项目实战:Ingress搭建Nginx+WP论坛+MariaDB
1. 网站架构

本次部署形式完全舍弃 Docker,将所有应用都置于Kubernetes,采用 Deployment 而非单 Pod 部署,稳定性得到升级。
2. 部署 MariaDB
[root@k8s-master ~]# mkdir tdr
[root@k8s-master ~]# cd tdr/
(1)定义 ConfigMap
[root@k8s-master tdr]# vim mariadb-configmap.yaml
apiVersion: v1
kind: ConfigMap
metadata:
name: mariadb-configmap
data:
USER: "wp"
PASSWORD: "123"
ROOT_PASSWORD: "123"
DATABASE: "db"
(2)定义 Deployment
[root@k8s-master tdr]# vim mariadb-deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: mariadb-deployment
labels:
app: mariadb-deployment
spec:
replicas:
selector:
matchLabels:
app: mariadb-deployment
template:
metadata:
labels:
app: mariadb-deployment
spec:
containers:
- name: mariadb
image: docker.io/library/mariadb:latest
imagePullPolicy: Never
ports:
- name: mariadbport
containerPort: 3306
envFrom:
- prefix: "MARIADB_"
configMapRef:
name: mariadb-configmap
(3)定义 Service
[root@k8s-master tdr]# vim mariadb-service.yaml
apiVersion: v1
kind: Service
metadata:
name: mariadb-service
spec:
selector:
app: mariadb-deployment
ports:
- port: 3306
targetPort: 3306
protocol: TCP
type: NodePort
(4)启动 MariaDB
[root@k8s-master tdr]# kubectl create -f mariadb-configmap.yaml
configmap/mariadb-configmap created
[root@k8s-master tdr]# kubectl create -f mariadb-deployment.yaml
deployment.apps/mariadb-deployment created
[root@k8s-master tdr]# kubectl create -f mariadb-service.yaml
service/mariadb-service created
[root@k8s-master tdr]# kubectl get all
NAME READY STATUS RESTARTS AGE
#pod信息:
pod/cluster-test-66bb44bd88-nk46t 1/1 Running 38 (14m ago) 10d
pod/mariadb-deployment-5bf6d9f98c-wt7cc 1/1 Running 0 25m
#service信息:
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 10d
service/mariadb-service NodePort 10.96.249.62 <none> 3306:30150/TCP 14m
#deployment信息:
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/cluster-test 1/1 1 1 10d
deployment.apps/mariadb-deployment 1/1 1 1 25m
#replicaset信息:
NAME DESIRED CURRENT READY AGE
replicaset.apps/cluster-test-66bb44bd88 1 1 1 10d
replicaset.apps/mariadb-deployment-5bf6d9f98c 1 1 1 25m
[root@k8s-master tdr]# kubectl exec -it pods/cluster-test-66bb44bd88-nk46t -- bash
(08:47 cluster-test-66bb44bd88-nk46t:/) nslookup mariadb-service
Server: 10.96.0.10
Address: 10.96.0.10#53
Name: mariadb-service.default.svc.cluster.local
Address: 10.96.249.62
3. 部署 Wrodpress
(1)定义 ConfigMap
[root@k8s-master tdr]# vim wordpress-configmap.yaml
apiVersion: v1
kind: ConfigMap
metadata:
name: wordpress-config
data:
NAME: "db"
USER: "wp"
PASSWORD: "123"
HOST: "mariadb-service"
(2)定义 Deployment
[root@k8s-master tdr]# vim wordpress-deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: wordpress-deployment
labels:
app: wordpress-deployment
spec:
replicas: 2
selector:
matchLabels:
app: wordpress-deployment
template:
metadata:
labels:
app: wordpress-deployment
spec:
containers:
- name: wp
image: docker.io/library/wordpress:latest
imagePullPolicy: Never
ports:
- name: wordpressport
containerPort: 80
envFrom:
- prefix: "WORDPRESS_DB_"
configMapRef:
name: wordpress-config
(3)定义 Service
[root@k8s-master tdr]# vim wordpress-service.yaml
apiVersion: v1
kind: Service
metadata:
name: wordpress-service
spec:
selector:
app: wordpress-deployment
ports:
- name: http
port: 80
targetPort: 80
protocol: TCP
nodePort: 32000
type: NodePort
(4)启动 WordPress
[root@k8s-master tdr]# kubectl create -f wordpress-configmap.yaml
configmap/workpress-config created
[root@k8s-master tdr]# kubectl create -f wordpress-deployment.yaml
deployment.apps/wordpress-deployment created
[root@k8s-master tdr]# kubectl create -f wordpress-service.yaml
service/wordpress-service created
[root@k8s-master tdr]# kubectl get po
NAME READY STATUS RESTARTS AGE
cluster-test-66bb44bd88-nk46t 1/1 Running 38 (50m ago) 10d
mariadb-deployment-5bf6d9f98c-wt7cc 1/1 Running 0 60m
wordpress-deployment-555685954b-77wb8 1/1 Running 0 107s
wordpress-deployment-555685954b-9g8rf 1/1 Running 0 107s
(5)访问测试
访问192.168.1.110:32000

