aws(学习笔记第六课) AWS的虚拟私有,共有子网以及ACL,定义公网碉堡主机子网以及varnish反向代理
aws(学习笔记第六课)
-
AWS的虚拟私有,共有子网以及ACL,定义公网碉堡主机子网以及varnish反向代理
学习内容:
AWS的虚拟私有,共有子网以及ACL- 定义公网碉堡主机子网,私有子网和共有子网以及
varnish反向代理
1. AWS的虚拟私有,共有子网以及ACL
AWS的虚拟私有子网,共有云以及ACLAWS的虚拟私有子网
用户可以在AWS上定义自己的私有子网,比如数据库,应用程序和apache的server,可以在私有网络上构建,之后通过共有网络,进行访问,向外提供服务。其实和C++的面向对象中,private的变量和方法,一定不要定义成public的,对终端用户公开,如出一辙。能在私有云中定义,不需要公开的服务,都要定义要私有云中。AWS的虚拟共有云
与上面的AWS私有云对应的就是共有云,共有云最终提供给用户服务,对于终端客户开发网络端口,共有网络的服务承上启下,既可以提供服务给用公户,同时能够访问私有子网的应用服务,数据库服务等其他服务。

ACL(network access control list)和SecuityGroup的区别- 应用的对象不同
ACL的设定对象是Subnet,对于Subnet设定网络访问规则。注意,默认的场合,同一个VPC之间的网络都是相通的,但是如果定义了ACL,那么就会根据ACL的限制,没有允许的网络是不通的
SecurityGroup的设定对象是ec2 server等服务,而不是Subnet。
- 有状态(
state)和无状态(stateless)ACL没有状态,允许入站的包,如果没有符合出站规则,那么也不能出站。SecurityGroup有状态,允许入站的包,那么都会出站允许。
- 应用的对象不同
2. 定义公网碉堡主机子网,私有子网和共有子网
-
整体网络拓扑(这里右边的共有子网使用
varnish进行反向代理,公开私有子网的apache server)

