CCNP350-401学习笔记(401-450题)
401、What is the function of vBond in a Cisco SDWAN deployment?
A. initiating connections with SD-WAN routers automatically
B. pushing of configuration toward SD-WAN routers
C. onboarding of SDWAN routers into the SD-WAN overlay
D. gathering telemetry data from SD-WAN routers
402、Which three resources must the hypervisor make available to the virtual machines? (Choose three)
A. memory
B. bandwidth
C. IP address
D. processor
E. storage
F. secure access
403、How does Protocol Independent Multicast function?
A. In sparse mode it establishes neighbor adjacencies and sends hello messages at 5-second intervals.
B. It uses the multicast routing table to perform the multicast forwarding function.
C. It uses unicast routing information to perform the multicast forwarding function.
D. It uses broadcast routing information to perform the multicast forwarding function.
404、What are two methods of ensuring that the multicast RPF check passes without changing the unicast routing table? (Choose two.)
A. implementing static mroutes
B. disabling BGP routing protocol
C. implementing MBGP
D. disabling the interface of the router back to the multicast source
E. implementing OSPF routing protocol
405、After a redundant route processor failure occurs on a Layer 3 device, which mechanism allows for packets to be forwarded from a neighboring router based on the most recent tables?
A. RPVST+
B. RP failover
C. BFD
D. NSF
406、Which two southbound interfaces originate from Cisco DNA Center and terminate at fabric underlay switches? (Choose two)
A. UDP 67: DHCP
B. ICMP: Discovery
C. TCP 23: Telnet
D. UDP 162: SNMP
E. UDP 6007: NetFlow
407、What is the function of a control-plane node in a Cisco SD-Access solution?
A. to run a mapping system that manages endpoint to network device relationships
B. to implement policies and communicate with networks outside the fabric
C. to connect external Layer 3 networks to the SD Access fabric.
D. to connect APs and wireless endpoints to the SD-Access fabric
408、Refer to the exhibit. What is the result when a switch that is running PVST+ is added to this network?

A. DSW2 operates in Rapid PVST+ and the new switch operates in PVST+
B. Both switches operate in the PVST+ mode
C. Spanning tree is disabled automatically on the network
D. Both switches operate in the Rapid PVST+ mode.
409、What is a characteristic of a next-generation firewall?
A. only required at the network perimeter
B. required in each layer of the network
C. filters traffic using Layer 3 and Layer 4 information only
D. provides intrusion prevention
410、Which measure is used by an NTP server to indicate its closeness to the authoritative time source?
A. stratum
B. hop count
C. time zone
D. latency
411、Which two results occur if Cisco DNA Center loses connectivity to devices in the SD-Access fabric?(Choose two )
A. All devices reload after detecting loss of connection to Cisco DNA Center
B. Already connected users are unaffected, but new users cannot connect
C. User connectivity is unaffected.
D. Cisco DNA Center is unable to collect monitoring data in Assurance.
E. Users lose connectivity
412、Which two components are supported by LISP? (choose two )
A. proxy ETR
B. egress tunnel router
C. route reflector
D. HMAC algorithm
E. spoke
413、Refer to the exhibit.

What does the output confirm about the switch’s spanning tree configuration?
A. The spanning-tree mode stp ieee command was entered on this switch
B. The spanning-tree operation mode for this switch is PVST
C. The spanning-tree operation mode for this switch is IEEE
D. The spanning-tree operation mode for this switch is PVST+
414、 A customer has recently implemented a new wireless infrastructure using WLC-5520S at a site directly next to a large commercial airport Users report that they intermittently lose Wi-Fi connectivity, and troubleshooting reveals it is due to frequent channel changes Which two actions fix this issue? (Choose two)
A. Remove UNII-2 and Extended UNII-2 channels from the 5 Ghz channel list
B. Restore the OCA default settings because this automatically avoids channel interference
C. Disable DFS channels to prevent interference writ) Doppler radar
D. Enable DFS channels because they are immune to radar interference
E. Configure channels on the UNII-2 and the Extended UNII-2 sub-bands of the 5 Ghz band only
415、What is a characteristic of para-virtualization?
A. Para-virtualization guest servers are unaware of one another
B. Para-virtualization allows direct access between the guest OS and the hypervisor
C. Para-virtualization allows the host hardware to be directly accessed
D. Para-virtualization lacks support for containers
416、A customer requests a network design that supports these requirements:
* FHRP redundancy
* multivendor router environment
* IPv4 and IPv6 hosts
Which protocol does the design include?
A. GLBP
B. VRRP version 2
C. VRRP version 3
D. HSRP version 2
417、Refer to the exhibit. What happens to access interfaces where VLAN 222 is assigned?

