ea4f @..;.....B..O..P获取对应的image后使用fdt addr 204afd20 即可获取到dtb
204afd20 = 20008000 + 4A7D20
4A7D20 = image前半段的大小
函数实现
extern struct fdt_header *working_fdt;struct fdt_header * do_bootm_states_fdt(void)
{const void *os_hdr;ulong load_end;int ret = 0;images.os.load = 0x20008000;//解压后的地址images.os.image_start = 0x22000040;//去掉uimage头部的地址images.os.image_len =0x2547ac;//全部大小images.os.comp = 3;//解压方式.xz = 3images.os.type = 2;run_command("nand read.e 0x22000000 RECOVERY 0x300000", 0);ret = bootm_load_os_long(&images, &load_end, 0);run_command("fdt addr 204afd20", 0);run_command("fdt header", 0);return working_fdt;
}
int len,err;int count;u32 cell[3*27];struct fdt_header *bootm_fdt;bootm_fdt=do_bootm_states_fdt();node = fdt_path_offset(bootm_fdt, "/soc/padmux"); val=fdt_getprop(bootm_fdt,node,"compatible",&len); err = fdtdec_get_int_array(bootm_fdt, node, "schematic", cell,ARRAY_SIZE(cell));for(i=0;i<27;i++)printf("***: unknow power ctrl type %d[%d %d %d]\n",err,cell[i*3],cell[i*3+1],cell[i*3+2]); magic: 0xd00dfeed
totalsize: 0x91aa (37290)
off_dt_struct: 0x38
off_dt_strings: 0x8cb0
off_mem_rsvmap: 0x28
version: 17
last_comp_version: 16
boot_cpuid_phys: 0x0
size_dt_strings: 0x4fa
size_dt_struct: 0x8c78
number mem_rsv: 0x0***: unknow power ctrl type [34796]***: unknow power ctrl type sstar-padmux[13]***: unknow power ctrl type 0[1 0 393474]***: unknow power ctrl type 0[2 16 393472]***: unknow power ctrl type 0[3 16 393473]***: unknow power ctrl type 0[4 52 524288]***: unknow power ctrl type 0[5 58 524544]***: unknow power ctrl type 0[6 0 327682]***: unknow power ctrl type 0[7 0 327683]***: unknow power ctrl type 0[8 45 458784]***: unknow power ctrl type 0[9 45 458785]***: unknow power ctrl type 0[11 0 397312]***: unknow power ctrl type 0[13 0 393475]***: unknow power ctrl type 0[17 0 196608]***: unknow power ctrl type 0[18 0 196609]***: unknow power ctrl type 0[15 30 458800]***: unknow power ctrl type 0[16 30 458801]***: unknow power ctrl type 0[49 40 458768]***: unknow power ctrl type 0[50 40 458769]***: unknow power ctrl type 0[0 0 131072]***: unknow power ctrl type 0[69 119 65536]***: unknow power ctrl type 0[70 119 65536]***: unknow power ctrl type 0[71 124 851968]***: unknow power ctrl type 0[79 126 917504]***: unknow power ctrl type 0[80 126 917504]***: unknow power ctrl type 0[81 126 917760]***: unknow power ctrl type 0[82 126 917760]***: unknow power ctrl type 0[85 101 721152]***: unknow power ctrl type 0[86 101 721153]已经成功获取到dtb文件节点
相关文章:

SSD202D-UBOOT-FDT-获取DTB
因为一些需求,我们决定给uboot添加一个功能,在boot阶段识别获取出dtb,然后获取dts参数 DTS引脚是这样设置的 /* * infinity2m-ssc011a-s01a-padmux-display.dtsi- Sigmastar * * Copyright (c) [2019~2020] SigmaStar Technology. * * * This software is licensed under the …...

