Tomcat Notes: Web Security, HTTPS In Tomcat
This is a personal study notes of Apache Tomcat. Below are main reference material.
- YouTube Apache Tomcat Full Tutorial,owed by Alpha Brains Courses. https://www.youtube.com/watch?v=rElJIPRw5iM&t=801s
- 1、Overview
- 2、Two Levels Of Web Security
- 2.1、Trace Of A Full Security Example
- 3、Some Security Conceptions
- 3.1、Man-In-The-Middle
- 3.2、 Key Store And Trust Store
- 3.3、Message Digests
- 3.4、Symmetric Encryption And Decryption
- 3.5、Asymmetric Encryption And Decryption
- 4、Process Of HTTPS
1、Overview
This article is about problems in web security, how HTTPS secure sending messages and some basic cryptology algorithm.
I’m not very confident with this article since I never make any practice on those concetions or theorys.
Any advice or correction is welcomed.
2、Two Levels Of Web Security
Web server and web app security covers two distinct but related levels.
Wire-level(transport-level): In this level it encrypts data transmission through all nodes.Users/roles security: User authentication and role authorization. Good news is Tomcat supports ‘Container-managed security’ in which Catalina, rather than a particular web app does this heavy lifting.
HTTPS is a way to secure in this two levels. HTTPS is a way to secure in this level. S of course stands for secure, There a lot of layers atop HTTPS but HTTPS is the most popular and dominant one.
Tomcat uses HTTP by default. We need to turn HTTPS on in TOMCAT_HOME/conf/server.xml. And other operations are also required.
Three problems HTTPS need to solve.
1. The one who sends you messages is who you think it is rather than other one who pretends to be it.
2. The messages are encrypted, even though other people capture the messages but we have the confidence they can't decrypt it.
3. The request(response) recieved by the server(the browser) is exactly same with initially sent by the brower(the server).
Here is the wire-level security and services in Alice-to-Bob messages sending scenario.
-
Peer Authentication (aka mutual chanllenge)
messages #Is it real Bob?Alice <------------->Bob#Is it real Alice? -
Confidentiality (message decryption/encryption)
message encrypted message messageAlice --------->encryption engine------------------>decryption engine--------> Bob -
Integrity:
message messageAlice--------->route------->Bob # does sent messge == recieved message?
2.1、Trace Of A Full Security Example
We are going to explore the details of web security with curl. The curlis used to issue a request over a HTTPSto a deployed web app.
Below is the output of curlissuing a HTTPSrequest.
* About to connect() to localhost port 8443 (#0) # 8443 is the conventional port fo HTTPS in Tomcat
* Trying ::1... connected # while 8080 is for HTTP
* Connected to localhost (::1) port 8443 (#0)
* successfully set certificate verify locations:
* CAfile: none CApath: /etc/ssl/certs #Exchange for certificates
* SSLv3, TLS handshake, Client hello (1):
* SSLv3, TLS handshake, Server hello (2):
* SSLv3, TLS handshake, CERT (11):
* SSLv3, TLS handshake, Server key exchange (12):
* SSLv3, TLS handshake, Server finished (14):
* SSLv3, TLS handshake, Client key exchange (16):
* SSLv3, TLS change cipher, Client hello (1):
* SSLv3, TLS handshake, Finished (20):
* SSLv3, TLS change cipher, Client hello (1):
* SSLv3, TLS handshake, Finished (20): #In handshake, the server and the client need to discuss
* SSL connection using EDH-RSA-DES-CBC3-SHA # which encryption to use and digital certificates.
* Server certificate: ...
* SSL certificate verify result: self signed certificate (18), continuing anyway.
* Server auth using Basic with user 'moe'
# one the SSl and TLS secure the connection, server begins to handle request
> GET /predictions HTTP/1.1
> Authorization: Basic bW9lOk1vZU1vZU1vZQ==
> User-Agent: curl libcurl OpenSSL zlib libidn
> Host: localhost:8443
> Accept: */*
>
< HTTP/1.1 200 OK
< Server: Apache-Coyote/1.1
< Cache-Control: private
< Transfer-Encoding: chunked
...
<
<html>
3、Some Security Conceptions
3.1、Man-In-The-Middle
Man-in-the-middle scenario.
Alice(sender)---------------------->Bob(intended recepient)|| Eve(eavesdropper)
Alice sends messages to Bob and Alice thinks the person she sent messages to is Bob but it is Eve in fact.
Bob thinks he receives messages from Alice but it is Eve in fact.
This is where peer authentication phase come in. It is meant to build trust on the Alice and Bob sides. In other words Alice
sends certificates to Bob to assure Bob that it is really Alice on the other side and Bob do the same thing to Alice to get trust.
3.2、 Key Store And Trust Store
Now let me intrduce more jargon which are key storeand trust store.
Java uses this terminology all over the place and it is also what we are going to use.
They bear directly on the topic of digital certificates.
The key storeis where we keep our digital certificates. So it’s database of our digital certificates. They are just some files.
The trust storeis database of digital certificates that I trust. The trust stroecould be the same with key storeby the way.
3.3、Message Digests
We see this thing before. When we download the Tomcat from Apache official site, we can see sha-1or md5used to verify the integrity, making sure the package we download has exactly same with that in Apache server.
