网络协议分析-http/https/tcp/udp
文章目录
- TCP三次握手/TCP三次挥手
- TCP三次握手
- TCP四次挥手
- 完整报文
- 实例代码
- HttpSampleClient
- HttpSampleServer
- HttpsSampleClient
- HttpsSampleServer
- TcpSampleClient
- TcpSampleServer
- UdpSampleClient
- UdpSampleSever
- 资料
TCP三次握手/TCP三次挥手
“三次握手”的目的是“为了防止已失效的连接请求报文段突然又传送到了服务端,因而产生 错误”。主要目的防止 server 端一直等待,浪费资源。换句话说,即是为了保证服务端能收 接受到客户端的信息并能做出正确的应答而进行前两次(第一次和第二次)握手,为了保证客 户端能够接收到服务端的信息并能做出正确的应答而进行后两次(第二次和第三次)握手。
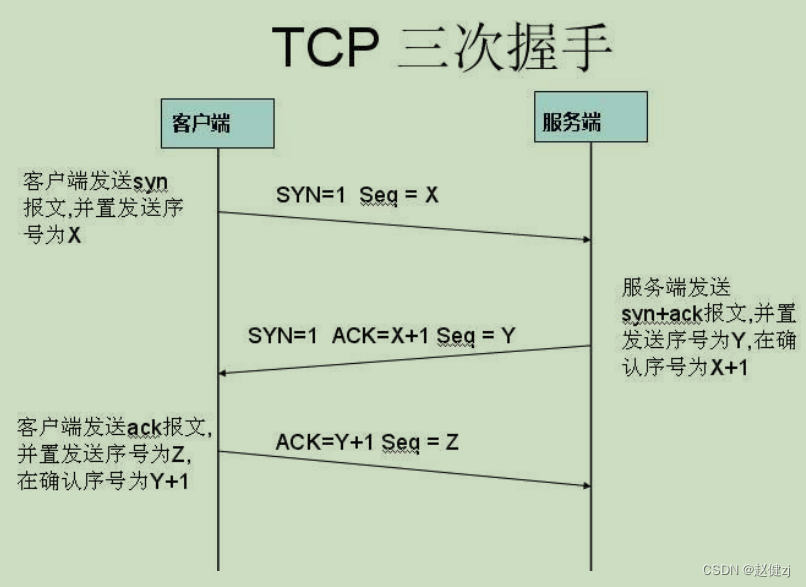
“四次挥手”原因是因为 tcp 是全双工模式,接收到 FIN 时意味将没有数据再发来,但是还是 可以继续发送数据。
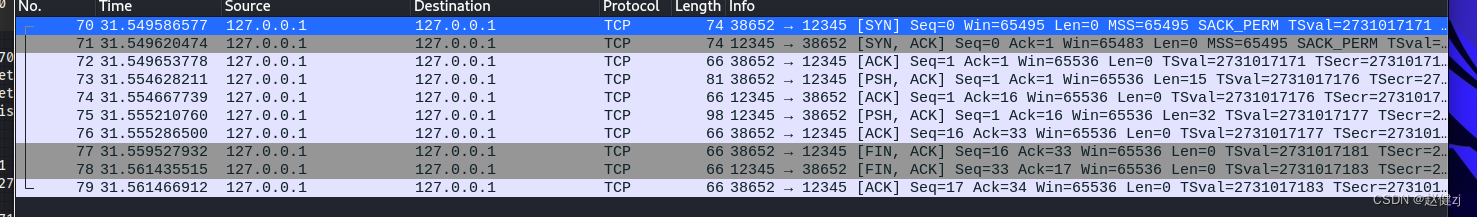
TCP三次握手
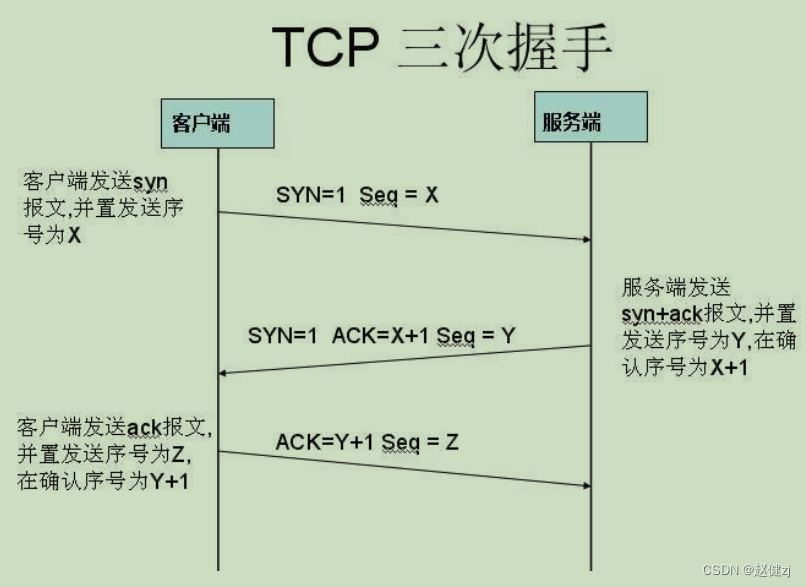
TCP四次挥手
完整报文
# 三次握手:SYN=1 Seq=0
No. Time Source Destination Protocol Length Info50 7.055660280 127.0.0.1 127.0.0.1 TCP 74 44156 → 12345 [SYN] Seq=0 Win=65495 Len=0 MSS=65495 SACK_PERM TSval=2731439096 TSecr=0 WS=128Frame 50: 74 bytes on wire (592 bits), 74 bytes captured (592 bits) on interface lo, id 0Section number: 1Interface id: 0 (lo)Encapsulation type: Ethernet (1)Arrival Time: Aug 29, 2023 08:26:32.312489778 EDT[Time shift for this packet: 0.000000000 seconds]Epoch Time: 1693311992.312489778 seconds[Time delta from previous captured frame: 0.004110298 seconds][Time delta from previous displayed frame: 0.000000000 seconds][Time since reference or first frame: 7.055660280 seconds]Frame Number: 50Frame Length: 74 bytes (592 bits)Capture Length: 74 bytes (592 bits)[Frame is marked: False][Frame is ignored: False][Protocols in frame: eth:ethertype:ip:tcp][Coloring Rule Name: TCP SYN/FIN][Coloring Rule String: tcp.flags & 0x02 || tcp.flags.fin == 1]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 44156, Dst Port: 12345, Seq: 0, Len: 0# 三次握手:SYN1 ACK=1 Seq=0
No. Time Source Destination Protocol Length Info51 7.055692471 127.0.0.1 127.0.0.1 TCP 74 12345 → 44156 [SYN, ACK] Seq=0 Ack=1 Win=65483 Len=0 MSS=65495 SACK_PERM TSval=2731439096 TSecr=2731439096 WS=128Frame 51: 74 bytes on wire (592 bits), 74 bytes captured (592 bits) on interface lo, id 0Section number: 1Interface id: 0 (lo)Encapsulation type: Ethernet (1)Arrival Time: Aug 29, 2023 08:26:32.312521969 EDT[Time shift for this packet: 0.000000000 seconds]Epoch Time: 1693311992.312521969 seconds[Time delta from previous captured frame: 0.000032191 seconds][Time delta from previous displayed frame: 0.000032191 seconds][Time since reference or first frame: 7.055692471 seconds]Frame Number: 51Frame Length: 74 bytes (592 bits)Capture Length: 74 bytes (592 bits)[Frame is marked: False][Frame is ignored: False][Protocols in frame: eth:ethertype:ip:tcp][Coloring Rule Name: TCP SYN/FIN][Coloring Rule String: tcp.flags & 0x02 || tcp.flags.fin == 1]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 12345, Dst Port: 44156, Seq: 0, Ack: 1, Len: 0# 三次握手:Ack=1 Seq=1
No. Time Source Destination Protocol Length Info52 7.055725041 127.0.0.1 127.0.0.1 TCP 66 44156 → 12345 [ACK] Seq=1 Ack=1 Win=65536 Len=0 TSval=2731439096 TSecr=2731439096Frame 52: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0Section number: 1Interface id: 0 (lo)Encapsulation type: Ethernet (1)Arrival Time: Aug 29, 2023 08:26:32.312554539 EDT[Time shift for this packet: 0.000000000 seconds]Epoch Time: 1693311992.312554539 seconds[Time delta from previous captured frame: 0.000032570 seconds][Time delta from previous displayed frame: 0.000032570 seconds][Time since reference or first frame: 7.055725041 seconds]Frame Number: 52Frame Length: 66 bytes (528 bits)Capture Length: 66 bytes (528 bits)[Frame is marked: False][Frame is ignored: False][Protocols in frame: eth:ethertype:ip:tcp][Coloring Rule Name: TCP][Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 44156, Dst Port: 12345, Seq: 1, Ack: 1, Len: 0# 客户端发送消息 Hello, server!.
