CTF-PWN: 全保护下格式化字符串利用 [第一届“吾杯”网络安全技能大赛 如果能重来] 赛后学习(不会)
通过网盘分享的文件:如果能重来.zip
链接: https://pan.baidu.com/s/1XKIJx32nWVcSpKiWFQGpYA?pwd=1111 提取码: 1111
--来自百度网盘超级会员v2的分享
漏洞分析
格式化字符串漏洞,在printf(format);
__int64 sub_13D7()
{char format[56]; // [rsp+10h] [rbp-40h] BYREFunsigned __int64 v2; // [rsp+48h] [rbp-8h]v2 = __readfsqword(0x28u);printf("Please input your name: ");if ( (int)sub_1247(format, 55LL) > 0 ){if ( dword_404C ){printf(format);--dword_404C;puts("There will be a gift for you here . . .");}else{puts("0.o? ");}return 0LL;}else{puts("Error reading name.");return 0xFFFFFFFFLL;}
}
确定参数偏移
❯ gdb pwn
GNU gdb (Ubuntu 12.1-0ubuntu1~22.04.2) 12.1
Copyright (C) 2022 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<https://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:<http://www.gnu.org/software/gdb/documentation/>.For help, type "help".
Type "apropos word" to search for commands related to "word"...
startpwndbg: loaded 165 pwndbg commands and 46 shell commands. Type pwndbg [--shell | --all] [filter] for a list.
pwndbg: created $rebase, $base, $bn_sym, $bn_var, $bn_eval, $ida GDB functions (can be used with print/break)
Reading symbols from pwn...
(No debugging symbols found in pwn)
------- tip of the day (disable with set show-tips off) -------
If you want Pwndbg to clear screen on each command (but still save previous output in history) use set context-clear-screen on
pwndbg> start
Temporary breakpoint 1 at 0x5555555550e0Temporary breakpoint 1, 0x00005555555550e0 in ?? ()
LEGEND: STACK | HEAP | CODE | DATA | WX | RODATA
───────────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]───────────────────────────────────────RAX 0x1cRBX 0RCX 0x7fffffffc478 —▸ 0x7fffffffc82b ◂— 'SYSTEMD_EXEC_PID=1816'RDX 0x7ffff7fe0d60 ◂— endbr64 RDI 0x7ffff7ffe190 —▸ 0x555555554000 ◂— 0x10102464c457fRSI 0x7ffff7ffe730 ◂— 0R8 0R9 2R10 0xfR11 0R12 0x5555555550e0 ◂— endbr64 R13 0x7fffffffc460 ◂— 1R14 0R15 0RBP 0RSP 0x7fffffffc460 ◂— 1RIP 0x5555555550e0 ◂— endbr64
────────────────────────────────────────────────[ DISASM / x86-64 / set emulate on ]────────────────────────────────────────────────► 0x5555555550e0 endbr64 0x5555555550e4 xor ebp, ebp EBP => 00x5555555550e6 mov r9, rdx R9 => 0x7ffff7fe0d60 ◂— endbr64 0x5555555550e9 pop rsi RSI => 10x5555555550ea mov rdx, rsp RDX => 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'0x5555555550ed and rsp, 0xfffffffffffffff0 RSP => 0x7fffffffc460 (0x7fffffffc468 & -0x10)0x5555555550f1 push rax0x5555555550f2 push rsp0x5555555550f3 lea r8, [rip + 0x426] R8 => 0x555555555520 ◂— endbr64 0x5555555550fa lea rcx, [rip + 0x3af] RCX => 0x5555555554b0 ◂— endbr64 0x555555555101 lea rdi, [rip + 0x385] RDI => 0x55555555548d ◂— endbr64
─────────────────────────────────────────────────────────────[ STACK ]──────────────────────────────────────────────────────────────
00:0000│ r13 rsp 0x7fffffffc460 ◂— 1
01:0008│ 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
02:0010│ 0x7fffffffc470 ◂— 0
03:0018│ rcx 0x7fffffffc478 —▸ 0x7fffffffc82b ◂— 'SYSTEMD_EXEC_PID=1816'
04:0020│ 0x7fffffffc480 —▸ 0x7fffffffc841 ◂— 'SSH_AUTH_SOCK=/run/user/1000/keyring/ssh'
05:0028│ 0x7fffffffc488 —▸ 0x7fffffffc86a ◂— 'SESSION_MANAGER=local/ubuntu:@/tmp/.ICE-unix/1816,unix/ubuntu:/tmp/.ICE-unix/1816'
06:0030│ 0x7fffffffc490 —▸ 0x7fffffffc8bc ◂— 'PAPERSIZE=a4'
07:0038│ 0x7fffffffc498 —▸ 0x7fffffffc8c9 ◂— 'GNOME_TERMINAL_SCREEN=/org/gnome/Terminal/screen/aab6f309_847c_4363_b37f_36574de33f67'
───────────────────────────────────────────────────────────[ BACKTRACE ]────────────────────────────────────────────────────────────► 0 0x5555555550e01 0x12 0x7fffffffc80b3 0x0
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> b *$rebase(0x1444)
Breakpoint 2 at 0x555555555401
pwndbg> run
Starting program: /home/a5rz/Desktop/pwn/file/pwn
Please input your name: aaaaaaaa%p%p%p%p%p%p%p%p%p%p%p%pBreakpoint 2, 0x0000555555555444 in ?? ()
LEGEND: STACK | HEAP | CODE | DATA | WX | RODATA
───────────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]───────────────────────────────────────RAX 0RBX 0x5555555554b0 ◂— endbr64 RCX 0RDX 1RDI 0x7fffffffc2e0 ◂— 'aaaaaaaa%p%p%p%p%p%p%p%p%p%p%p%pSomething strange here'RSI 0x7fffffffc2af ◂— 0x1000000200a /* '\n ' */R8 0x18R9 0x18R10 0x555555556008 ◂— 'Please input your name: 'R11 0x246R12 0x5555555550e0 ◂— endbr64 R13 0x7fffffffc460 ◂— 1R14 0R15 0RBP 0x7fffffffc320 —▸ 0x7fffffffc360 —▸ 0x7fffffffc370 ◂— 0RSP 0x7fffffffc2d0 ◂— 0RIP 0x555555555444 ◂— call 0x5555555550b0
