CCNP350-401学习笔记(301-350题)
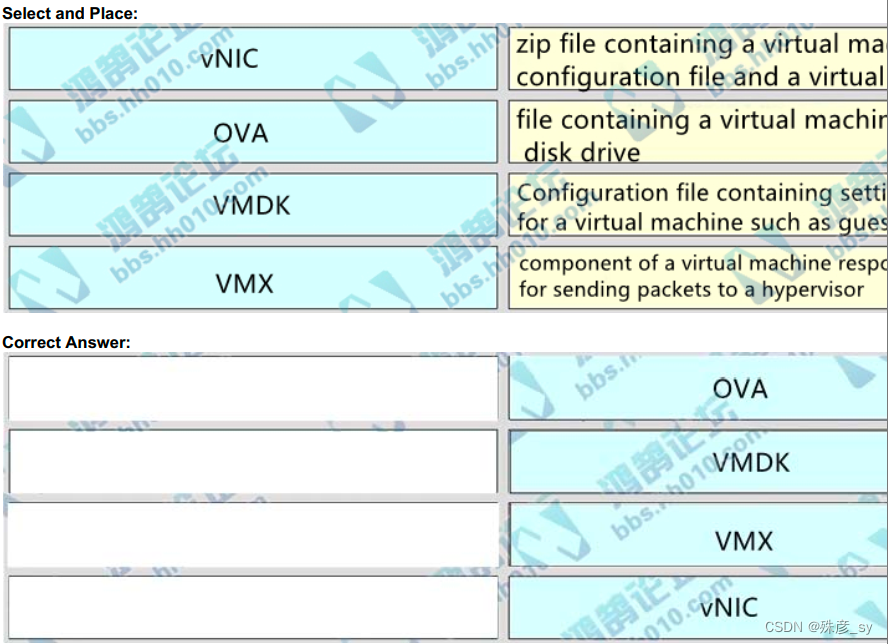
301、Drag and drop the virtual component from the left onto their descriptions on the right.
302、Which two actions, when applied in the LAN network segment, will facilitate Layer 3 CAPWAP discovery for lightweight AP? (Choose two.)
A. Utilize DHCP option 43
B. Configure WLC IP address on LAN switch
C. Enable port security on the switch port.
D. Utilize DHCP option 17
E. Configure an ip helper-address on the router interface.
303、
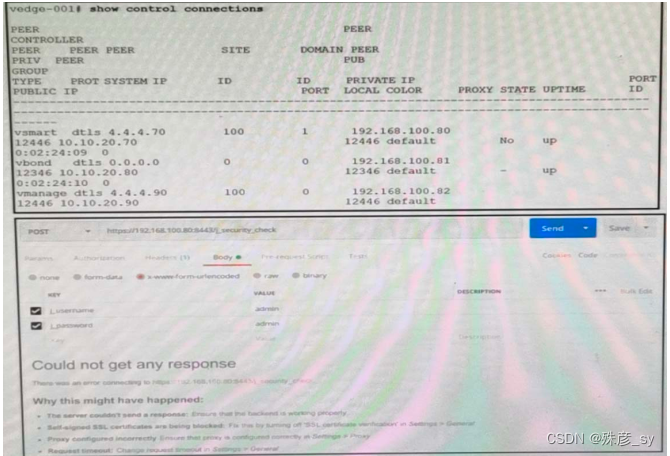
Refer to the exhibit. What step resolves the authentication issue?
A. use basic authentication
B. change the port to 12446
C. target 192 168.100.82 in the URI
D. restart the vsmart host
304、 Which data is properly formatted with JSON?
A. {
"name": "Peter",
"age", "25",
"likesJson": true,
"characteristics": ["small","strong",18]
}
B. {
"name": "Peter",
"age": "25",
"likesJson": true,
"characteristics": ["small","strong","18"],
}
C. {
"name": Peter,
"age": 25,
"likesJson": true,
"characteristics": ["small","strong","18"],
}
D. {
"name":"Peter"
"age":"25"
"likesJson":true
"characteristics":["small","strong",18]
}
305、
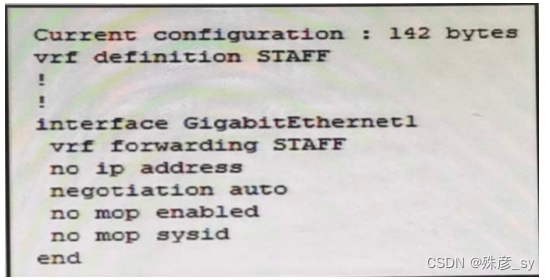
Refer to the exhibit. An engineer must assign an IP address of 192. 168.1.1/24 to the GigabitEthemnet interface. Which two commands must be.added to the existing configuration to accomplish this task?(Choose two.)
A. Router(config-if)#ip address 192.168.1.1 255.255.255.0
B. Router(config-if)#address-family ipv4
C. Router(config-vrf)#address-family ipv6
D. Router(config-vrf)#address-family ipv4
E. Router(config-vrf)#ip address 192.168.1.1 255.255.255.0
306、A company has an existing Cisco 5520 HA cluster using SSO. An engineer deploys a new single Cisco Catalyst 9800 WLC to test new features. The engineer successfully configures a mobility tunnel between the 5520 cluster and 9800 WLC.Clients connected to the corporate WLAN roam seamlessly between access points on the 5520 and 9800 WLC. After a failure on the primary 5520 WLC, all WLAN services remain functional;however, clients cannot roam between the 5520 and 9800 controllers without dropping their connection. Which feature must be configured to remedy the issue?
A. mobility MAC on the 5520 cluster
B. mobility MAC on the 9800 WLC
C. new mobility on the 5520 cluster
D. new mobility on the 9800 WLC
307、Which three methods does Cisco DNA Center use to discover devices? (Choose three.)
A. CDP
B. SNMP
C. LLDP
D. ping
E. NETCONF
F. a specified range of IP addresses
308、What is the difference between the MAC address table and TCAM?
A. The MAC address table supports partial matches. TCAM requires an exact match
B. TCAM is used to make L2 fonwarding decisions. CAM is used to build routing tables
C. The MAC address table is contained in TCAM. ACL and QoS information is stored in TCAM
D. Router prefix lookups happen in TCAM. MAC address table lookups happen in CAM
309、The following system log message is presented after a network administrator configures a GRE tunnel:%TUN-RECURDOWN Interface Tunnel 0 temporarily disabled due to recursive
routing
Why is Tunnel 0 disabled?
A. Because dynamic routing is not enabled
B. Because the tunnel cannot reach its tunnel destination.
C. Because the best path to the tunnel destination is through the tunnel itself
D. Because the router cannot recursively identify its egress forwarding interfac
310、