A. STP BPDU guard is enabled
B. A description “RSPAN” is added
C. They are placed into an inactive state
D. They cannot provide PoE
418、 Which solution do IaaS service providers use to extend a Layer 2 segment across a Layer 3 network?
A. VXLAN
B. VTEP
C. VLAN
D. VRF
419、What is a characteristic of a next-generation firewall?
A. only required at the network perimeter
B. required in each layer of the network
C. filters traffic using Layer 3 and Layer 4 information only
D. provides intrusion prevention
420、Which unit measures the power of a radio signal with reference to 1 milliwatt?
A. dBw
B. dBi
C. mW
D. dBm
421、Refer to the exhibit. An engineer must deny HTTP traffic from host A to host V while allowing all other communication between the hosts, drag and drop the commands into the configuration to achieve these results.


422、What are two benefits of YANG?(choose two)
A. it collects statistical constraint analysis information
B. In enforces the use of specific encoding format for NETCONF
C. in enforces configuration semantics
D. it enables multiple leaf statements to exist within a leaf list
E. it enforces configuration constraints
423、

Which configuration change will force BR2 to reach 209.165.201.0/27 via BR1?
A. Set the origin to igp on BR2 toward PE2 inbound
B. Set the local preference to 150 on PE1 toward BR1 outbound
C. Set the weight attribute to 65,535 on BR1 toward PE1
D. Set the MED to 1 on PE2 toward BR2 outbound
424、An engineer must export the contents of the devices object in JSON format. Which statement must be use?

A. json.print(Devices)
B. json.loads(Devices)
C. json.dumps(Devices)
D. json.repr(Devices)
425、 what is the function of Cisco DNA Center in a cisco SD-Access deployment?
A. It is responsible for routing decisions inside the fabric
B. It is responsible for the design,management,deployment,provisioning,and assurance of the fabric network devices
C. It possesses information about all endponints,nodes,and extemal network related to the fabric
D. It provides integration and automation for all noonfabric nodes and their fabric counterparts.
426、

A network engineer must configure a password expiry mechanism on the gateway router for all local passwords to expire after 60 days. What is required to complete this task?
A. Add the username admin privilege 15 common-criteria-policy Administrators password 0 Cisco013579! command
B. No further action is required. The configuration is complete
C. Add the aaa authentication enable default Administrators command
D. The password expiry mechanism is on the AAA server and must be configured there
427、

An engineer troubleshoots connectivity issues with an application. Testing is performed from the server gateway, and traffic with the DF bit set is dropped along the path after increasing packet size. Removing the DF bit setting at the gateway prevents the packets from being dropped. What is the cause of this issue?
A. PMTUD does not work due to ICMP Packet Too Big messages being dropped by an ACL
B. The remote router drops the traffic due to high CPU load
C. The server should not set the DF bit in any type of traffic that is sent toward the network
D. There is a CoPP policy in place protecting the WAN router CPU from this type of traffic
428、What are two benefits of virtual switching when compared to hardware switching? (Choose two)
A. increased MTU size
B. hardware independence
C. VM-level isolation
D. increased flexibility
E. extended 802.1Q VLAN range
429、

Refer to the exhibit.An engineer configures VRRP and issues the show commands to verify
operation,What does the engineer confirm about VRRP group 1 from the output ?
A. communcation between VRRP members is encrypted using MD5
B. If R1 reboots,R2 becomes the master virtual router until R2 reboots
C. There is no route to 10.10.1.1/32 in R2's routing table
D. R1 is master if 10.10.1.1/32 is in its routing table
430、 Refer to the exhibit.Which single security feature is recommended to provide Network Access Control in the enterprise ?

A. MAB
B. 802.1X
C. WebAuth
D. Port Security sticky MAC
431、Refer to the exhbit.An engineer must add the SNMP interface table to the NetFlow protocol flow records.where should the SNMP table option be added ?
A. under the interface
B. under the flow record
C. under the flow monitor
D. under the flow exporter
432、Which two operational models enable an AP to scan one or more wireless channels for rouge access points and at the same time provide wireless services to clients? (Choose two)
A. Sniffer
B. Rouge detector
C. Local
D. FlexConnect
E. Monitor
433、How does a router behave when configured with the default DNS lookup settings, and a URL is entered onthe CLI?
A. prompts the user to specify the desired IP address.
B. initiates a pinfsfg request to the URL.
C. continuously attxempts tos resolve the URL until the command is cancelled.
D. attempts to query a DNS server on the network
434、What does a router do when configured with the default DNS lookup settings, and a URL is entered on the CLI?
A. initiates a ping request to the URL
B. prompts the user to specify the desired IP address
C. continuously attempts to resolve the URL until the command is cancelled
D. sends a broadcast message in an attempt to resolve the URL
435、An engineer must provide wirelss coverage in a square office.The engineer has only one AP and belives that it should be placed it in the middle of the room.which antenna type should the engineer use ?
A. directional
B. polarized
C. Yagi
D. omnidirectional
436、