No. Time Source Destination Protocol Length Info53 7.057834891 127.0.0.1 127.0.0.1 TCP 81 44156 → 12345 [PSH, ACK] Seq=1 Ack=1 Win=65536 Len=15 TSval=2731439098 TSecr=2731439096Frame 53: 81 bytes on wire (648 bits), 81 bytes captured (648 bits) on interface lo, id 0Section number: 1Interface id: 0 (lo)Encapsulation type: Ethernet (1)Arrival Time: Aug 29, 2023 08:26:32.314664389 EDT[Time shift for this packet: 0.000000000 seconds]Epoch Time: 1693311992.314664389 seconds[Time delta from previous captured frame: 0.002109850 seconds][Time delta from previous displayed frame: 0.002109850 seconds][Time since reference or first frame: 7.057834891 seconds]Frame Number: 53Frame Length: 81 bytes (648 bits)Capture Length: 81 bytes (648 bits)[Frame is marked: False][Frame is ignored: False][Protocols in frame: eth:ethertype:ip:tcp:data][Coloring Rule Name: TCP][Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 44156, Dst Port: 12345, Seq: 1, Ack: 1, Len: 15
Data (15 bytes)0000 48 65 6c 6c 6f 2c 20 73 65 72 76 65 72 21 0a Hello, server!.# 服务端应答
No. Time Source Destination Protocol Length Info54 7.057859991 127.0.0.1 127.0.0.1 TCP 66 12345 → 44156 [ACK] Seq=1 Ack=16 Win=65536 Len=0 TSval=2731439098 TSecr=2731439098Frame 54: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0Section number: 1Interface id: 0 (lo)Encapsulation type: Ethernet (1)Arrival Time: Aug 29, 2023 08:26:32.314689489 EDT[Time shift for this packet: 0.000000000 seconds]Epoch Time: 1693311992.314689489 seconds[Time delta from previous captured frame: 0.000025100 seconds][Time delta from previous displayed frame: 0.000025100 seconds][Time since reference or first frame: 7.057859991 seconds]Frame Number: 54Frame Length: 66 bytes (528 bits)Capture Length: 66 bytes (528 bits)[Frame is marked: False][Frame is ignored: False][Protocols in frame: eth:ethertype:ip:tcp][Coloring Rule Name: TCP][Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 12345, Dst Port: 44156, Seq: 1, Ack: 16, Len: 0# 服务端发送消息 Server received: Hello, server!.
No. Time Source Destination Protocol Length Info55 7.059237157 127.0.0.1 127.0.0.1 TCP 98 12345 → 44156 [PSH, ACK] Seq=1 Ack=16 Win=65536 Len=32 TSval=2731439100 TSecr=2731439098Frame 55: 98 bytes on wire (784 bits), 98 bytes captured (784 bits) on interface lo, id 0Section number: 1Interface id: 0 (lo)Encapsulation type: Ethernet (1)Arrival Time: Aug 29, 2023 08:26:32.316066655 EDT[Time shift for this packet: 0.000000000 seconds]Epoch Time: 1693311992.316066655 seconds[Time delta from previous captured frame: 0.001377166 seconds][Time delta from previous displayed frame: 0.001377166 seconds][Time since reference or first frame: 7.059237157 seconds]Frame Number: 55Frame Length: 98 bytes (784 bits)Capture Length: 98 bytes (784 bits)[Frame is marked: False][Frame is ignored: False][Protocols in frame: eth:ethertype:ip:tcp:data][Coloring Rule Name: TCP][Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 12345, Dst Port: 44156, Seq: 1, Ack: 16, Len: 32
Data (32 bytes)0000 53 65 72 76 65 72 20 72 65 63 65 69 76 65 64 3a Server received:
0010 20 48 65 6c 6c 6f 2c 20 73 65 72 76 65 72 21 0a Hello, server!.# 客户端还给了一个回应
No. Time Source Destination Protocol Length Info56 7.059273656 127.0.0.1 127.0.0.1 TCP 66 44156 → 12345 [ACK] Seq=16 Ack=33 Win=65536 Len=0 TSval=2731439100 TSecr=2731439100Frame 56: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0Section number: 1Interface id: 0 (lo)Encapsulation type: Ethernet (1)Arrival Time: Aug 29, 2023 08:26:32.316103154 EDT[Time shift for this packet: 0.000000000 seconds]Epoch Time: 1693311992.316103154 seconds[Time delta from previous captured frame: 0.000036499 seconds][Time delta from previous displayed frame: 0.000036499 seconds][Time since reference or first frame: 7.059273656 seconds]Frame Number: 56Frame Length: 66 bytes (528 bits)Capture Length: 66 bytes (528 bits)[Frame is marked: False][Frame is ignored: False][Protocols in frame: eth:ethertype:ip:tcp][Coloring Rule Name: TCP][Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 44156, Dst Port: 12345, Seq: 16, Ack: 33, Len: 0# 四次挥手 1 FIN=1 Ack=33 Seq=16
No. Time Source Destination Protocol Length Info57 7.062253079 127.0.0.1 127.0.0.1 TCP 66 44156 → 12345 [FIN, ACK] Seq=16 Ack=33 Win=65536 Len=0 TSval=2731439103 TSecr=2731439100Frame 57: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0Section number: 1Interface id: 0 (lo)Encapsulation type: Ethernet (1)Arrival Time: Aug 29, 2023 08:26:32.319082577 EDT[Time shift for this packet: 0.000000000 seconds]Epoch Time: 1693311992.319082577 seconds[Time delta from previous captured frame: 0.002979423 seconds][Time delta from previous displayed frame: 0.002979423 seconds][Time since reference or first frame: 7.062253079 seconds]Frame Number: 57Frame Length: 66 bytes (528 bits)Capture Length: 66 bytes (528 bits)[Frame is marked: False][Frame is ignored: False][Protocols in frame: eth:ethertype:ip:tcp][Coloring Rule Name: TCP SYN/FIN][Coloring Rule String: tcp.flags & 0x02 || tcp.flags.fin == 1]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 44156, Dst Port: 12345, Seq: 16, Ack: 33, Len: 0# 四次挥手 2 ACK=17 Seq=33
No. Time Source Destination Protocol Length Info58 7.110165407 127.0.0.1 127.0.0.1 TCP 66 12345 → 44156 [ACK] Seq=33 Ack=17 Win=65536 Len=0 TSval=2731439151 TSecr=2731439103Frame 58: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0Section number: 1Interface id: 0 (lo)Encapsulation type: Ethernet (1)Arrival Time: Aug 29, 2023 08:26:32.366994905 EDT[Time shift for this packet: 0.000000000 seconds]Epoch Time: 1693311992.366994905 seconds[Time delta from previous captured frame: 0.047912328 seconds][Time delta from previous displayed frame: 0.047912328 seconds][Time since reference or first frame: 7.110165407 seconds]Frame Number: 58Frame Length: 66 bytes (528 bits)Capture Length: 66 bytes (528 bits)[Frame is marked: False][Frame is ignored: False][Protocols in frame: eth:ethertype:ip:tcp][Coloring Rule Name: TCP][Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 12345, Dst Port: 44156, Seq: 33, Ack: 17, Len: 0# 四次挥手: 3 Fin=1 Ack=17 Seq=33