Refer to the exhibit. A network engineer must simplify the IPsec configuration by enabling IPsec over GRE
using IPsec profiles. Which two configuration changes accomplish this? (Choose two).
A. Remove the crypto map and modify the ACL to allow traffc between 10.10.0.0/24 to 10.20.0.0/24.
B. Create an IPsec profile, associate the transform-set ACL, and apply the profile to the tunnel interface.
C. Apply the crypto map to the tunnel interface and change the tunnel mode to tunnel mode ipsec ipv4
D. Remove all configuration related to crypto map from R1 and R2 and eliminate the ACL
E. Create an IPsec profile, associate the transform-set, and apply the profile to the tunnel interface.
311、
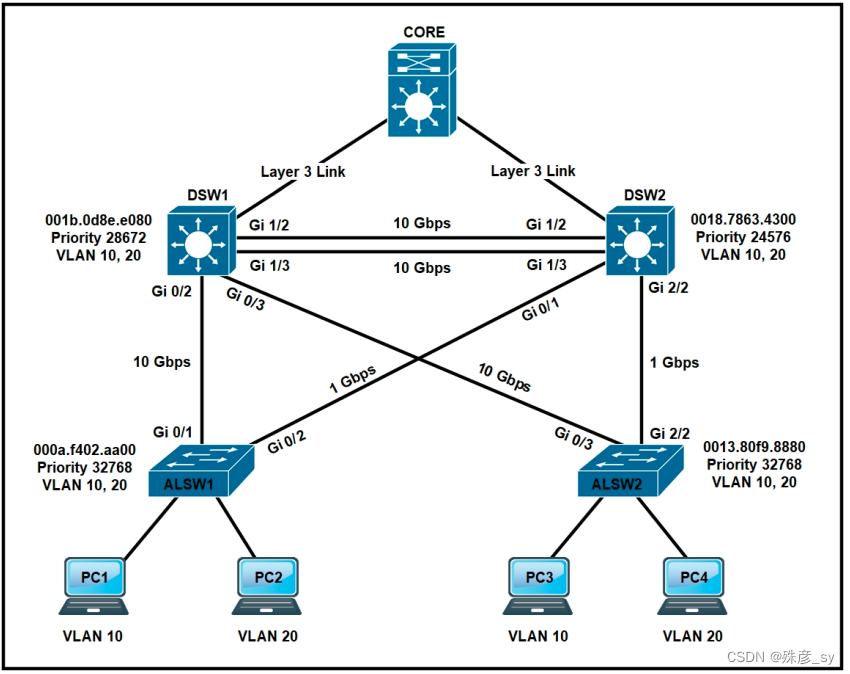
Refer to the exhibit. All switches are confiqured with the default port priority value. Which two commands ensure that traffic from PC1 is forwarded over the Gi1/3 trunk port between DSW1 and DSW2? (Choose two.)
A. DSW1 (config-if)#spanning-tree port-priority 0
B. DSW2(config-if)#spanning-tree port-priority 128
C. DSW2(config-if)#spanning-tree port-priority 16
D. DSW2(config)#interface gi1/3
E. DSW1(config)#interface gi1/3
312、Which encryption hashing algorithm does NTP use for authentication?
A. SSL
B. MD5
C. AES128
D. AES256
313、A customer has completed the installation of a Wi-Fi 6 greenfield deployment at their new campus. They want to leverage Wi-Fi 6 enhanced speeds.on the trusted employee WLAN. To configure the employee WLAN, which two Layer 2 security policies should be used? (Choose two.)
A. WPA (AES)
B. WEP
C. WPA2 (AES)
D. 802.1X
E. OPEN
314、

Refer to the exhibit. A network engineer configures OSPF and reviews the router confguration. Whichinterface or interfaces are able to establish OSPF adjacency?
A. GigabitEthernet0/1 and GigabitEthemnet0/1.40
B. only GigabitEthernet0/0
C. GigabitEthernet0/0 and GigabitEthernet0/1
D. only GigabitEthernet0/1
315、

Refer to the exhibit. Communication between London and New York is down. Which command set must be
applied to resolve this issue?
A. NewYork(config)int f0/1
NewYork(config)#switchport mode dynamic desirable
NewYork(config)end
NewYork#
B. NewYork(config)int f0/1
NewYork(config)switchport nonegotiate
NewYork(config)#end
NewYork#
C. NewYork(config)#int f0/1
NewYork(config)#switchport trunk encap dot1q
NewYork(config)#fend
NewYork#
D. NewYork(config)#int f0/1
NewYork(config)#switchport mode trunk
NewYork(config)#end
NewYork#
316、 What is YANG used for?
A. scraping data via CLI
B. processing SNMP read-only polls
C. describing data models
D. providing a transport for network configuration data between client and server
317、An engineer must configure a GRE tunnel interface in the default mode. The engineer has assigned an IPv4 address on the tunnel and sourced the tunnel from an Ethernet interface. Which additional configuration must be made on the tunnel interface?
A. (config-if)# tunnel destination <ip address>
B. (config-if)# keepalive <seconds retries>
C. (config-if)# ip tcp adjust-mss <value>
D. (config-if)# ip mtu svalue>
318、
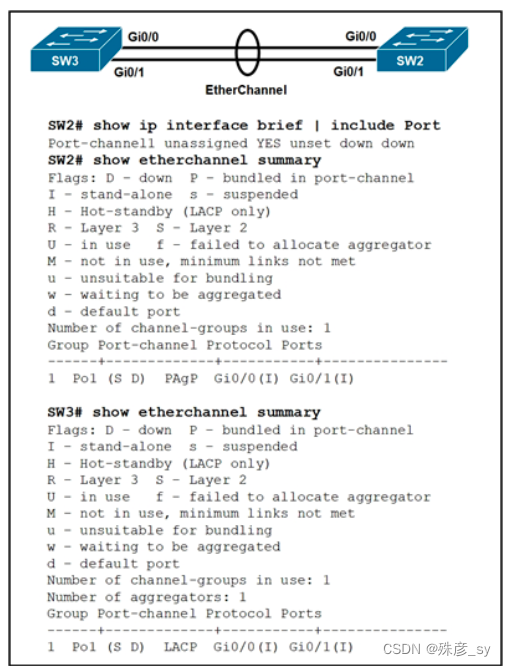
Refer to the exhibit. Which action resolves the EtherChannel issue between SW2 and SW3?
A. Configure channel-group 1 mode active on both interfaces
B. Configure switchport mode trunk on SW2
C. Configure switchport nonegotiate on SW3
D. Configure channel-group 1 mode desirable on both interfaces
319、Which two network problems indicate a need to implement QoS in a campus network? (Choose two.)
A. port flapping
B. excess jitter
C. misrouted network packets
D. duplicate IP addresses
E. bandwidth-related packet loss
320、

Refer to the exhibit Which configuration change ensures that R1 is the active gateway whenever it is in a functional state for the 172. 30.110.0/24 network?
A. R2
standby 1 priority 100
standby 1 preempt
B. R1
standby 1 preempt
R2
standby 1 priority 100
C. R1
standby 1 preempt
R2
standby 1 priority 90
D. R2
standby 1 priority 90
standby 1 preempt
321、In a Cisco SD-Access solution, what is the role of the Identity Services Engine?
A. It is leveraged for dynamic endpoint to group mapping and policy definition.
B. It provides GUI management and abstraction via apps that share context
C. It is used to analyze endpoint to app flows and monitor fabric status
D. It manages the LISP EID database.
322、Which two methods are used to reduce the AP coverage area? (Choose two.)
A. Reduce AP transmit power.
B. Reduce channel width from 40 MHz to 20 MHz.
C. Disable 2.4 GHz and use only 5 GHz.
D. Increase minimum mandatory data rate.
E. Enable Fastlane.
323、Which outcome is achieved with this Python code?client.connect (ip, port= 22, username= usr, password= pswd )stdin, stdout, stderr = client.exec_command ('show ip bgp 192.168.101.0
bestpathin')print (stdout)
A. connects to a Cisco device using SSH and exports the BGP table for the prefix
B. connects to a Cisco device using SSH and exports the routing table information
C. displays the output of the show command in a formatted way
D. connects to a Cisco device using Telnet and exports the routing table information
324、Which technology does VXLAN use to provide segmentation for Layer 2 and Layer 3 traffic?
A. VNI
B. VRF
C. bridge domain
D. VLAN
325、Based on the output below, which Python code shows the value of the "upTime" key?
{
"response": [{
"family": "Routers",
"type. "Cisco ASR 1001-X Router",
"errorCode": null
"location": null,macAddress" "00:c8:8b:80:bc:00",
"hostname": "asr1001-x abcinc","role": "BORDER ROUTER",
"lastUpdateTime": 1577391777128,
"serialNumber":"FXS1932Q2SE",
"softwareeVersion": "16.3.2",
"locationName": null,
"upTime":"49 days. 13:43:44:231",
"lastUpdated": "2019-12-22 14:55:23"
}]
}
A. json_data = json.loads(response text)
print(json_datalresponsel['family']['upTime'])
B. json_data = response.json()
print(json_data['response'][0]['upTime'])
C. json_data = response.json()
print(json_data)['response'][family]['upTime'])
D. json_data = response.json()
print(json_data['response'][0][upTime])
326、
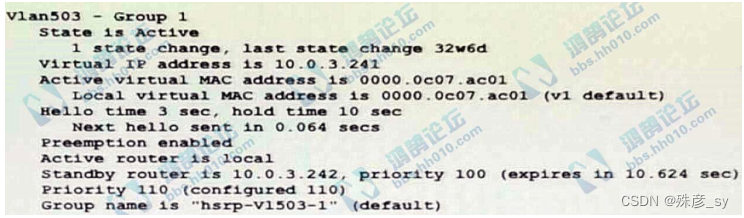
Refer to the exhibit. Which two facts does the device output confirm? (Choose two.)
A. The device's HSRP group uses the virtual IP address 10.0.3.242
B. The device is configured with the default HSRP priority.
C. The standby device is configured with the default HSRP priority.
D. The device is using the default HSRP hello timer.
E. The device sends unicast messages to its peers.
327、In a three-tier hierarchical campus network design, which action is a design best-practice for the core layer?A. provide QoS prioritization services such as marking, queueing, and classification for critical network traffic.
B. provide redundant Layer 3 point-to-point links between the core devices for more predictable and faster convergence
C. provide advanced network security features such as 802.1X. DHCP snooping, VACLs, and port security
D. provide redundant aggregation for access layer devices and first-hop redundancy protocols such as VRRP
328、What is a VPN in a Cisco SD-WAN deployment?
A. common exchange point between two different services
B. attribute to identify a set of services offered in specific places in the SD-WAN fabric
C. virtualized environment that provides traffic isolation and segmentation in the SD-WAN fabric
D. virtual channel used to carry control plane information
329、What is an emulated machine that has dedicated compute, memory, and storage resources and a fully installed operating system?
A. container
B. mainframe
C. host
D. virtual machine
330、Which entity is a Type 1 hypervisor?
A. Oracle VM VirtualBox
B. VMware server
C. Citrix XenServer
D. Microsoft Virtual PC
331、
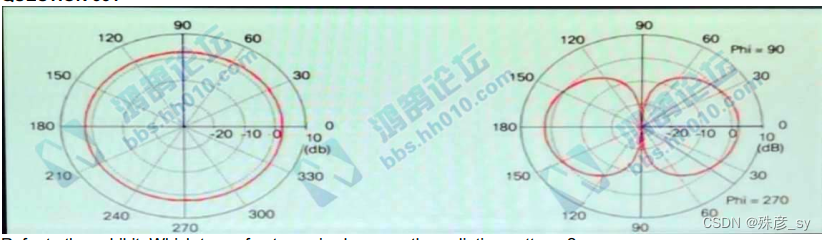
Refer to the exhibit. Which type of antenna is shown on the radiation patterns?
A. omnidirectional
B. Yagi
C. dipole
D. patch
332、