By the way output of the Message Digestcould be encrypted forming a digital signature.
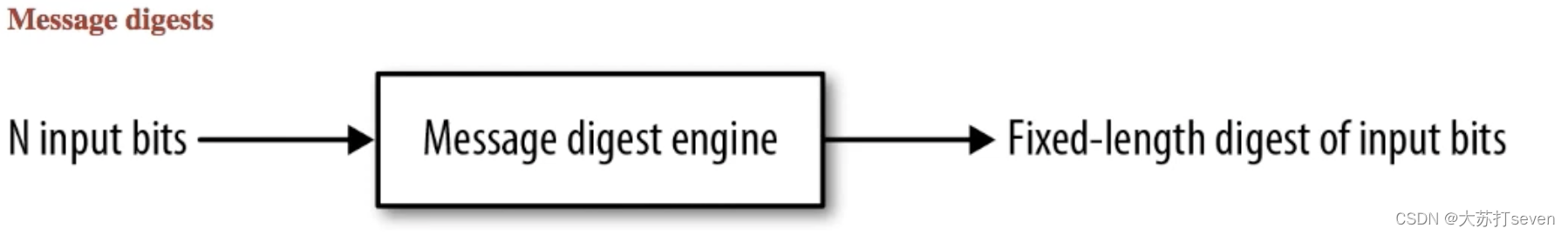
Below is the processes of sending a message, and Message Digestis part of the encryption engine.

3.4、Symmetric Encryption And Decryption
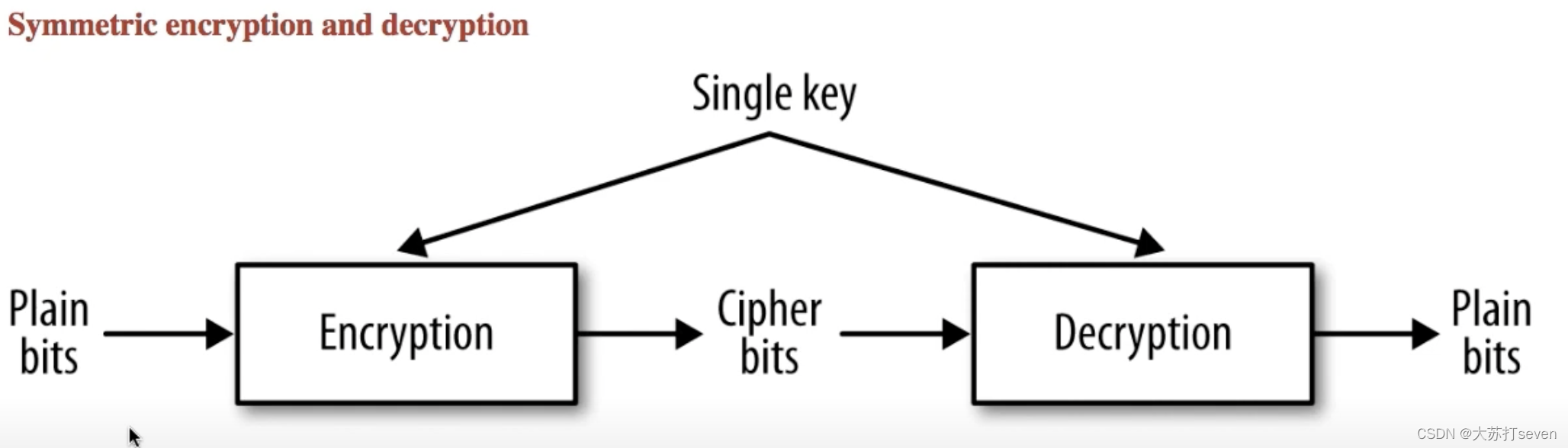
Now we are going to get further about the encryption keyand the decryption key.
In the modal called Symmetric encryption and decryption, encryption keyand decryption keyis the same one.
It brings a new problem, if Alice has the single key, how can she manage to send the single key to Bob safely or vice versa?
That’s sometimes called the key distribution problem.
The upside of this modal is that it’s fast. Roughly speaking it 1000 times faster than Asymmetric encryption and decryption.
3.5、Asymmetric Encryption And Decryption
In this modal, it uses a pair of key, containing a public keyand a private key, to encryption and decryption.
This pair of key is generated by the recipient. The public keyis used to encryption and the encrypted message can be decrypted only with the private key.
The pulic key can be held by anyone just like its name so it basically can be percieved as an indentity, while the private name can only be held by the recipient.
Supposing Alice wants to send a message to Bob.
- Alice firstly get Bob’s
public key. - Alice encrypts message with the
public key. - Bob recieves the encrypted message then decrypts it with it’s private key.
In this way it assure Alice that her messages can be understood only by Bob.
While it’s not perfect, Alice knows who she sent messages to but Bob does’t know where the messages come from.

4、Process Of HTTPS
With the basis of above conceptions we are going to get into how ‘S’ in HTTPSworks.
Three terms play a role in wire-level security ‘peer authentication’ in particular.
-
Key Pair: A pulic key and a private key. Unlike the asymmetric cryptology, the public key in here is used to decryption while the private key is used to encryption. -
Digital Certificate: Including thekey pairand a digital signature as a voucher for message sent by someone.Digital signature is a message digest encrypted by the private key.