────────────────────────────────────────────────[ DISASM / x86-64 / set emulate on ]────────────────────────────────────────────────► 0x555555555444 call printf@plt <printf@plt>format: 0x7fffffffc2e0 ◂— 'aaaaaaaa%p%p%p%p%p%p%p%p%p%p%p%pSomething strange here'vararg: 0x7fffffffc2af ◂— 0x1000000200a /* '\n ' */0x555555555449 mov eax, dword ptr [rip + 0x2bfd] EAX, [0x55555555804c]0x55555555544f sub eax, 10x555555555452 mov dword ptr [rip + 0x2bf4], eax0x555555555458 lea rdi, [rip + 0xbd9] RDI => 0x555555556038 ◂— 'There will be a gift for you here . . .'0x55555555545f call puts@plt <puts@plt>0x555555555464 jmp 0x555555555472 <0x555555555472>↓0x555555555472 mov eax, 0 EAX => 00x555555555477 mov rdx, qword ptr [rbp - 8]0x55555555547b xor rdx, qword ptr fs:[0x28]0x555555555484 je 0x55555555548b <0x55555555548b>
─────────────────────────────────────────────────────────────[ STACK ]──────────────────────────────────────────────────────────────
00:0000│ rsp 0x7fffffffc2d0 ◂— 0
01:0008│-048 0x7fffffffc2d8 ◂— 0xf7fc37d0f7fc25c0
02:0010│ rdi 0x7fffffffc2e0 ◂— 'aaaaaaaa%p%p%p%p%p%p%p%p%p%p%p%pSomething strange here'
03:0018│-038 0x7fffffffc2e8 ◂— '%p%p%p%p%p%p%p%p%p%p%p%pSomething strange here'
... ↓ 2 skipped
06:0030│-020 0x7fffffffc300 ◂— 'Something strange here'
07:0038│-018 0x7fffffffc308 ◂— 'g strange here'
───────────────────────────────────────────────────────────[ BACKTRACE ]────────────────────────────────────────────────────────────► 0 0x5555555554441 0x5555555553bc2 0x5555555554a93 0x7ffff7df9083 __libc_start_main+2434 0x55555555510e
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> stack 90
00:0000│ rsp 0x7fffffffc2d0 ◂— 0
01:0008│-048 0x7fffffffc2d8 ◂— 0xf7fc37d0f7fc25c0
02:0010│ rdi 0x7fffffffc2e0 ◂— 'aaaaaaaa%p%p%p%p%p%p%p%p%p%p%p%pSomething strange here'
03:0018│-038 0x7fffffffc2e8 ◂— '%p%p%p%p%p%p%p%p%p%p%p%pSomething strange here'
... ↓ 2 skipped
06:0030│-020 0x7fffffffc300 ◂— 'Something strange here'
07:0038│-018 0x7fffffffc308 ◂— 'g strange here'
08:0040│-010 0x7fffffffc310 ◂— 0x657265682065 /* 'e here' */
09:0048│-008 0x7fffffffc318 ◂— 0x4d8fe1de9078d800
0a:0050│ rbp 0x7fffffffc320 —▸ 0x7fffffffc360 —▸ 0x7fffffffc370 ◂— 0
0b:0058│+008 0x7fffffffc328 —▸ 0x5555555553bc ◂— mov eax, 0
0c:0060│+010 0x7fffffffc330 ◂— 'welcome to WuCup !'
0d:0068│+018 0x7fffffffc338 ◂— 'to WuCup !'
0e:0070│+020 0x7fffffffc340 ◂— 0x555555002120 /* ' !' */
0f:0078│+028 0x7fffffffc348 —▸ 0x7fffffffc460 ◂— 1
10:0080│+030 0x7fffffffc350 ◂— 0
11:0088│+038 0x7fffffffc358 ◂— 0x4d8fe1de9078d800
12:0090│+040 0x7fffffffc360 —▸ 0x7fffffffc370 ◂— 0
13:0098│+048 0x7fffffffc368 —▸ 0x5555555554a9 ◂— mov eax, 0
14:00a0│+050 0x7fffffffc370 ◂— 0
15:00a8│+058 0x7fffffffc378 —▸ 0x7ffff7df9083 (__libc_start_main+243) ◂— mov edi, eax
16:00b0│+060 0x7fffffffc380 —▸ 0x7ffff7ffc620 (_rtld_global_ro) ◂— 0x50fa700000000
17:00b8│+068 0x7fffffffc388 —▸ 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
18:00c0│+070 0x7fffffffc390 ◂— 0x100000000
19:00c8│+078 0x7fffffffc398 —▸ 0x55555555548d ◂— endbr64
1a:00d0│+080 0x7fffffffc3a0 —▸ 0x5555555554b0 ◂— endbr64
1b:00d8│+088 0x7fffffffc3a8 ◂— 0xb19ed39ac14d0a56
1c:00e0│+090 0x7fffffffc3b0 —▸ 0x5555555550e0 ◂— endbr64
1d:00e8│+098 0x7fffffffc3b8 —▸ 0x7fffffffc460 ◂— 1
1e:00f0│+0a0 0x7fffffffc3c0 ◂— 0
1f:00f8│+0a8 0x7fffffffc3c8 ◂— 0
20:0100│+0b0 0x7fffffffc3d0 ◂— 0x4e612c65464d0a56 ('V\nMFe,aN')
21:0108│+0b8 0x7fffffffc3d8 ◂— 0x4e613c25e1230a56
22:0110│+0c0 0x7fffffffc3e0 ◂— 0
... ↓ 2 skipped
25:0128│+0d8 0x7fffffffc3f8 ◂— 1
26:0130│+0e0 0x7fffffffc400 —▸ 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
27:0138│+0e8 0x7fffffffc408 —▸ 0x7fffffffc478 —▸ 0x7fffffffc82b ◂— 'SYSTEMD_EXEC_PID=1816'
28:0140│+0f0 0x7fffffffc410 —▸ 0x7ffff7ffe190 —▸ 0x555555554000 ◂— 0x10102464c457f
29:0148│+0f8 0x7fffffffc418 ◂— 0
2a:0150│+100 0x7fffffffc420 ◂— 0
2b:0158│+108 0x7fffffffc428 —▸ 0x5555555550e0 ◂— endbr64
2c:0160│+110 0x7fffffffc430 —▸ 0x7fffffffc460 ◂— 1
2d:0168│+118 0x7fffffffc438 ◂— 0
2e:0170│+120 0x7fffffffc440 ◂— 0
2f:0178│+128 0x7fffffffc448 —▸ 0x55555555510e ◂— hlt
30:0180│+130 0x7fffffffc450 —▸ 0x7fffffffc458 ◂— 0x1c
31:0188│+138 0x7fffffffc458 ◂— 0x1c
32:0190│ r13 0x7fffffffc460 ◂— 1
33:0198│+148 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
34:01a0│+150 0x7fffffffc470 ◂— 0
35:01a8│+158 0x7fffffffc478 —▸ 0x7fffffffc82b ◂— 'SYSTEMD_EXEC_PID=1816'
36:01b0│+160 0x7fffffffc480 —▸ 0x7fffffffc841 ◂— 'SSH_AUTH_SOCK=/run/user/1000/keyring/ssh'
37:01b8│+168 0x7fffffffc488 —▸ 0x7fffffffc86a ◂— 'SESSION_MANAGER=local/ubuntu:@/tmp/.ICE-unix/1816,unix/ubuntu:/tmp/.ICE-unix/1816'
38:01c0│+170 0x7fffffffc490 —▸ 0x7fffffffc8bc ◂— 'PAPERSIZE=a4'
