K8S应用笔记 —— 签发自签名证书用于Ingress的https配置
一、需求描述
在本地签发自命名证书,用于K8S集群的Ingress的https配置。
前提条件:
- 完成
K8S集群搭建。- 完成证书制作机器的
openssl服务安装。
二、自签名证书制作
2.1 脚本及配置文件准备
2.1.1 CA.sh脚本准备
注意事项:
openssl服务默认CA.sh地址为:/etc/pki/tls/misc/CA.sh,为证书拷贝方便基于原CA.sh进行复制对其原部分路径改写(改为读取同路径下的openssl.cnf文件)。
#!/bin/sh
#
# CA - wrapper around ca to make it easier to use ... basically ca requires
# some setup stuff to be done before you can use it and this makes
# things easier between now and when Eric is convinced to fix it :-)
#
# CA -newca ... will setup the right stuff
# CA -newreq ... will generate a certificate request
# CA -sign ... will sign the generated request and output
#
# At the end of that grab newreq.pem and newcert.pem (one has the key
# and the other the certificate) and cat them together and that is what
# you want/need ... I'll make even this a little cleaner later.
#
#
# 12-Jan-96 tjh Added more things ... including CA -signcert which
# converts a certificate to a request and then signs it.
# 10-Jan-96 eay Fixed a few more bugs and added the SSLEAY_CONFIG
# environment variable so this can be driven from
# a script.
# 25-Jul-96 eay Cleaned up filenames some more.
# 11-Jun-96 eay Fixed a few filename missmatches.
# 03-May-96 eay Modified to use 'ssleay cmd' instead of 'cmd'.
# 18-Apr-96 tjh Original hacking
#
# Tim Hudson
# tjh@cryptsoft.com
## default openssl.cnf file has setup as per the following
# demoCA ... where everything is stored
cp_pem() {infile=$1outfile=$2bound=$3flag=0exec <$infile;while read line; doif [ $flag -eq 1 ]; thenecho $line|grep "^-----END.*$bound" 2>/dev/null 1>/dev/nullif [ $? -eq 0 ] ; thenecho $line >>$outfilebreakelseecho $line >>$outfilefifiecho $line|grep "^-----BEGIN.*$bound" 2>/dev/null 1>/dev/nullif [ $? -eq 0 ]; thenecho $line >$outfileflag=1fidone
}usage() {echo "usage: $0 -newcert|-newreq|-newreq-nodes|-newca|-sign|-verify" >&2
}if [ -z "$OPENSSL" ]; then OPENSSL=openssl; fiif [ -z "$DAYS" ] ; then DAYS="-days 365" ; fi # 1 year
CADAYS="-days 3650" # 10 years
REQ="$OPENSSL req $SSLEAY_CONFIG"
CA="$OPENSSL ca $SSLEAY_CONFIG"
VERIFY="$OPENSSL verify"
X509="$OPENSSL x509"
PKCS12="openssl pkcs12"if [ -z "$CATOP" ] ; then CATOP=./demoCA ; fi
CAKEY=./cakey.pem
CAREQ=./careq.pem
CACERT=./cacert.pemRET=0while [ "$1" != "" ] ; do
case $1 in
-\?|-h|-help)usageexit 0;;
-newcert)# create a certificate$REQ -config openssl.cnf -new -x509 -keyout newkey.pem -out newcert.pem $DAYSRET=$?echo "Certificate is in newcert.pem, private key is in newkey.pem";;
-newreq)# create a certificate request$REQ -config openssl.cnf -new -keyout newkey.pem -out newreq.pem $DAYSRET=$?echo "Request is in newreq.pem, private key is in newkey.pem";;
-newreq-nodes) # create a certificate request$REQ -config openssl.cnf -new -nodes -keyout newreq.pem -out newreq.pem $DAYSRET=$?echo "Request (and private key) is in newreq.pem";;
-newca)# if explicitly asked for or it doesn't exist then setup the directory# structure that Eric likes to manage thingsNEW="1"if [ "$NEW" -o ! -f ${CATOP}/serial ]; then# create the directory hierarchymkdir -p ${CATOP}mkdir -p ${CATOP}/certsmkdir -p ${CATOP}/crlmkdir -p ${CATOP}/newcertsmkdir -p ${CATOP}/privatetouch ${CATOP}/index.txtfiif [ ! -f ${CATOP}/private/$CAKEY ]; thenecho "CA certificate filename (or enter to create)"read FILE# ask user for existing CA certificateif [ "$FILE" ]; thencp_pem $FILE ${CATOP}/private/$CAKEY PRIVATEcp_pem $FILE ${CATOP}/$CACERT CERTIFICATERET=$?if [ ! -f "${CATOP}/serial" ]; then$X509 -config openssl.cnf -in ${CATOP}/$CACERT -noout -next_serial \-out ${CATOP}/serialfielseecho "Making CA certificate ..."$REQ -config openssl.cnf -new -keyout ${CATOP}/private/$CAKEY \-out ${CATOP}/$CAREQ$CA -config openssl.cnf -create_serial -out ${CATOP}/$CACERT $CADAYS -batch \-keyfile ${CATOP}/private/$CAKEY -selfsign \-extensions v3_ca \-infiles ${CATOP}/$CAREQRET=$?fifi;;
-xsign)$CA -config openssl.cnf -policy policy_anything -infiles newreq.pemRET=$?;;
-pkcs12)if [ -z "$2" ] ; thenCNAME="My Certificate"elseCNAME="$2"fi$PKCS12 -config openssl.cnf -in newcert.pem -inkey newreq.pem -certfile ${CATOP}/$CACERT \-out newcert.p12 -export -name "$CNAME"RET=$?exit $RET;;
-sign|-signreq)$CA -config openssl.cnf -policy policy_anything -out newcert.pem -infiles newreq.pemRET=$?cat newcert.pemecho "Signed certificate is in newcert.pem";;
-signCA)$CA -config openssl.cnf -policy policy_anything -out newcert.pem -extensions v3_ca -infiles newreq.pemRET=$?echo "Signed CA certificate is in newcert.pem";;
-signcert)echo "Cert passphrase will be requested twice - bug?"$X509 -config openssl.cnf -x509toreq -in newreq.pem -signkey newreq.pem -out tmp.pem$CA -config openssl.cnf -policy policy_anything -out newcert.pem -infiles tmp.pemRET=$?cat newcert.pemecho "Signed certificate is in newcert.pem";;
-verify)shiftif [ -z "$1" ]; then$VERIFY -CAfile $CATOP/$CACERT newcert.pemRET=$?elsefor jdo$VERIFY -CAfile $CATOP/$CACERT $jif [ $? != 0 ]; thenRET=$?fidonefiexit $RET;;
*)echo "Unknown arg $i" >&2usageexit 1;;
esac
shift
done
exit $RET
命令参数选项 :
-newcert:新证书-newreq:新请求-newreq-nodes:新请求节点-newca:新的CA证书-sign:签证-verify:验证
2.1.2 配置文件openssl.cnf
#
# OpenSSL example configuration file.
# This is mostly being used for generation of certificate requests.
## This definition stops the following lines choking if HOME isn't
# defined.
HOME = .
RANDFILE = $ENV::HOME/.rnd# Extra OBJECT IDENTIFIER info:
#oid_file = $ENV::HOME/.oid
oid_section = new_oids# To use this configuration file with the "-extfile" option of the
# "openssl x509" utility, name here the section containing the
# X.509v3 extensions to use:
# extensions =
# (Alternatively, use a configuration file that has only
# X.509v3 extensions in its main [= default] section.)[ new_oids ]# We can add new OIDs in here for use by 'ca', 'req' and 'ts'.
# Add a simple OID like this:
# testoid1=1.2.3.4
# Or use config file substitution like this:
# testoid2=${testoid1}.5.6# Policies used by the TSA examples.
tsa_policy1 = 1.2.3.4.1
tsa_policy2 = 1.2.3.4.5.6
tsa_policy3 = 1.2.3.4.5.7####################################################################
[ ca ]
default_ca = CA_default # The default ca section####################################################################
[ CA_default ]dir = ./demoCA # Where everything is kept
certs = $dir/certs # Where the issued certs are kept
crl_dir = $dir/crl # Where the issued crl are kept
database = $dir/index.txt # database index file.
#unique_subject = no # Set to 'no' to allow creation of# several ctificates with same subject.
new_certs_dir = $dir/newcerts # default place for new certs.certificate = $dir/cacert.pem # The CA certificate
serial = $dir/serial # The current serial number
crlnumber = $dir/crlnumber # the current crl number# must be commented out to leave a V1 CRL
crl = $dir/crl.pem # The current CRL
private_key = $dir/private/cakey.pem# The private key
RANDFILE = $dir/private/.rand # private random number filex509_extensions = usr_cert # The extentions to add to the cert# Comment out the following two lines for the "traditional"
# (and highly broken) format.
name_opt = ca_default # Subject Name options
cert_opt = ca_default # Certificate field options# Extension copying option: use with caution.