No. Time Source Destination Protocol Length Info61 7.390471256 127.0.0.1 127.0.0.1 TCP 66 12345 → 44156 [FIN, ACK] Seq=33 Ack=17 Win=65536 Len=0 TSval=2731439431 TSecr=2731439103Frame 61: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0Section number: 1Interface id: 0 (lo)Encapsulation type: Ethernet (1)Arrival Time: Aug 29, 2023 08:26:32.647300754 EDT[Time shift for this packet: 0.000000000 seconds]Epoch Time: 1693311992.647300754 seconds[Time delta from previous captured frame: 0.000234452 seconds][Time delta from previous displayed frame: 0.280305849 seconds][Time since reference or first frame: 7.390471256 seconds]Frame Number: 61Frame Length: 66 bytes (528 bits)Capture Length: 66 bytes (528 bits)[Frame is marked: False][Frame is ignored: False][Protocols in frame: eth:ethertype:ip:tcp][Coloring Rule Name: TCP SYN/FIN][Coloring Rule String: tcp.flags & 0x02 || tcp.flags.fin == 1]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 12345, Dst Port: 44156, Seq: 33, Ack: 17, Len: 0# 四次挥手 4 Ack=34 Seq=17
No. Time Source Destination Protocol Length Info62 7.390499061 127.0.0.1 127.0.0.1 TCP 66 44156 → 12345 [ACK] Seq=17 Ack=34 Win=65536 Len=0 TSval=2731439431 TSecr=2731439431Frame 62: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface lo, id 0Section number: 1Interface id: 0 (lo)Encapsulation type: Ethernet (1)Arrival Time: Aug 29, 2023 08:26:32.647328559 EDT[Time shift for this packet: 0.000000000 seconds]Epoch Time: 1693311992.647328559 seconds[Time delta from previous captured frame: 0.000027805 seconds][Time delta from previous displayed frame: 0.000027805 seconds][Time since reference or first frame: 7.390499061 seconds]Frame Number: 62Frame Length: 66 bytes (528 bits)Capture Length: 66 bytes (528 bits)[Frame is marked: False][Frame is ignored: False][Protocols in frame: eth:ethertype:ip:tcp][Coloring Rule Name: TCP][Coloring Rule String: tcp]
Ethernet II, Src: 00:00:00_00:00:00 (00:00:00:00:00:00), Dst: 00:00:00_00:00:00 (00:00:00:00:00:00)
Internet Protocol Version 4, Src: 127.0.0.1, Dst: 127.0.0.1
Transmission Control Protocol, Src Port: 44156, Dst Port: 12345, Seq: 17, Ack: 34, Len: 0实例代码
HttpSampleClient
import java.io.BufferedReader;
import java.io.InputStreamReader;
import java.net.HttpURLConnection;
import java.net.URL;public class HttpSampleClient {public static void main(String[] args) {try {URL url = new URL("http://localhost:8080");HttpURLConnection connection = (HttpURLConnection) url.openConnection();connection.setRequestMethod("GET");int responseCode = connection.getResponseCode();System.out.println("Response Code:" + responseCode);// read contentBufferedReader reader = new BufferedReader(new InputStreamReader(connection.getInputStream()));String line;StringBuilder response = new StringBuilder();while ((line = reader.readLine()) != null) {response.append(line);}reader.close();System.out.println("Response Body: " + response);connection.disconnect();} catch (Exception e) {e.printStackTrace();}}
}HttpSampleServer
import com.sun.net.httpserver.HttpExchange;
import com.sun.net.httpserver.HttpHandler;
import com.sun.net.httpserver.HttpServer;import java.io.IOException;
import java.io.OutputStream;
import java.net.InetSocketAddress;public class HttpSampleServer {public static void main(String[] args) {try {// create http server to bind 8080HttpServer server = HttpServer.create(new InetSocketAddress("127.0.0.1", 8080), 0);// bind pathserver.createContext("/", new MyHandler());server.start();System.out.println("Http Sever started on port 8080");} catch (Exception e) {e.printStackTrace();}}static class MyHandler implements HttpHandler {// 设置响应头c@Overridepublic void handle(HttpExchange exchange) throws IOException {String response = "Hello from the local HTTP server!";exchange.sendResponseHeaders(200, response.getBytes().length);// 获取输出流并写入响应内容OutputStream os = exchange.getResponseBody();os.write(response.getBytes());os.close();}}
}HttpsSampleClient
import javax.net.ssl.*;
import java.io.BufferedReader;
import java.io.InputStreamReader;
import java.io.PrintWriter;public class HttpsSampleClient {public static void main(String[] args) {try {// Create and configure the SSL contextSSLContext sslContext = SSLContext.getInstance("TLS");sslContext.init(null, new TrustManager[]{new X509TrustManager() {public java.security.cert.X509Certificate[] getAcceptedIssuers() {return null;}public void checkClientTrusted(java.security.cert.X509Certificate[] certs, String authType) {}public void checkServerTrusted(java.security.cert.X509Certificate[] certs, String authType) {}}}, new java.security.SecureRandom());// Create an SSL socketSSLSocketFactory sslSocketFactory = sslContext.getSocketFactory();SSLSocket socket = (SSLSocket) sslSocketFactory.createSocket("localhost", 12345);// Get input and output streams for secure communicationBufferedReader reader = new BufferedReader(new InputStreamReader(socket.getInputStream()));PrintWriter writer = new PrintWriter(socket.getOutputStream(), true); // autoFlush// Send a message to the serverString message = "Hello, server!";writer.println(message);// Read response from the serverString serverResponse = reader.readLine();System.out.println("Server response: " + serverResponse);// Close resourcesreader.close();writer.close();socket.close();} catch (Exception e) {e.printStackTrace();}}
}HttpsSampleServer
import javax.net.ssl.*;
import java.io.BufferedReader;
import java.io.FileInputStream;
import java.io.InputStreamReader;
import java.io.PrintWriter;