-
Certificate Authority: Company that voucher for adigital certificate.Company voucher for a
DCby adding it’s digital signature to theDC.
HTTPS addresses the man-in-the-middle by having the two sides(Alice and Bob) exchanges their DCto confirm their indenties.
Here’s is the five steps that Alice would go through in order to send messages to Bob.
- Alice sends a signed certificate reqeust containing her name her public key and perhaps some additional information to a
CA. - The
CAcreates a message M from Alice’s request. signing the message M with its private key, thereby creating a seperate signature message SIG, - The
CAreturns Alice the message M with its signature message M. Together M and SIG form Alice’s certificate. - Alice sends her newly minted certificate to Bob to give him access to her public key .
- Bob verfies the signature SIG using the
CA'spublic key. If the signature proves valid, which means the message does come from Alice, he accepts the public key in the certificates as Alice’s public key which is her identity.
相关文章:

Tomcat Notes: Web Security, HTTPS In Tomcat
This is a personal study notes of Apache Tomcat. Below are main reference material. - YouTube Apache Tomcat Full Tutorial,owed by Alpha Brains Courses. https://www.youtube.com/watch?vrElJIPRw5iM&t801s 1、Overview2、Two Levels Of Web Securi…...

智能小程序登陆能力开发文档及示例代码
小程序登录 涂鸦官方提供了登录能力,开发者可以通过相关 API 获取 App 的用户身份标识,快速的建立小程序内的用户体系。 登录流程 说明 需要调用 ty.login() 获取 临时登录凭证 code,并将 code 传到开发者服务器开发者服务器调用涂鸦云开发…...
常见の算法
前言本文主要使用Java 什么,是快乐星球#¥%……什么是算法? 算法是一组完成任务的指令。任何代码片段都可视为算法,但我们主要介绍常见算法 一、引入——二分查找 二分查找是一种算法,其输入是一个有序的元素列表。如…...

openssl3.2/test/certs - 041 - 1024-bit leaf key
文章目录 openssl3.2/test/certs - 041 - 1024-bit leaf key概述笔记END openssl3.2/test/certs - 041 - 1024-bit leaf key 概述 openssl3.2 - 官方demo学习 - test - certs 笔记 /*! * \file D:\my_dev\my_local_git_prj\study\openSSL\test_certs\041\my_openssl_linux_…...

「创新引领未来」科东软件荣获第十二届中国创新创业大赛(广东·广州赛区)优胜奖
近日,广州市科学技术局公布第十二届中国创新创业大赛(广东广州赛区)暨2023年广州科技创新创业大赛常规赛拟获奖企业名单。科东软件凭借国产化技术创新优势、强大的应用场景落地能力和丰富的行业解决方案,荣获第十二届中国创新创业…...
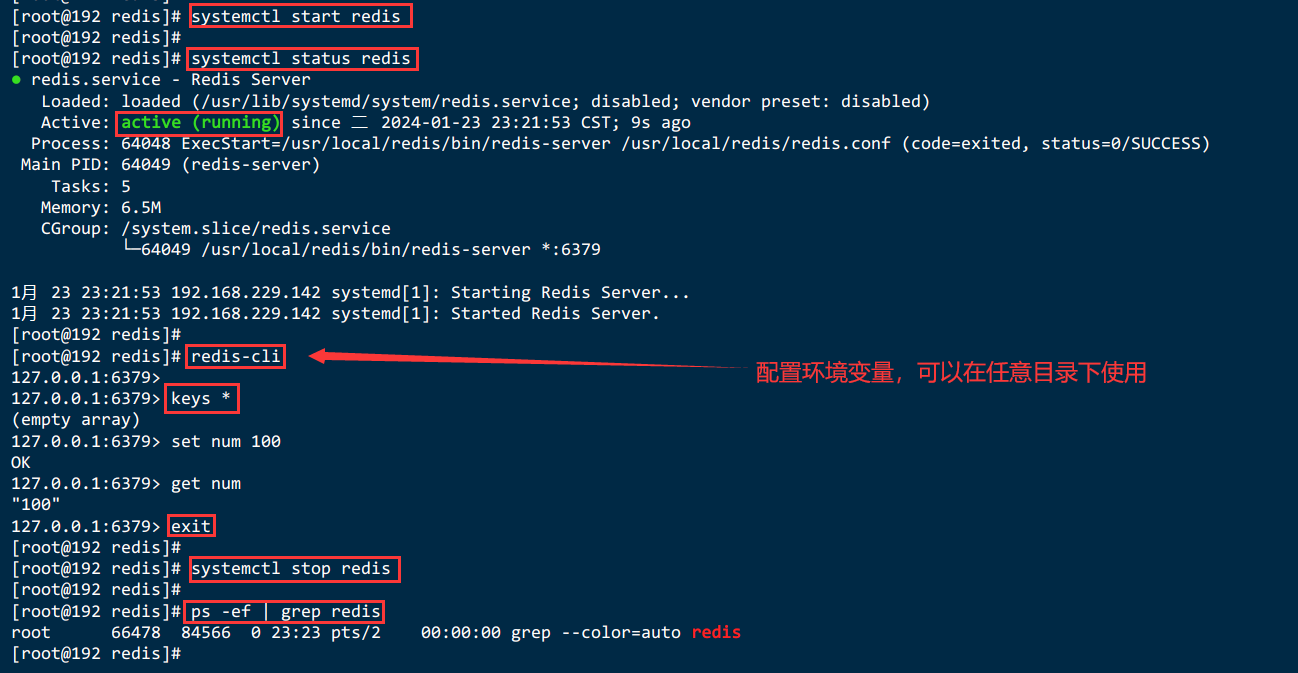
Linux下安装 Redis7
Linux下安装 Redis7 三、Linux下安装 Redis7【redis-7.2.4.tar.gz】3.1.下载redis的安装包3.1.1.手动下载Redis压缩包并上传【redis-7.2.4.tar.gz】3.1.2.wget工具下载redis-7.2.4.tar.gz 3.2.将安装包进行解压缩3.3.进入redis的安装包3.4.检查是否有gcc 环境3.5.编译和安装并指…...

