[ACTF2023]复现
MDH
源题:
from hashlib import sha256
from secret import flagr = 128
c = 96
p = 308955606868885551120230861462612873078105583047156930179459717798715109629
Fp = GF(p)def gen():a1 = random_matrix(Fp, r, c)a2 = random_matrix(Fp, r, c)A = a1 * a2.Treturn (a1, a2), Ask_alice, pk_alice = gen()
sk_bob, pk_bob = gen()
shared = (sk_alice[0].T * pk_bob * sk_alice[1]).trace()
ct = int(sha256(str(int(shared)).encode()).hexdigest(), 16) ^^ int.from_bytes(flag, 'big')with open('output.txt', 'wb') as f:f.write(str(ct).encode() + b'\n')f.write(str(list(pk_alice)).encode() + b'\n')f.write(str(list(pk_bob)).encode() + b'\n')
思路:本题思路很简单,高等代数,sk_alice[0].T * pk_bob * sk_alice[1]和pk_bob*pk_alice.T的迹的大小是相等的。
exp:
from hashlib import sha256
from Crypto.Util.number import*r = 128
c = 96
p = 308955606868885551120230861462612873078105583047156930179459717798715109629
Fp = GF(p)f = open('output.txt','r')
ct = eval(f.readline())
a1 = eval(f.readline())
a2 = eval(f.readline())pk_alice = matrix(Fp,a1)
pk_bob = matrix(Fp,a2)
# print(pk_alice)
# print(pk_bob)
shared = (pk_bob*pk_alice.T).trace()
m = int(sha256(str(int(shared)).encode()).hexdigest(), 16) ^^ ct
print(long_to_bytes(m))claw crane
源码:
!/usr/bin/env python3
from Crypto.Util.number import (bytes_to_long, long_to_bytes
)
from hashlib import md5
import os, signal
import sys
import randomBITS = 128class ClawCrane(object):def __init__(self) -> None:self.seed = bytes_to_long(os.urandom(BITS//8))self.bless = 0self.score = 0def get_input(self, prompt="> "):print(prompt, end="")sys.stdout.flush()return input()def check_pos(self, pos, moves):col, row = 0, 0for move in moves:if move == "W":if row < 15: row += 1elif move == "S":if row > 0: row -= 1elif move == "A":if col > 0: col -= 1elif move == "D":if col < 15: col += 1else:return -1print(col, row)return pos == [col, row]def gen_chaos(self, inp):def mapping(x):if x=='W': return "0"if x=='S': return "1"if x=='A': return "2"if x=='D': return "3"vs = int("".join(map(mapping, inp)), 4)chaos = bytes_to_long(md5(long_to_bytes((self.seed + vs) % pow(2,BITS))).digest())self.seed = (self.seed + chaos + 1) % pow(2,BITS)return chaosdef destiny_claw(self, delta):bits = bin(delta)[2:]if len(bits) < 128+self.bless:bits += "0"*(128+self.bless - len(bits))c = random.choice(bits)if c=='0': return Trueelse: return Falsedef run(self):pos = [random.randrange(1,16), random.randrange(1,16)]moves = self.get_input(f"i am at {pos}, claw me.\nYour moves: ")if len(moves) > 100:print("too many steps")returnif not self.check_pos(pos, moves):print("sorry, clawed nothing")returnr = self.gen_chaos(moves[:64])print(f"choas: {r}")p, q = map(int, self.get_input(f"give me your claw using p,q and p,q in [0, 18446744073709551615] (e.g.: 1,1): ").split(","))if not (p>0 and p<pow(2,BITS//2) and q>0 and q<pow(2,BITS//2)):print("not in range")returndelta = abs(r*q - p*pow(2,BITS))if self.destiny_claw(delta):self.score += 10self.bless = 0print("you clawed it")else:self.bless += 16print("sorry, clawed nothing")def main():signal.alarm(600)cc = ClawCrane()for _ in range(256):try:cc.run()print(f"your score: {cc.score}")except:print(f"abort")breakif cc.score >= 2220:print(f"flag: {open('/flag.txt').read()}")if __name__ == "__main__":main()思路:在本题目中我们需要绕过proof验证、check_pos的位置验证和以下
chaos = bytes_to_long(md5(long_to_bytes((self.seed + vs) % pow(2,BITS))).digest()) self.seed = (self.seed + chaos + 1) % pow(2,BITS)
首先:
proof验证:我们知道是将十六进制数输入,进行sha1操作与已知输出对比,相同即可通过,我们在输入的十六进制数的前六位未知,直接爆破即可。
check_pos的位置验证:我们观察源码,源码是通过构造的输入序列(‘A’,'B','C','D'),对此时在(0,0)的点进行位移输入到随机确认的pos位置上,若最终移动的位置相同,即可通过。
由于 r = self.gen_chaos(moves[:64]),moves是我们自己输入的,此时函数仅仅需要前64位进行运算获得r的值,我们需要固定r的值的大小,所以此时便在seed上做文章,令每次输入的vs都在上一个vs的基础上减去(chaos + 1),此时,输出的chaos值固定。
于是,check_pos的位置验证中,我们输入序列的前64位由上述r取值中确认,我们需要计算出64次移动后的位置,再寻找到pos点的移动所需里程。
完成上述操作后,开始运算,当cc.score >= 2220时,我们即可得到flag的值
exp:
import itertools
from Crypto.Util.number import *
from hashlib import md5
import gmpy2
from pwn import *
from tqdm import tqdm
from hashlib import *
from time import *BITS = 128def proof():sh.recvuntil(b'sha1(prefix+"')k = sh.recvuntil(b'"')[:-1]sh.recvuntil(b')==')cc = sh.recvuntil(b'\n')[:-1]sh.recvuntil(b'prefix = ?\n')String = b'0123456789abcdef'# print(k,cc)start = time()for i1, i2, i3, i4, i5, i6 in tqdm(itertools.product(String, String, String, String, String, String)):kk = str(chr(i1)) + str(chr(i2)) + str(chr(i3)) + str(chr(i4)) + str(chr(i5)) + str(chr(i6)) + k.decode()# print(kk,k.decode())# print(sha1(kk.encode()).hexdigest(),cc.decode())if sha1(kk.encode()).hexdigest() == cc.decode():print(kk[:6])sh.sendline(kk[:6].encode())breakend = time()print(f"consume {end - start} time")def check_pos(pos, moves):col, row = int(pos[0]), int(pos[1])for move in moves:if move == "W":if row < 15: row += 1elif move == "S":if row > 0: row -= 1elif move == "A":if col > 0: col -= 1elif move == "D":if col < 15: col += 1else:return -1print(col, row)return [col, row]def solve_chaos(la_chaos, idx):def mapping(x):if x == '0': return "W"if x == '1': return "S"if x == '2': return "A"if x == '3': return "D"New_vs = (-la_chaos - 1) * (idx - 1) % (2 ^ 128)target = New_vs % 4new_vs = ''while New_vs:if target == 0:new_vs += 'W'New_vs = New_vs // 4if target == 1:new_vs += 'S'New_vs = New_vs // 4if target == 2:new_vs += 'A'New_vs = New_vs // 4if target == 3:new_vs += 'D'New_vs = New_vs // 4target = New_vs % 4# print(new_vs)new_vs = new_vs[::-1]if len(new_vs) != 64:new_vs = mapping("0") * (64 - len(new_vs)) + new_vsprint('solve_chaos:', new_vs)return new_vsdef solve_pos(cu_pos, new_pos, sol):x0, y0 = cu_posx1, y1 = new_posif x0 < x1:sol += 'D' * ((x1 - x0) % 16)else:sol += 'A' * ((x0 - x1) % 16)if y0 < y1:sol += 'W' * ((y1 - y0) % 16)else:sol += 'S' * ((y0 - y1) % 16)return soldef solve_pq(chaos):K = matrix(ZZ, [[2 ^ 128, 0], [chaos, 1]])KK = K.LLL()# print(num)v = K.solve_left(KK[0])p, q = v[0], v[1]return abs(p), abs(q)for i in range(1, 10000):print(f'Try {i} times')sh = process(['python3', 'server.py'])proof()Assert, chaos, idx, failure, success = 0, -1, 0, 0, 0p, q = 0, 0try:while idx < 256:idx += 1print(f'----------The {idx} quarters---------')sh.recvuntil(b'i am at ')pos = eval(sh.recvuntil(b']'))sh.recvuntil(b'Your moves: ')x1, y1 = int(pos[0]), int(pos[1])# print(pos,x1,y1,chaos)vs = solve_chaos(chaos, idx)# print(vs)x0, y0 = check_pos((0, 0), vs)moves = solve_pos((x0, y0), (x1, y1), vs)sh.sendline(moves.encode())sh.recvuntil(b'choas: ')chaos = int(sh.recvuntil(b'\n')[:-1])if not p and not q:p, q = solve_pq(chaos)x = abs(chaos * q - p * pow(2, 128))print(bin(x)[2:].count('1'))print(bin(x)[2:])if bin(x)[2:].count('1') > 23:breakprint(abs(chaos * q - p * pow(2, 128)))sh.recvuntil(b'give me your claw using p,q and p,q in [0, 18446744073709551615] (e.g.: 1,1): ')sh.sendline(f'{p},{q}'.encode())ding = sh.recvline()# print(ding)sh.recvuntil(b'your score: ')score = sh.recvuntil(b'\n')[:-1]print('Your score: ', score)sh.interactive()except:continueEazyRSA
源码:
from secret import flag
from Crypto.Util.number import *def genKey(nbits, dbits):bbits = (nbits // 2 - dbits) // 2while True:a = getRandomNBitInteger(dbits)b = getRandomNBitInteger(bbits)c = getRandomNBitInteger(bbits)p1 = a * b * c + 1if isPrime(p1):# print("p1 =", p1)breakwhile True:d = getRandomNBitInteger(dbits)p2 = b * c * d + 1if isPrime(p2):# print("p2 =", p2)breakwhile True:e = getRandomNBitInteger(bbits)f = getRandomNBitInteger(bbits)q1 = e * d * f + 1p3 = a * e * f + 1if isPrime(q1) and isPrime(p3):# print("p3 =", p3)# print("q1 =", q1)breakwhile True:d_ = getRandomNBitInteger(dbits)if GCD(a * b * c * d * e * f, d_) != 1:continuee_ = inverse(d_, a * b * c * d * e * f)k1 = (e_ * d_ - 1) // (a * b * c * d * e * f)assert e_ * d_ == (a * b * c * d * e * f) * k1 + 1q2 = k1 * e * f + 1q3 = k1 * b * c + 1if isPrime(q2) and isPrime(q3):# print("q2 =", q2)# print("q3 =", q3)# print("e =", e_)# print("d =", d_)breakn1 = p1 * q1n2 = p2 * q2n3 = p3 * q3assert pow(pow(0xdeadbeef, e_, n1), d_, n1) == 0xdeadbeefassert pow(pow(0xdeadbeef, e_, n2), d_, n2) == 0xdeadbeefassert pow(pow(0xdeadbeef, e_, n3), d_, n3) == 0xdeadbeefreturn(e_, n1, n2, n3)nbits = 0x600
dbits = 0x210m = bytes_to_long(flag)
e, n1, n2, n3 = genKey(nbits, dbits)
c = pow(m, e, n1)print("c =", c)
print("e =", e)
print("n1 =", n1)
print("n2 =", n2)
print("n3 =", n3)# c = 63442255298812942222810837512019302954917822996915527697525497640413662503768308023517128481053593562877494934841788054865410798751447333551319775025362132176942795107214528962480350398519459474033659025815248579631003928932688495682277210240277909527931445899728273182691941548330126199931886748296031014210795428593631253184315074234352536885430181103986084755140024577780815130067722355861473639612699372152970688687877075365330095265612016350599320999156644
# e = 272785315258275494478303901715994595013215169713087273945370833673873860340153367010424559026764907254821416435761617347240970711252213646287464416524071944646705551816941437389777294159359383356817408302841561284559712640940354294840597133394851851877857751302209309529938795265777557840238332937938235024502686737802184255165075195042860413556866222562167425361146312096189555572705076252573222261842045286782816083933952875990572937346408235562417656218440227
# n1 = 473173031410877037287927970398347001343136400938581274026578368211539730987889738033351265663756061524526288423355193643110804217683860550767181983527932872361546531994961481442866335447011683462904976896894011884907968495626837219900141842587071512040734664898328709989285205714628355052565784162841441867556282849760230635164284802614010844226671736675222842060257156860013384955769045790763119616939897544697150710631300004180868397245728064351907334273953201
# n2 = 327163771871802208683424470007561712270872666244394076667663345333853591836596054597471607916850284565474732679392694515656845653581599800514388800663813830528483334021178531162556250468743461443904645773493383915711571062775922446922917130005772040139744330987272549252540089872170217864935146429898458644025927741607569303966038195226388964722300472005107075179204987774627759625183739199425329481632596633992804636690274844290983438078815836605603147141262181
# n3 = 442893163857502334109676162774199722362644200933618691728267162172376730137502879609506615568680508257973678725536472848428042122350184530077765734033425406055810373669798840851851090476687785235612051747082232947418290952863499263547598032467577778461061567081620676910480684540883879257518083587862219344609851852177109722186714811329766477552794034774928983660538381764930765795290189612024799300768559485810526074992569676241537503405494203262336327709010421
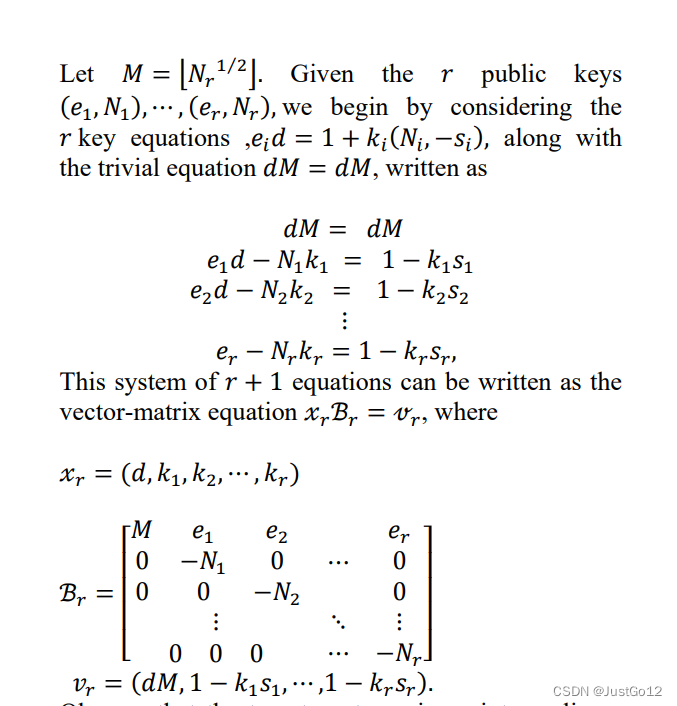