Refer to the exhibit. Which JSON syntax is derived from this data?
A. {[{'First Name': Johnny', "Last Name': 'Table', "Hobbies': [Running', Video games']}, {First Name' 'Billy, "Last Name': 'Smith', "Hobbies': ['Napping', 'Reading']}]}
B. {'Person': [{First Name': 'Johnny', 'Last Name': 'Table', "Hobbies: 'Running', 'Video games'}, {First Name': 'Billy', 'Last Name': 'Smith', "Hobbies": Napping', Reading'}]}
C. {[{'First Name': 'Johnny', "Last Name': 'Table', 'Hobbies': 'Running', 'Hobbies': 'Video games'}, {'First Name': 'Billy', 'Last Name': 'Smith','Hobbies': 'Napping', 'Hobbies': 'Reading'}]}
D. {'Person': {{'First Name': 'Johnny', 'Last Name': 'Table', 'Hobbies': ['Running', 'Video games']}, {'First Name': 'Billy', 'Last Name': 'Smith','Hobbies':['Napping', 'Reading']}]}
333、In a fabric-enabled wireless network, which device is responsible for maintaining the endpoint ID database?
A. fabric border node
B. fabric edge node
C. fabric wireless controller
D. control plane node
334、

Refer to the exhibit A network administrator confiqured RSPAN to troubleshoot an issue between switch1 and switch2. The switches are connected using interface GigabitEthernet 1/1. An external packet capture device is connected to swich2 interface GigabitEthernet1/2. Which two commands must be added to complete this confiquration? (Choose two.)
A. switch2(config)# monitor session 2 destination vlan 10
B. switch1(config)# interface GigabitEthernet 1/1
switch1(confia-if# switchport mode access
switch1(config-if)# switchport access vlan 10
switch2(config)# interface GigabitEthernet 1/1
switch2(config-if)# switchport mode access
switch2(config-if)# switchport access vlan 10
C. switch2(config)# monitor session 1 source remote vlan 70
switch2(config)# monitor session 1 destination interface GigabitEthernet1/1
D. switch2(config-if)# switchport trunk allowed vlan 10,20,30,40,50,60,70-80
E. switch2(config)# monitor session 1 source remote vlan 70
switch2(confia)# monitor session 1 destination interface GigabitEthernet1/2
335、What is the data policy in a Cisco SD-WAN deployment?
A. list of ordered statements that define node configurations and authentication used within the SDWAN overlay
B. Set of statements that defines how data is forwarded based on IP packet information and specific VPNs
C. detailed database mapping several kinds of addresses with their corresponding location
D. group of services tested to guarantee devices and links liveliness within the SD-WAN overlay