【Maven】Setting文件分享
<?xml version"1.0" encoding"UTF-8"?><!-- Licensed to the Apache Software Foundation (ASF) under one or more contributor license agreements. See the NOTICE file distributed with this work for additional information regarding …...
)
使用requestAnimationFrame 实现倒计时功能js(简单秒数倒计时)
拿一个简单的例子吧 就是获取验证码的倒计时 一般来说就是60秒 首先可能想到就是 setInterval let count 60 setInterval(() > { count --; }, 1000) 还有一种就是 setTImeout 函数的递归调用 let count 60 function coundown() { count --; if(count >…...
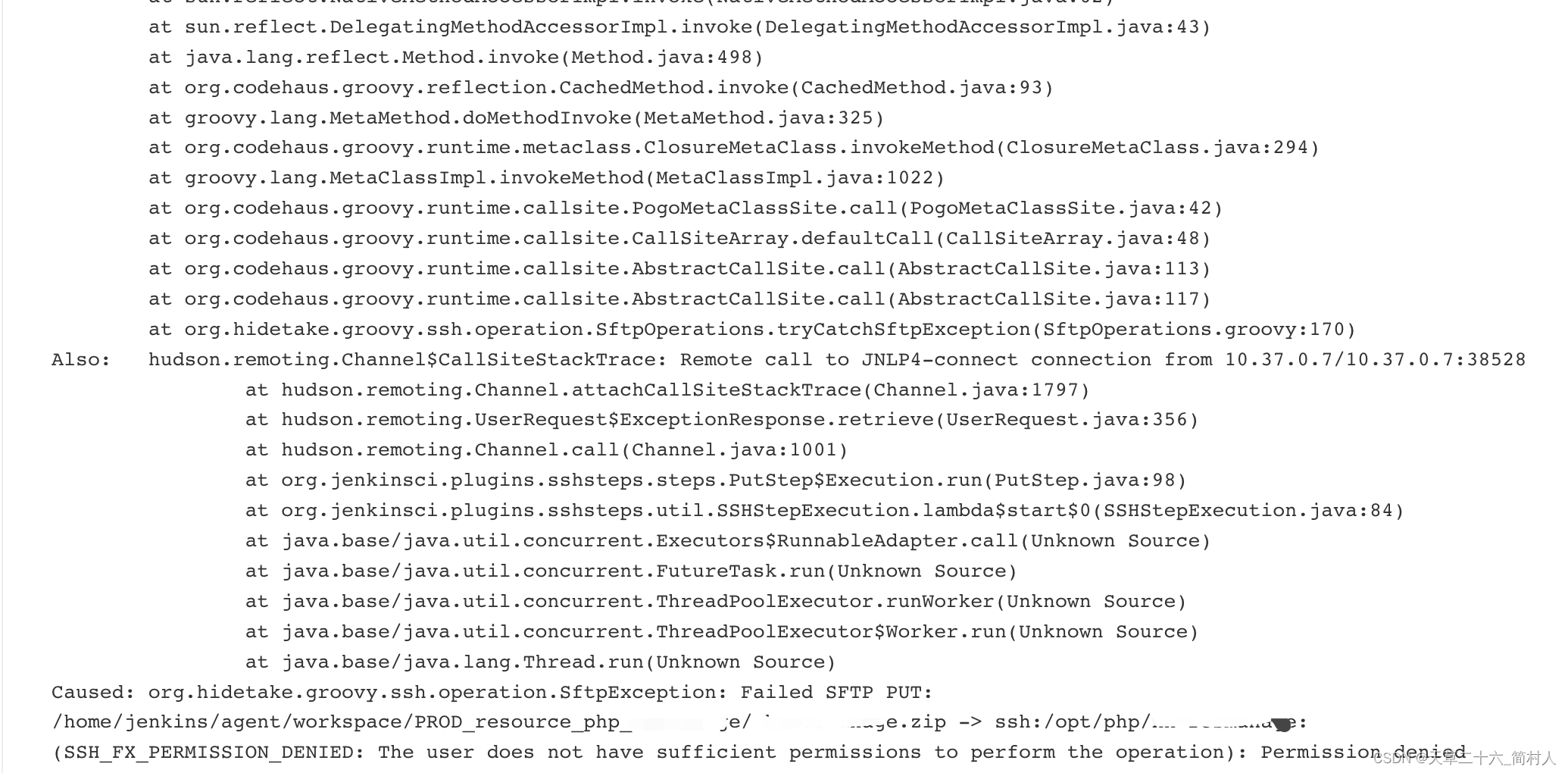
jenkins通过sshPut传输文件的时候,报错Permission denied的SftpException
一、背景 使用jenkins的ssh插件传输文件至远程机器的指定目录,php程序打包后,经过zip压缩为oms.zip zip -rq oms.zip ./ -x .git/* -x .env然后我们求md5值 md5sum oms.zip最后执行传输。 09:03:02 Executing command on ssh[116.61.10.149]: mkdir…...
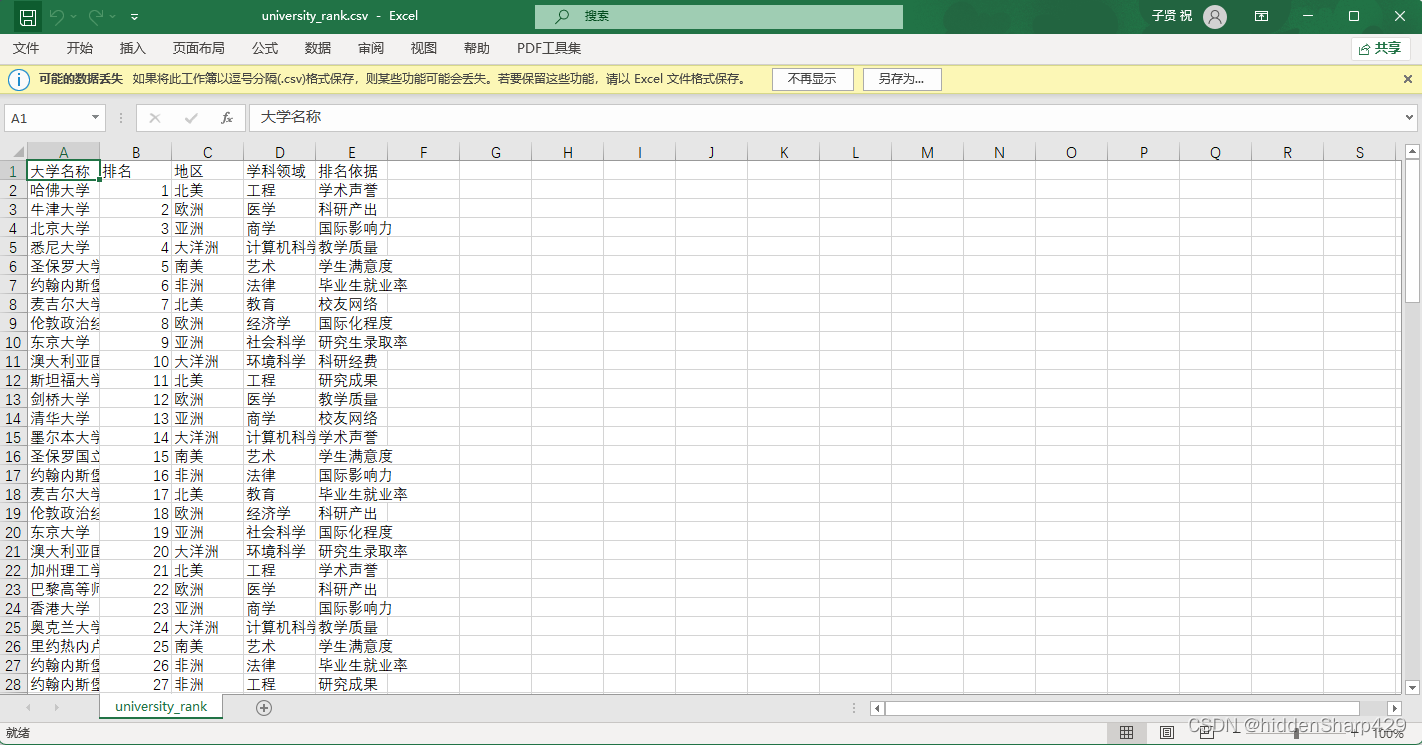
【Python】数据分析+数据挖掘——探索Pandas中的数据筛选
1. 前言 当涉及数据处理和分析时,Pandas是Python编程语言中最强大、灵活且广泛使用的工具之一。Pandas提供了丰富的功能和方法,使得数据的选择、筛选和处理变得简单而高效。在本博客中,我们将重点介绍Pandas中数据筛选的关键知识点ÿ…...