import java.security.KeyStore;public class HttpsSampleServer {public static void main(String[] args) {String keystorePath = "./keystore.jks";char[] keystorePassword = "flannery".toCharArray();try {// Load the keystore containing the server's SSL certificateKeyStore keystore = KeyStore.getInstance("JKS");keystore.load(new FileInputStream(keystorePath), keystorePassword);// Create and configure the SSL contextKeyManagerFactory kmf = KeyManagerFactory.getInstance("SunX509");kmf.init(keystore, keystorePassword);SSLContext sslContext = SSLContext.getInstance("TLS");sslContext.init(kmf.getKeyManagers(), null, null);// Create an SSL server socketSSLServerSocketFactory sslServerSocketFactory = sslContext.getServerSocketFactory();SSLServerSocket serverSocket = (SSLServerSocket) sslServerSocketFactory.createServerSocket(12345);System.out.println("Server listening on port 12345...");// Wait for a client to connectSSLSocket clientSocket = (SSLSocket) serverSocket.accept();System.out.println("Client connected: " + clientSocket.getInetAddress().getHostAddress());// Get input and output streams for secure communicationBufferedReader reader = new BufferedReader(new InputStreamReader(clientSocket.getInputStream()));PrintWriter writer = new PrintWriter(clientSocket.getOutputStream(), true); // autoFlush// Read data from client and respondString clientMessage;while ((clientMessage = reader.readLine()) != null) {System.out.println("Received from client: " + clientMessage);writer.println("Server received: " + clientMessage);}// Close resourcesreader.close();writer.close();clientSocket.close();serverSocket.close();} catch (Exception e) {e.printStackTrace();}}
}TcpSampleClient
import java.io.*;
import java.net.Socket;public class TcpSampleClient {public static void main(String[] args) {try {// Create a socket to connect to the serverSocket socket = new Socket("localhost", 12345);// Get input and output streams for the socketInputStream inputStream = socket.getInputStream();OutputStream outputStream = socket.getOutputStream();// Create readers and writers for easier communicationBufferedReader reader = new BufferedReader(new InputStreamReader(inputStream));PrintWriter writer = new PrintWriter(outputStream, true); // autoFlush// Send a message to the serverString message = "Hello, server!";writer.println(message);// Read response from the serverString serverResponse = reader.readLine();System.out.println("Server response: " + serverResponse);// Close resourcesreader.close();writer.close();socket.close();} catch (IOException e) {e.printStackTrace();}}
}TcpSampleServer
import java.io.*;
import java.net.ServerSocket;
import java.net.Socket;
public class TcpSampleServer {public static void main(String[] args) {extracted();}private static void extracted() {try {// Create a server socketServerSocket serverSocket = new ServerSocket(12345);System.out.println("Server listening on port 12345...");// Wait for a client to connectSocket clientSocket = serverSocket.accept();System.out.println("Client connected: " + clientSocket.getInetAddress().getHostAddress());// Get input and output streams for the socketInputStream inputStream = clientSocket.getInputStream();OutputStream outputStream = clientSocket.getOutputStream();// Create readers and writers for easier communicationBufferedReader reader = new BufferedReader(new InputStreamReader(inputStream));PrintWriter writer = new PrintWriter(outputStream, true); // autoFlush// Read data from client and respondString clientMessage;while ((clientMessage = reader.readLine()) != null) {System.out.println("Received from client: " + clientMessage);writer.println("Server received: " + clientMessage);}// Close resources//reader.close();//writer.close();//clientSocket.close();//serverSocket.close();} catch (IOException e) {e.printStackTrace();}}}UdpSampleClient
import java.io.IOException;
import java.net.DatagramPacket;
import java.net.DatagramSocket;
import java.net.InetAddress;public class UdpSampleClient {public static void main(String[] args) {try {DatagramSocket clientSocket = new DatagramSocket();String message = "Hello, server!";byte[] sendData = message.getBytes();InetAddress serverAddress = InetAddress.getByName("localhost");int serverPort = 12345;DatagramPacket sendPacket = new DatagramPacket(sendData, sendData.length, serverAddress, serverPort);clientSocket.send(sendPacket);byte[] receiveData = new byte[1024];DatagramPacket receivePacket = new DatagramPacket(receiveData, receiveData.length);clientSocket.receive(receivePacket);String serverResponse = new String(receivePacket.getData(), 0, receivePacket.getLength());System.out.println("Server response: " + serverResponse);clientSocket.close();} catch (IOException e) {e.printStackTrace();}}}UdpSampleSever
import java.io.IOException;
import java.net.DatagramPacket;
import java.net.DatagramSocket;
import java.net.InetAddress;public class UdpSampleSever {public static void main(String[] args) {try {DatagramSocket serverSocket = new DatagramSocket(12345);System.out.println("Server listening on port 12345...");byte[] receiveData = new byte[1024];while (true) {DatagramPacket receivePacket = new DatagramPacket(receiveData, receiveData.length);serverSocket.receive(receivePacket);String clientMessage = new String(receivePacket.getData(), 0, receivePacket.getLength());System.out.println("Received from client: " + clientMessage);InetAddress clientAddress = receivePacket.getAddress();int clientPort = receivePacket.getPort();String serverResponse = "Server received: " + clientMessage;byte[] sendData = serverResponse.getBytes();DatagramPacket sendPacket = new DatagramPacket(sendData, sendData.length, clientAddress, clientPort);serverSocket.send(sendPacket);}} catch (IOException e) {e.printStackTrace();}}
}资料
超详细的wireshark抓包使用教程
jks证书文件的生成步骤
如何使用wireshark抓取HTTPS数据包?
wireshark抓包分析HTTPS
Burp Suite的基本介绍及使用
渗透测试工具Burp Suite详解
vmware ctrl键粘滞的问题
wireshark过滤规则
Burp Suite HTTPS详解
相关文章:

网络协议分析-http/https/tcp/udp
文章目录 TCP三次握手/TCP三次挥手TCP三次握手TCP四次挥手完整报文 实例代码HttpSampleClientHttpSampleServerHttpsSampleClientHttpsSampleServerTcpSampleClientTcpSampleServerUdpSampleClientUdpSampleSever 资料 TCP三次握手/TCP三次挥手 “三次握手”的目的是“为了防止…...

基于aarch64分析kernel源码 四:printk 内核打印
一、参考 Message logging with printk — The Linux Kernel documentation 如何获得正确的printk格式占位符 — The Linux Kernel documentation 使用printk记录消息 — The Linux Kernel documentation printk 内核打印 – 人人都懂物联网 (getiot.tech) 内核printk原理…...

机器人中的数值优化(六)—— 线搜索最速下降法
本系列文章主要是我在学习《数值优化》过程中的一些笔记和相关思考,主要的学习资料是深蓝学院的课程《机器人中的数值优化》和高立编著的《数值最优化方法》等,本系列文章篇数较多,不定期更新,上半部分介绍无约束优化,…...

postman调试注意事项
Postman是一个强大的API调试工具,它可以帮助开发人员测试和调试API端点,以确保它们按预期工作。在使用Postman进行接口调试时,以下是一些注意事项和可能出现的问题,以及如何解决这些问题。 确保请求参数正确 在测试API接口时&am…...

【C#】泛型
【C#】泛型 泛型是什么 泛型是将类型作为参数传递给类、结构、接口和方法,这些参数相当于类型占位符。当我们定义类或方法时使用占位符代替变量类型,真正使用时再具体指定数据类型,以此来达到代码重用目的。 泛型特点 提高代码重用性一定…...

CLIP:连接文本-图像
Contrastive Language-Image Pre-Training CLIP的主要目标是通过对比学习,学习匹配图像和文本。CLIP最主要的作用:可以将文本和图像表征映射到同一个表示空间 这是通过训练模型来预测哪个图像属于给定的文本,反之亦然。在训练过程中&#…...