336、What ate two characteristics of Cisco SD-Access elements? (Choose two )
A. The border node is required for communication between fabric and nonfabric devices.
B. Fabric endpoints are connected directly to the border node
C. Traffic within the fabric always goes through the control plane node
D. The control plane node has the full RLOC-to-EID mapping database
E. The border node has the full RLOC-to-EID mapping database
337、Drag and drop the solutions that comprise Cisco Cyber Threat Defense from the left onto the objectives they accomplish on the right.
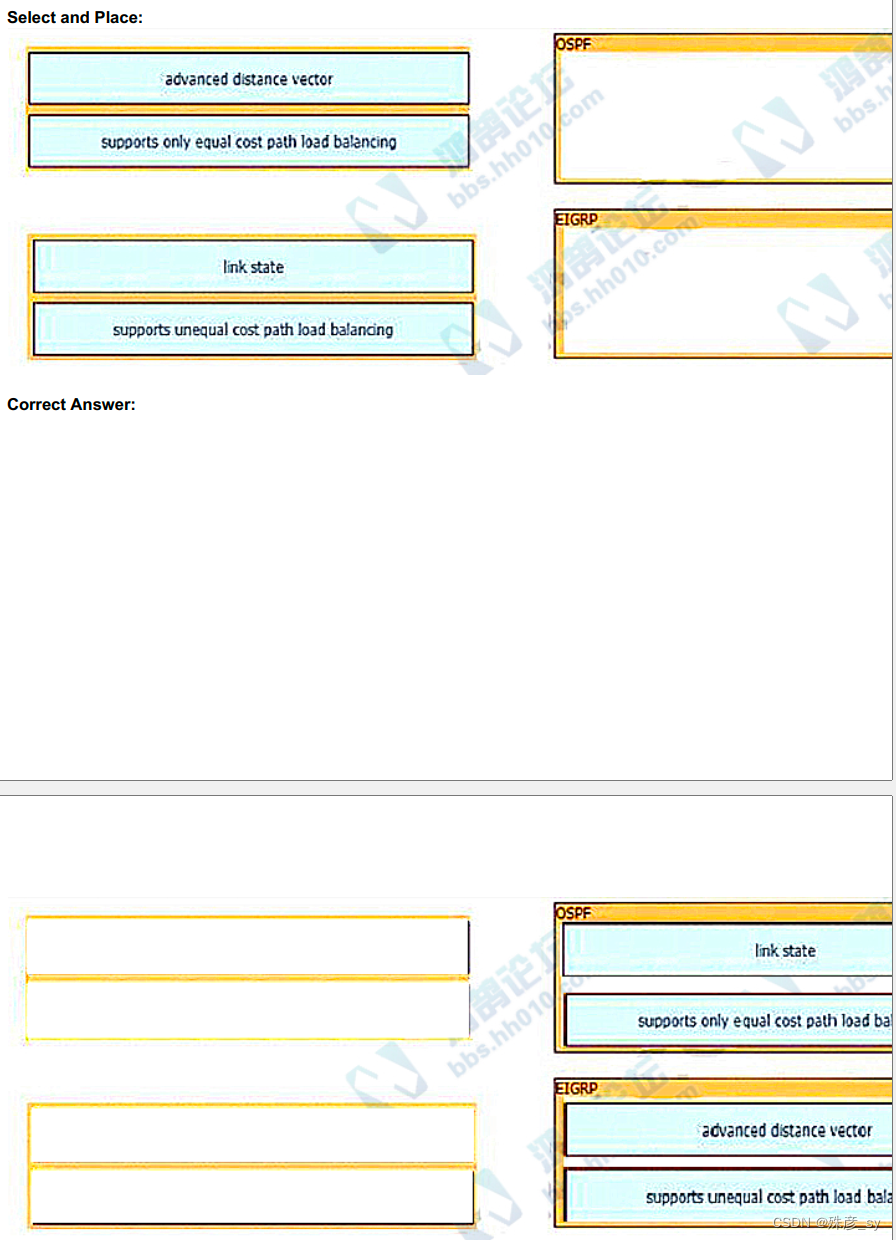
338、Drag and drop the descriptions from the left onto the routing protocol they describe on the right.
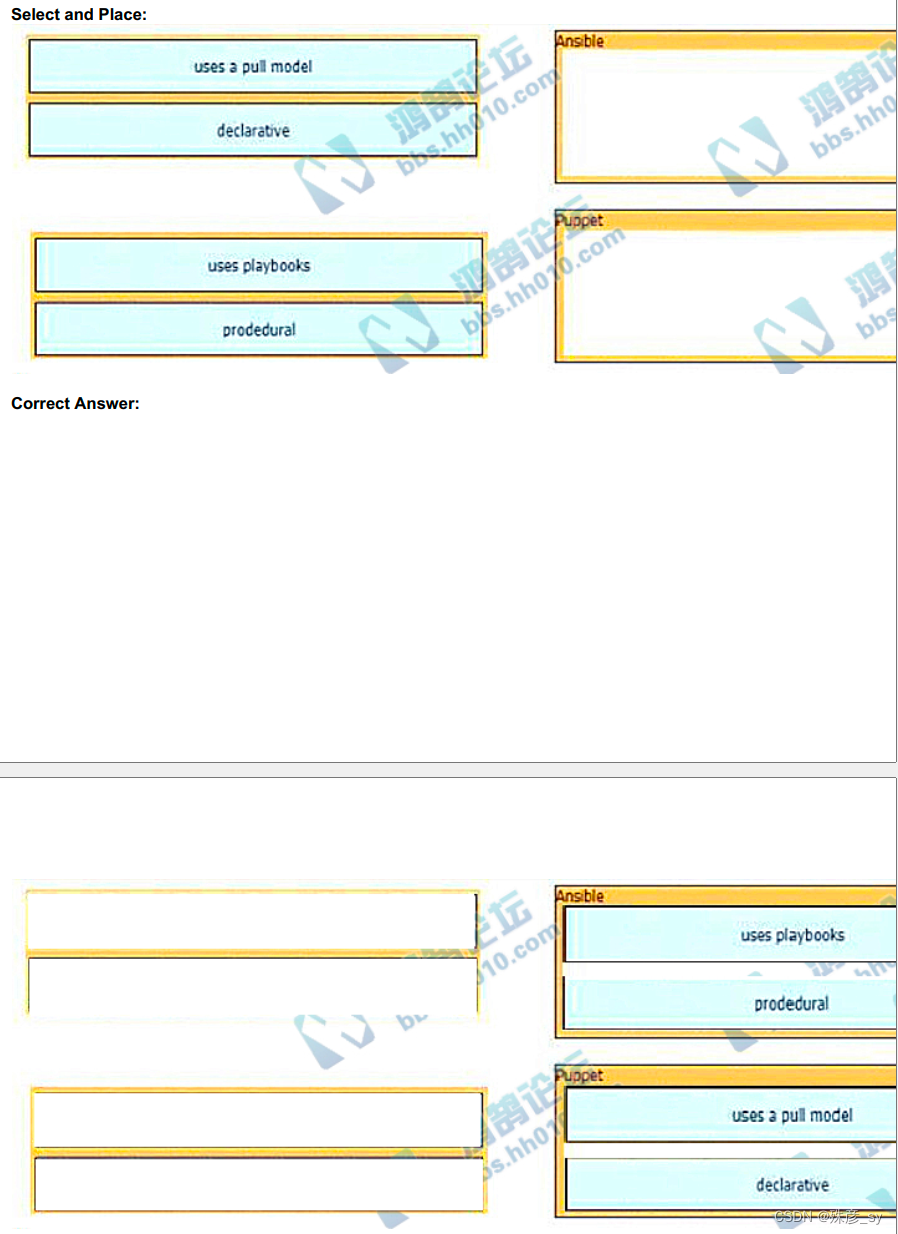
339、Drag and drop the characteristic from the left onto the orchestration tools that they describe on the right.
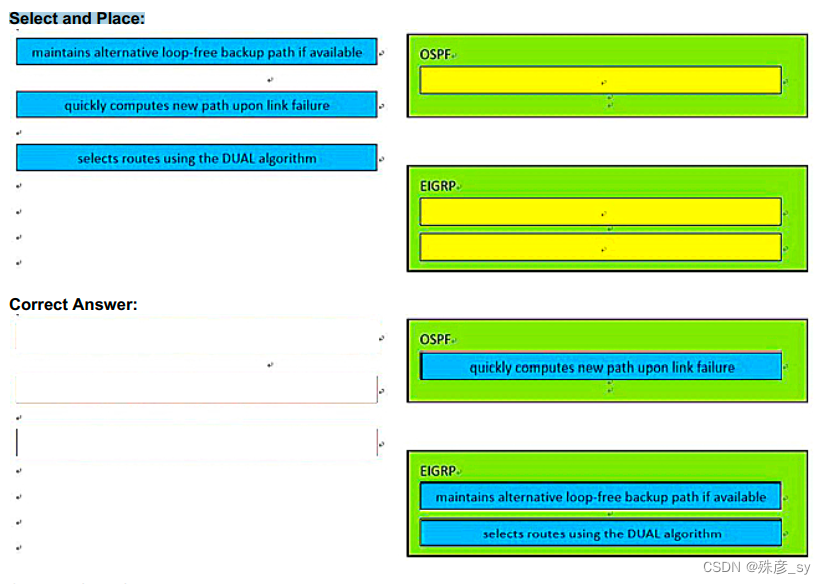
340、Drag and drop the characteristics from the left onto the routing protocols they describes on the right.
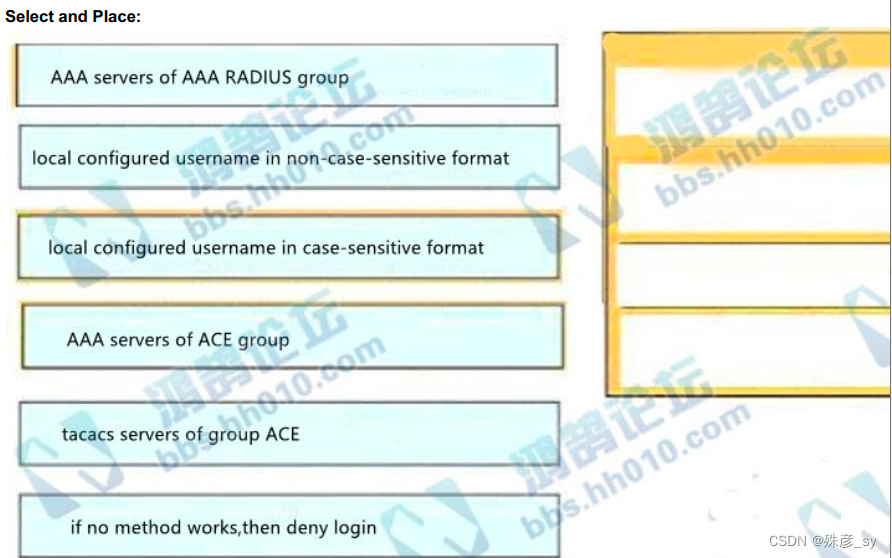
341、An engineer creates the configuration below. Drag and drop the authentication methods from the left into
the order of priority on the right. Not all options are used.
R1#show run | i aaa
aaa new-model
aaa authentication login default froup ACE group AAA_RADIUS local-case
aaa session-id common
R1#
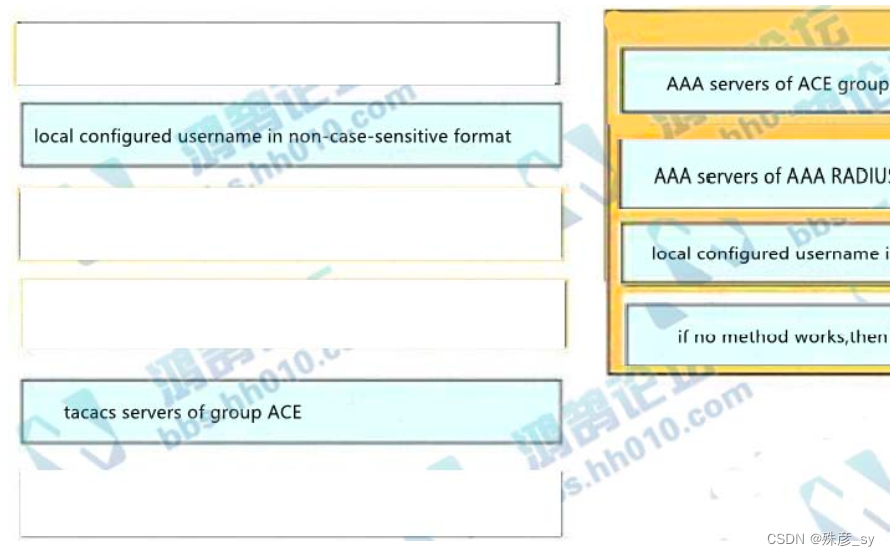
342、What is a characteristic of a virtual machine?
A. It must be aware of other virtual machines, in order to allocate physical resource for
them
B. It is deployable without a hypervisor to host it
C. It must run the same operating system as its host
D. It relies on hypervisor to allocate computing resources for it
343、 How do stratum levels relate to the distance from a time source?
A. Stratum 0 devices are connected directly to an authoritative time source
B. Stratum 1 devices are connected directly to an authoritative time source
C. Stratum 15 devices are connected directly to an authoritative time source
D. Stratum 15 devices are an authoritative time source
344、What is the function of a fabric border node in a Cisco SD-Access environment?
A. To collect traffic flow information toward external networks
B. To connect the Cisco SD-Access fabric to another fabric or external Layer 3 networks
C. To attach and register clients to the fabric
D. To handle an ordered list of IP addresses and locations for endpoints in the fabric
345、Which AP mode allows an engineer to scan configured channels for rogue access