[数据集][目标检测]天牛数据集目标检测数据集VOC格式3050张
数据集格式:Pascal VOC格式(不包含分割路径的txt文件和yolo格式的txt文件,仅仅包含jpg图片和对应的xml) 图片数量(jpg文件个数):3050 标注数量(xml文件个数):3050 标注类别数:1 标注类别名称:["longicorn"] …...
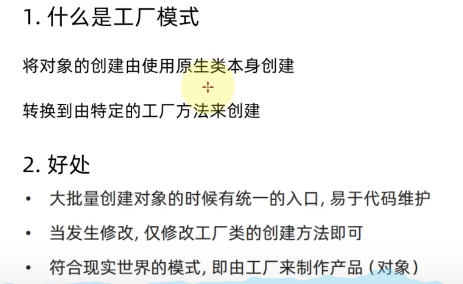
python_day16_设计模式
“”“单例模式”“” “”“工厂模式”“” class Person:passclass Worker(Person):passclass Student(Person):passclass Teacher(Person):passclass Factory:def get_person(self, p_type):if p_type w:return Worker()elif p_type s:return Student()else:return Te…...
uniapp开发小程序-实现中间凸起的 tabbar
一、效果展示: 二、代码实现: 1.首先在pages.json文件中进行tabbar的样式和列表配置,代码如下: {"pages": [ //pages数组中第一项表示应用启动页,参考:https://uniapp.dcloud.io/collocation/p…...