spire.doc合并word文档
文章目录 spire.doc合并word文档1. 引入maven依赖2. 需要合并的word3. 合并文档代码4. 合并结果 spire.doc合并word文档 1. 引入maven依赖 <repositories><repository><id>com.e-iceblue</id><name>e-iceblue</name><url>https://r…...

蓝桥杯官网填空题(01串的熵)
问题描述 答案提交 这是一道结果填空的题, 你只需要算出结果后提交即可。本题的结果为一 个整数, 在提交答案时只填写这个整数, 填写多余的内容将无法得分。 import java.util.*;public class Main {public static void main(String[] args) {for(double zero1;zero<2333…...
【CodeTop】TOP 100 刷题 51-60
文章目录 51. 缺失的第一个正数题目描述代码与解题思路 52. 训练计划 II题目描述代码与解题思路 53. 子集题目描述代码与解题思路 54. 最小覆盖子串题目描述代码与解题思路 55. 从前序与中序遍历序列构造二叉树题目描述代码与解题思路 56. 零钱兑换题目描述代码与解题思路 57. …...

k8s的图形化工具---rancher
rancher是一个开源的企业级多集群的k8s管理平台。 rancher和k8s的区别:都是为了容器的调度和编排系统。但是rancher不仅可以调度还可以管理整个k8s集群。 rancher自带监控(普罗米修斯) 实验部署 master01 20.0.0.32 node01 20.0.0.34 node02 20.0.0.35 test …...
npm安装卡住问题(最新版)
npm安装卡住问题(最新版) 背景: 最近这两天用npm安装一些包的时候,发现一直卡住: 报错: idealTree:npm: sill idealTree buildDeps之前能用的现在不能用了,我一想,是不是源头的问题,还真是…...
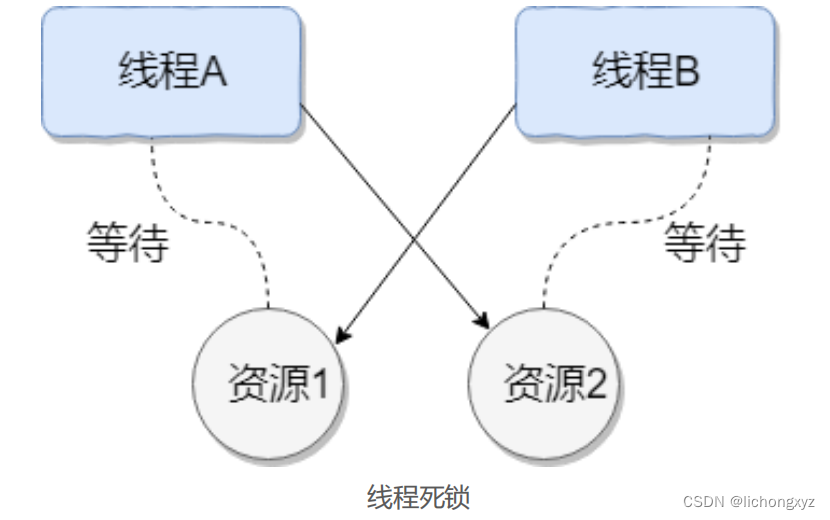
什么是线程死锁
死锁是指两个或两个以上的进程(线程)在执行过程中,由于竞争资 源或者由于彼此通信而造成的一种阻塞的现象,若无外力作用,它们都将无法推 进下去。此时称系统处于死锁状态或系统产生了死锁,这些永远在互相…...
Django从入门到精通(二)
目录 三、视图 3.1、文件or文件夹 3.2、相对和绝对导入urls 3.3、视图参数requests 3.4、返回值 3.5、响应头 3.6、FBV和CBV FBV 四、静态资源 4.1、静态文件 4.2、媒体文件 五、模板 5.1、寻找html模板 5.2、模板处理的本质 5.3、常见模板语法 5.4、内置模板函…...

建筑物防雷检测安全接地应用解决方案
雷电是一种自然现象,具有极高的电压和电流,对建筑物及其内部设备、人员和财产可能造成严重的危害,如火灾、爆炸、电击、电磁干扰等。因此,建筑物必须采取有效的防雷措施,以保障建筑物的安全和可靠运行。建筑物防雷检测…...