points?
A. sniffer
B. monitor
C. bridge
D. local
346、
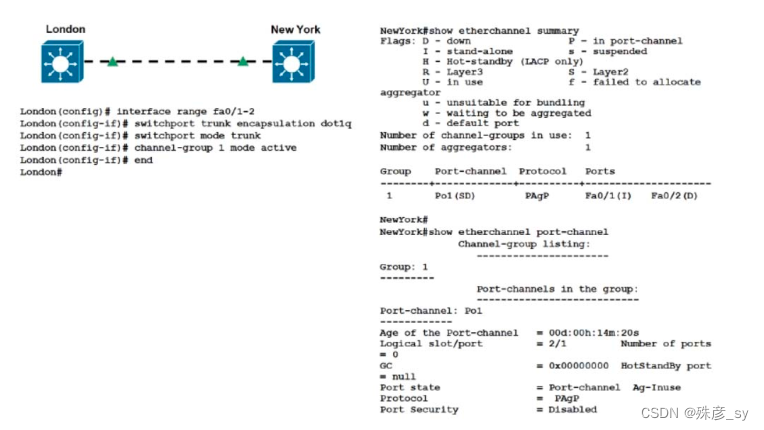
Refer to the exhibit. Communication between London and New York is down. Which
command set must be applied to the New York switch to resolve this issue?
A. NewYork(config)# no int po1
NewYork(config)# interface range fa-/1-2
NewYork(config-if)# channel-group 1 mode negotiate
NewYork(config)-if# end
NewYork#
B. NewYork(config)# no int po1
NewYork(config)# interface range fa-/1-2
NewYork(config-if)# channel-group 1 mode auto
NewYork(config)-if# end
NewYork#
C. NewYork(config)# no int po1
NewYork(config)# interface range fa-/1-2
NewYork(config-if)# channel-group 1 mode on
NewYork(config)-if# end
NewYork#
D. NewYork(config)# no int po1
NewYork(config)# interface range fa-/1-2
NewYork(config-if)# channel-group 1 mode passive
NewYork(config)-if# end
NewYork#
347、
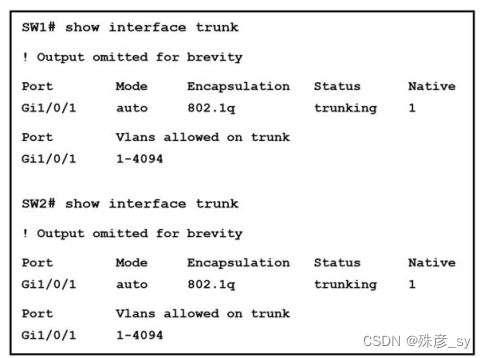
Refer to the exhibit. The trunk between Gig1/0/1 of switch SW2 and Gig1/0/1 of switch
SW1 is not operational.
Which action resolves this issue?
A. Configure both interfaces in dynamic auto DTP mode and ensure that the switches
are in the same VTP domain
B. Configure both interfaces in dynamic desirable DTP mode and ensure that the
switches are in the same VTP domain
C. Configure both interfaces in nonegotiate and ensure that the switches are in the
different VTP domain
D. Configure both interfaces in dynamic auto DTP mode and ensure that the switches
are in the different VTP domain
348、
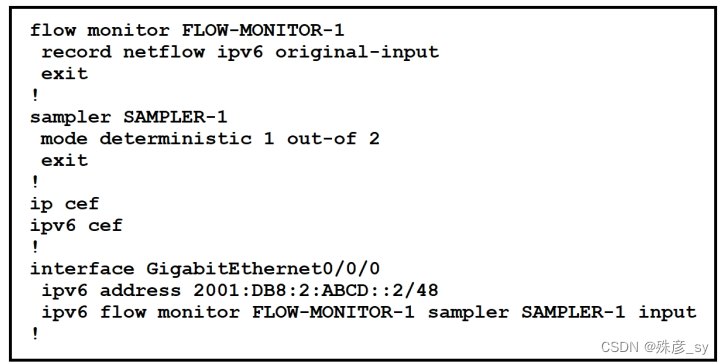
Refer to the exhibit. What is the effect of introducing the sampler feature into the FlexibleNetFlow configuration on the router?
A. NetFlow updates to the collector are sent 50% less frequently
B. Every second IPv4 packet is forward to the collector for inspection
C. CPU and memory utilization are reduced when compared with what is required for full
NetFlow
D. The resolution of sampling data increases, but it requires more performance from the
router
349、Which signal strength and noise values meet the minimum SNR for voice networks?
A. signal strength -69 dBm, noise 94 dBm
B. signal strength -67 dBm, noise 91 dBm
C. signal strength -68 dBm, noise 89 dBm
D. signal strength -66 dBm, noise 90 dBm
350、
Refer to the exhibit. Which command must be added to enable R2 to take over as master
when Serial Interface 0/0.1 is down on R1?
A. R1# no standy 100 track 26
B. R2# no standy 100 track 26
C. R2# standy 100 preempt
D. R2# standy 100 priority 100
相关文章:

CCNP350-401学习笔记(301-350题)
301、Drag and drop the virtual component from the left onto their descriptions on the right. 302、Which two actions, when applied in the LAN network segment, will facilitate Layer 3 CAPWAP discovery for lightweight AP? (Choose two.)A. Utilize DHCP option …...
【LeetCode】No.225. 用队列实现栈 -- Java Version
题目链接:https://leetcode.cn/problems/implement-stack-using-queues/ 1. 题目介绍(225. 用队列实现栈) 请你仅使用两个队列实现一个后入先出(LIFO)的栈,并支持普通栈的全部四种操作(push、t…...
45个写规范代码的小技巧
目录 1、规范命名 2、规范代码格式 3、写好代码注释 4、try catch 内部代码抽成一个方法 5、方法别太长 6、抽取重复代码 7、多用return 8、if条件表达式不要太复杂 9、优雅地参数校验 10、统一返回值 11、统一异常处理 12、尽量不传递null值 13、尽量不返回null值…...
MindFusion Diagramming for Java, 最新版 Crack
Diagramming for Java, V4.6.1 A unique Java Swing library for any type of flowchart.您需要的每一个图表功能 图表、方案、图形、网络、算法、树、图表 - 所有这些都是使用 MindFusion Diagramming for Java 工具快速轻松地构建的。结果令人着迷。 Java Dagram 库ÿ…...
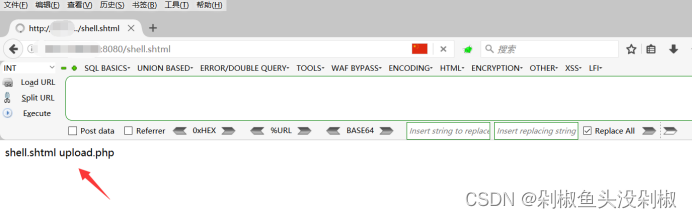
中间件安全—Apache常见漏洞
中间件安全—Apache常见漏洞1.Apache常见漏洞1.1.Apache介绍1.2.Apache HTTPD 换行解析漏洞(CVE-2017-15715)1.2.1.漏洞介绍1.2.2.漏洞环境1.2.2.1.运行漏洞环境1.2.2.2.访问漏洞环境1.2.3.漏洞复现1.2.3.1.拦截1.2.3.2.添加换行1.2.3.3.访问文件1.3.Apa…...
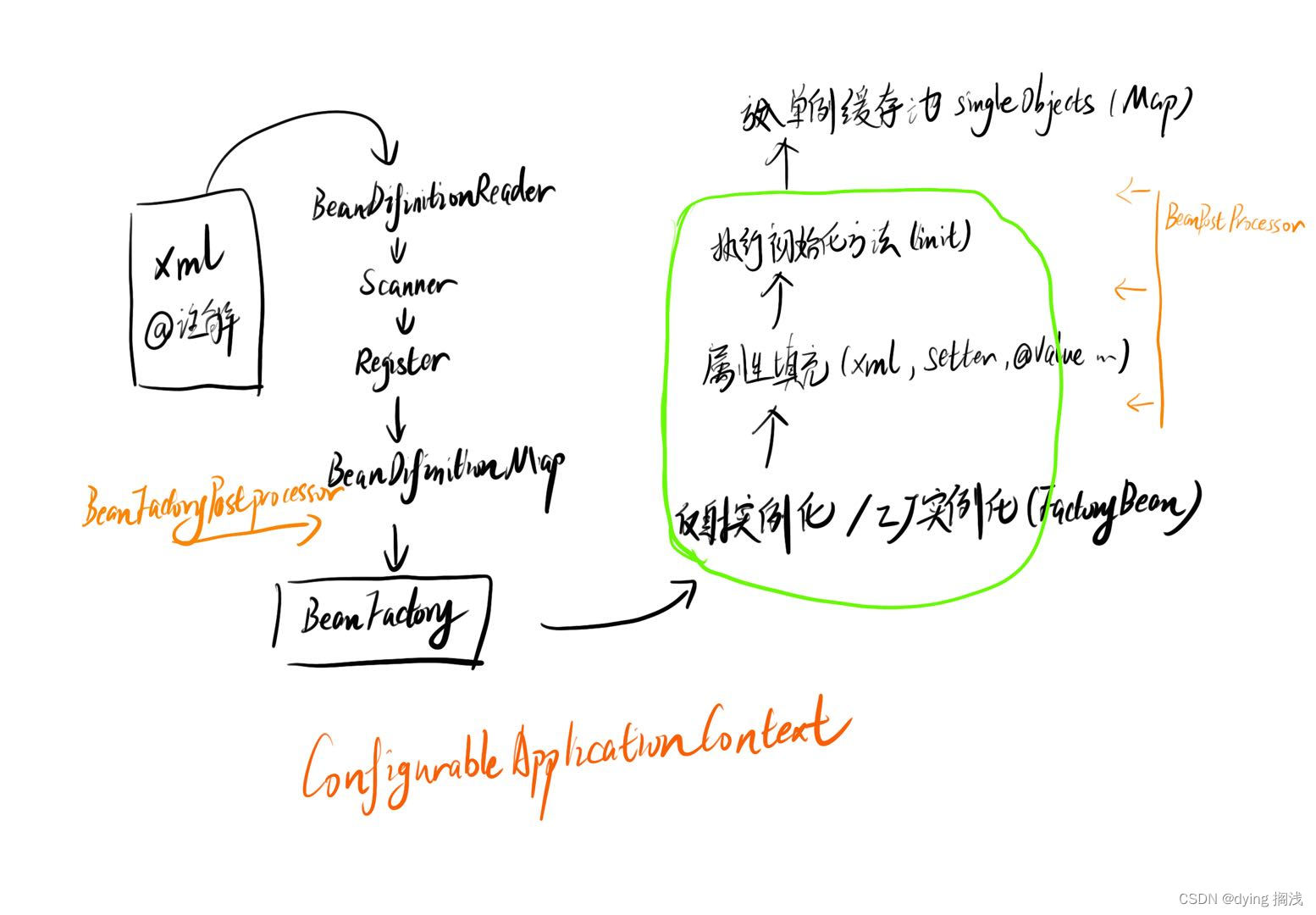
Spring IOC 容器 Bean 加载过程
Spring IOC 容器 Bean 加载过程 Spring 对于我们所有的类对象进行了统一抽象,抽象为 BeanDefinition ,即 Bean 的定义,其中定义了类的全限定类名、加载机制、初始化方式、作用域等信息,用于对我们要自动装配的类进行生成。 Sprin…...
)
【DRF】Django Rest Framework(5.DRF中的通用视图类-GenericAPIView方法说明与使用说明)
1. GenericAPIView [通用视图类],概述 继承自 APIView增加了操作序列化器和数据库查询的方法,作用是为下面Mixin扩展类的执行提供方法支持。通常在使用时,可搭配一个或者多个Mixin扩展类源码 当我们查看 GenericAPIView 的源码时,…...