Vue引入与Vue拦截原理
1. vue引入 第一种方法:在线引入 <script src"https://cdn.jsdelivr.net/npm/vue/dist/vue.js"></script> 第二种方法:本地引入 2. Vue拦截原理——例题 el用于绑定id,data用于定义数据如下例题 <!DOCTYPE html&…...
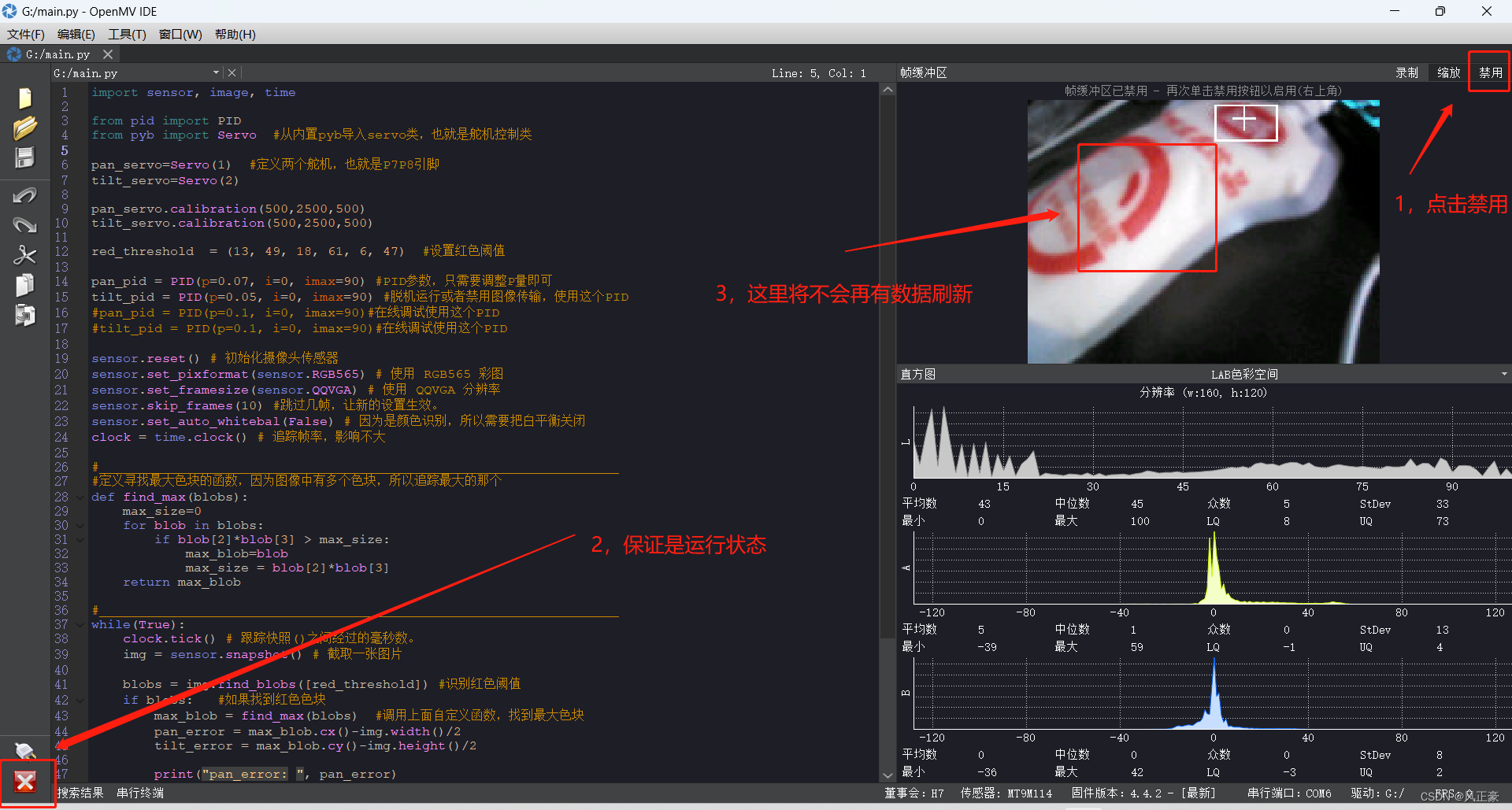
2023年电赛---运动目标控制与自动追踪系统(E题)OpenMV方案
前言 (1)废话少说,很多人可能无法访问GitHub,所以我直接贴出可能要用的代码。此博客还会进行更新,先贴教程和代码 (2)视频教程: https://singtown.com/learn/49603/ (3&a…...
6G内存运行Llama2-Chinese-7B-chat模型
6G内存运行Llama2-Chinese-7B-chat模型 Llama2-Chinese中文社区 第一步: 从huggingface下载 Llama2-Chinese-7b-Chat-GGML模型放到本地的某一目录。 第二步: 执行python程序 git clone https://github.com/Rayrtfr/llama2-webui.gitcd llama2-web…...
项目经理必备-项目总体计划模板-制式文件,可直接填写使用-公司可用