思路:造格即可
exp:
from sage.all import *
from Crypto.Util.number import *
import randomc = 63442255298812942222810837512019302954917822996915527697525497640413662503768308023517128481053593562877494934841788054865410798751447333551319775025362132176942795107214528962480350398519459474033659025815248579631003928932688495682277210240277909527931445899728273182691941548330126199931886748296031014210795428593631253184315074234352536885430181103986084755140024577780815130067722355861473639612699372152970688687877075365330095265612016350599320999156644
e = 272785315258275494478303901715994595013215169713087273945370833673873860340153367010424559026764907254821416435761617347240970711252213646287464416524071944646705551816941437389777294159359383356817408302841561284559712640940354294840597133394851851877857751302209309529938795265777557840238332937938235024502686737802184255165075195042860413556866222562167425361146312096189555572705076252573222261842045286782816083933952875990572937346408235562417656218440227
n1 = 473173031410877037287927970398347001343136400938581274026578368211539730987889738033351265663756061524526288423355193643110804217683860550767181983527932872361546531994961481442866335447011683462904976896894011884907968495626837219900141842587071512040734664898328709989285205714628355052565784162841441867556282849760230635164284802614010844226671736675222842060257156860013384955769045790763119616939897544697150710631300004180868397245728064351907334273953201
n2 = 327163771871802208683424470007561712270872666244394076667663345333853591836596054597471607916850284565474732679392694515656845653581599800514388800663813830528483334021178531162556250468743461443904645773493383915711571062775922446922917130005772040139744330987272549252540089872170217864935146429898458644025927741607569303966038195226388964722300472005107075179204987774627759625183739199425329481632596633992804636690274844290983438078815836605603147141262181
n3 = 442893163857502334109676162774199722362644200933618691728267162172376730137502879609506615568680508257973678725536472848428042122350184530077765734033425406055810373669798840851851090476687785235612051747082232947418290952863499263547598032467577778461061567081620676910480684540883879257518083587862219344609851852177109722186714811329766477552794034774928983660538381764930765795290189612024799300768559485810526074992569676241537503405494203262336327709010421M = int(random.randint(n1,2*n2) ** 0.5)
K = matrix([[M,e,e,e],[0,-n1,0,0],[0,0,-n2,0],[0,0,0,-n3]])
KK = K.LLL()
d = int(KK[0][0]/M)
m = pow(c,d,n1)
print(long_to_bytes(int(m)))MidRSA
源码:
from secret import flag
from Crypto.Util.number import *def genKey(nbits, dbits):bbits = (nbits // 2 - dbits) // 2while True:a = getRandomNBitInteger(dbits)b = getRandomNBitInteger(bbits)c = getRandomNBitInteger(bbits)p1 = a * b * c + 1if isPrime(p1):# print("p1 =", p1)breakwhile True:d = getRandomNBitInteger(dbits)p2 = b * c * d + 1if isPrime(p2):# print("p2 =", p2)breakwhile True:e = getRandomNBitInteger(bbits)f = getRandomNBitInteger(bbits)q1 = e * d * f + 1p3 = a * e * f + 1if isPrime(q1) and isPrime(p3):# print("p3 =", p3)# print("q1 =", q1)breakwhile True:d_ = getRandomNBitInteger(dbits)if GCD(a * b * c * d * e * f, d_) != 1:continuee_ = inverse(d_, a * b * c * d * e * f)k1 = (e_ * d_ - 1) // (a * b * c * d * e * f)assert e_ * d_ == (a * b * c * d * e * f) * k1 + 1q2 = k1 * e * f + 1q3 = k1 * b * c + 1if isPrime(q2) and isPrime(q3):# print("q2 =", q2)# print("q3 =", q3)# print("e =", e_)print("d =", d_)breakn1 = p1 * q1n2 = p2 * q2n3 = p3 * q3assert pow(pow(0xdeadbeef, e_, n1), d_, n1) == 0xdeadbeefassert pow(pow(0xdeadbeef, e_, n2), d_, n2) == 0xdeadbeefassert pow(pow(0xdeadbeef, e_, n3), d_, n3) == 0xdeadbeefreturn(e_, n1, n2, n3)nbits = 0x600
dbits = 0x240m = bytes_to_long(flag)
e, n1, n2, n3 = genKey(nbits, dbits)
c = pow(m, e, n1)print("c =", c)
print("e =", e)
print("n1 =", n1)
print("n2 =", n2)
print("n3 =", n3)# c = 598823083137858565473505718525815255620672892612784824187302545127574115000325539999824374357957135208478070797113625659118825530731575573239221853507638809719397849963861367352055486212696958923800593172417262351719477530809870735637329898331854130533160020420263724619225174940214193740379571953951059401685115164634005411478583529751890781498407518739069969017597521632392997743956791839564573371955246955738575593780508817401390102856295102225132502636316844