39:01c8│+178 0x7fffffffc498 —▸ 0x7fffffffc8c9 ◂— 'GNOME_TERMINAL_SCREEN=/org/gnome/Terminal/screen/aab6f309_847c_4363_b37f_36574de33f67'
3a:01d0│+180 0x7fffffffc4a0 —▸ 0x7fffffffc91f ◂— 'LANGUAGE=zh_CN:en_GB:en'
3b:01d8│+188 0x7fffffffc4a8 —▸ 0x7fffffffc937 ◂— 'LANG=zh_CN.UTF-8'
3c:01e0│+190 0x7fffffffc4b0 —▸ 0x7fffffffc948 ◂— 'WAYLAND_DISPLAY=wayland-0'
3d:01e8│+198 0x7fffffffc4b8 —▸ 0x7fffffffc962 ◂— 'LC_IDENTIFICATION=zh_CN.UTF-8'
3e:01f0│+1a0 0x7fffffffc4c0 —▸ 0x7fffffffc980 ◂— 'XDG_SESSION_CLASS=user'
3f:01f8│+1a8 0x7fffffffc4c8 —▸ 0x7fffffffc997 ◂— 'XDG_CURRENT_DESKTOP=ubuntu:GNOME'
40:0200│+1b0 0x7fffffffc4d0 —▸ 0x7fffffffc9b8 ◂— 'PWD=/home/a5rz/Desktop/pwn/file'
41:0208│+1b8 0x7fffffffc4d8 —▸ 0x7fffffffc9d8 ◂— 'QT_IM_MODULE=ibus'
42:0210│+1c0 0x7fffffffc4e0 —▸ 0x7fffffffc9ea ◂— 'USER=a5rz'
43:0218│+1c8 0x7fffffffc4e8 —▸ 0x7fffffffc9f4 ◂— 'DESKTOP_SESSION=ubuntu'
44:0220│+1d0 0x7fffffffc4f0 —▸ 0x7fffffffca0b ◂— 'XDG_MENU_PREFIX=gnome-'
45:0228│+1d8 0x7fffffffc4f8 —▸ 0x7fffffffca22 ◂— 'OLDPWD=/home/a5rz/Desktop/pwn/file'
46:0230│+1e0 0x7fffffffc500 —▸ 0x7fffffffca45 ◂— 'LC_MEASUREMENT=zh_CN.UTF-8'
47:0238│+1e8 0x7fffffffc508 —▸ 0x7fffffffca60 ◂— 'DBUS_SESSION_BUS_ADDRESS=unix:path=/run/user/1000/bus,guid=648017a497f89697dfa1bf47674d827a'
48:0240│+1f0 0x7fffffffc510 —▸ 0x7fffffffcabc ◂— 'LC_NUMERIC=zh_CN.UTF-8'
49:0248│+1f8 0x7fffffffc518 —▸ 0x7fffffffcad3 ◂— 'SSH_AGENT_LAUNCHER=gnome-keyring'
4a:0250│+200 0x7fffffffc520 —▸ 0x7fffffffcaf4 ◂— '_=/home/a5rz/Desktop/pwn/file/pwn'
4b:0258│+208 0x7fffffffc528 —▸ 0x7fffffffcb16 ◂— 'GTK_MODULES=gail:atk-bridge'
4c:0260│+210 0x7fffffffc530 —▸ 0x7fffffffcb32 ◂— 'VTE_VERSION=6800'
4d:0268│+218 0x7fffffffc538 —▸ 0x7fffffffcb43 ◂— 'XDG_SESSION_DESKTOP=ubuntu'
4e:0270│+220 0x7fffffffc540 —▸ 0x7fffffffcb5e ◂— 'QT_ACCESSIBILITY=1'
4f:0278│+228 0x7fffffffc548 —▸ 0x7fffffffcb71 ◂— 'GNOME_DESKTOP_SESSION_ID=this-is-deprecated'
50:0280│+230 0x7fffffffc550 —▸ 0x7fffffffcb9d ◂— 'GNOME_SETUP_DISPLAY=:1'
51:0288│+238 0x7fffffffc558 —▸ 0x7fffffffcbb4 ◂— 'LC_TIME=zh_CN.UTF-8'
52:0290│+240 0x7fffffffc560 —▸ 0x7fffffffcbc8 ◂— 'LOGNAME=a5rz'
53:0298│+248 0x7fffffffc568 —▸ 0x7fffffffcbd5 ◂— 'GNOME_TERMINAL_SERVICE=:1.112'
54:02a0│+250 0x7fffffffc570 —▸ 0x7fffffffcbf3 ◂— 'LC_PAPER=zh_CN.UTF-8'
55:02a8│+258 0x7fffffffc578 —▸ 0x7fffffffcc08 ◂— 'HOME=/home/a5rz'
56:02b0│+260 0x7fffffffc580 —▸ 0x7fffffffcc18 ◂— 'GNOME_SHELL_SESSION_MODE=ubuntu'
57:02b8│+268 0x7fffffffc588 —▸ 0x7fffffffcc38 ◂— 'XDG_DATA_DIRS=/usr/local/share/:/usr/share/:/var/lib/snapd/desktop'
58:02c0│+270 0x7fffffffc590 —▸ 0x7fffffffcc7b ◂— 'XMODIFIERS=@im=ibus'
59:02c8│+278 0x7fffffffc598 —▸ 0x7fffffffcc8f ◂— 'XDG_RUNTIME_DIR=/run/user/1000'
pwndbg> ni
aaaaaaaa0x7fffffffc2af0x1(nil)0x180x18(nil)0xf7fc37d0f7fc25c00x61616161616161610x70257025702570250x70257025702570250x70257025702570250x6e696874656d6f53Something
aaaaaaaa
0x7fffffffc2af
0x1
(nil)
0x18
0x18
(nil)
0xf7fc37d0f7fc25c0
0x6161616161616161
0x70257025702570250x70257025702570250x70257025702570250x6e696874656d6f53Something
得知偏移量为8,验证
pwndbg> run
Starting program: /home/a5rz/Desktop/pwn/file/pwn
Please input your name: aaaaaaaa%8$pBreakpoint 2, 0x0000555555555444 in ?? ()
LEGEND: STACK | HEAP | CODE | DATA | WX | RODATA
───────────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]───────────────────────────────────────RAX 0RBX 0x5555555554b0 ◂— endbr64 RCX 0RDX 1RDI 0x7fffffffc2e0 ◂— 0x6161616161616161 ('aaaaaaaa')RSI 0x7fffffffc2af ◂— 0x10000000c0a /* '\n\x0c' */R8 0x18R9 0x18R10 0x555555556008 ◂— 'Please input your name: 'R11 0x246R12 0x5555555550e0 ◂— endbr64 R13 0x7fffffffc460 ◂— 1R14 0R15 0RBP 0x7fffffffc320 —▸ 0x7fffffffc360 —▸ 0x7fffffffc370 ◂— 0RSP 0x7fffffffc2d0 ◂— 0RIP 0x555555555444 ◂— call 0x5555555550b0
────────────────────────────────────────────────[ DISASM / x86-64 / set emulate on ]────────────────────────────────────────────────► 0x555555555444 call printf@plt <printf@plt>format: 0x7fffffffc2e0 ◂— 0x6161616161616161 ('aaaaaaaa')vararg: 0x7fffffffc2af ◂— 0x10000000c0a /* '\n\x0c' */0x555555555449 mov eax, dword ptr [rip + 0x2bfd] EAX, [0x55555555804c]0x55555555544f sub eax, 10x555555555452 mov dword ptr [rip + 0x2bf4], eax0x555555555458 lea rdi, [rip + 0xbd9] RDI => 0x555555556038 ◂— 'There will be a gift for you here . . .'0x55555555545f call puts@plt <puts@plt>0x555555555464 jmp 0x555555555472 <0x555555555472>↓0x555555555472 mov eax, 0 EAX => 00x555555555477 mov rdx, qword ptr [rbp - 8]0x55555555547b xor rdx, qword ptr fs:[0x28]0x555555555484 je 0x55555555548b <0x55555555548b>
─────────────────────────────────────────────────────────────[ STACK ]──────────────────────────────────────────────────────────────