Refer to the exhibit.POSTMAN is showing an attempt to retrieve network device information from Cisco DNA Center API. what is the issue?
A. The URI string is incorrect
B. The token has expired
C. Authentication has failed
D. The JSON payload contains the incorrect UUID
437、

Refer to the exhibit.An engineer configures a new HSRP group.while reviewing the HSRP status,the
engineer sees the logging message generated on R2.What is the cause of he message ?
A. The HSRP configuration has caused a routing loop
B. The HSRP configuration has caused a spanning-tree loop
C. A PC is on the network using the IP address 10.10.1.1
D. The same virtual IP address has been configured for two HSRP groups
438、

Which HTTP code must be retumed to prevent the script from exiting ?
A. 200
B. 201
C. 300
D. 301
439、what is a consideration when designing a Cisco SD-Access underlay network ?
A. The underlay switches provide endpoint physical connectivity for users
B. End user subnets and ednpoints are part of the underlay network
C. It must support IPv4 and IPv6 underlay networks
D. static routing is a requirement
440、

Refer to the exhibit.Running the script causes the output in the exhibit.what should be the first line of the script?
A. from ncclient import manager
B. import manager
C. from ncclient import *
D. ncclient manager import
441、What happens to the signal strength of an RF signal due to wave spreading?
A. The signal strength of the RF signal will fall off equally near the transmitter and also farther away
B. The signal strength of the RF signal will fall off quickly near the transmitter but more slowly farther away
C. The signal strength of the RF signal will fall off slowly near the receiver and more quickly farther away
D. The signal strength of the RF signal will fall off slowly near the transmitter but more quickly farther away
442、Which two statements about AAA authentication are true? (Choose two)
A. RADIUS authentication queries the router’s local username database
B. TACACS+ authentication uses an RSA server to authenticate users
C. Local user names are case-insensitive
D. Local authentication is maintained on the router
E. KRB5 authentication disables user access when an incorrect password is entered
443、what is the output of this code ?

A. cisco
B. get_credentials
C. username
D. username:cisco
444、

Refer to the exhibit.An engineer is troubleshooting a connectivity issue and ececutes a tracerout.what does the result confirm?
A. The probe times out
B. The destination server reported it is too busy
C. The protocol is unreachable
D. The destination port is unreachable
445、where is radie resource management performed in a Cisco SD-Access wireless solution ?
A. DNA Center
B. control plane node
C. wireless controller
D. Cisco CMX
446、

Refer to the exhibit.Router1 is currently operating as the HSRP primary with a priority of 110. Router1 fails and Router2 takes over the forwarding role.which command on Router1 causes it to take over the forwarding role when it returns to service ?
A. standby 2 priority
B. standby 2 preempt
C. standby 2 track
D. standby 2 timers
447、
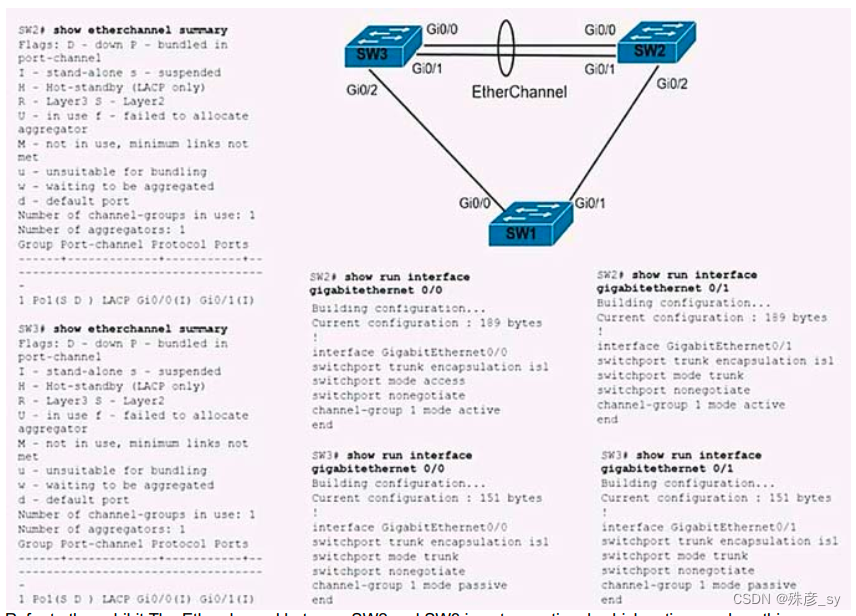
Refer to the exhibit.The Etherchannel between SW2 and SW3 is not operational. which action resolves this issue ?
A. configure the mode on sw2 Gi0/0 to trunk
B. configure the mode on sw2 Gi0/1 to access
C. configure the channel-group mode on SW2 Gi0/0 and Gi0/1 to on
D. configure the channel-group mode on SW2 Gi0/0 and Gi0/1 to active
448、''HTTP/1.1 204 No Content'' is returned when the curl -i -x DELETE command is issued.which situation has occurred ?
A. The object could not be located at the URL path
B. The command succeeded in deleting the object
C. The object was located at he URL,but it could not be deleted
D. The URL was invalid
449、what is one benefit of implementang a VSS archtecture?
A. It uses a single database to manage configuration for multiple switches
B. It provides a single point of management for improved efficiency
C. It provides multiple points of management for redundancy and improved support
D. It uses GLBP to balance traffic between gateways
450、How is MSDP used to interconnect multiple PIM-SM domains?
A. MSDP depends on BGP or multiprotocol BGP for interdomain operation
B. MSDP messages are used to advertise active sources in a domain
C. MSDP SA request messages are used to request a list of active sources for a specific group
D. MSDP allows a rendezvous point to dynamically discover active sources outside of its domain
相关文章:

CCNP350-401学习笔记(401-450题)
401、What is the function of vBond in a Cisco SDWAN deployment? A. initiating connections with SD-WAN routers automatically B. pushing of configuration toward SD-WAN routersC. onboarding of SDWAN routers into the SD-WAN overlay D. gathering telemetry dat…...

一文带你看透前端世界里的日期时间,对就是Date
很高兴我们能够通过不同空间,不同时间,通过这篇博客相识,那一定是一种缘分,一种你和狗哥的缘分。今天我希望通过这篇博客对我所熟知的前端世界里的日期时间做一个汇总,不止是代码上的汇总哦! 目录 一、时区…...
易基因|RRBS单碱基绘制580种动物的基因组规模DNA甲基化谱:Nature子刊
大家好,这里是专注表观组学十余年,领跑多组学科研服务的易基因。2023年01月16日,奥地利科学院分子医学研究中心(CeMM)研究团队在《Nat Commun》杂志发表了题为“Comparative analysis of genome-scale, base-resolution DNA methylation prof…...
面试官:能用JavaScript手写一个bind函数吗
经常会看到网上各种手写bind的教程,下面是我在自己实现手写bind的过程中遇到的问题与思考。如果对于如何实现一个手写bind还有疑惑的话,那么可以先看看上面两篇文章。 手写bind vs 原生bind 我们先使用一个典型的手写bind的例子,代码如下&a…...

美国拟发布纽扣电池或硬币电池安全标准和通知要求ANSI C18. 3M
2023年2月10日,美国向WTO提交G/TBT/N/USA/1964号通报,拟发布纽扣电池或硬币电池以及含有此类电池的消费品的安全标准和通知要求,征求意见截止日期为2023年3月13日,拟通过日期和生效日期待定。联[1]系 拟定规则通知根据H.R.5313瑞…...
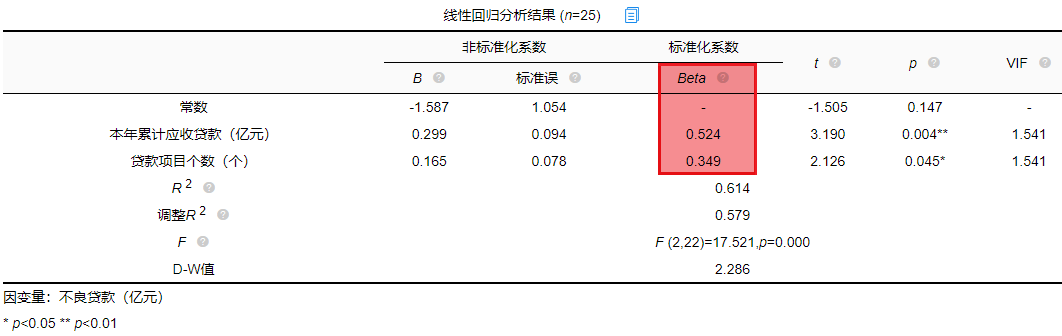
双因素方差分析
一、案例与数据 一家大型商业银行在多地区设有分行,其业务主要是进行基础设施建设,国家重点项目建设,固定资产投资等项目的贷款。近年来,该银行的贷款额平稳增长,但不良贷款额也有较大比例的提高,这给银行…...