# e = 334726528702628887205076146544909357751287869200972341824248480332256143541098971600873722567713812425364296038771650383962046800505086167635487091757206238206029361844181642521606953049529231154613145553220809927001722518303114599682529196697410089598230645579658906203453435640824934159645602447676974027474924465177723434855318446073578465621382859962701578350462059764095163424218813852195709023435581237538699769359084386399099644884006684995755938605201771
# n1 = 621786427956510577894657745225233425730501124908354697121702414978035232119311662357181409283130180887720760732555757426221953950475736078765267856308595870951635246720750862259255389006679454647170476427262240270915881126875224574474706572728931213060252787326765271752969318854360970801540289807965575654629288558728966771231501959974533484678236051025940684114262451777094234017210230731492336480895879764397821363102224085859281971513276968559080593778873231
# n2 = 335133378611627373902246132362791381335635839627660359611198202073307340179794138179041524058800936207811546752188713855950891460382258433727589232119735602364790267515558352318957355100518427499530387075144776790492766973547088838586041648900788325902589777445641895775357091753360428198189998860317775077739054298868885308909495601041757108114540069950359802851809227248145281594107487276003206931533768902437356652676341735882783415106786497390475670647453821
# n3 = 220290953009399899705676642623181513318918775662713704923101352853965768389363281894663344270979715555659079125651553079702318700200824118622766698792556506368153467944348604006011828780474050012010677204862020009069971864222175380878120025727369117819196954091417740367068284457817961773989542151049465711430065838517386380261817772422927774945414543880659243592749932727798690742051285364898081188510009069286094647222933710799481899960520270189522155672272451
思路:相比于EazyRSA题目,提高了dbits的比特数,使得无法计算,此时我们需要爆破一定的高位即可。
exp:
from sage.all import *
from Crypto.Util.number import *
import random
from tqdm import tqdmc = 598823083137858565473505718525815255620672892612784824187302545127574115000325539999824374357957135208478070797113625659118825530731575573239221853507638809719397849963861367352055486212696958923800593172417262351719477530809870735637329898331854130533160020420263724619225174940214193740379571953951059401685115164634005411478583529751890781498407518739069969017597521632392997743956791839564573371955246955738575593780508817401390102856295102225132502636316844
e = 334726528702628887205076146544909357751287869200972341824248480332256143541098971600873722567713812425364296038771650383962046800505086167635487091757206238206029361844181642521606953049529231154613145553220809927001722518303114599682529196697410089598230645579658906203453435640824934159645602447676974027474924465177723434855318446073578465621382859962701578350462059764095163424218813852195709023435581237538699769359084386399099644884006684995755938605201771
n1 = 621786427956510577894657745225233425730501124908354697121702414978035232119311662357181409283130180887720760732555757426221953950475736078765267856308595870951635246720750862259255389006679454647170476427262240270915881126875224574474706572728931213060252787326765271752969318854360970801540289807965575654629288558728966771231501959974533484678236051025940684114262451777094234017210230731492336480895879764397821363102224085859281971513276968559080593778873231
n2 = 335133378611627373902246132362791381335635839627660359611198202073307340179794138179041524058800936207811546752188713855950891460382258433727589232119735602364790267515558352318957355100518427499530387075144776790492766973547088838586041648900788325902589777445641895775357091753360428198189998860317775077739054298868885308909495601041757108114540069950359802851809227248145281594107487276003206931533768902437356652676341735882783415106786497390475670647453821
n3 = 220290953009399899705676642623181513318918775662713704923101352853965768389363281894663344270979715555659079125651553079702318700200824118622766698792556506368153467944348604006011828780474050012010677204862020009069971864222175380878120025727369117819196954091417740367068284457817961773989542151049465711430065838517386380261817772422927774945414543880659243592749932727798690742051285364898081188510009069286094647222933710799481899960520270189522155672272451for i in tqdm(range(70000,2^20)):t1 = bin(i)[2:].zfill(21)h = int('1'+t1[:3],2) << 0x23ch1 = int(t1[3:9],2) << 1338h2 = int(t1[9:15],2) << 1338h3 = int(t1[15:21],2) << 1338M = Matrix(QQ,[[-e,-e,-e,2^766,0,0,0,0],[n1,0,0,0,0,0,0,0],[0,n2,0,0,0,0,0,0],[0,0,n3,0,0,0,0,0],[-h*e,-h*e,-h*e,0,2^(1338),0,0,0],[-h1,0,0,0,0,2^1338,0,0],[0,-h2,0,0,0,0,2^1338,0],[0,0,-h3,0,0,0,0,2^1338]])
# e_*d_-k1*n1,n1res = M.LLL()d = int(res[0][3]//2^766) + hif b'ACTF' in long_to_bytes(ZZ(pow(c,d,n1))):print(long_to_bytes(ZZ(pow(c,d,n1))))
相关文章:

[ACTF2023]复现
MDH 源题: from hashlib import sha256 from secret import flagr 128 c 96 p 308955606868885551120230861462612873078105583047156930179459717798715109629 Fp GF(p)def gen():a1 random_matrix(Fp, r, c)a2 random_matrix(Fp, r, c)A a1 * a2.Treturn…...
HNU-编译原理-讨论课1
讨论课安排:2次4学时,分别完成四大主题讨论 分组:每个班分为8组,每组4~5人,自选组长1人 要求和说明: 以小组为单位上台报告;每次每组汇报2个小主题,每组按要求在2个小主题中各选1…...

【Linux】关于Nginx的详细使用,部署项目
前言: 今天小编给大家带来的是关于Nginx的详细使用,部署项目,希望可以给正在学习,工作的你带来有效的帮助! 一,Nginx简介 Nginx是一个高性能的开源Web服务器和反向代理服务器。它最初由Igor Sysoev在2004年…...

编写 navigation2 控制器插件
简介 本教程展示了如何创建自己的控制器插件。在本教程中,我们将基于这篇论文实现纯追踪路径跟踪算法。建议您阅读该论文。 注意:本教程基于 Nav2 堆栈中以前存在的简化版本的 Regulated Pure Pursuit 控制器。您可以在此处找到与本教程相匹配的源代…...

计算机网络 第六章应用层
文章目录 1 应用层功能概述2 网络应用模型:客户服务器(CS)3 网络应用模型:PeerToPeer(P2P)4 域名和域名系统5 常见域名解析服务器6 两种域名解析过程7 什么是FTP8 FTP的工作原理9 EMail的组成 1 应用层功能概述 2 网络应用模型:客户服务器(CS…...
)
人工智能领域CCF推荐国际学术刊物最新目录(全)
2021年1月,CCF决定启动新一轮中国计算机学会推荐国际学术会议和期刊目录调整工作并委托CCF学术工作委员会组织实施。 2023年3月8日, 中国计算机学会正式发布了2022版《中国计算机学会推荐国际学术会议和期刊目录》(以下简称《目录》) 。 相较于上一版目录࿰…...
实现基于 Azure DevOps 的数据库 CI/CD 最佳实践
数据库变更一直是整个应用发布过程中效率最低、流程最复杂、风险最高的环节,也是 DevOps 流程中最难以攻克的阵地。那我们是否能在具体的 CI/CD 流程中,像处理代码那样处理数据库变更呢? DORA 调研报告 DORA(DevOps Research &am…...