-
逐步创建
VPC以及其他服务-
创建
VPC和IGW(Internet GateWay)"VPC": {"Type": "AWS::EC2::VPC","Properties": {"CidrBlock": "10.0.0.0/16","EnableDnsHostnames": "true"}},"InternetGateway": {"Type": "AWS::EC2::InternetGateway","Properties": {}},"VPCGatewayAttachment": {"Type": "AWS::EC2::VPCGatewayAttachment","Properties": {"VpcId": {"Ref": "VPC"},"InternetGatewayId": {"Ref": "InternetGateway"}}}, -
创建堡垒机子网(共有子网)
Bastion
CidrBlock是10.0.1.0/24
RoutePublicSSHBastionToInternet定义,堡垒机子网能够访问internet。
NetworkAclEntryInPublicSSHBastionSSH,定义internet的其他主机能够访问使用22端口访问(入站规则,egress = true)。
NetworkAclEntryInPublicSSHBastionEphemeralPorts,定义VPC主机能够访问使用随机端口访问(入站规则,egress = true)。
NetworkAclEntryOutPublicSSHBastionSSH,定义堡垒子网的主机能够通过22端口访问其他主机(出站规则,egress = false)。
NetworkAclEntryOutPublicSSHBastionEphemeralPorts,定义internet的主机,能够访问使用随机端口访问(出站规则,egress = false)。"SubnetPublicSSHBastion": {"Type": "AWS::EC2::Subnet","Properties": {"AvailabilityZone": {"Fn::Select": ["0", {"Fn::GetAZs": ""}]},"CidrBlock": "10.0.1.0/24","VpcId": {"Ref": "VPC"}}},"RouteTablePublicSSHBastion": {"Type": "AWS::EC2::RouteTable","Properties": {"VpcId": {"Ref": "VPC"}}},"RouteTableAssociationPublicSSHBastion": {"Type": "AWS::EC2::SubnetRouteTableAssociation","Properties": {"SubnetId": {"Ref": "SubnetPublicSSHBastion"},"RouteTableId": {"Ref": "RouteTablePublicSSHBastion"}}},"RoutePublicSSHBastionToInternet": {"Type": "AWS::EC2::Route","Properties": {"RouteTableId": {"Ref": "RouteTablePublicSSHBastion"},"DestinationCidrBlock": "0.0.0.0/0","GatewayId": {"Ref": "InternetGateway"}},"DependsOn": "VPCGatewayAttachment"},"NetworkAclPublicSSHBastion": {"Type": "AWS::EC2::NetworkAcl","Properties": {"VpcId": {"Ref": "VPC"}}},"SubnetNetworkAclAssociationPublicSSHBastion": {"Type": "AWS::EC2::SubnetNetworkAclAssociation","Properties": {"SubnetId": {"Ref": "SubnetPublicSSHBastion"},"NetworkAclId": {"Ref": "NetworkAclPublicSSHBastion"}}},"NetworkAclEntryInPublicSSHBastionSSH": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicSSHBastion"},"RuleNumber": "100","Protocol": "6","PortRange": {"From": "22","To": "22"},"RuleAction": "allow","Egress": "false","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryInPublicSSHBastionEphemeralPorts": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicSSHBastion"},"RuleNumber": "200","Protocol": "6","PortRange": {"From": "1024","To": "65535"},"RuleAction": "allow","Egress": "false","CidrBlock": "10.0.0.0/16"}},"NetworkAclEntryOutPublicSSHBastionSSH": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicSSHBastion"},"RuleNumber": "100","Protocol": "6","PortRange": {"From": "22","To": "22"},"RuleAction": "allow","Egress": "true","CidrBlock": "10.0.0.0/16"}},"NetworkAclEntryOutPublicSSHBastionEphemeralPorts": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicSSHBastion"},"RuleNumber": "200","Protocol": "6","PortRange": {"From": "1024","To": "65535"},"RuleAction": "allow","Egress": "true","CidrBlock": "0.0.0.0/0"}}, -
创建varnish子网(共有子网)
varnish"SubnetPublicVarnish": {"Type": "AWS::EC2::Subnet","Properties": {"AvailabilityZone": {"Fn::Select": ["0", {"Fn::GetAZs": ""}]},"CidrBlock": "10.0.2.0/24","VpcId": {"Ref": "VPC"}}},"RouteTablePublicVarnish": {"Type": "AWS::EC2::RouteTable","Properties": {"VpcId": {"Ref": "VPC"}}},"RouteTableAssociationPublicVarnish": {"Type": "AWS::EC2::SubnetRouteTableAssociation","Properties": {"SubnetId": {"Ref": "SubnetPublicVarnish"},"RouteTableId": {"Ref": "RouteTablePublicVarnish"}}},"RoutePublicVarnishToInternet": {"Type": "AWS::EC2::Route","Properties": {"RouteTableId": {"Ref": "RouteTablePublicVarnish"},"DestinationCidrBlock": "0.0.0.0/0","GatewayId": {"Ref": "InternetGateway"}},"DependsOn": "VPCGatewayAttachment"},"NetworkAclPublicVarnish": {"Type": "AWS::EC2::NetworkAcl","Properties": {"VpcId": {"Ref": "VPC"}}},"SubnetNetworkAclAssociationPublicVarnish": {"Type": "AWS::EC2::SubnetNetworkAclAssociation","Properties": {"SubnetId": {"Ref": "SubnetPublicVarnish"},"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"}}},"NetworkAclEntryInPublicVarnishSSH": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"},"RuleNumber": "100","Protocol": "6","PortRange": {"From": "22","To": "22"},"RuleAction": "allow","Egress": "false","CidrBlock": "10.0.1.0/24"}},"NetworkAclEntryInPublicVarnishHTTP": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"},"RuleNumber": "110","Protocol": "6","PortRange": {"From": "80","To": "80"},"RuleAction": "allow","Egress": "false","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryInPublicVarnishEphemeralPorts": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"},"RuleNumber": "200","Protocol": "6","PortRange": {"From": "1024","To": "65535"},"RuleAction": "allow","Egress": "false","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryOutPublicVarnishHTTP": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"},"RuleNumber": "100","Protocol": "6","PortRange": {"From": "80","To": "80"},"RuleAction": "allow","Egress": "true","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryOutPublicVarnishHTTPS": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"},"RuleNumber": "110","Protocol": "6","PortRange": {"From": "443","To": "443"},"RuleAction": "allow","Egress": "true","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryOutPublicVarnishEphemeralPorts": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"},"RuleNumber": "200","Protocol": "6","PortRange": {"From": "1024","To": "65535"},"RuleAction": "allow","Egress": "true","CidrBlock": "0.0.0.0/0"}}, -
创建私有子网
"SubnetPrivateApache": {"Type": "AWS::EC2::Subnet","Properties": {"AvailabilityZone": {"Fn::Select": ["0", {"Fn::GetAZs": ""}]},"CidrBlock": "10.0.3.0/24","VpcId": {"Ref": "VPC"}}},"RouteTablePrivateApache": {"Type": "AWS::EC2::RouteTable","Properties": {"VpcId": {"Ref": "VPC"}}},"RouteTableAssociationPrivateApache": {"Type": "AWS::EC2::SubnetRouteTableAssociation","Properties": {"SubnetId": {"Ref": "SubnetPrivateApache"},"RouteTableId": {"Ref": "RouteTablePrivateApache"}}},"RoutePrivateApacheToInternet": {"Type": "AWS::EC2::Route","Properties": {"RouteTableId": {"Ref": "RouteTablePrivateApache"},"DestinationCidrBlock": "0.0.0.0/0","InstanceId": {"Ref": "NatServer"}}},"NetworkAclPrivateApache": {"Type": "AWS::EC2::NetworkAcl","Properties": {"VpcId": {"Ref": "VPC"}}},"SubnetNetworkAclAssociationPrivateApache": {"Type": "AWS::EC2::SubnetNetworkAclAssociation","Properties": {"SubnetId": {"Ref": "SubnetPrivateApache"},"NetworkAclId": {"Ref": "NetworkAclPrivateApache"}}},"NetworkAclEntryInPrivateApacheSSH": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPrivateApache"},"RuleNumber": "100","Protocol": "6","PortRange": {"From": "22","To": "22"},"RuleAction": "allow","Egress": "false","CidrBlock": "10.0.1.0/24"}},"NetworkAclEntryInPrivateApacheHTTP": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPrivateApache"},"RuleNumber": "110","Protocol": "6","PortRange": {"From": "80","To": "80"},"RuleAction": "allow","Egress": "false","CidrBlock": "10.0.2.0/24"}},"NetworkAclEntryInPrivateApacheEphemeralPorts": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPrivateApache"},"RuleNumber": "200","Protocol": "6","PortRange": {"From": "1024","To": "65535"},"RuleAction": "allow","Egress": "false","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryOutPrivateApacheHTTP": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPrivateApache"},"RuleNumber": "100","Protocol": "6","PortRange": {"From": "80","To": "80"},"RuleAction": "allow","Egress": "true","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryOutPrivateApacheHTTPS": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPrivateApache"},"RuleNumber": "110","Protocol": "6","PortRange": {"From": "443","To": "443"},"RuleAction": "allow","Egress": "true","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryOutPrivateApacheEphemeralPorts": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPrivateApache"},"RuleNumber": "200","Protocol": "6","PortRange": {"From": "1024","To": "65535"},"RuleAction": "allow","Egress": "true","CidrBlock": "10.0.0.0/16"}}, -
创建整体的
AWS的stack{"AWSTemplateFormatVersion": "2010-09-09","Description": "(VPC)","Parameters": {"KeyName": {"Description": "Key Pair name","Type": "AWS::EC2::KeyPair::KeyName","Default": "my-cli-key"}},"Mappings": {"EC2RegionMap": {"ap-northeast-1": {"AmazonLinuxAMIHVMEBSBacked64bit": "ami-03f584e50b2d32776", "AmazonLinuxNATAMIHVMEBSBacked64bit": "ami-03cf3903"},"ap-southeast-1": {"AmazonLinuxAMIHVMEBSBacked64bit": "ami-68d8e93a", "AmazonLinuxNATAMIHVMEBSBacked64bit": "ami-b49dace6"},"ap-southeast-2": {"AmazonLinuxAMIHVMEBSBacked64bit": "ami-fd9cecc7", "AmazonLinuxNATAMIHVMEBSBacked64bit": "ami-e7ee9edd"},"eu-central-1": {"AmazonLinuxAMIHVMEBSBacked64bit": "ami-a8221fb5", "AmazonLinuxNATAMIHVMEBSBacked64bit": "ami-46073a5b"},"eu-west-1": {"AmazonLinuxAMIHVMEBSBacked64bit": "ami-a10897d6", "AmazonLinuxNATAMIHVMEBSBacked64bit": "ami-6975eb1e"},"sa-east-1": {"AmazonLinuxAMIHVMEBSBacked64bit": "ami-b52890a8", "AmazonLinuxNATAMIHVMEBSBacked64bit": "ami-fbfa41e6"},"us-east-1": {"AmazonLinuxAMIHVMEBSBacked64bit": "ami-1ecae776", "AmazonLinuxNATAMIHVMEBSBacked64bit": "ami-303b1458"},"us-west-1": {"AmazonLinuxAMIHVMEBSBacked64bit": "ami-d114f295", "AmazonLinuxNATAMIHVMEBSBacked64bit": "ami-7da94839"},"us-west-2": {"AmazonLinuxAMIHVMEBSBacked64bit": "ami-e7527ed7", "AmazonLinuxNATAMIHVMEBSBacked64bit": "ami-69ae8259"}}},"Resources": {"SecurityGroup": {"Type": "AWS::EC2::SecurityGroup","Properties": {"GroupDescription": "My security