00:0000│ rsp 0x7fffffffc2d0 ◂— 0
01:0008│-048 0x7fffffffc2d8 ◂— 0xf7fc37d0f7fc25c0
02:0010│ rdi 0x7fffffffc2e0 ◂— 0x6161616161616161 ('aaaaaaaa')
03:0018│-038 0x7fffffffc2e8 ◂— 0x7fff70243825
04:0020│-030 0x7fffffffc2f0 ◂— 0
05:0028│-028 0x7fffffffc2f8 —▸ 0x7fffffffc300 ◂— 'Something strange here'
06:0030│-020 0x7fffffffc300 ◂— 'Something strange here'
07:0038│-018 0x7fffffffc308 ◂— 'g strange here'
───────────────────────────────────────────────────────────[ BACKTRACE ]────────────────────────────────────────────────────────────► 0 0x5555555554441 0x5555555553bc2 0x5555555554a93 0x7ffff7df9083 __libc_start_main+2434 0x55555555510e
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> c
Continuing.
aaaaaaaa0x6161616161616161�There will be a gift for you here . . .
[Inferior 1 (process 3806) exited normally]
ebp总是指向上一个ebp,我们可以使用这个特性用第一个ebp改写第二个ebp,再用第二个ebp作为跳板更改栈上任意地址?
pwndbg> stack 60
00:0000│ rsp 0x7fffffffc2d0 ◂— 0
01:0008│-048 0x7fffffffc2d8 ◂— 0xf7fc37d0f7fc25c0
02:0010│ rdi 0x7fffffffc2e0 ◂— 0x30 /* '0' */
03:0018│-038 0x7fffffffc2e8 —▸ 0x7ffff7e67525 ◂— cmp eax, -1
04:0020│-030 0x7fffffffc2f0 ◂— 0
05:0028│-028 0x7fffffffc2f8 —▸ 0x7fffffffc300 ◂— 'Something strange here'
06:0030│-020 0x7fffffffc300 ◂— 'Something strange here'
07:0038│-018 0x7fffffffc308 ◂— 'g strange here'
08:0040│-010 0x7fffffffc310 ◂— 0x657265682065 /* 'e here' */
09:0048│-008 0x7fffffffc318 ◂— 0x1fdd857982303200
0a:0050│ rbp 0x7fffffffc320 —▸ 0x7fffffffc360 —▸ 0x7fffffffc370 ◂— 0
0b:0058│+008 0x7fffffffc328 —▸ 0x5555555553bc ◂— mov eax, 0
0c:0060│+010 0x7fffffffc330 ◂— 'welcome to WuCup !'
0d:0068│+018 0x7fffffffc338 ◂— 'to WuCup !'
0e:0070│+020 0x7fffffffc340 ◂— 0x555555002120 /* ' !' */
0f:0078│+028 0x7fffffffc348 —▸ 0x7fffffffc460 ◂— 1
10:0080│+030 0x7fffffffc350 ◂— 0
11:0088│+038 0x7fffffffc358 ◂— 0x1fdd857982303200
12:0090│+040 0x7fffffffc360 —▸ 0x7fffffffc370 ◂— 0
13:0098│+048 0x7fffffffc368 —▸ 0x5555555554a9 ◂— mov eax, 0
14:00a0│+050 0x7fffffffc370 ◂— 0
15:00a8│+058 0x7fffffffc378 —▸ 0x7ffff7df9083 (__libc_start_main+243) ◂— mov edi, eax
16:00b0│+060 0x7fffffffc380 —▸ 0x7ffff7ffc620 (_rtld_global_ro) ◂— 0x50fa700000000
17:00b8│+068 0x7fffffffc388 —▸ 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
18:00c0│+070 0x7fffffffc390 ◂— 0x100000000
19:00c8│+078 0x7fffffffc398 —▸ 0x55555555548d ◂— endbr64
1a:00d0│+080 0x7fffffffc3a0 —▸ 0x5555555554b0 ◂— endbr64
1b:00d8│+088 0x7fffffffc3a8 ◂— 0x3d68c2224b0eb8ed
1c:00e0│+090 0x7fffffffc3b0 —▸ 0x5555555550e0 ◂— endbr64
1d:00e8│+098 0x7fffffffc3b8 —▸ 0x7fffffffc460 ◂— 1
1e:00f0│+0a0 0x7fffffffc3c0 ◂— 0
1f:00f8│+0a8 0x7fffffffc3c8 ◂— 0
20:0100│+0b0 0x7fffffffc3d0 ◂— 0xc2973dddcc0eb8ed
21:0108│+0b8 0x7fffffffc3d8 ◂— 0xc2972d9d6b60b8ed
22:0110│+0c0 0x7fffffffc3e0 ◂— 0
... ↓ 2 skipped
25:0128│+0d8 0x7fffffffc3f8 ◂— 1
26:0130│+0e0 0x7fffffffc400 —▸ 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
27:0138│+0e8 0x7fffffffc408 —▸ 0x7fffffffc478 —▸ 0x7fffffffc82b ◂— 'SYSTEMD_EXEC_PID=1816'
28:0140│+0f0 0x7fffffffc410 —▸ 0x7ffff7ffe190 —▸ 0x555555554000 ◂— 0x10102464c457f
29:0148│+0f8 0x7fffffffc418 ◂— 0
2a:0150│+100 0x7fffffffc420 ◂— 0
2b:0158│+108 0x7fffffffc428 —▸ 0x5555555550e0 ◂— endbr64
2c:0160│+110 0x7fffffffc430 —▸ 0x7fffffffc460 ◂— 1
2d:0168│+118 0x7fffffffc438 ◂— 0
2e:0170│+120 0x7fffffffc440 ◂— 0
2f:0178│+128 0x7fffffffc448 —▸ 0x55555555510e ◂— hlt
30:0180│+130 0x7fffffffc450 —▸ 0x7fffffffc458 ◂— 0x1c
31:0188│+138 0x7fffffffc458 ◂— 0x1c
32:0190│ r13 0x7fffffffc460 ◂— 1
33:0198│+148 0x7fffffffc468 —▸ 0x7fffffffc80b ◂— '/home/a5rz/Desktop/pwn/file/pwn'
34:01a0│+150 0x7fffffffc470 ◂— 0
35:01a8│+158 0x7fffffffc478 —▸ 0x7fffffffc82b ◂— 'SYSTEMD_EXEC_PID=1816'
36:01b0│+160 0x7fffffffc480 —▸ 0x7fffffffc841 ◂— 'SSH_AUTH_SOCK=/run/user/1000/keyring/ssh'
37:01b8│+168 0x7fffffffc488 —▸ 0x7fffffffc86a ◂— 'SESSION_MANAGER=local/ubuntu:@/tmp/.ICE-unix/1816,unix/ubuntu:/tmp/.ICE-unix/1816'
38:01c0│+170 0x7fffffffc490 —▸ 0x7fffffffc8bc ◂— 'PAPERSIZE=a4'
39:01c8│+178 0x7fffffffc498 —▸ 0x7fffffffc8c9 ◂— 'GNOME_TERMINAL_SCREEN=/org/gnome/Terminal/screen/aab6f309_847c_4363_b37f_36574de33f67'
3a:01d0│+180 0x7fffffffc4a0 —▸ 0x7fffffffc91f ◂— 'LANGUAGE=zh_CN:en_GB:en'
3b:01d8│+188 0x7fffffffc4a8 —▸ 0x7fffffffc937 ◂— 'LANG=zh_CN.UTF-8'
确实没思路了,有没有师傅能发个wp或指点一下?谢谢了,先看看另一道web&pwn了
相关文章:
)
CTF-PWN: 全保护下格式化字符串利用 [第一届“吾杯”网络安全技能大赛 如果能重来] 赛后学习(不会)
通过网盘分享的文件:如果能重来.zip 链接: https://pan.baidu.com/s/1XKIJx32nWVcSpKiWFQGpYA?pwd1111 提取码: 1111 --来自百度网盘超级会员v2的分享漏洞分析 格式化字符串漏洞,在printf(format); __int64 sub_13D7() {char format[56]; // [rsp10h] [rbp-40h]…...