# copy_extensions = copy# Extensions to add to a CRL. Note: Netscape communicator chokes on V2 CRLs
# so this is commented out by default to leave a V1 CRL.
# crlnumber must also be commented out to leave a V1 CRL.
# crl_extensions = crl_extdefault_days = 3650 # how long to certify for
default_crl_days= 30 # how long before next CRL
default_md = default # use public key default MD
preserve = no # keep passed DN ordering# A few difference way of specifying how similar the request should look
# For type CA, the listed attributes must be the same, and the optional
# and supplied fields are just that :-)
policy = policy_match# For the CA policy
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional# For the 'anything' policy
# At this point in time, you must list all acceptable 'object'
# types.
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional####################################################################
[ req ]
default_bits = 2048
default_keyfile = privkey.pem
distinguished_name = req_distinguished_name
attributes = req_attributes
x509_extensions = v3_ca # The extentions to add to the self signed cert# Passwords for private keys if not present they will be prompted for
# input_password = secret
# output_password = secret# This sets a mask for permitted string types. There are several options.
# default: PrintableString, T61String, BMPString.
# pkix : PrintableString, BMPString (PKIX recommendation before 2004)
# utf8only: only UTF8Strings (PKIX recommendation after 2004).
# nombstr : PrintableString, T61String (no BMPStrings or UTF8Strings).
# MASK:XXXX a literal mask value.
# WARNING: ancient versions of Netscape crash on BMPStrings or UTF8Strings.
string_mask = utf8only# req_extensions = v3_req # The extensions to add to a certificate request[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = AU
countryName_min = 2
countryName_max = 2stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Some-StatelocalityName = Locality Name (eg, city)0.organizationName = Organization Name (eg, company)
0.organizationName_default = Internet Widgits Pty Ltd# we can do this but it is not needed normally :-)
#1.organizationName = Second Organization Name (eg, company)
#1.organizationName_default = World Wide Web Pty LtdorganizationalUnitName = Organizational Unit Name (eg, section)
#organizationalUnitName_default =commonName = Common Name (e.g. server FQDN or YOUR name)
commonName_max = 64emailAddress = Email Address
emailAddress_max = 64# SET-ex3 = SET extension number 3[ req_attributes ]
challengePassword = A challenge password
challengePassword_min = 4
challengePassword_max = 20unstructuredName = An optional company name[ usr_cert ]# These extensions are added when 'ca' signs a request.# This goes against PKIX guidelines but some CAs do it and some software
# requires this to avoid interpreting an end user certificate as a CA.basicConstraints=CA:FALSE# Here are some examples of the usage of nsCertType. If it is omitted
# the certificate can be used for anything *except* object signing.# This is OK for an SSL server.
# nsCertType = server# For an object signing certificate this would be used.
# nsCertType = objsign# For normal client use this is typical
# nsCertType = client, email# and for everything including object signing:
# nsCertType = client, email, objsign# This is typical in keyUsage for a client certificate.
# keyUsage = nonRepudiation, digitalSignature, keyEncipherment# This will be displayed in Netscape's comment listbox.
nsComment = "OpenSSL Generated Certificate"# PKIX recommendations harmless if included in all certificates.
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer# This stuff is for subjectAltName and issuerAltname.
# Import the email address.
# subjectAltName=email:copy
# An alternative to produce certificates that aren't
# deprecated according to PKIX.
# subjectAltName=email:move# Copy subject details
# issuerAltName=issuer:copy#nsCaRevocationUrl = http://www.domain.dom/ca-crl.pem
#nsBaseUrl
#nsRevocationUrl
#nsRenewalUrl
#nsCaPolicyUrl
#nsSslServerName# This is required for TSA certificates.
# extendedKeyUsage = critical,timeStamping[ v3_req ]# Extensions to add to a certificate requestbasicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment[ v3_ca ]# Extensions for a typical CA# PKIX recommendation.subjectKeyIdentifier=hashauthorityKeyIdentifier=keyid:always,issuer# This is what PKIX recommends but some broken software chokes on critical
# extensions.
#basicConstraints = critical,CA:true
# So we do this instead.
basicConstraints = CA:true# Key usage: this is typical for a CA certificate. However since it will
# prevent it being used as an test self-signed certificate it is best
# left out by default.
# keyUsage = cRLSign, keyCertSign# Some might want this also
# nsCertType = sslCA, emailCA# Include email address in subject alt name: another PKIX recommendation
# subjectAltName=email:copy
subjectAltName=@alt_names
[alt_names]
DNS.1 = nginx.local
DNS.2 = *.nginx.local
IP.1 = 192.168.0.50
IP.2 = 192.168.0.51# Copy issuer details
# issuerAltName=issuer:copy# DER hex encoding of an extension: beware experts only!
# obj=DER:02:03
# Where 'obj' is a standard or added object
# You can even override a supported extension:
# basicConstraints= critical, DER:30:03:01:01:FF[ crl_ext ]# CRL extensions.
# Only issuerAltName and authorityKeyIdentifier make any sense in a CRL.# issuerAltName=issuer:copy
authorityKeyIdentifier=keyid:always[ proxy_cert_ext ]
# These extensions should be added when creating a proxy certificate# This goes against PKIX guidelines but some CAs do it and some software
# requires this to avoid interpreting an end user certificate as a CA.basicConstraints=CA:FALSE# Here are some examples of the usage of nsCertType. If it is omitted
# the certificate can be used for anything *except* object signing.# This is OK for an SSL server.
# nsCertType = server# For an object signing certificate this would be used.
# nsCertType = objsign# For normal client use this is typical
# nsCertType = client, email# and for everything including object signing:
# nsCertType = client, email, objsign# This is typical in keyUsage for a client certificate.
# keyUsage = nonRepudiation, digitalSignature, keyEncipherment# This will be displayed in Netscape's comment listbox.
nsComment = "OpenSSL Generated Certificate"# PKIX recommendations harmless if included in all certificates.
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer# This stuff is for subjectAltName and issuerAltname.
# Import the email address.
# subjectAltName=email:copy
# An alternative to produce certificates that aren't
# deprecated according to PKIX.
# subjectAltName=email:move# Copy subject details
# issuerAltName=issuer:copy#nsCaRevocationUrl = http://www.domain.dom/ca-crl.pem
#nsBaseUrl
#nsRevocationUrl
#nsRenewalUrl
#nsCaPolicyUrl
#nsSslServerName# This really needs to be in place for it to be a proxy certificate.
proxyCertInfo=critical,language:id-ppl-anyLanguage,pathlen:3,policy:foo####################################################################
[ tsa ]default_tsa = tsa_config1 # the default TSA section[ tsa_config1 ]# These are used by the TSA reply generation only.
dir = ./demoCA # TSA root directory
serial = $dir/tsaserial # The current serial number (mandatory)
crypto_device = builtin # OpenSSL engine to use for signing
signer_cert = $dir/tsacert.pem # The TSA signing certificate# (optional)
certs = $dir/cacert.pem # Certificate chain to include in reply# (optional)
signer_key = $dir/private/tsakey.pem # The TSA private key (optional)default_policy = tsa_policy1 # Policy if request did not specify it# (optional)
other_policies = tsa_policy2, tsa_policy3 # acceptable policies (optional)
digests = md5, sha1 # Acceptable message digests (mandatory)
accuracy = secs:1, millisecs:500, microsecs:100 # (optional)
clock_precision_digits = 0 # number of digits after dot. (optional)
ordering = yes # Is ordering defined for timestamps?# (optional, default: no)
tsa_name = yes # Must the TSA name be included in the reply?# (optional, default: no)
ess_cert_id_chain = no # Must the ESS cert id chain be included?# (optional, default: no)
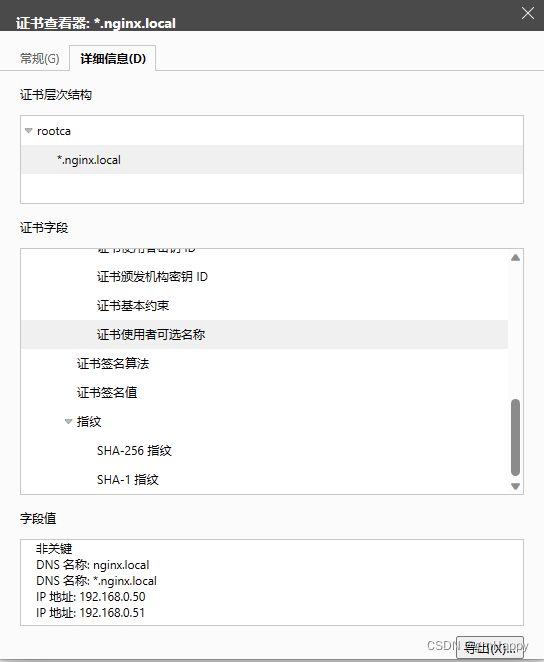
通过以下配置:
subjectAltName=@alt_names
[alt_names]
DNS.1 = nginx.local
DNS.2 = *.nginx.local
IP.1 = 192.168.0.50
IP.2 = 192.168.0.51
指定扩展属性(证书使用者可选名称)为:指定主域名、泛域名和本地IP。
最新效果:
2.2 生成根CA
[root@k8s-master openssl-CA]# sh CA.sh -newca
CA certificate filename (or enter to create)Making CA certificate ...