[ vulhub漏洞复现篇 ] Drupal XSS漏洞 (CVE-2019-6341)
🍬 博主介绍 👨🎓 博主介绍:大家好,我是 _PowerShell ,很高兴认识大家~ ✨主攻领域:【渗透领域】【数据通信】 【通讯安全】 【web安全】【面试分析】 🎉点赞➕评论➕收藏 养成习…...

「TCG 规范解读」第8章 TPM工作组 TPM 1.2中 SHA1的使用
可信计算组织(Ttrusted Computing Group,TCG)是一个非盈利的工业标准组织,它的宗旨是加强在相异计算机平台上的计算环境的安全性。TCG于2003年春成立,并采纳了由可信计算平台联盟(the Trusted Computing Platform Alli…...

熵权法计算权重
文章目录1. 多属性决策问题2. 熵(entropy)3. 信息熵4. 熵权法5. 熵权法的实现基于信息论的熵值法是根据各指标所含信息有序程度的差异性来确定指标权重的客观赋权方法,仅依赖于数据本身的离散程度。熵用于度量不确定性,指标的离散…...

redis实现用户签到,统计活跃用户,用户在线状态,用户留存率
开发的过程中,可能会遇到用户签到、统计当天的活跃用户、以及每个用户的在线状态,用户留存率的开发需求,可能会用传统的方法,根据相应的需求设计数据库表等,但这样耗费的存储空间大,以及性能方面也不会太好…...
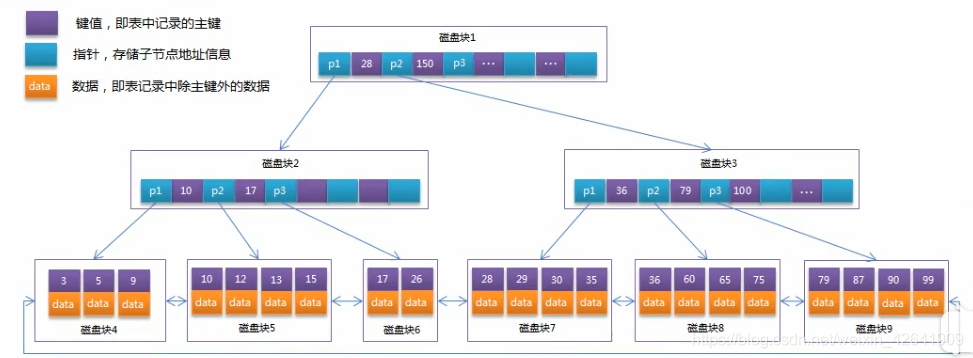
MySQL中有多少种索引?索引的底层实现原理
索引存储在内存中,为服务器存储引擎为了快速找到记录的一种数据结构。索引的主要作用是加快数据查找速度,提高数据库的性能。索引的分类(1) 普通索引:最基本的索引,它没有任何限制。(2) 唯一索引:与普通索引类似&#…...
以及线索二叉树java详解)
LeetCode经典算法题:二叉树遍历(递归遍历+迭代遍历+层序遍历)以及线索二叉树java详解
LeetCode经典算法题:二叉树遍历(递归遍历迭代遍历层序遍历)以及线索二叉树java详解 文章目录二叉树遍历题目描述解题思路与代码递归遍历迭代遍历层序遍历线索二叉树:二叉树遍历 题目描述 从根节点往下查找,先找左子树…...

【Java闭关修炼】MyBatis-接口代理的方式实现Dao层
【Java闭关修炼】MyBatis-接口代理的方式实现Dao层实现规则代码实现代理对象分析接口代理方式小结实现规则 映射配置文件中的名称空间必须和Dao层接口的全类名相同映射配置文件的增删改查标签的id属性必须和Dao层接口方法的参数相同映射配置文件中的增删改查标签的parameterTyp…...