group","VpcId": {"Ref": "VPC"}}},"SecurityGroupIngress": {"Type": "AWS::EC2::SecurityGroupIngress","Properties":{"IpProtocol": "-1","FromPort": "-1","ToPort": "-1","CidrIp": "0.0.0.0/0","GroupId": {"Ref": "SecurityGroup"}}},"SecurityGroupEgress": {"Type": "AWS::EC2::SecurityGroupEgress","Properties":{"IpProtocol": "-1","FromPort": "-1","ToPort": "-1","CidrIp": "0.0.0.0/0","GroupId": {"Ref": "SecurityGroup"}}},"VPC": {"Type": "AWS::EC2::VPC","Properties": {"CidrBlock": "10.0.0.0/16","EnableDnsHostnames": "true"}},"InternetGateway": {"Type": "AWS::EC2::InternetGateway","Properties": {}},"VPCGatewayAttachment": {"Type": "AWS::EC2::VPCGatewayAttachment","Properties": {"VpcId": {"Ref": "VPC"},"InternetGatewayId": {"Ref": "InternetGateway"}}},"SubnetPublicSSHBastion": {"Type": "AWS::EC2::Subnet","Properties": {"AvailabilityZone": {"Fn::Select": ["0", {"Fn::GetAZs": ""}]},"CidrBlock": "10.0.1.0/24","VpcId": {"Ref": "VPC"}}},"RouteTablePublicSSHBastion": {"Type": "AWS::EC2::RouteTable","Properties": {"VpcId": {"Ref": "VPC"}}},"RouteTableAssociationPublicSSHBastion": {"Type": "AWS::EC2::SubnetRouteTableAssociation","Properties": {"SubnetId": {"Ref": "SubnetPublicSSHBastion"},"RouteTableId": {"Ref": "RouteTablePublicSSHBastion"}}},"RoutePublicSSHBastionToInternet": {"Type": "AWS::EC2::Route","Properties": {"RouteTableId": {"Ref": "RouteTablePublicSSHBastion"},"DestinationCidrBlock": "0.0.0.0/0","GatewayId": {"Ref": "InternetGateway"}},"DependsOn": "VPCGatewayAttachment"},"NetworkAclPublicSSHBastion": {"Type": "AWS::EC2::NetworkAcl","Properties": {"VpcId": {"Ref": "VPC"}}},"SubnetNetworkAclAssociationPublicSSHBastion": {"Type": "AWS::EC2::SubnetNetworkAclAssociation","Properties": {"SubnetId": {"Ref": "SubnetPublicSSHBastion"},"NetworkAclId": {"Ref": "NetworkAclPublicSSHBastion"}}},"NetworkAclEntryInPublicSSHBastionSSH": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicSSHBastion"},"RuleNumber": "100","Protocol": "6","PortRange": {"From": "22","To": "22"},"RuleAction": "allow","Egress": "false","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryInPublicSSHBastionEphemeralPorts": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicSSHBastion"},"RuleNumber": "200","Protocol": "6","PortRange": {"From": "1024","To": "65535"},"RuleAction": "allow","Egress": "false","CidrBlock": "10.0.0.0/16"}},"NetworkAclEntryOutPublicSSHBastionSSH": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicSSHBastion"},"RuleNumber": "100","Protocol": "6","PortRange": {"From": "22","To": "22"},"RuleAction": "allow","Egress": "true","CidrBlock": "10.0.0.0/16"}},"NetworkAclEntryOutPublicSSHBastionEphemeralPorts": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicSSHBastion"},"RuleNumber": "200","Protocol": "6","PortRange": {"From": "1024","To": "65535"},"RuleAction": "allow","Egress": "true","CidrBlock": "0.0.0.0/0"}},"SubnetPublicVarnish": {"Type": "AWS::EC2::Subnet","Properties": {"AvailabilityZone": {"Fn::Select": ["0", {"Fn::GetAZs": ""}]},"CidrBlock": "10.0.2.0/24","VpcId": {"Ref": "VPC"}}},"RouteTablePublicVarnish": {"Type": "AWS::EC2::RouteTable","Properties": {"VpcId": {"Ref": "VPC"}}},"RouteTableAssociationPublicVarnish": {"Type": "AWS::EC2::SubnetRouteTableAssociation","Properties": {"SubnetId": {"Ref": "SubnetPublicVarnish"},"RouteTableId": {"Ref": "RouteTablePublicVarnish"}}},"RoutePublicVarnishToInternet": {"Type": "AWS::EC2::Route","Properties": {"RouteTableId": {"Ref": "RouteTablePublicVarnish"},"DestinationCidrBlock": "0.0.0.0/0","GatewayId": {"Ref": "InternetGateway"}},"DependsOn": "VPCGatewayAttachment"},"NetworkAclPublicVarnish": {"Type": "AWS::EC2::NetworkAcl","Properties": {"VpcId": {"Ref": "VPC"}}},"SubnetNetworkAclAssociationPublicVarnish": {"Type": "AWS::EC2::SubnetNetworkAclAssociation","Properties": {"SubnetId": {"Ref": "SubnetPublicVarnish"},"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"}}},"NetworkAclEntryInPublicVarnishSSH": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"},"RuleNumber": "100","Protocol": "6","PortRange": {"From": "22","To": "22"},"RuleAction": "allow","Egress": "false","CidrBlock": "10.0.1.0/24"}},"NetworkAclEntryInPublicVarnishHTTP": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"},"RuleNumber": "110","Protocol": "6","PortRange": {"From": "80","To": "80"},"RuleAction": "allow","Egress": "false","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryInPublicVarnishEphemeralPorts": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"},"RuleNumber": "200","Protocol": "6","PortRange": {"From": "1024","To": "65535"},"RuleAction": "allow","Egress": "false","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryOutPublicVarnishHTTP": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"},"RuleNumber": "100","Protocol": "6","PortRange": {"From": "80","To": "80"},"RuleAction": "allow","Egress": "true","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryOutPublicVarnishHTTPS": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"},"RuleNumber": "110","Protocol": "6","PortRange": {"From": "443","To": "443"},"RuleAction": "allow","Egress": "true","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryOutPublicVarnishEphemeralPorts": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPublicVarnish"},"RuleNumber": "200","Protocol": "6","PortRange": {"From": "1024","To": "65535"},"RuleAction": "allow","Egress": "true","CidrBlock": "0.0.0.0/0"}},"SubnetPrivateApache": {"Type": "AWS::EC2::Subnet","Properties": {"AvailabilityZone": {"Fn::Select": ["0", {"Fn::GetAZs": ""}]},"CidrBlock": "10.0.3.0/24","VpcId": {"Ref": "VPC"}}},"RouteTablePrivateApache": {"Type": "AWS::EC2::RouteTable","Properties": {"VpcId": {"Ref": "VPC"}}},"RouteTableAssociationPrivateApache": {"Type": "AWS::EC2::SubnetRouteTableAssociation","Properties": {"SubnetId": {"Ref": "SubnetPrivateApache"},"RouteTableId": {"Ref": "RouteTablePrivateApache"}}},"NetworkAclPrivateApache": {"Type": "AWS::EC2::NetworkAcl","Properties": {"VpcId": {"Ref": "VPC"}}},"SubnetNetworkAclAssociationPrivateApache": {"Type": "AWS::EC2::SubnetNetworkAclAssociation","Properties": {"SubnetId": {"Ref": "SubnetPrivateApache"},"NetworkAclId": {"Ref": "NetworkAclPrivateApache"}}},"NetworkAclEntryInPrivateApacheSSH": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPrivateApache"},"RuleNumber": "100","Protocol": "6","PortRange": {"From": "22","To": "22"},"RuleAction": "allow","Egress": "false","CidrBlock": "10.0.1.0/24"}},"NetworkAclEntryInPrivateApacheHTTP": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPrivateApache"},"RuleNumber": "110","Protocol": "6","PortRange": {"From": "80","To": "80"},"RuleAction": "allow","Egress": "false","CidrBlock": "10.0.2.0/24"}},"NetworkAclEntryInPrivateApacheEphemeralPorts": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPrivateApache"},"RuleNumber": "200","Protocol": "6","PortRange": {"From": "1024","To": "65535"},"RuleAction": "allow","Egress": "false","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryOutPrivateApacheHTTP": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPrivateApache"},"RuleNumber": "100","Protocol": "6","PortRange": {"From": "80","To": "80"},"RuleAction": "allow","Egress": "true","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryOutPrivateApacheHTTPS": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPrivateApache"},"RuleNumber": "110","Protocol": "6","PortRange": {"From": "443","To": "443"},"RuleAction": "allow","Egress": "true","CidrBlock": "0.0.0.0/0"}},"NetworkAclEntryOutPrivateApacheEphemeralPorts": {"Type": "AWS::EC2::NetworkAclEntry","Properties": {"NetworkAclId": {"Ref": "NetworkAclPrivateApache"},"RuleNumber": "200","Protocol": "6","PortRange": {"From": "1024","To": "65535"},"RuleAction": "allow","Egress": "true","CidrBlock": "10.0.0.0/16"}},"BastionHost": {"Type": "AWS::EC2::Instance","Properties": {"ImageId": {"Fn::FindInMap": ["EC2RegionMap", {"Ref": "AWS::Region"}, "AmazonLinuxAMIHVMEBSBacked64bit"]},"InstanceType": "t2.micro","KeyName": {"Ref": "KeyName"},"NetworkInterfaces": [{"AssociatePublicIpAddress": "true","DeleteOnTermination": "true","SubnetId": {"Ref": "SubnetPublicSSHBastion"},"DeviceIndex": "0","GroupSet": [{"Ref": "SecurityGroup"}]}]},"DependsOn": "VPCGatewayAttachment"},"VarnishServer": {"Type": "AWS::EC2::Instance","Properties": {"ImageId": {"Fn::FindInMap": ["EC2RegionMap", {"Ref": "AWS::Region"}, "AmazonLinuxAMIHVMEBSBacked64bit"]},"InstanceType": "t2.micro","KeyName": {"Ref": "KeyName"},"NetworkInterfaces": [{"AssociatePublicIpAddress": "true","DeleteOnTermination": "true","SubnetId": {"Ref": "SubnetPublicVarnish"},"DeviceIndex": "0","GroupSet": [{"Ref": "SecurityGroup"}]}],"UserData": {"Fn::Base64": {"Fn::Join": ["", ["#!/bin/bash -ex\n","yum -y install varnish-3.0.7\n","cat > /etc/varnish/default.vcl << EOF\n","backend default {\n"," .host = \"", {"Fn::GetAtt": ["ApacheServer", "PrivateIp"]} ,"\";\n"," .port = \"80\";\n","}\n","EOF\n","sed -i.bak \"s/^VARNISH_LISTEN_PORT=.*/VARNISH_LISTEN_PORT=80/\" /etc/sysconfig/varnish\n","service varnish start\n","/opt/aws/bin/cfn-signal --stack ", {"Ref": "AWS::StackName"}, " --resource VarnishServer --region ", {"Ref": "AWS::Region"}, "\n"]]}}},"DependsOn": "VPCGatewayAttachment"},"ApacheServer": {"Type": "AWS::EC2::Instance","Properties": {"ImageId": {"Fn::FindInMap": ["EC2RegionMap", {"Ref": "AWS::Region"}, "AmazonLinuxAMIHVMEBSBacked64bit"]},"InstanceType": "t2.micro","KeyName": {"Ref": "KeyName"},"NetworkInterfaces": [{"AssociatePublicIpAddress": "false","DeleteOnTermination": "true","SubnetId": {"Ref": "SubnetPrivateApache"},"DeviceIndex": "0","GroupSet": [{"Ref": "SecurityGroup"}]}],"UserData": {"Fn::Base64": {"Fn::Join": ["", ["#!/bin/bash -ex\n","yum -y install httpd\n","service httpd start\n","/opt/aws/bin/cfn-signal --stack ", {"Ref": "AWS::StackName"}, " --resource ApacheServer --region ", {"Ref": "AWS::Region"}, "\n"]]}}}}},"Outputs": {"BastionHostPublicName": {"Value": {"Fn::GetAtt": ["BastionHost", "PublicDnsName"]},"Description": "connect via SSH as user ec2-user"},"VarnishServerPublicName": {"Value": {"Fn::GetAtt": ["VarnishServer", "PublicDnsName"]},"Description": "handles HTTP requests"},"VarnishServerPrivateIp": {"Value": {"Fn::GetAtt": ["VarnishServer", "PrivateIp"]},"Description": "connect via SSH from bastion host"},"ApacheServerPrivateIp": {"Value": {"Fn::GetAtt": ["ApacheServer", "PrivateIp"]},"Description": "connect via SSH from bastion host"}} } -
测试创建结果
-
执行结果