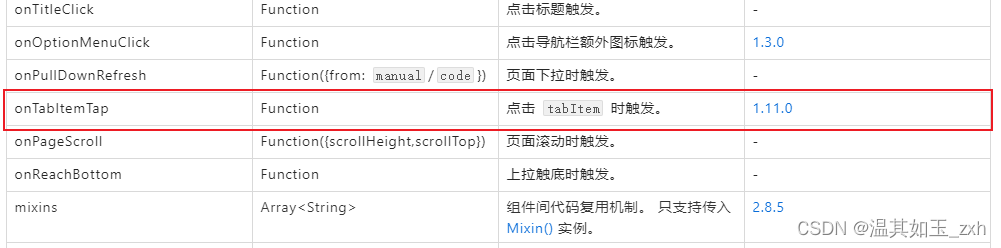
支付宝小程序开发踩坑笔记(支付宝、学习强国小程序)
1、接口请求安卓端回调 success,IOS 端回调 fail 原因:dataType 设置不对,默认是 json 格式,对返回数据会进行 json 解析,如果解析失败,就会回调 fail 。加密传输一般是 text 格式。 2、input 禁止输入空格…...
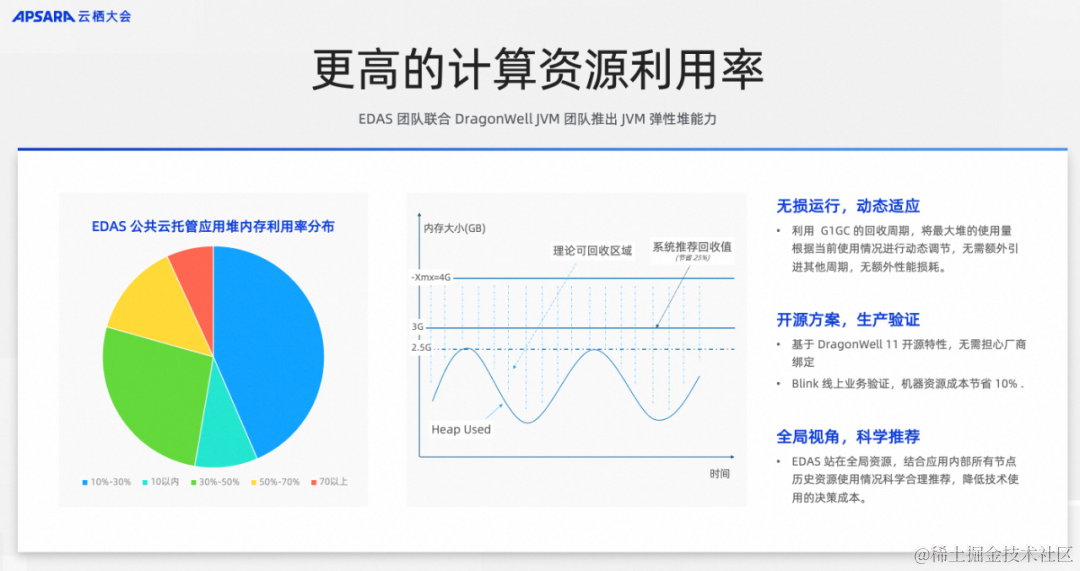
如何降低微服务复杂度丨云栖大会微服务主题分享实录
作者:谢吉宝 本文整理自阿里云资深技术专家、中间件负责人谢吉宝在2023云栖大会《极简微服务模式,降低微服务复杂度的最佳实践》的分享 2023 云栖大会现场 当面临复杂的挑战时,"分而治之"的方法往往能取得显著的效果。微服务架构…...
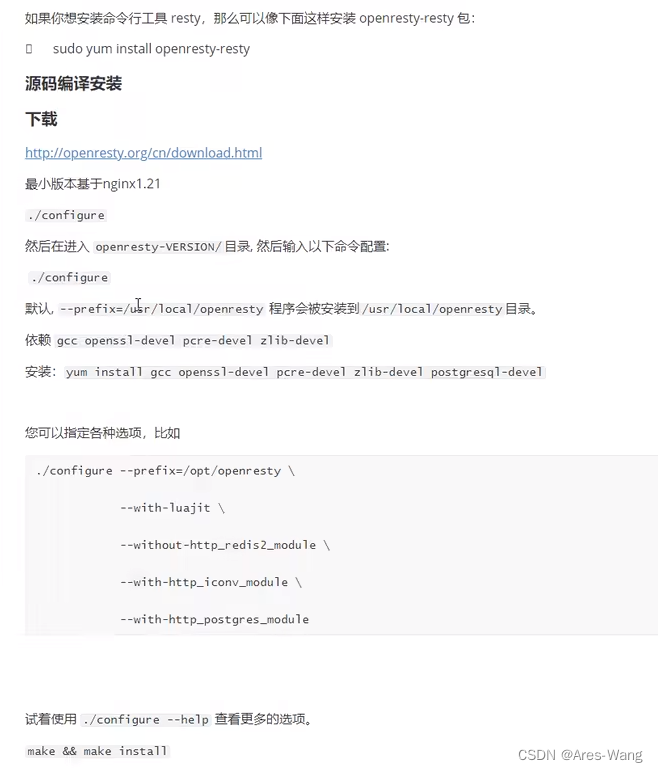
openresty 安装, nginx与 openresty
openresty VS nginx Nginx 是一款高性能的 Web 服务器和反向代理服务器,具备基础的功能如HTTP服务、负载均衡、反向代理以及动静分离等。它是许多互联网应用的核心组件,因其模块化和可扩展的设计而受到欢迎。1 OpenResty 是基于 Nginx 的 Web 平台&…...