合同中完整项目名称,黑体,28号字, 居中对齐,项目名称较长时换行填写 当前文档名称,黑体,小初, 居中对齐,文档名称较长时 换行填写 版 本 号 x.x 编制人 日期 20xx年xx月xx日…...
)
正则表达式系列|(以xx开头xx结尾提取、切分、替换)
正则表达式系列|(以xx开头xx结尾提取、切分、替换) 文章目录 正则表达式系列|(以xx开头xx结尾提取、切分、替换)[TOC] 前言一、以xx开头xx结尾进行数据处理?1.以xx开头xx结尾对文本拆分2.以xx开头xx结尾提取内容3.以xx…...
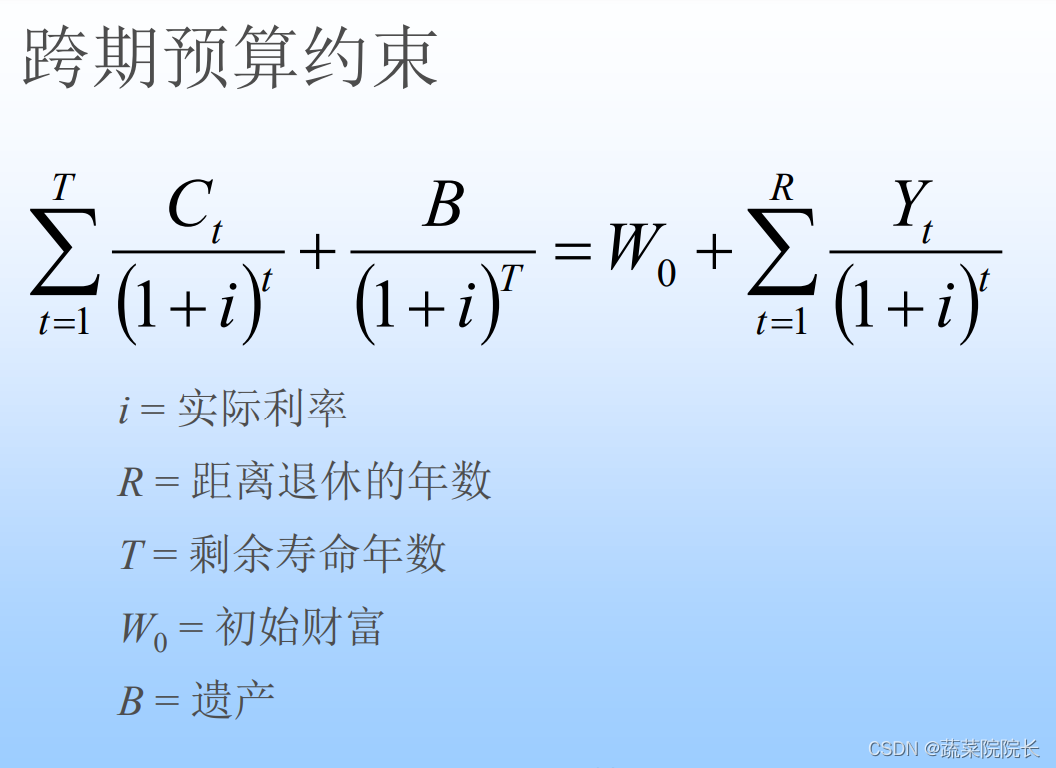
金融学复习博迪(第1-5章)
第一部分 金融和金融体系 第1章 金融学 金融:资金的流通,即储蓄,信贷、汇兑、股票和证券交易等经济活动的总称。 金融学:研究货币流通的学问。 传统的金融学研究领域大致有两个方向: >宏观层面的金融市场运行理论…...
【前端知识】React 基础巩固(三十七)——自定义connect高阶组件
React 基础巩固(三十七)——自定义connect高阶组件 一、手撸一个自定义connect高阶组件 import { PureComponent } from "react"; import store from "../store";/*** connect的参数:* 参数一: 函数* 参数二: 函数* 返…...