Generating a 2048 bit RSA private key
...................+++
...............................................................................................................+++
writing new private key to './demoCA/private/./cakey.pem'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:Heilongjiang
Locality Name (eg, city) []:haerbin
Organization Name (eg, company) [Internet Widgits Pty Ltd]:IT
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:rootca
Email Address []:Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from openssl.cnf
Enter pass phrase for ./demoCA/private/./cakey.pem:
139713450506128:error:28069065:lib(40):UI_set_result:result too small:ui_lib.c:831:You must type in 4 to 1023 characters
Enter pass phrase for ./demoCA/private/./cakey.pem:
139713450506128:error:28069065:lib(40):UI_set_result:result too small:ui_lib.c:831:You must type in 4 to 1023 characters
Enter pass phrase for ./demoCA/private/./cakey.pem:
139713450506128:error:28069065:lib(40):UI_set_result:result too small:ui_lib.c:831:You must type in 4 to 1023 characters
Enter pass phrase for ./demoCA/private/./cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:Serial Number:e7:e3:fc:9f:64:e6:9c:c2ValidityNot Before: Aug 18 06:15:34 2023 GMTNot After : Aug 15 06:15:34 2033 GMTSubject:countryName = CNstateOrProvinceName = HeilongjiangorganizationName = ITcommonName = rootcaX509v3 extensions:X509v3 Subject Key Identifier: 99:D0:C2:47:62:E4:16:CE:83:2D:21:83:2C:21:6A:A9:63:7D:03:AAX509v3 Authority Key Identifier: keyid:99:D0:C2:47:62:E4:16:CE:83:2D:21:83:2C:21:6A:A9:63:7D:03:AAX509v3 Basic Constraints: CA:TRUEX509v3 Subject Alternative Name: DNS:nginx.local, DNS:*.nginx.local, IP Address:192.168.0.50, IP Address:192.168.0.51
Certificate is to be certified until Aug 15 06:15:34 2033 GMT (3650 days)Write out database with 1 new entries
Data Base Updated
[root@k8s-master openssl-CA]#
注意事项:
- 提示
Enter PEM pass phrase:时输入密码,自定义,请记住后续还需使用。
2.3 产生证书请求
[root@k8s-master openssl-CA]# sh CA.sh -newreq
Generating a 2048 bit RSA private key
..................................................+++
....................+++
writing new private key to 'newkey.pem'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:Heilong
Locality Name (eg, city) []:haerbin
Organization Name (eg, company) [Internet Widgits Pty Ltd]:IT
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:*.nginx.local
Email Address []:Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:
Request is in newreq.pem, private key is in newkey.pem
[root@k8s-master openssl-CA]#
注意事项:
- 提示
Common Name (e.g. server FQDN or YOUR name) []:时我输入的为*.nginx.local泛域名。
2.4 签发证书
[root@k8s-master openssl-CA]# sh CA.sh -signCA
Using configuration from openssl.cnf
Enter pass phrase for ./demoCA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:Serial Number:e7:e3:fc:9f:64:e6:9c:c3ValidityNot Before: Aug 18 06:20:48 2023 GMTNot After : Aug 15 06:20:48 2033 GMTSubject:countryName = CNstateOrProvinceName = HeilonglocalityName = haerbinorganizationName = ITcommonName = *.nginx.localX509v3 extensions:X509v3 Subject Key Identifier: 3E:AD:81:4C:AA:85:3E:D6:78:83:5B:63:3D:CA:A5:F2:59:97:42:14X509v3 Authority Key Identifier: keyid:99:D0:C2:47:62:E4:16:CE:83:2D:21:83:2C:21:6A:A9:63:7D:03:AAX509v3 Basic Constraints: CA:TRUEX509v3 Subject Alternative Name: DNS:nginx.local, DNS:*.nginx.local, IP Address:192.168.0.50, IP Address:192.168.0.51
Certificate is to be certified until Aug 15 06:20:48 2033 GMT (3650 days)
Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
Signed CA certificate is in newcert.pem
[root@k8s-master openssl-CA]#
2.5 导出私钥
注意事项:
- 避免出现:服务启动提示输入:
PEM pass phrase情况,故将私钥导出。
[root@k8s-master openssl-CA]# openssl rsa -in newkey.pem -out nginx.local.key
Enter pass phrase for newkey.pem:
writing RSA key
2.6 导出证书
[root@k8s-master openssl-CA]# openssl x509 -in newcert.pem -out nginx.local.pem
[root@k8s-master openssl-CA]#
2.7 导出Windows平台能安装的根证书
[root@k8s-master openssl-CA]# cd demoCA/
[root@k8s-master demoCA]# openssl x509 -in cacert.pem -out cacert.crt
[root@k8s-master demoCA]# cd ..
[root@k8s-master openssl-CA]#
2.8 导出Linux平台能安装的根证书
[root@k8s-master openssl-CA]# openssl x509 -in demoCA/cacert.pem -out ca.pem
[root@k8s-master openssl-CA]#
查看根证书ca.pem
切换root权限,将根证书内容追加到受信任根证书列表配置文件
[root@k8s-master openssl-CA]#
[root@k8s-master openssl-CA]# cat ca.pem >> /etc/pki/tls/certs/ca-bundle.crt
三、自签名证书写入secret
kubectl create secret tls nginx.local --key nginx.local.key --cert nginx.local.pem
四、Deployment具体配置
完整配置文件myapp-deployment.yaml:
---
kind: Deployment
apiVersion: apps/v1
metadata:name: myappnamespace: defaultannotations: {}
spec:replicas: 5selector:matchLabels:app: myapprelease: canarytemplate:metadata:creationTimestamp: nulllabels:app: myapprelease: canaryspec:containers:- name: myappimage: 'ikubernetes/myapp:v2'ports:- name: httpdcontainerPort: 80protocol: TCPresources: {}terminationMessagePath: /dev/termination-logterminationMessagePolicy: FileimagePullPolicy: IfNotPresentrestartPolicy: AlwaysterminationGracePeriodSeconds: 30dnsPolicy: ClusterFirstsecurityContext: {}schedulerName: default-schedulerstrategy:type: RollingUpdaterollingUpdate:maxUnavailable: 25%maxSurge: 25%revisionHistoryLimit: 10progressDeadlineSeconds: 600---