puppeteer实现截图
Window服务器说明 1.在本地安装 puppeteer 先创建一个本地文件夹puppeteer,我的地址D:\common_workspace\puppeteer 然后使用cmd打开这个文件夹所在位置,再执行如下两条命令即可。 npm install -g cnpm --registryhttps://registry.npm.taobao.orgcnpm …...
【2024Java面试突击】并发编程、线程池面试实战
前言 最近在更新面试突击专栏,我把每一篇将字数都尽量控制在 2000 字以内,可能在文章里边写的没有那么细致,主要是提供一些 问题 以及 回答的思路 ,以及 面试中可能忽略的漏洞 ,所以在看完文章之后,如果自…...
ASUS华硕无畏Pro15笔记本电脑(M6500QB,M6500QH)工厂模式原厂OEM预装Windows11.22H2系统 含Recovery恢复
原装出厂Windows11系统适用于华硕无畏15笔记本电脑型号:M6500QB和M6500QH 链接:https://pan.baidu.com/s/1AVGLN6-ILIRogOMj48Mk1w?pwdmi7d 提取码:mi7d 带有ASUS RECOVERY恢复功能、自带所有驱动、出厂主题专用壁纸、系统属性联机支持…...
)
论文解读:交大港大上海AI Lab开源论文 | 宇树机器人多姿态起立控制强化学习框架(二)
HoST框架核心实现方法详解 - 论文深度解读(第二部分) 《Learning Humanoid Standing-up Control across Diverse Postures》 系列文章: 论文深度解读 + 算法与代码分析(二) 作者机构: 上海AI Lab, 上海交通大学, 香港大学, 浙江大学, 香港中文大学 论文主题: 人形机器人…...
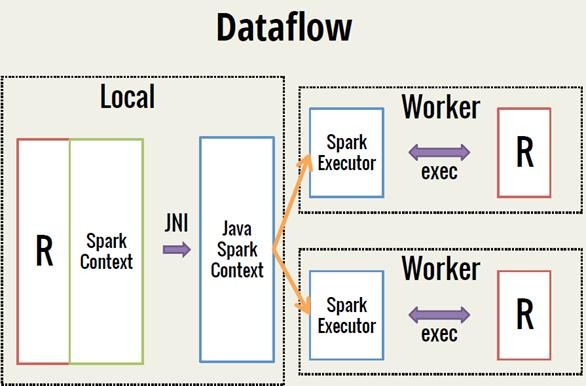
Spark 之 入门讲解详细版(1)
1、简介 1.1 Spark简介 Spark是加州大学伯克利分校AMP实验室(Algorithms, Machines, and People Lab)开发通用内存并行计算框架。Spark在2013年6月进入Apache成为孵化项目,8个月后成为Apache顶级项目,速度之快足见过人之处&…...

反向工程与模型迁移:打造未来商品详情API的可持续创新体系
在电商行业蓬勃发展的当下,商品详情API作为连接电商平台与开发者、商家及用户的关键纽带,其重要性日益凸显。传统商品详情API主要聚焦于商品基本信息(如名称、价格、库存等)的获取与展示,已难以满足市场对个性化、智能…...
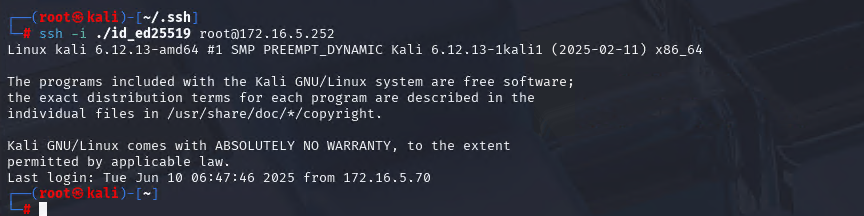
Xshell远程连接Kali(默认 | 私钥)Note版
前言:xshell远程连接,私钥连接和常规默认连接 任务一 开启ssh服务 service ssh status //查看ssh服务状态 service ssh start //开启ssh服务 update-rc.d ssh enable //开启自启动ssh服务 任务二 修改配置文件 vi /etc/ssh/ssh_config //第一…...