上海实习小记
8月3日入职10月27日离职,原本还想做满3个月再走,可惜公司提早要迁到成都,就只好 离职了回学校了。在博客随便写写记录一下这几个月的生活吧,想到哪里写到哪里 实习的公司是一个小公司,开发一款类似于咸鱼之王的游戏&am…...
uniapp实现路线规划
UniApp是一个基于Vue.js框架开发的跨平台应用开发框架,可以同时构建iOS、Android、H5等多个平台的应用。它使用了基于前端技术栈的Web开发方式,通过编写一套代码,即可在不同平台上运行和发布应用。 UniApp具有以下特点: 跨平台开…...
飞利浦双串口51单片机485网关
主要功能将PC端的数据接收下来,分发到不同的设备,也是轮询设备数据读取回来,打包回传到PC端,数据包包头包尾识别,数据校验,接收超时处理,将协议结构化处理,协议的改动不需要改动程序…...
生态扩展:Flink Doris Connector
生态扩展:Flink Doris Connector 官网地址: https://doris.apache.org/zh-CN/docs/dev/ecosystem/flink-doris-connector flink的安装: tar -zxvf flink-1.16.0-bin-scala_2.12.tgz mv flink-1.16.0-bin-scala_2.12.tgz /opt/flinkflink环境…...

HarmonyOS(二)—— 初识ArkTS开发语言(上)之TypeScript入门
前言 Mozilla创造了JS,Microsoft创建了TS,而Huawei进一步推出了ArkTS。因此在学习使用ArkTS前,需要掌握基本的TS开发技能。 ArkTS介绍 ArkTS是HarmonyOS优选的主力应用开发语言。它在TypeScript(简称TS)的基础上&am…...
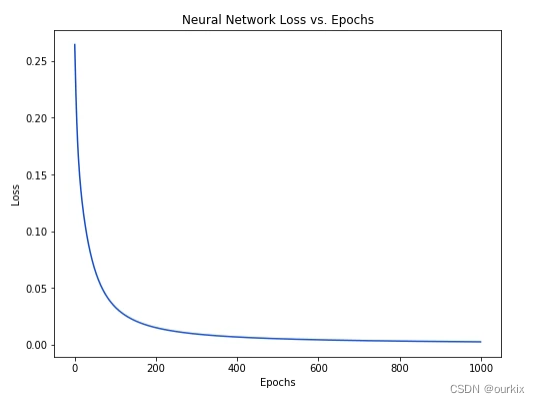
从零开始实现神经网络(一)_NN神经网络
参考文章:神经网络介绍 一、神经元 这一神经网络的基本单元,神经元接受输入,对它们进行一些数学运算,并产生一个输出。 这里有三步。 首先,将每个输入(X1)乘以一个权重: 接下来&…...

C语言 每日一题 Day10
1.使用函数判断完全平方数 本题要求实现一个判断整数是否为完全平方数的简单函数。 函数接口定义: int IsSquare(int n); 其中n是用户传入的参数,在长整型范围内。如果n是完全平方数,则函数IsSquare必须返回1,否则返回0。 代码实…...
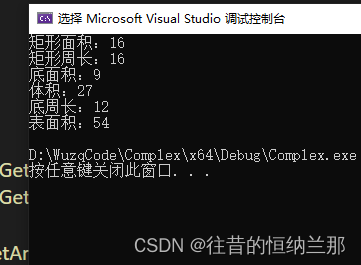
C++继承——矩形和长方体
Rectangle矩形类 /*矩形类*/ class Rectangle { private:double L 0;double W 0; public:Rectangle() default;Rectangle(double a, double b);double GetArea(); /*矩形面积*/double GetGirth(); /*矩形周长*/ }; /*构造函数*/ Rectangle::Rectangle(double a, double b) …...

代码随想录打卡第五十八天|● 583. 两个字符串的删除操作 ● 72. 编辑距离
583. 两个字符串的删除操作 题目: 给定两个单词 word1 和 word2 ,返回使得 word1 和 word2 相同所需的最小步数。 每步 可以删除任意一个字符串中的一个字符。 题目链接: 583. 两个字符串的删除操作 解题思路: dp数组的含义&am…...

面试流程之——程序员如何写项目经验
在简历中介绍IT项目经验,你可以遵循以下步骤: 明确项目目标:首先,清晰地阐述项目的目标。这可以是提升某个软件的性能,改进某个系统的用户界面,或者增加某款产品的功能。让读者了解你的工作与项目的整体目…...
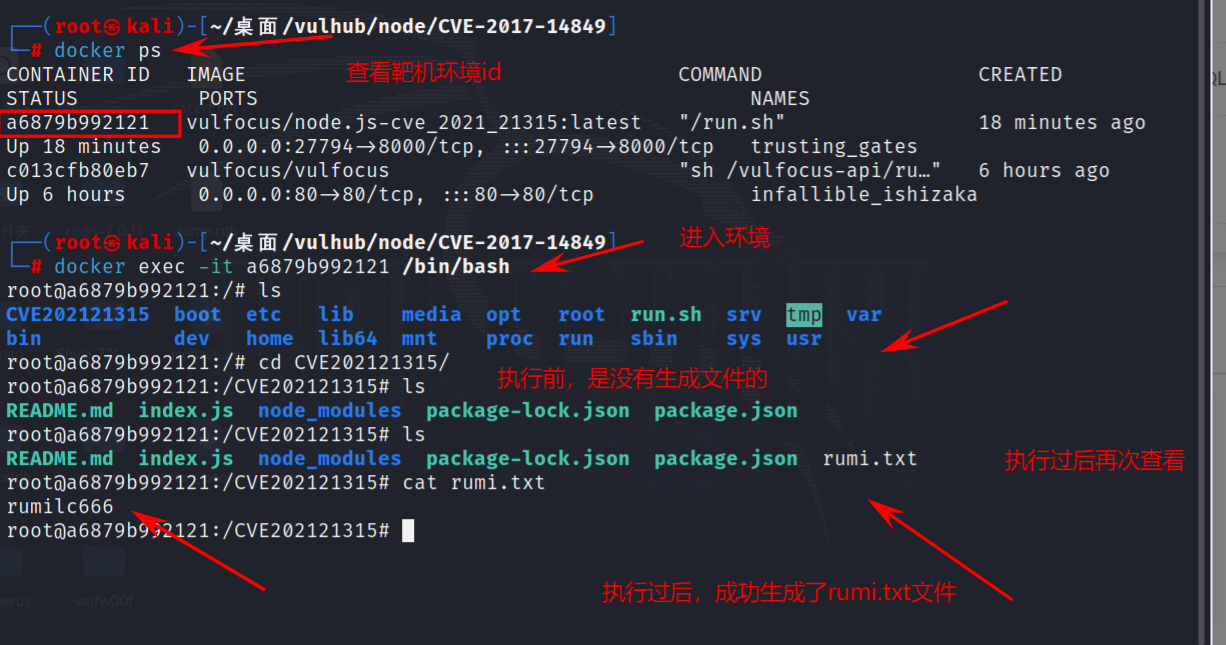
框架安全-CVE 漏洞复现DjangoFlaskNode.jsJQuery框架漏洞复现
目录 服务攻防-框架安全&CVE复现&Django&Flask&Node.JS&JQuery漏洞复现中间件列表介绍常见语言开发框架Python开发框架安全-Django&Flask漏洞复现Django开发框架漏洞复现CVE-2019-14234(Django JSONField/HStoreField SQL注入漏洞ÿ…...