4. 部署Nginx Ingress Controller
(1)安装Ingress Controller
https://www.yuque.com/login?goto=https%3A%2F%2Fwww.yuque.com%2Fattachments%2Fyuque%2F0%2F2024%2Fyaml%2F27632550%2F1704426623262-496917bf-7f4b-48e6-83e1-429f2e1ee853.yaml
下载附件再导入到服务器内,再进行安装
[root@k8s-master tdr]# cat ingress.yaml
apiVersion: v1
kind: Namespace
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
name: ingress-nginx
---
apiVersion: v1
automountServiceAccountToken: true
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx
namespace: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- namespaces
verbs:
- get
- apiGroups:
- ""
resources:
- configmaps
- pods
- secrets
- endpoints
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io
resources:
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- coordination.k8s.io
resourceNames:
- ingress-nginx-leader
resources:
- leases
verbs:
- get
- update
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- create
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- discovery.k8s.io
resources:
- endpointslices
verbs:
- list
- watch
- get
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-admission
namespace: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- secrets
verbs:
- get
- create
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
- namespaces
verbs:
- list
- watch
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- list
- watch
- apiGroups:
- ""
resources:
- nodes
verbs:
- get
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io
resources:
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- discovery.k8s.io
resources:
- endpointslices
verbs:
- list
- watch
- get
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-admission
rules:
- apiGroups:
- admissionregistration.k8s.io
resources:
- validatingwebhookconfigurations
verbs:
- get
- update
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-admission
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-admission
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: v1
data:
allow-snippet-annotations: "true"
kind: ConfigMap
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-controller
namespace: ingress-nginx
---
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
ipFamilies:
- IPv4
ipFamilyPolicy: SingleStack
ports:
- appProtocol: http
name: http
port: 80
protocol: TCP
targetPort: http
- appProtocol: https
name: https
port: 443
protocol: TCP
targetPort: https
selector:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
type: NodePort
---
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-controller-admission
namespace: ingress-nginx
spec:
ports:
- appProtocol: https
name: https-webhook
port: 443
targetPort: webhook
selector:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
type: ClusterIP
---
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
minReadySeconds: 0
revisionHistoryLimit: 10
selector:
matchLabels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
template:
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
spec:
containers:
- args:
- /nginx-ingress-controller
- --election-id=ingress-nginx-leader
- --controller-class=k8s.io/ingress-nginx
- --ingress-class=nginx
- --configmap=$(POD_NAMESPACE)/ingress-nginx-controller
- --validating-webhook=:8443
- --validating-webhook-certificate=/usr/local/certificates/cert
- --validating-webhook-key=/usr/local/certificates/key
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
- name: LD_PRELOAD
value: /usr/local/lib/libmimalloc.so
image: registry.cn-beijing.aliyuncs.com/dotbalo/ingress-nginx-controller:v1.7.1
imagePullPolicy: IfNotPresent
lifecycle:
preStop:
exec:
command:
- /wait-shutdown
livenessProbe:
failureThreshold: 5
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
name: controller
ports:
- containerPort: 80
name: http
protocol: TCP
- containerPort: 443
name: https
protocol: TCP
- containerPort: 8443
name: webhook
protocol: TCP
readinessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
resources:
requests:
cpu: 100m
memory: 90Mi
securityContext:
allowPrivilegeEscalation: true
capabilities:
add:
- NET_BIND_SERVICE
drop:
- ALL
runAsUser: 101
volumeMounts:
- mountPath: /usr/local/certificates/
name: webhook-cert
readOnly: true
dnsPolicy: ClusterFirst
nodeSelector:
kubernetes.io/os: linux
serviceAccountName: ingress-nginx
terminationGracePeriodSeconds: 300
volumes:
- name: webhook-cert
secret:
secretName: ingress-nginx-admission
---
apiVersion: batch/v1
kind: Job
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-admission-create
namespace: ingress-nginx