kind: Service
apiVersion: v1
metadata:name: myappnamespace: defaultannotations: {}
spec:ports:- name: httpprotocol: TCPport: 80targetPort: 80selector:app: myapprelease: canarytype: ClusterIPsessionAffinity: NoneipFamilies:- IPv4ipFamilyPolicy: SingleStackinternalTrafficPolicy: Cluster---
kind: Ingress
apiVersion: networking.k8s.io/v1
metadata:name: myappnamespace: default
spec:ingressClassName: nginx-ingresstls:- hosts:- myapp.nginx.localsecretName: nginx.localrules:- host: myapp.nginx.localhttp:paths:- path: /pathType: Prefixbackend:service:name: myappport:number: 80---
kind: Secret
apiVersion: v1
metadata:name: nginx.localnamespace: default
data:tls.crt: >-LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURvRENDQW9pZ0F3SUJBZ0lKQU9mai9KOWs1cHpETUEwR0NTcUdTSWIzRFFFQkN3VUFNRUl4Q3pBSkJnTlYKQkFZVEFrTk9NUlV3RXdZRFZRUUlEQXhJWldsc2IyNW5hbWxoYm1jeEN6QUpCZ05WQkFvTUFrbFVNUTh3RFFZRApWUVFEREFaeWIyOTBZMkV3SGhjTk1qTXdPREU0TURZeU1EUTRXaGNOTXpNd09ERTFNRFl5TURRNFdqQldNUXN3CkNRWURWUVFHRXdKRFRqRVFNQTRHQTFVRUNBd0hTR1ZwYkc5dVp6RVFNQTRHQTFVRUJ3d0hhR0ZsY21KcGJqRUwKTUFrR0ExVUVDZ3dDU1ZReEZqQVVCZ05WQkFNTURTb3VibWRwYm5ndWJHOWpZV3d3Z2dFaU1BMEdDU3FHU0liMwpEUUVCQVFVQUE0SUJEd0F3Z2dFS0FvSUJBUUR1ZC83R0FSdlFzaHkwVnBrTE5Uam1pSzBTcThZdHhOQTFUbXNDCnQvT3RWR3k1NEVzVWUwdklManBWSFZ1UDhXZ0hFcWZia2RjdUlGTkJWeFVkcU5jZlpjeDhtOEZOclNtbS9HdUkKL0FsdjhWRTBtcFpqLzlvbXlOWURmbUw2dSs2b1RYbXJjSVU3N25IbGJRdkFzYkxEN2lmMUY5ODBTR3NPZnltMAplaXVMRmtwTFFvNGQxekdPOWVrbWg0L0FyQkwxREcycEpuTFZ4Y3lBeHhxS0MzaDd4RHFPNStTWVNWa1dhZWhNCmhpNlJOdXdQQmMvM0I5bzRZRm1xV2RlYTMxdlJtUW1nQ3picEF4WWQ4NFdNSWNKSVlJYXIwN1hOYlV2TE8zdjcKbmcwVTIyT080NFJmOFRONTdFN0JjZ0twS3dGMTZuakk5WHdLRWFON0h1a0ovOEZ2QWdNQkFBR2pnWVF3Z1lFdwpIUVlEVlIwT0JCWUVGRDZ0Z1V5cWhUN1dlSU5iWXozS3BmSlpsMElVTUI4R0ExVWRJd1FZTUJhQUZKblF3a2RpCjVCYk9neTBoZ3l3aGFxbGpmUU9xTUF3R0ExVWRFd1FGTUFNQkFmOHdNUVlEVlIwUkJDb3dLSUlMYm1kcGJuZ3UKYkc5allXeUNEU291Ym1kcGJuZ3ViRzlqWVd5SEJNQ29BREtIQk1Db0FETXdEUVlKS29aSWh2Y05BUUVMQlFBRApnZ0VCQUJhOXFBQVFIQm1WNFhyMWk4d3N6cXdLdXh3eXA4UWF5Z1p5aVAycGh0UytNWjVnWlN2WkVUMW55SHJRCllNbTVIeGpZaGVFSWdhUU5Fck9TRnRpbTJ0UUpNbmdkM3dvNEgvS3QvNzJYazc1ZnJXVXlUa1dFbGVDQVBXdXoKUXEweHpqdHdzeThXR2hMWW1KVFFVRnIrcU1qcjV5UTJhRUhMZ2FrU3dIUFdTdmlqRm1Lcmd5enc3MTlnay96egpybm5pRnZ0dHo5S1dtTXBXOUUrc0drVUhYWEhRY2pTbklNNmZwUzB4amhiS09HcHNSbDJlanUwN3JMNjQwRzhlClFBT1VaYXphNW9nVW5RRU93Wm5XQW5iZVp6ZGhBSVhsV1lRV3BKVFIzT2lZMnZkUmdMZ3lqRXAxVG5OK0JBRWQKOWlkYldEQTdtWDYyTGtuSS82VVlyWVpEMGIwPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==tls.key: >-LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBN25mK3hnRWIwTEljdEZhWkN6VTQ1b2l0RXF2R0xjVFFOVTVyQXJmenJWUnN1ZUJMCkZIdEx5QzQ2VlIxYmovRm9CeEtuMjVIWExpQlRRVmNWSGFqWEgyWE1mSnZCVGEwcHB2eHJpUHdKYi9GUk5KcVcKWS8vYUpzaldBMzVpK3J2dXFFMTVxM0NGTys1eDVXMEx3TEd5dys0bjlSZmZORWhyRG44cHRIb3JpeFpLUzBLTwpIZGN4anZYcEpvZVB3S3dTOVF4dHFTWnkxY1hNZ01jYWlndDRlOFE2anVma21FbFpGbW5vVElZdWtUYnNEd1hQCjl3ZmFPR0JacWxuWG10OWIwWmtKb0FzMjZRTVdIZk9GakNIQ1NHQ0dxOU8xelcxTHl6dDcrNTRORk50amp1T0UKWC9FemVleE93WElDcVNzQmRlcDR5UFY4Q2hHamV4N3BDZi9CYndJREFRQUJBb0lCQUV6b1JqSjFpUkwxWG15Swp3VERzS1Qyd05xRWU1UHM5emloaThnQWVjMmdqSWkyUU9LYVNYUTVpV2syNCtoNmlMSHFiZWFkR2thOCtuWnNsCkNwcFdLWXJtdWR3MkgxRjkxMEVUaDFyV2JmUzhUd1E0RnVpSlMwSFc0NjZjeEM4NURPOGFqWExOQnlzYzYzNmkKZkhmWTExNTVJRW5iT1JFVGlmTlM3NUJWRmxYMGF1N2QrWG1TNE1kbW9Md3E5NUExbG1rUFVjOUxoSWdoTWZjaApMdythMnFSM0wva0hCQWJESGM1Tng0WFQrR2YycnpCOXRpUit2TkpacjkzNDZXb2JiMVZvOWZrcWxKTVdzaUd1Cmp3T1ZoM096VEtib05DaVl2aWJIYnFUU1NlTXhkUVlORllIMDQ0TjArNndzRjA0MzJBWll3SERHaWxPNGg3ZUQKU3d3YVFnRUNnWUVBL3VEWmhCek5KVit1dlMzQkgydm9wT3NUWGFsVko3aXY1b1pHRXc1bVVicWxkL3pZWUtSSAoyRTFUdE0vOTNjRDRNNi8wRHNsMDArWjkvWDZpdWpaNlZadkJnaWhjTnNNb3p1akt2NTNlL0JiTC9jUy95VjBLCnR5RnpSNVJ4cXBQZUxJUDVEbGJQZUk4LzhzTys3OUMyWFlHaTM2aytXYlZtNURodUNwNXV4TjhDZ1lFQTc0U28KZ0lPQmZnS2RzdEZMSkRxaXl1SEoxdGpseWdEcWozSTZ6U1JSZ0s2d0RQdjdBbFUwQnhFSmlMWWt1a2t1dmhrbAoxQ1NaeXA1YWZBM0QwTTY2WDFnOGpRL04xMGt1SUlxZENsQkR6YVBKb1RKbmdnbUV6TjV0RG5jTmxsKzJrekpzCmpMaVUrSEVQK3JGeDZzeWxBMUowRnBZSnY4S0RSTWgzM09DTmhYRUNnWUJnUVM0a05IUk0vdnVRdWl6SzN3ZTIKOElnWndROUZ0dnZIQlVLRmc5U2tYT2FNajlKdmZOc2RGdWJiekFqRnJGQ1B4STFZNEQvY25wbEtHSDcvNy83MwpRYUVzdEcxT3lSa3FPc1FHNVdvR3JkMVA4dk95Nmc1WDVxd1Foa0QrK0dUWlR1WEp3b01MdHAyaDRzYkM3b0ZRCmd0cXR1TTZ4Tms2ck5aeHBLamdPNVFLQmdRQ2xSTzhVQmluQzdrRXNVdmc3WG01WCthWlJKa2FndFRNa21kaHoKRnIxYVFxOWR0ajFFSmRDSms3cjFaMkUrWFNMd3J0K0lXMXozRDM4MkhEVmlqbExSV1V3bXRhSCtEQlBWQm5CSAozb3g2aDZxb0hPU0pPTkkybnIrM2ZIU1dyeUtHdlFOanNqV3duQ3MvZTFNMGhkTFMwUUVqV0pJUGpFTVJvaFg3CkJjTUJNUUtCZ0gvTU8wTEkzN3ZKeDg2U00xSVhVeVFmVzlTYjlBNHpkc1FqanJ1OUtYVjU0NW01R09QMUY5aEQKVDhFdmh2RkN6cno5ZmRuWitTcWo2OFB0UWtDbFdkSGd5Y2pFaXFDUjNJU1hHYmZVNkhwWVVaZitvajVPS0NsRgpMQXdHVi9kWnU5RjVTVlBUQjEwNk0wS0tCUldHaW5aVXdLUXJwZzBMZDQvNkR0cDVoNk12Ci0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==
type: kubernetes.io/tls
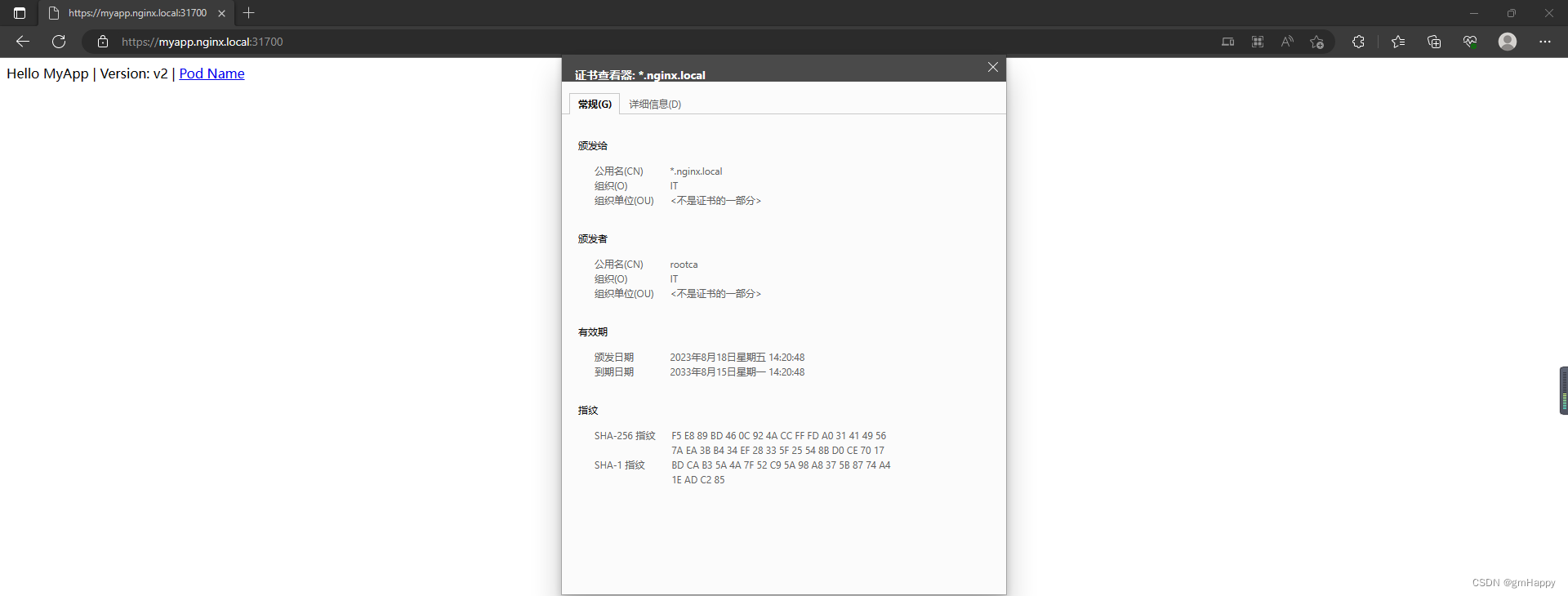
五、效果
将导出Windows平台能安装的根证书进行安装。最后效果:
相关文章:

K8S应用笔记 —— 签发自签名证书用于Ingress的https配置
一、需求描述 在本地签发自命名证书,用于K8S集群的Ingress的https配置。 前提条件: 完成K8S集群搭建。完成证书制作机器的openssl服务安装。 二、自签名证书制作 2.1 脚本及配置文件准备 2.1.1 CA.sh脚本准备 注意事项: openssl服务默认CA…...
webpack 和 ts 简单配置及使用
如何使用webpack 与 ts结合使用 新建项目 ,执行项目初始化 npm init -y会生成 {"name": "tsdemo01","version": "1.0.0","description": "","main": "index.js","scripts&…...