debian 11 虚拟机环境搭建过坑记录
目录 安装过程系统配置修改 sudoers 文件网络配置换源安装桌面mount nfs 挂载安装复制功能tab 无法补全其他安装 软件配置eclipse 配置git 配置老虚拟机硬盘挂载 参考 原来去 debian 官网下载了一个最新的 debian 12,安装后出现包依赖问题,搞了半天&…...

MYSQL 什么是内连接 外连接 左连接 右连接?及适用场景
在 SQL 中,连接(JOIN)是用于组合来自两个或更多表的行的一种方法。根据连接的方式不同,可以分为几种类型的连接:内连接(INNER JOIN)、外连接(OUTER JOIN)、左连接&#x…...

利用Ubuntu批量下载modis图像(New)
由于最近modis原来批量下载的代码不再直接给出,因此,再次梳理如何利用Ubuntu下载modis数据。 之前的下载代码为十分长,现在只给出一部分,需要自己再补充另一部分。之前的为: 感谢郭师兄的指导(https://blo…...

【Springboot】@Autowired和@Resource的区别
【Springboot】Autowired和Resource的区别 【一】定义【1】Autowired【2】Resource 【二】区别【1】包含的属性不同【2】Autowired默认按byType自动装配,而Resource默认byName自动装配【3】注解应用的地方不同【4】出处不同【5】装配顺序不用(1ÿ…...