spec:
template:
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-admission-create
spec:
containers:
- args:
- create
- --host=ingress-nginx-controller-admission,ingress-nginx-controller-admission.$(POD_NAMESPACE).svc
- --namespace=$(POD_NAMESPACE)
- --secret-name=ingress-nginx-admission
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: registry.cn-beijing.aliyuncs.com/dotbalo/kube-webhook-certgen:v20230312
imagePullPolicy: IfNotPresent
name: create
securityContext:
allowPrivilegeEscalation: false
nodeSelector:
kubernetes.io/os: linux
restartPolicy: OnFailure
securityContext:
fsGroup: 2000
runAsNonRoot: true
runAsUser: 2000
serviceAccountName: ingress-nginx-admission
---
apiVersion: batch/v1
kind: Job
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-admission-patch
namespace: ingress-nginx
spec:
template:
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-admission-patch
spec:
containers:
- args:
- patch
- --webhook-name=ingress-nginx-admission
- --namespace=$(POD_NAMESPACE)
- --patch-mutating=false
- --secret-name=ingress-nginx-admission
- --patch-failure-policy=Fail
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: registry.cn-beijing.aliyuncs.com/dotbalo/kube-webhook-certgen:v20230312
imagePullPolicy: IfNotPresent
name: patch
securityContext:
allowPrivilegeEscalation: false
nodeSelector:
kubernetes.io/os: linux
restartPolicy: OnFailure
securityContext:
fsGroup: 2000
runAsNonRoot: true
runAsUser: 2000
serviceAccountName: ingress-nginx-admission
---
apiVersion: networking.k8s.io/v1
kind: IngressClass
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: nginx
spec:
controller: k8s.io/ingress-nginx
---
apiVersion: admissionregistration.k8s.io/v1
kind: ValidatingWebhookConfiguration
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.7.1
name: ingress-nginx-admission
webhooks:
- admissionReviewVersions:
- v1
clientConfig:
service:
name: ingress-nginx-controller-admission
namespace: ingress-nginx
path: /networking/v1/ingresses
failurePolicy: Fail
matchPolicy: Equivalent
name: validate.nginx.ingress.kubernetes.io
rules:
- apiGroups:
- networking.k8s.io
apiVersions:
- v1
operations:
- CREATE
- UPDATE
resources:
- ingresses
sideEffects: None
[root@k8s-master tdr]# kubectl create -f ingress.yaml
namespace/ingress-nginx created
serviceaccount/ingress-nginx created
serviceaccount/ingress-nginx-admission created
role.rbac.authorization.k8s.io/ingress-nginx created
role.rbac.authorization.k8s.io/ingress-nginx-admission created
clusterrole.rbac.authorization.k8s.io/ingress-nginx created
clusterrole.rbac.authorization.k8s.io/ingress-nginx-admission created
rolebinding.rbac.authorization.k8s.io/ingress-nginx created
rolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created
clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx created
clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created
configmap/ingress-nginx-controller created
service/ingress-nginx-controller created
service/ingress-nginx-controller-admission created
deployment.apps/ingress-nginx-controller created
job.batch/ingress-nginx-admission-create created
job.batch/ingress-nginx-admission-patch created
ingressclass.networking.k8s.io/nginx created
validatingwebhookconfiguration.admissionregistration.k8s.io/ingress-nginx-admission created
[root@k8s-master tdr]# kubectl get po -n ingress-nginx
NAME READY STATUS RESTARTS AGE
ingress-nginx-admission-create-mxff4 0/1 Completed 0 13m
ingress-nginx-admission-patch-lbmck 0/1 Completed 2 13m
ingress-nginx-controller-674f66cf96-xjs2t 1/1 Running 0 13m
[root@k8s-master ~]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.96.184.233 <none> 80:31546/TCP,443:31757/TCP 14m
ingress-nginx-controller-admission ClusterIP 10.96.243.95 <none> 443/TCP
#记住ingress-nginx-controller的端口映射80=>31546
(2)部署Ingress
在安装本文的Ingress时,Ingress class已连带被定义,所以直接部署 Ingress
[root@k8s-master tdr]# kubectl get ingressclasses.networking.k8s.io
NAME CONTROLLER PARAMETERS AGE
nginx k8s.io/ingress-nginx <none> 29m
[root@k8s-master tdr]# vim web-ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-ingress
spec:
ingressClassName: nginx
rules:
- host: wp-web.com #域名
http:
paths:
- backend:
service:
name: wordpress-service #service名称,这里要匹配到wordpress的service
port:
number: 80
path: /
pathType: ImplementationSpecific #路径匹配方式
[root@k8s-master tdr]# kubectl create -f web-ingress.yaml
ingress.networking.k8s.io/nginx-ingress created
5. 访问测试
(1)主机hosts劫持
修改 windows 映射文件:C:\Windows\System32\drivers\etc
找到 hosts 文件,使用记事本打开,编辑最后的内容