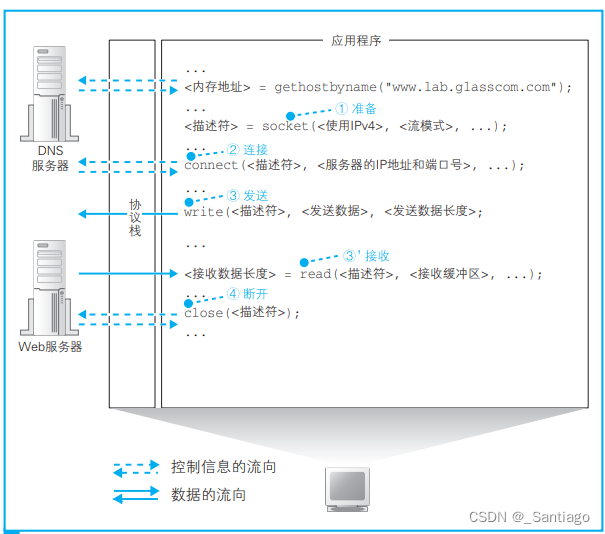
MFC网络编程简单例程
目录 一、关于网络的部分概念1 URL(网址)及URL的解析2 URL的解析3 域名及域名解析3 IP及子网掩码4 什么是Web服务器5 HTTP的基本概念6 Socket库概念7 协议栈8 Socket库收发数据基本步骤 二、基于TCP的网络应用程序三、基于UDP的网络应用程序 一、关于网络的部分概念 1 URL(网址…...
)
云原生简介 (Cloud Native)
云原生(cloud Native) 云原生的概念诞生于10年前,netflix 在 AWS 上的一次演讲中。有趣的是当初没有明确的定义,现在也没有明确的定义,对不同的人来说,有不同的概念。 概念 云原生:是在云上构…...
【SpringBoot系列】 测试框架之@SpringBootTest的使用
SpringBootTest的详细介绍 SpringBootTest 是 Spring Boot 测试框架中的注解,用于标识一个测试类,以指示该类是一个 Spring Boot 应用程序的测试类。它允许你在测试环境中加载整个 Spring Boot 应用程序上下文,测试应用程序的各种组件、服务…...
【数据结构与算法篇】手撕八大排序算法之交换排序
👻内容专栏: 《数据结构与算法篇》 🐨本文概括:常见交换排序包括冒泡排序与快速排序,本篇讲述冒泡排序与快速排序的思想及实现、复杂度分析。 🐼本文作者: 花 蝶 🐸发布时间&#…...
ArcGIS Pro实践技术应用、制图、空间分析、影像分析、三维建模、空间统计分析与建模、python融合
GIS是利用电子计算机及其外部设备,采集、存储、分析和描述整个或部分地球表面与空间信息系统。简单地讲,它是在一定的地域内,将地理空间信息和 一些与该地域地理信息相关的属性信息结合起来,达到对地理和属性信息的综合管理。GIS的…...

uniapp 项目实践总结(一)uniapp 框架知识总结
导语:最近开发了一个基于 uniapp 框架的项目,有一些感触和体会,所以想记录以下一些技术和经验,在这里做一个系列总结,算是对自己做一个交代吧。 目录 简介全局文件全局组件常用 API条件编译插件开发 简介 uniapp 是…...

Oracle查看与修改隐藏参数
Oracle查看与修改隐藏参数 查看隐藏参数修改隐藏参数 查看隐藏参数 查看数据库中所有的隐藏参数: SELECT a.ksppinm "Parameter", b.KSPPSTDF "Default Value",b.ksppstvl "Session Value", c.ksppstvl "Instance Value"…...

基于MQTT协议的物联网网关实现远程数据采集及监控
在数字化时代的浪潮中,工业界正面临着前所未有的变革与机遇。而在这场变革中,基于MQTT协议的物联网网关崭露头角,成为连接工业设备、实现远程数据采集与监控的利器。其中,HiWoo Box作为一款出色的工业边缘网关,引领着这…...

服务内部错误: stderr: bash: docker-compose: 未找到命令
报错描述 1Panel在应用商店安装软件失败,重建或者重启报错"服务内部错误: stderr: bash: docker-compose: 未找到命令" 执行命令"docker-compose --version"结果为"Docker Compose version v2.17.2",说明docker-compose已…...

自然语言处理(六):词的相似性和类比任务
词的相似性和类比任务 在前面的章节中,我们在一个小的数据集上训练了一个word2vec模型,并使用它为一个输入词寻找语义相似的词。实际上,在大型语料库上预先训练的词向量可以应用于下游的自然语言处理任务,为了直观地演示大型语料…...

安防监控视频平台EasyCVR视频汇聚平台定制项目增加AI智能算法详细介绍
安防视频集中存储EasyCVR视频汇聚平台,可支持海量视频的轻量化接入与汇聚管理。平台能提供视频存储磁盘阵列、视频监控直播、视频轮播、视频录像、云存储、回放与检索、智能告警、服务器集群、语音对讲、云台控制、电子地图、平台级联、H.265自动转码等功能。为了便…...

VB个人邮件处理系统设计与实现
简述 当今世界电子邮件已经是网络生活中不可或缺的,相信每个认知网络的人都会有一个或多个自己的电子邮箱,人们通过电子邮件进行通信和交流,许多商家和组织机构也用电子邮件进行各种商业活动和业务联系,毫无疑问,电子邮件已经逐渐开始取代普通的信件,成为为主流的信件交流…...
第一章辩证唯物论,考点七思维导图
逻辑框架 考点七思维导图:...
)
Python入门教程 - 基本函数(四)
目录 一、什么是函数 二、自定义函数并使用它 一、什么是函数 前面我们学习了像input()、print()、type()等等,他们都是函数。这些其实是由Python内部帮我们定义好的。我们直接用就可以了。 关于函数,除了用内部定义好的,我们也可以自己定…...
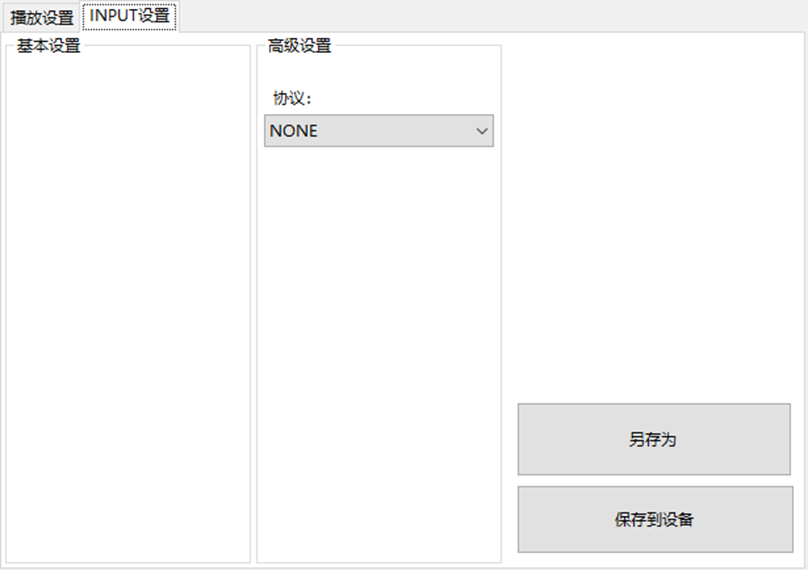
LBE-LEX系列工业语音播放器|预警播报器|喇叭蜂鸣器的上位机配置操作说明
LBE-LEX系列工业语音播放器|预警播报器|喇叭蜂鸣器专为工业环境精心打造,完美适配AGV和无人叉车。同时,集成以太网与语音合成技术,为各类高级系统(如MES、调度系统、库位管理、立库等)提供高效便捷的语音交互体验。 L…...