MATLAB算法实战应用案例精讲-【图像处理】交并比
目录 交并比 非极大值抑制 Soft NMS Soft NMS 提出背景 Soft NMS 算法流程 Soft NMS 算法示例...
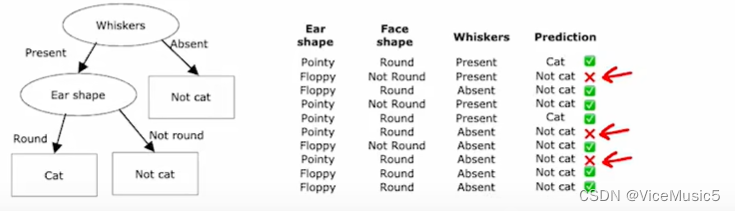
[Machine Learning] decision tree 决策树
(为了节约时间,后面关于机器学习和有关内容哦就是用中文进行书写了,如果有需要的话,我在目前手头项目交工以后,用英文重写一遍) (祝,本文同时用于比赛学习笔记和机器学习基础课程&a…...
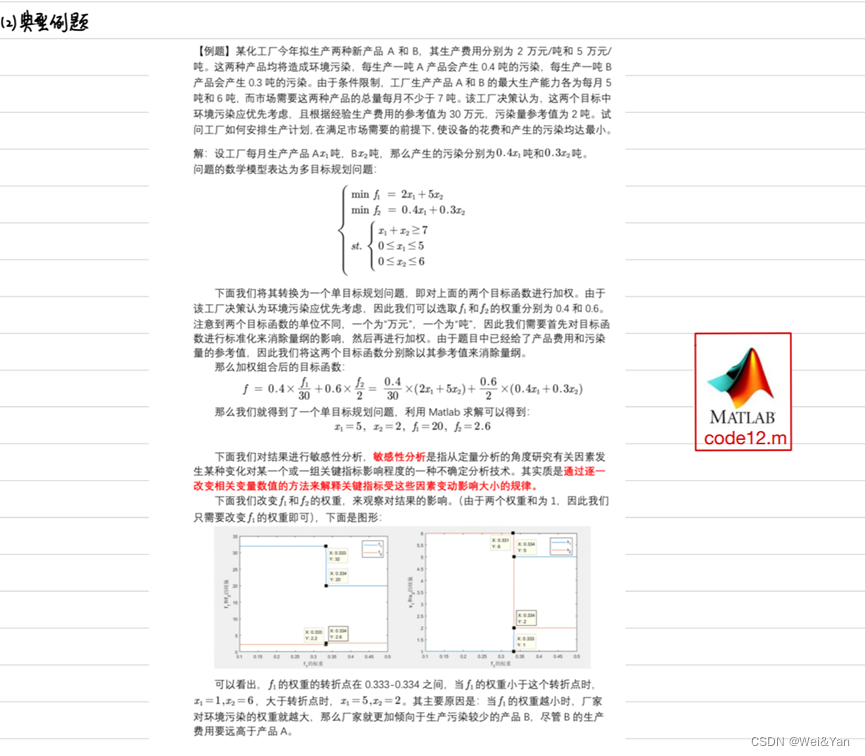
【数学建模】-- 数学规划模型
概述: 什么是数学规划? 数学建模中的数学规划是指利用数学方法和技巧对问题进行数学建模,并通过数学规划模型求解最优解的过程。数学规划是一种数学优化方法,旨在找到使目标函数达到最大值或最小值的变量取值,同时满足…...

SpringBoot使用RabbitMQ自动创建Exchange和Queue
背景 小项目,使用RabbitMQ作为消息队列,发布到不同的新环境时,由于新搭建的MQ中不存在Exchange和Queue,就会出错,还得手动去创建,比较麻烦,于是想在代码中将这些定义好后,自动控制M…...
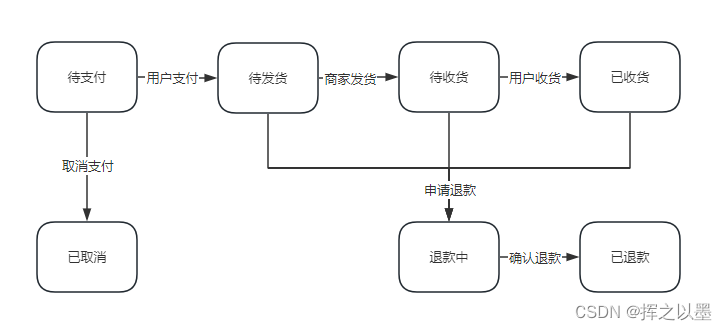
【设计模式】订单状态流传中的状态机与状态模式
文章目录 1. 前言2.状态模式2.1.订单状态流转案例2.1.1.状态枚举定义2.1.2.状态接口与实现2.1.3.状态机2.1.4.测试 2.2.退款状态的拓展2.2.1.代码拓展2.2.2.测试 2.3.小结 3.总结 1. 前言 状态模式一般是用在对象内部的状态流转场景中,用来实现状态机。 什么是状态…...
用来修改或者添加属性或者属性值)
2.js中attr()用来修改或者添加属性或者属性值
attr()可以用来修改或者添加属性或者属性值 例:<input type"button" class"btn btn-info" id"subbtn" style"font-size:12px" value"我也说一句"/>1.如果想获取input中value的值 $(#subbtn).attr(value);…...
【虫洞攻击检测】使用多层神经网络的移动自组织网络中的虫洞攻击检测研究(Matlab代码实现)
💥💥💞💞欢迎来到本博客❤️❤️💥💥 🏆博主优势:🌞🌞🌞博客内容尽量做到思维缜密,逻辑清晰,为了方便读者。 ⛳️座右铭&a…...

微分流形学习之一:基本定义
微分流形学习之一:基本定义引入 引言一、微分流形的历史简介二、拓扑空间三、微分流形 引言 本文是作者在学习微分流形的时候的笔记,尽量严格完整,并带有一定理解,绝不是结论的简单罗列。如果读者知道数学分析中的 ϵ − δ \ep…...
[C++]笔记-制作自己的静态库
一.静态库的创建 在项目属性c/c里面,选用无预编译头,创建头文件与cpp文件,需要注意release模式下还是debug模式,在用库时候要与该模式相匹配,库的函数实现是外界无法看到的,最后在要使用的项目里面导入.h文件和.lib文件 二.使用一个循环给二维数组赋值 行数 : 第几个元素 / …...

优酷视频码率、爱奇艺视频码率、B站视频码率、抖音视频码率对比
优酷视频码率、爱奇艺视频码率与YouTube视频码率对比 优酷视频码率: 优酷的视频码率可以根据视频质量、分辨率和内容类型而变化。一般而言,优酷提供了不同的码率选项,包括较低的标清(SD)码率和较高的高清(…...
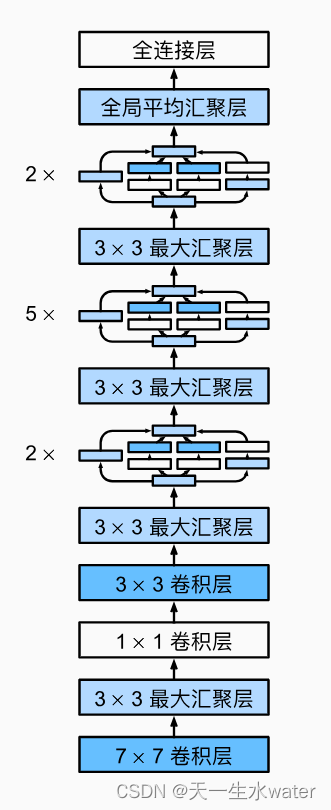
用pytorch实现google net
GoogleNet(也称为Inception v1)是由Google在2014年提出的一个深度卷积神经网络架构。它在ImageNet Large Scale Visual Recognition Challenge (ILSVRC) 2014比赛中取得了优秀的成绩,并引起了广泛的关注。 GoogleNet的设计目标是构建一个更…...