-
一点注意
不要认为连接ec2 server使用的用户就是ec2-user,有的AMI使用的是ubuntu用户
最好在ec2 server的连接画面进行确认。
-
通过堡垒机
SSH访问apache server(私有子网)
ssh -A ubuntu@ec2-13-230-4-241.ap-northeast-1.compute.amazonaws.com通过AgentForward模式进行访问堡垒机。
ssh 10.0.3.198直接就可以访问私有子网的apache主机。Dell@DESKTOP-DHMQMJG MINGW64 / $ eval `ssh-agent` Agent pid 2195Dell@DESKTOP-DHMQMJG MINGW64 / $ ssh-add ~/.ssh/my-cli-key.pem Identity added: /c/Users/Dell/.ssh/my-cli-key.pem (/c/Users/Dell/.ssh/my-cli-key.pem)Dell@DESKTOP-DHMQMJG MINGW64 / $ ssh -A ubuntu@ec2-13-230-4-241.ap-northeast-1.compute.amazonaws.com Welcome to Ubuntu 24.04.1 LTS (GNU/Linux 6.8.0-1016-aws x86_64)ubuntu@ip-10-0-1-169:~$ ssh 10.0.3.198 Welcome to Ubuntu 24.04.1 LTS (GNU/Linux 6.8.0-1016-aws x86_64) -
通过堡varnish反向代理
HTTP访问apache server(私有子网)ubuntu@ip-10-0-1-169:~$ ssh ec2-52-195-182-135.ap-northeast-1.compute.amazonaws.com The authenticity of host 'ec2-52-195-182-135.ap-northeast-1.compute.amazonaws.com (10.0.2.170)' can't be established. ED25519 key fingerprint is SHA256:r4A9nVkEUhL1ovBuKc90hnYZUNilz/xxFKlPYj0kyOQ.
-
-
相关文章:

aws(学习笔记第六课) AWS的虚拟私有,共有子网以及ACL,定义公网碉堡主机子网以及varnish反向代理
aws(学习笔记第六课) AWS的虚拟私有,共有子网以及ACL,定义公网碉堡主机子网以及varnish反向代理 学习内容: AWS的虚拟私有,共有子网以及ACL定义公网碉堡主机子网,私有子网和共有子网以及varnish反向代理 1. AWS的虚拟…...

接口测试(三)jmeter——连接mysql数据库
一、jmeter安装jdbc 1. 下载插件包,mysql数据库为例,驱动 com.mysql.jdbc.Driver 需要下载 mysql-connector-java-5.1.7-bin.jar 插件包,将插件包放到 jmeter 安装目录下的 lib 目录 2. 给jmeter安装jdbc驱动 二、jmeter操作数据库 1.…...

双十一购物节有哪些好物值得入手?2024双十一好物清单合集分享
一年一度的双十一购物狂欢节即将来临,各大平台纷纷开启预热活动,伴随着品牌的疯狂折扣和满减优惠,众多商品即将迎来超值的价格。现在正是大家“剁手”换新装备的大好时机。作为一名深耕智能产品多年的资深达人,今天这期我将从不同…...

jmeter中请求参数:Parameters、Body Data的区别
使用jmeter发送请求,常常要伴随传递参数。有两种请求参数: Parameters, Body Data, 它们的使用方式有很大不同。 先看下get和post请求的区别。 get请求:顾名思义是从服务器获取资源。 post请求:顾名思义是往服务器提交要处理的数据。 直观…...

Docker安装ActiveMQ镜像以及通过Java生产消费activemq示例
拉取镜像 docker pull docker.io/webcenter/activemq 启动容器 docker run -d --name myactivemq -p 61616:61616 -p 8162:8161 docker.io/webcenter/activemq:latest 这样就代表启动成功了 浏览器访问 http://localhost:8162/ admin admin 开启验证 修改配置文件/opt/ac…...

迅为RK3562开发板/核心板240PIN引脚全部引出,产品升级自如
可应用于人脸跟踪、身体跟踪、视频监控、自动语音识别(ASR)、图像分类驾驶员辅助系统(ADAS)、车牌识别、物体识别等。 iTOP-3562开发板/核心板采用瑞芯微RK3562处理器,内部集成了四核A53Mali G52架构,主频2GHZ,内置1TOPSNPU算力,R…...