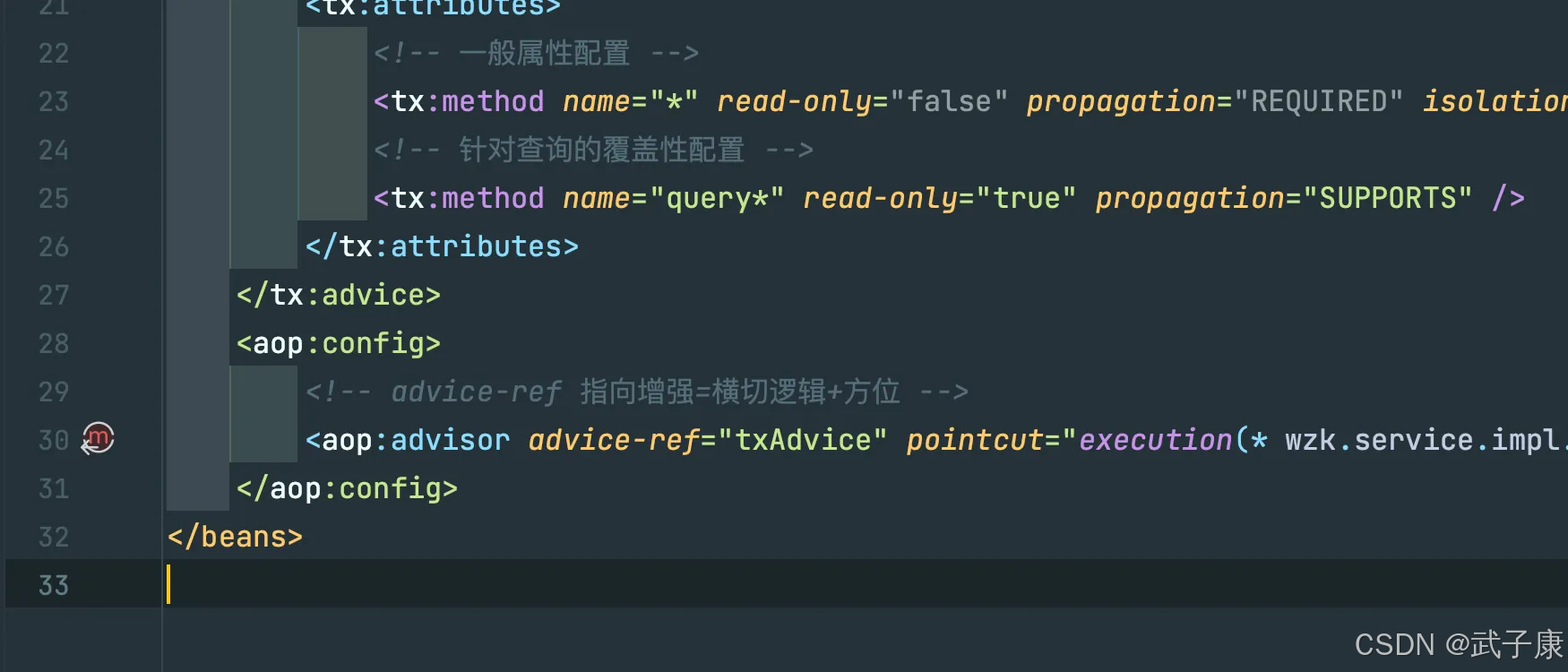
Java-41 深入浅出 Spring - 声明式事务的支持 事务配置 XML模式 XML+注解模式
点一下关注吧!!!非常感谢!!持续更新!!! 🚀 AI篇持续更新中!(长期更新) 目前2025年06月05日更新到: AI炼丹日志-28 - Aud…...
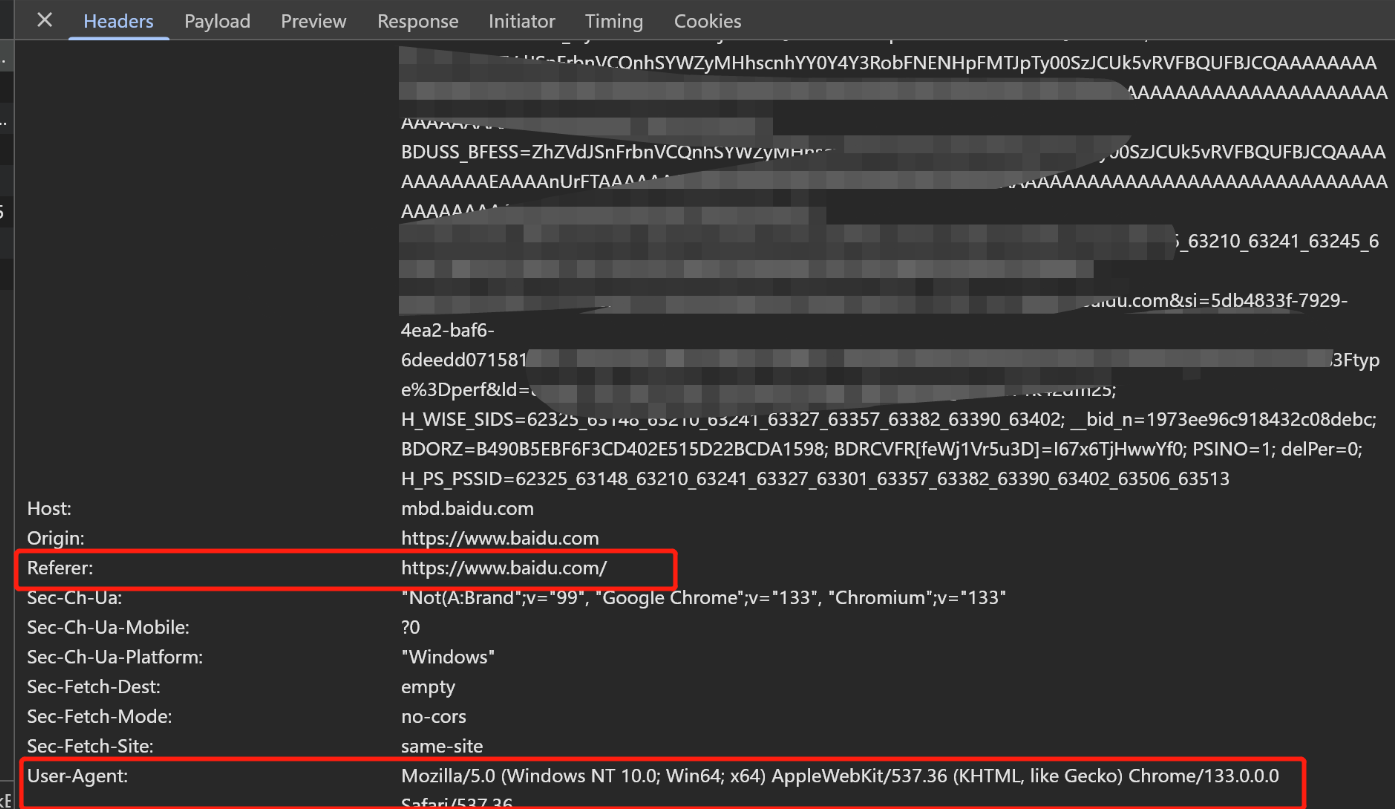
Python爬虫(一):爬虫伪装
一、网站防爬机制概述 在当今互联网环境中,具有一定规模或盈利性质的网站几乎都实施了各种防爬措施。这些措施主要分为两大类: 身份验证机制:直接将未经授权的爬虫阻挡在外反爬技术体系:通过各种技术手段增加爬虫获取数据的难度…...