2023-8-15差分矩阵
题目链接:差分矩阵 #include <iostream>using namespace std;const int N 1010;int n, m, q; int a[N][N], b[N][N];void insert(int x1, int y1, int x2, int y2, int c) {b[x1][y1] c;b[x1][y2 1] - c;b[x2 1][y1] - c;b[x2 1][y2 1] c; }int main…...

物理公式分类
(99 封私信 / 81 条消息) 定义式和决定式有什么区别,怎么区分? - 知乎 (zhihu.com) 1、首先,定义一个物理符号(物理量)来表征物理世界最直观/最基本的物理现象,例如,长度(米…...

vue实现登录注册
目录 一、登录页面 二、注册页面 三、配置路由 一、登录页面 <template><div class"login_container" style"background-color: rgb(243,243,243);height: 93.68vh;background-image: url(https://ts1.cn.mm.bing.net/th/id/R-C.f878c96c4179c501a6…...
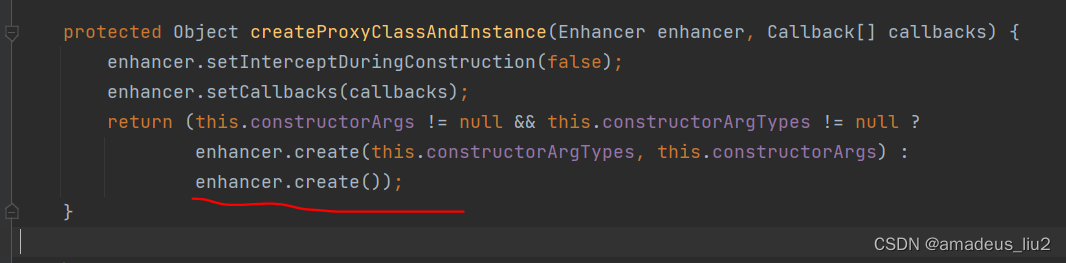
SpringBoot复习:(55)在service类中的方法上加上@Transactional注解后,Spring底层是怎么生成代理对象的?
SpringBoot run方法代码如下: 可以看到它会调用refreshContext方法来刷新Spring容器,这个refreshContext方法最终会调用AbstractApplicationContext的refresh方法,代码如下 如上图,refresh方法最终会调用finisheBeanFactoryInit…...

常用的图像校正方法
在数字图像处理中,常用的校正方法包括明场均匀性校正、查找表(LUT)校正和伽玛(Gamma)校正。这些校正方法分别针对不同的图像问题,可以改善图像质量,提升图像的可读性和可分析性。下面是这三种校…...
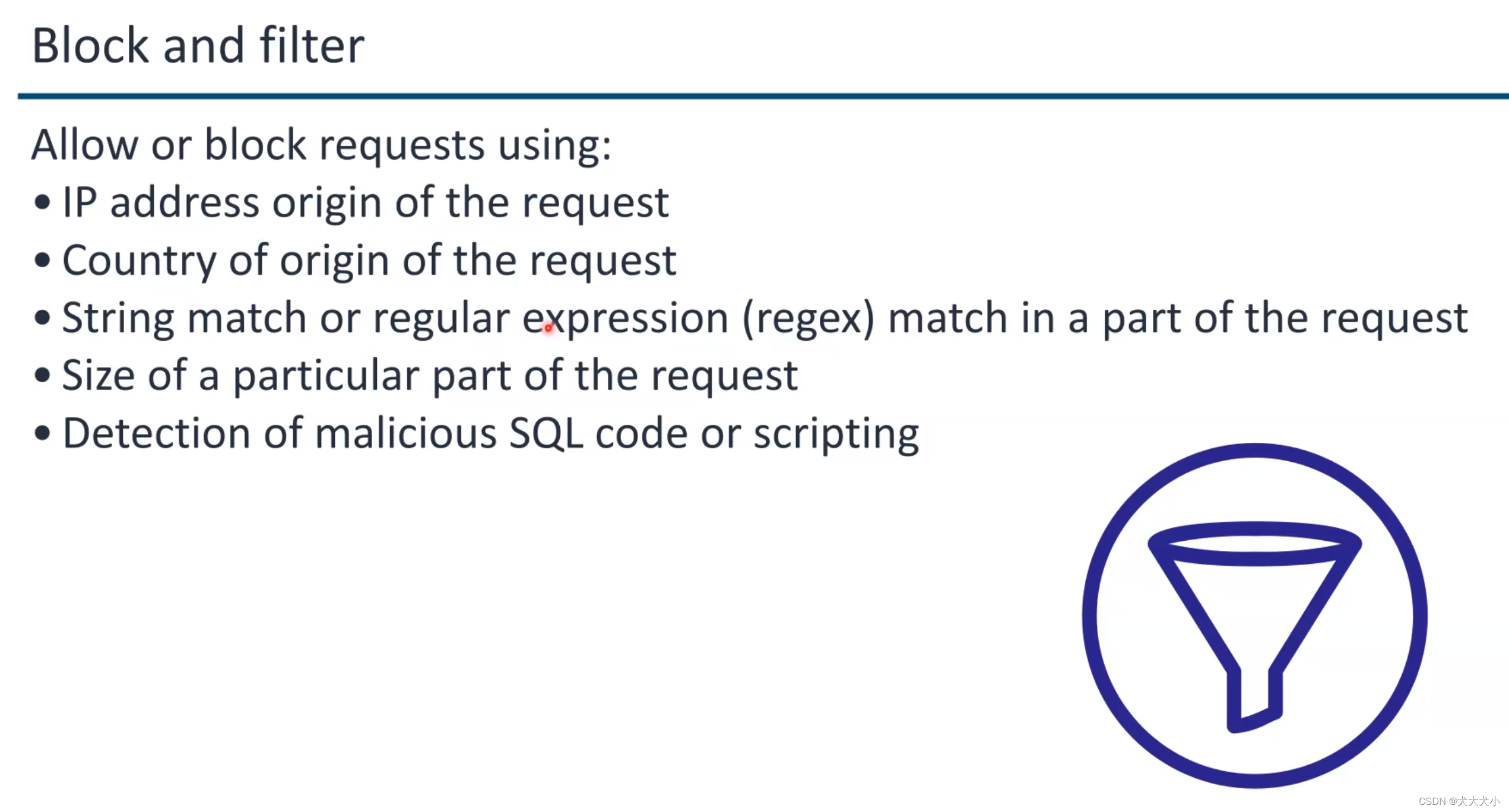
AWS security 培训笔记
云计算的好处 Amazon S3 (Storage) Amazon EC2 (Compute) 上图aws 的几个支柱:安全是其中一个啦 其中安全有几个方面 IAMdetection基础架构保护数据保护应急响应 关于云供应商的责任 data center 原来长这样 ,据说非常之隐蔽的 如果有天退役了…...
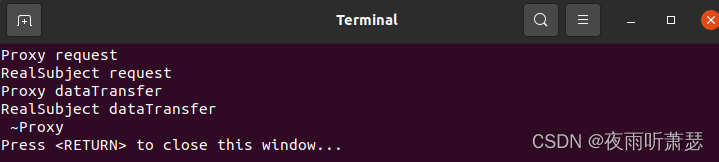
设计模式之代理模式(Proxy)的C++实现
1、代理模式的提出 在组件的开发过程中,有些对象由于某种原因(比如对象创建的开销很大,或者对象的一些操作需要做安全控制,或者需要进程外的访问等),会使Client使用者在操作这类对象时可能会存在问题&…...
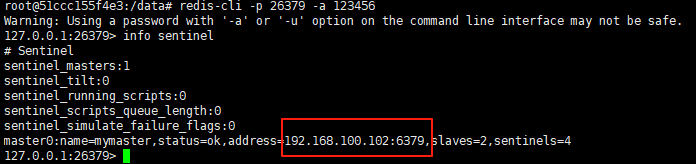
使用docker在3台服务器上搭建基于redis 6.x的一主两从三台均是哨兵模式
一、环境及版本说明 如果服务器已经安装了docker,则忽略此步骤,如果没有安装,则可以按照一下方式安装: 1. 在线安装(有互联网环境): 请看我这篇文章 传送阵>> 点我查看 2. 离线安装(内网环境):请看我这篇文章 传送阵>> 点我查看 说明:假设每台服务器已…...