C++实现顺序栈和链栈操作(实验3--作业)
顺序栈 一、主要功能 实现了顺序栈(SqStack)的数据结构,并利用该数据结构进行了栈的基本操作以及数制转换的功能。 二、数据结构定义 定义了一些常量: MAXSIZE表示栈的最大长度为 100。OVERFLOw表示存储失败的错误码为 -2。O…...
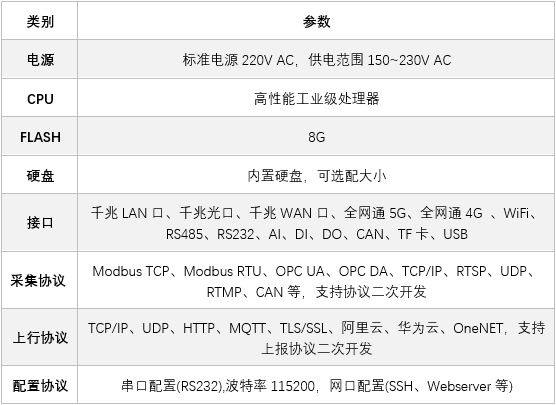
龙兴物联一体机:设备监测的智能先锋
龙兴物联物联网一体机的崛起 龙兴物联物联网一体机在设备监测领域占据着至关重要的地位。随着科技的不断进步和各行业对设备监测需求的日益增长,龙兴物联物联网一体机以其卓越的性能和广泛的适用性,迅速崛起并成为众多企业和机构的首选。 在当今数字化时…...
KinectDK相机SDK封装Dll出现k4abt_tracker_create()创建追踪器失败的问题
项目场景: KinectDK相机SDK封装Dll 问题描述 在 C 环境下,使用 GPU 模式(默认)调用 k4abt_tracker_create 函数正常工作。但是,在 Python 环境下,通过 ctypes 调用相同的 DLL,当使用 GPU 模式…...

Linux 命令—— ping、telnet、curl、wget(网络连接相关命令)
文章目录 网络连接相关命令pingtelnetcurlwget 网络连接相关命令 ping ping 命令是用于测试网络连接和诊断网络问题的工具。它通过向目标主机发送 ICMP(Internet Control Message Protocol)回显请求,并等待回复,以确定目标主机是…...

高速缓冲存储器Cache是如何工作的、主要功能、高速缓冲存储器Cache和主存有哪些区别
1、高速缓冲存储器Cache是如何工作的 高速缓冲存储器Cache的工作主要基于程序和数据访问的局部性原理,其工作方式可以概括为以下几点: 存储近期可能访问的数据和指令:Cache会存储CPU近期可能访问的数据和指令,当CPU需要访问这些…...

极简版Java敏感词检测SDK
敏感词工具 sensitive-word 基于 DFA 算法实现的高性能敏感词工具,开源在GitHub:https://github.com/houbb/sensitive-word。用于敏感词/违禁词/违法词/脏词等的识别和阻拦,是基于 DFA 算法实现的高性能 java 敏感词过滤工具框架。 使用场景…...

H3C路由器交换机操作系统介绍
路由器 路由器的作用 连接具有不同介质的链路连接网络或子网,隔离广播对数据报文执行寻路和转发交换和维护路由信息 H3C 路由器系列 CR系列核心路由器SR系列高端路由器MSR系列路由器ER系列路由器 交换机 交换机的作用 连接多个以太网物理段,隔离冲…...
【项目案例】-音乐播放器-Android前端实现-Java后端实现
精品专题: 01.C语言从不挂科到高绩点 https://blog.csdn.net/yueyehuguang/category_12753294.html?spm1001.2014.3001.5482https://blog.csdn.net/yueyehuguang/category_12753294.html?spm1001.2014.3001.5482 02. SpringBoot详细教程 https://blog.csdn.ne…...

EasyX图形库的安装
前言 EasyX是一个图形库,可以用来做一些c/c小游戏,帮助学习。 一、进入EasyX官网 https://easyx.cn/ 二、点击下载EasyX 三、下载好后以管理员身份运行它 四、点击下一步 五、然后它会自动检测你的编辑器,用哪个就在哪个点安装 六、安装成功…...

数据结构 - 队列
队列也是一种操作受限的线性数据结构,与栈很相似。 01定义 栈的操作受限表现为只允许在队列的一端进行元素插入操作,在队列的另一端只允许删除操作。这一特性可以总结为先进先出(First In First Out,简称FIFO)。这意味…...

基于springboot美食推荐商城的设计与实现
基于springboot美食推荐商城的设计与实现 开发语言:Java 框架:springboot JDK版本:JDK1.8 服务器:tomcat7 数据库:mysql 5.7 数据库工具:Navicat11 开发软件:idea 源码获取:https:…...

React开发一个WebSocket
export default class SocketService {static instance null;static get Instance() {if (!this.instance) {this.instance new SocketService();}return this.instance;}// 和服务端连接的socket对象ws null;// 存储回调函数callBackMapping {};// 标识是否连接成功connec…...

Oracle DECODE 丢失时间精度的原因与解决方案
在Oracle数据库中,DECODE 函数是一个非常实用的条件处理函数,通常用于替代简单的 CASE WHEN 语句。它根据给定的值列表进行匹配,如果匹配成功则返回相应的值。如果不匹配,返回一个默认值。 问题描述 SELECT DECODE(-21, -1, NU…...

如何用示波器检测次级点火系统(一)
写在最前面: 单看标题可能会让你觉得这篇文章的主题是关于检测线圈,火花塞和火花塞插头电线。但我们指的是分析燃烧室内电子的行为。目标是看燃料混合物,阀座,压缩,积碳和其它影响这种特性的症状。最终目的是要学会分…...
国防科技大学计算机基础课程笔记02信息编码
1.机内码和国标码 国标码就是我们非常熟悉的这个GB2312,但是因为都是16进制,因此这个了16进制的数据既可以翻译成为这个机器码,也可以翻译成为这个国标码,所以这个时候很容易会出现这个歧义的情况; 因此,我们的这个国…...
微服务商城-商品微服务
数据表 CREATE TABLE product (id bigint(20) UNSIGNED NOT NULL AUTO_INCREMENT COMMENT 商品id,cateid smallint(6) UNSIGNED NOT NULL DEFAULT 0 COMMENT 类别Id,name varchar(100) NOT NULL DEFAULT COMMENT 商品名称,subtitle varchar(200) NOT NULL DEFAULT COMMENT 商…...