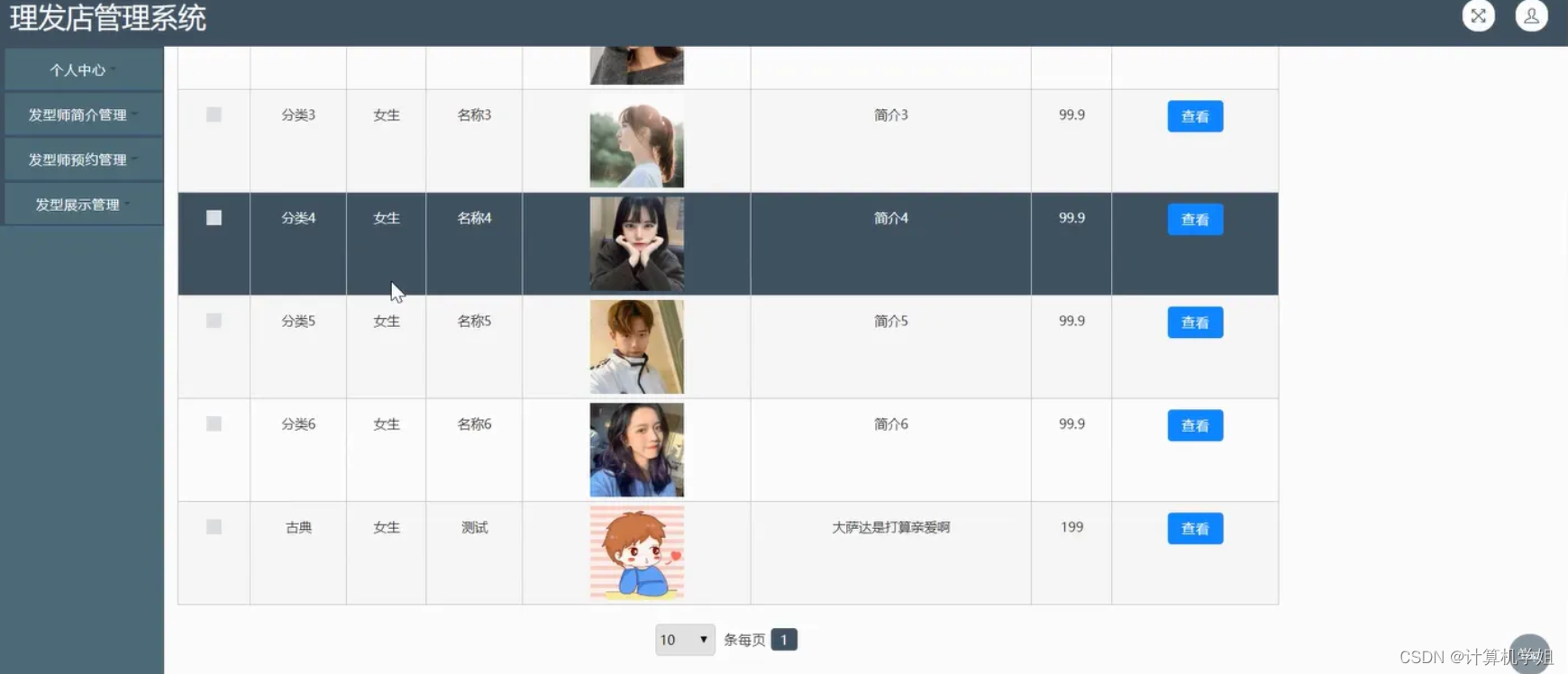
基于SSM的理发店管理系统
基于SSM的理发店管理系统的设计与实现~ 开发语言:Java数据库:MySQL技术:SpringSpringMVCMyBatis工具:IDEA/Ecilpse、Navicat、Maven 系统展示 主页 公告信息 管理员界面 用户界面 摘要 基于SSM(Spring、Spring MVC、…...
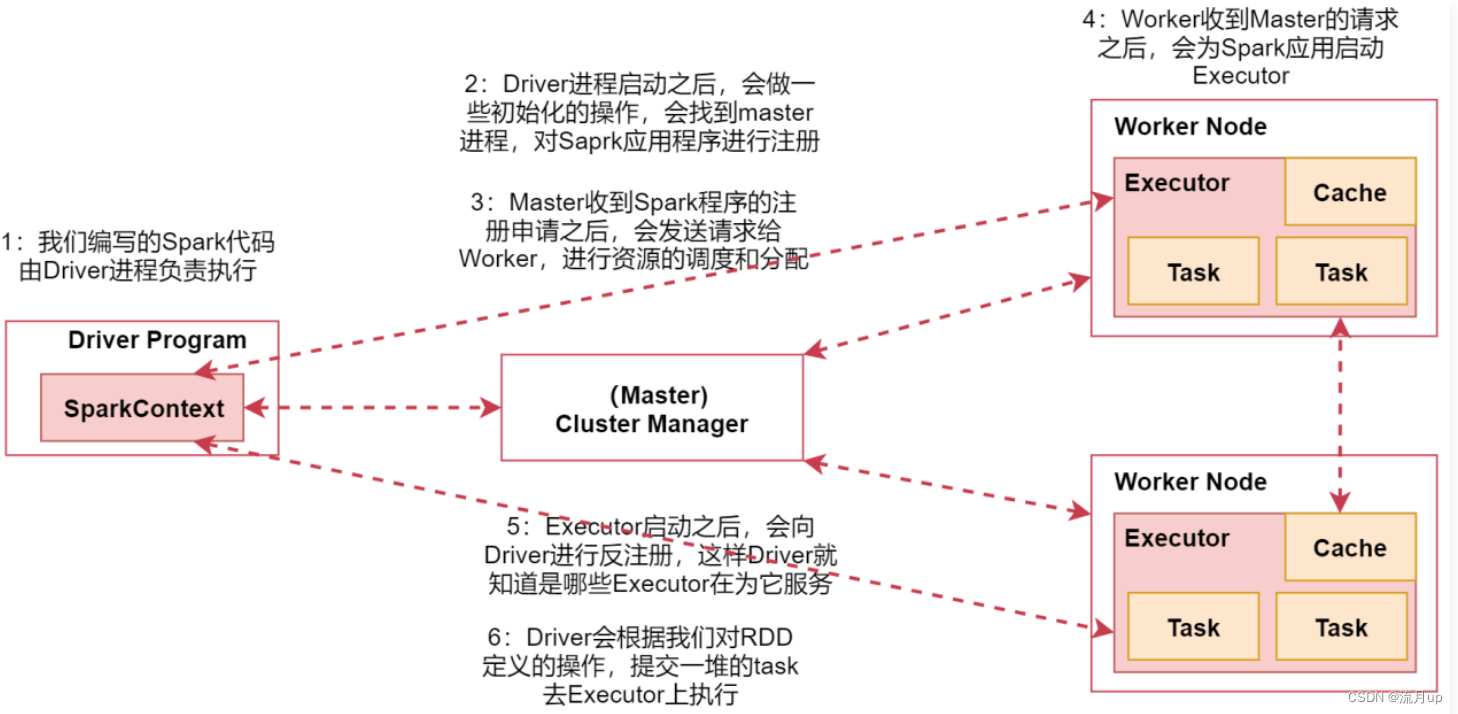
2.Spark的工作与架构原理
概述 目标: spark的工作原理spark数据处理通用流程rdd 什么是rddrdd 的特点 spark架构 spark架构相关进程spark架构原理 spark的工作原理 spark 的工作原理,如下图 图中中间部分是spark集群,也可以是基于 yarn 的,图上可以…...