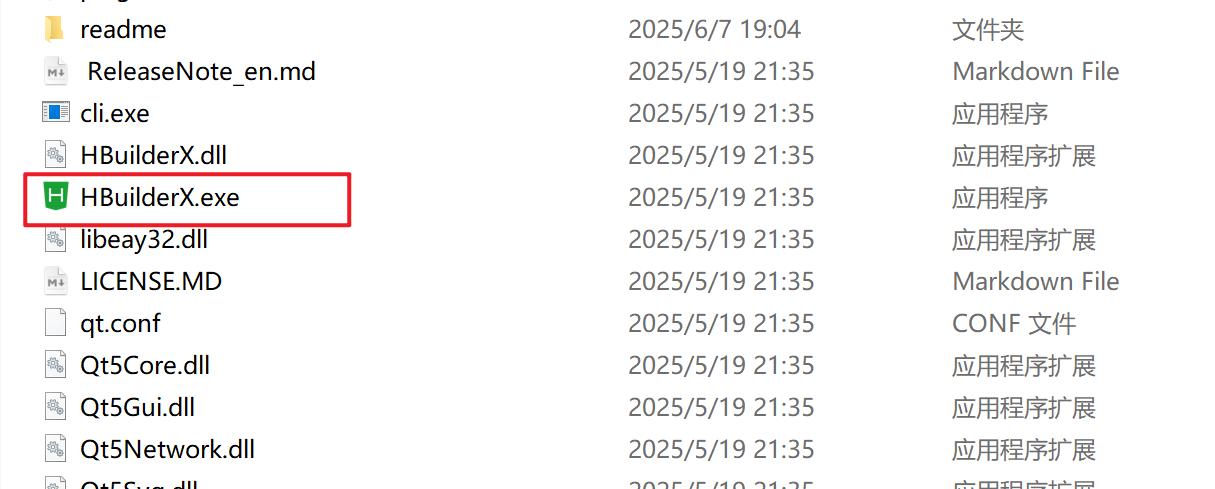
HBuilderX安装(uni-app和小程序开发)
下载HBuilderX 访问官方网站:https://www.dcloud.io/hbuilderx.html 根据您的操作系统选择合适版本: Windows版(推荐下载标准版) Windows系统安装步骤 运行安装程序: 双击下载的.exe安装文件 如果出现安全提示&…...
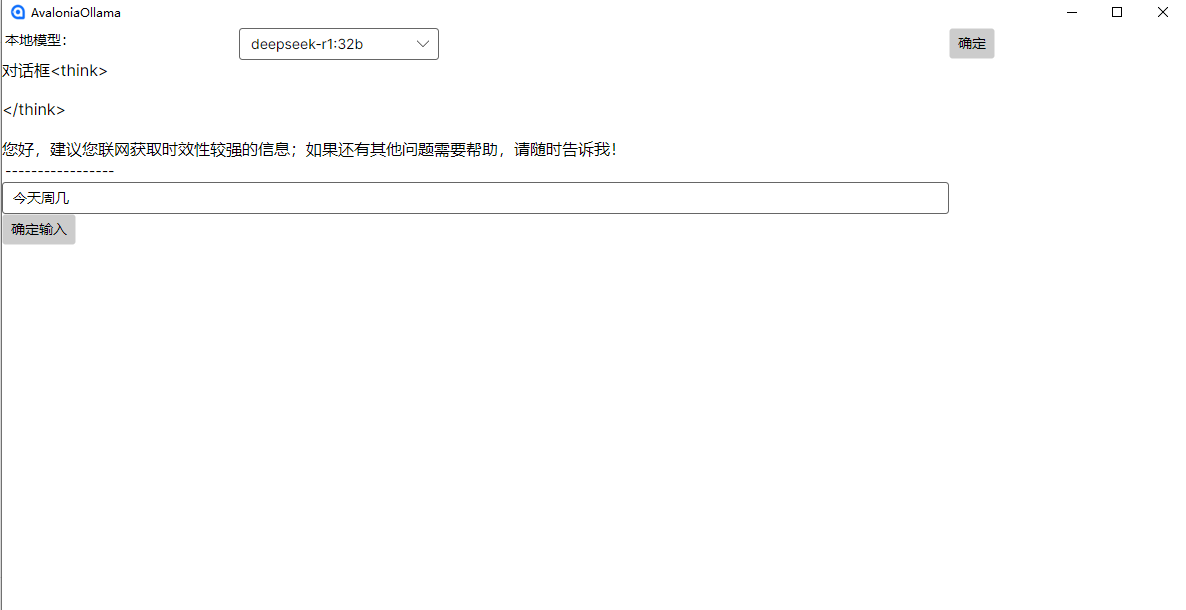
c#开发AI模型对话
AI模型 前面已经介绍了一般AI模型本地部署,直接调用现成的模型数据。这里主要讲述讲接口集成到我们自己的程序中使用方式。 微软提供了ML.NET来开发和使用AI模型,但是目前国内可能使用不多,至少实践例子很少看见。开发训练模型就不介绍了&am…...
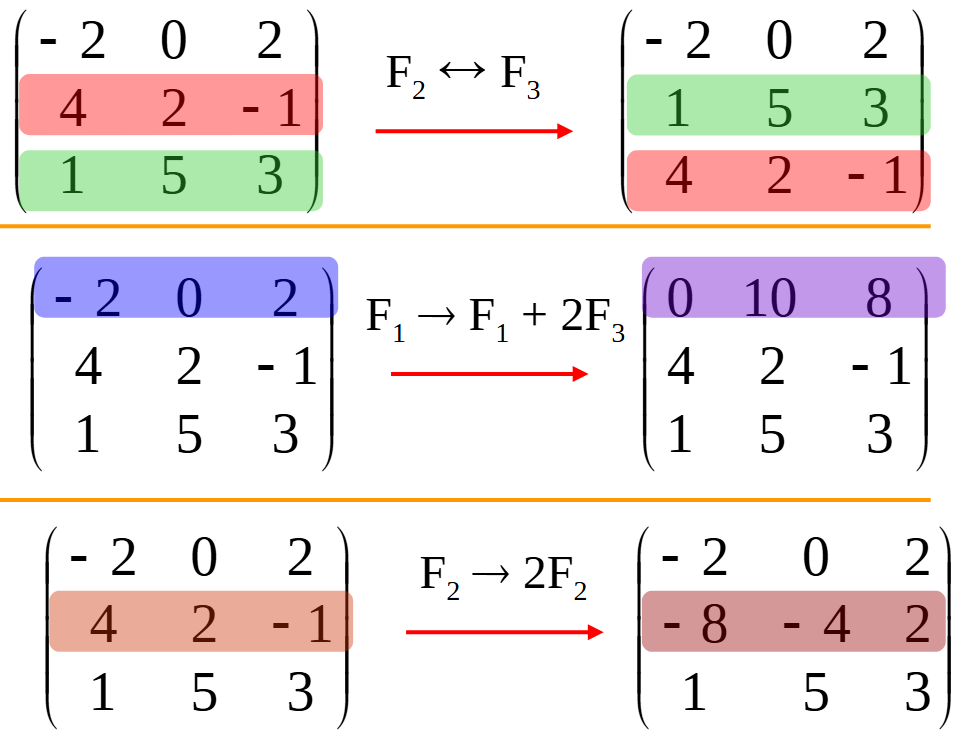
使用 SymPy 进行向量和矩阵的高级操作
在科学计算和工程领域,向量和矩阵操作是解决问题的核心技能之一。Python 的 SymPy 库提供了强大的符号计算功能,能够高效地处理向量和矩阵的各种操作。本文将深入探讨如何使用 SymPy 进行向量和矩阵的创建、合并以及维度拓展等操作,并通过具体…...