UIE与ERNIE-Layout:智能视频问答任务初探
内容来自百度飞桨ai社区UIE与ERNIE-Layout:智能视频问答任务初探: 如有侵权,请联系删除 1 环境准备 In [2] # 安装依赖库 !pip install paddlenlp --upgrade !pip install paddleocr --upgrade !pip install paddlespeech --upgrade In …...

数据结构:树
树的基本定义: 树是一种数据结构,它是由n(n>1)个有限节点组成一个具有层次关系的集合。把它叫做 “树” 是因为它看起来像一棵倒挂的树,也就是说它是根朝上,而叶朝下的。它具有以下的特点: …...

docker 怎么启动nginx
在Docker中启动Nginx容器是一个简单的过程。以下是启动Nginx容器的步骤: 拉取Nginx镜像: 首先,你需要从Docker Hub拉取Nginx的官方镜像。使用以下命令: docker pull nginx运行Nginx容器: 使用docker run命令来启动一个…...

【智商检测——DP】
题目 代码 #include <bits/stdc.h> using namespace std; const int N 1e510, M 110; int f[N][M]; int main() {int n, k;cin >> n >> k;for(int i 1; i < n; i){int x;cin >> x;f[i][0] __gcd(f[i-1][0], x);for(int j 1; j < min(i, k)…...

YOLOv11改进,YOLOv11添加SAConv可切换空洞卷积,二次创新C3k2结构
摘要 作者提出的技术结合了递归特征金字塔和可切换空洞卷积,通过强化多尺度特征学习和自适应的空洞卷积,显著提升了目标检测的效果。 理论介绍 空洞卷积(Atrous Convolution)是一种可以在卷积操作中插入“空洞”来扩大感受野的技术,更有效地捕捉到图像中的大范围上下文…...

使用R语言优雅的获取任意区域的POI,道路,河流等数据
POI是“Polnt of Information”的缩写,中文可以翻译为“信息点”。是地图上任何非地理意义的有意义的点,如商店,酒吧,加油站,医院,车站等。POI,道路网,河流等是我们日常研究中经常需…...

【设计模式】工厂方法模式 在java中的应用
文章目录 1. 引言工厂方法模式的定义 2. 工厂方法模式的核心概念工厂方法模式的目的和原理与其他创建型模式的比较(如简单工厂和抽象工厂) 3. Java中工厂方法模式的实现基本的工厂方法模式结构示例代码:创建不同类型的日志记录器 4. 工厂方法…...

Pytest框架学习20--conftest.py
conftest.py作用 正常情况下,如果多个py文件之间需要共享数据,如一个变量,或者调用一个方法 需要先在一个新文件中编写函数等,然后在使用的文件中导入,然后使用 pytest中定义个conftest.py来实现数据,参…...

【面试开放题】挫折、问题、擅长、应用技能
1. 项目中遇到的最大挫折是什么?你是如何应对的? 解答思路: 这个问题通常考察你的问题解决能力、抗压能力和团队协作精神。回答时,可以从以下几个角度展开: 问题背景: 描述项目中遇到的具体挑战。是技术难…...
)
CTF-PWN: 全保护下格式化字符串利用 [第一届“吾杯”网络安全技能大赛 如果能重来] 赛后学习(没思路了)
通过网盘分享的文件:如果能重来.zip 链接: https://pan.baidu.com/s/1XKIJx32nWVcSpKiWFQGpYA?pwd1111 提取码: 1111 --来自百度网盘超级会员v2的分享漏洞分析 格式化字符串漏洞,在printf(format); __int64 sub_13D7() {char format[56]; // [rsp10h] [rbp-40h]…...

C++学习日记---第16天
笔记复习 1.C对象模型 在C中,类内的成员变量和成员函数分开存储 我们知道,C中的成员变量和成员函数均可分为两种,一种是普通的,一种是静态的,对于静态成员变量和静态成员函数,我们知道他们不属于类的对象…...

SOA、分布式、微服务之间的关系和区别?
在当今的软件开发领域,SOA(面向服务架构)、分布式系统和微服务是三个重要的概念。它们各自有着独特的特性和应用场景,同时也存在着密切的关系。以下是关于这三者之间关系和区别的详细分析: 关系 分布式架构的范畴&…...

java基础概念46-数据结构1
一、引入 List集合的三种实现类使用了不同的数据结构! 二、数据结构的定义 三、常见的数据结构 3-1、栈 特点:先进后出,后进先出。 java内存容器: 3-2、队列 特点:先进先出、后进后出。 栈VS队列-小结 3-3、数组 3-…...