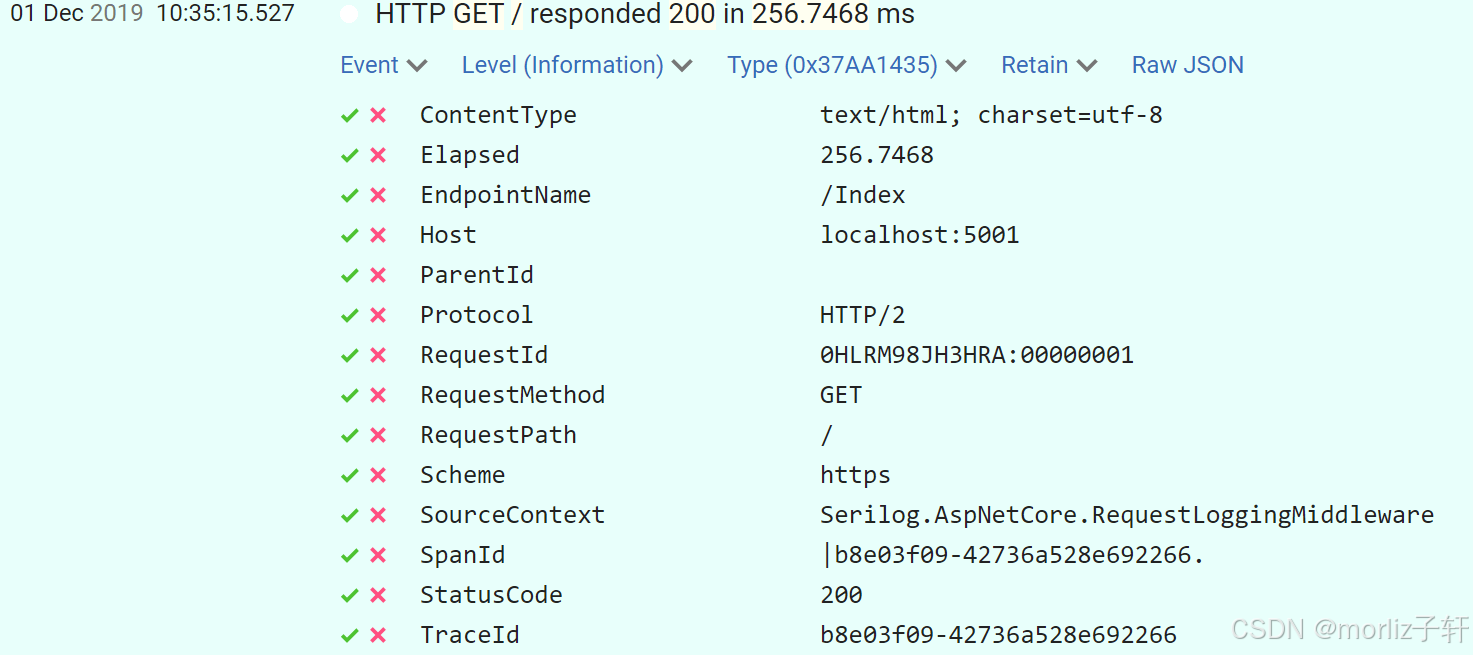
深入浅出Asp.Net Core MVC应用开发系列-AspNetCore中的日志记录
ASP.NET Core 是一个跨平台的开源框架,用于在 Windows、macOS 或 Linux 上生成基于云的新式 Web 应用。 ASP.NET Core 中的日志记录 .NET 通过 ILogger API 支持高性能结构化日志记录,以帮助监视应用程序行为和诊断问题。 可以通过配置不同的记录提供程…...