前端PDF导出,使用html2Canvas和jsPDF插件
import html2Canvas from "html2canvas"; import jsPDF from "jspdf"; export function downloadPDF(dom, filename) {const scale 2;window.pageYOffset 0;// 滚动到顶部,避免打印不全document.documentElement.scrollTop 0;document.body.…...

Android 设备兼容性使用详解
和你一起终身学习,这里是程序员Android 经典好文推荐,通过阅读本文,您将收获以下知识点: 一、设备兼容性分类二、硬件设备兼容三、软件 APP 兼容四、兼容不同语言五、兼容不同分辨率六、兼容不同屏幕方向布局七、兼容不同硬件 Feature八、兼容…...

vnc加固
0x00 认识VNC 先我们看看VNC运行的工作流程: VNC客户端通过浏览器或VNC Viewer连接至VNC Server; VNC Server传送一个对话窗口至客户端,要求输入连接密码(可能为空),以及存取的VNC Server显示装置&#…...
Windows下Nginx安装与配置教程
一、前言 1、Nginx是什么? Nginx是一个开源的Web服务器,同时Nginx也提供了反向代理和负载均衡的功能。 Nginx通常作为负载均衡器暴露在外网接受用户请求,同时也使用其反向代理的功能,将用户的请求转发到实际提供服务的内网服务器…...

Iterator迭代器和Generator生成器
Iterator迭代器和for/of循环原理 Iterator迭代器规范 自己创建一个Iterator类,来实现ES6中的迭代器规范: class Iterator {constructor(assemble) {// assemble:需要迭代的数据结构this.assemble = assemble// index:记录迭代的次数(或者索引)this.index = -1}// 必须具…...
国防科技大学计算机基础课程笔记02信息编码
1.机内码和国标码 国标码就是我们非常熟悉的这个GB2312,但是因为都是16进制,因此这个了16进制的数据既可以翻译成为这个机器码,也可以翻译成为这个国标码,所以这个时候很容易会出现这个歧义的情况; 因此,我们的这个国…...
日语AI面试高效通关秘籍:专业解读与青柚面试智能助攻
在如今就业市场竞争日益激烈的背景下,越来越多的求职者将目光投向了日本及中日双语岗位。但是,一场日语面试往往让许多人感到步履维艰。你是否也曾因为面试官抛出的“刁钻问题”而心生畏惧?面对生疏的日语交流环境,即便提前恶补了…...
微信小程序之bind和catch
这两个呢,都是绑定事件用的,具体使用有些小区别。 官方文档: 事件冒泡处理不同 bind:绑定的事件会向上冒泡,即触发当前组件的事件后,还会继续触发父组件的相同事件。例如,有一个子视图绑定了b…...