2022年网络安全政策态势分析与2023年立法趋势
近日,公安部第三研究所网络安全法律研究中心与 360 集团法务中心联合共同发布了《全球网络安全政策法律发展年度报告(2022)》。《报告》概览2022年全球网络安全形势与政策法律态势,并对2023年及后续短期内网络安全政策、立法趋势进…...
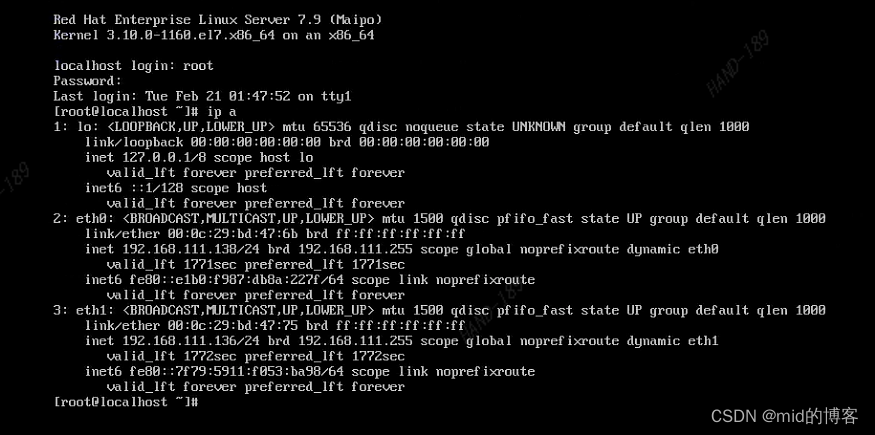
使用vmware制作云平台redhat7.9镜像模板
一、概述 1.1 redhat7.9 定制镜像上传到云平台。 这个制作镜像得方式适用于多种iso 镜像。 将iso 镜像通过vmware 创建出一台虚机,对虚机做一些基础配置。在虚机上安装kvm 虚拟化得工具, 将iso 镜像在导入虚机种通过kvm创建一下虚机, 虚机创…...

OpenCV基础(28)使用OpenCV进行摄像机标定Python和C++
摄像头是机器人、监控、太空探索、社交媒体、工业自动化甚至娱乐业等多个领域不可或缺的一部分。 对于许多应用,必须了解相机的参数才能有效地将其用作视觉传感器。 在这篇文章中,您将了解相机校准所涉及的步骤及其意义。 我们还共享 C 和 Python 代码以…...
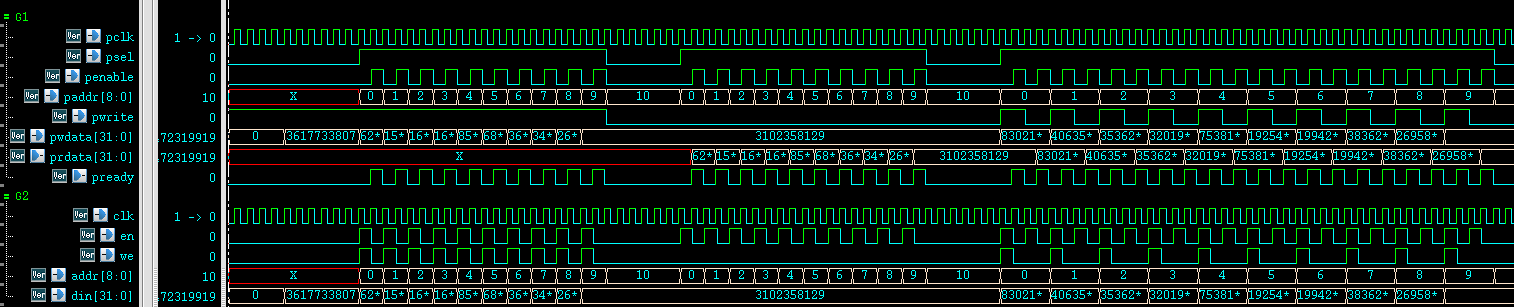
APB总线详解及手撕代码
本文的参考资料为官方文档AMBA™3 APB Protocol specification文档下载地址: https://pan.baidu.com/s/1Vsj4RdyCLan6jE-quAsEuw?pwdw5bi 提取码:w5bi APB端口介绍介绍总线具体握手规则之前,需要先熟悉一下APB总线端口,APB的端口…...

【Linux/Windows】源文件乱码问题解决方法总结
🐚作者简介:花神庙码农(专注于Linux、WLAN、TCP/IP、Python等技术方向)🐳博客主页:花神庙码农 ,地址:https://blog.csdn.net/qxhgd🌐系列专栏:Linux技术&…...
Python 四大主流 Web 编程框架
目前Python的网络编程框架已经多达几十个,逐个学习它们显然不现实。但这些框架在系统架构和运行环境中有很多共通之处,本文带领读者学习基于Python网络框架开发的常用知识,及目前的4种主流Python网络框架:Django、Tornado、Flask、Twisted。 …...
学UI设计,可以向哪些方向发展?该怎么学?
1、什么是UI设计?UI设计,全称 User Interface,翻译成中文意思叫做用户界面设计。2、UI设计的类型UI设计按用户和界面来分可分成四种UI设计。分别是移动端UI设计,PC端UI设计,游戏UI设计,以及其它UI设计。第一…...