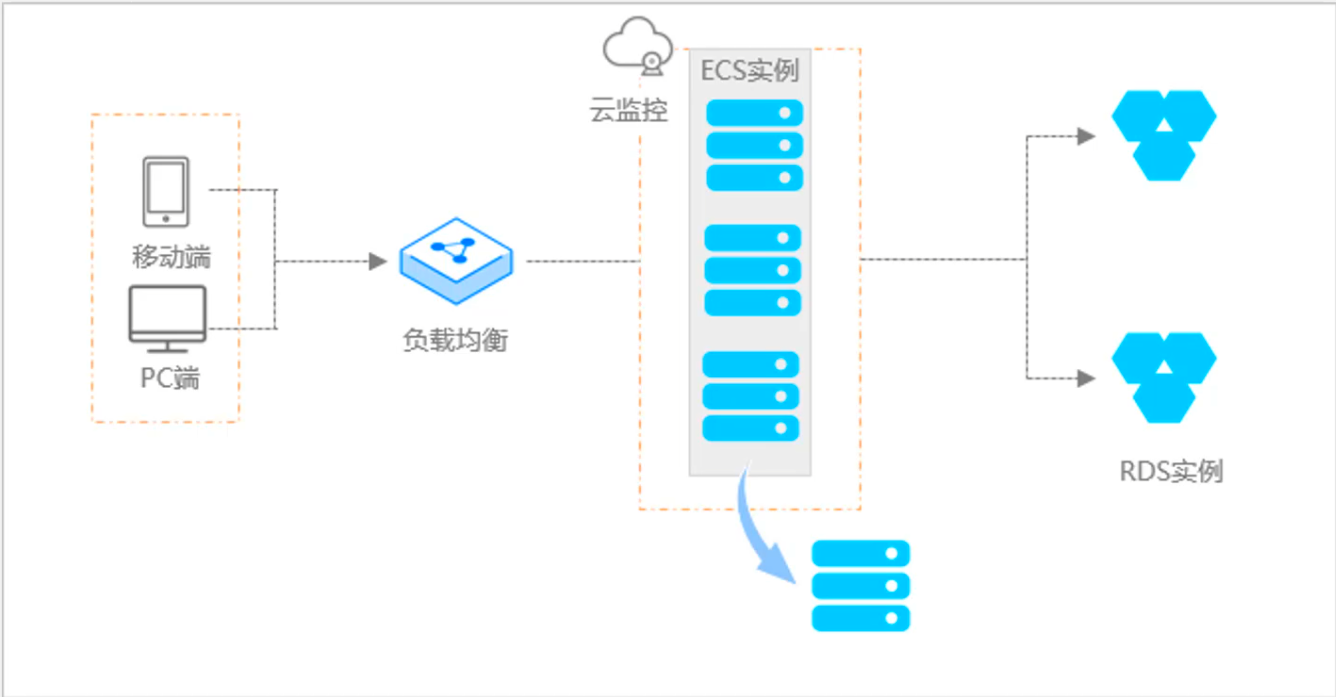
阿里云ACP云计算备考笔记 (5)——弹性伸缩
目录 第一章 概述 第二章 弹性伸缩简介 1、弹性伸缩 2、垂直伸缩 3、优势 4、应用场景 ① 无规律的业务量波动 ② 有规律的业务量波动 ③ 无明显业务量波动 ④ 混合型业务 ⑤ 消息通知 ⑥ 生命周期挂钩 ⑦ 自定义方式 ⑧ 滚的升级 5、使用限制 第三章 主要定义 …...

ssc377d修改flash分区大小
1、flash的分区默认分配16M、 / # df -h Filesystem Size Used Available Use% Mounted on /dev/root 1.9M 1.9M 0 100% / /dev/mtdblock4 3.0M...
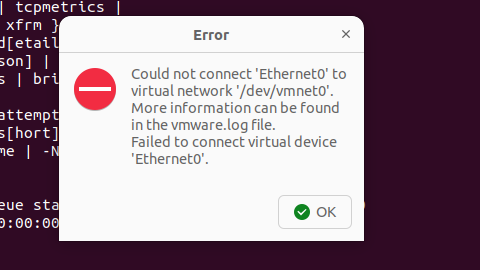
解决Ubuntu22.04 VMware失败的问题 ubuntu入门之二十八
现象1 打开VMware失败 Ubuntu升级之后打开VMware上报需要安装vmmon和vmnet,点击确认后如下提示 最终上报fail 解决方法 内核升级导致,需要在新内核下重新下载编译安装 查看版本 $ vmware -v VMware Workstation 17.5.1 build-23298084$ lsb_release…...

基于服务器使用 apt 安装、配置 Nginx
🧾 一、查看可安装的 Nginx 版本 首先,你可以运行以下命令查看可用版本: apt-cache madison nginx-core输出示例: nginx-core | 1.18.0-6ubuntu14.6 | http://archive.ubuntu.com/ubuntu focal-updates/main amd64 Packages ng…...

服务器硬防的应用场景都有哪些?
服务器硬防是指一种通过硬件设备层面的安全措施来防御服务器系统受到网络攻击的方式,避免服务器受到各种恶意攻击和网络威胁,那么,服务器硬防通常都会应用在哪些场景当中呢? 硬防服务器中一般会配备入侵检测系统和预防系统&#x…...

unix/linux,sudo,其发展历程详细时间线、由来、历史背景
sudo 的诞生和演化,本身就是一部 Unix/Linux 系统管理哲学变迁的微缩史。来,让我们拨开时间的迷雾,一同探寻 sudo 那波澜壮阔(也颇为实用主义)的发展历程。 历史背景:su的时代与困境 ( 20 世纪 70 年代 - 80 年代初) 在 sudo 出现之前,Unix 系统管理员和需要特权操作的…...
:邮件营销与用户参与度的关键指标优化指南)
精益数据分析(97/126):邮件营销与用户参与度的关键指标优化指南
精益数据分析(97/126):邮件营销与用户参与度的关键指标优化指南 在数字化营销时代,邮件列表效度、用户参与度和网站性能等指标往往决定着创业公司的增长成败。今天,我们将深入解析邮件打开率、网站可用性、页面参与时…...
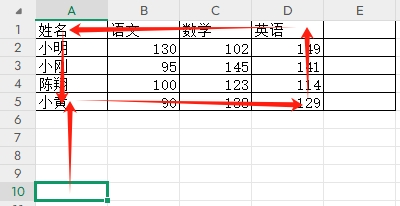
3-11单元格区域边界定位(End属性)学习笔记
返回一个Range 对象,只读。该对象代表包含源区域的区域上端下端左端右端的最后一个单元格。等同于按键 End 向上键(End(xlUp))、End向下键(End(xlDown))、End向左键(End(xlToLeft)End向右键(End(xlToRight)) 注意:它移动的位置必须是相连的有内容的单元格…...
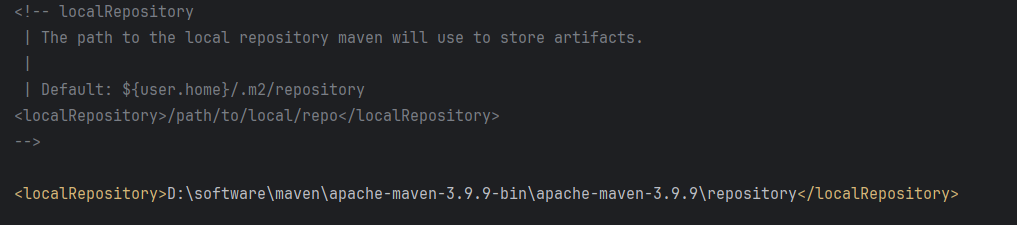
Maven 概述、安装、配置、仓库、私服详解
目录 1、Maven 概述 1.1 Maven 的定义 1.2 Maven 解决的问题 1.3 Maven 的核心特性与优势 2、Maven 安装 2.1 下载 Maven 2.2 安装配置 Maven 2.3 测试安装 2.4 修改 Maven 本地仓库的默认路径 3、Maven 配置 3.1 配置本地仓库 3.2 配置 JDK 3.3 IDEA 配置本地 Ma…...