Node.js-Mongodb数据库
MongoDB MongoDB是什么? MongoDB是一个基于分布式文件存储的数据库 数据库是什么? 数据库(DataBase)是按照数据结构来组织、存储和管理数据的应用程序(软件) 数据库作用? 对数据进行增、删…...

STM32 ADC --- 知识点总结
STM32 ADC — 知识点总结 文章目录 STM32 ADC --- 知识点总结cubeMX中配置注解单次转换模式、连续转换模式、扫描模式单通道采样的情况单次转换模式:连续转换模式: 多通道采样的情况禁止扫描模式(单次转换模式或连续转换模式)单次…...
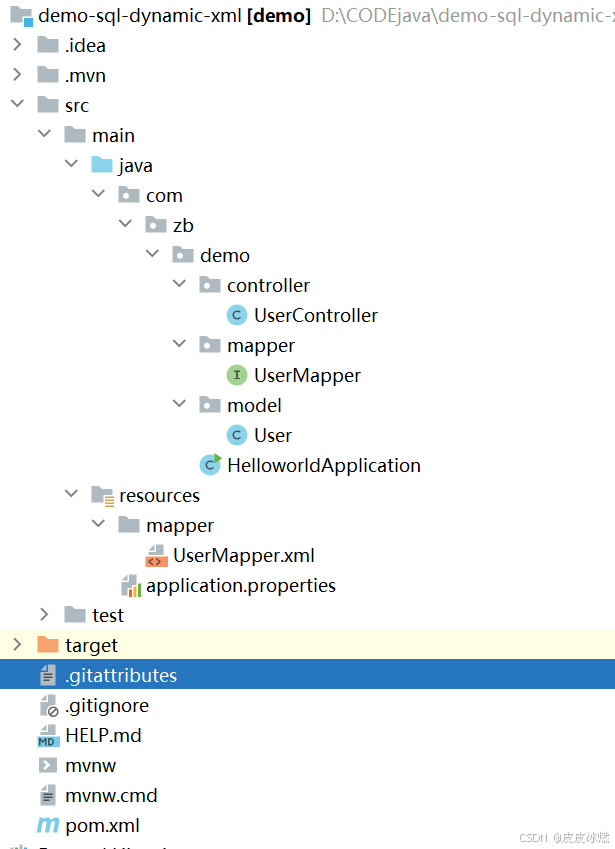
SpringBoot-17-MyBatis动态SQL标签之常用标签
文章目录 1 代码1.1 实体User.java1.2 接口UserMapper.java1.3 映射UserMapper.xml1.3.1 标签if1.3.2 标签if和where1.3.3 标签choose和when和otherwise1.4 UserController.java2 常用动态SQL标签2.1 标签set2.1.1 UserMapper.java2.1.2 UserMapper.xml2.1.3 UserController.ja…...

超短脉冲激光自聚焦效应
前言与目录 强激光引起自聚焦效应机理 超短脉冲激光在脆性材料内部加工时引起的自聚焦效应,这是一种非线性光学现象,主要涉及光学克尔效应和材料的非线性光学特性。 自聚焦效应可以产生局部的强光场,对材料产生非线性响应,可能…...
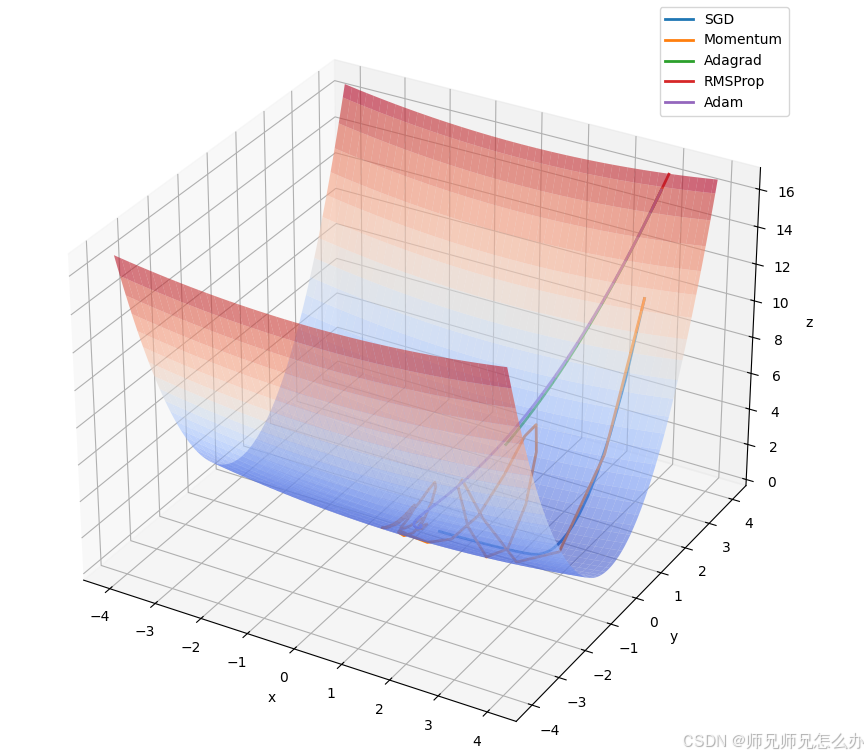
【人工智能】神经网络的优化器optimizer(二):Adagrad自适应学习率优化器
一.自适应梯度算法Adagrad概述 Adagrad(Adaptive Gradient Algorithm)是一种自适应学习率的优化算法,由Duchi等人在2011年提出。其核心思想是针对不同参数自动调整学习率,适合处理稀疏数据和不同参数梯度差异较大的场景。Adagrad通…...
Cesium相机控制)
三维GIS开发cesium智慧地铁教程(5)Cesium相机控制
一、环境搭建 <script src"../cesium1.99/Build/Cesium/Cesium.js"></script> <link rel"stylesheet" href"../cesium1.99/Build/Cesium/Widgets/widgets.css"> 关键配置点: 路径验证:确保相对路径.…...