STM32 OTA应用开发——自制BootLoader
STM32 OTA应用开发——自制BootLoader 目录STM32 OTA应用开发——自制BootLoader前言1 环境搭建2 BootLoader工作原理以及常见分区介绍3 BootLoader的制作4 烧录下载配置5 运行测试结束语前言 什么是OTA? 百度百科:空中下载技术(Over-the-Ai…...

时域和频域的简单理解
目录文章背景结论举例说明说回频域连续或离散总结文章背景 时域和频域在傅里叶变换和拉普拉斯变换,z变换中经常提到的高频词。本文的重点就是想说明怎么理解 “频域” 这个名词。 结论 频域就是一个信号 所有组成频率的取值范围的集合 举例说明 以大家从中小学开…...

华为OD机试 - 第 K 个最小码值的字母 | 机试题算法思路 【2023】
最近更新的博客 华为OD机试 - 简易压缩算法(Python) | 机试题算法思路 【2023】 华为OD机试题 - 获取最大软件版本号(JavaScript) 华为OD机试 - 猜字谜(Python) | 机试题+算法思路 【2023】 华为OD机试 - 删除指定目录(Python) | 机试题算法思路 【2023】 华为OD机试 …...
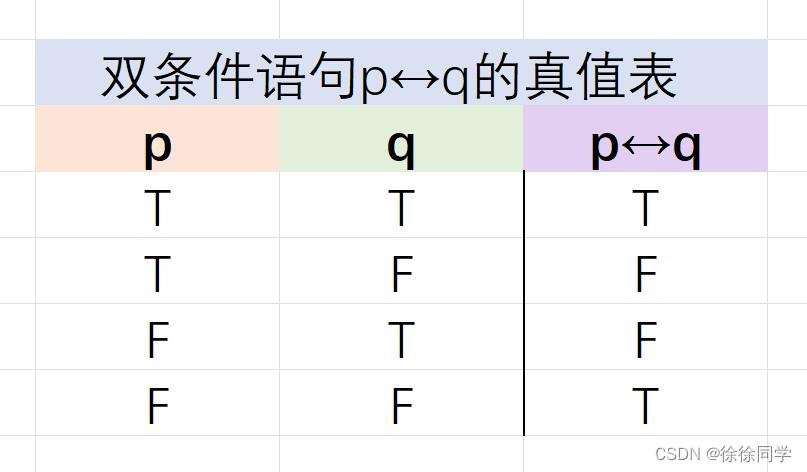
离散数学笔记_第一章:逻辑和证明(1)
1.1命题逻辑1.1.1 命题 1.1.2 逻辑运算符 定义1: 否定联结词定义2: 合取联结词定义3: 析取联结词定义4: 异或联结词1.1.3 条件语句 定义5: 条件语句定义6: 双条件语句1.1.1 命题 1.命题:是…...

Rust FFI 与C语言互相调用
参考 https://cloud.tencent.com/developer/article/2077534 https://github.com/shepmaster/rust-ffi-omnibus cbindgen 简介 二进制方式构建 $ cargo install cbindgen //默认构建C头文件 C语言需要 --lang C $ cd /path/to/my/project && cbindgen . -o target/…...

从全局变量寻找到Tomcat回显方式
前言 对于回显的获取主要是在ApplicationFilterChain类的lastServicedRequest / lastServicedResponse两个属性,是使用的ThreadLocal进行修饰的,并且,在执行请求的过程中,通过反射修改属性值,能够记录下当前线程的req…...

Tapdata Connector 实用指南:数据入仓场景之数据实时同步到 BigQuery
【前言】作为中国的 “Fivetran/Airbyte”, Tapdata 是一个以低延迟数据移动为核心优势构建的现代数据平台,内置 60 数据连接器,拥有稳定的实时采集和传输能力、秒级响应的数据实时计算能力、稳定易用的数据实时服务能力,以及低代码可视化操作…...
关于机器人状态估计(12)-VIO/VSLAM的稀疏与稠密
VIO三相性与世界观室内ALL IN ONE 首先以此链接先对近期工作的视频做个正经的引流,完成得这么好的效果,仅仅是因为知乎限流1分钟以内的视频,导致整个浏览量不到300,让人非常不爽。 这套系统已经完成了,很快将正式发布…...
Python每日一练(20230220)
目录 1. 存在重复元素 II 2. 按要求实现程序功能 3. 分割链表 附录 链表 1. 存在重复元素 II 给定一个整数数组和一个整数 k,判断数组中是否存在两个不同的索引 i 和 j,使得 nums [i] nums [j],并且 i 和 j 的差的 绝对值 至多为 k。 …...

技术总监的“技术提升”
技术负责人的能力要求是什么?成本中心技术负责人最重要的工作是让其他CXO理解、认可并且支持技术部的工作,否则作为成本部门,在公司的地位会很低。技术创新光是让其他部门理解还不行,技术还需要创造价值,所以需要做技术创新。上面…...
kettle安装部署_简单认识_Spoon勺子界面---大数据之kettle工作笔记002
然后我们来看一下这个kettle的安装,很简单,下载解压就可以了 上面的地址是官网很烂 下面的地址好一些 这个是官网可以看到很慢,很不友好 这个是下面那个地址,可以看到 最新的是9.0了,一般都用 一般都用8.2 这里下载这个就可以了 下载以后可以看到有个pdi...
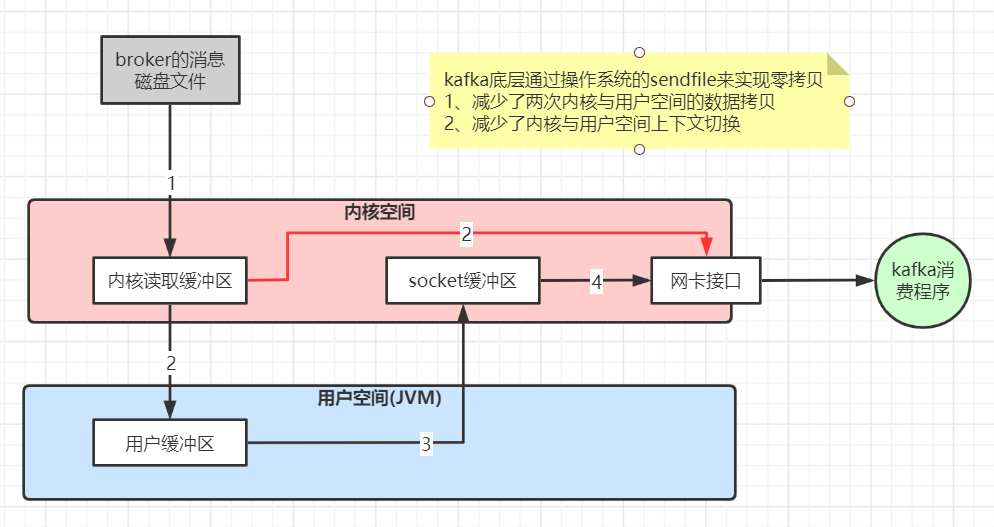
第三章 Kafka生产问题总结及性能优化实践
第三章 Kafka生产问题总结及性能优化实践 1、线上环境规划 JVM参数设置 kafka 是 scala 语言开发,运行在 JVM 上,需要对 JVM 参数合理设置,参看 JVM 调优专题 修改 bin/kafka-start-server.sh 中的 JVM 设置,假设机器是 32G 内…...

Comparable和Comparator的区别
一、概述 Comparable和Comparator都是用来实现比较的,一般用于集合中元素的比较 基本包装类型,Integer、Long以及String都实现了Comparable接口,该接口的排序逻辑必须写在比较对象中,所以又叫自然排序 我们一般集合排序使用的Col…...