Fabric V2.5 通用溯源系统——增加图片上传与下载功能
fabric-trace项目在发布一年后,部署量已突破1000次,为支持更多场景,现新增支持图片信息上链,本文对图片上传、下载功能代码进行梳理,包含智能合约、后端、前端部分。 一、智能合约修改 为了增加图片信息上链溯源,需要对底层数据结构进行修改,在此对智能合约中的农产品数…...
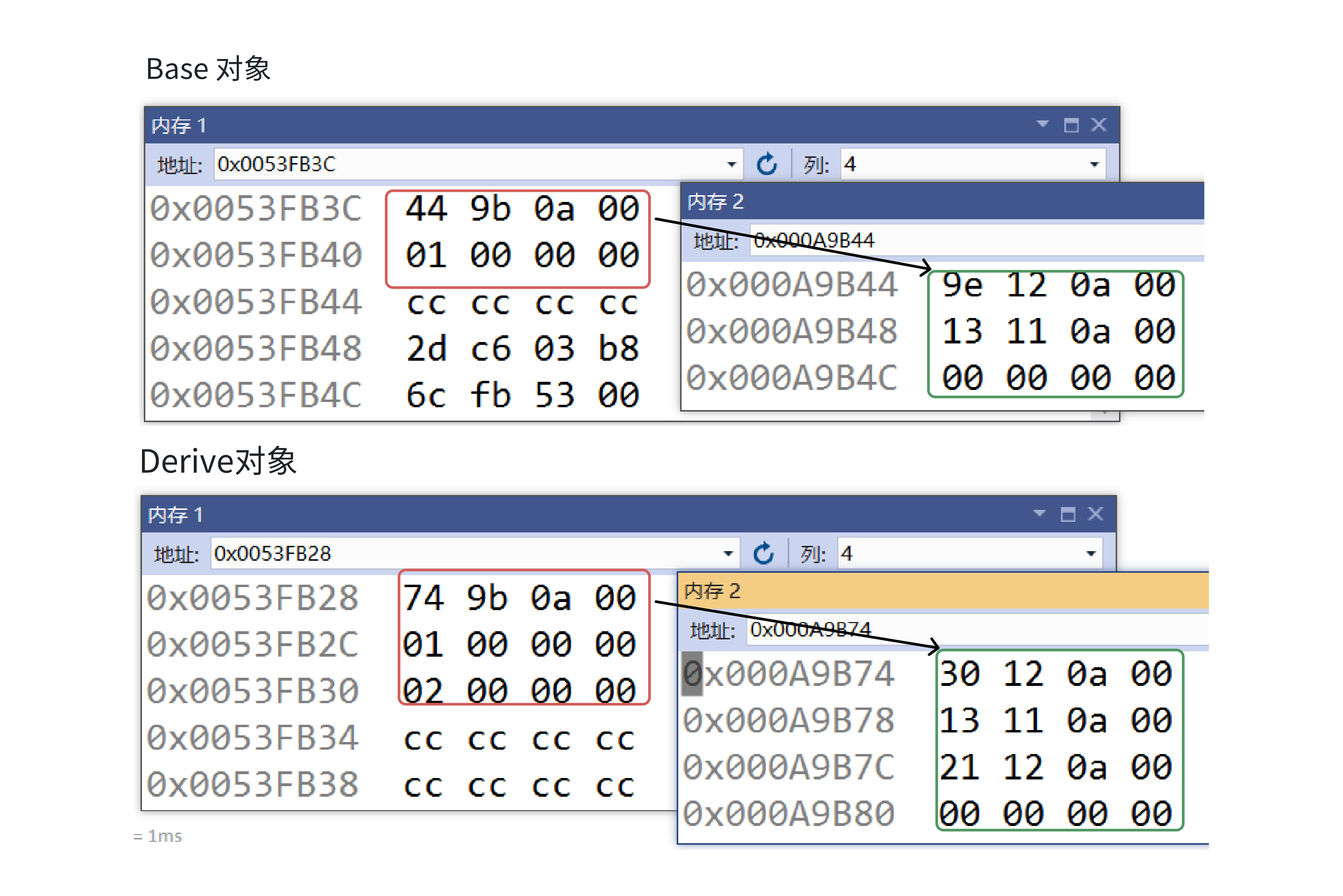
C++:多态机制详解
目录 一. 多态的概念 1.静态多态(编译时多态) 二.动态多态的定义及实现 1.多态的构成条件 2.虚函数 3.虚函数的重写/覆盖 4.虚函数重写的一些其他问题 1).协变 2).析构函数的重写 5.override 和 final关键字 1&#…...
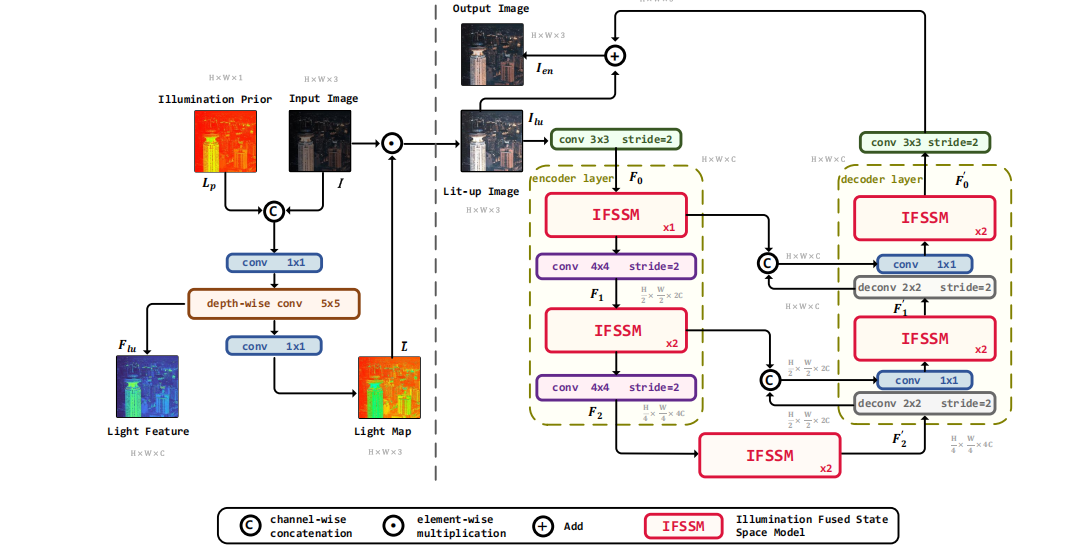
深度学习水论文:mamba+图像增强
🧀当前视觉领域对高效长序列建模需求激增,对Mamba图像增强这方向的研究自然也逐渐火热。原因在于其高效长程建模,以及动态计算优势,在图像质量提升和细节恢复方面有难以替代的作用。 🧀因此短时间内,就有不…...
C++ 设计模式 《小明的奶茶加料风波》
👨🎓 模式名称:装饰器模式(Decorator Pattern) 👦 小明最近上线了校园奶茶配送功能,业务火爆,大家都在加料: 有的同学要加波霸 🟤,有的要加椰果…...