反向工程与模型迁移:打造未来商品详情API的可持续创新体系
在电商行业蓬勃发展的当下,商品详情API作为连接电商平台与开发者、商家及用户的关键纽带,其重要性日益凸显。传统商品详情API主要聚焦于商品基本信息(如名称、价格、库存等)的获取与展示,已难以满足市场对个性化、智能…...

2025年能源电力系统与流体力学国际会议 (EPSFD 2025)
2025年能源电力系统与流体力学国际会议(EPSFD 2025)将于本年度在美丽的杭州盛大召开。作为全球能源、电力系统以及流体力学领域的顶级盛会,EPSFD 2025旨在为来自世界各地的科学家、工程师和研究人员提供一个展示最新研究成果、分享实践经验及…...

Python:操作 Excel 折叠
💖亲爱的技术爱好者们,热烈欢迎来到 Kant2048 的博客!我是 Thomas Kant,很开心能在CSDN上与你们相遇~💖 本博客的精华专栏: 【自动化测试】 【测试经验】 【人工智能】 【Python】 Python 操作 Excel 系列 读取单元格数据按行写入设置行高和列宽自动调整行高和列宽水平…...
基于uniapp+WebSocket实现聊天对话、消息监听、消息推送、聊天室等功能,多端兼容
基于 UniApp + WebSocket实现多端兼容的实时通讯系统,涵盖WebSocket连接建立、消息收发机制、多端兼容性配置、消息实时监听等功能,适配微信小程序、H5、Android、iOS等终端 目录 技术选型分析WebSocket协议优势UniApp跨平台特性WebSocket 基础实现连接管理消息收发连接…...
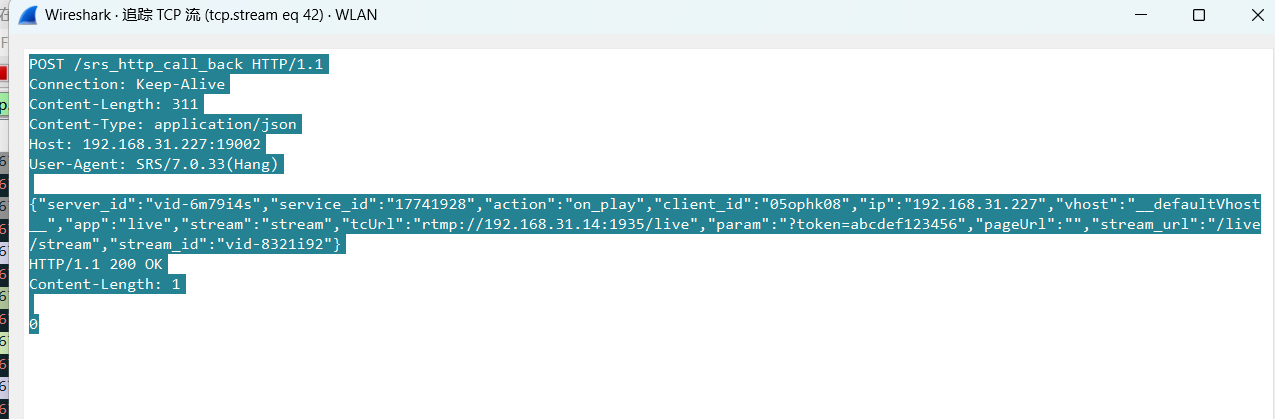
srs linux
下载编译运行 git clone https:///ossrs/srs.git ./configure --h265on make 编译完成后即可启动SRS # 启动 ./objs/srs -c conf/srs.conf # 查看日志 tail -n 30 -f ./objs/srs.log 开放端口 默认RTMP接收推流端口是1935,SRS管理页面端口是8080,可…...

LLM基础1_语言模型如何处理文本
基于GitHub项目:https://github.com/datawhalechina/llms-from-scratch-cn 工具介绍 tiktoken:OpenAI开发的专业"分词器" torch:Facebook开发的强力计算引擎,相当于超级计算器 理解词嵌入:给词语画"…...

大模型多显卡多服务器并行计算方法与实践指南
一、分布式训练概述 大规模语言模型的训练通常需要分布式计算技术,以解决单机资源不足的问题。分布式训练主要分为两种模式: 数据并行:将数据分片到不同设备,每个设备拥有完整的模型副本 模型并行:将模型分割到不同设备,每个设备处理部分模型计算 现代大模型训练通常结合…...