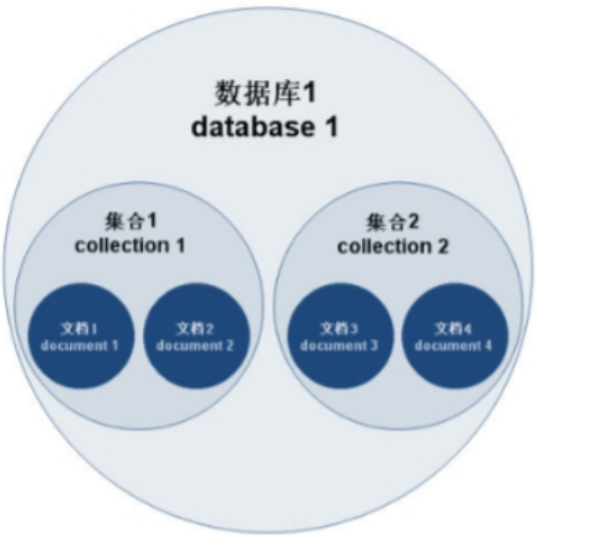
MongoDB学习和应用(高效的非关系型数据库)
一丶 MongoDB简介 对于社交类软件的功能,我们需要对它的功能特点进行分析: 数据量会随着用户数增大而增大读多写少价值较低非好友看不到其动态信息地理位置的查询… 针对以上特点进行分析各大存储工具: mysql:关系型数据库&am…...
【HarmonyOS 5.0】DevEco Testing:鸿蒙应用质量保障的终极武器
——全方位测试解决方案与代码实战 一、工具定位与核心能力 DevEco Testing是HarmonyOS官方推出的一体化测试平台,覆盖应用全生命周期测试需求,主要提供五大核心能力: 测试类型检测目标关键指标功能体验基…...

uni-app学习笔记二十二---使用vite.config.js全局导入常用依赖
在前面的练习中,每个页面需要使用ref,onShow等生命周期钩子函数时都需要像下面这样导入 import {onMounted, ref} from "vue" 如果不想每个页面都导入,需要使用node.js命令npm安装unplugin-auto-import npm install unplugin-au…...
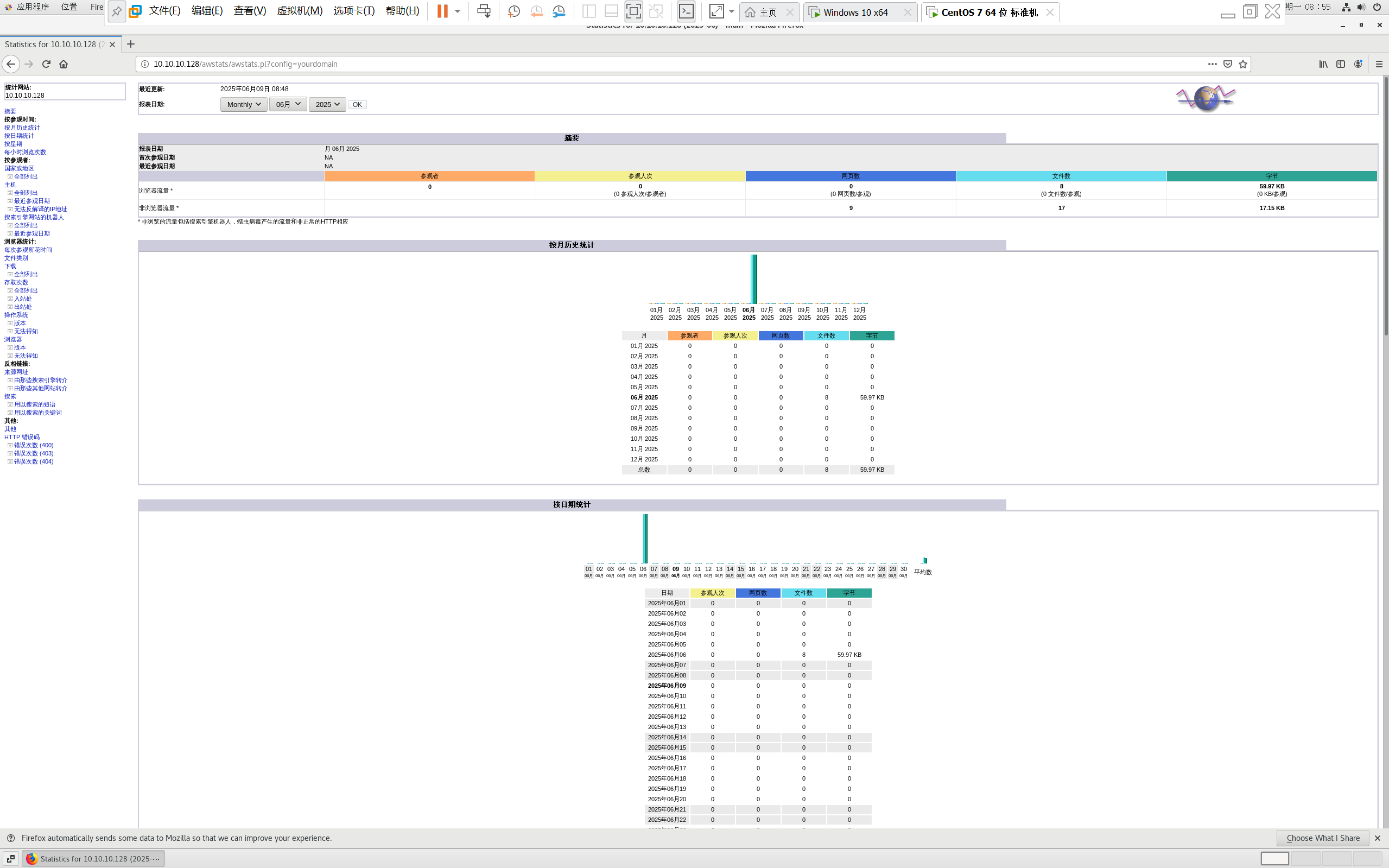
centos 7 部署awstats 网站访问检测
一、基础环境准备(两种安装方式都要做) bash # 安装必要依赖 yum install -y httpd perl mod_perl perl-Time-HiRes perl-DateTime systemctl enable httpd # 设置 Apache 开机自启 systemctl start httpd # 启动 Apache二、安装 AWStats࿰…...