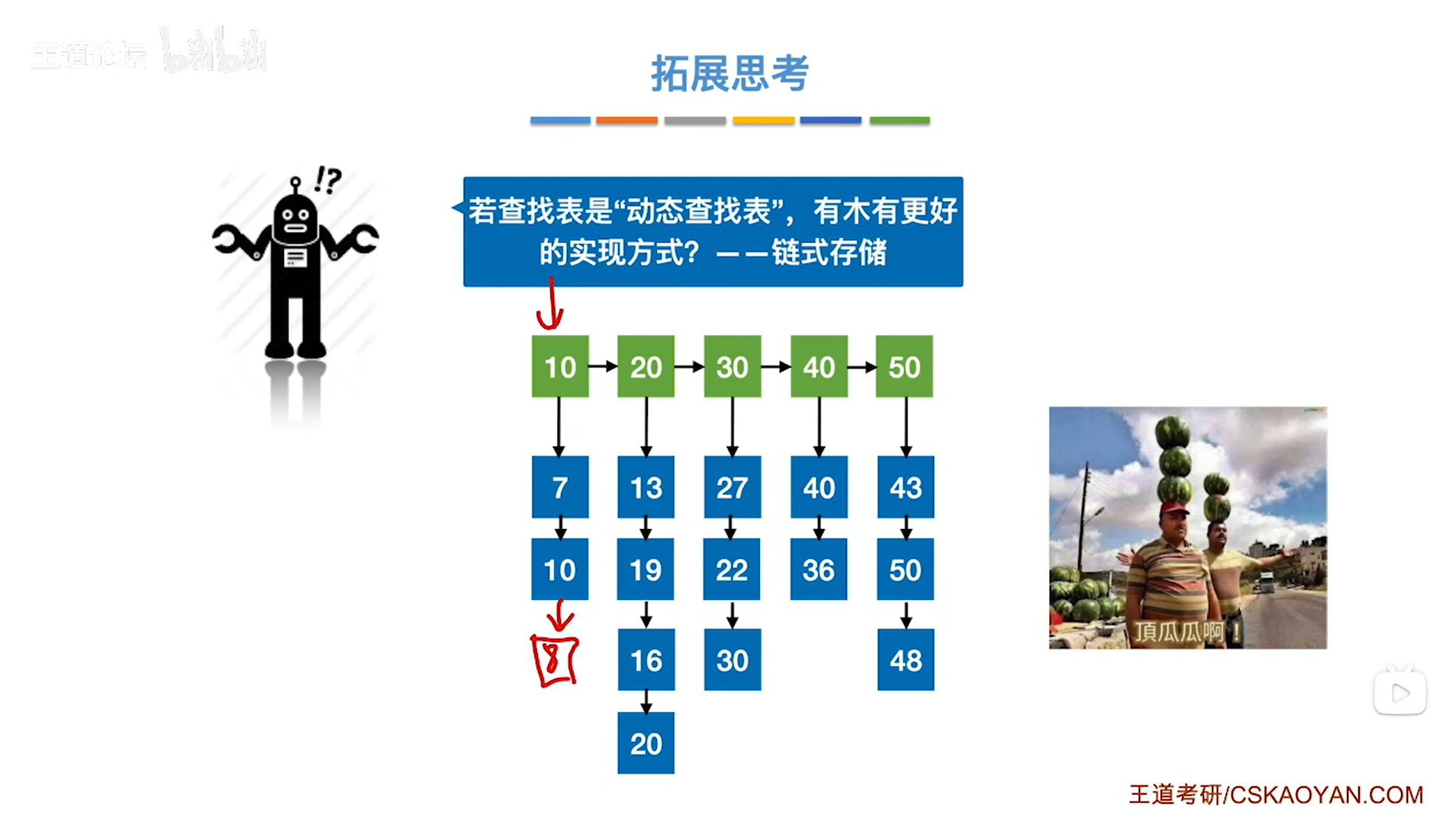
7.4.分块查找
一.分块查找的算法思想: 1.实例: 以上述图片的顺序表为例, 该顺序表的数据元素从整体来看是乱序的,但如果把这些数据元素分成一块一块的小区间, 第一个区间[0,1]索引上的数据元素都是小于等于10的, 第二…...
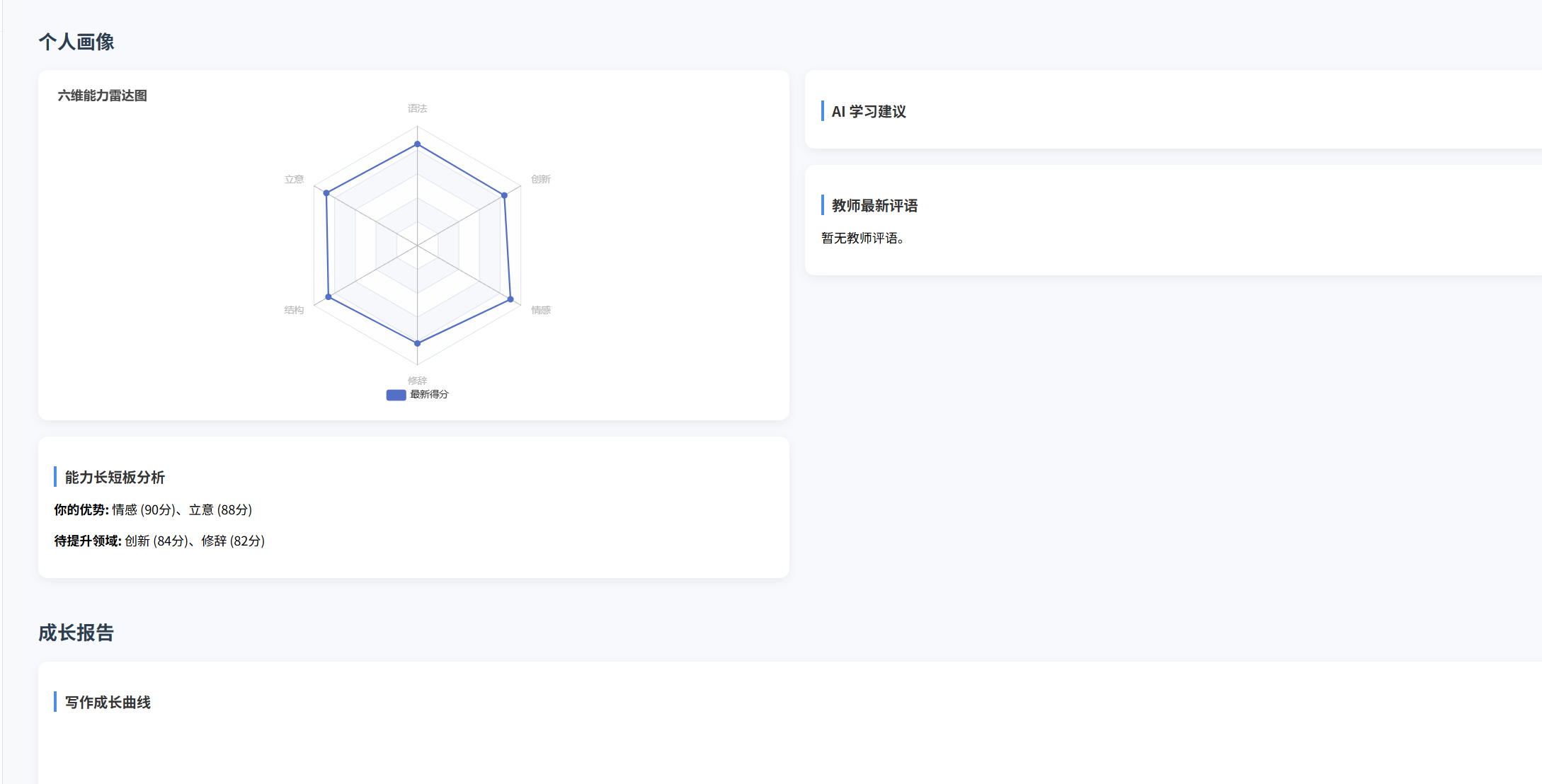
(十)学生端搭建
本次旨在将之前的已完成的部分功能进行拼装到学生端,同时完善学生端的构建。本次工作主要包括: 1.学生端整体界面布局 2.模拟考场与部分个人画像流程的串联 3.整体学生端逻辑 一、学生端 在主界面可以选择自己的用户角色 选择学生则进入学生登录界面…...
:爬虫完整流程)
Python爬虫(二):爬虫完整流程
爬虫完整流程详解(7大核心步骤实战技巧) 一、爬虫完整工作流程 以下是爬虫开发的完整流程,我将结合具体技术点和实战经验展开说明: 1. 目标分析与前期准备 网站技术分析: 使用浏览器开发者工具(F12&…...
前端开发面试题总结-JavaScript篇(一)
文章目录 JavaScript高频问答一、作用域与闭包1.什么是闭包(Closure)?闭包有什么应用场景和潜在问题?2.解释 JavaScript 的作用域链(Scope Chain) 二、原型与继承3.原型链是什么?如何实现继承&a…...

Caliper 配置文件解析:config.yaml
Caliper 是一个区块链性能基准测试工具,用于评估不同区块链平台的性能。下面我将详细解释你提供的 fisco-bcos.json 文件结构,并说明它与 config.yaml 文件的关系。 fisco-bcos.json 文件解析 这个文件是针对 FISCO-BCOS 区块链网络的 Caliper 配置文件,主要包含以下几个部…...