【python异步多线程】异步多线程爬虫代码示例
claude生成的python多线程、异步代码示例,模拟20个网页的爬取,每个网页假设要0.5-2秒完成。 代码 Python多线程爬虫教程 核心概念 多线程:允许程序同时执行多个任务,提高IO密集型任务(如网络请求)的效率…...
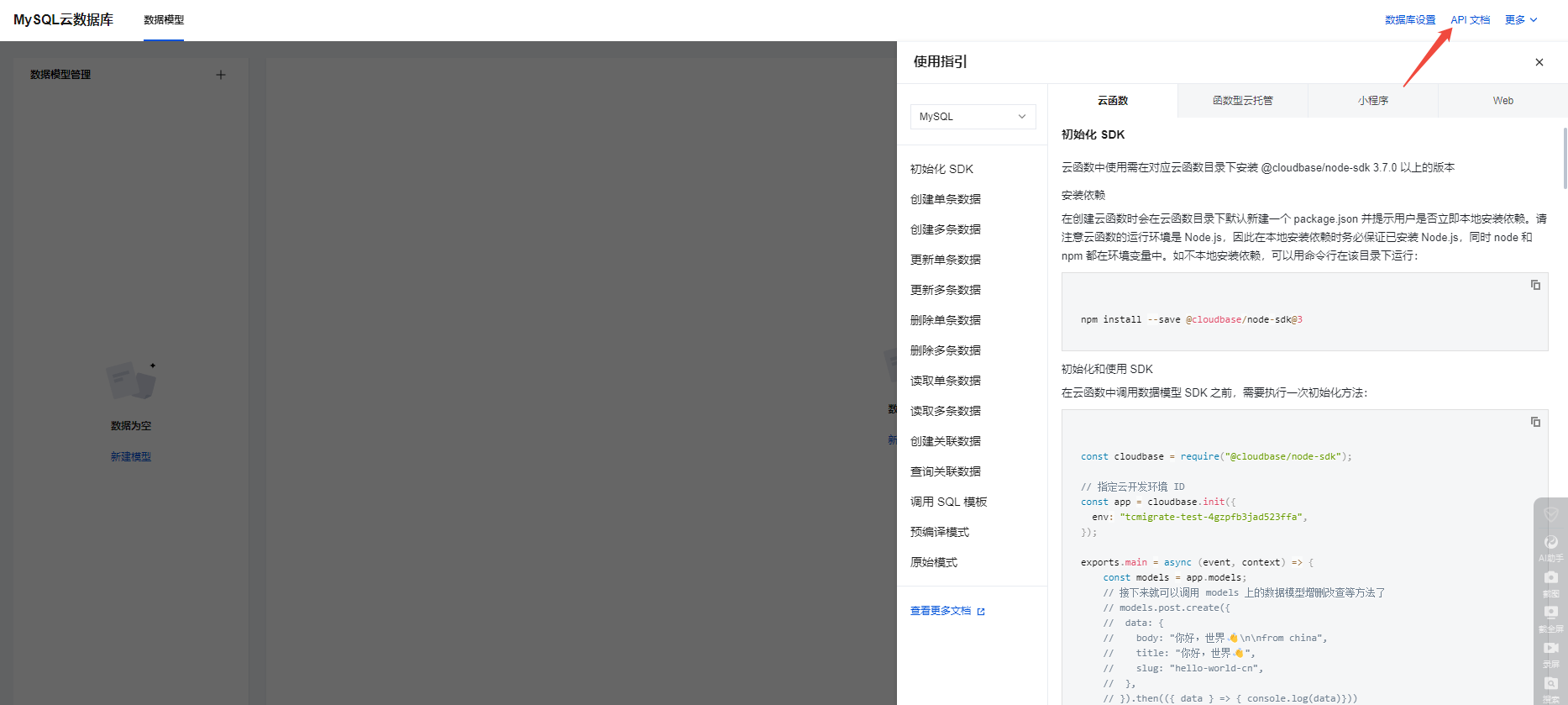
微信小程序云开发平台MySQL的连接方式
注:微信小程序云开发平台指的是腾讯云开发 先给结论:微信小程序云开发平台的MySQL,无法通过获取数据库连接信息的方式进行连接,连接只能通过云开发的SDK连接,具体要参考官方文档: 为什么? 因为…...
)
OpenLayers 分屏对比(地图联动)
注:当前使用的是 ol 5.3.0 版本,天地图使用的key请到天地图官网申请,并替换为自己的key 地图分屏对比在WebGIS开发中是很常见的功能,和卷帘图层不一样的是,分屏对比是在各个地图中添加相同或者不同的图层进行对比查看。…...