(2)测试访问IP
访问 IP+Ingress 映射的端口是无法进入后端服务器的

(3)测试访问 URL
只有访问先前定义的域名+端口才可访问到后端服务器
本次实战域名服务器为:wp-web.com:31546
后续论坛网站自行搭建

相关文章:

项目实战:Ingress搭建Nginx+WP论坛+MariaDB
1. 网站架构 本次部署形式完全舍弃 Docker,将所有应用都置于Kubernetes,采用 Deployment 而非单 Pod 部署,稳定性得到升级。 2. 部署 MariaDB [rootk8s-master ~]# mkdir tdr [rootk8s-master ~]# cd tdr/ (1)定义 …...
UWA支持鸿蒙HarmonyOS NEXT
华为在开发者大会上,宣布了鸿蒙HarmonyOS NEXT将仅支持鸿蒙内核和鸿蒙系统的应用,不再兼容安卓应用,这意味着它将构建一个全新且完全独立的生态系统。 为此,UWA也将在最新版的UWA SDK v2.5.0中支持鸿蒙HarmonyOS NEXT,…...

【齐家网-注册/登录安全分析报告】
前言 由于网站注册入口容易被黑客攻击,存在如下安全问题: 暴力破解密码,造成用户信息泄露短信盗刷的安全问题,影响业务及导致用户投诉带来经济损失,尤其是后付费客户,风险巨大,造成亏损无底洞…...

MyBatis 基本概念
MyBatis 基本概念详解 MyBatis 是一个优秀的持久层框架,它支持定制 SQL、存储过程以及高级映射,用于将 Java 对象与数据库中的记录进行映射。作为 ORM(对象关系映射)框架,MyBatis 的主要优势在于灵活性高,…...

前端开发之装饰器模式
介绍 装饰器模式 是在不修改对象内部结构的情况下,动态地给对象添加功能的一种设计模式。在软件开发中,有时候我们需要为已有对象添加一些额外的行为,但不希望修改该对象的代码,装饰器模式可以很好的满足这一需求。 在TypeScrip…...

【STL】pair 与 map:基础、操作与应用
C 标准库中提供了许多用于处理数据结构的容器和工具。pair 和 map 是两个非常有用的工具,广泛应用于存储和处理关联数据。在本文中,我们将详细介绍 pair 与 map 的相关操作,并结合代码实例为读者提供清晰的理解。 pair:成对数据的…...

深度学习-图像处理篇4VGG网络
CNN感受野...

初级css+初级选择器
一、css基础样式 html: 标签 > 网页骨架 css: 美化这个网页的骨架 >样式去装饰网页 1. css 层叠样式表 (英文全称: Cascading Style Sheets) >修饰网页内容 比如: 文字大小 颜色 网页排版 高宽等等 2. css写在哪里?——行内样式 内部样式 外部样…...

gitlab 的CI/CD (二)
前言 上文完成了gitlab-runner的基础配置及将gitlab的制品上传至软件包库(产品库)的脚本编写; 本文实现gitlab的ci/cd对远程服务器的操作; 介绍 要让Gitlab Runner部署到远程机器,远程机器必须信任gitlab runner账…...

【html】基础(一)
本专栏内容为:前端专栏 记录学习前端,分为若干个子专栏,html js css vue等 💓博主csdn个人主页:小小unicorn ⏩专栏分类:js专栏 🚚代码仓库:小小unicorn的代码仓库🚚 &am…...

【网站架构部署与优化】Nginx优化
文章目录 Nginx服务优化一、隐藏Nginx版本号,避免安全漏洞泄漏方法一:通过修改配置文件方法二:通过修改源码并重新编译安装 修改Nginx的用户和组修改用户与组 配置Nginx网页缓存时间配置Nginx连接保持的超时时间KeepAlive模式简介Nginx中的超…...

gitlab修改访问端口
目录 1.找到gitlab.rb文件,一般在/etc/gitlab/路径下 2.打开配置文件,加上代码 3.重新配置 4.重启gitlab 1.找到gitlab.rb文件,一般在/etc/gitlab/路径下 2.打开配置文件,加上代码 打开文件 sudo vi gitlab.rb 加上默认端口配…...