Vim 调用外部命令学习笔记
Vim 外部命令集成完全指南 文章目录 Vim 外部命令集成完全指南核心概念理解命令语法解析语法对比 常用外部命令详解文本排序与去重文本筛选与搜索高级 grep 搜索技巧文本替换与编辑字符处理高级文本处理编程语言处理其他实用命令 范围操作示例指定行范围处理复合命令示例 实用技…...
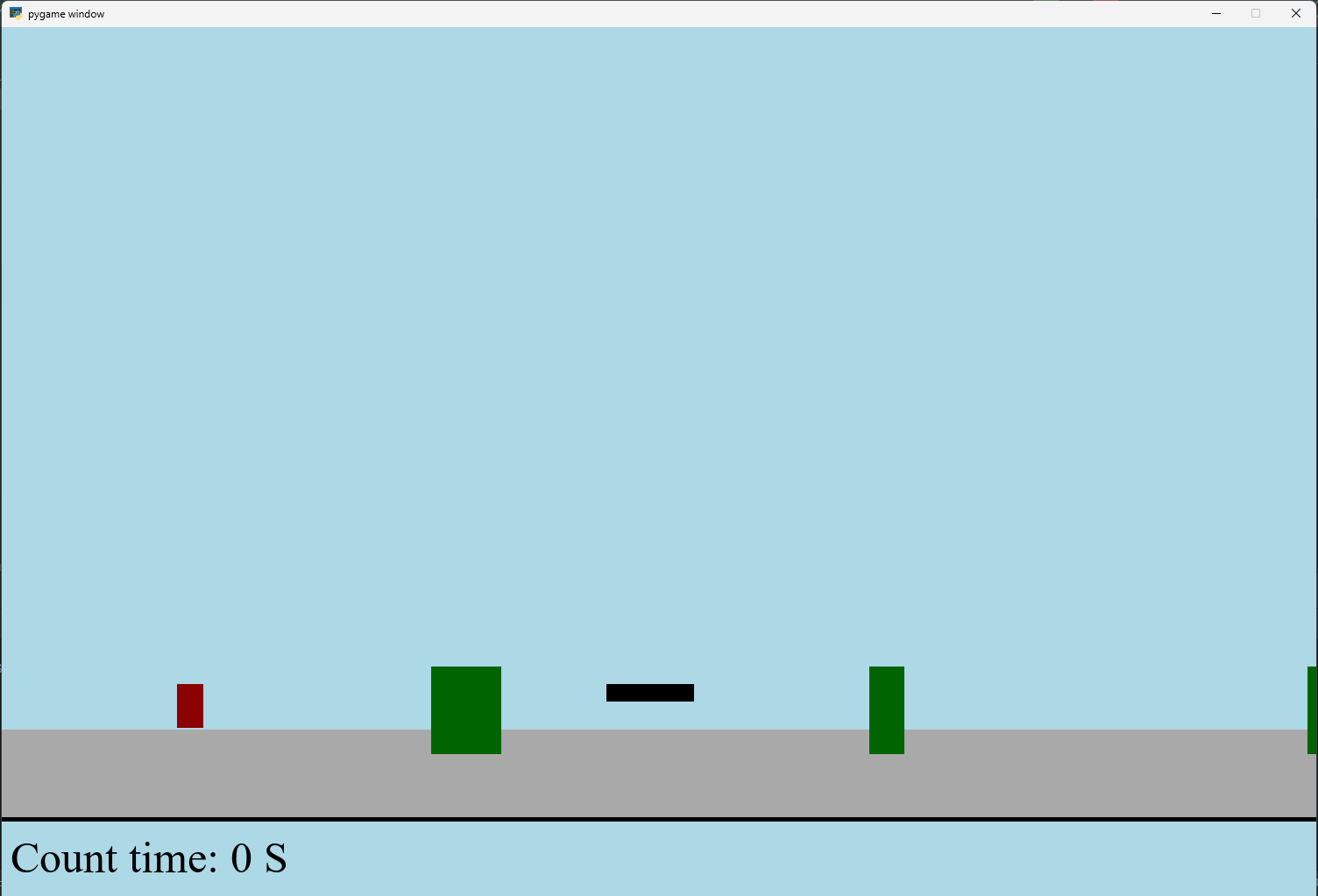
【Python】 -- 趣味代码 - 小恐龙游戏
文章目录 文章目录 00 小恐龙游戏程序设计框架代码结构和功能游戏流程总结01 小恐龙游戏程序设计02 百度网盘地址00 小恐龙游戏程序设计框架 这段代码是一个基于 Pygame 的简易跑酷游戏的完整实现,玩家控制一个角色(龙)躲避障碍物(仙人掌和乌鸦)。以下是代码的详细介绍:…...

关于iview组件中使用 table , 绑定序号分页后序号从1开始的解决方案
问题描述:iview使用table 中type: "index",分页之后 ,索引还是从1开始,试过绑定后台返回数据的id, 这种方法可行,就是后台返回数据的每个页面id都不完全是按照从1开始的升序,因此百度了下,找到了…...
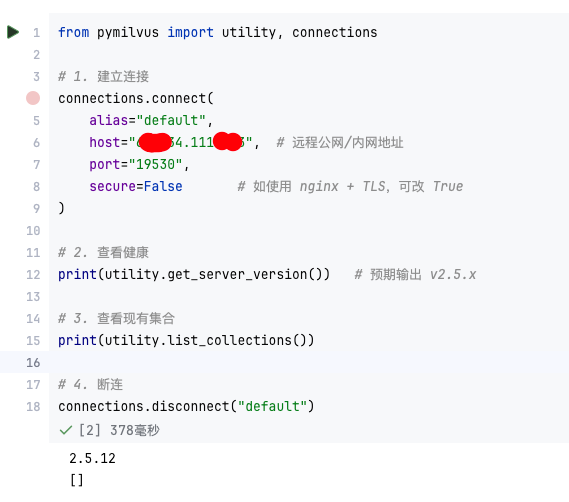
【大模型RAG】Docker 一键部署 Milvus 完整攻略
本文概要 Milvus 2.5 Stand-alone 版可通过 Docker 在几分钟内完成安装;只需暴露 19530(gRPC)与 9091(HTTP/WebUI)两个端口,即可让本地电脑通过 PyMilvus 或浏览器访问远程 Linux 服务器上的 Milvus。下面…...

Auto-Coder使用GPT-4o完成:在用TabPFN这个模型构建一个预测未来3天涨跌的分类任务
通过akshare库,获取股票数据,并生成TabPFN这个模型 可以识别、处理的格式,写一个完整的预处理示例,并构建一个预测未来 3 天股价涨跌的分类任务 用TabPFN这个模型构建一个预测未来 3 天股价涨跌的分类任务,进行预测并输…...
新能源汽车智慧充电桩管理方案:新能源充电桩散热问题及消防安全监管方案
随着新能源汽车的快速普及,充电桩作为核心配套设施,其安全性与可靠性备受关注。然而,在高温、高负荷运行环境下,充电桩的散热问题与消防安全隐患日益凸显,成为制约行业发展的关键瓶颈。 如何通过智慧化管理手段优化散…...
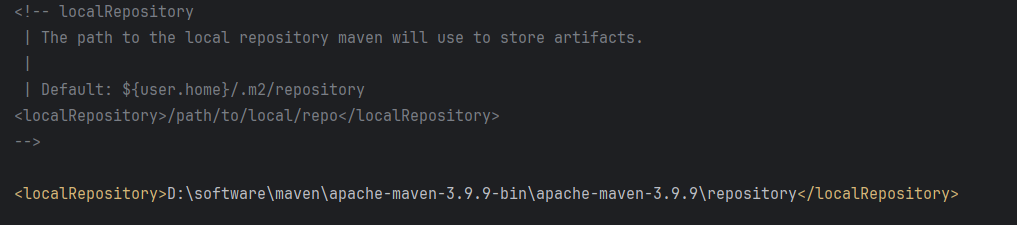
Maven 概述、安装、配置、仓库、私服详解
目录 1、Maven 概述 1.1 Maven 的定义 1.2 Maven 解决的问题 1.3 Maven 的核心特性与优势 2、Maven 安装 2.1 下载 Maven 2.2 安装配置 Maven 2.3 测试安装 2.4 修改 Maven 本地仓库的默认路径 3、Maven 配置 3.1 配置本地仓库 3.2 配置 JDK 3.3 IDEA 配置本地 Ma…...
【笔记】WSL 中 Rust 安装与测试完整记录
#工作记录 WSL 中 Rust 安装与测试完整记录 1. 运行环境 系统:Ubuntu 24.04 LTS (WSL2)架构:x86_64 (GNU/Linux)Rust 版本:rustc 1.87.0 (2025-05-09)Cargo 版本:cargo 1.87.0 (2025-05-06) 2. 安装 Rust 2.1 使用 Rust 官方安…...

站群服务器的应用场景都有哪些?
站群服务器主要是为了多个网站的托管和管理所设计的,可以通过集中管理和高效资源的分配,来支持多个独立的网站同时运行,让每一个网站都可以分配到独立的IP地址,避免出现IP关联的风险,用户还可以通过控制面板进行管理功…...
)
C#学习第29天:表达式树(Expression Trees)
目录 什么是表达式树? 核心概念 1.表达式树的构建 2. 表达式树与Lambda表达式 3.解析和访问表达式树 4.动态条件查询 表达式树的优势 1.动态构建查询 2.LINQ 提供程序支持: 3.性能优化 4.元数据处理 5.代码转换和重写 适用场景 代码复杂性…...