Java编程之桥接模式
定义 桥接模式(Bridge Pattern)属于结构型设计模式,它的核心意图是将抽象部分与实现部分分离,使它们可以独立地变化。这种模式通过组合关系来替代继承关系,从而降低了抽象和实现这两个可变维度之间的耦合度。 用例子…...
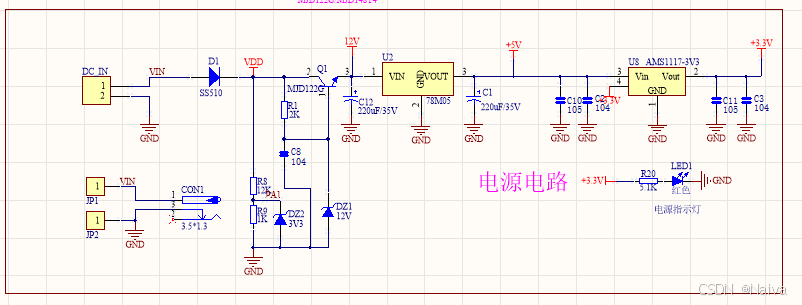
【电力电子】基于STM32F103C8T6单片机双极性SPWM逆变(硬件篇)
本项目是基于 STM32F103C8T6 微控制器的 SPWM(正弦脉宽调制)电源模块,能够生成可调频率和幅值的正弦波交流电源输出。该项目适用于逆变器、UPS电源、变频器等应用场景。 供电电源 输入电压采集 上图为本设计的电源电路,图中 D1 为二极管, 其目的是防止正负极电源反接, …...
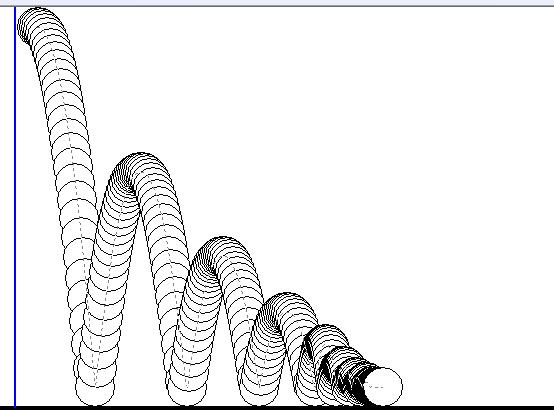
MFC 抛体运动模拟:常见问题解决与界面美化
在 MFC 中开发抛体运动模拟程序时,我们常遇到 轨迹残留、无效刷新、视觉单调、物理逻辑瑕疵 等问题。本文将针对这些痛点,详细解析原因并提供解决方案,同时兼顾界面美化,让模拟效果更专业、更高效。 问题一:历史轨迹与小球残影残留 现象 小球运动后,历史位置的 “残影”…...

Proxmox Mail Gateway安装指南:从零开始配置高效邮件过滤系统
💝💝💝欢迎莅临我的博客,很高兴能够在这里和您见面!希望您在这里可以感受到一份轻松愉快的氛围,不仅可以获得有趣的内容和知识,也可以畅所欲言、分享您的想法和见解。 推荐:「storms…...
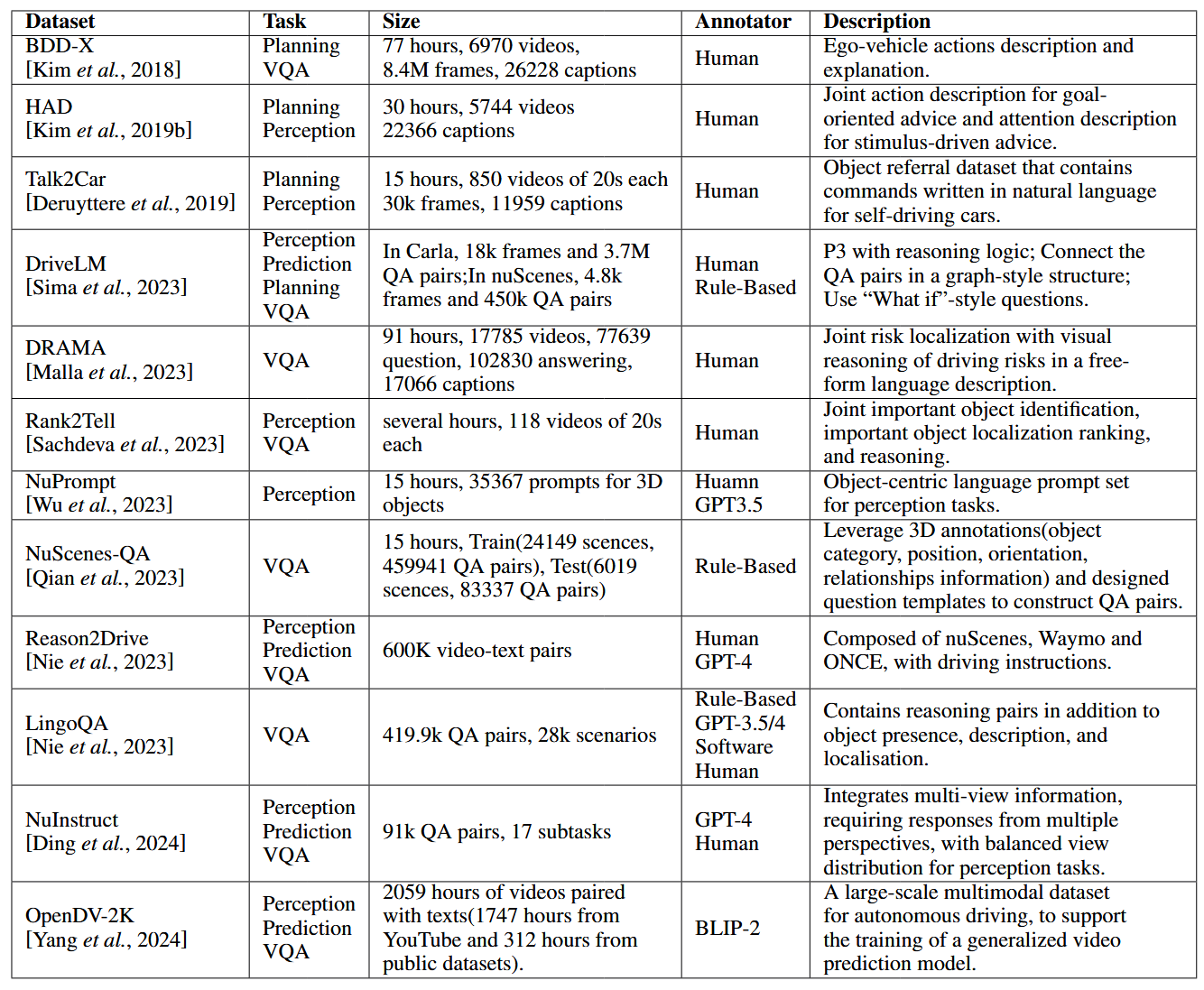
论文阅读:LLM4Drive: A Survey of Large Language Models for Autonomous Driving
地址:LLM4Drive: A Survey of Large Language Models for Autonomous Driving 摘要翻译 自动驾驶技术作为推动交通和城市出行变革的催化剂,正从基于规则的系统向数据驱动策略转变。传统的模块化系统受限于级联模块间的累积误差和缺乏灵活性的预设规则。…...