分库分表-分页排序查询
优质博文:IT-BLOG-CN 背景:我们系统上云后,数据根据用户UDL部分数据在国内,部分数据存储在海外,因此需要考虑分库查询的分页排序问题 一、分库后带来的问题 需求根据订单创单时间进行排序分页查询,在单表…...

【openwrt-21.02】openwrt PPTP Passthrough 不生效问题解决方案
Openwrt版本 NAME="OpenWrt" VERSION="21.02-SNAPSHOT" ID="openwrt" ID_LIKE="lede openwrt" PRETTY_NAME="OpenWrt 21.02-SNAPSHOT" VERSION_ID="21.02-snapshot" HOME_URL="https://openwrt.org/" …...

【编程基础知识】Mysql的各个索引数据结构及其适用场景
一、引言 在数据库的世界中,索引是提升查询速度的超级英雄。就像图书馔的目录帮助我们快速找到书籍一样,MySQL中的索引加速了数据检索的过程。本文将带你深入了解MySQL索引的多种数据结构、它们的适用场景以及如何巧妙地使用它们来优化性能。 二、索引…...

解决IDEA出现:java: 程序包javax.servlet不存在的问题
问题截图: 解决如下: 1. 点击文件——>项目结构 2. 点击库——>点击——>点击java 3. 找到Tomcat的文件夹,找到lib文件夹中的servlet-api.jar,点击确定 4. 选择要添加的模块 5. 点击应用——>确定...
Comfyui控制人物骨骼,细节也能完美调整!
前言 本文涉及的工作流和插件,需要的朋友请扫描免费获取哦~ 在我们利用Comfyui生成图像的工作中,是否常常因为人物的动作无法得到精确的控制而感到苦恼,生成出来的图片常常达不到自己心中满意的效果。 今天给大家分享的这个工作流ÿ…...
)
mysql学习教程,从入门到精通,SQL LEFT JOIN 语句(23)
1、SQL LEFT JOIN 语句 在SQL中,LEFT JOIN(也称为左连接)是一种将左表(LEFT JOIN左侧的表)的所有记录与右表(LEFT JOIN右侧的表)中匹配的记录结合起来的查询方式。如果左表中的记录在右表中没有…...

VSCode远程切换Python虚拟环境
VSCode远程切换Python虚拟环境 引言 在现代开发环境中,使用虚拟环境来管理项目依赖是一种普遍的做法。它不仅可以避免不同项目间的依赖冲突,还能让开发者更好地控制和隔离各个项目的环境。Visual Studio Code(VSCode)是一款广受…...

【CSS in Depth 2 精译_038】6.2 CSS 定位技术之:绝对定位
当前内容所在位置(可进入专栏查看其他译好的章节内容) 第一章 层叠、优先级与继承(已完结)第二章 相对单位(已完结)第三章 文档流与盒模型(已完结)第四章 Flexbox 布局(已…...
最新SpringBoot+SpringCloud+Nacos微服务框架分享
文章目录 前言一、服务规划二、架构核心1.cloud的pom2.gateway的异常handler3.gateway的filter4、admin的pom5、admin的登录核心 三、code-helper分享总结 前言 最近有个活蛮赶的,根据Excel列的需求预估的工时直接打骨折,不要问我为什么,主要…...
华为云Flexus+DeepSeek征文|DeepSeek-V3/R1 商用服务开通全流程与本地部署搭建
华为云FlexusDeepSeek征文|DeepSeek-V3/R1 商用服务开通全流程与本地部署搭建 前言 如今大模型其性能出色,华为云 ModelArts Studio_MaaS大模型即服务平台华为云内置了大模型,能助力我们轻松驾驭 DeepSeek-V3/R1,本文中将分享如何…...