【SpringBoot】100、SpringBoot中使用自定义注解+AOP实现参数自动解密
在实际项目中,用户注册、登录、修改密码等操作,都涉及到参数传输安全问题。所以我们需要在前端对账户、密码等敏感信息加密传输,在后端接收到数据后能自动解密。 1、引入依赖 <dependency><groupId>org.springframework.boot</groupId><artifactId...

1688商品列表API与其他数据源的对接思路
将1688商品列表API与其他数据源对接时,需结合业务场景设计数据流转链路,重点关注数据格式兼容性、接口调用频率控制及数据一致性维护。以下是具体对接思路及关键技术点: 一、核心对接场景与目标 商品数据同步 场景:将1688商品信息…...

STM32F4基本定时器使用和原理详解
STM32F4基本定时器使用和原理详解 前言如何确定定时器挂载在哪条时钟线上配置及使用方法参数配置PrescalerCounter ModeCounter Periodauto-reload preloadTrigger Event Selection 中断配置生成的代码及使用方法初始化代码基本定时器触发DCA或者ADC的代码讲解中断代码定时启动…...

对WWDC 2025 Keynote 内容的预测
借助我们以往对苹果公司发展路径的深入研究经验,以及大语言模型的分析能力,我们系统梳理了多年来苹果 WWDC 主题演讲的规律。在 WWDC 2025 即将揭幕之际,我们让 ChatGPT 对今年的 Keynote 内容进行了一个初步预测,聊作存档。等到明…...

linux 错误码总结
1,错误码的概念与作用 在Linux系统中,错误码是系统调用或库函数在执行失败时返回的特定数值,用于指示具体的错误类型。这些错误码通过全局变量errno来存储和传递,errno由操作系统维护,保存最近一次发生的错误信息。值得注意的是,errno的值在每次系统调用或函数调用失败时…...

论文浅尝 | 基于判别指令微调生成式大语言模型的知识图谱补全方法(ISWC2024)
笔记整理:刘治强,浙江大学硕士生,研究方向为知识图谱表示学习,大语言模型 论文链接:http://arxiv.org/abs/2407.16127 发表会议:ISWC 2024 1. 动机 传统的知识图谱补全(KGC)模型通过…...
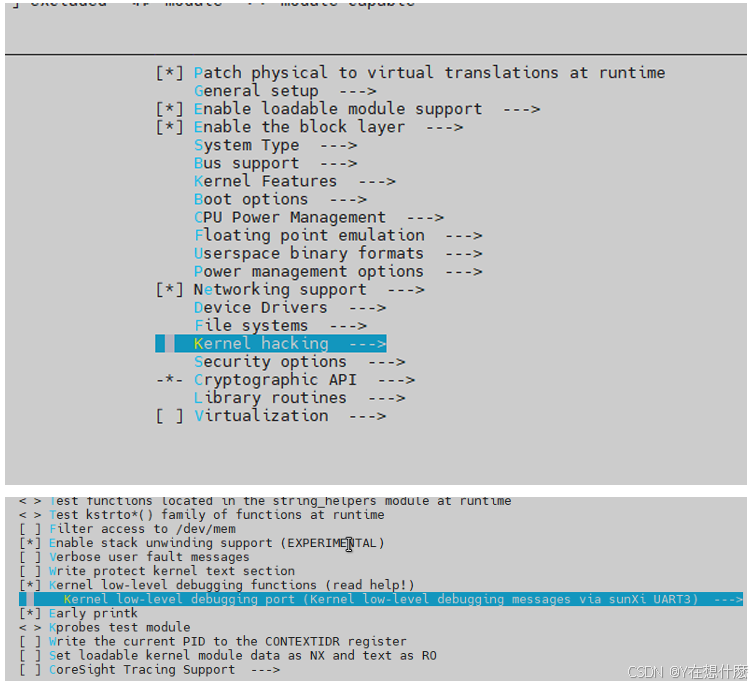
全志A40i android7.1 调试信息打印串口由uart0改为uart3
一,概述 1. 目的 将调试信息打印串口由uart0改为uart3。 2. 版本信息 Uboot版本:2014.07; Kernel版本:Linux-3.10; 二,Uboot 1. sys_config.fex改动 使能uart3(TX:PH00 RX:PH01),并让boo…...

CSS | transition 和 transform的用处和区别
省流总结: transform用于变换/变形,transition是动画控制器 transform 用来对元素进行变形,常见的操作如下,它是立即生效的样式变形属性。 旋转 rotate(角度deg)、平移 translateX(像素px)、缩放 scale(倍数)、倾斜 skewX(角度…...