BCS 2025|百度副总裁陈洋:智能体在安全领域的应用实践
6月5日,2025全球数字经济大会数字安全主论坛暨北京网络安全大会在国家会议中心隆重开幕。百度副总裁陈洋受邀出席,并作《智能体在安全领域的应用实践》主题演讲,分享了在智能体在安全领域的突破性实践。他指出,百度通过将安全能力…...

Unit 1 深度强化学习简介
Deep RL Course ——Unit 1 Introduction 从理论和实践层面深入学习深度强化学习。学会使用知名的深度强化学习库,例如 Stable Baselines3、RL Baselines3 Zoo、Sample Factory 和 CleanRL。在独特的环境中训练智能体,比如 SnowballFight、Huggy the Do…...

全面解析各类VPN技术:GRE、IPsec、L2TP、SSL与MPLS VPN对比
目录 引言 VPN技术概述 GRE VPN 3.1 GRE封装结构 3.2 GRE的应用场景 GRE over IPsec 4.1 GRE over IPsec封装结构 4.2 为什么使用GRE over IPsec? IPsec VPN 5.1 IPsec传输模式(Transport Mode) 5.2 IPsec隧道模式(Tunne…...
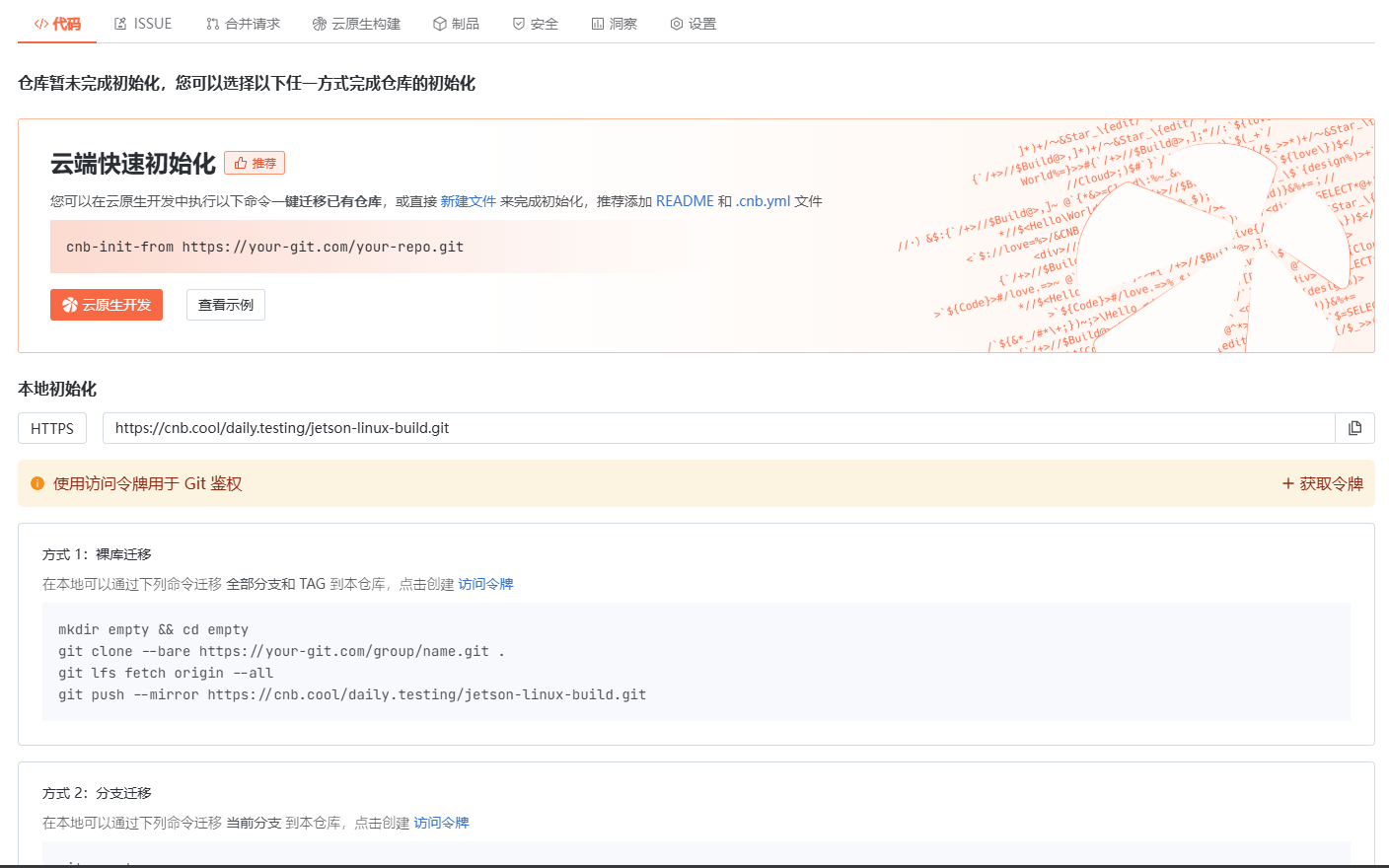
云原生玩法三问:构建自定义开发环境
云原生玩法三问:构建自定义开发环境 引言 临时运维一个古董项目,无文档,无环境,无交接人,俗称三无。 运行设备的环境老,本地环境版本高,ssh不过去。正好最近对 腾讯出品的云原生 cnb 感兴趣&…...

高效线程安全的单例模式:Python 中的懒加载与自定义初始化参数
高效线程安全的单例模式:Python 中的懒加载与自定义初始化参数 在软件开发中,单例模式(Singleton Pattern)是一种常见的设计模式,确保一个类仅有一个实例,并提供一个全局访问点。在多线程环境下,实现单例模式时需要注意线程安全问题,以防止多个线程同时创建实例,导致…...

安宝特方案丨船舶智造的“AR+AI+作业标准化管理解决方案”(装配)
船舶制造装配管理现状:装配工作依赖人工经验,装配工人凭借长期实践积累的操作技巧完成零部件组装。企业通常制定了装配作业指导书,但在实际执行中,工人对指导书的理解和遵循程度参差不齐。 船舶装配过程中的挑战与需求 挑战 (1…...