【Oracle】分区表
个人主页:Guiat 归属专栏:Oracle 文章目录 1. 分区表基础概述1.1 分区表的概念与优势1.2 分区类型概览1.3 分区表的工作原理 2. 范围分区 (RANGE Partitioning)2.1 基础范围分区2.1.1 按日期范围分区2.1.2 按数值范围分区 2.2 间隔分区 (INTERVAL Partit…...
-HIve数据分析)
大数据学习(132)-HIve数据分析
🍋🍋大数据学习🍋🍋 🔥系列专栏: 👑哲学语录: 用力所能及,改变世界。 💖如果觉得博主的文章还不错的话,请点赞👍收藏⭐️留言Ǵ…...
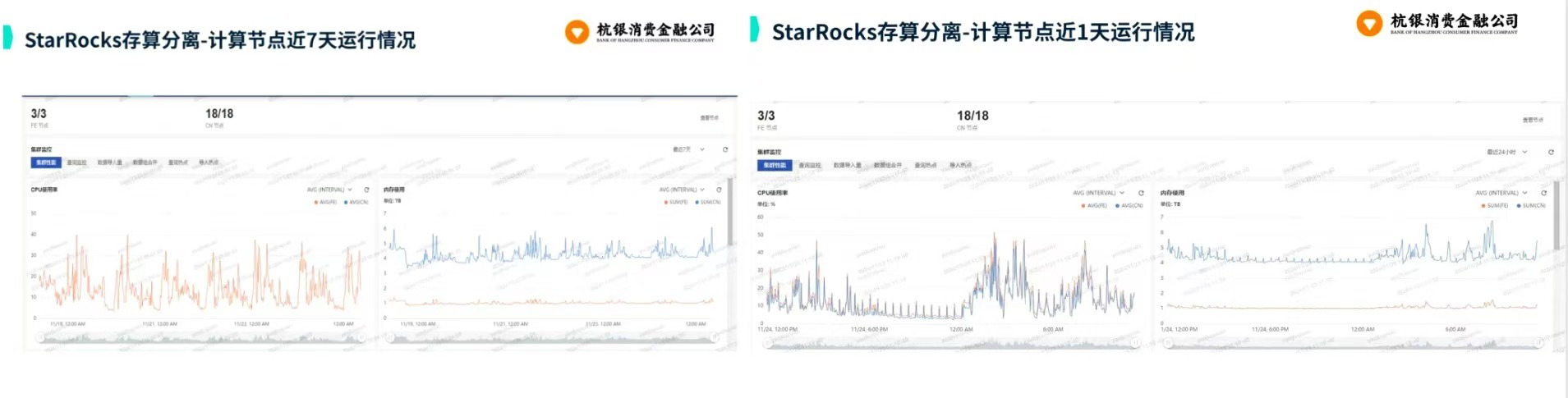
从 GreenPlum 到镜舟数据库:杭银消费金融湖仓一体转型实践
作者:吴岐诗,杭银消费金融大数据应用开发工程师 本文整理自杭银消费金融大数据应用开发工程师在StarRocks Summit Asia 2024的分享 引言:融合数据湖与数仓的创新之路 在数字金融时代,数据已成为金融机构的核心竞争力。杭银消费金…...

Sklearn 机器学习 缺失值处理 获取填充失值的统计值
💖亲爱的技术爱好者们,热烈欢迎来到 Kant2048 的博客!我是 Thomas Kant,很开心能在CSDN上与你们相遇~💖 本博客的精华专栏: 【自动化测试】 【测试经验】 【人工智能】 【Python】 使用 Scikit-learn 处理缺失值并提取填充统计信息的完整指南 在机器学习项目中,数据清…...

Pydantic + Function Calling的结合
1、Pydantic Pydantic 是一个 Python 库,用于数据验证和设置管理,通过 Python 类型注解强制执行数据类型。它广泛用于 API 开发(如 FastAPI)、配置管理和数据解析,核心功能包括: 数据验证:通过…...

【HarmonyOS 5】鸿蒙中Stage模型与FA模型详解
一、前言 在HarmonyOS 5的应用开发模型中,featureAbility是旧版FA模型(Feature Ability)的用法,Stage模型已采用全新的应用架构,推荐使用组件化的上下文获取方式,而非依赖featureAbility。 FA大概是API7之…...

CppCon 2015 学习:Time Programming Fundamentals
Civil Time 公历时间 特点: 共 6 个字段: Year(年)Month(月)Day(日)Hour(小时)Minute(分钟)Second(秒) 表示…...

Vue 3 + WebSocket 实战:公司通知实时推送功能详解
📢 Vue 3 WebSocket 实战:公司通知实时推送功能详解 📌 收藏 点赞 关注,项目中要用到推送功能时就不怕找不到了! 实时通知是企业系统中常见的功能,比如:管理员发布通知后,所有用户…...