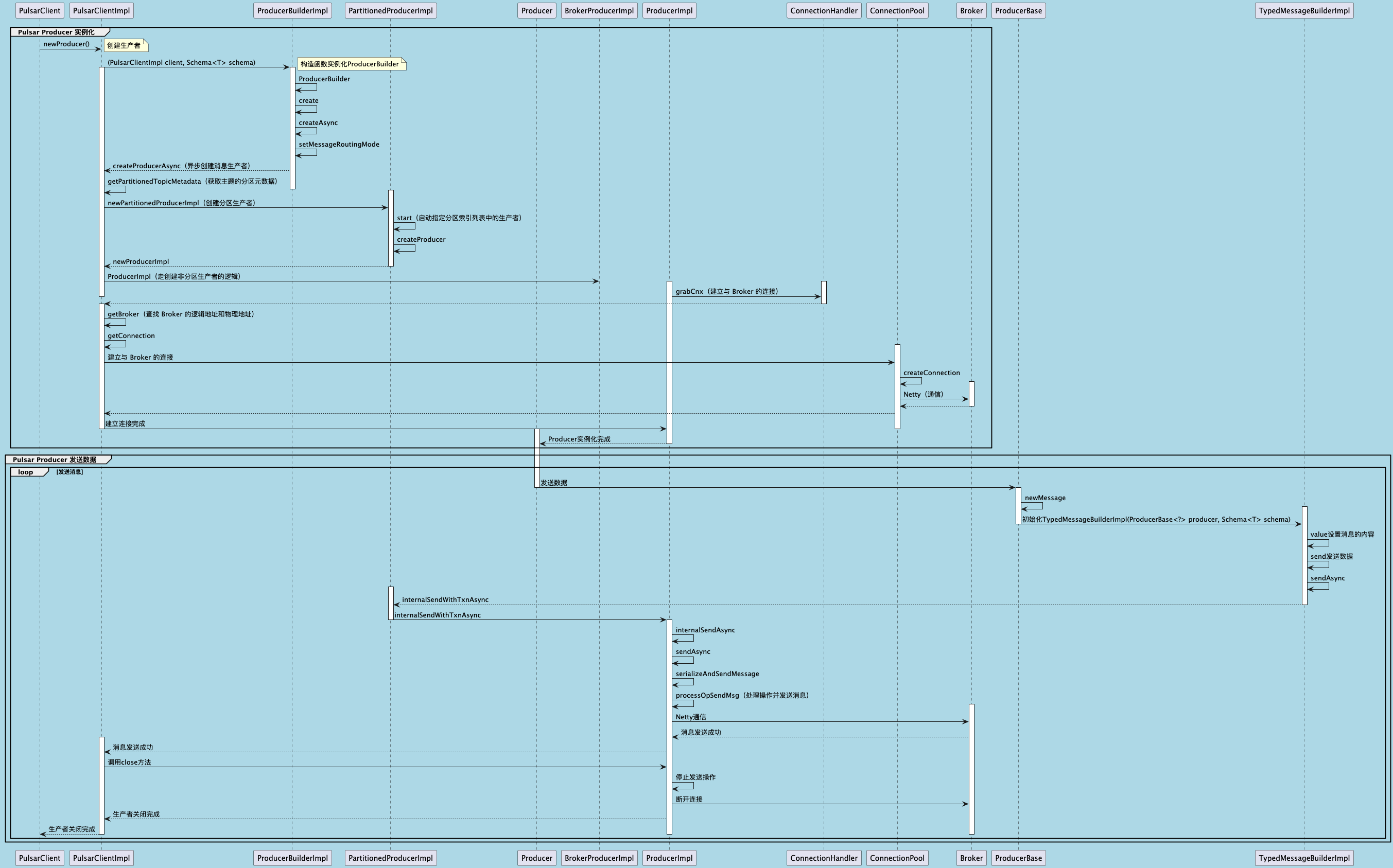
聊聊 Pulsar:Producer 源码解析
一、前言 Apache Pulsar 是一个企业级的开源分布式消息传递平台,以其高性能、可扩展性和存储计算分离架构在消息队列和流处理领域独树一帜。在 Pulsar 的核心架构中,Producer(生产者) 是连接客户端应用与消息队列的第一步。生产者…...

在四层代理中还原真实客户端ngx_stream_realip_module
一、模块原理与价值 PROXY Protocol 回溯 第三方负载均衡(如 HAProxy、AWS NLB、阿里 SLB)发起上游连接时,将真实客户端 IP/Port 写入 PROXY Protocol v1/v2 头。Stream 层接收到头部后,ngx_stream_realip_module 从中提取原始信息…...