Neko虚拟浏览器远程协作方案:Docker+内网穿透技术部署实践
前言:本文将向开发者介绍一款创新性协作工具——Neko虚拟浏览器。在数字化协作场景中,跨地域的团队常需面对实时共享屏幕、协同编辑文档等需求。通过本指南,你将掌握在Ubuntu系统中使用容器化技术部署该工具的具体方案,并结合内网…...
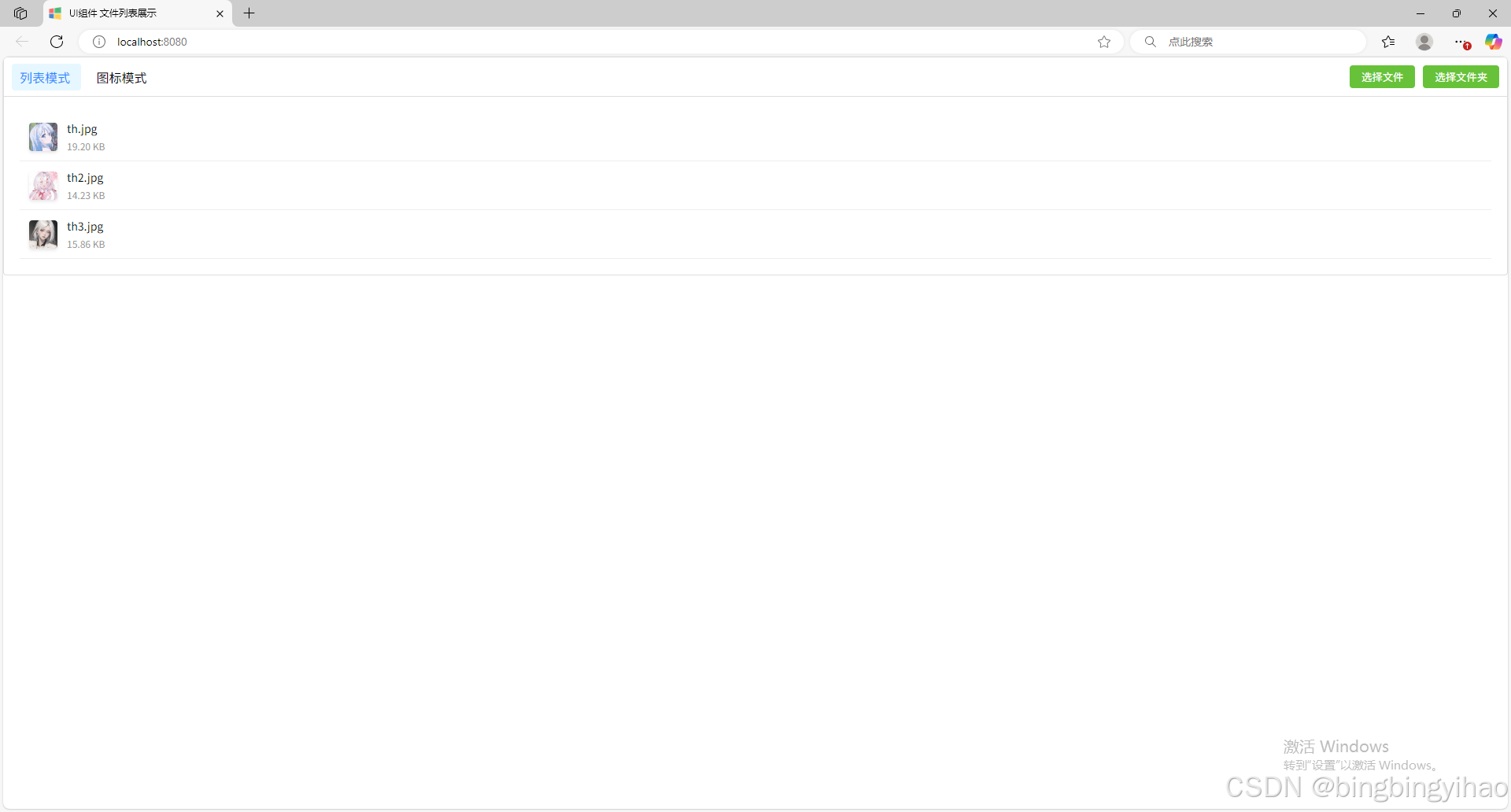
ui框架-文件列表展示
ui框架-文件列表展示 介绍 UI框架的文件列表展示组件,可以展示文件夹,支持列表展示和图标展示模式。组件提供了丰富的功能和可配置选项,适用于文件管理、文件上传等场景。 功能特性 支持列表模式和网格模式的切换展示支持文件和文件夹的层…...