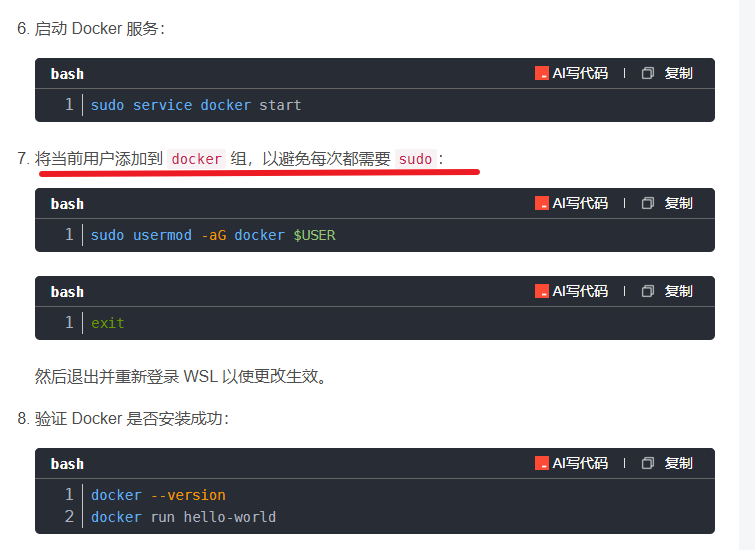
在WSL2的Ubuntu镜像中安装Docker
Docker官网链接: https://docs.docker.com/engine/install/ubuntu/ 1、运行以下命令卸载所有冲突的软件包: for pkg in docker.io docker-doc docker-compose docker-compose-v2 podman-docker containerd runc; do sudo apt-get remove $pkg; done2、设置Docker…...
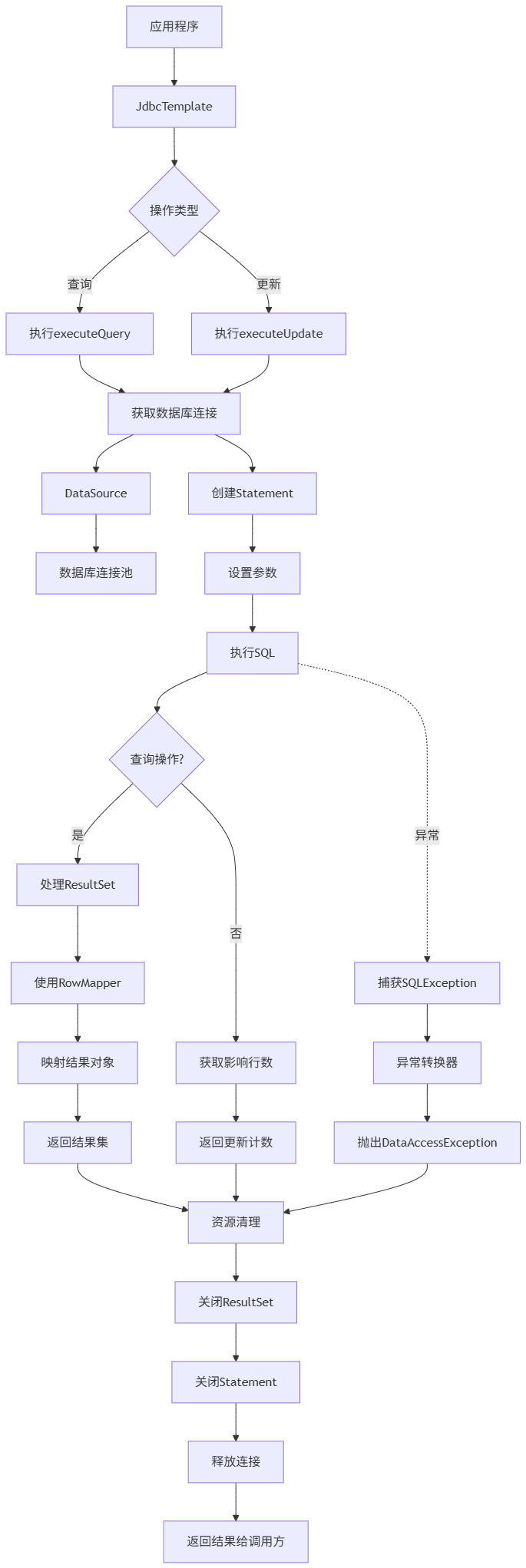
Spring数据访问模块设计
前面我们已经完成了IoC和web模块的设计,聪明的码友立马就知道了,该到数据访问模块了,要不就这俩玩个6啊,查库势在必行,至此,它来了。 一、核心设计理念 1、痛点在哪 应用离不开数据(数据库、No…...
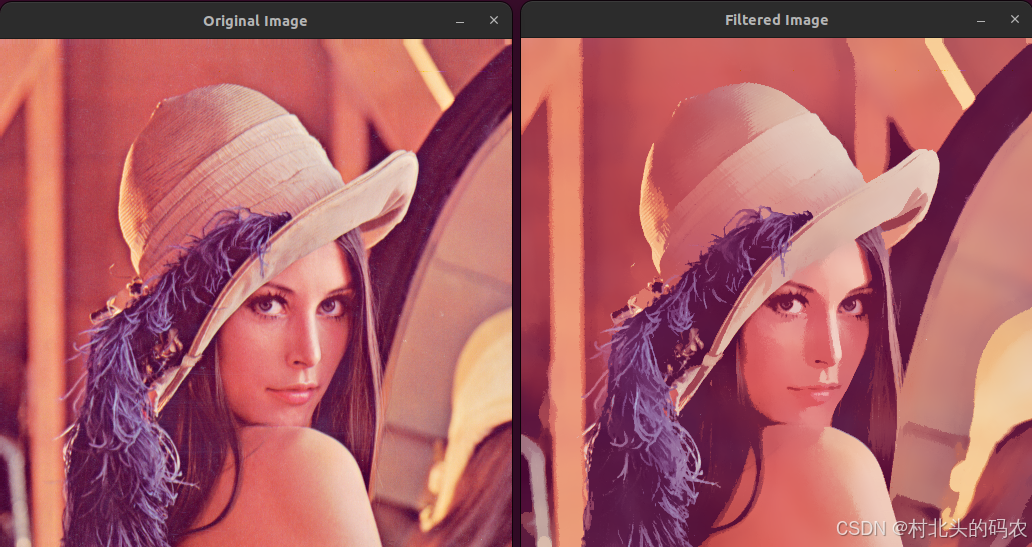
OPenCV CUDA模块图像处理-----对图像执行 均值漂移滤波(Mean Shift Filtering)函数meanShiftFiltering()
操作系统:ubuntu22.04 OpenCV版本:OpenCV4.9 IDE:Visual Studio Code 编程语言:C11 算法描述 在 GPU 上对图像执行 均值漂移滤波(Mean Shift Filtering),用于图像分割或平滑处理。 该函数将输入图像中的…...
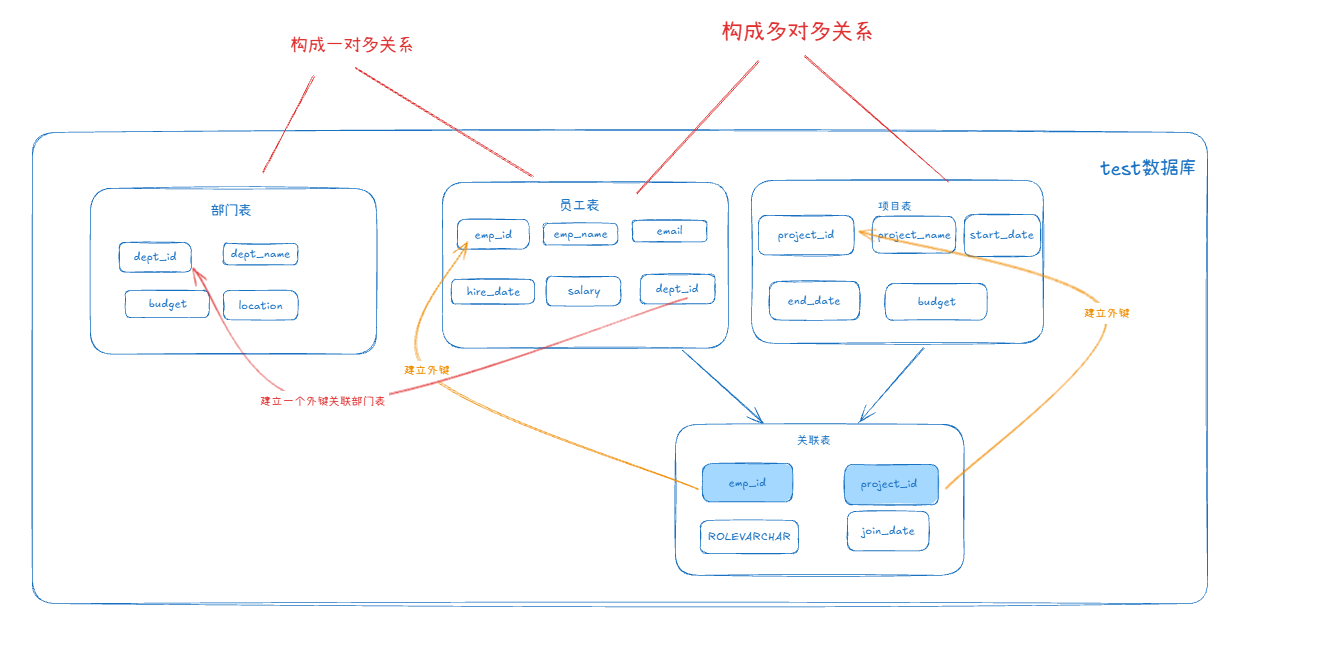
MySQL 知识小结(一)
一、my.cnf配置详解 我们知道安装MySQL有两种方式来安装咱们的MySQL数据库,分别是二进制安装编译数据库或者使用三方yum来进行安装,第三方yum的安装相对于二进制压缩包的安装更快捷,但是文件存放起来数据比较冗余,用二进制能够更好管理咱们M…...
